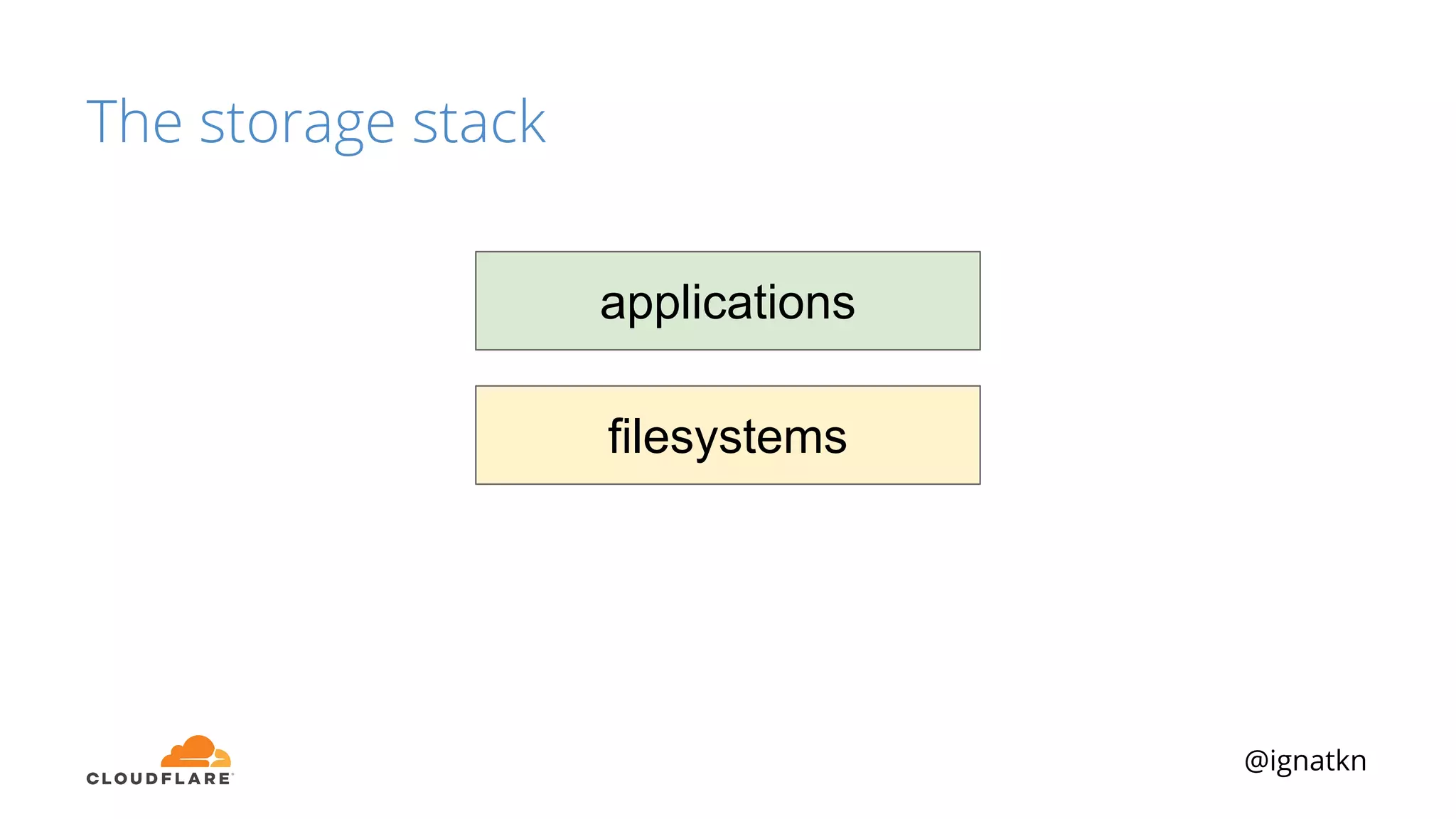
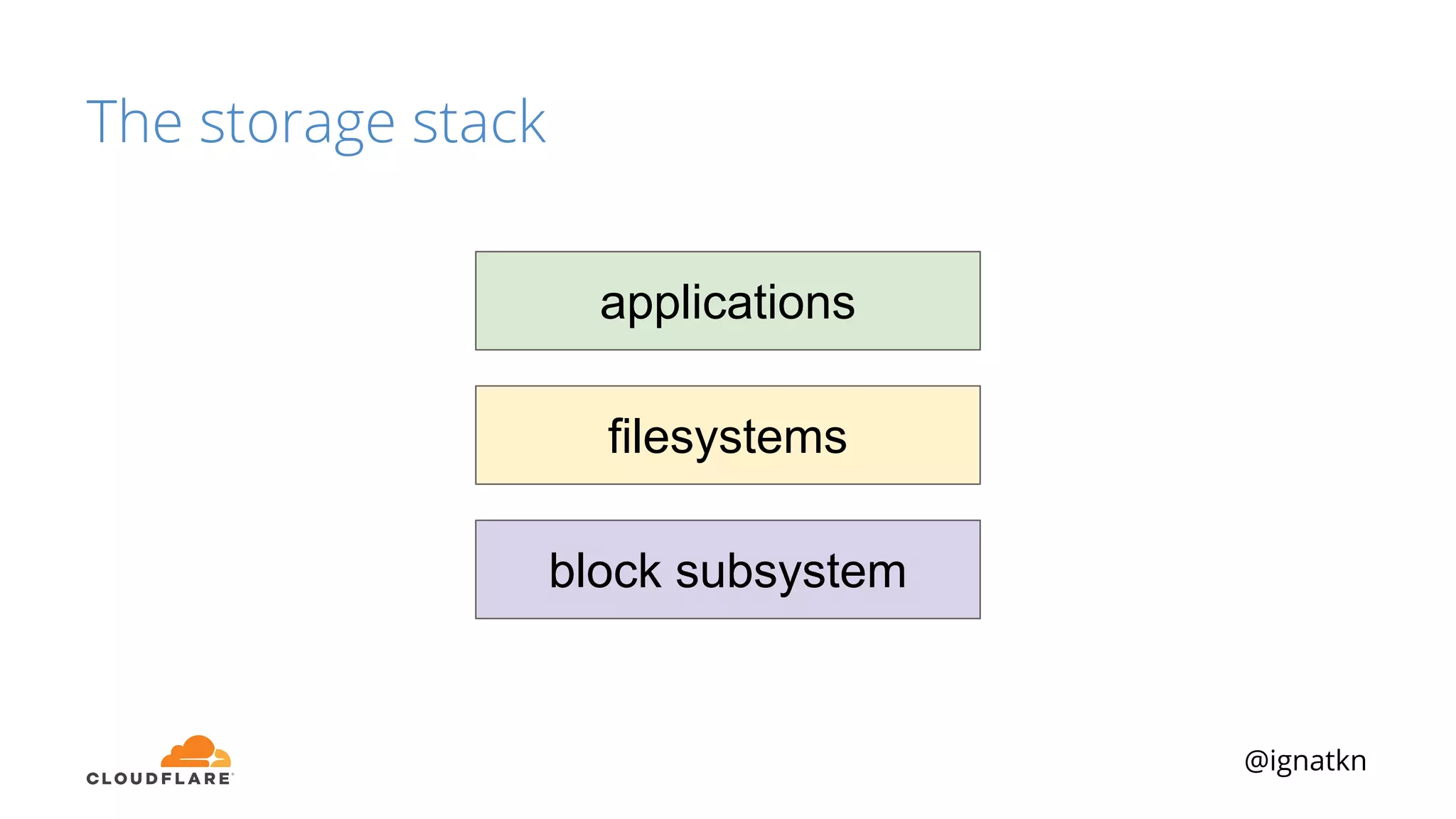
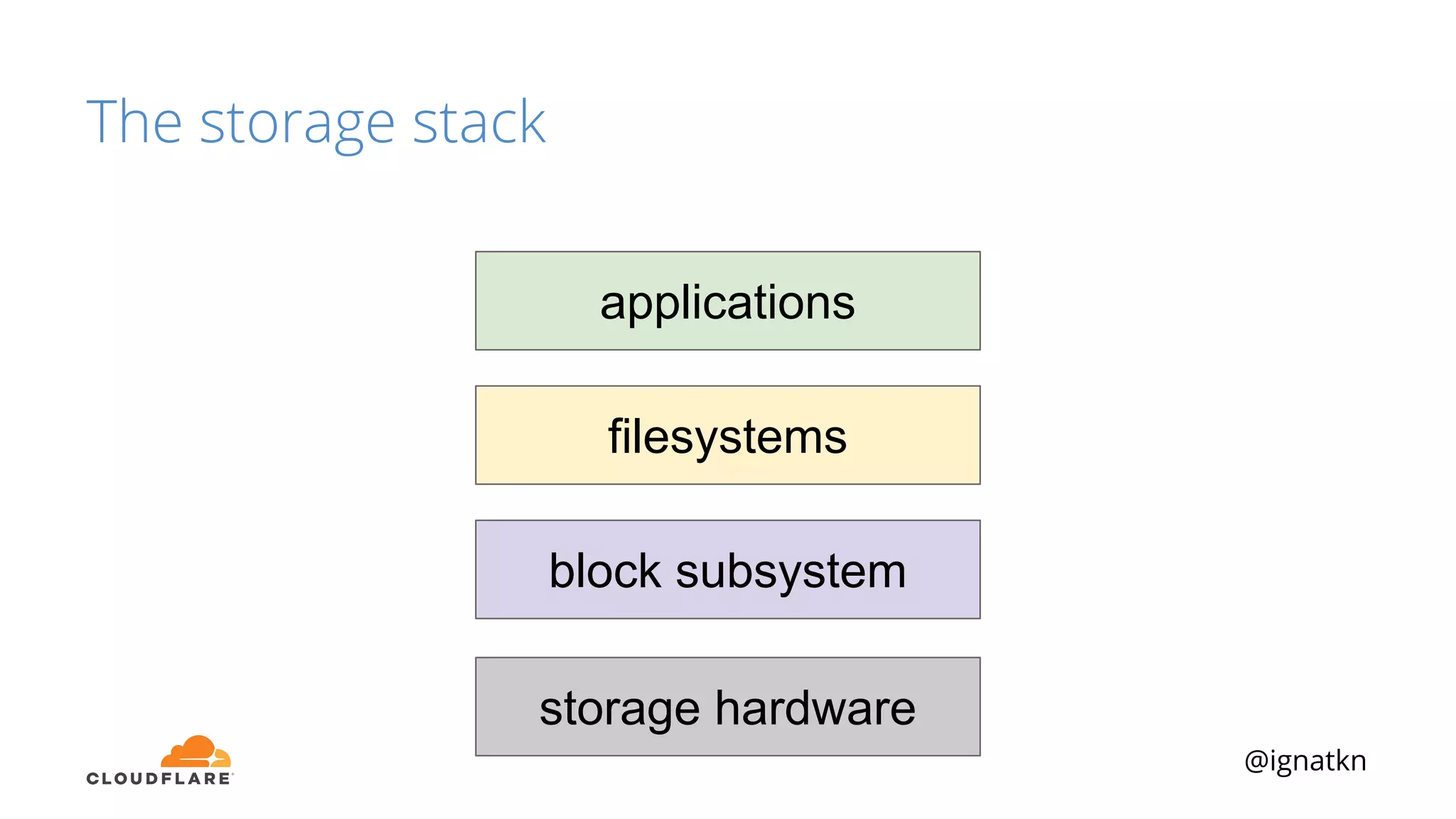
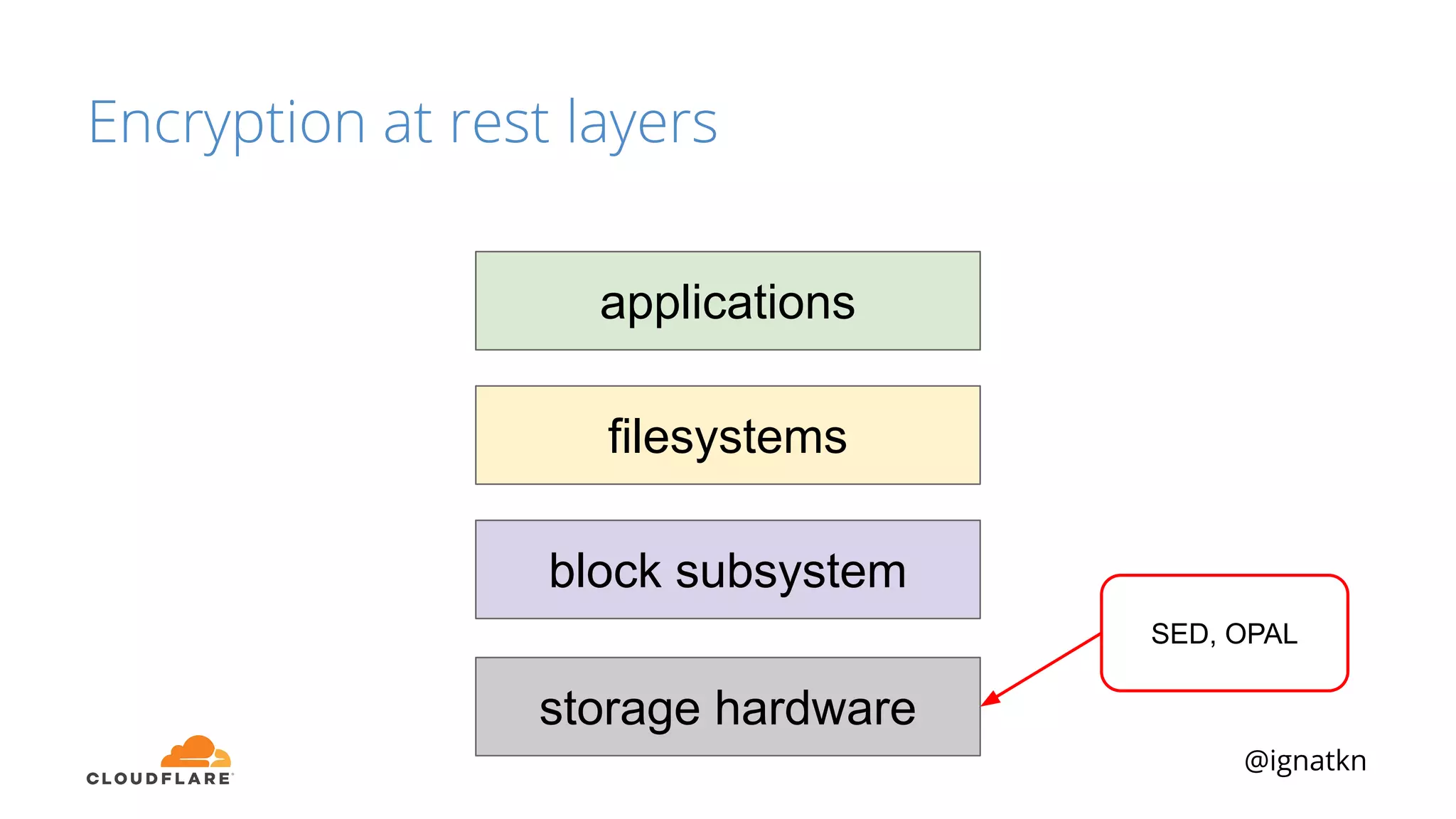
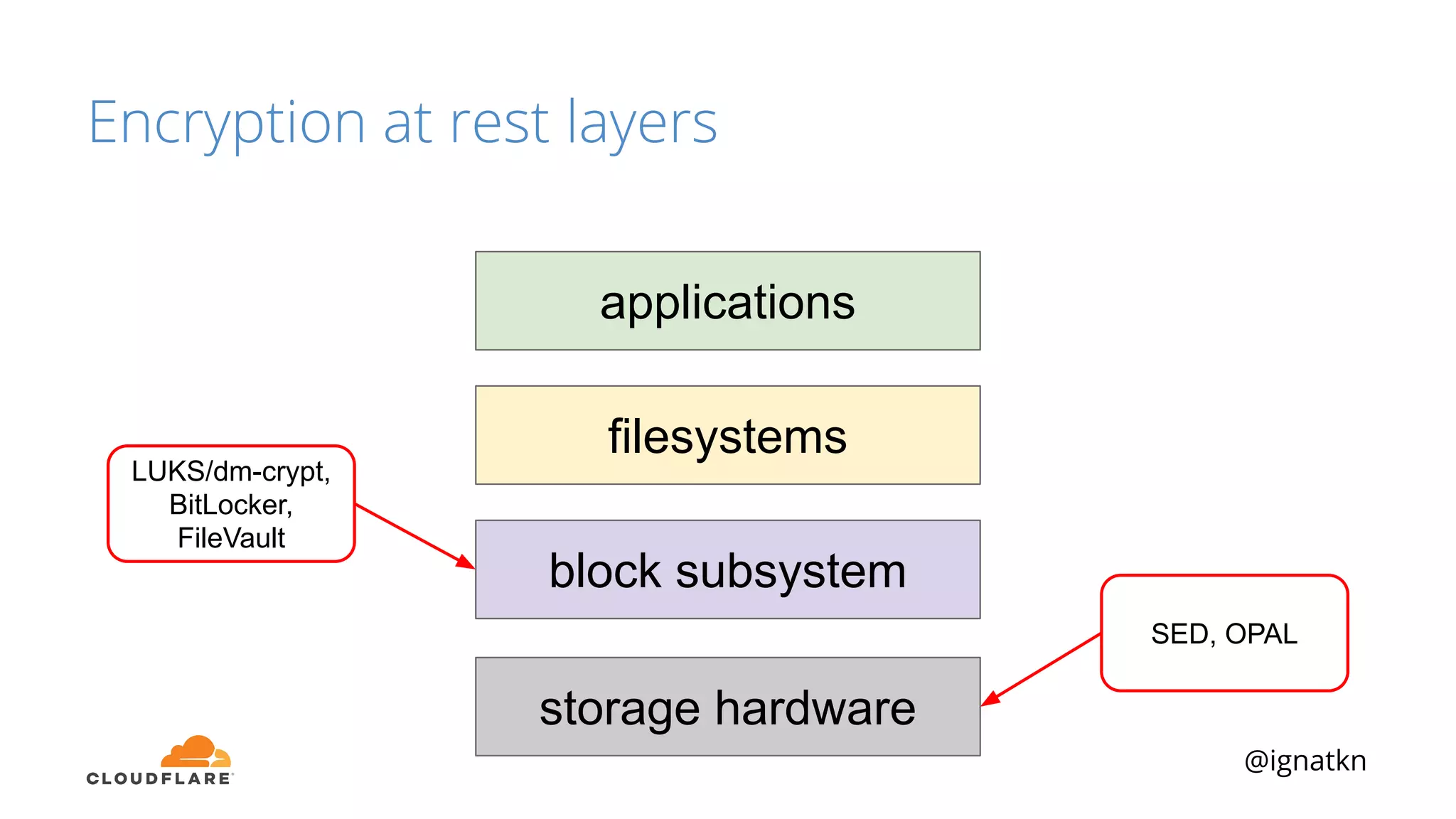
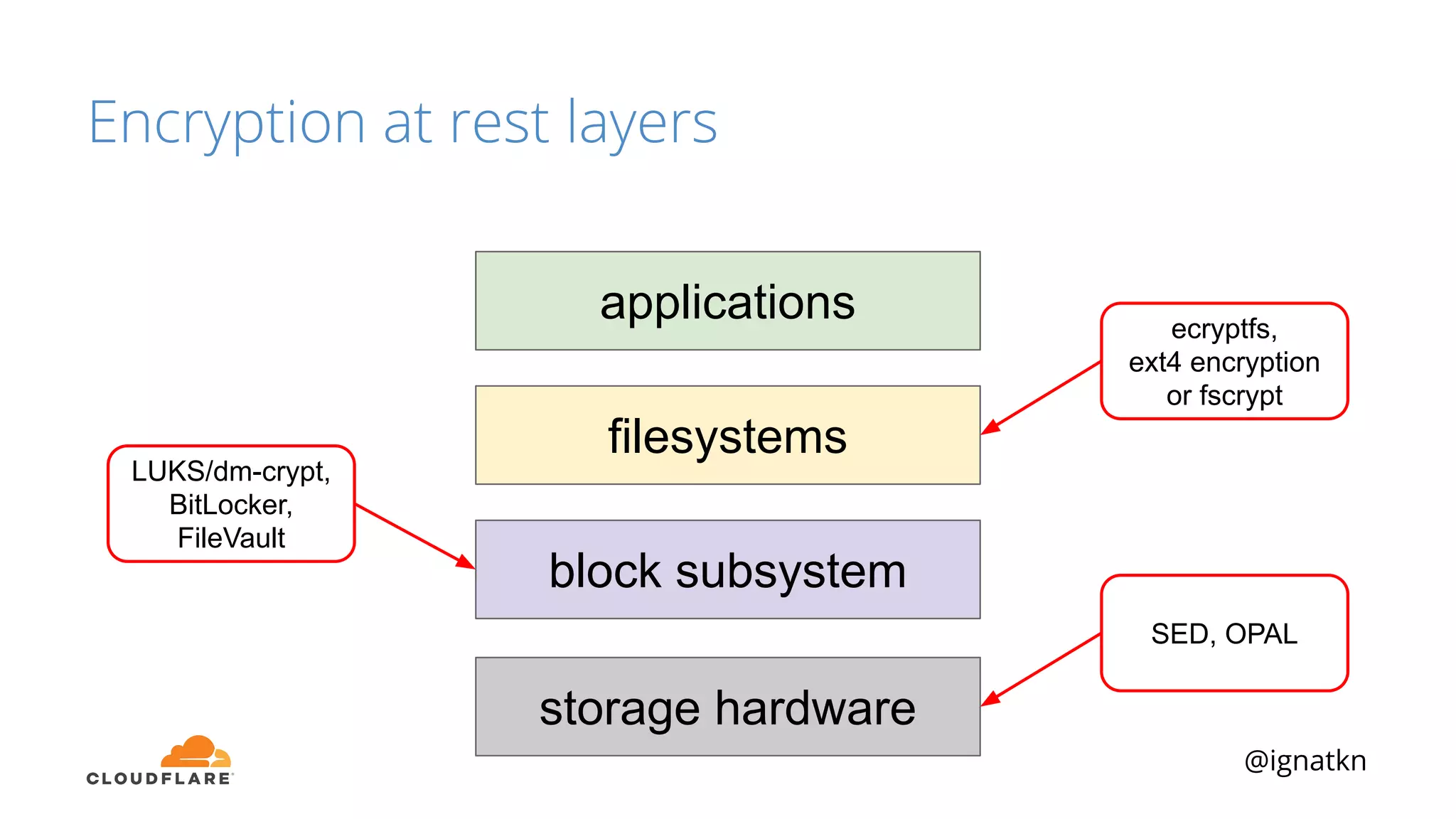
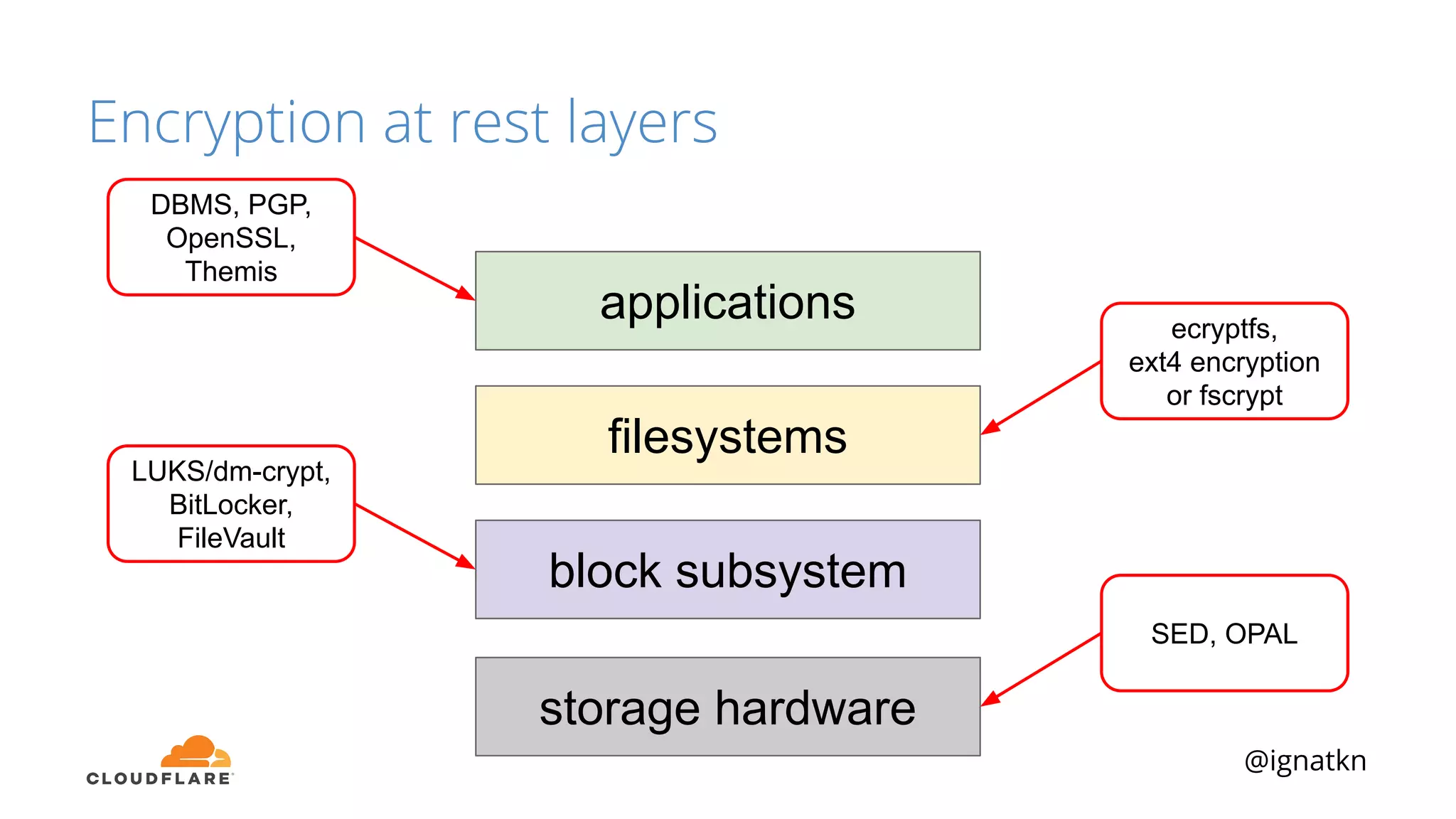
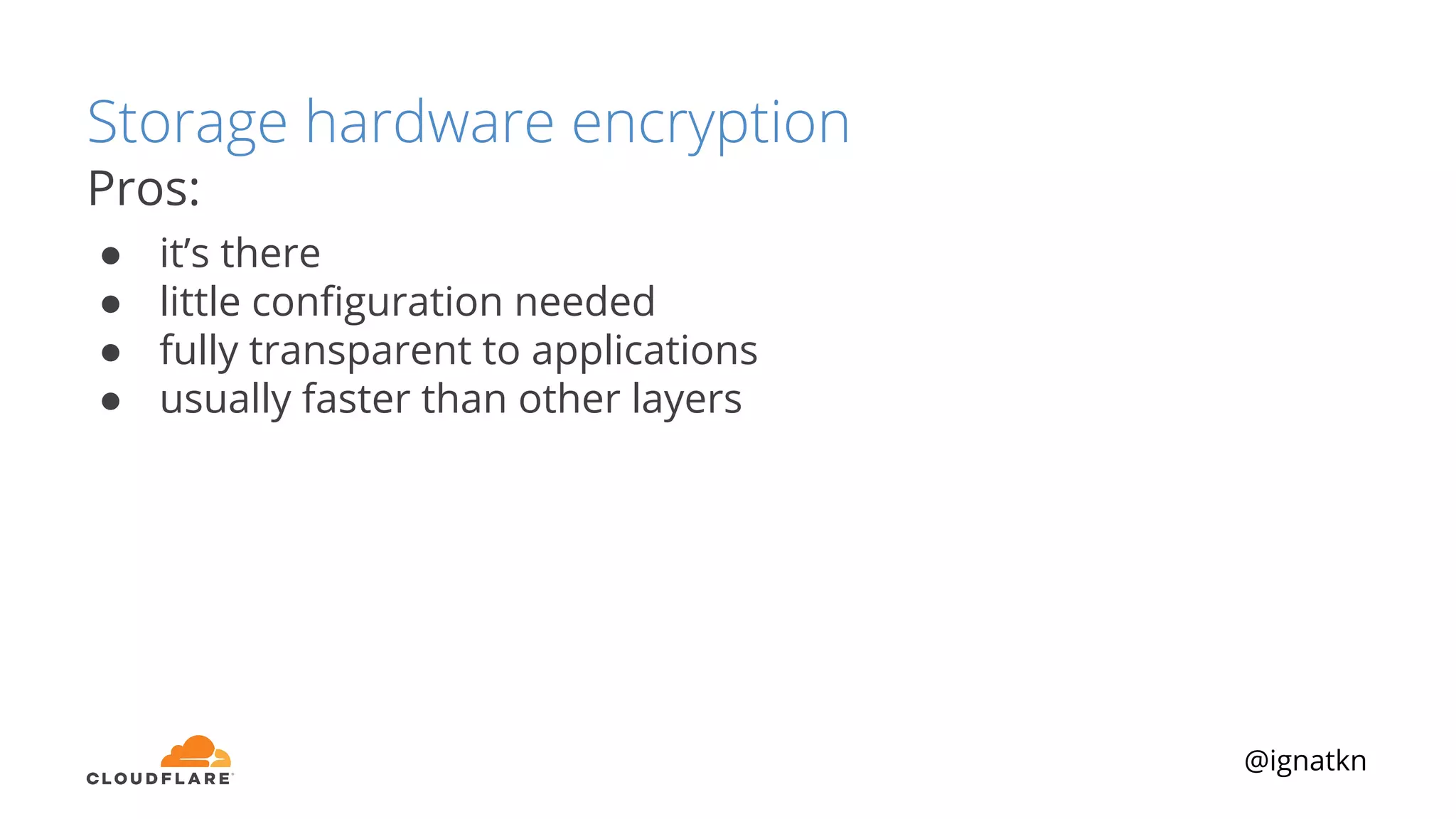
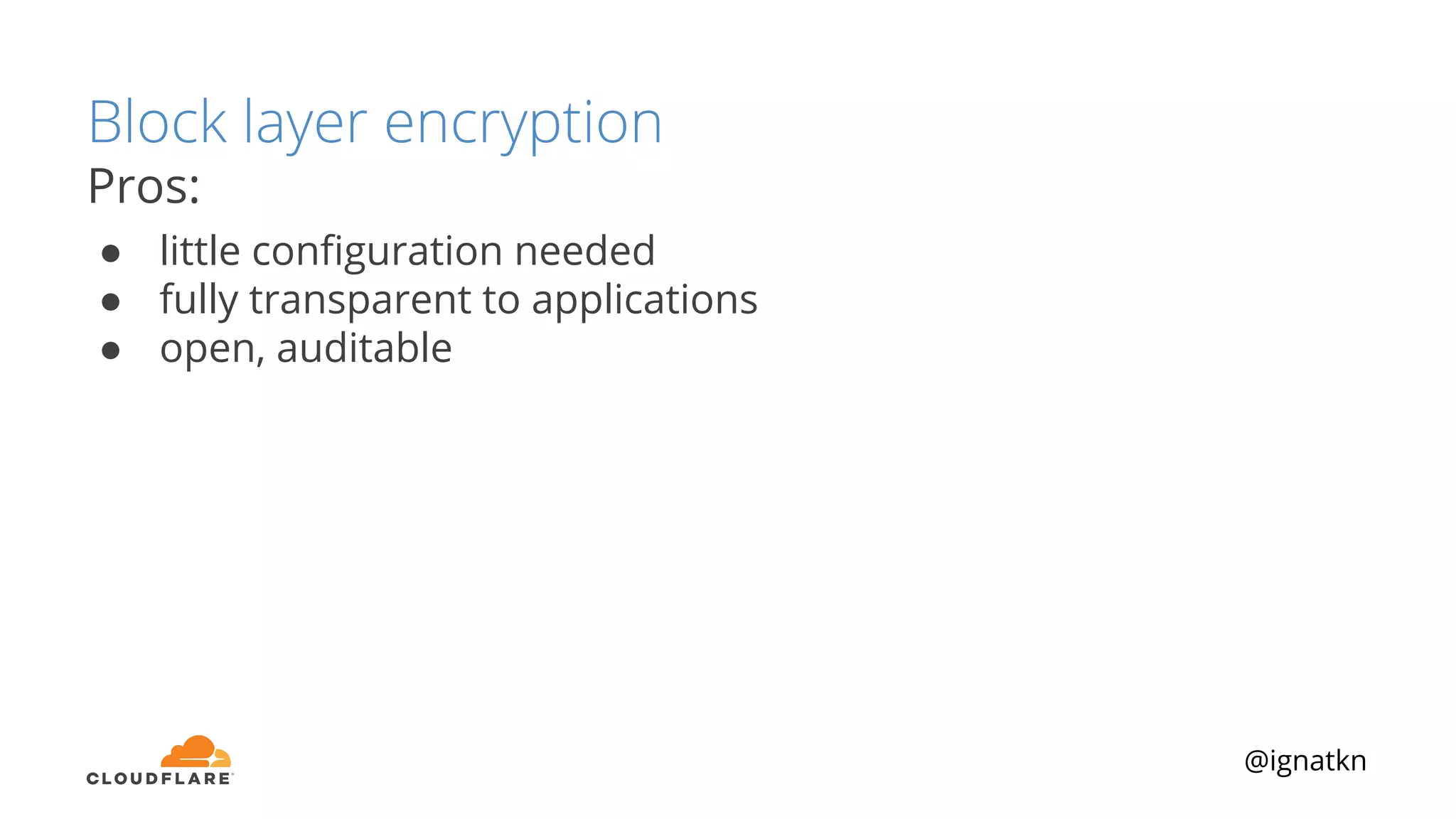
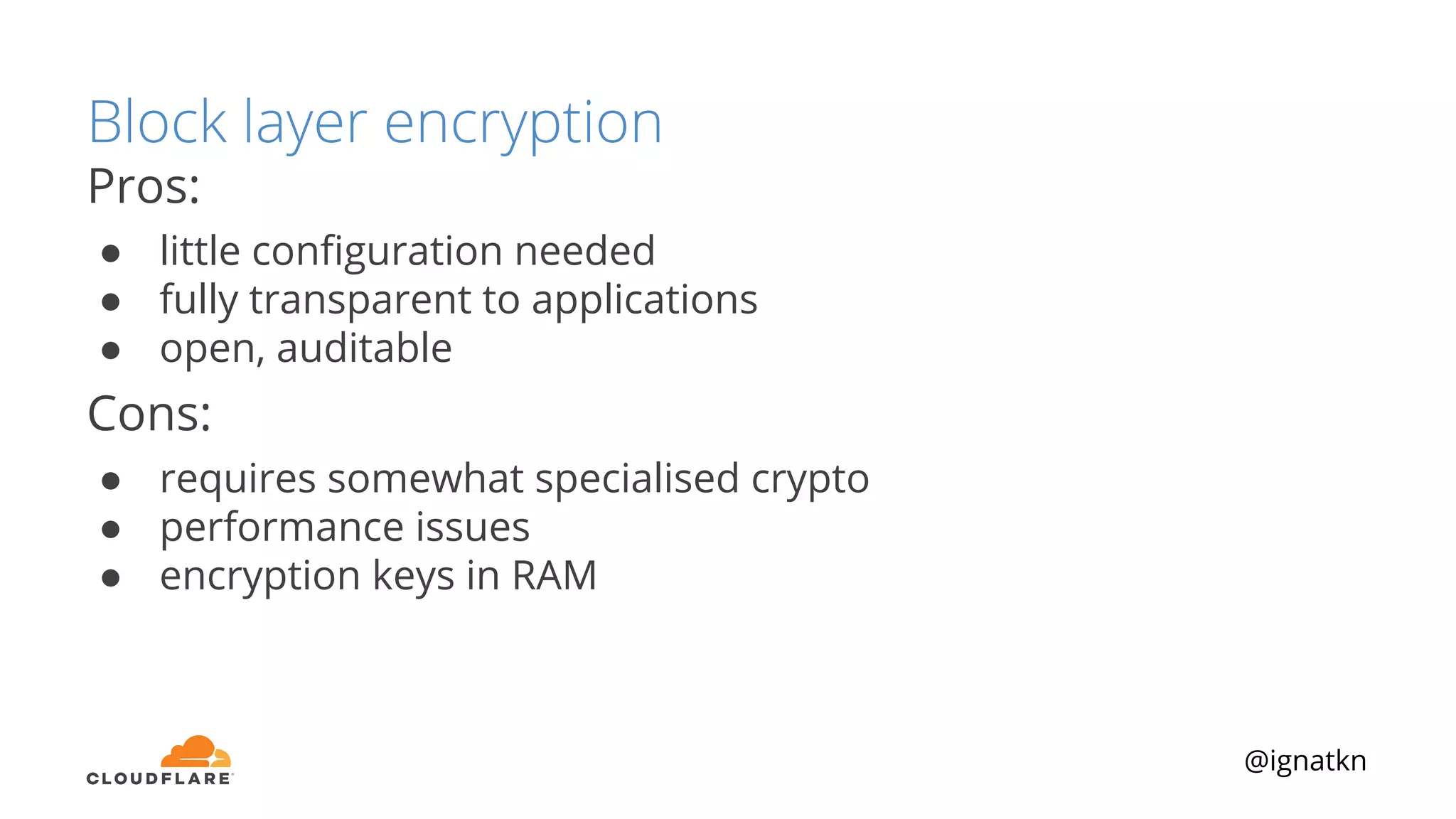
