Embed presentation
Download as PDF, PPTX


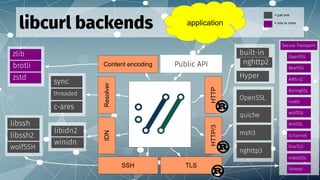


The document discusses the increasing focus on Rust for improving memory safety in the context of various technologies, such as Hyper for HTTP protocols and Rustls for TLS. It highlights several experimental components and suggests that component-based memory safety approaches are not widely embraced. The document also touches on future developments and API compatibility efforts related to these technologies.







