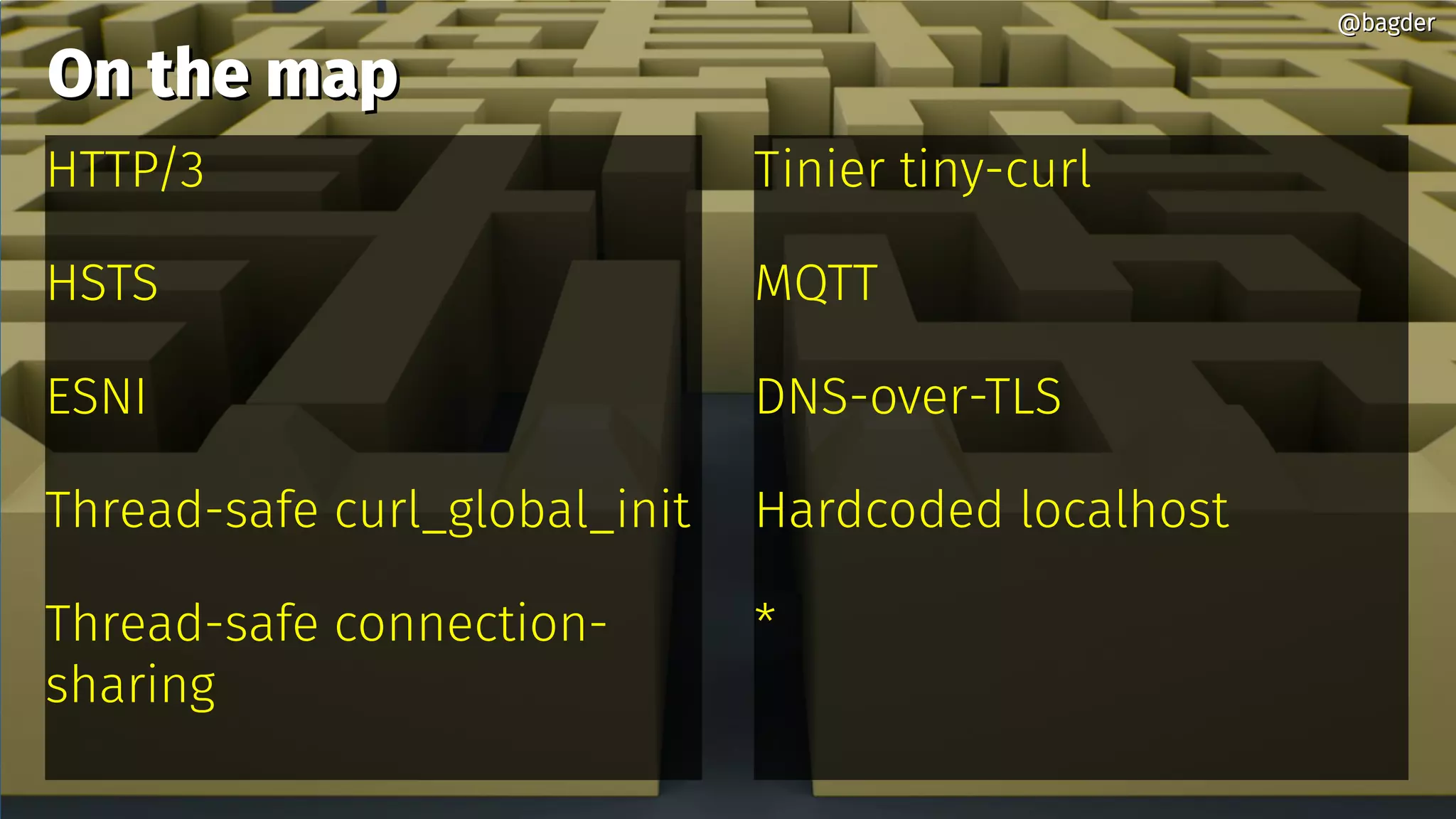
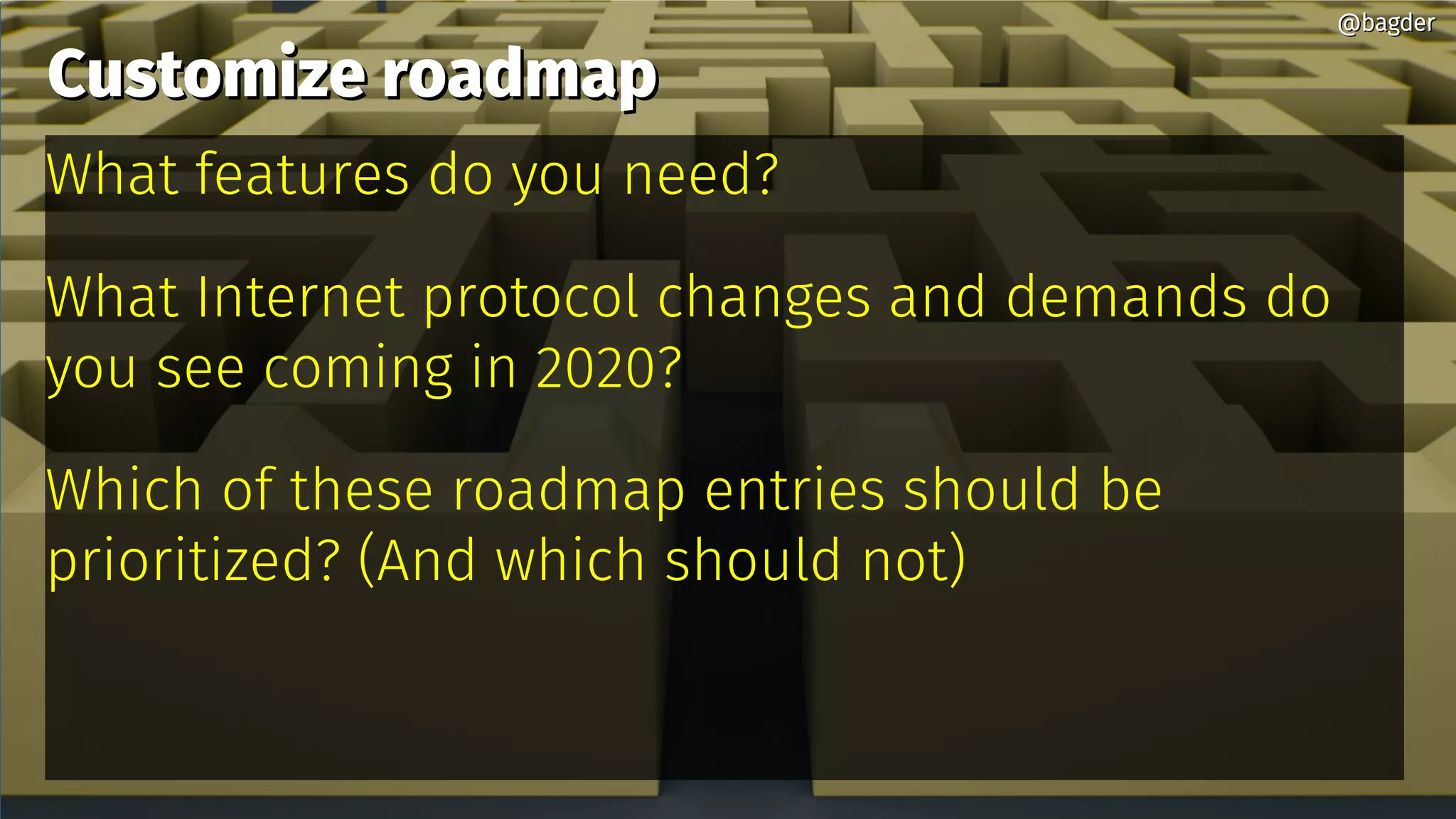
The document outlines Daniel Stenberg's roadmap for curl in 2020, emphasizing the importance of community contributions and prioritizing security and privacy. Key developments include support for HTTP/3, DNS-over-TLS, and improvements in thread safety and performance. The release cycle is structured with an 8-week period for feature merging and bug fixes, with openness to user suggestions for future developments.