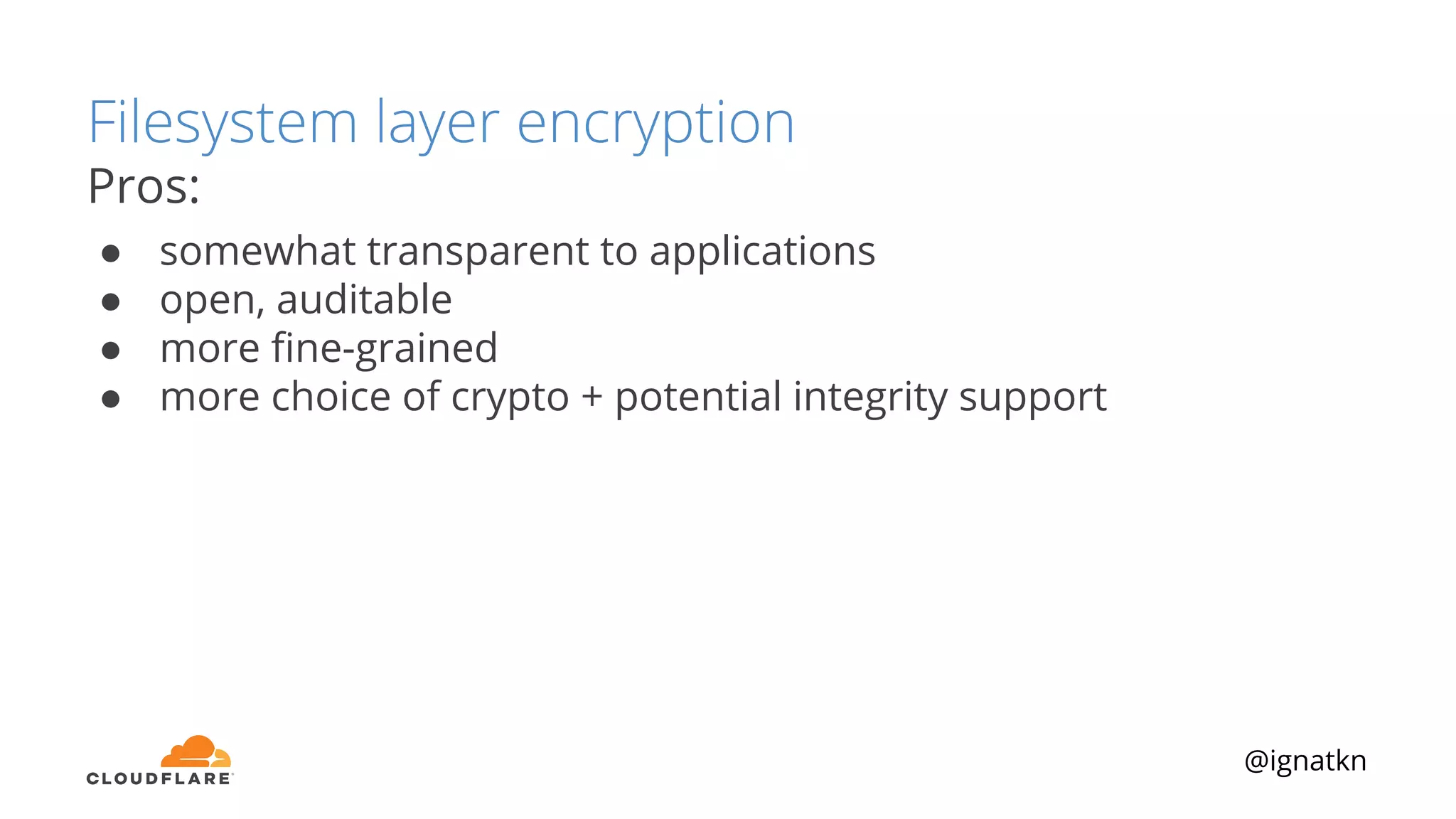
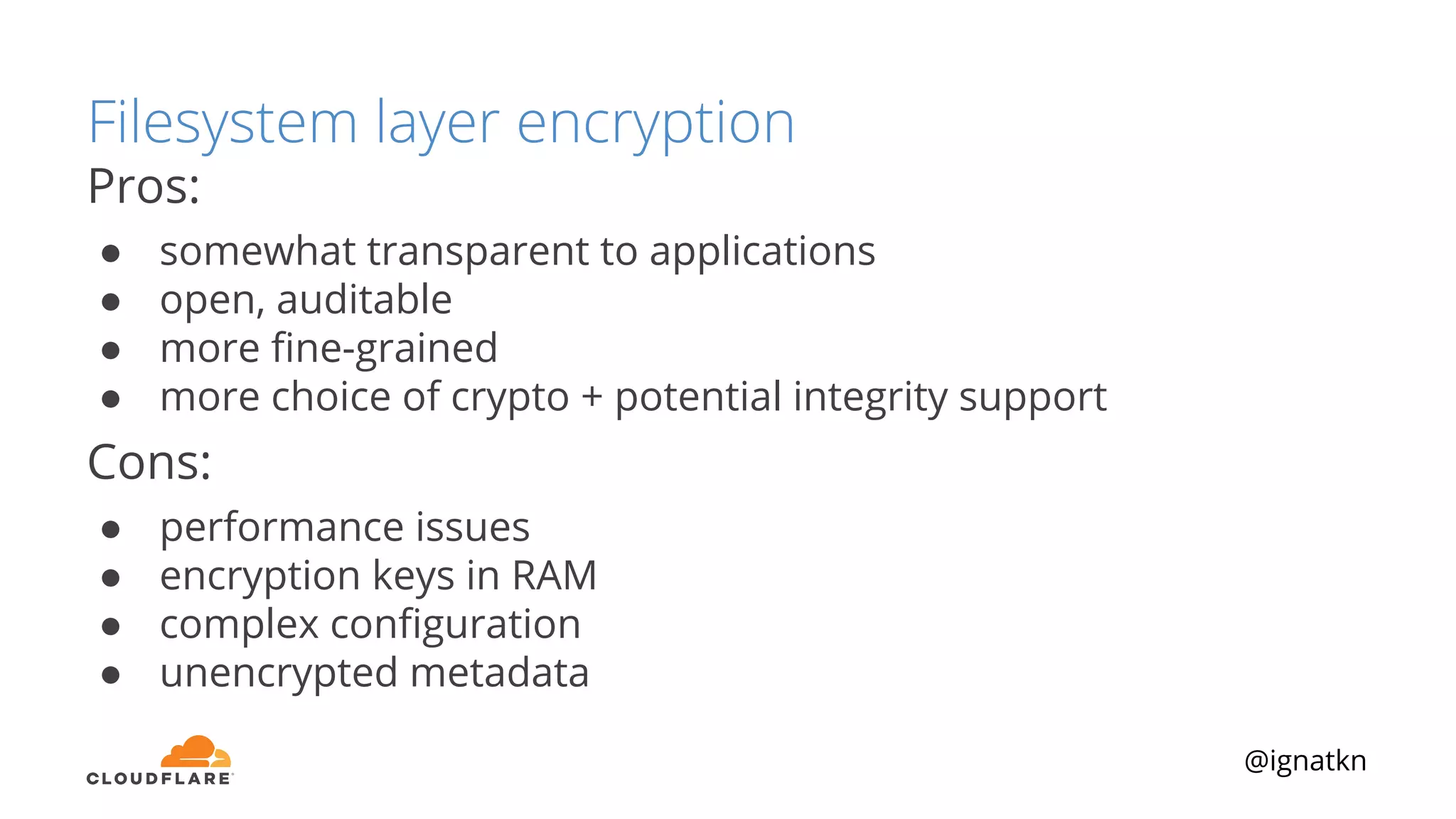
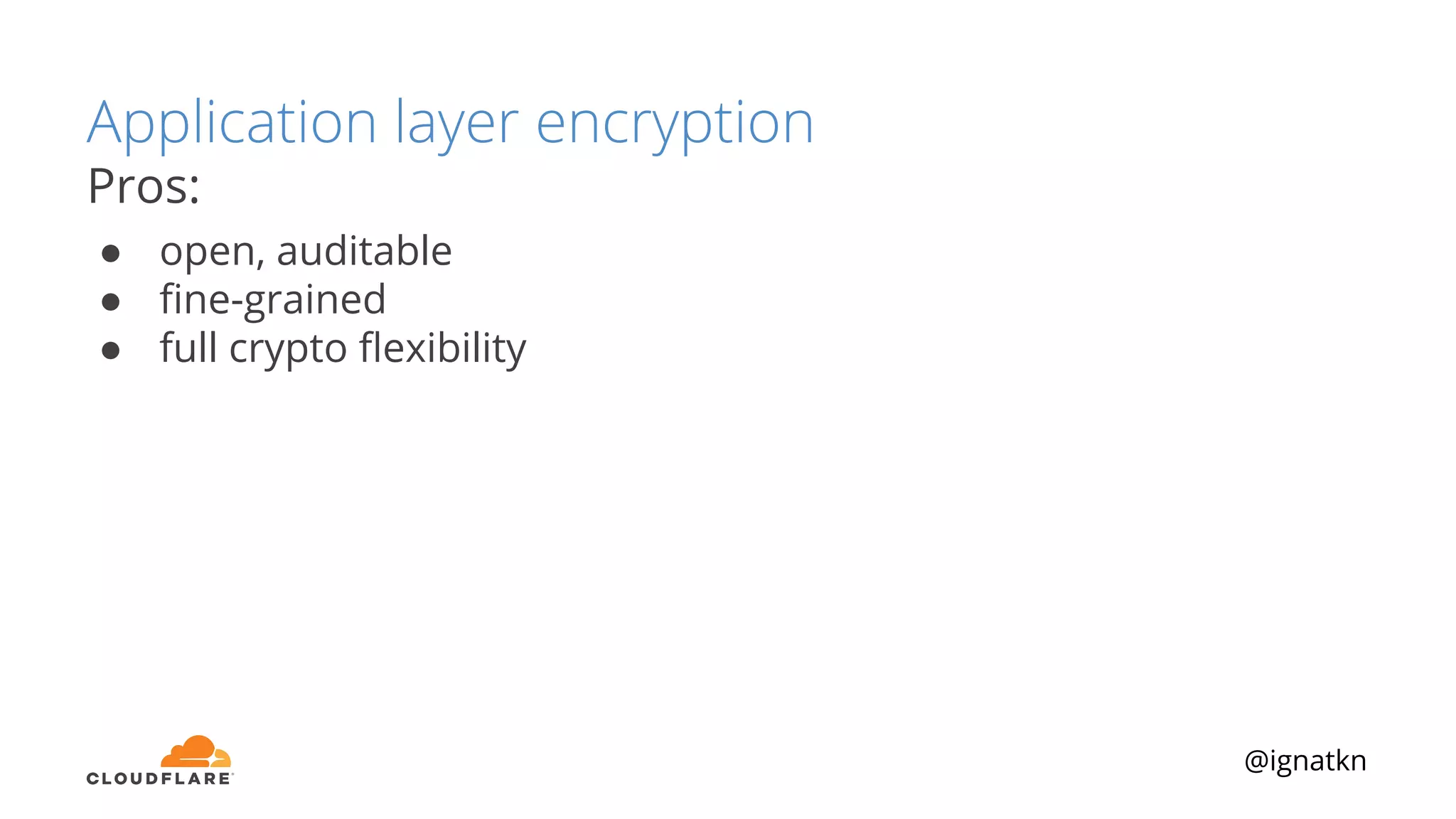
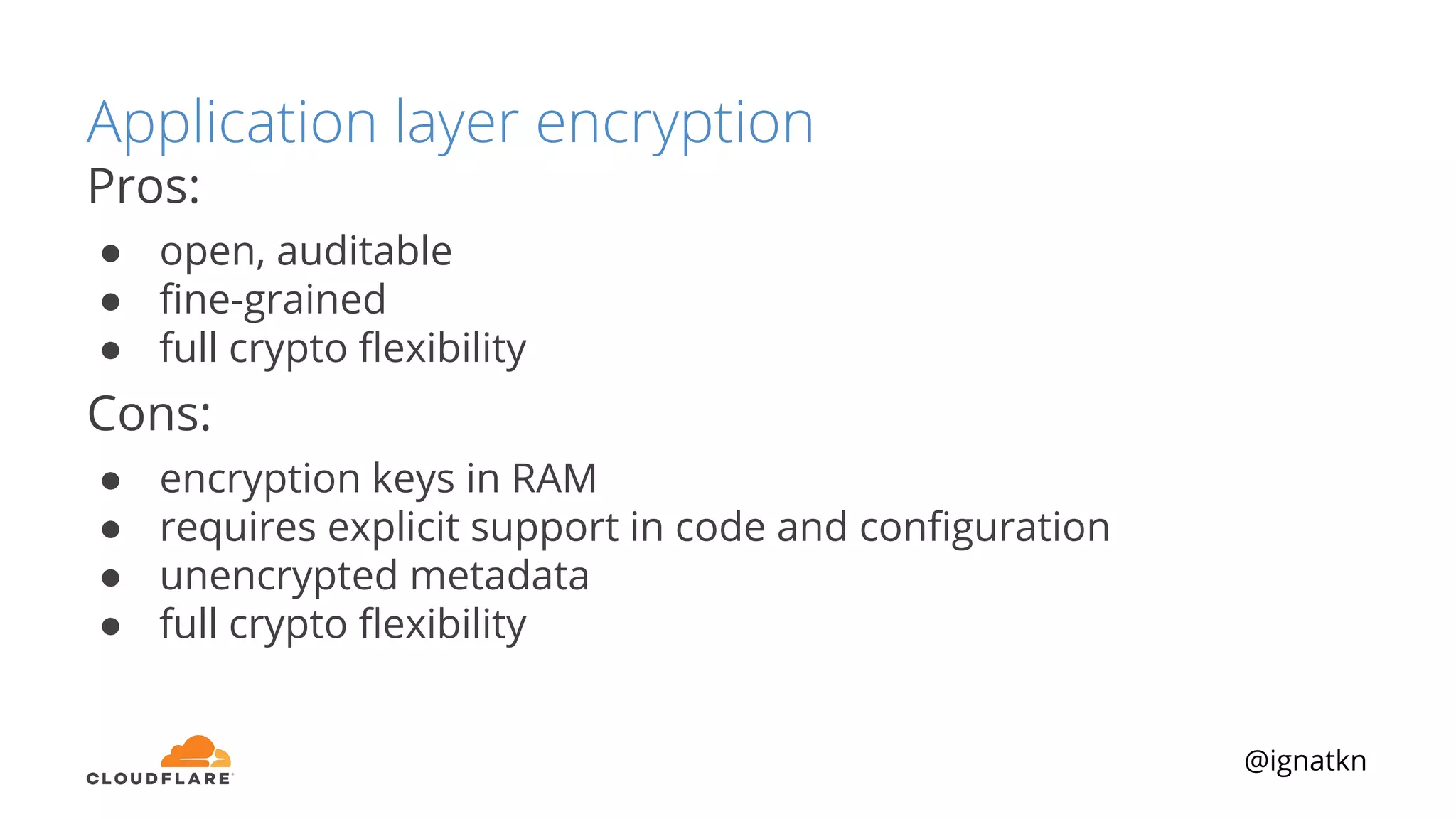
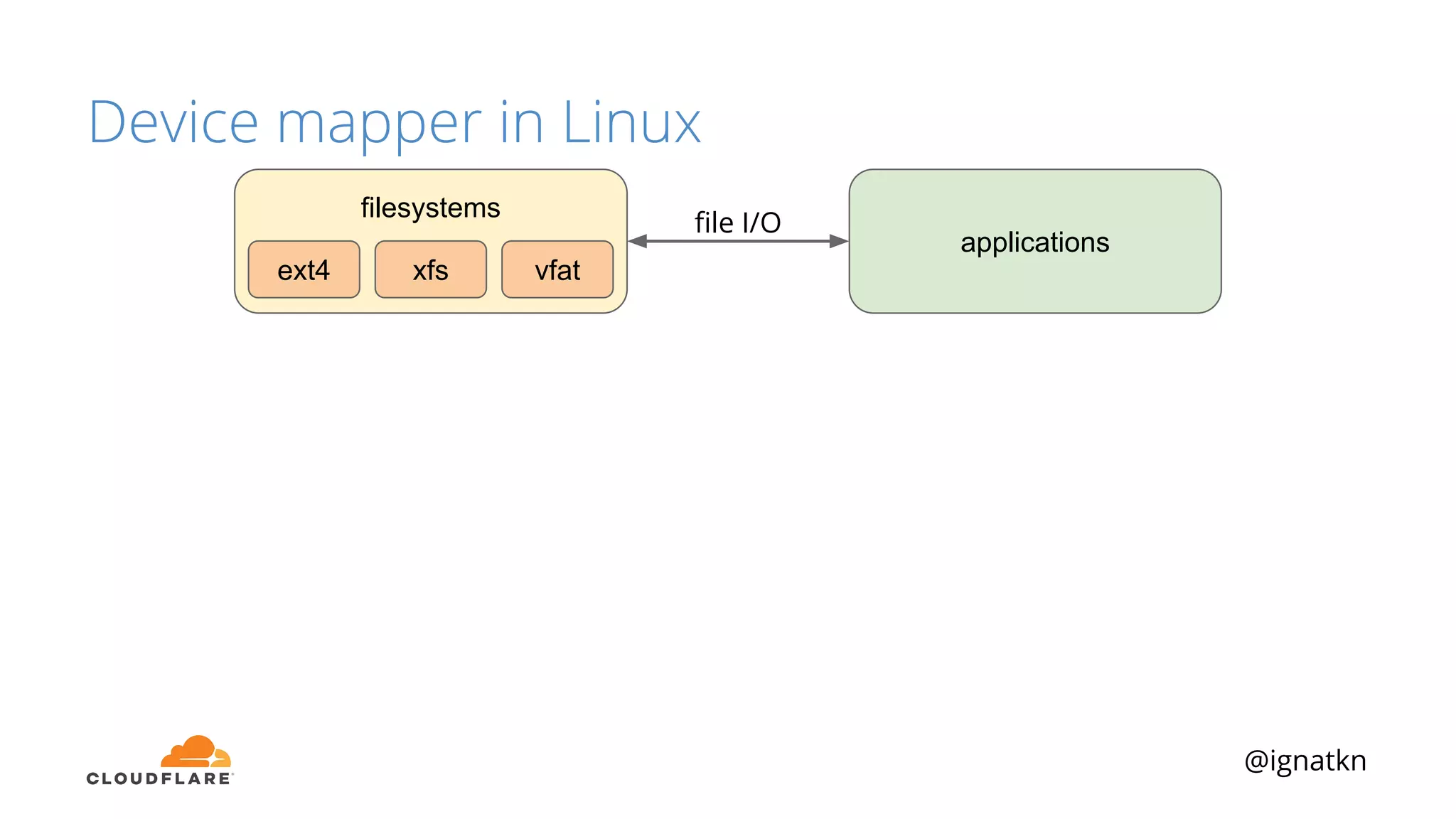
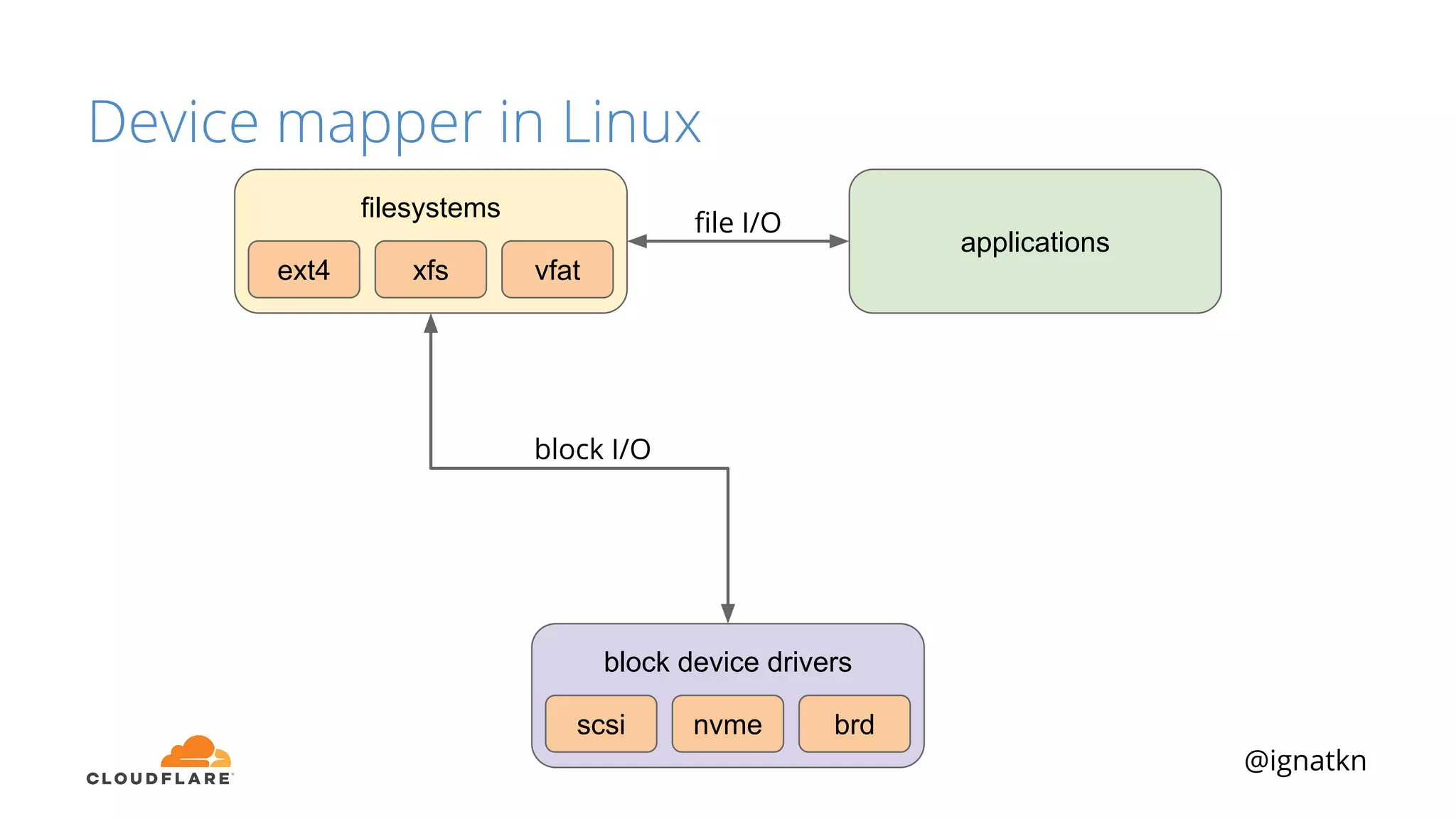
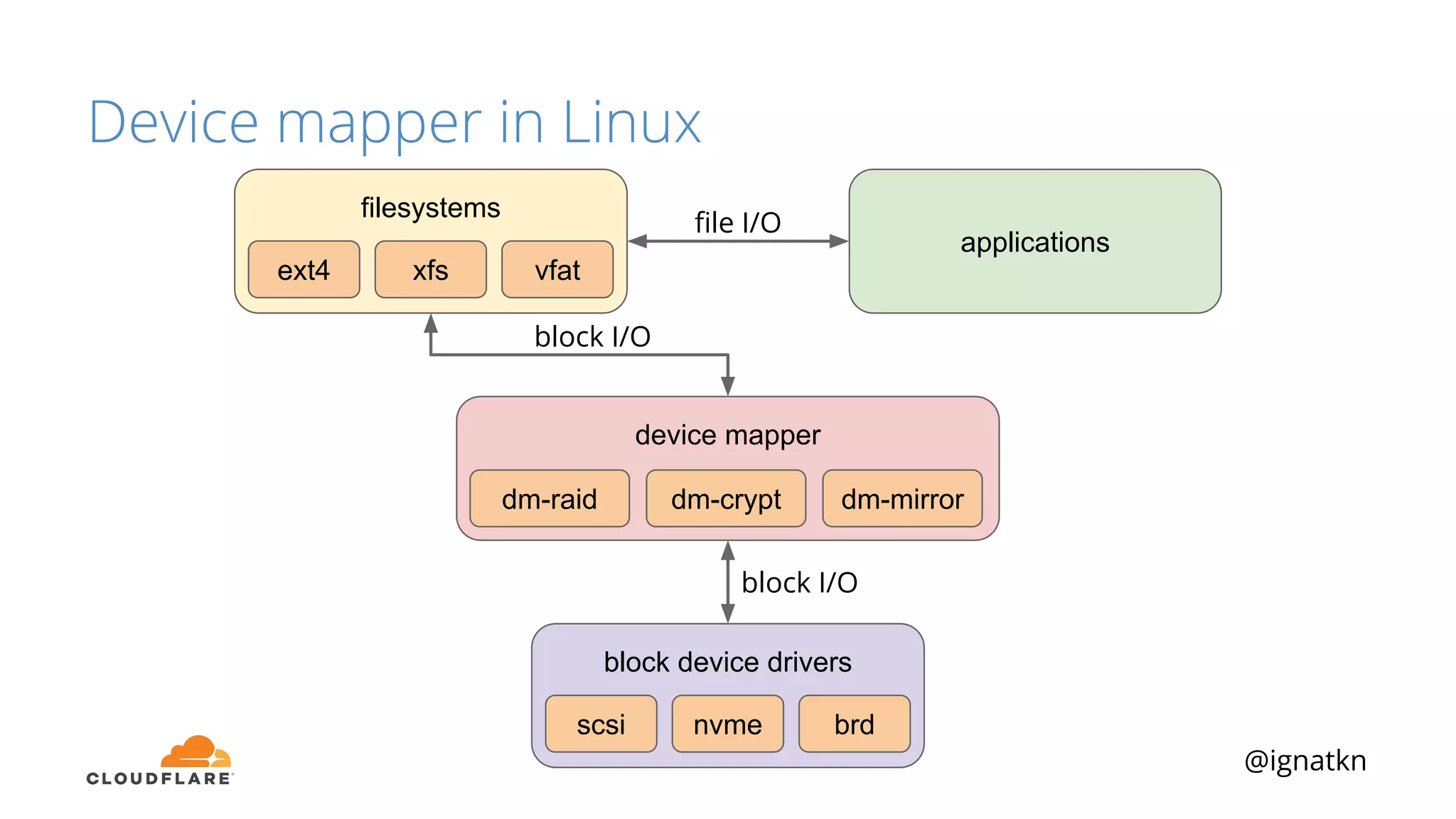
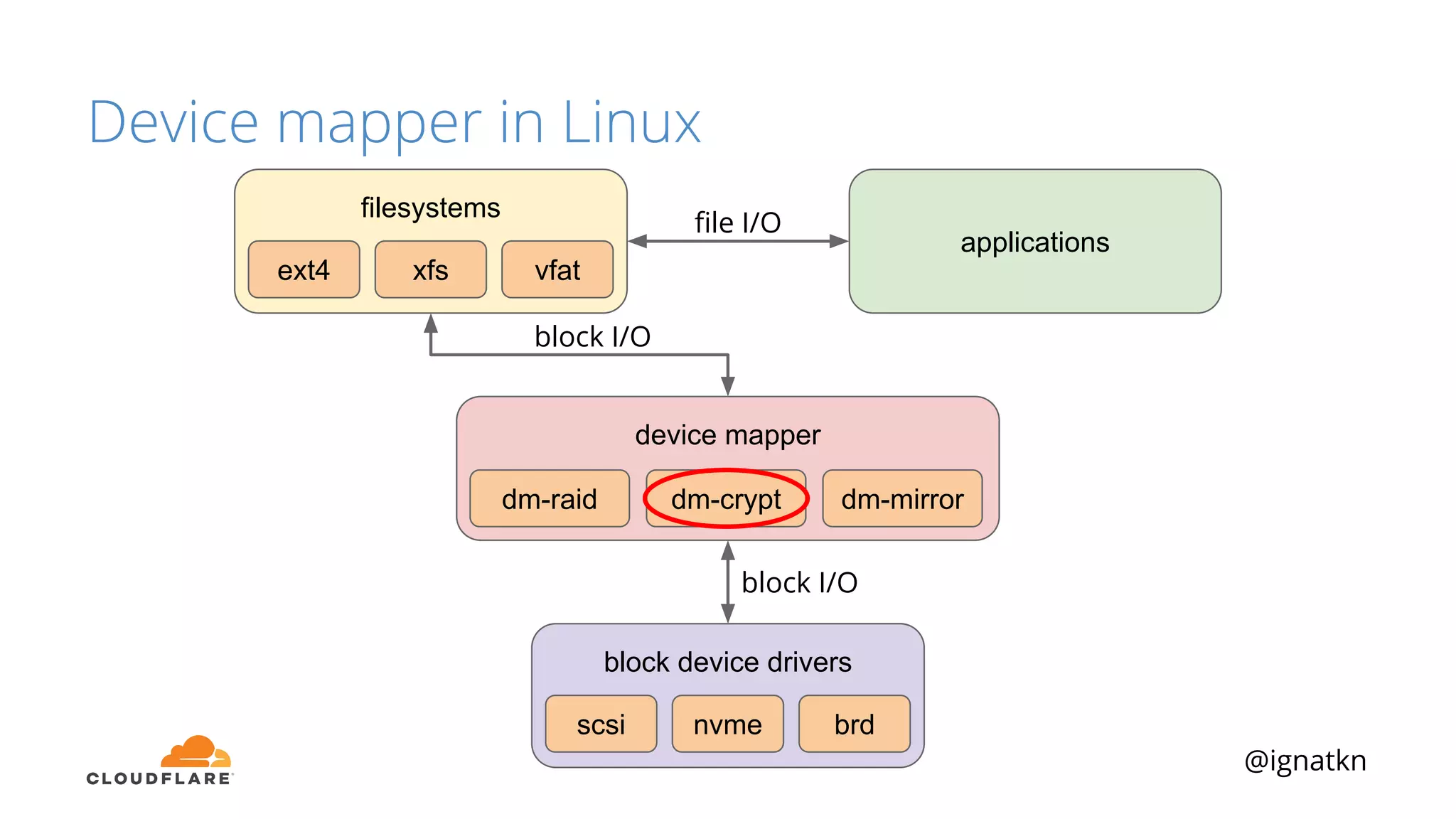
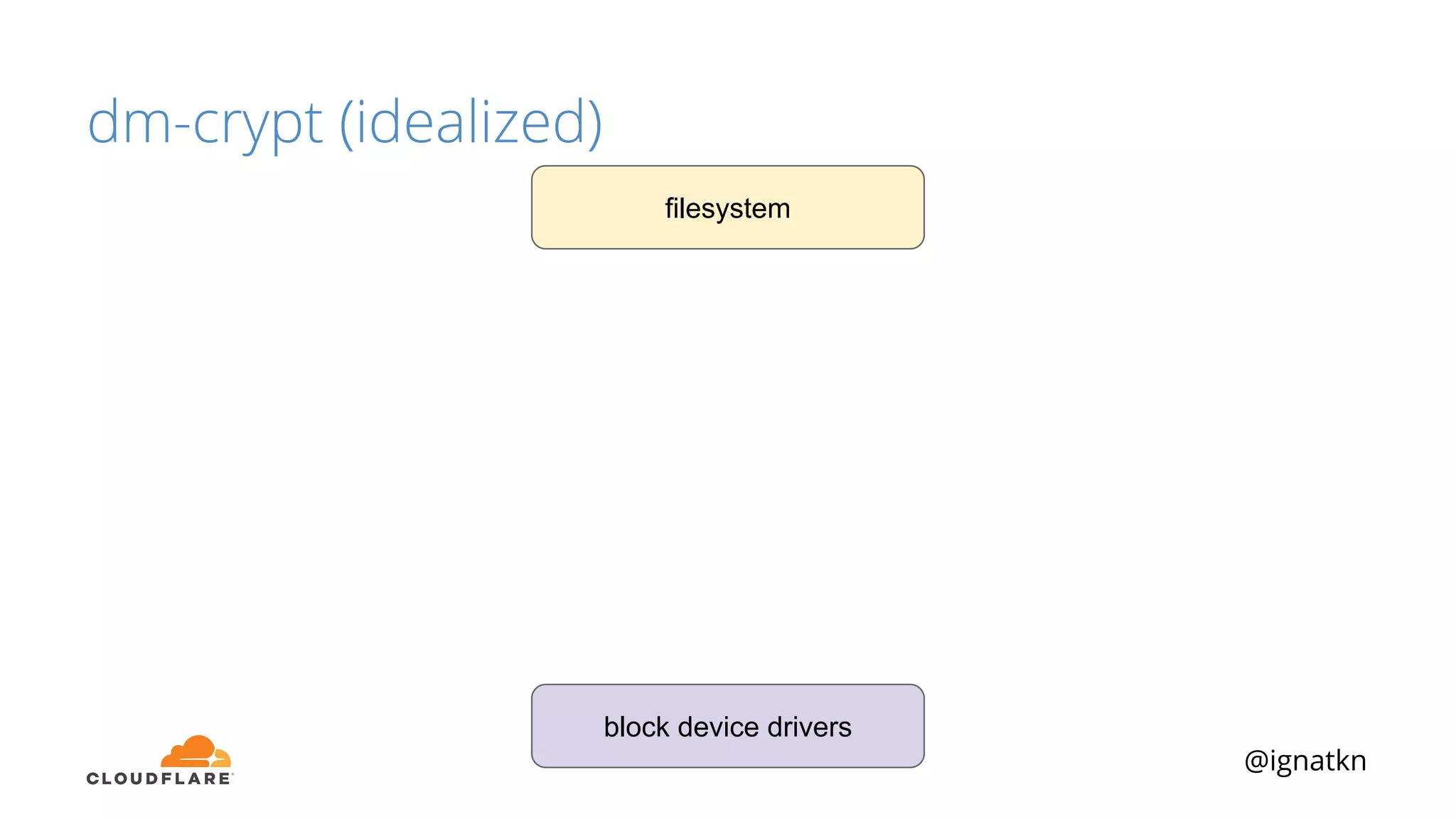
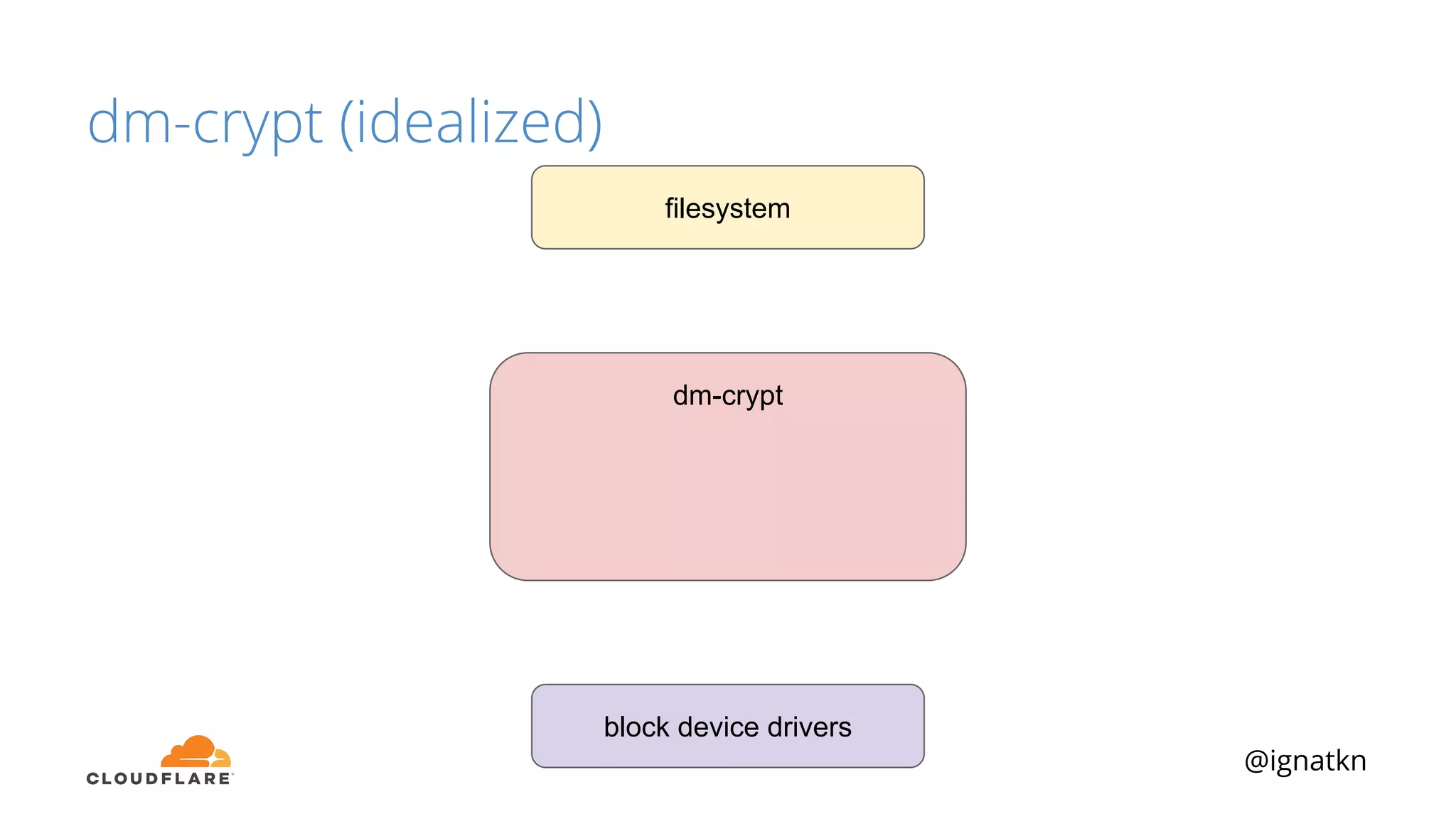
