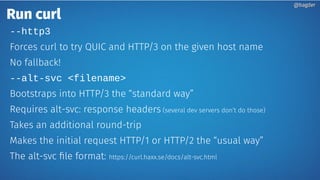
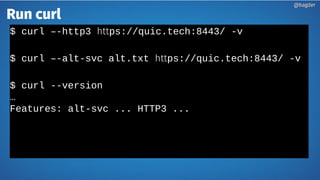
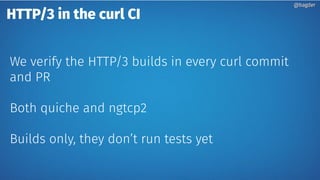
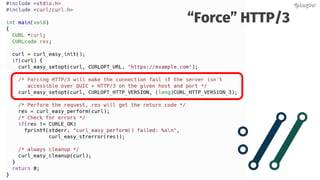
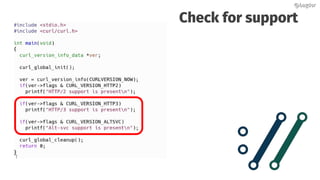
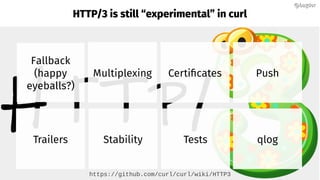
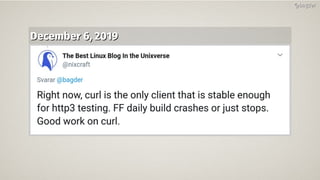
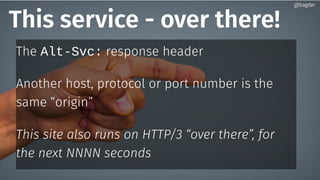
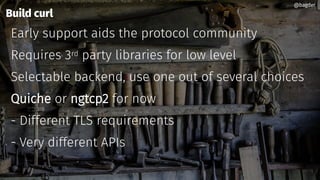
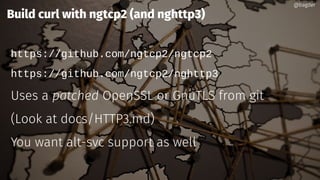
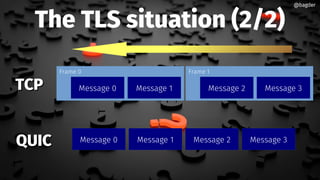
Daniel Stenberg discusses the progress being made to enable HTTP/3 support in the curl tool and libcurl library. HTTP/3 uses QUIC as its underlying transport protocol. Several challenges remain, including fallback options, stability testing, and full browser/server support. Stenberg explains how to build curl with various QUIC libraries like Quiche and ngtcp2. HTTP/3 support in curl is still experimental but aims to provide a similar user experience to HTTP/1. Support may be included in future releases as QUIC and HTTP/3 specifications continue development and more servers/browsers are deployed.






















![@bagder@bagder
OpenSSL
No support in any release, nor git
“once the 3.0 release is done, QUIC will become a significant
focus of our effort” + “final [3.0] release in early Q4 2020”
PR #8797 OpenSSL offers an API similar to the BoringSSL one.
https://github.com/openssl/openssl/pull/8797
ngtcp2 uses OpenSSL+8797
… and so does msquic, node.js and more
@bagder@bagder](https://image.slidesharecdn.com/http3-in-curl-200505072014/85/HTTP-3-in-curl-2020-27-320.jpg)