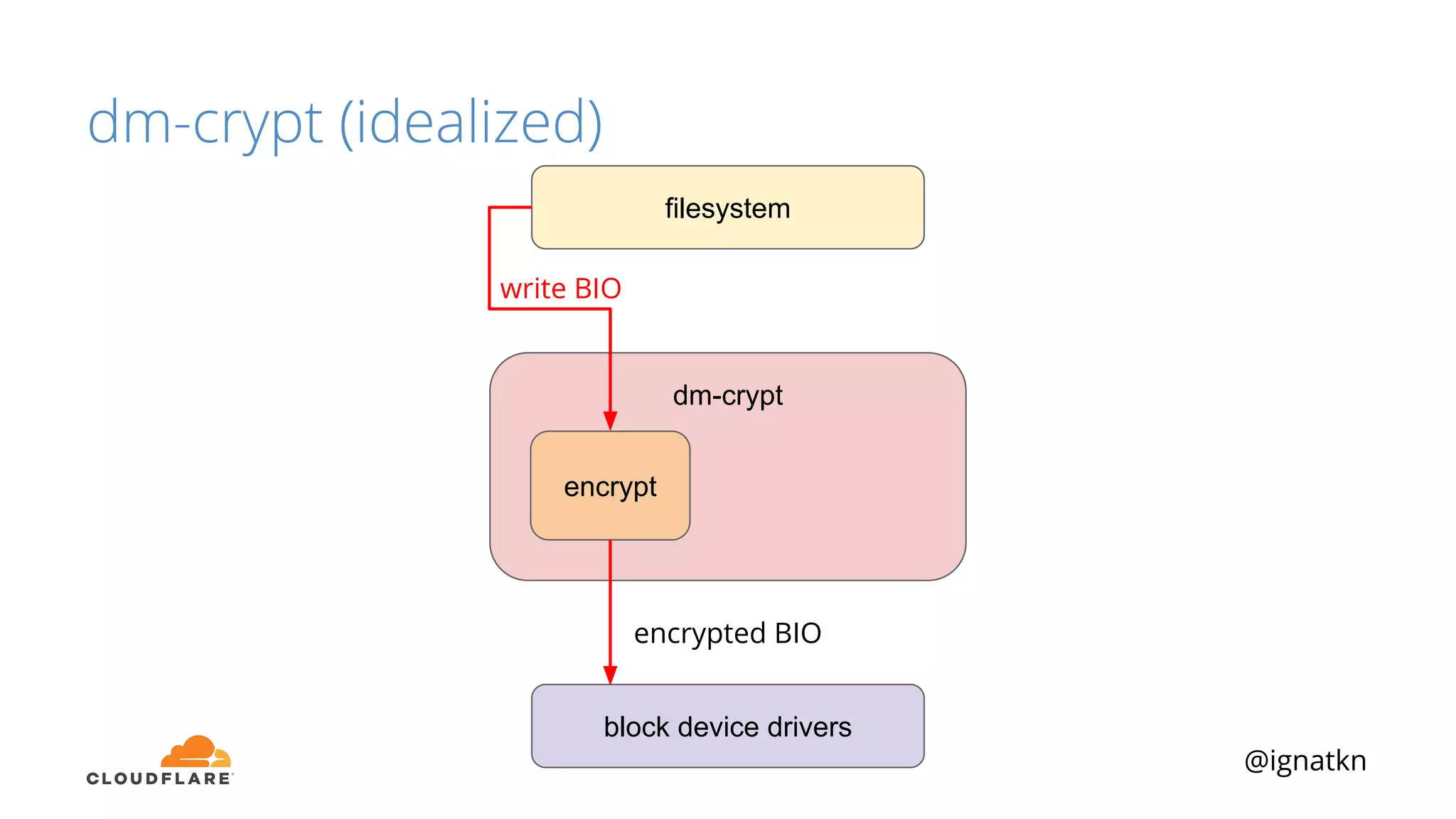
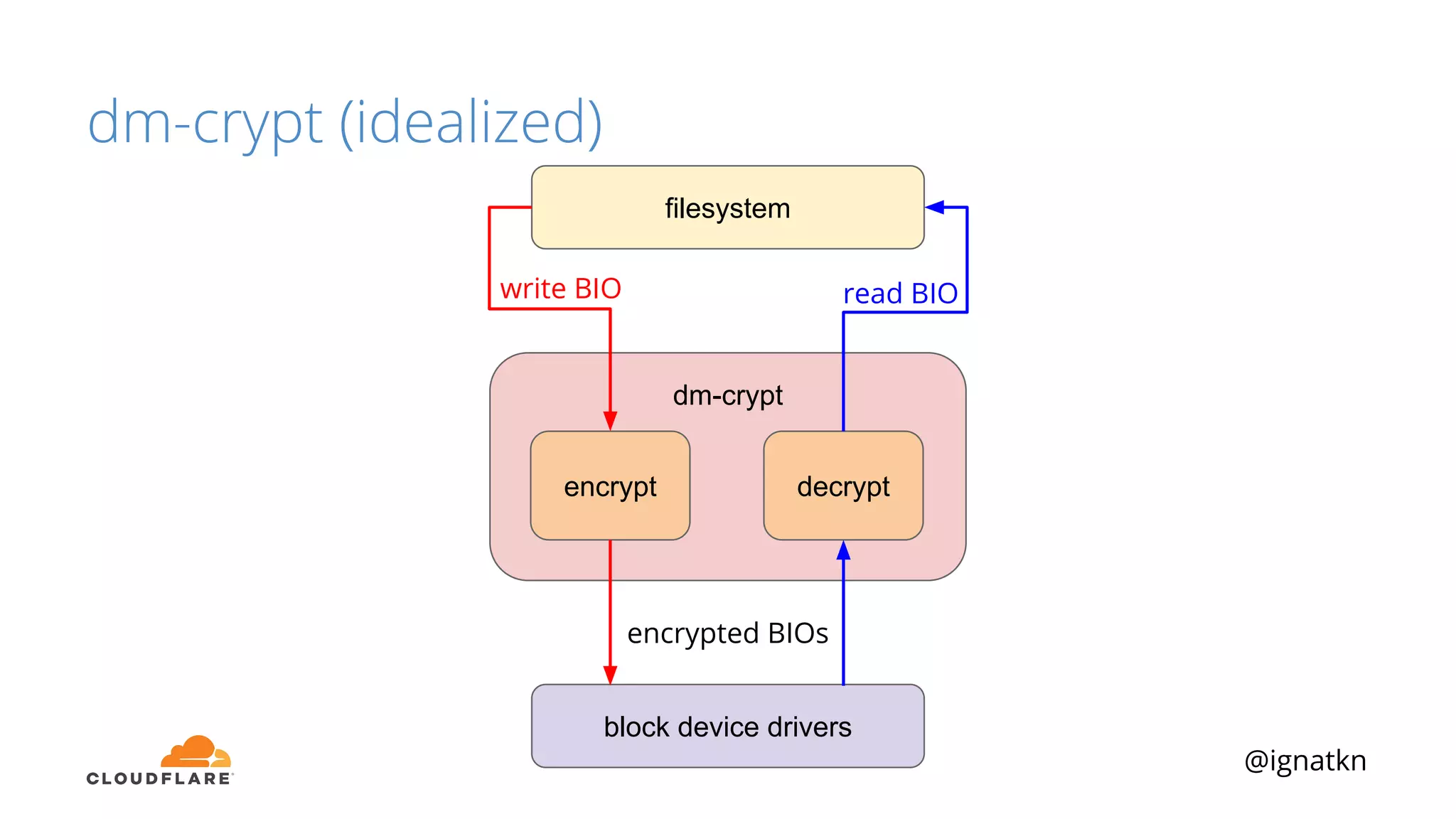
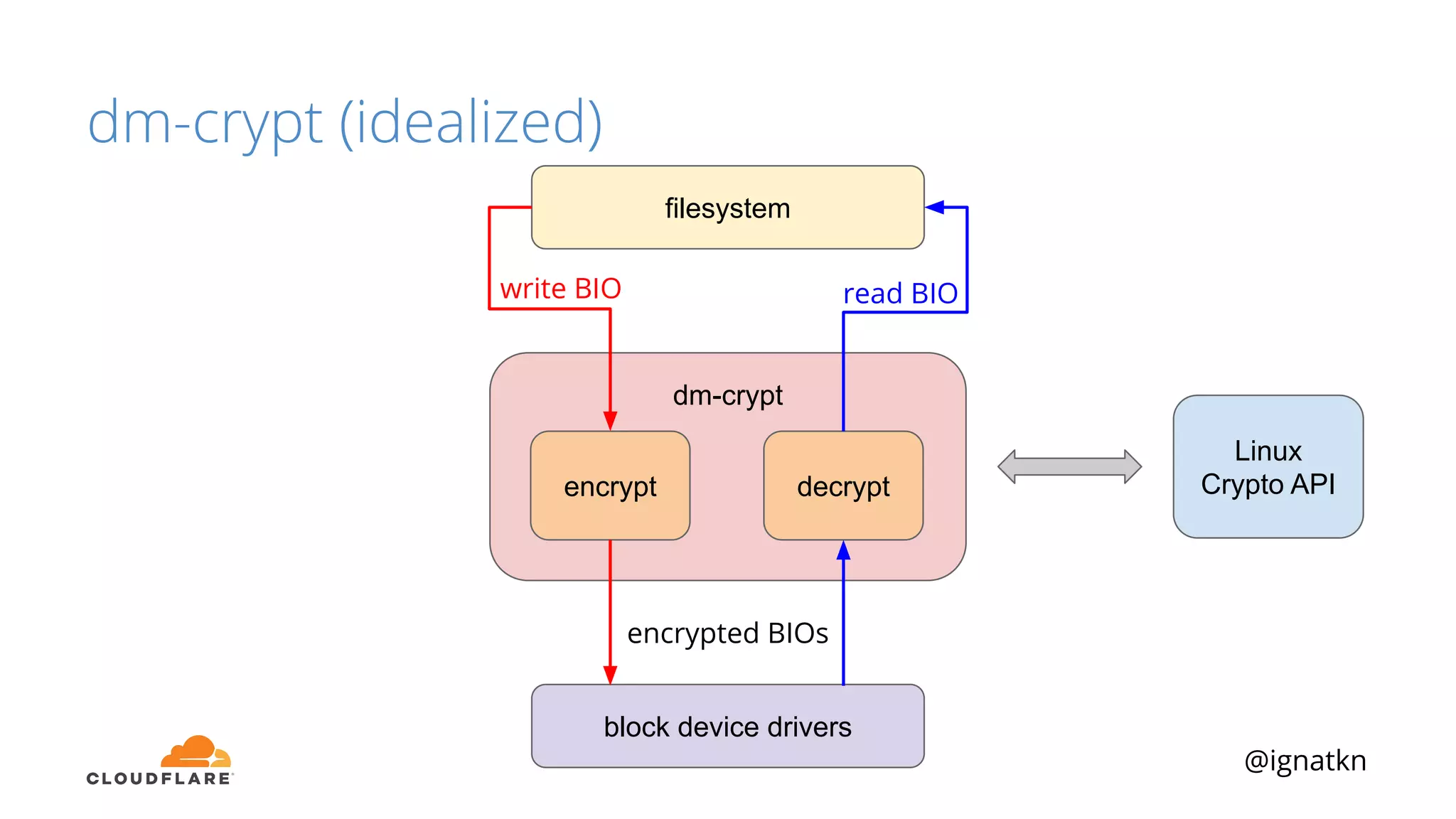
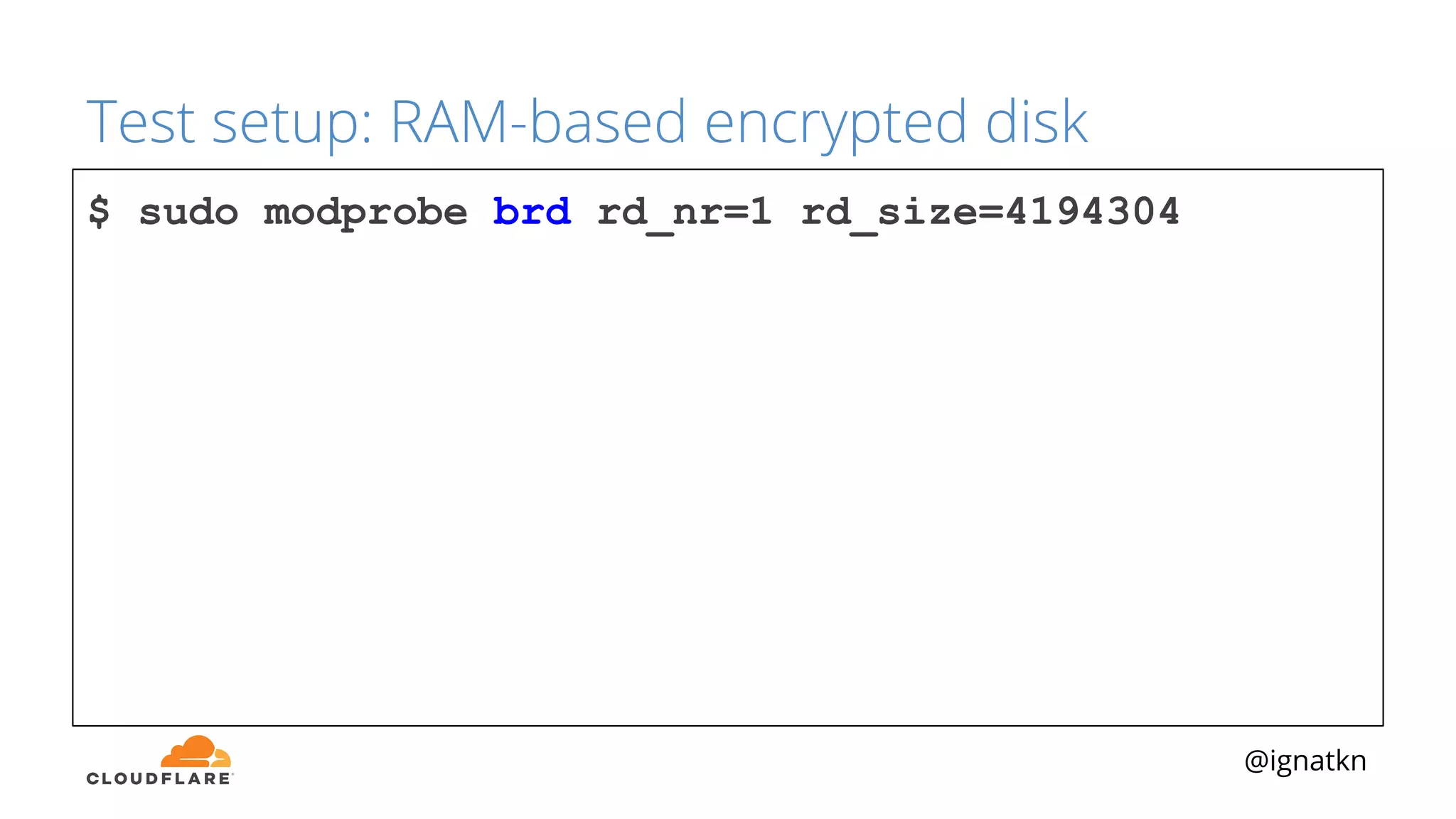
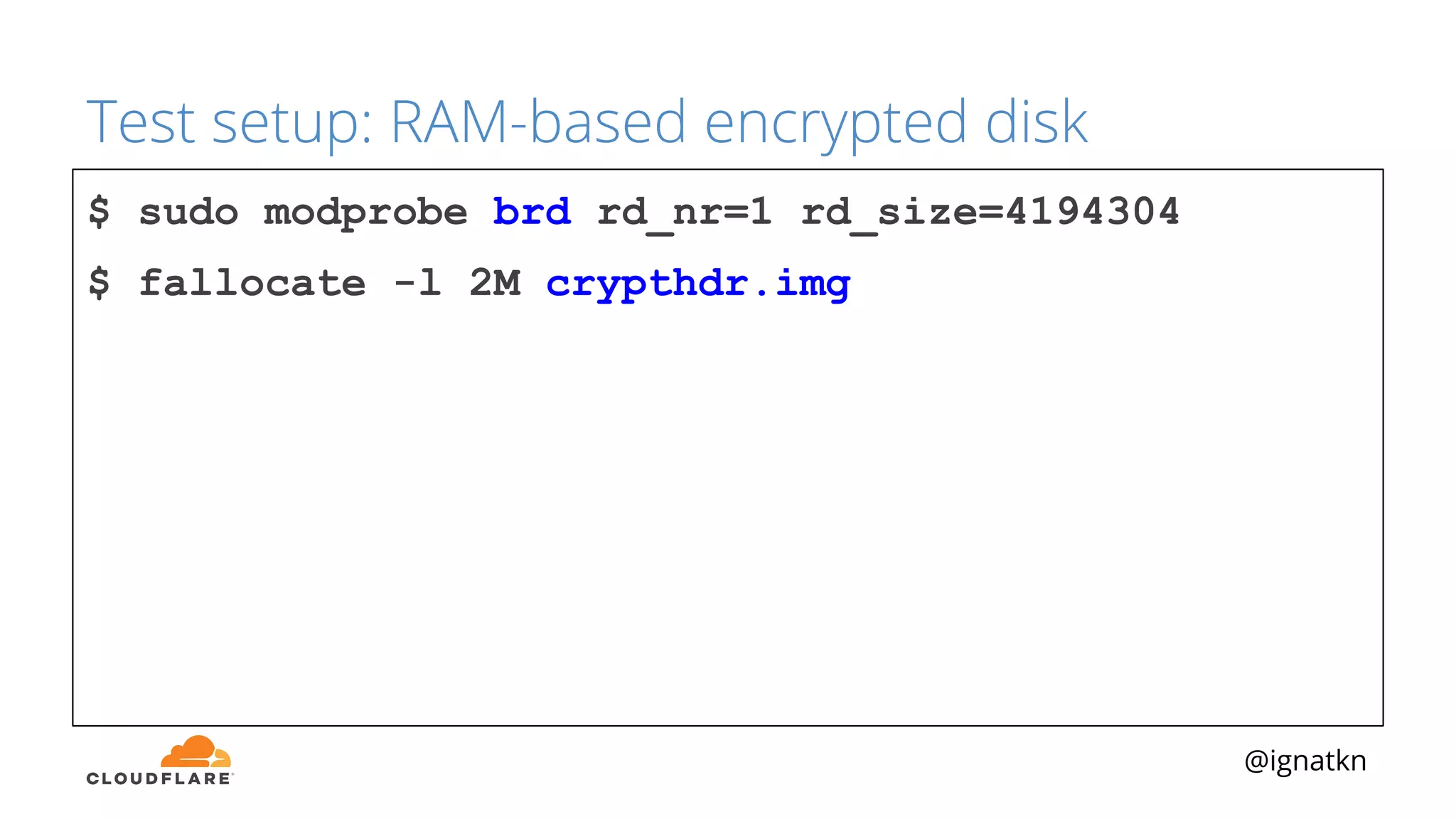
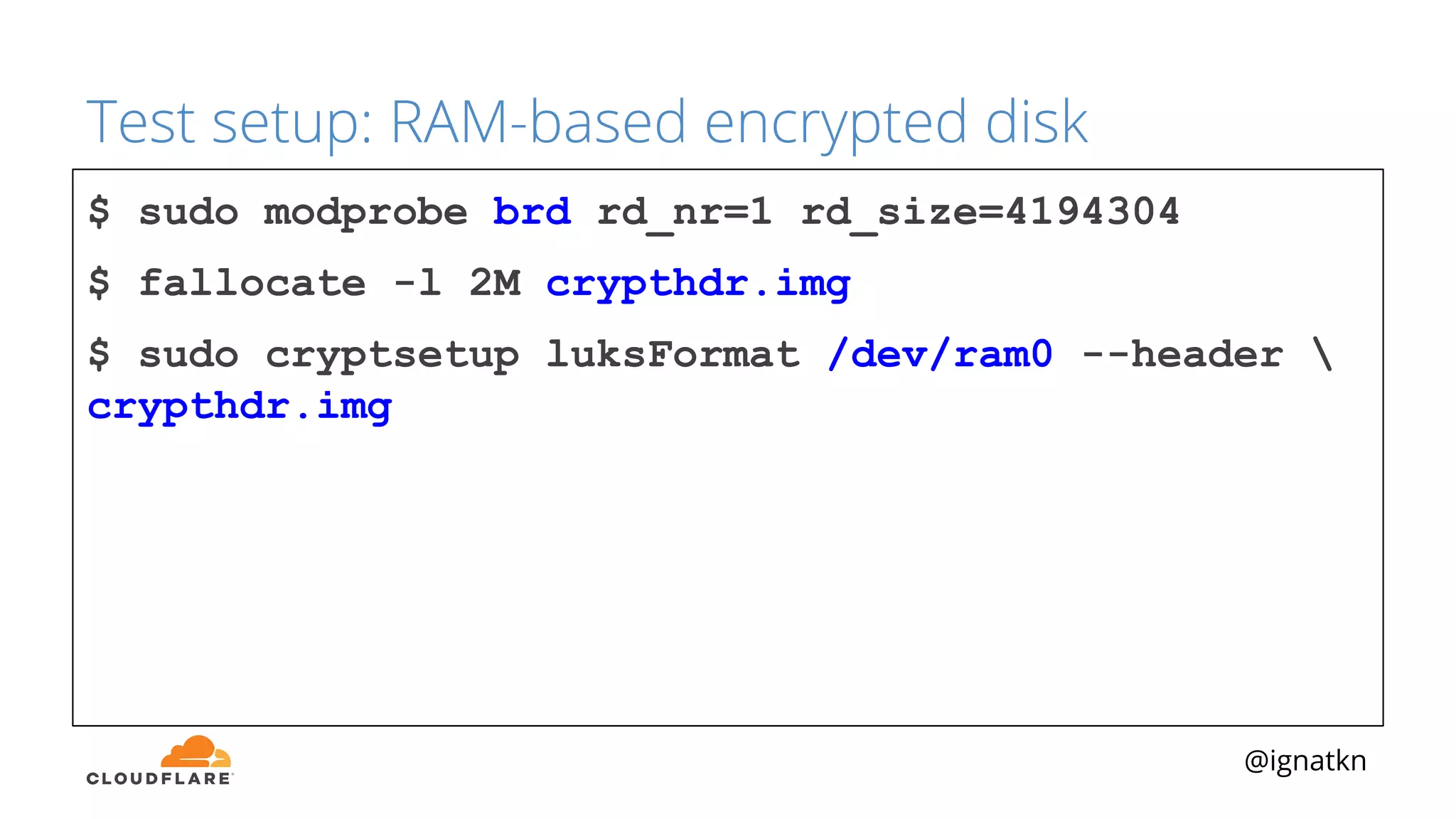
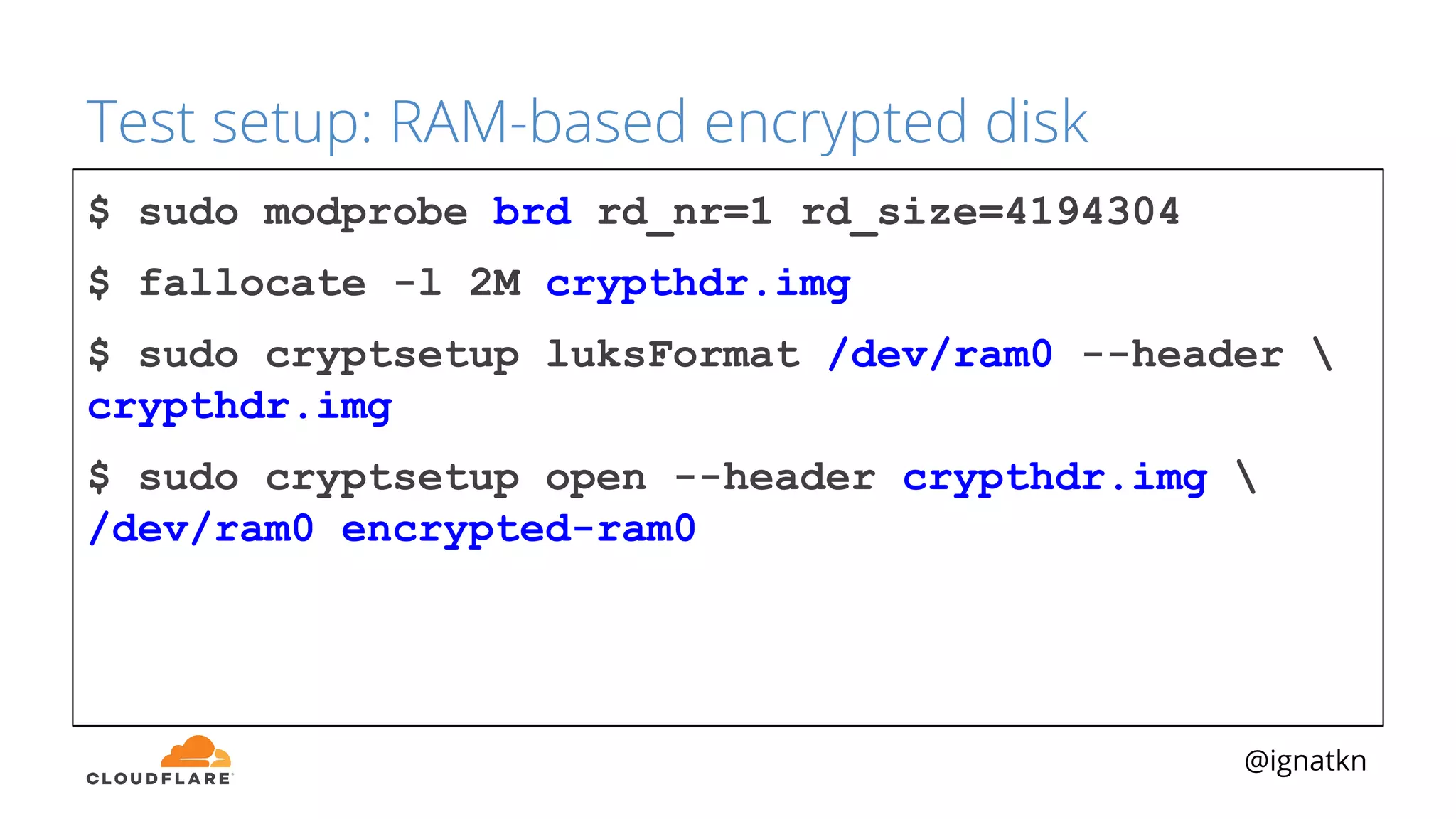
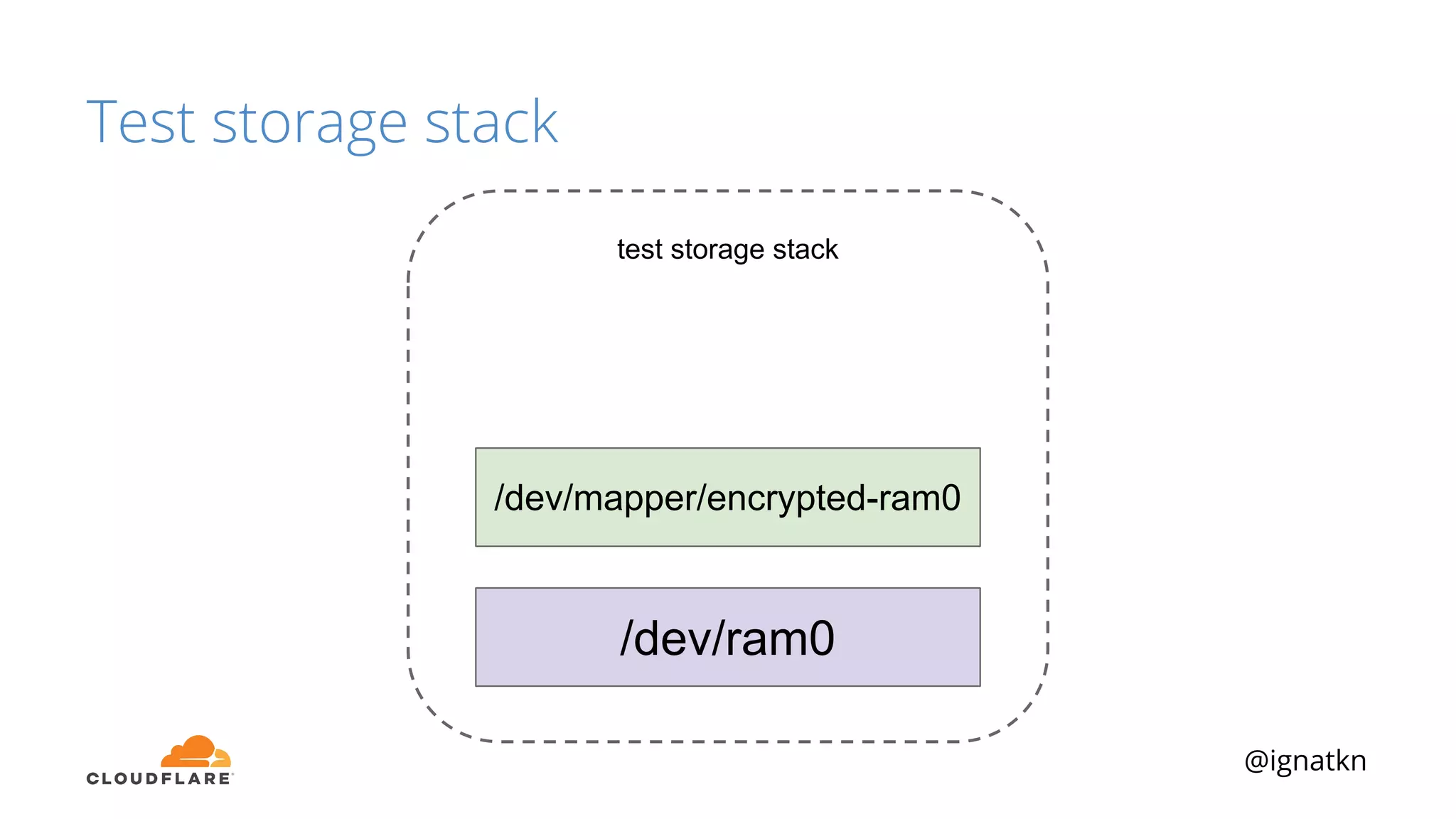
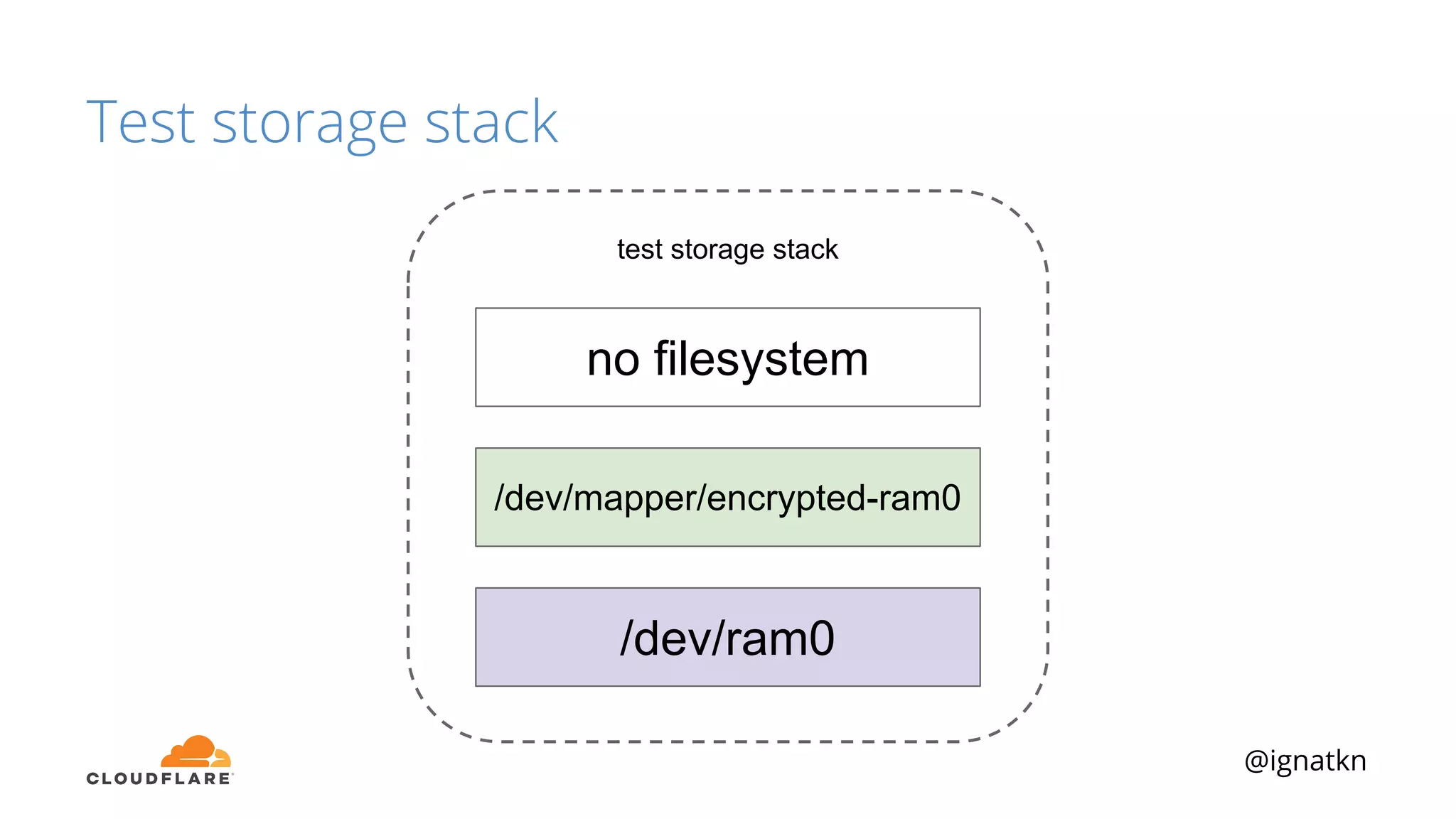
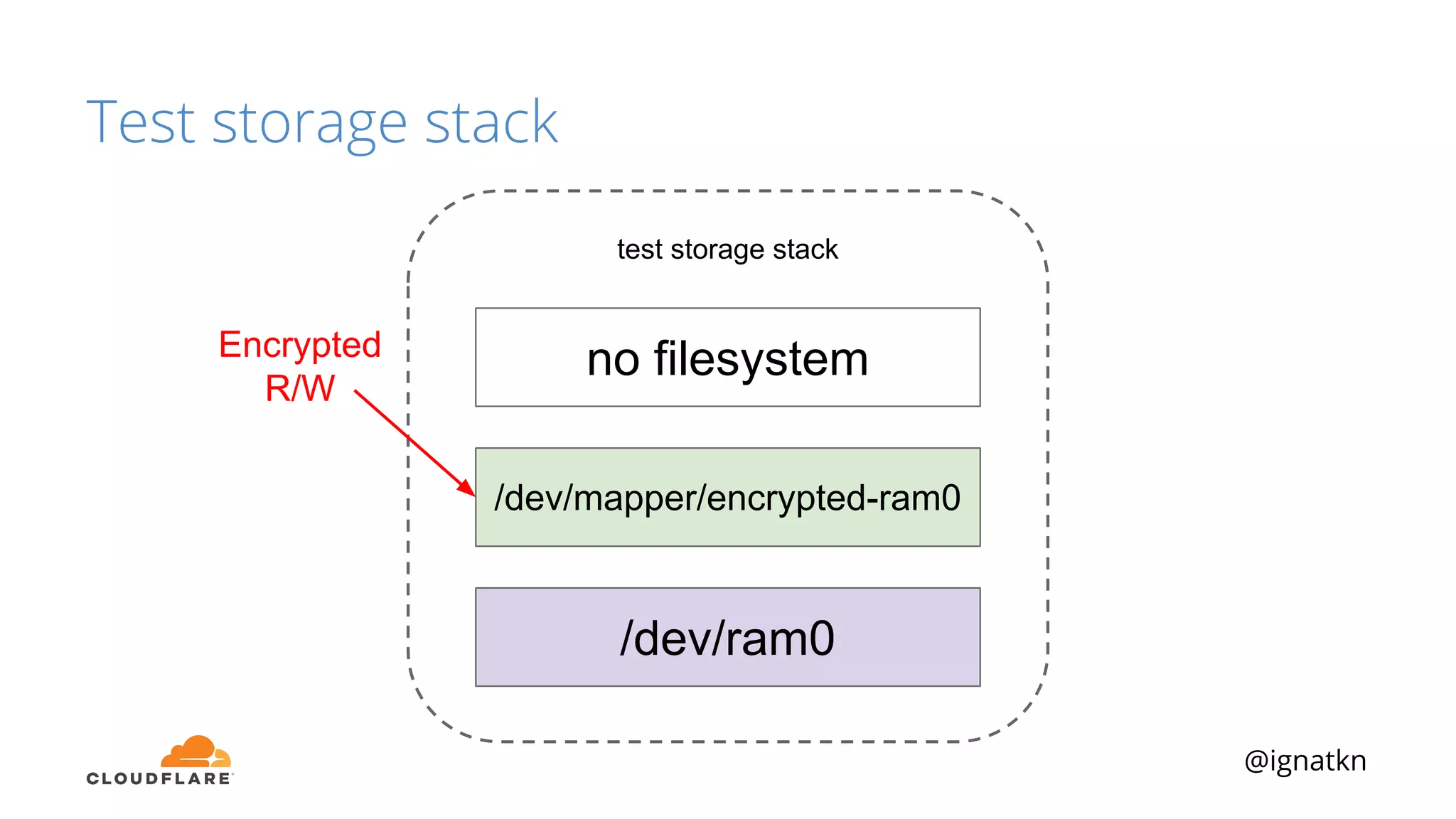
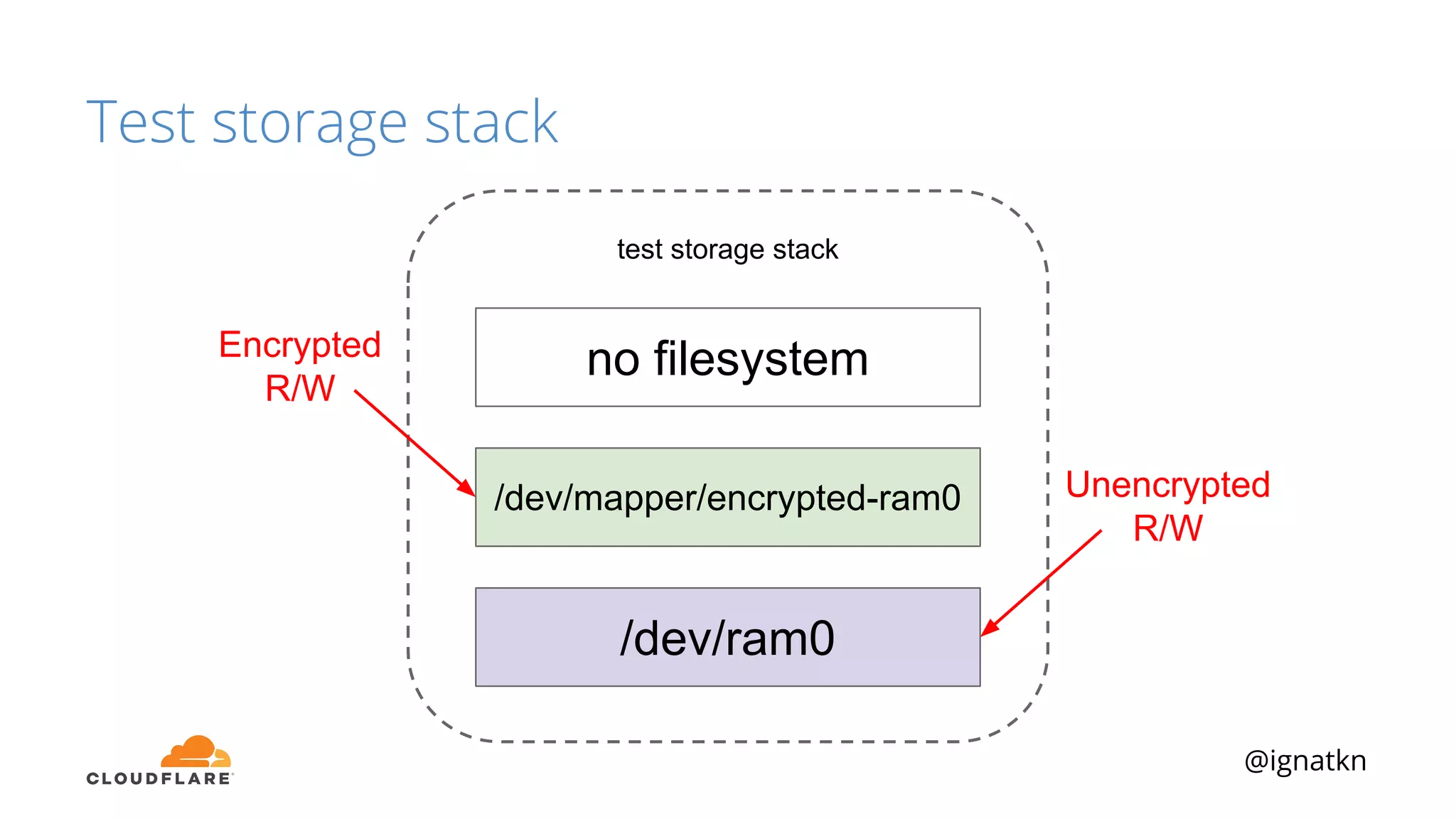
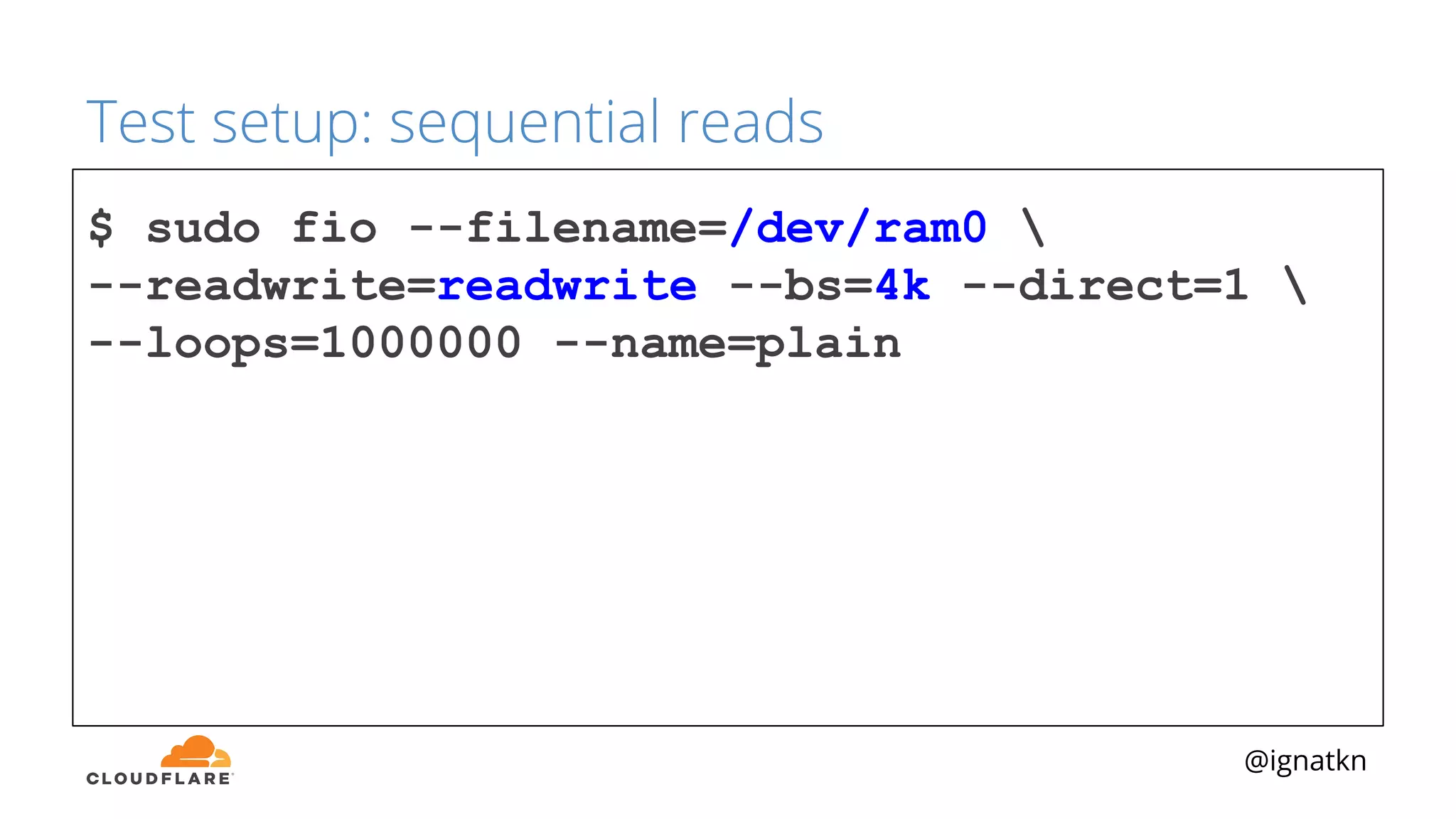
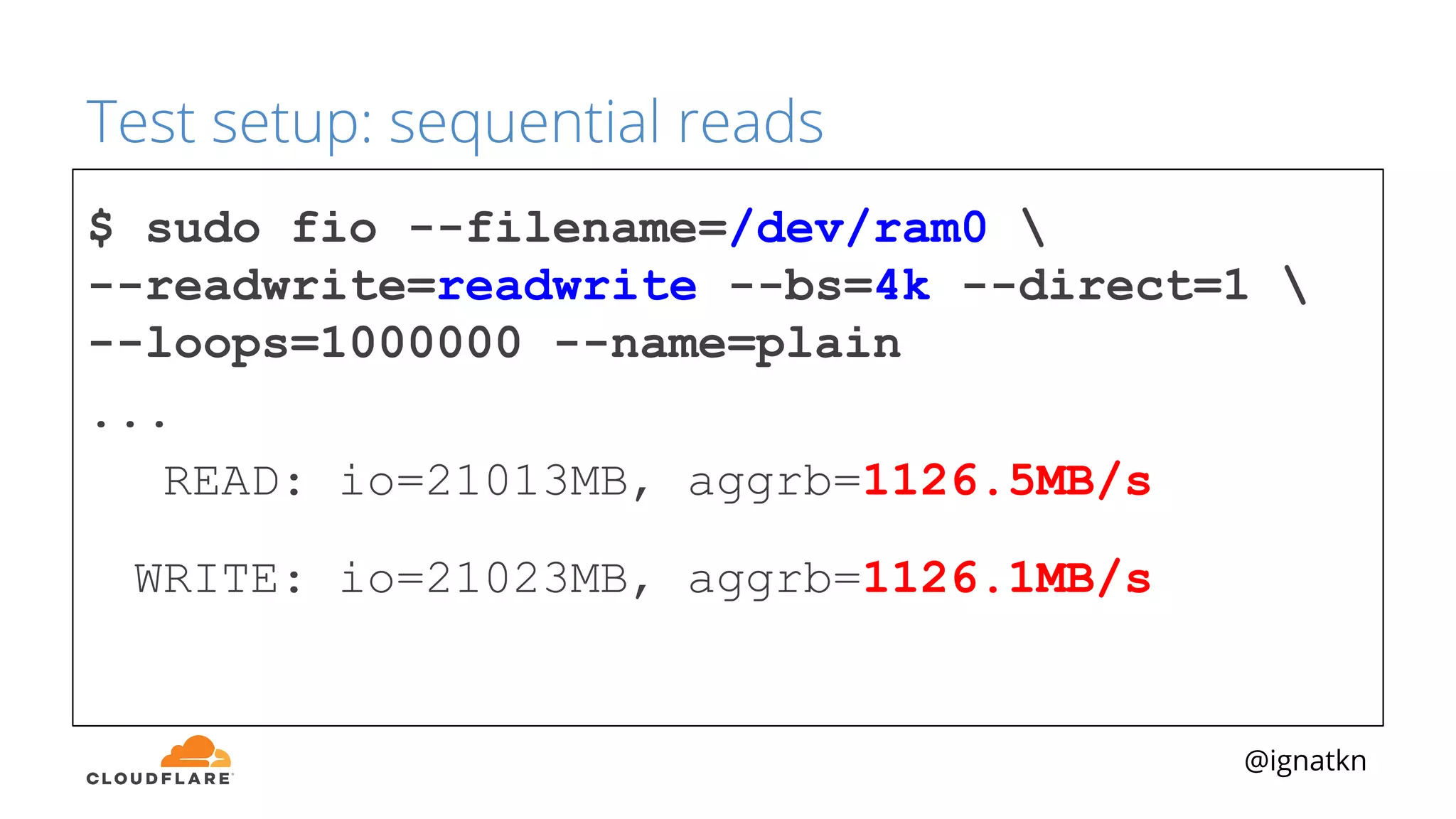
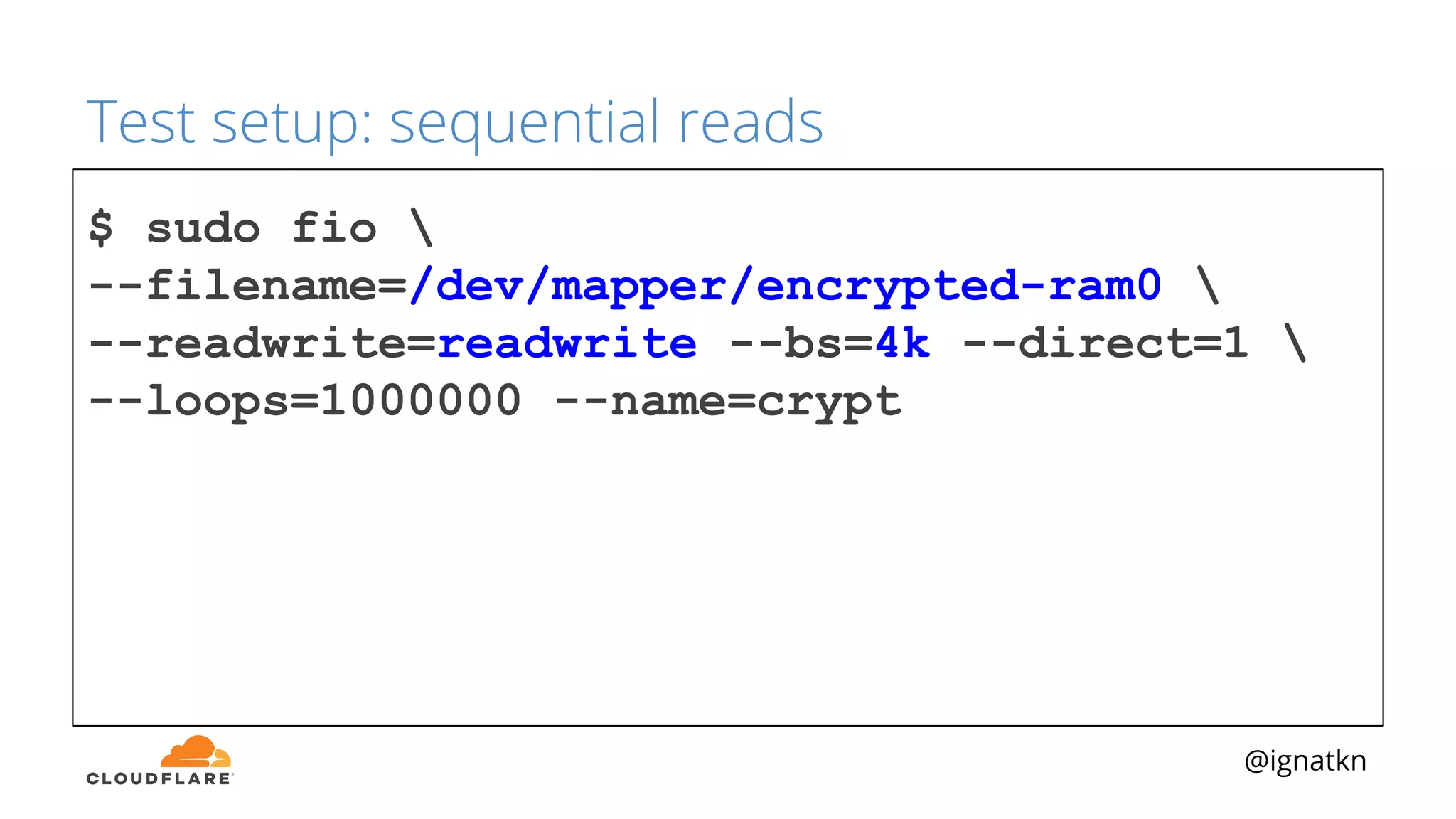
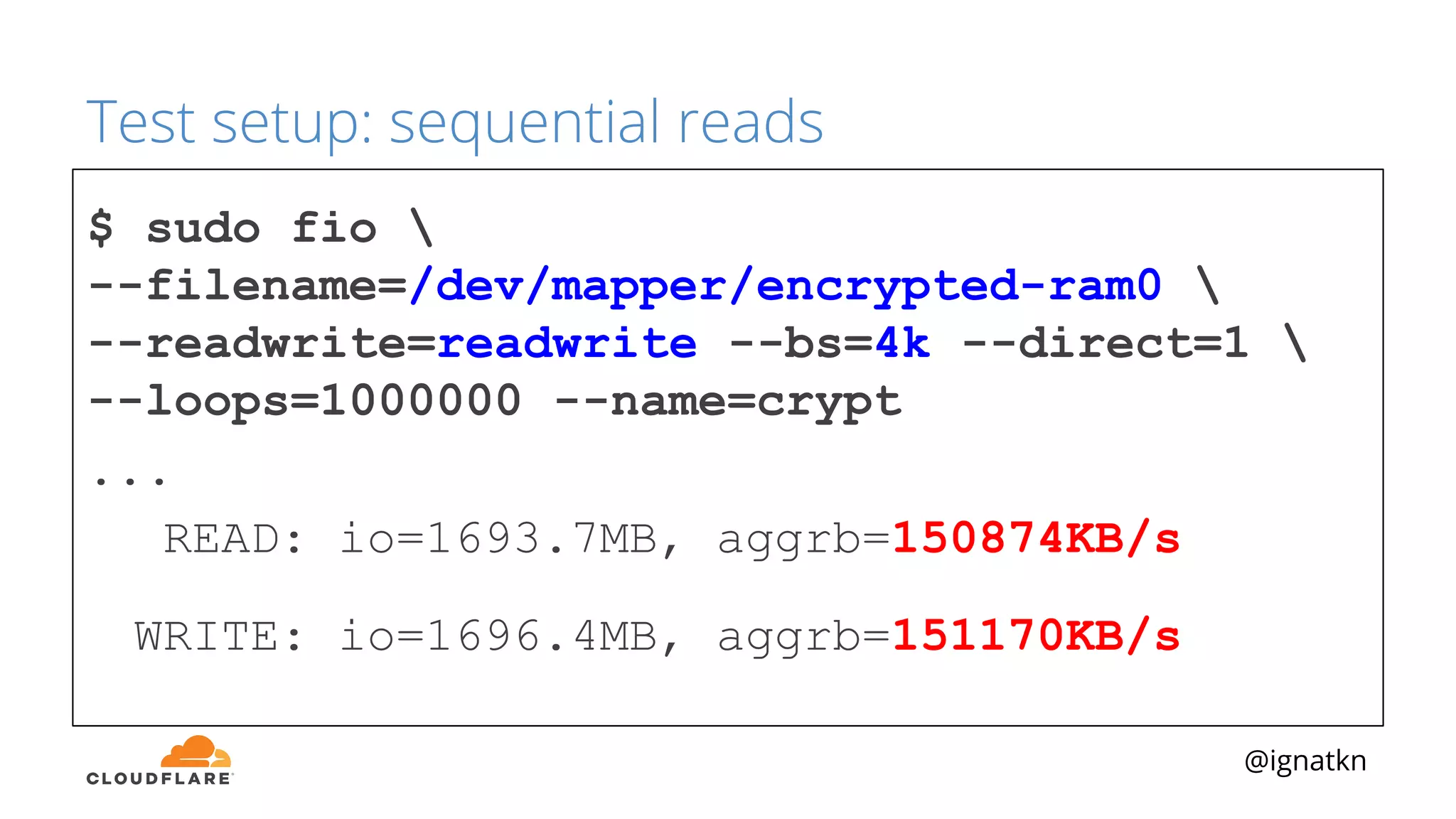
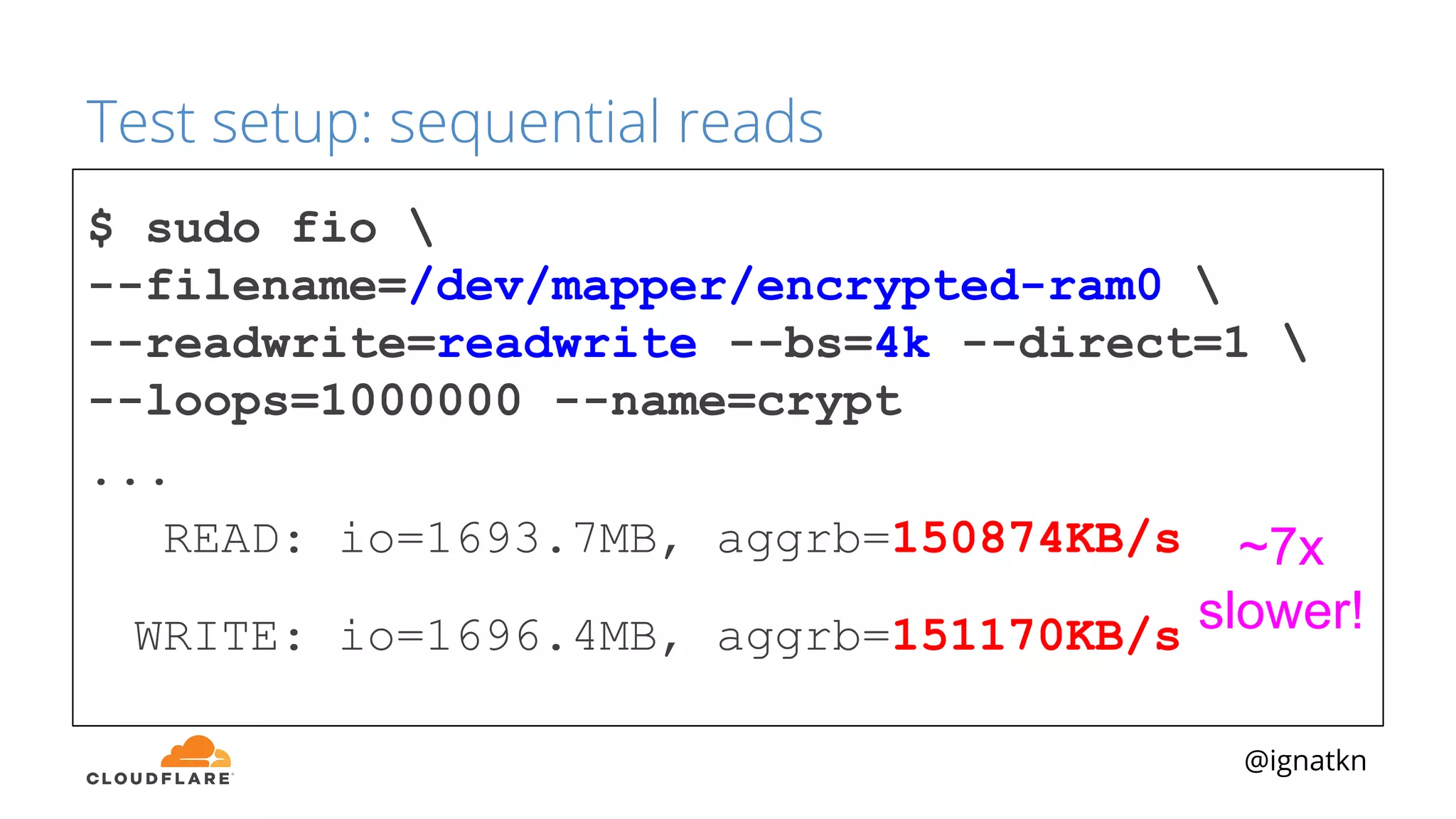
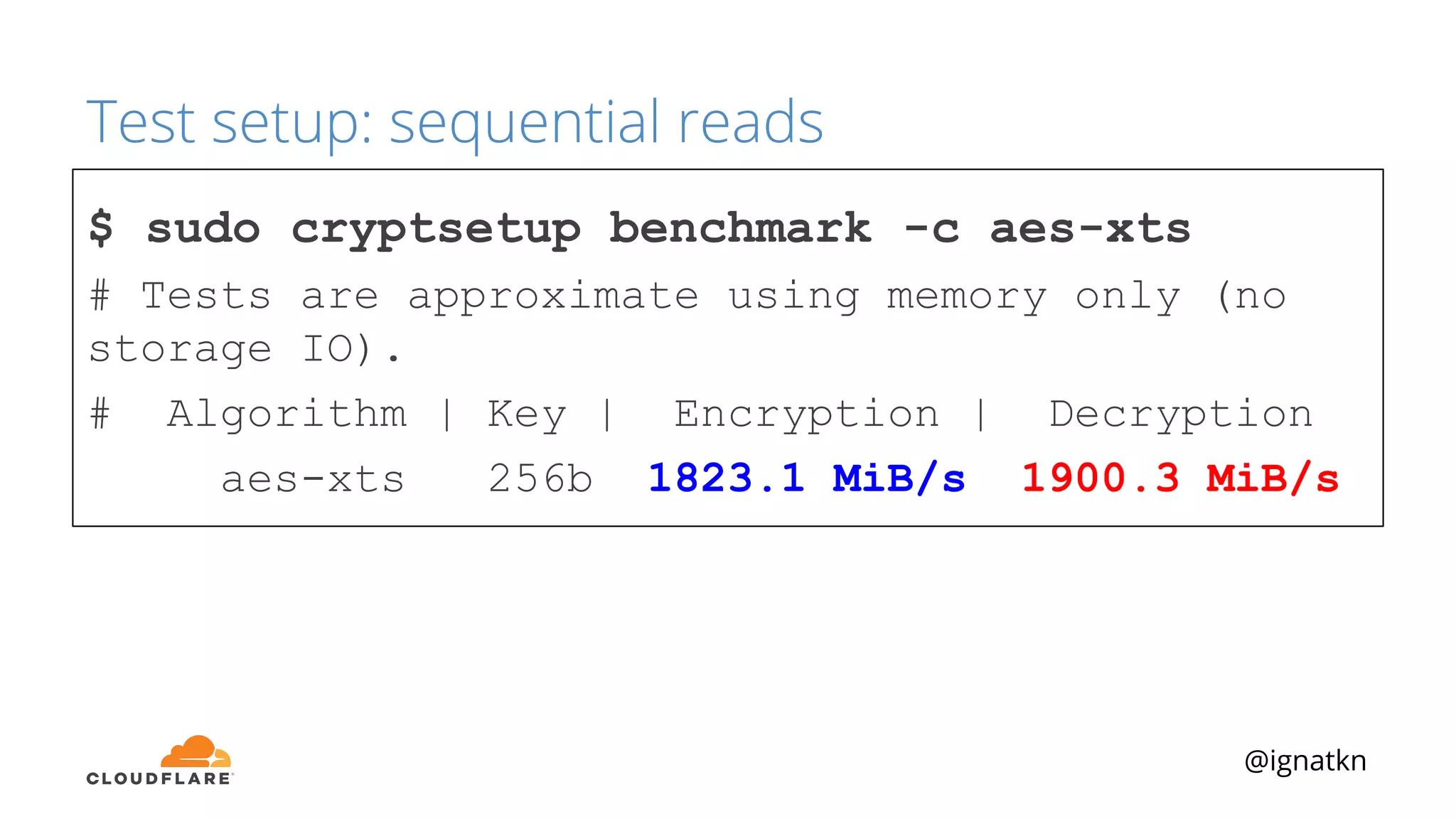
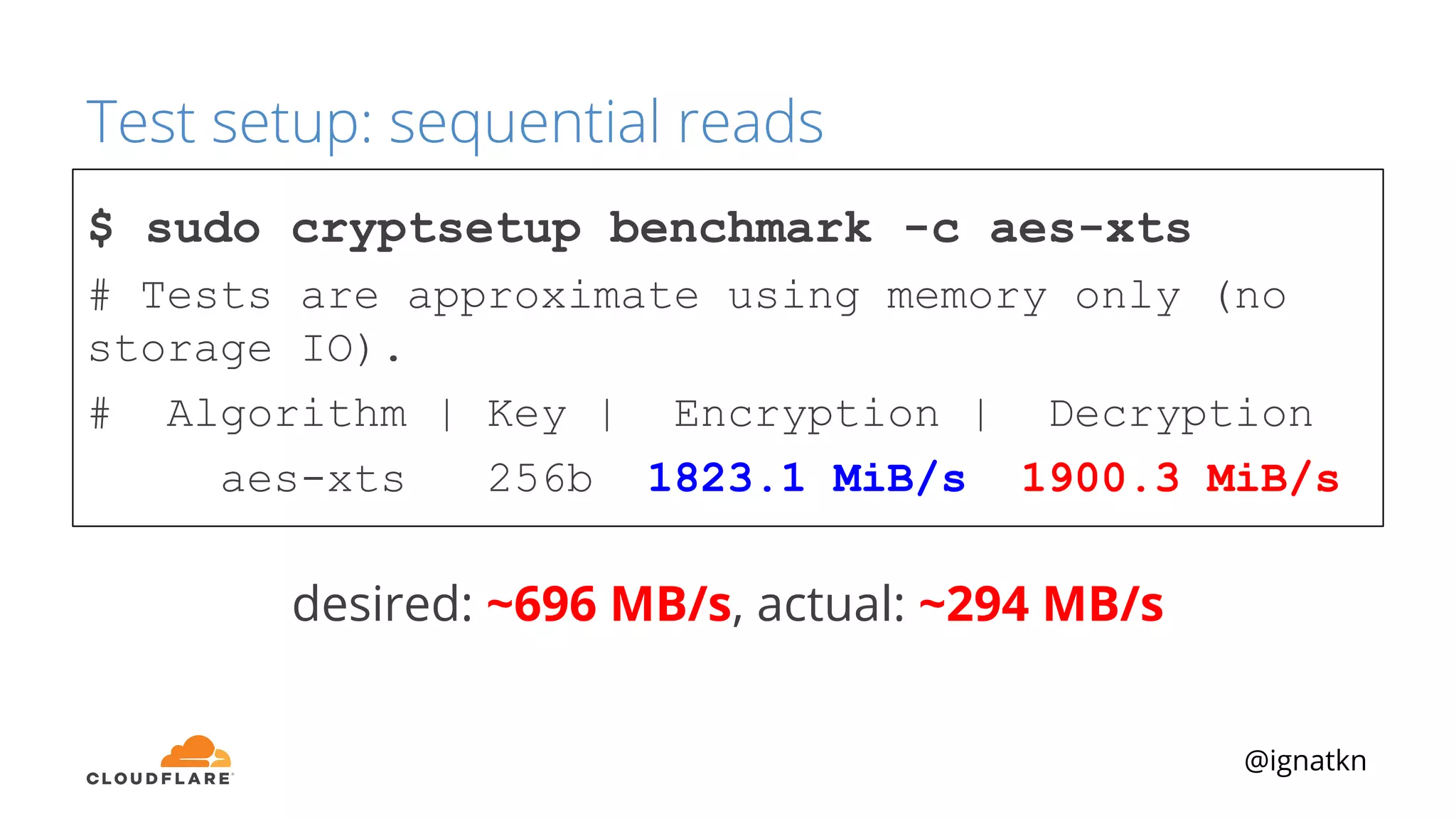
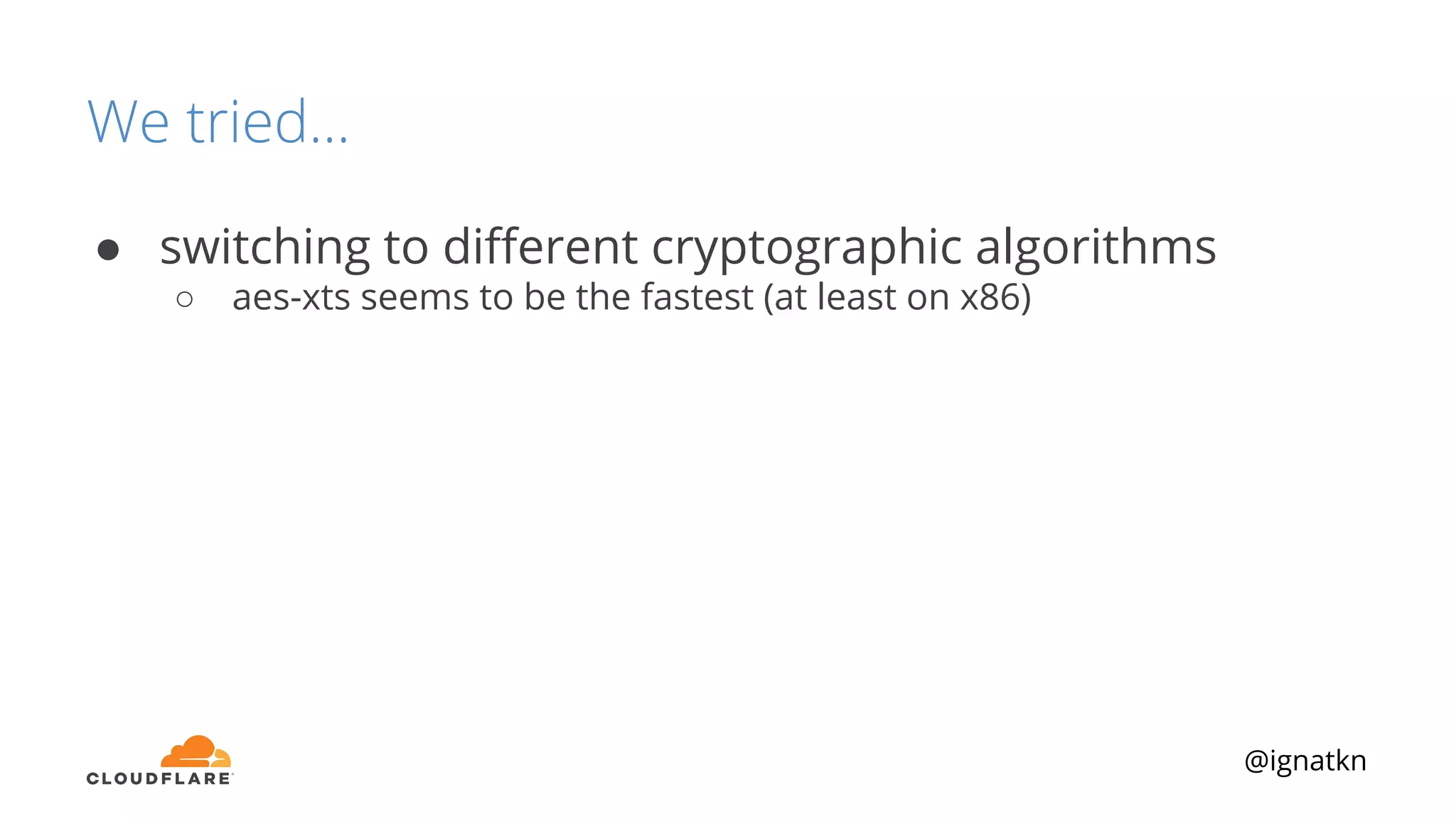
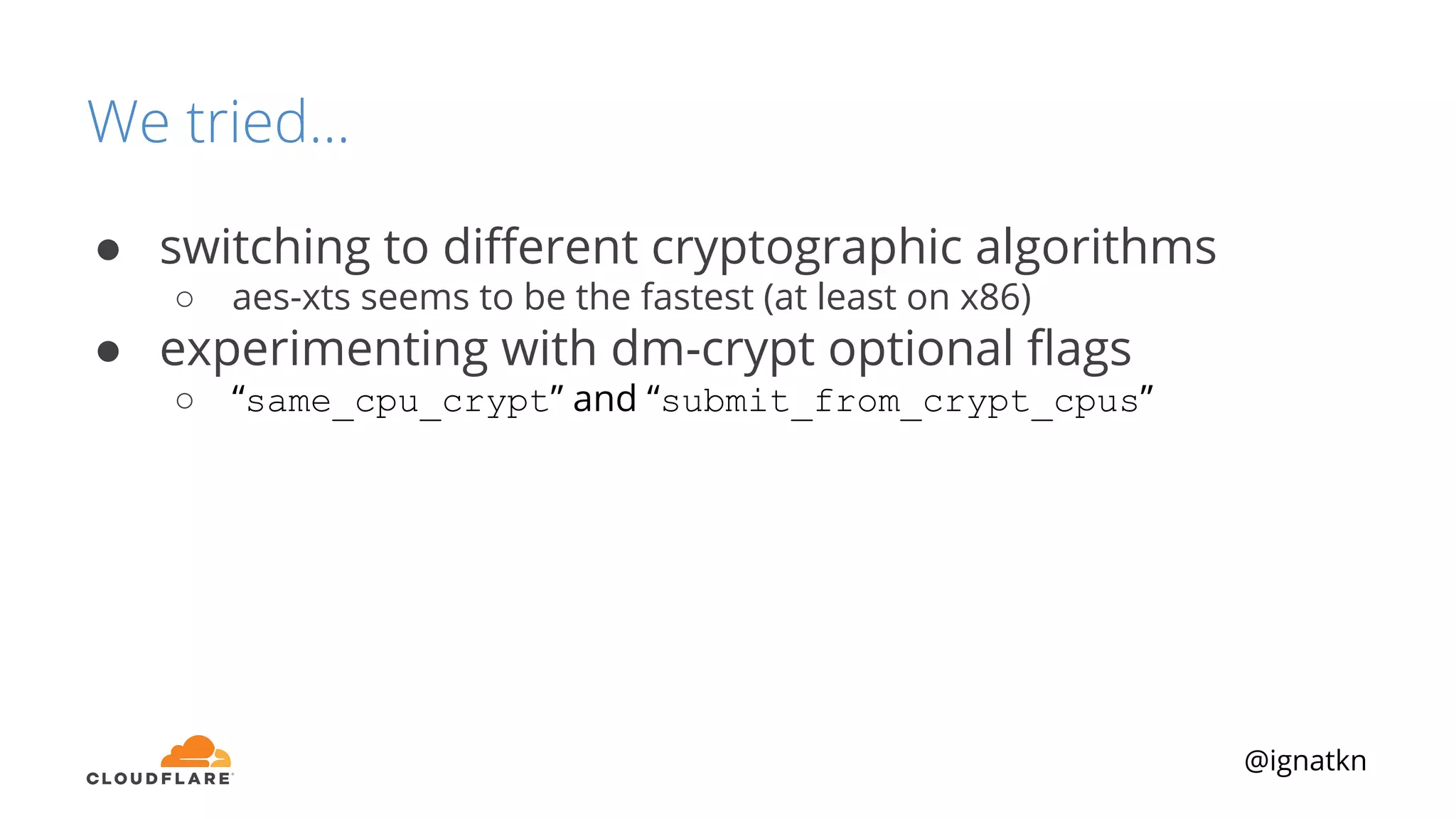
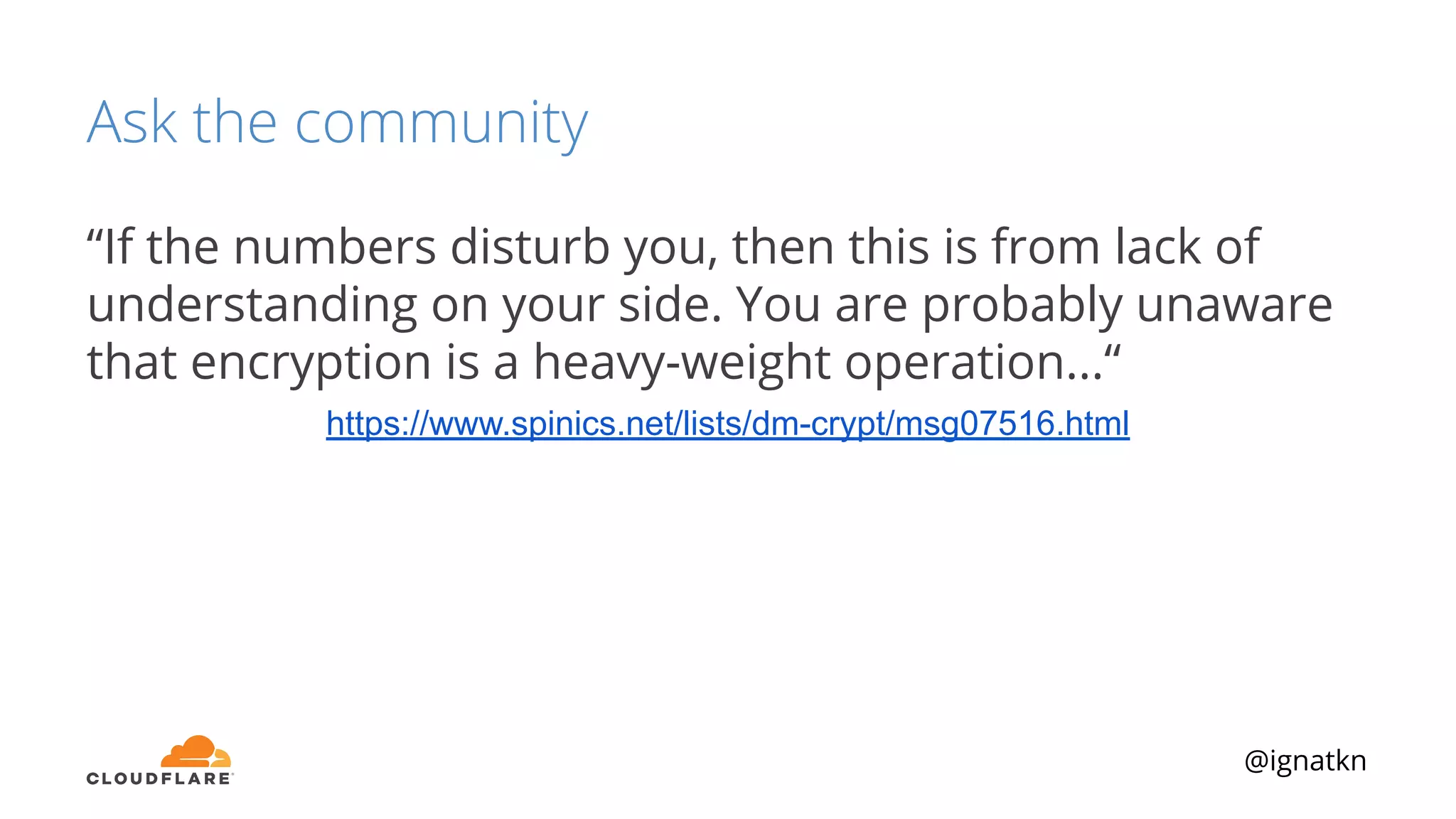
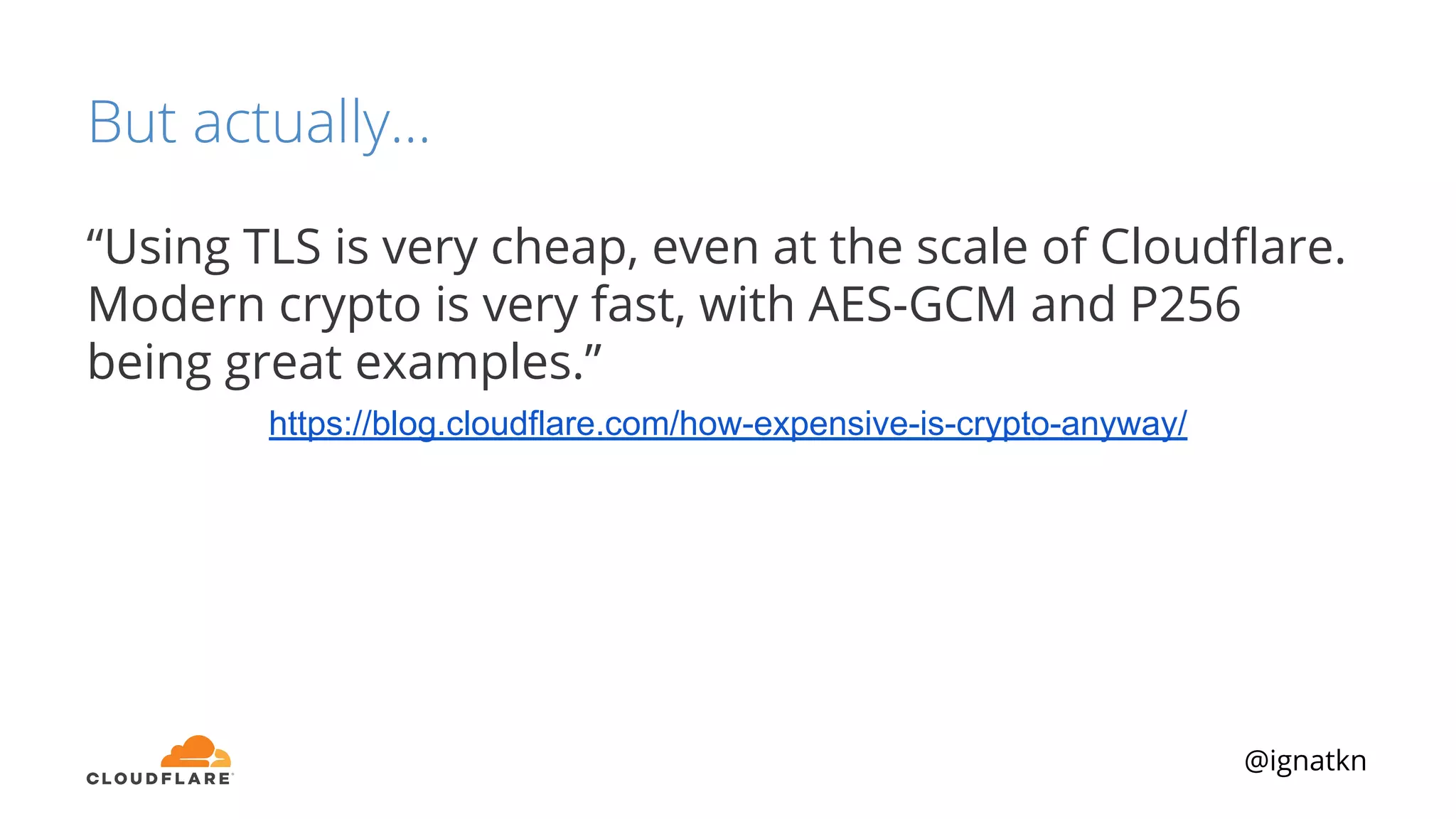
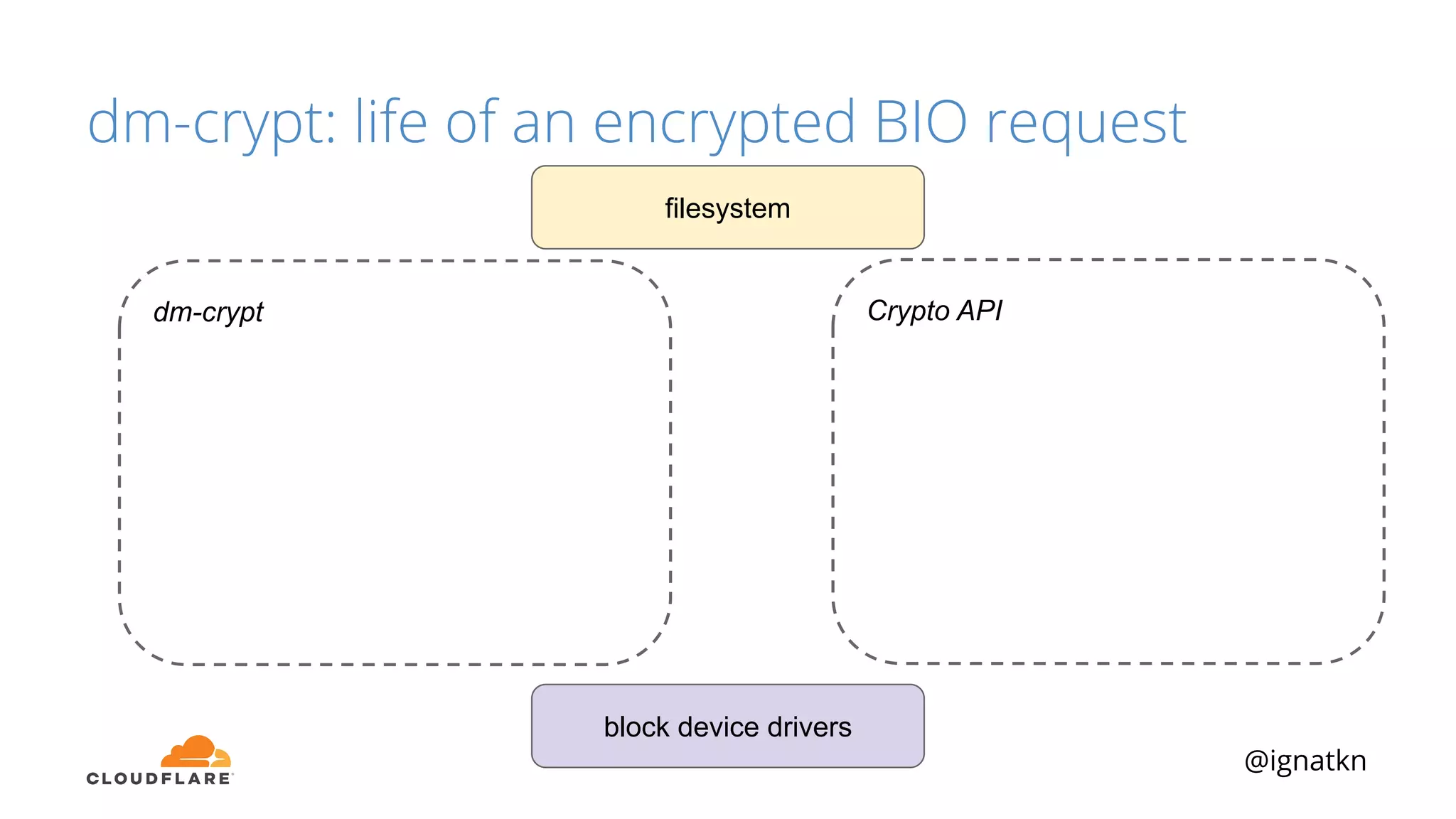
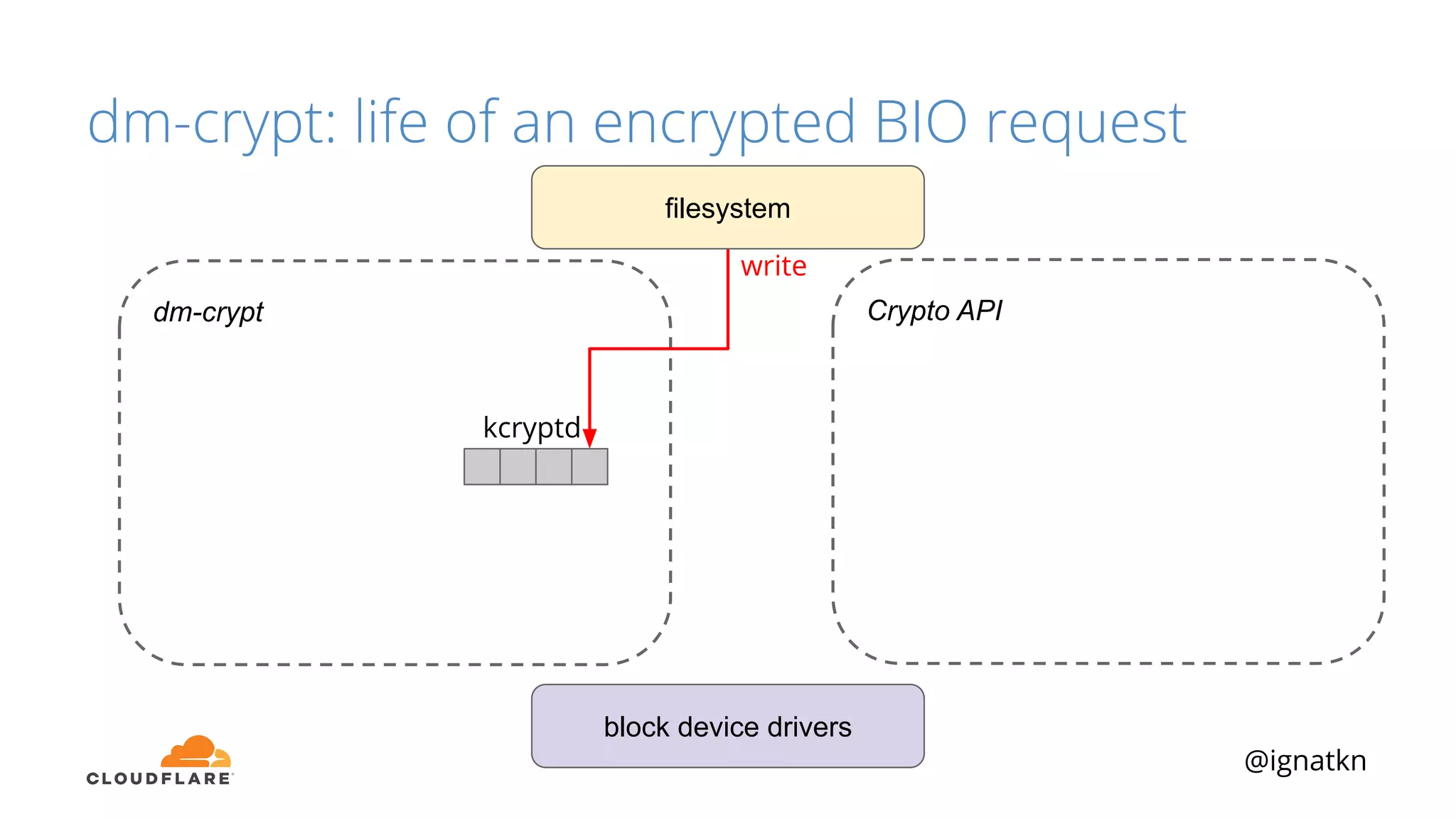
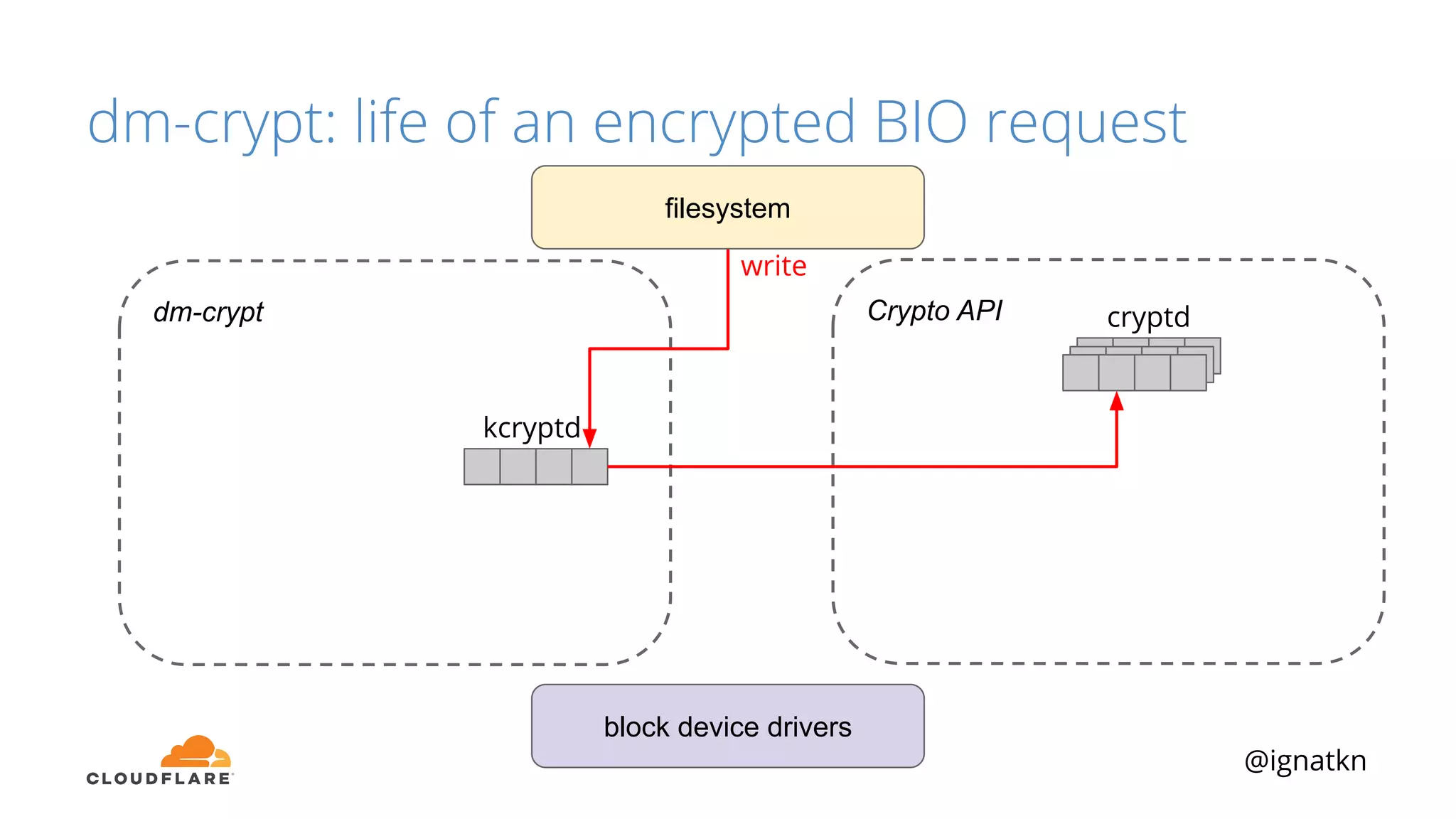
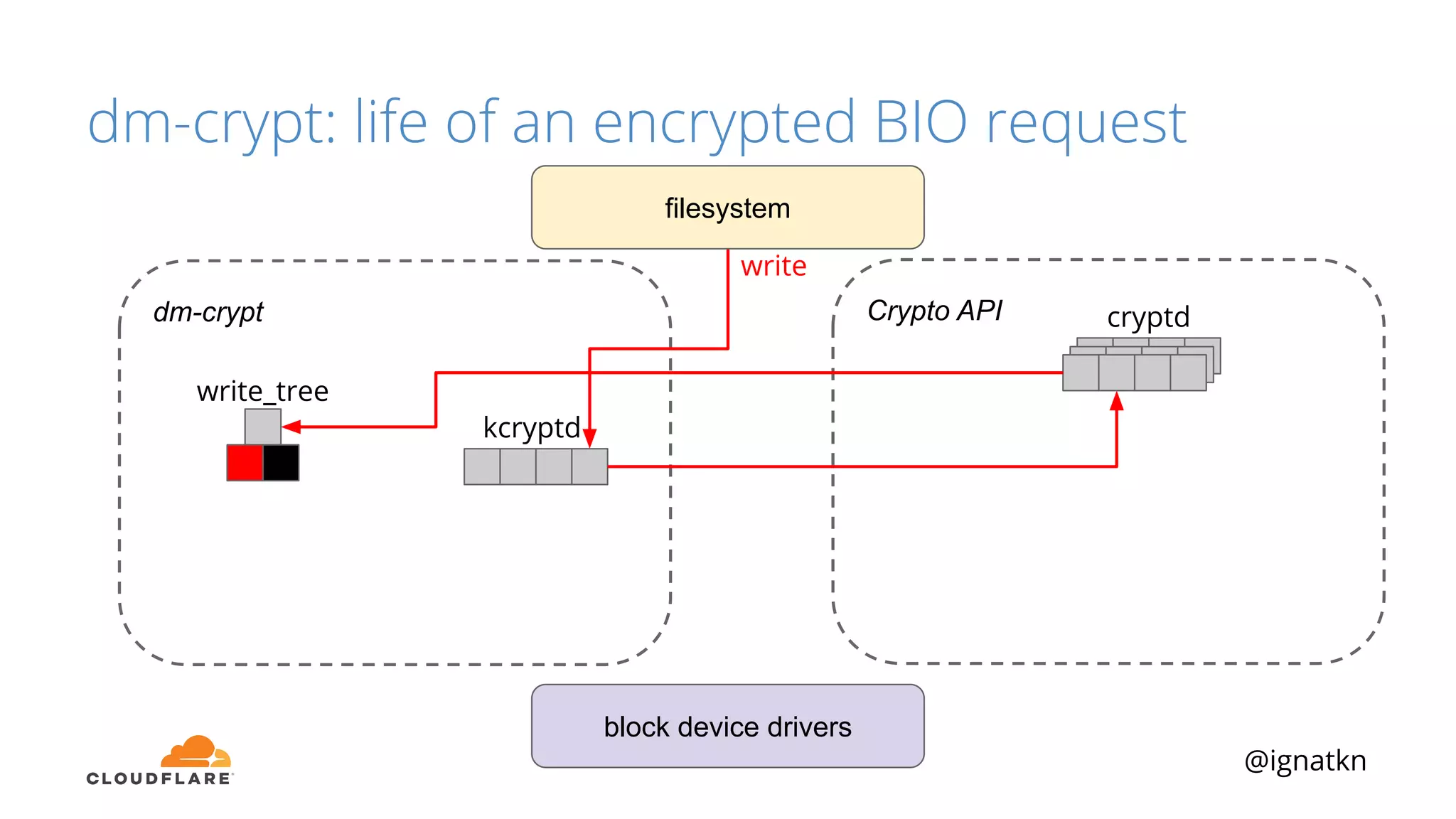
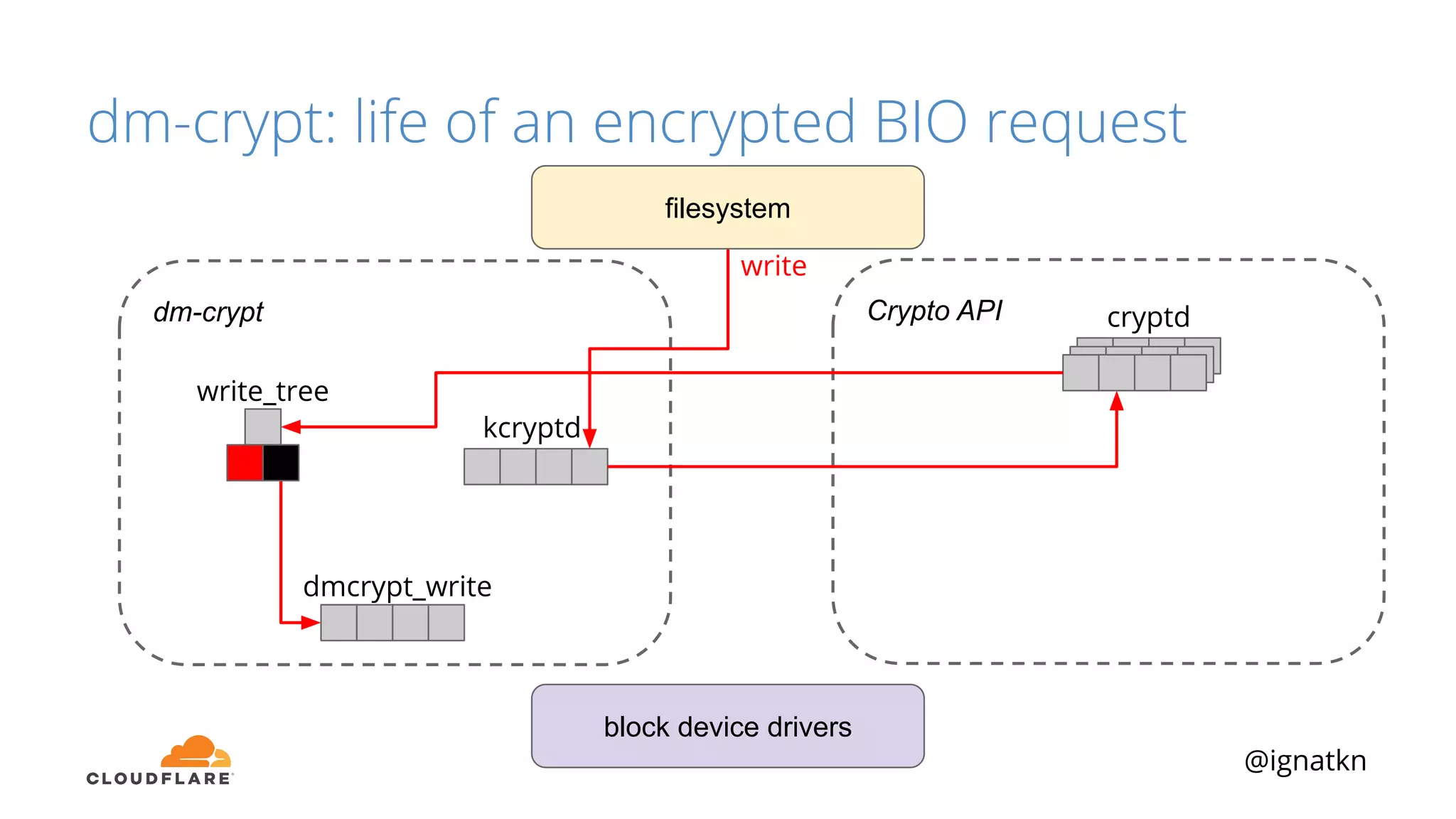
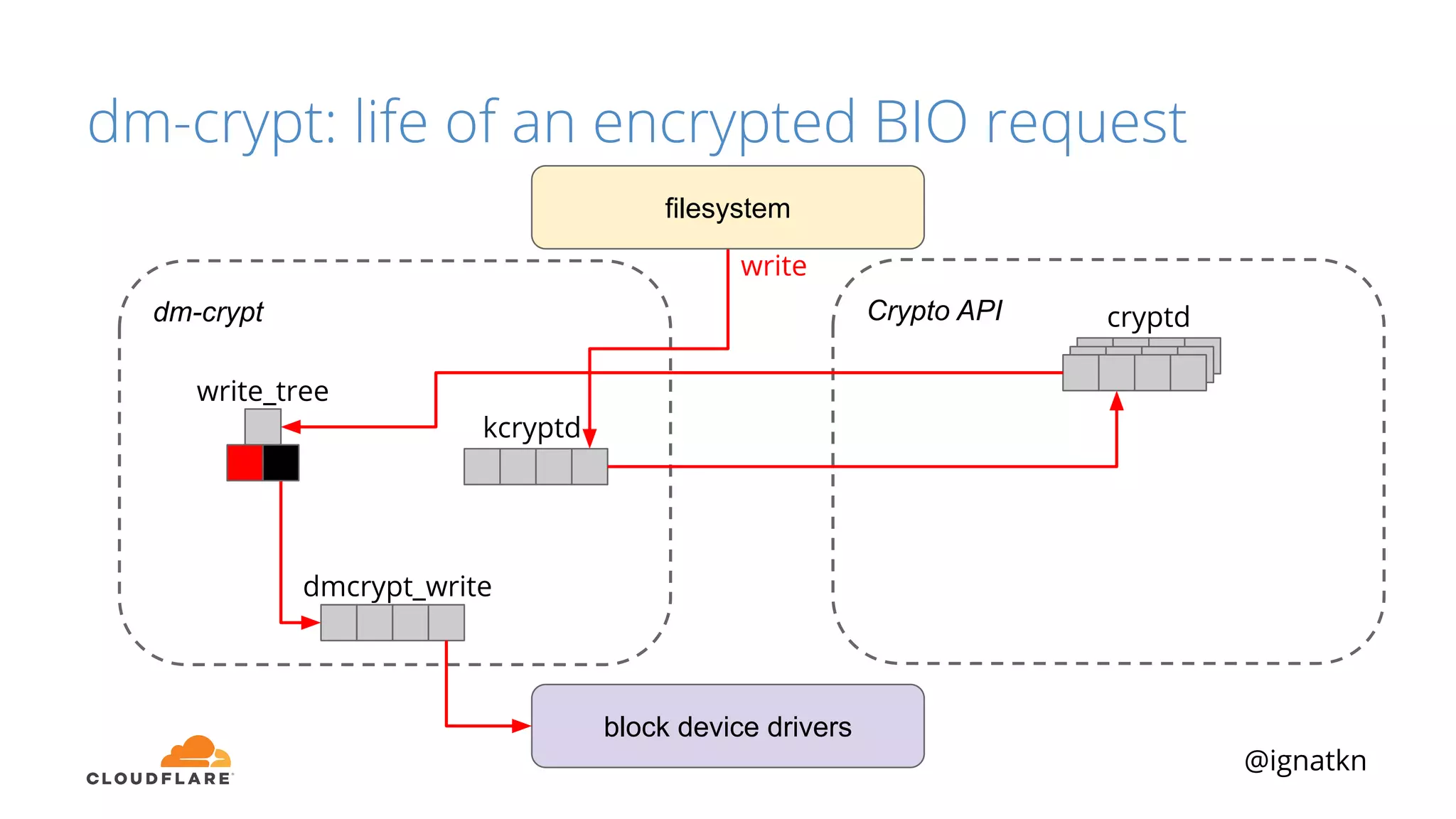
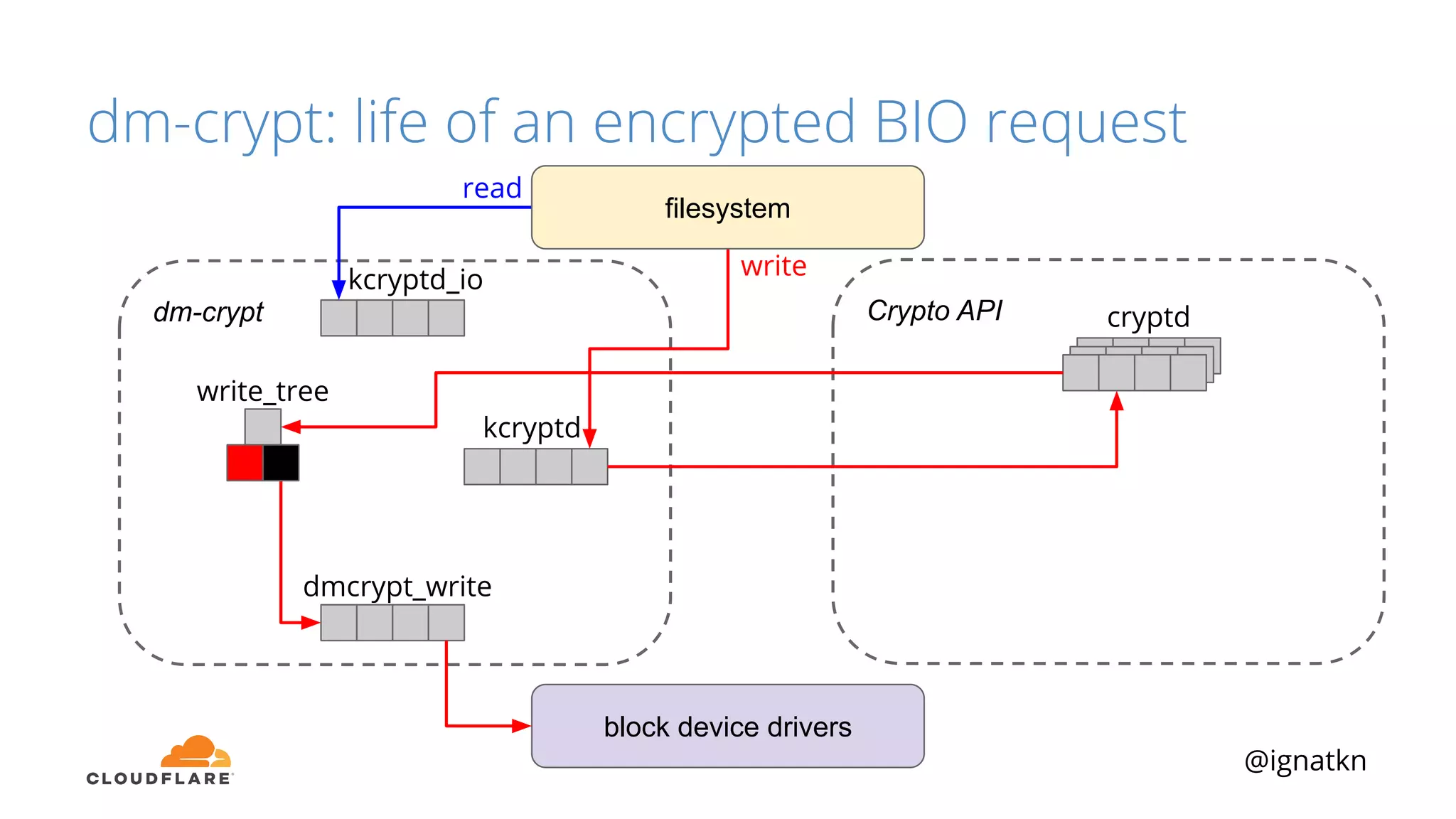
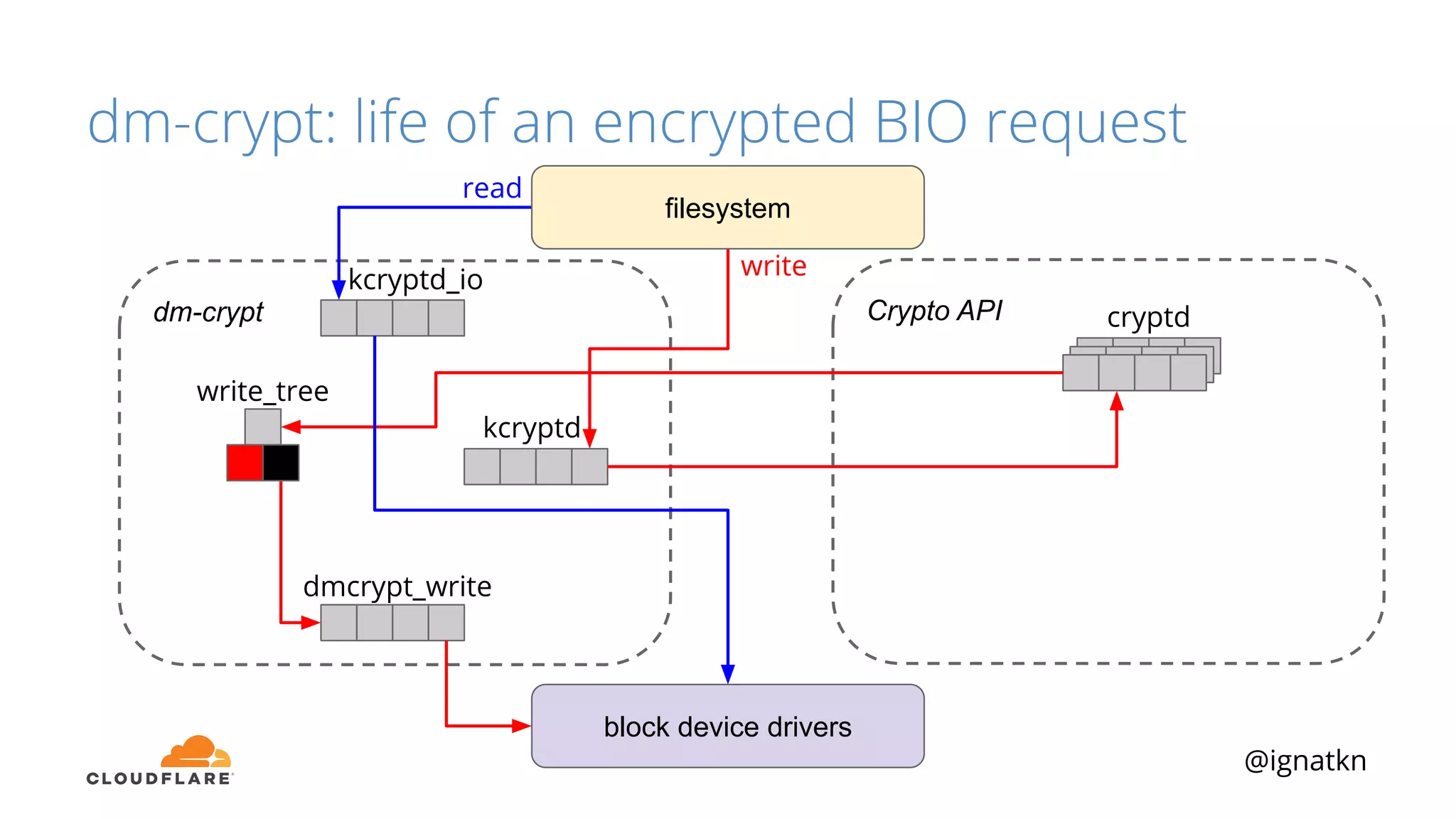
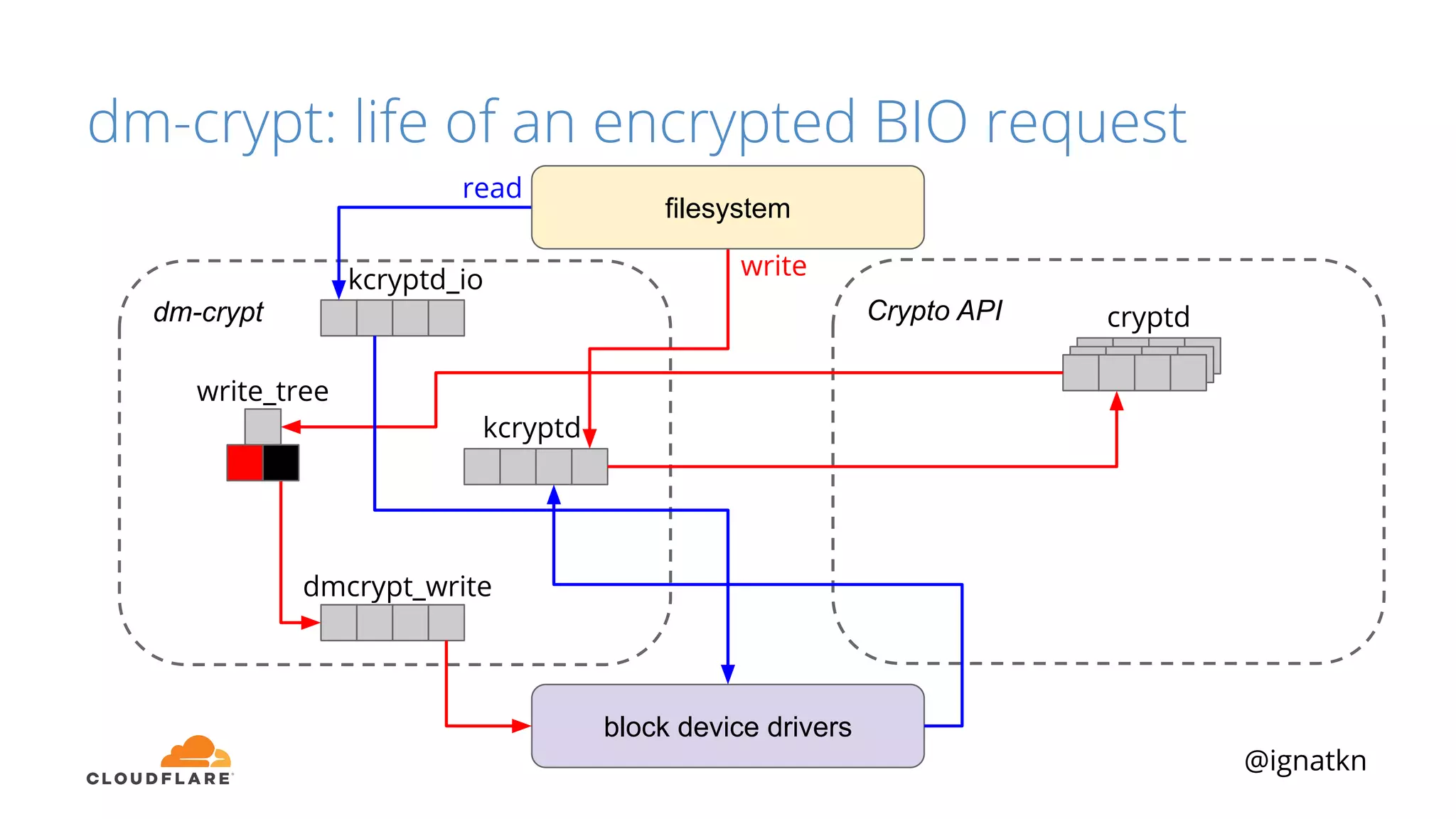
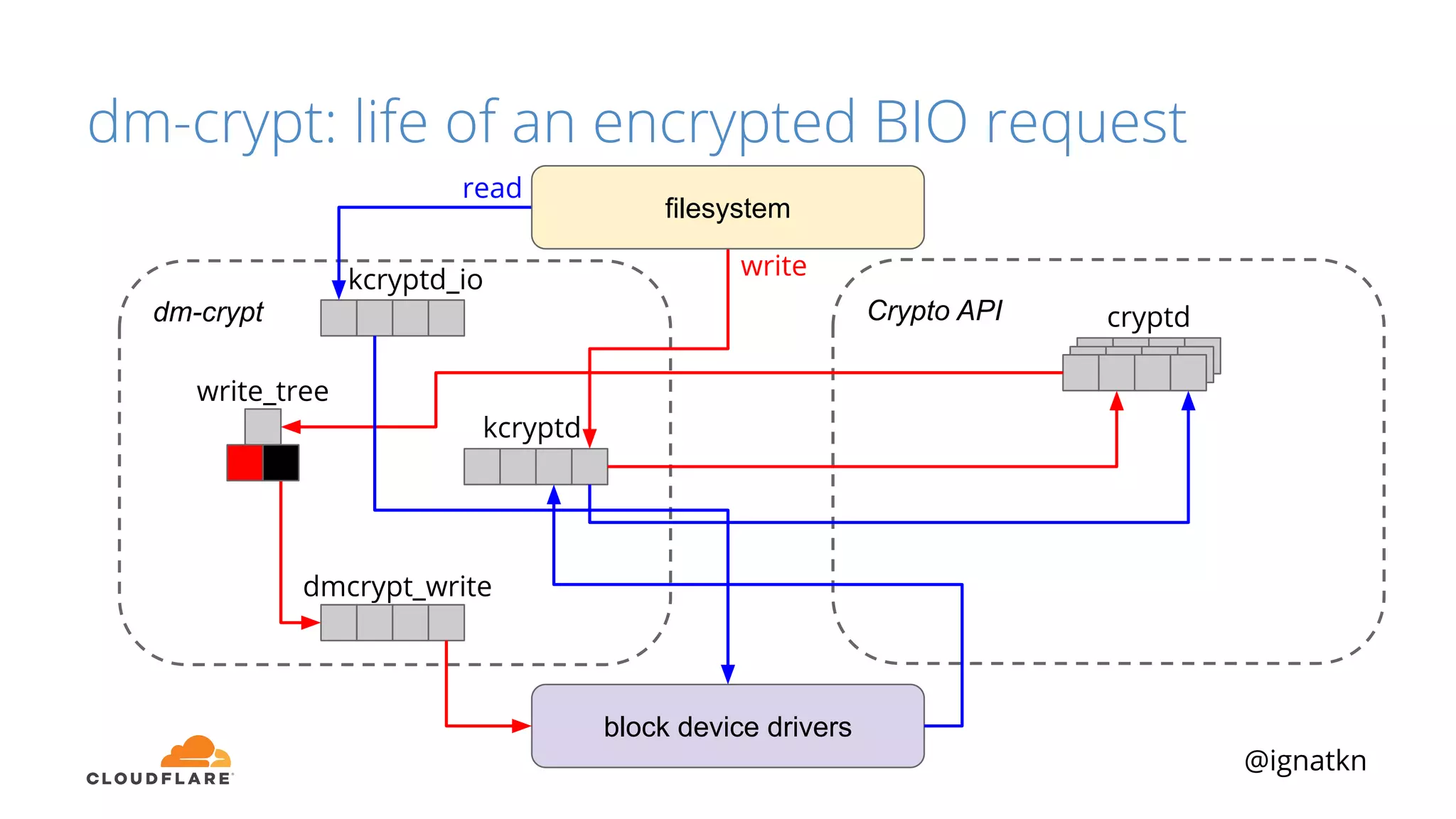
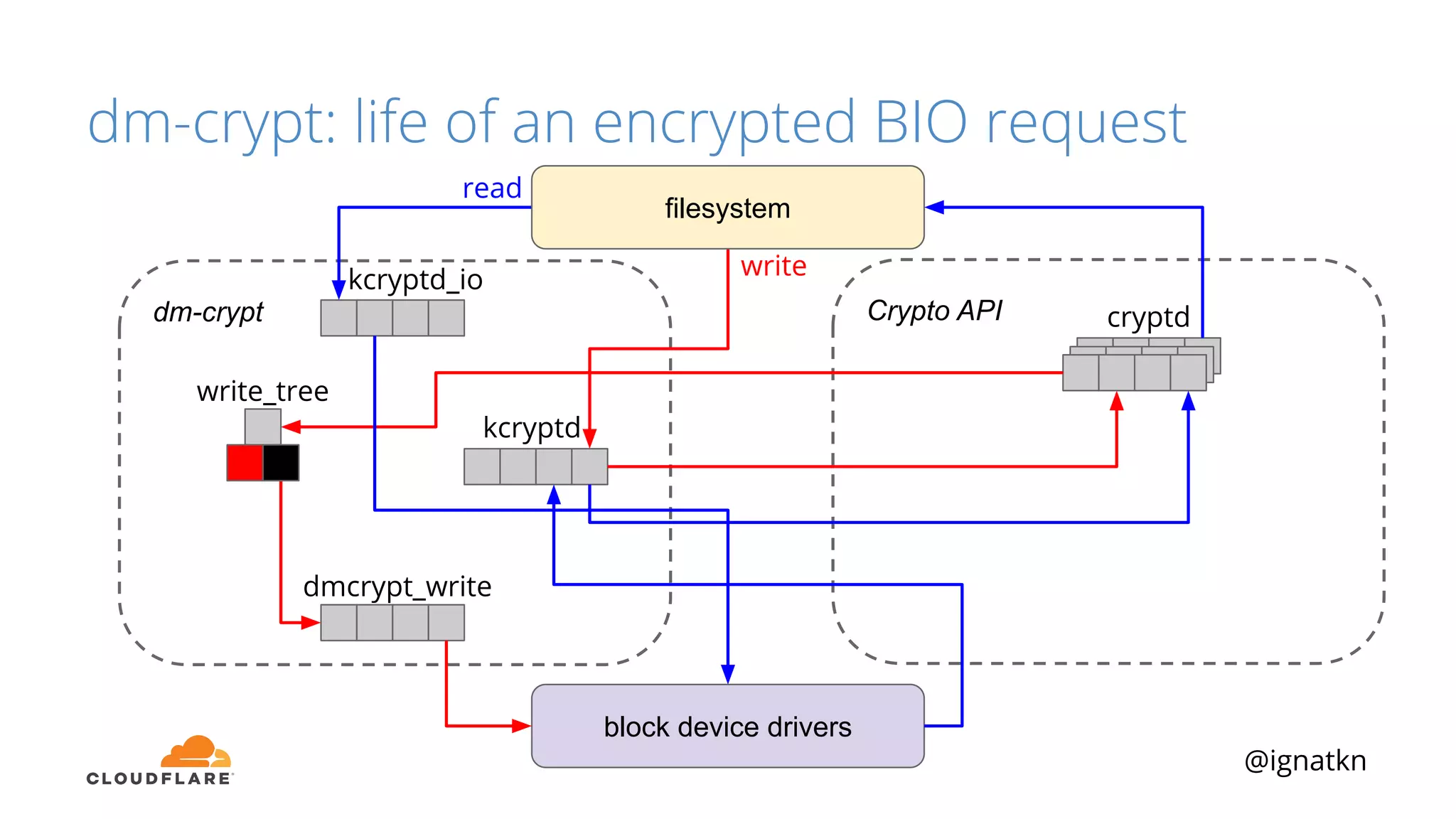
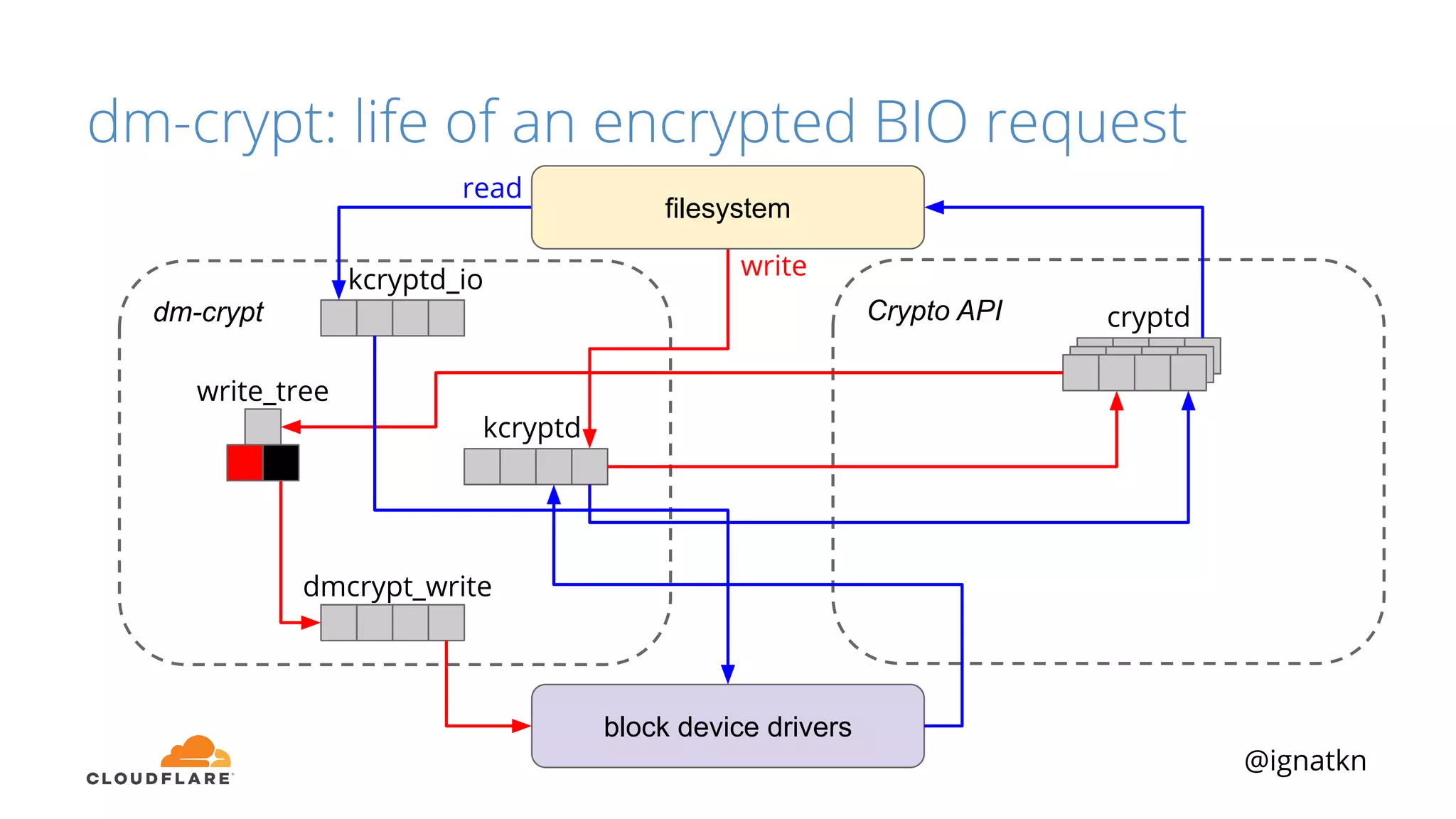
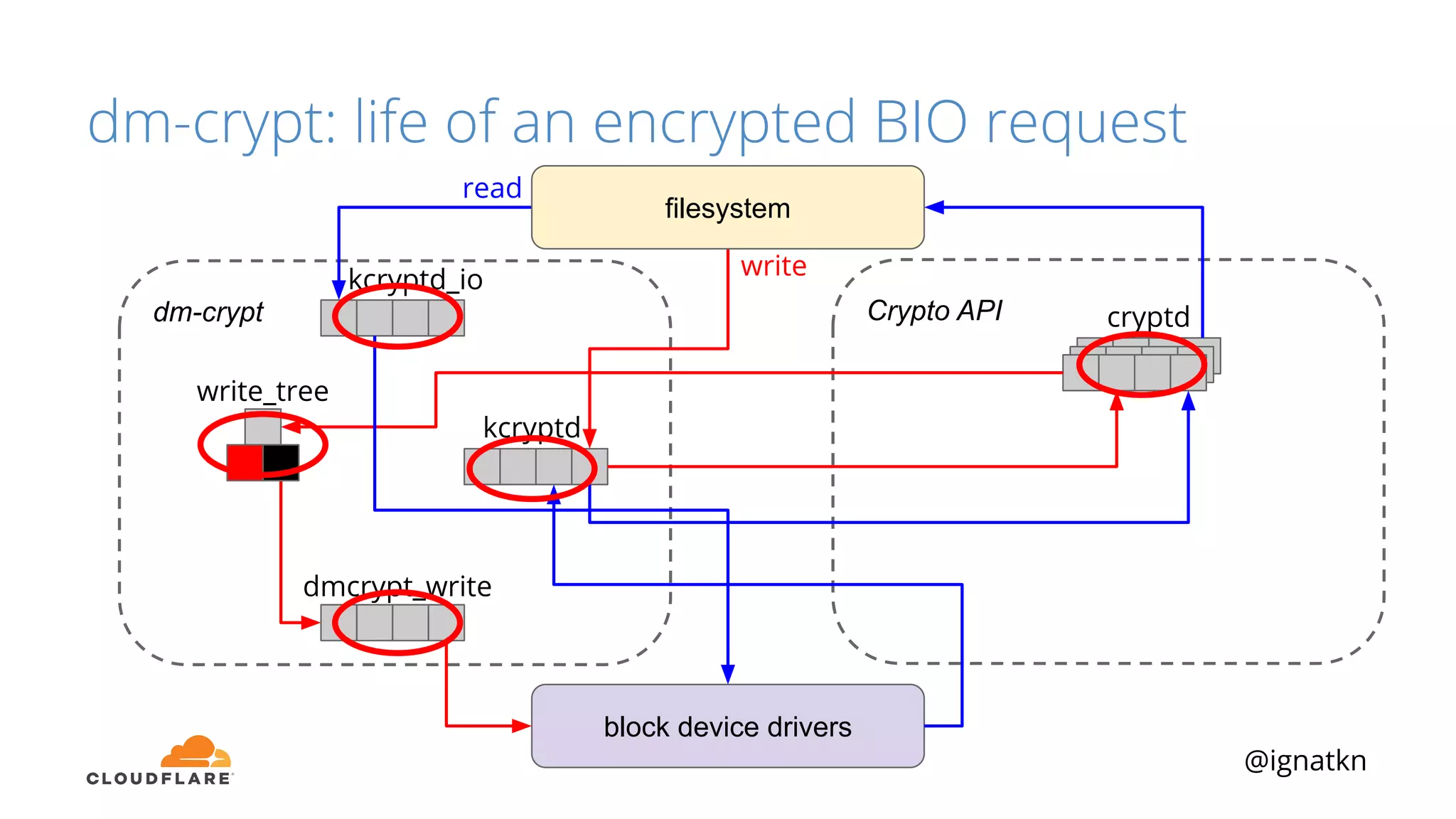
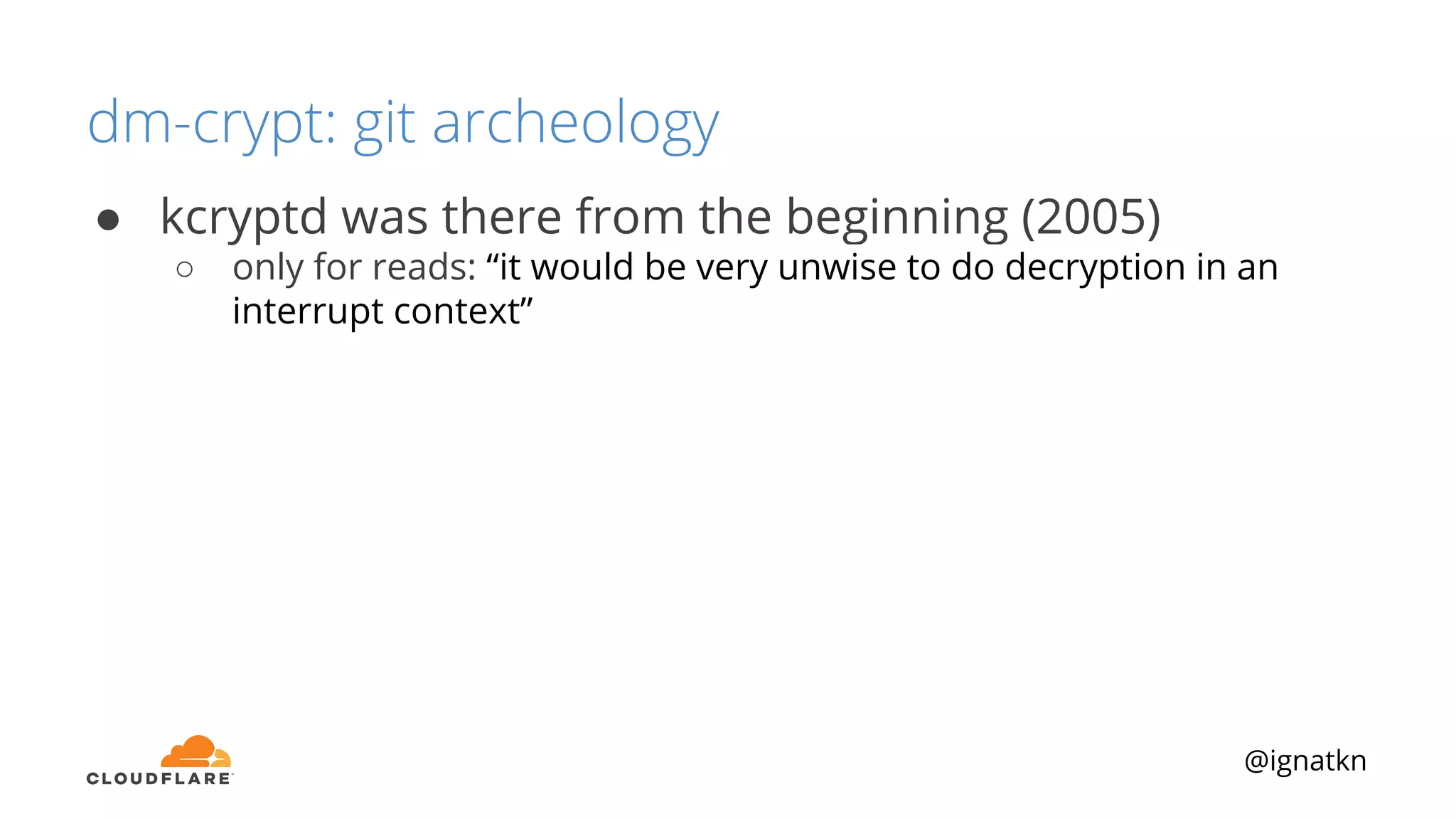
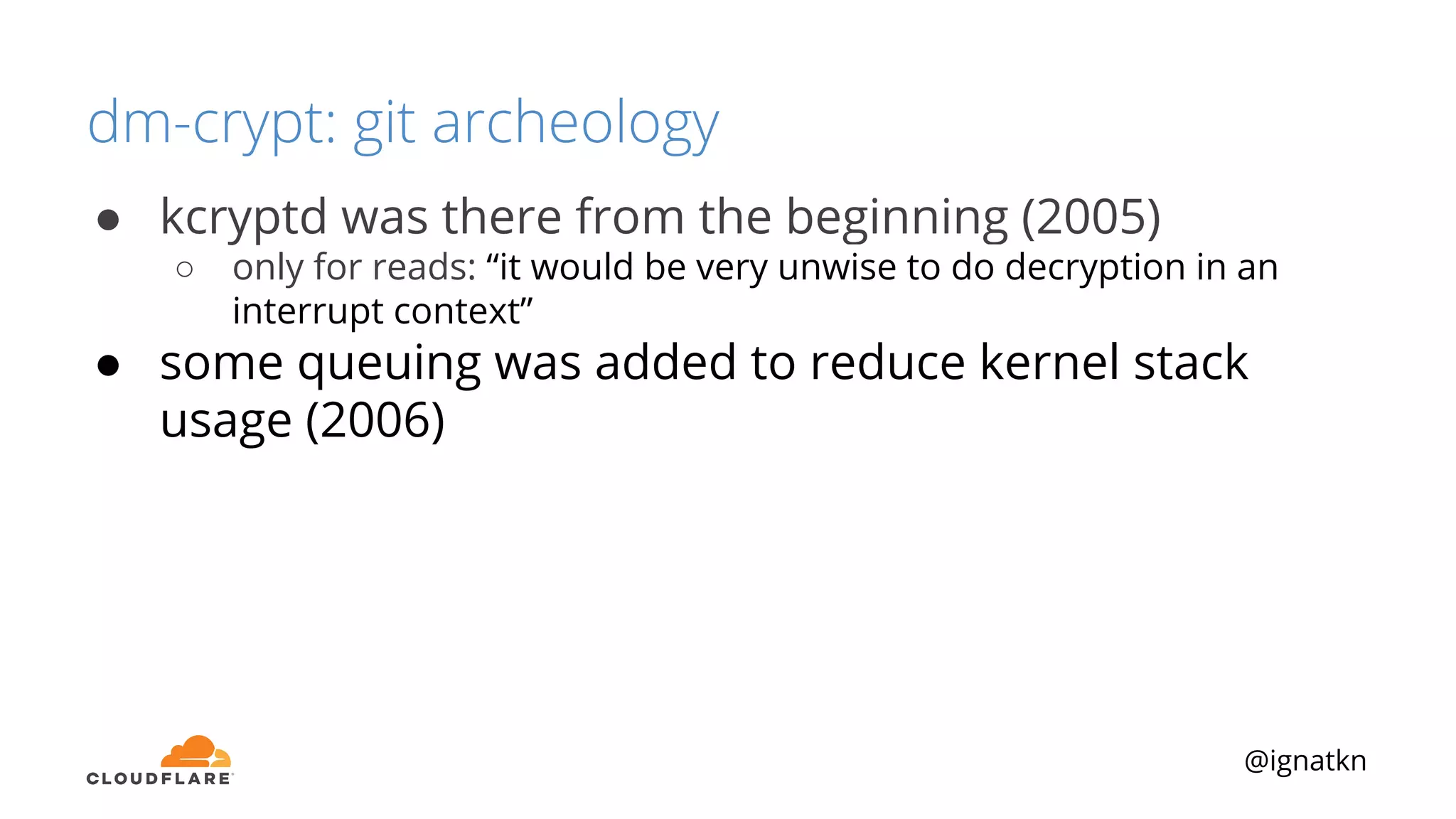
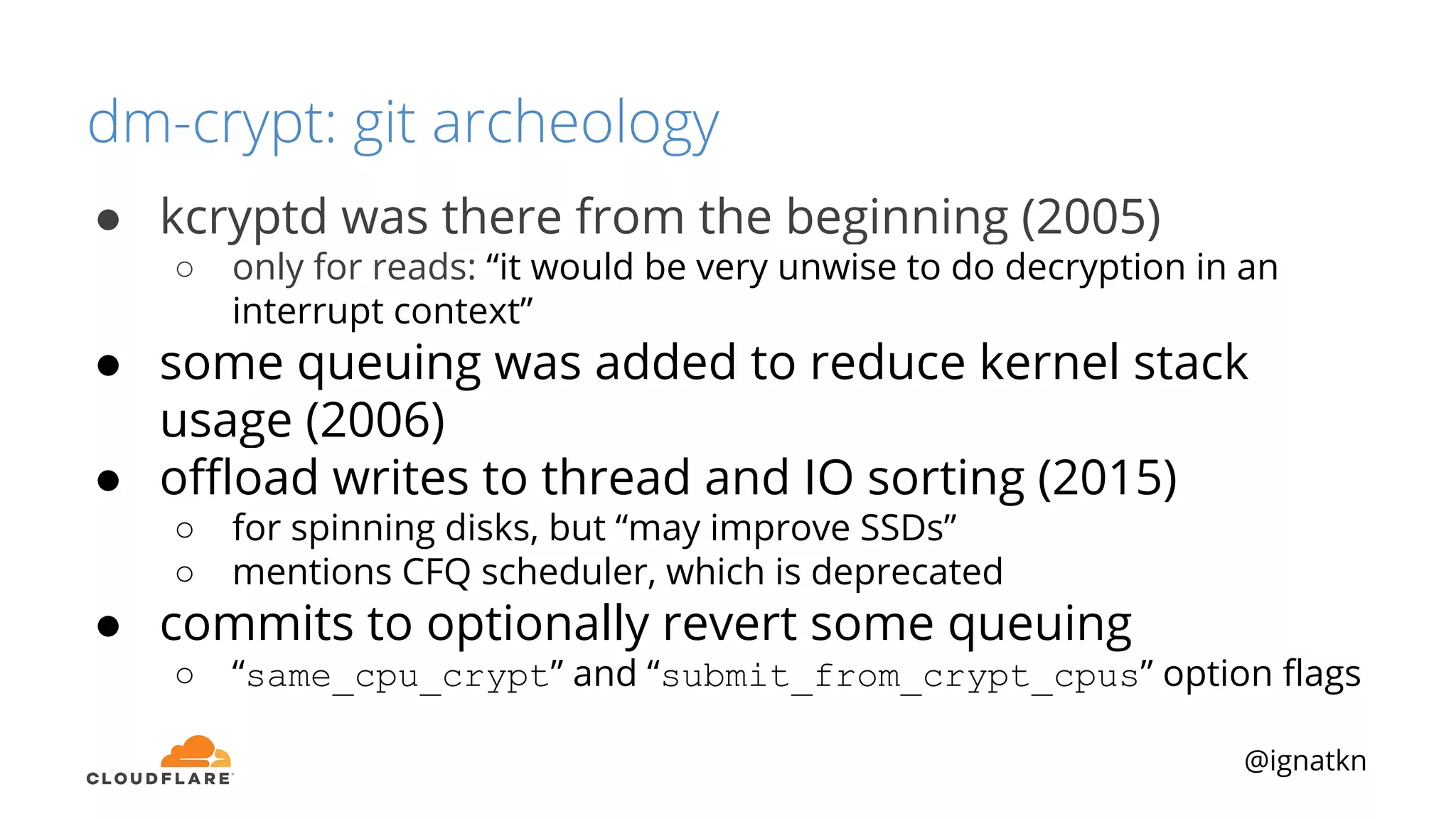
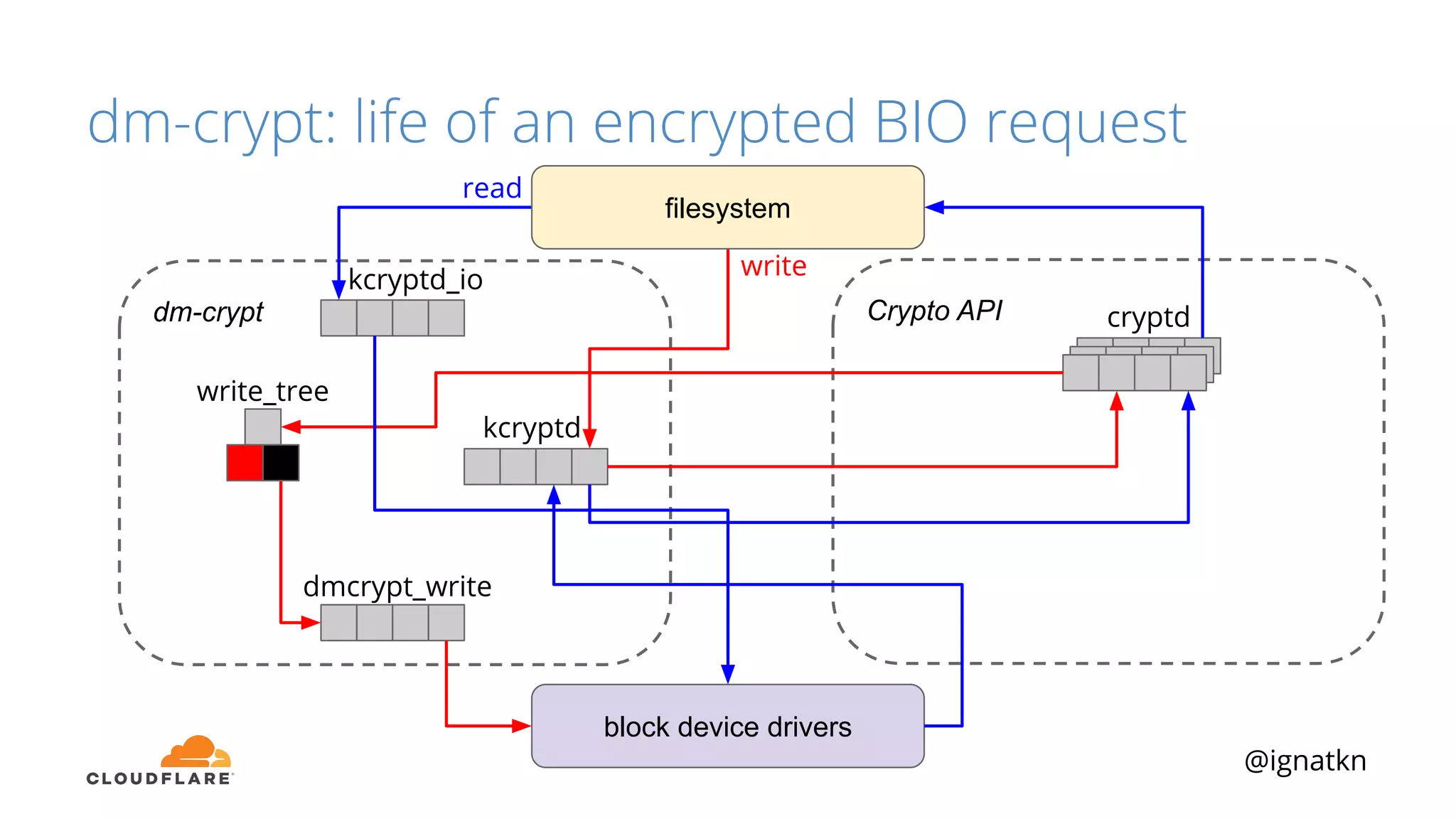
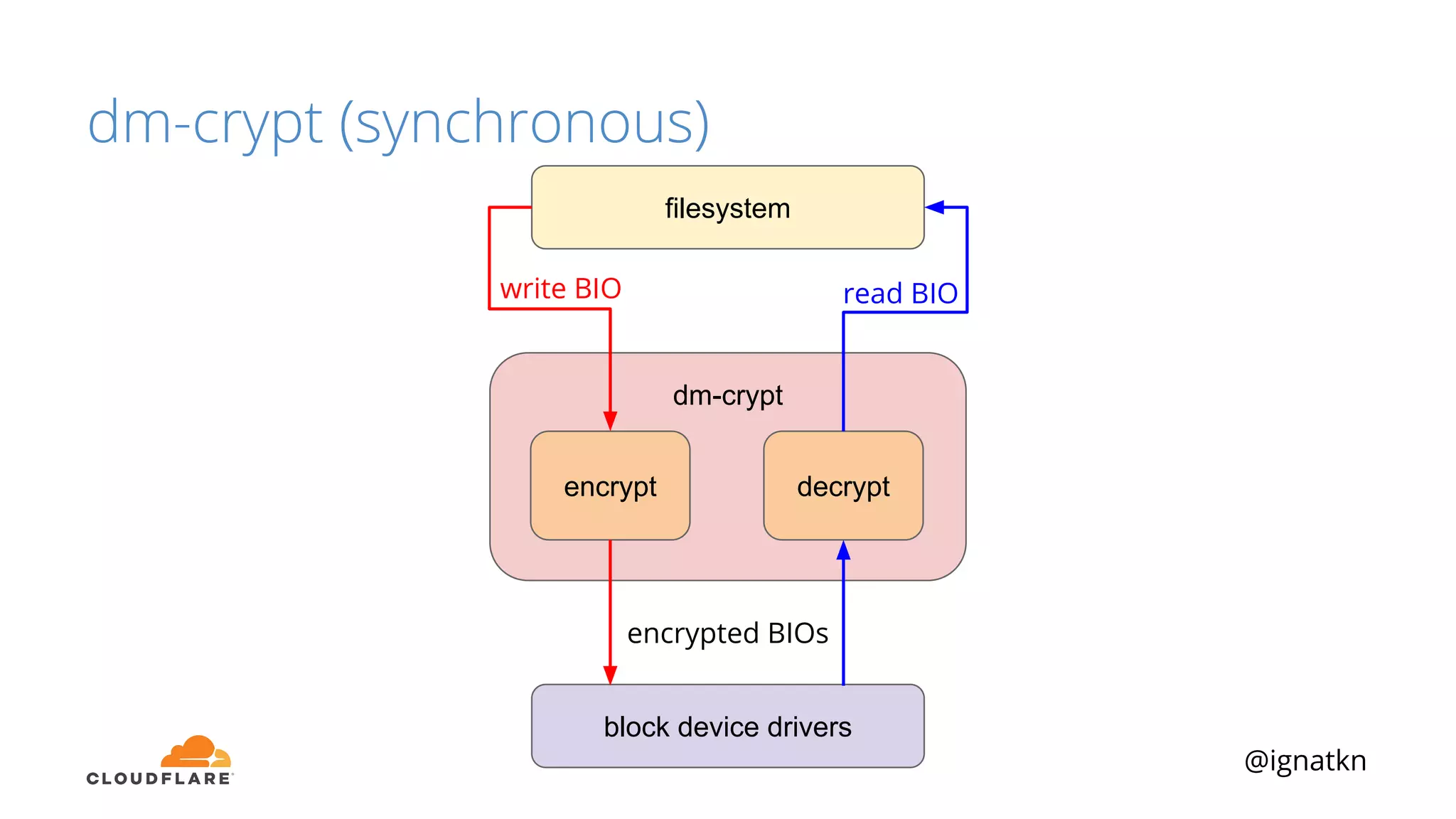
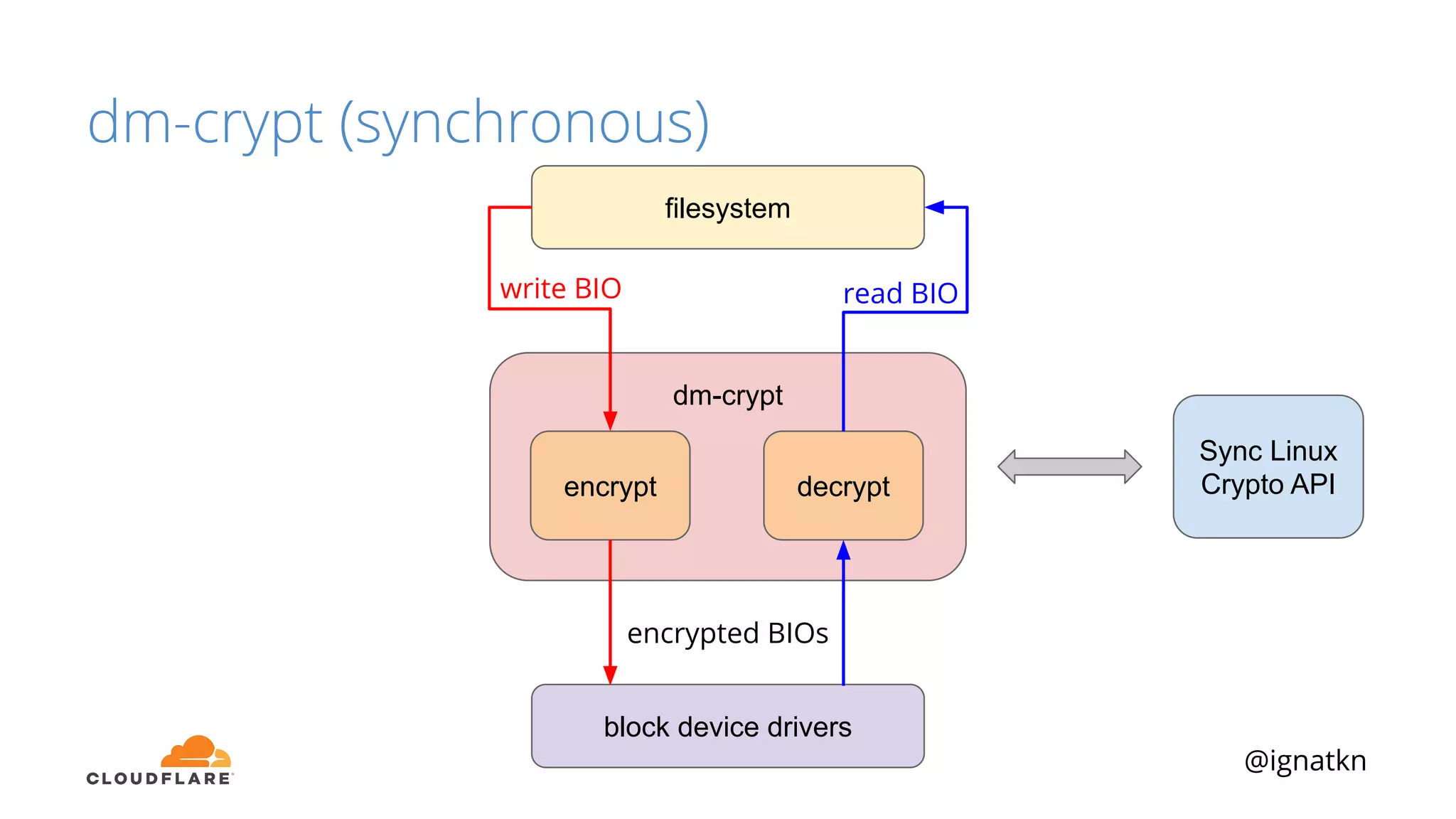
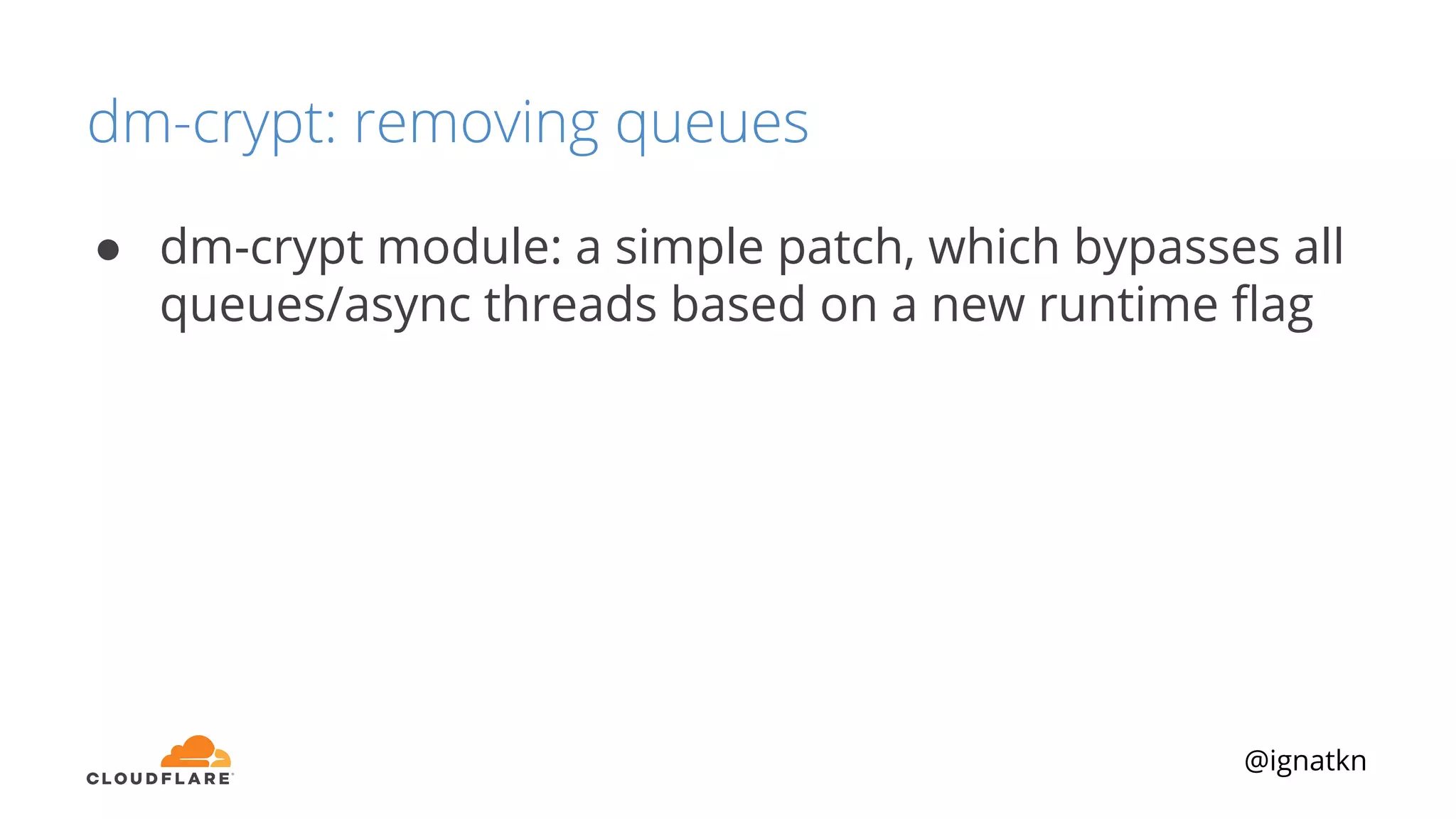
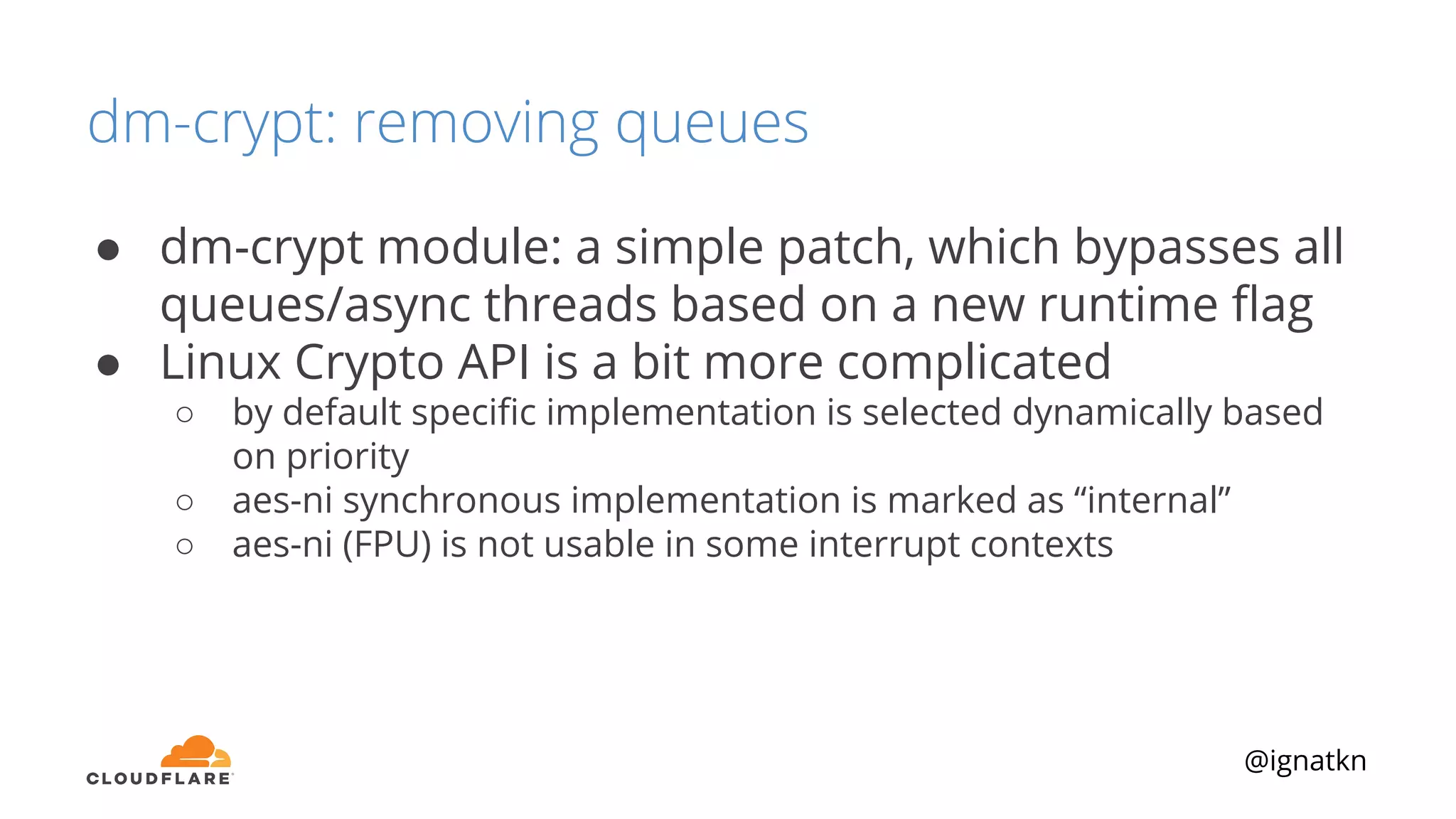
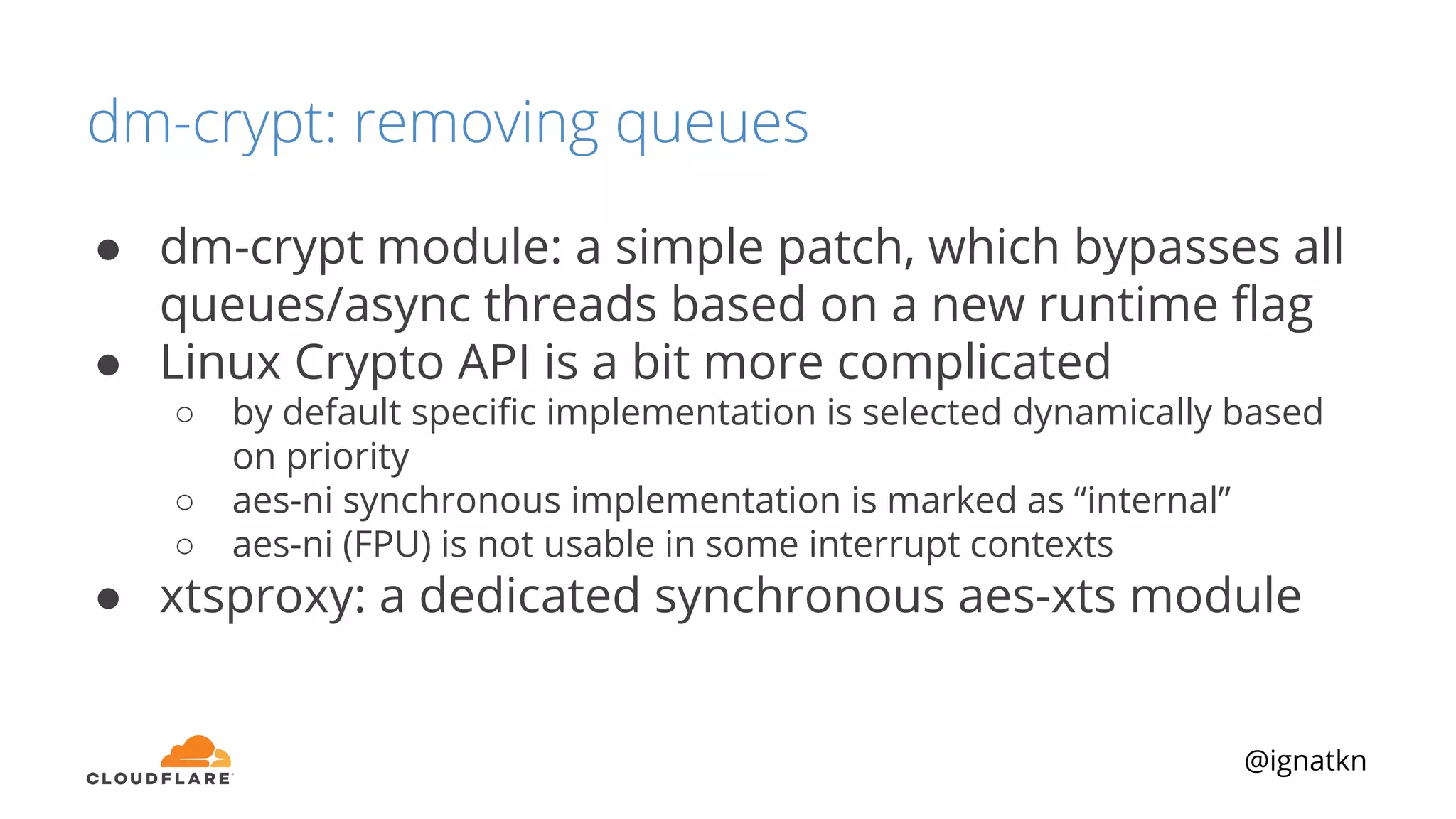
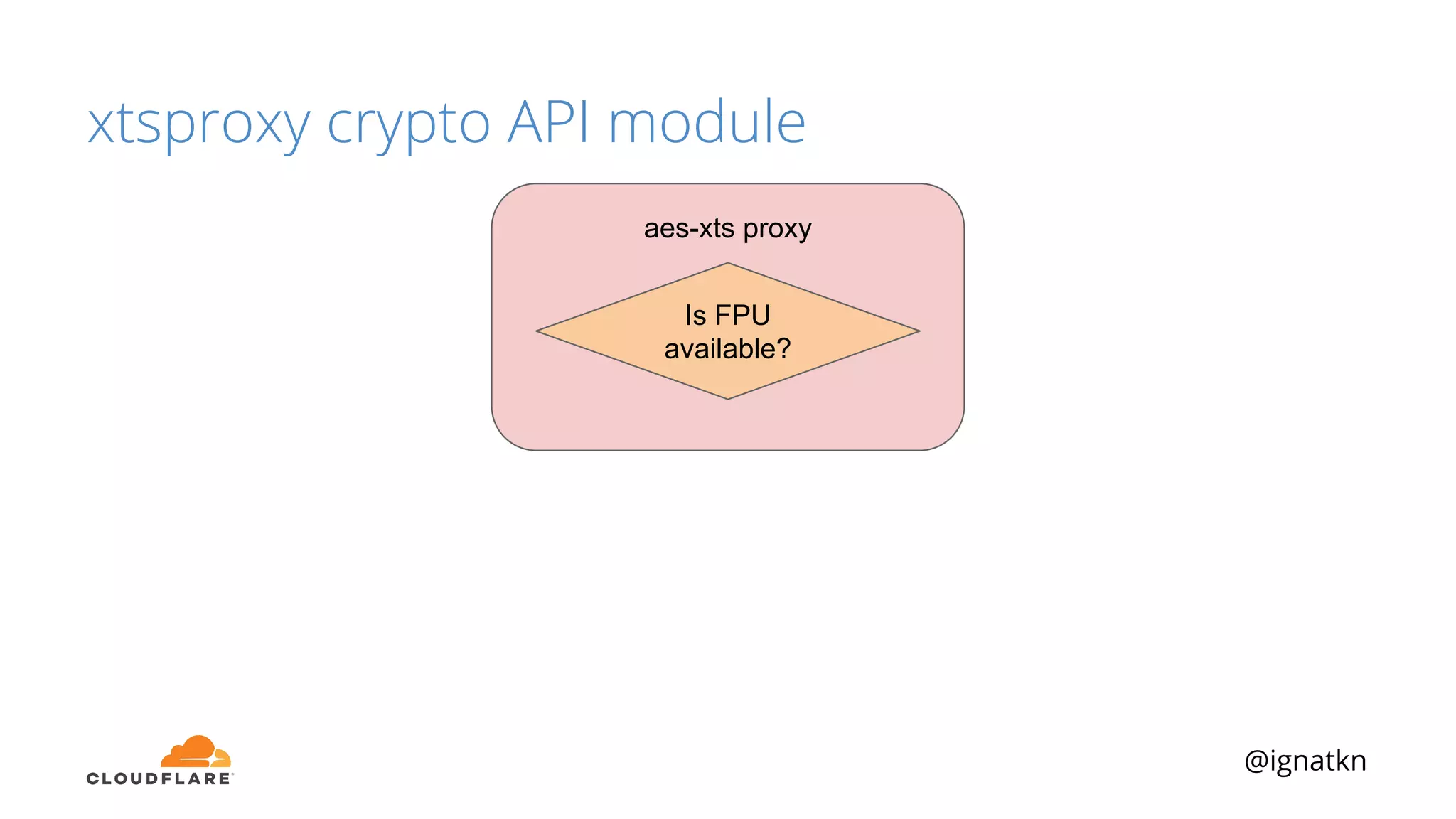
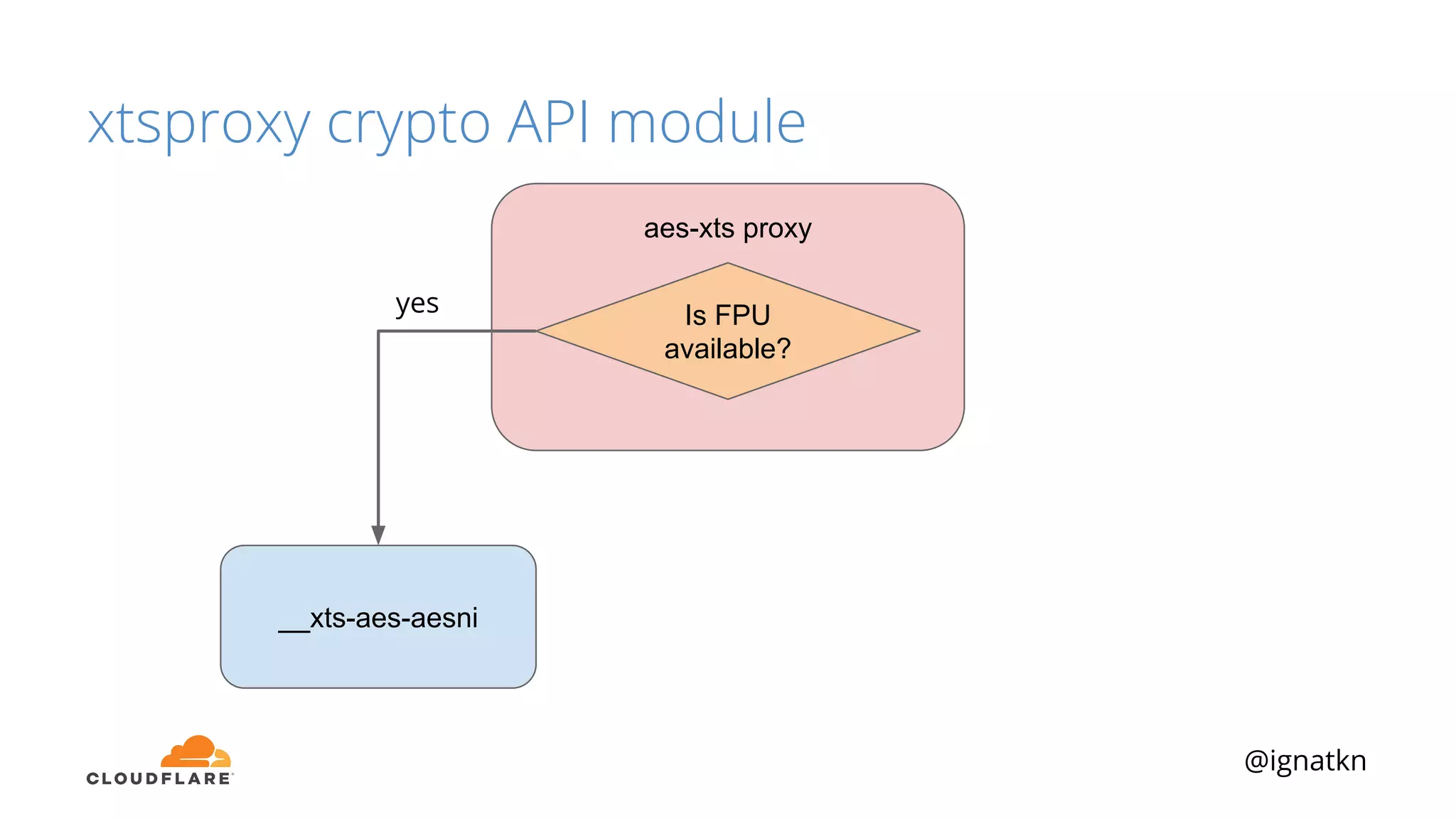
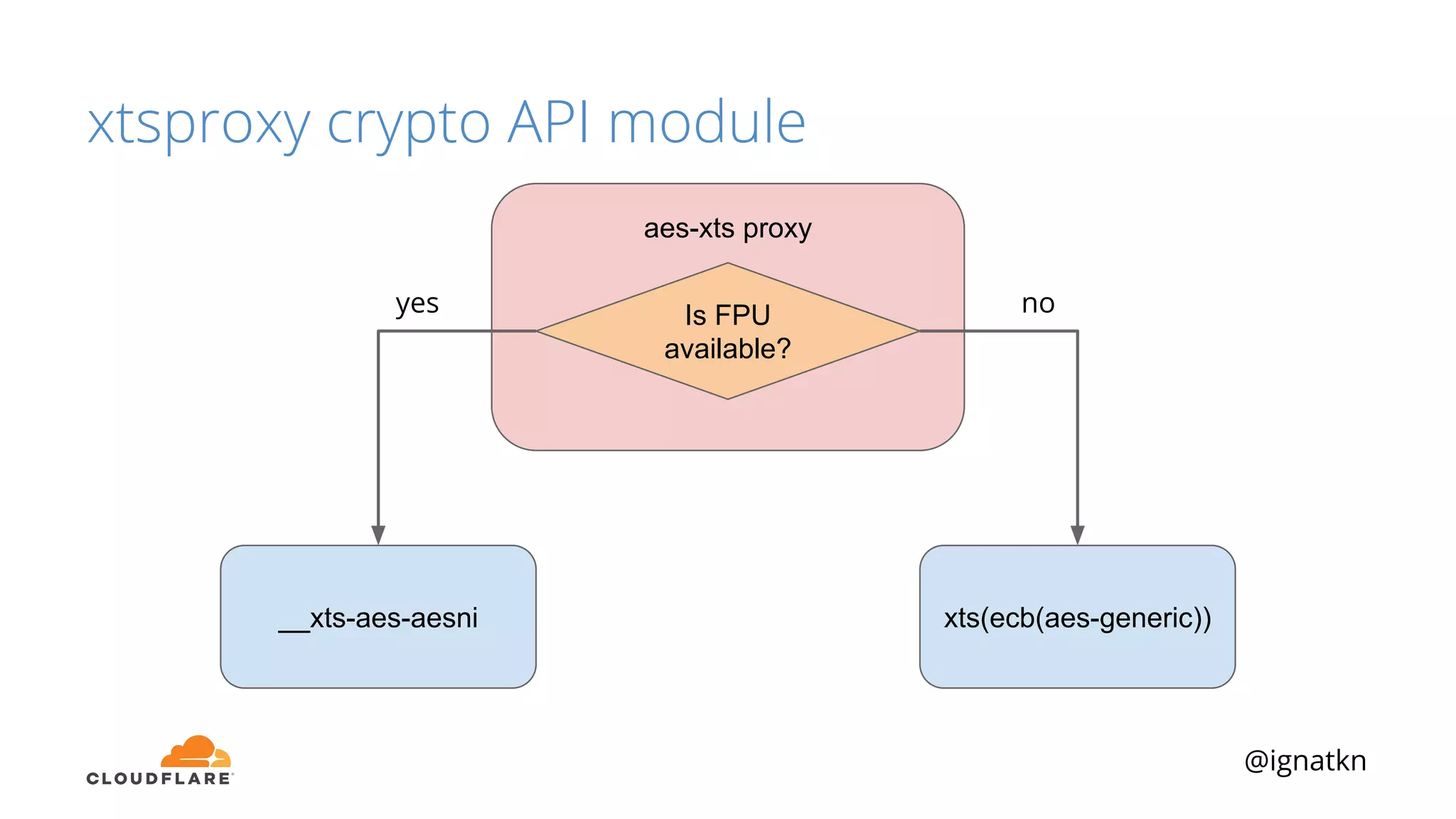
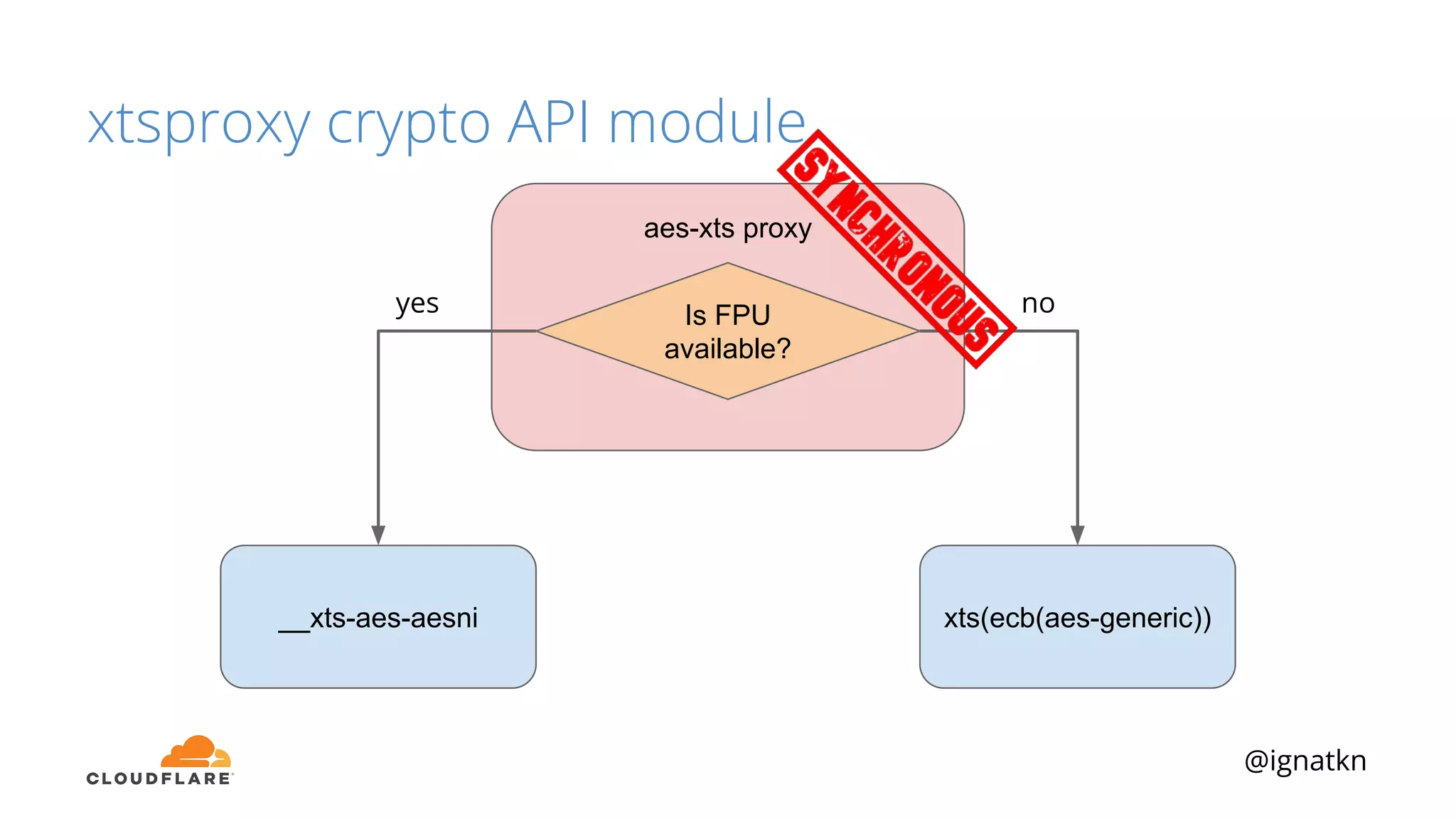
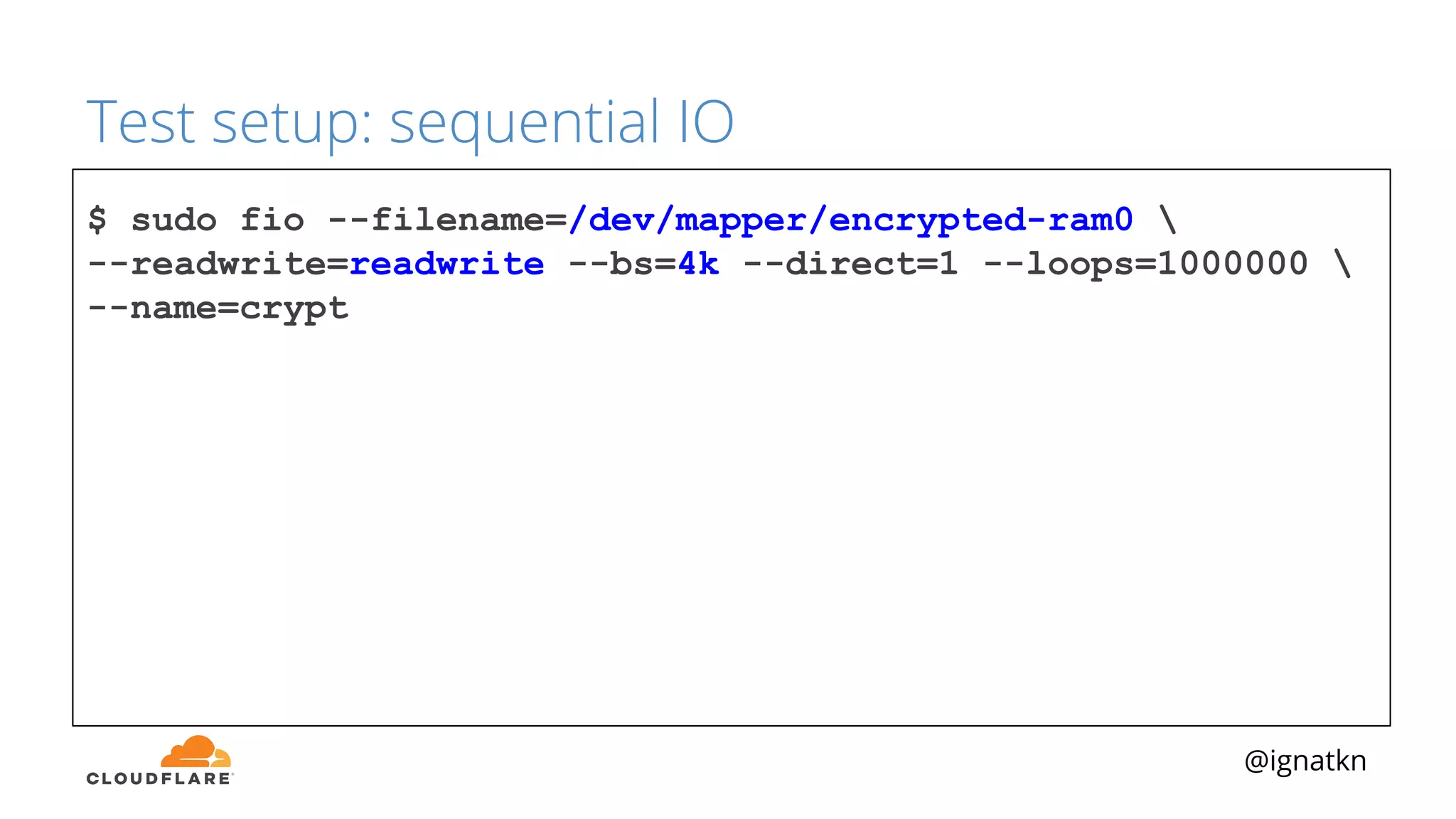
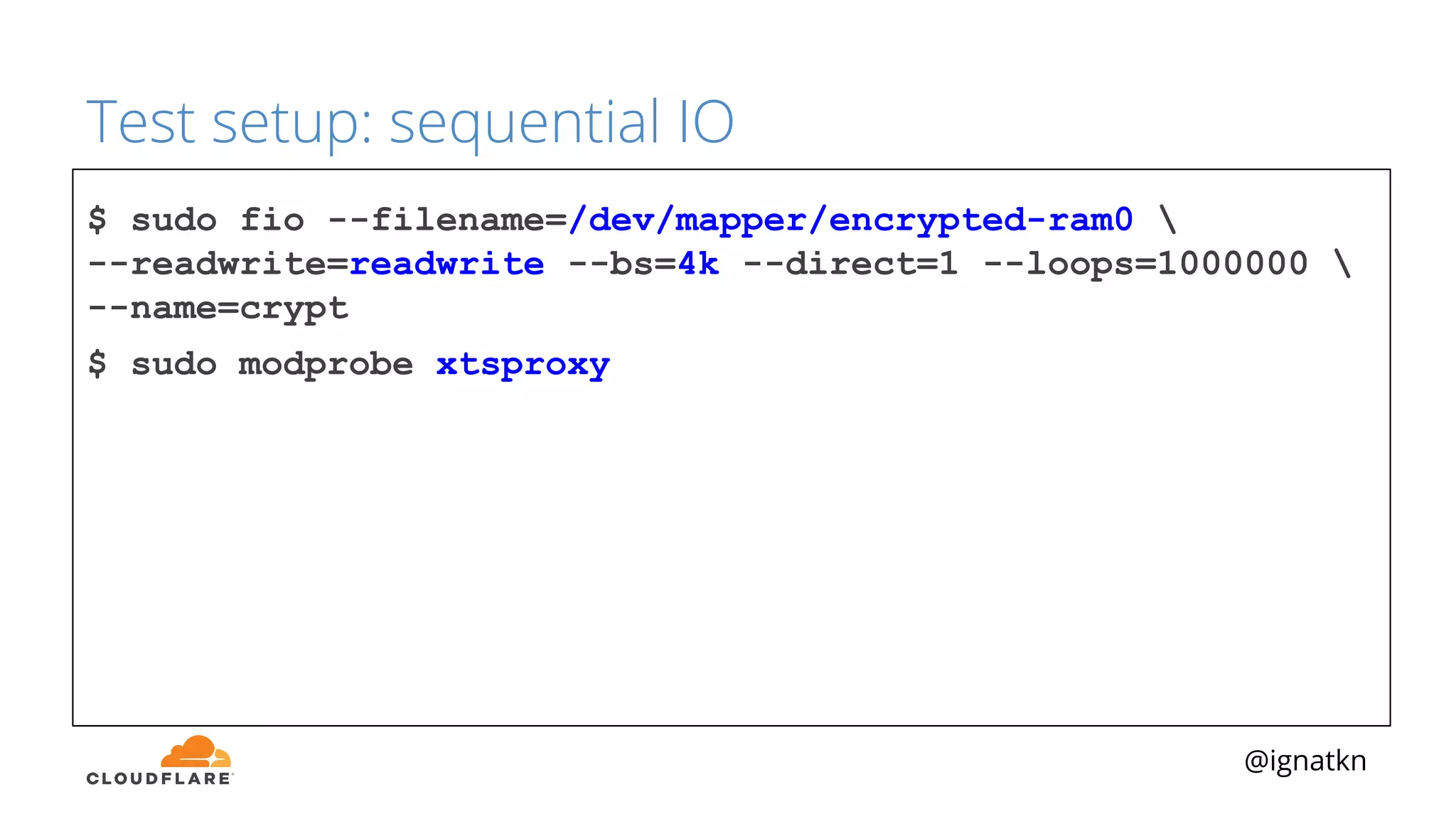
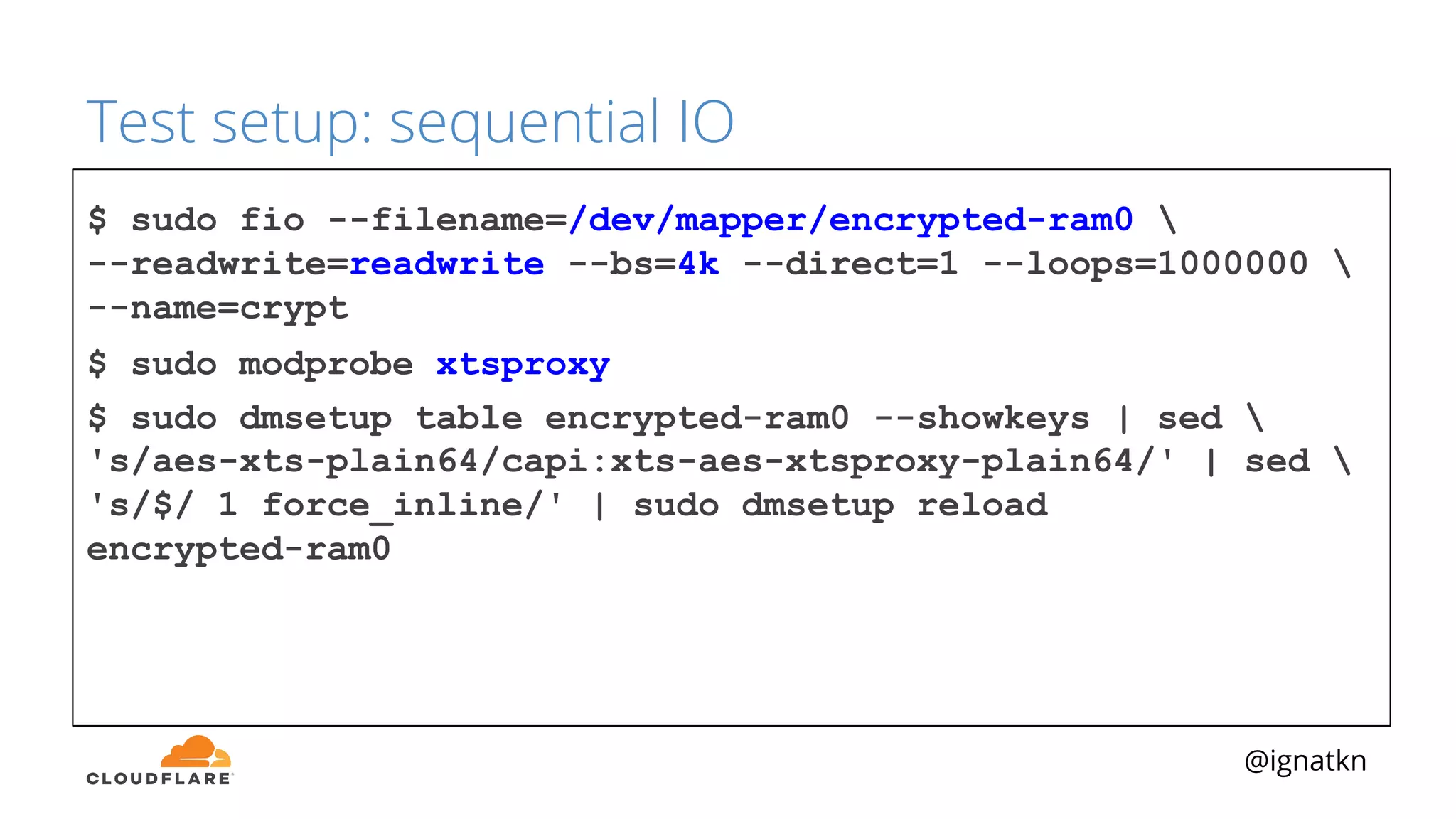
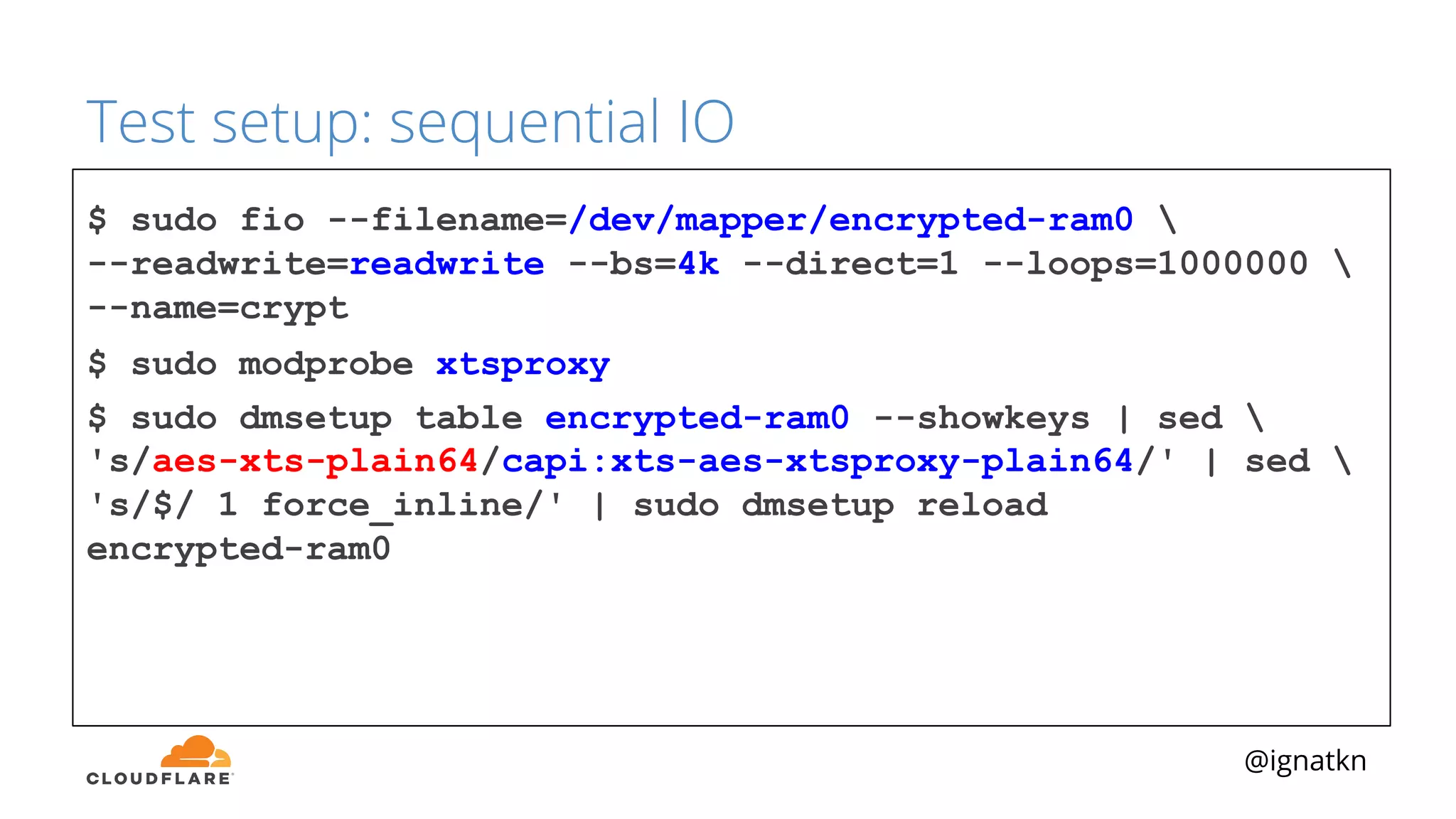
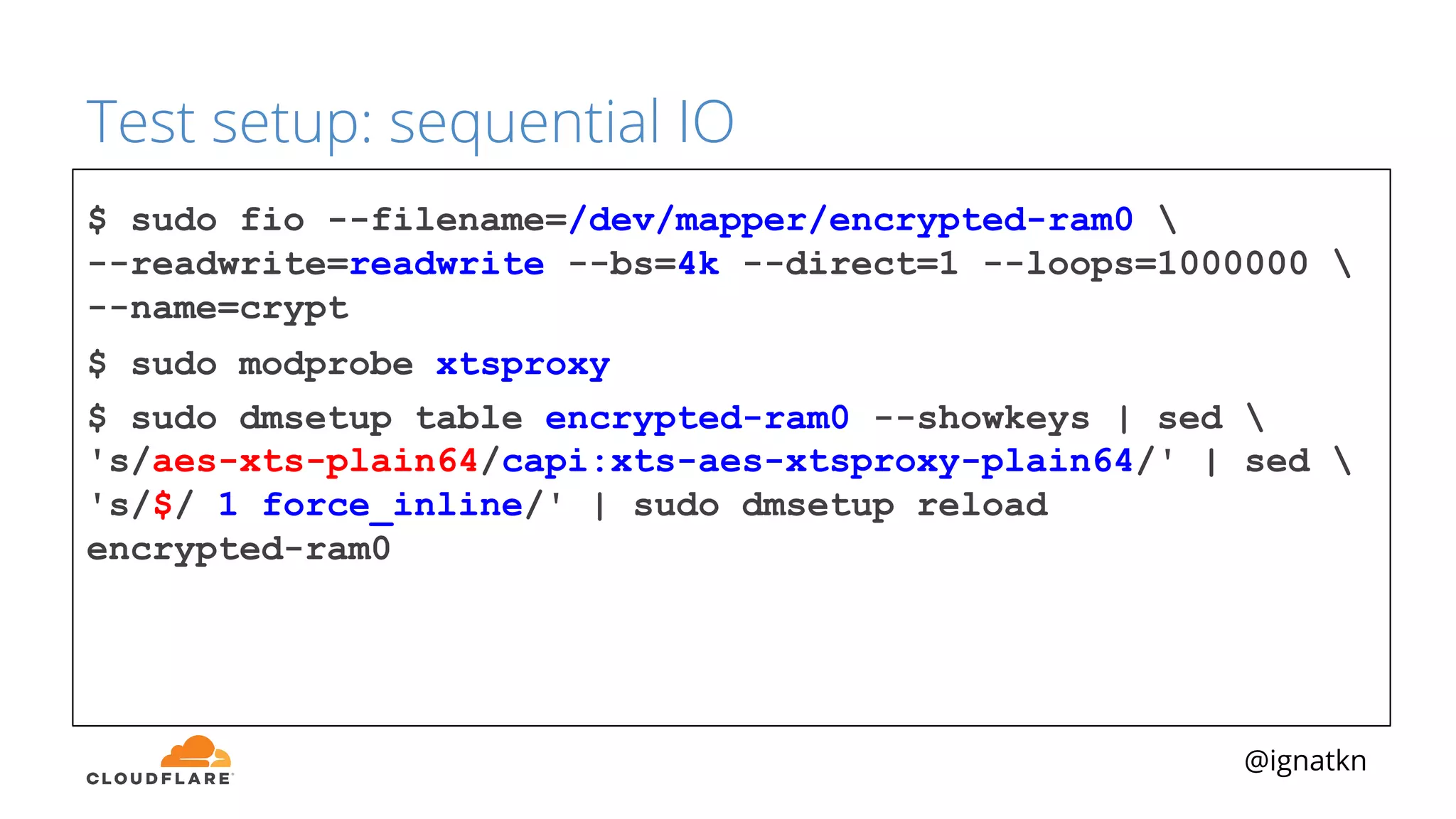
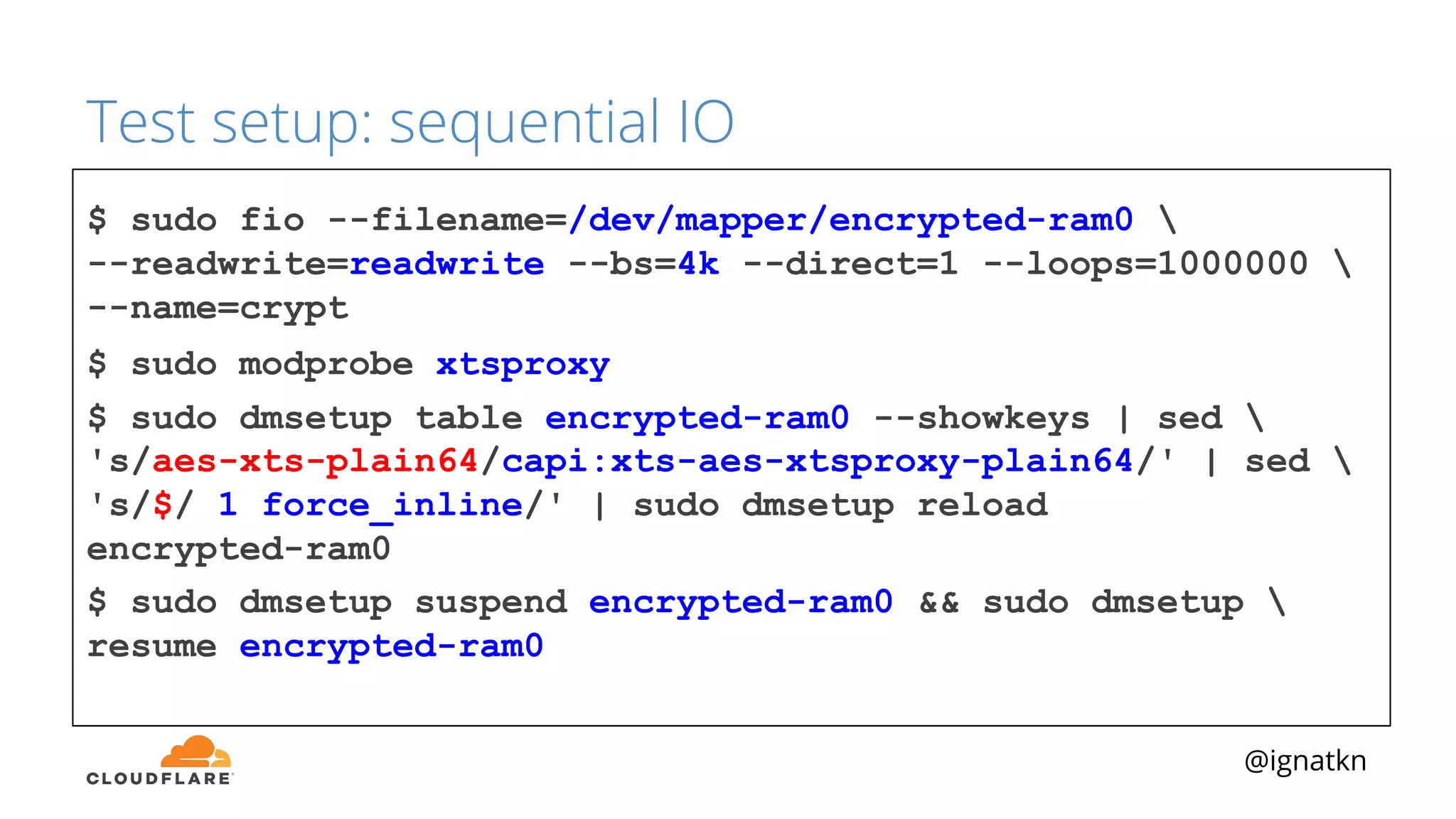
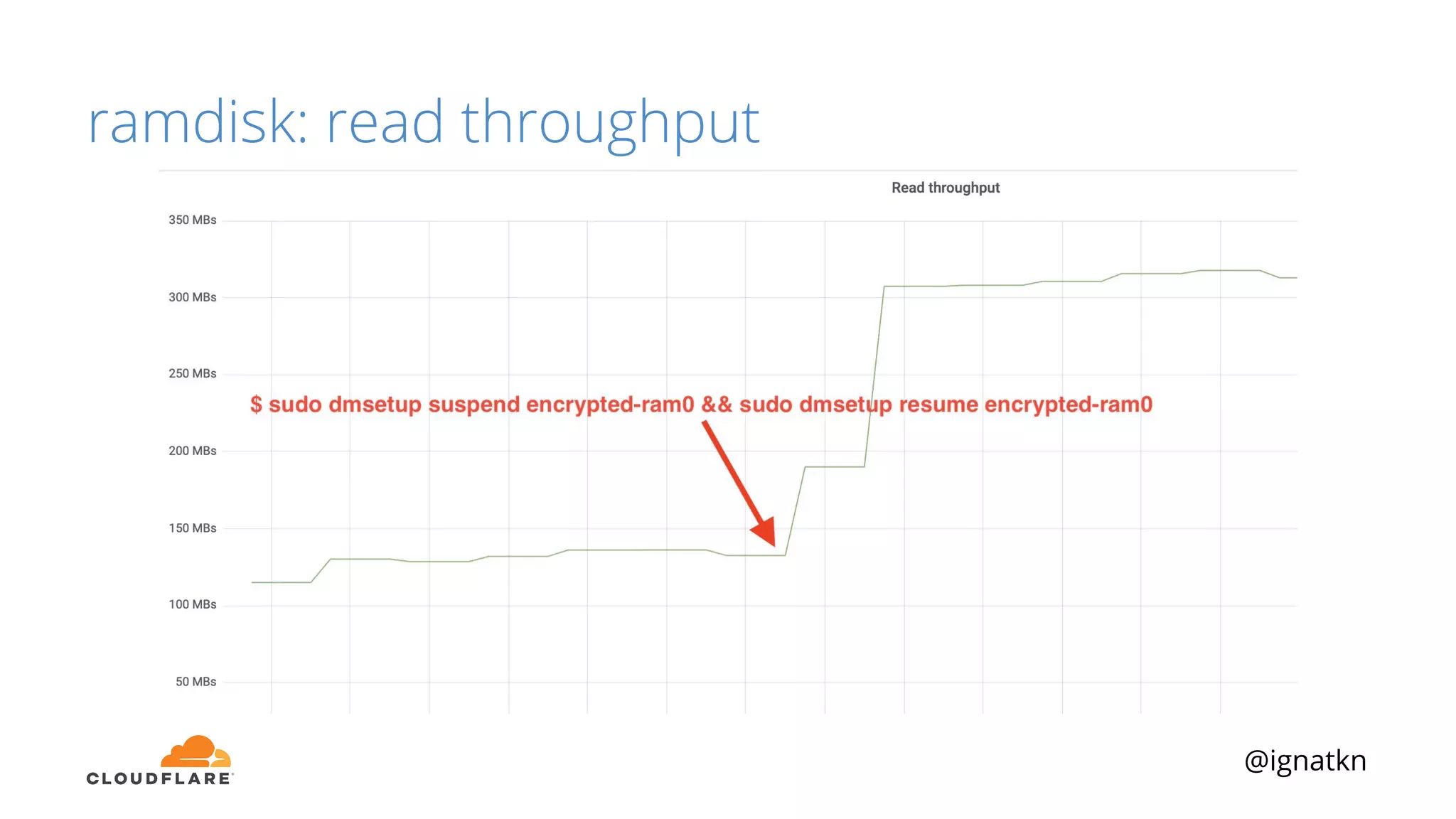
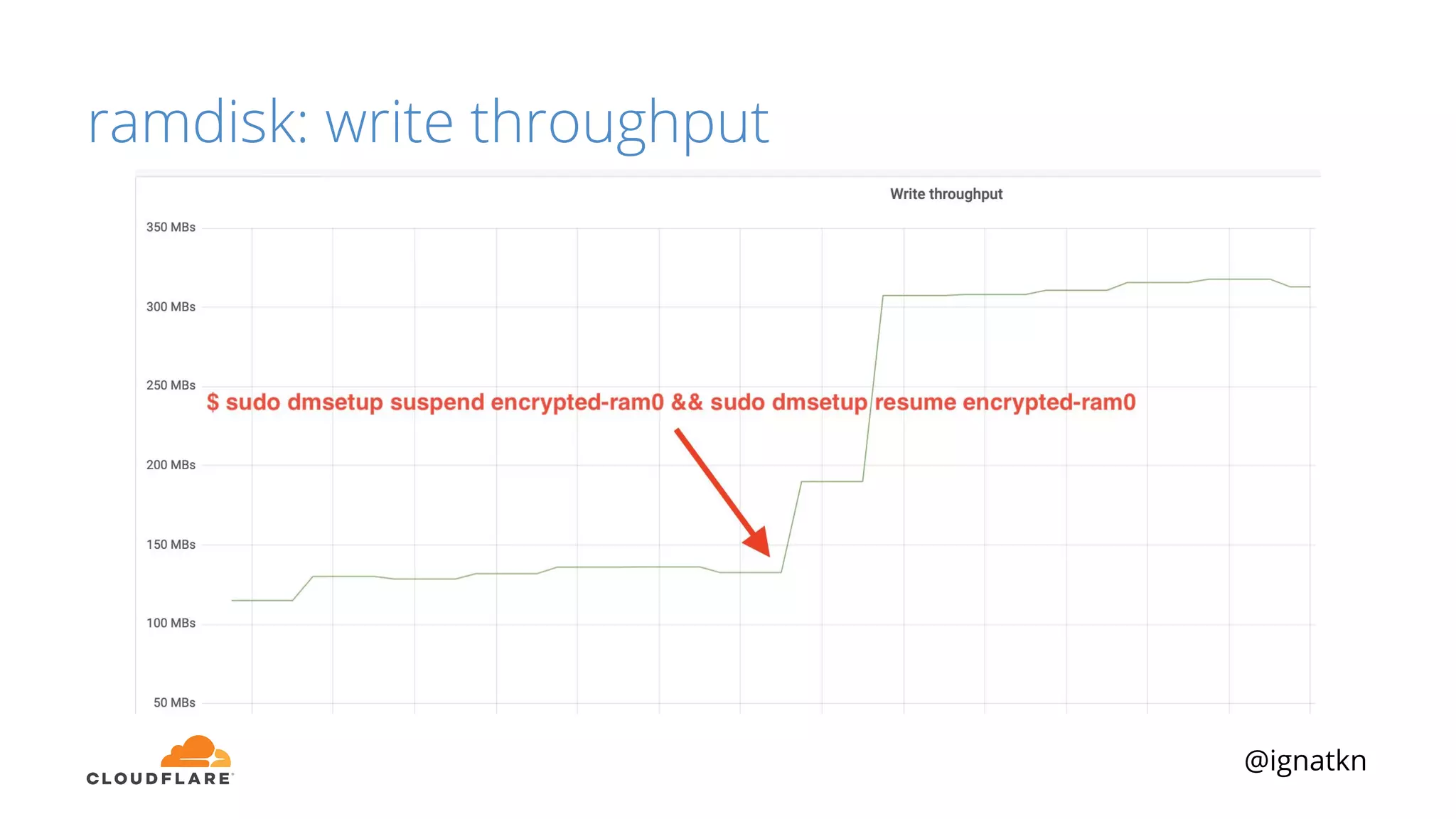
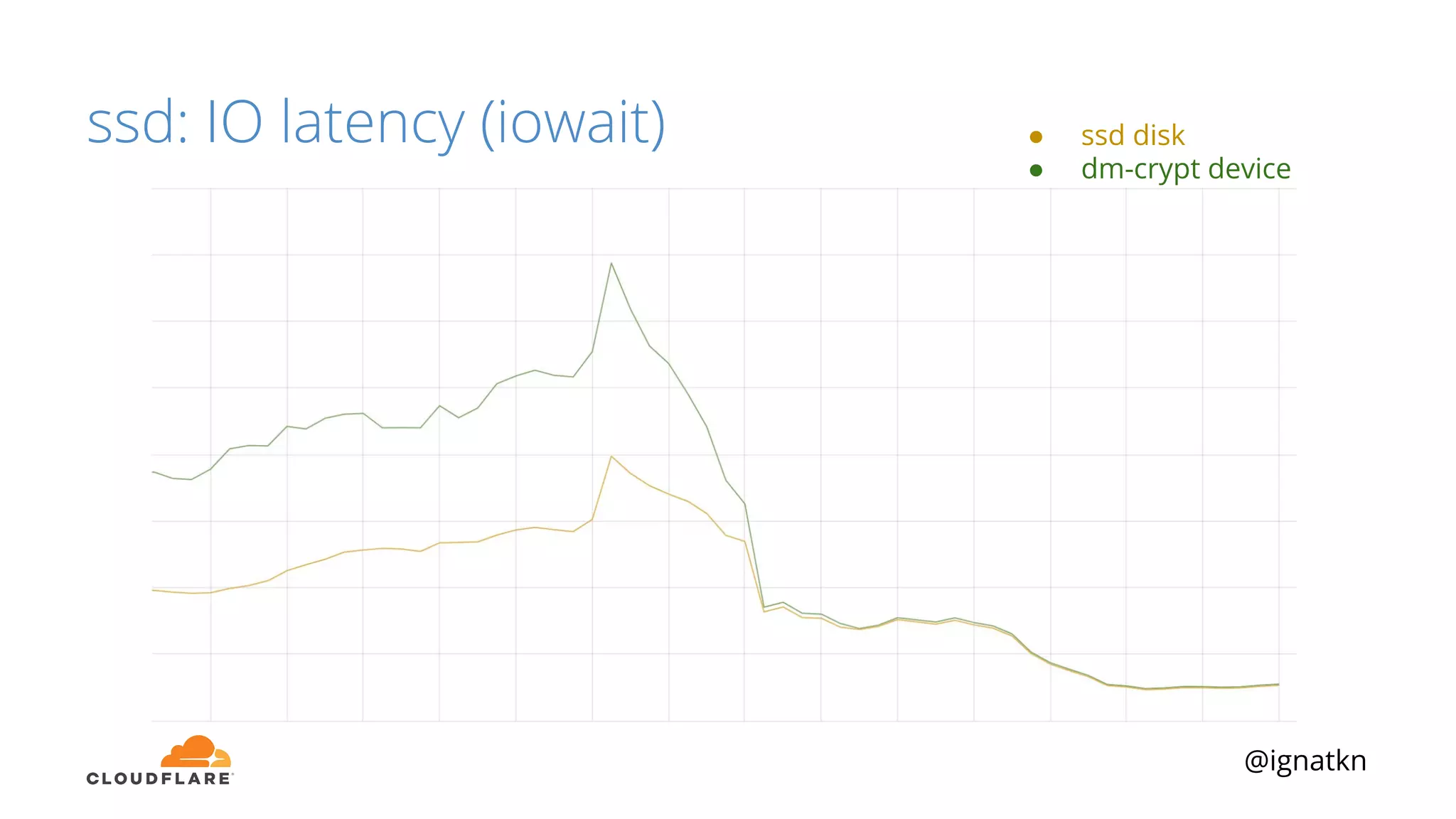
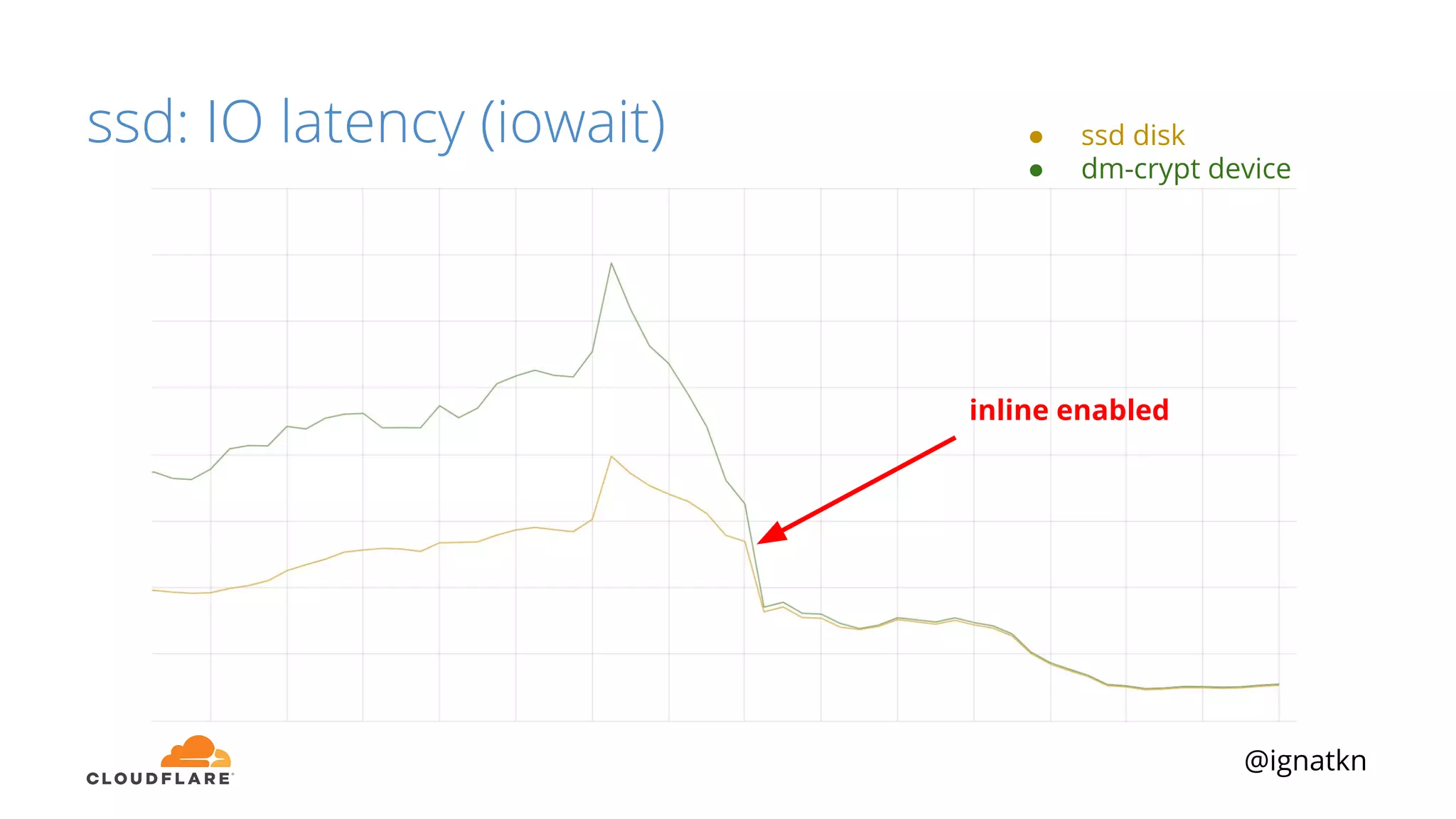
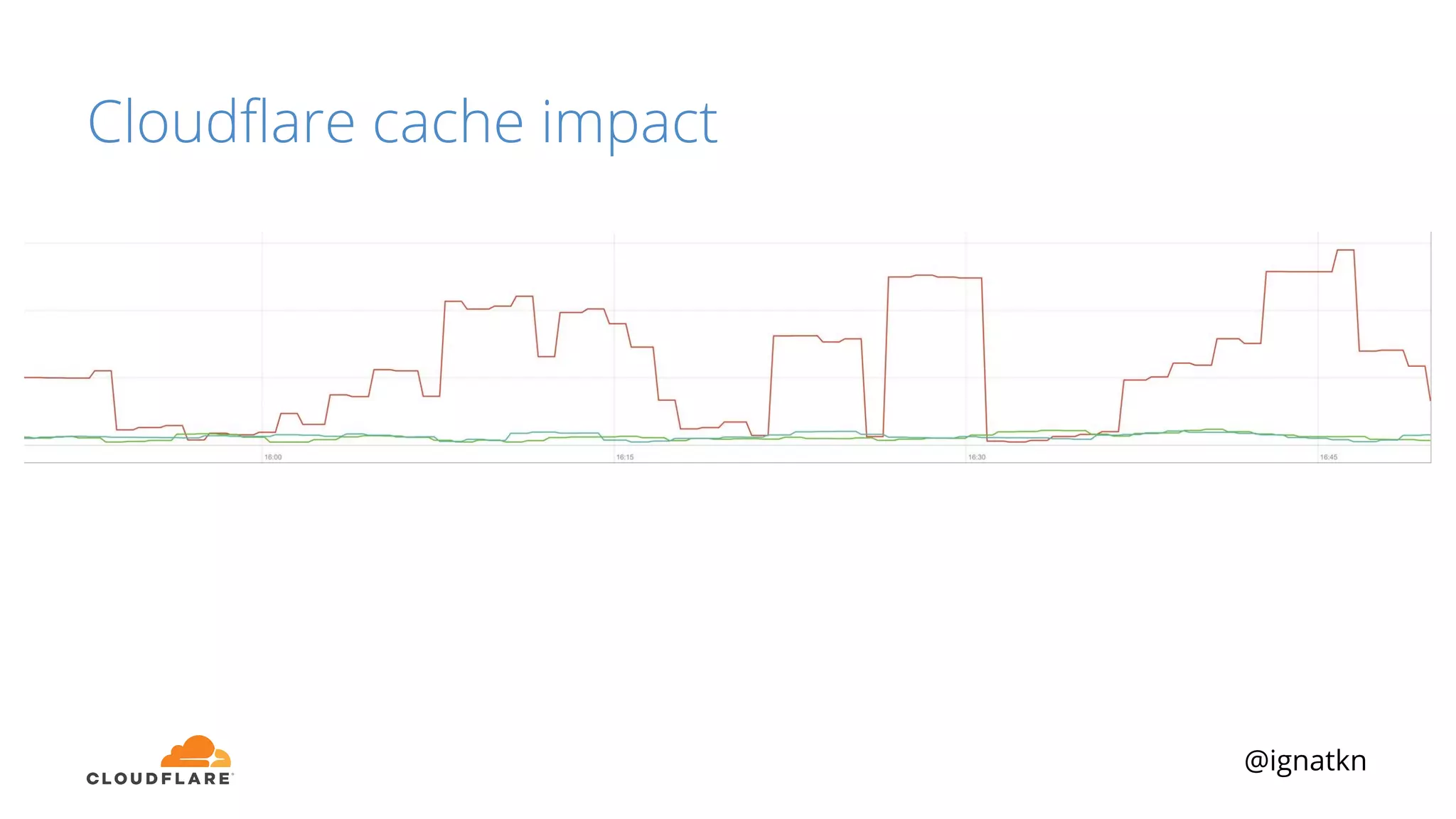
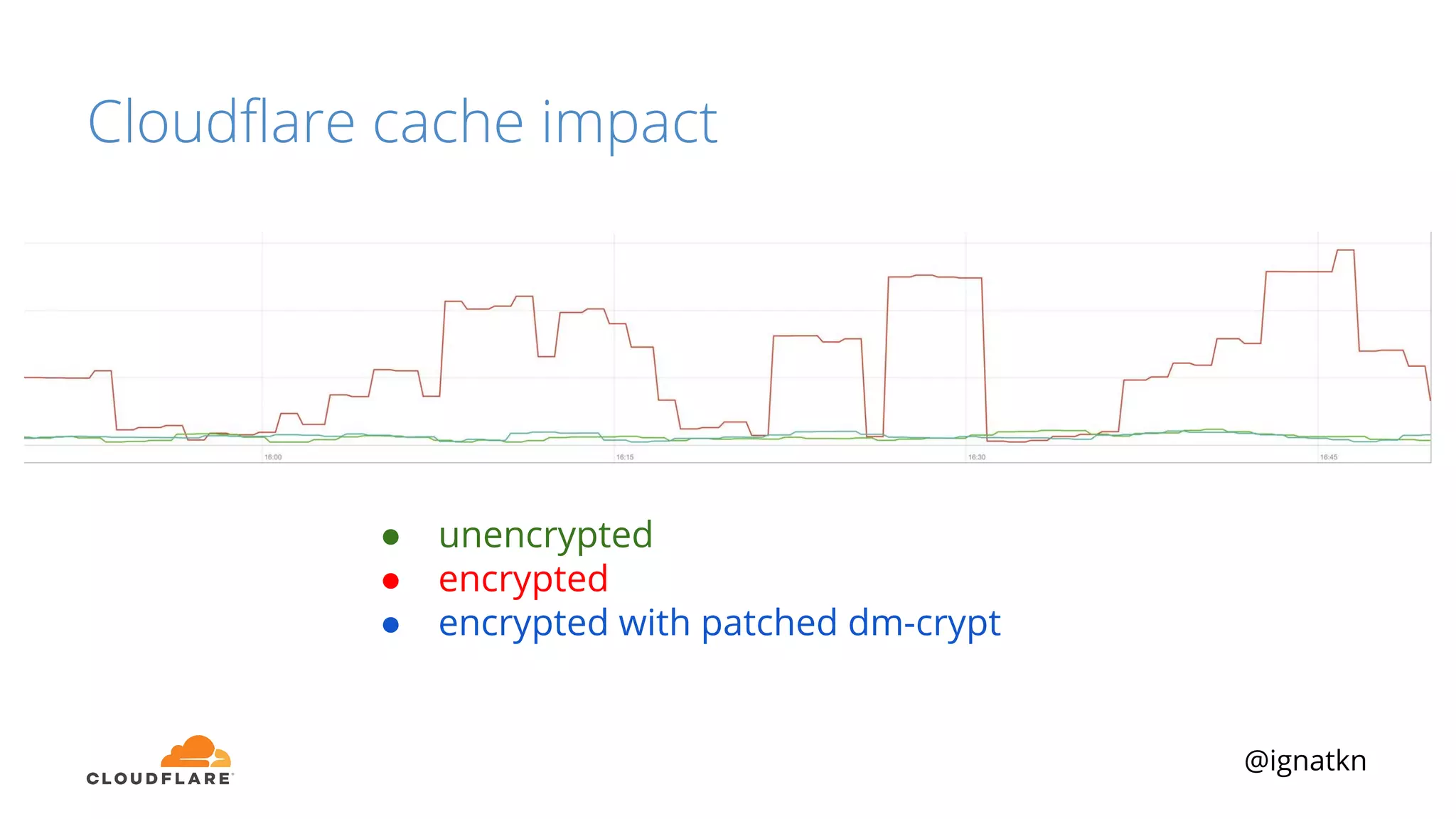
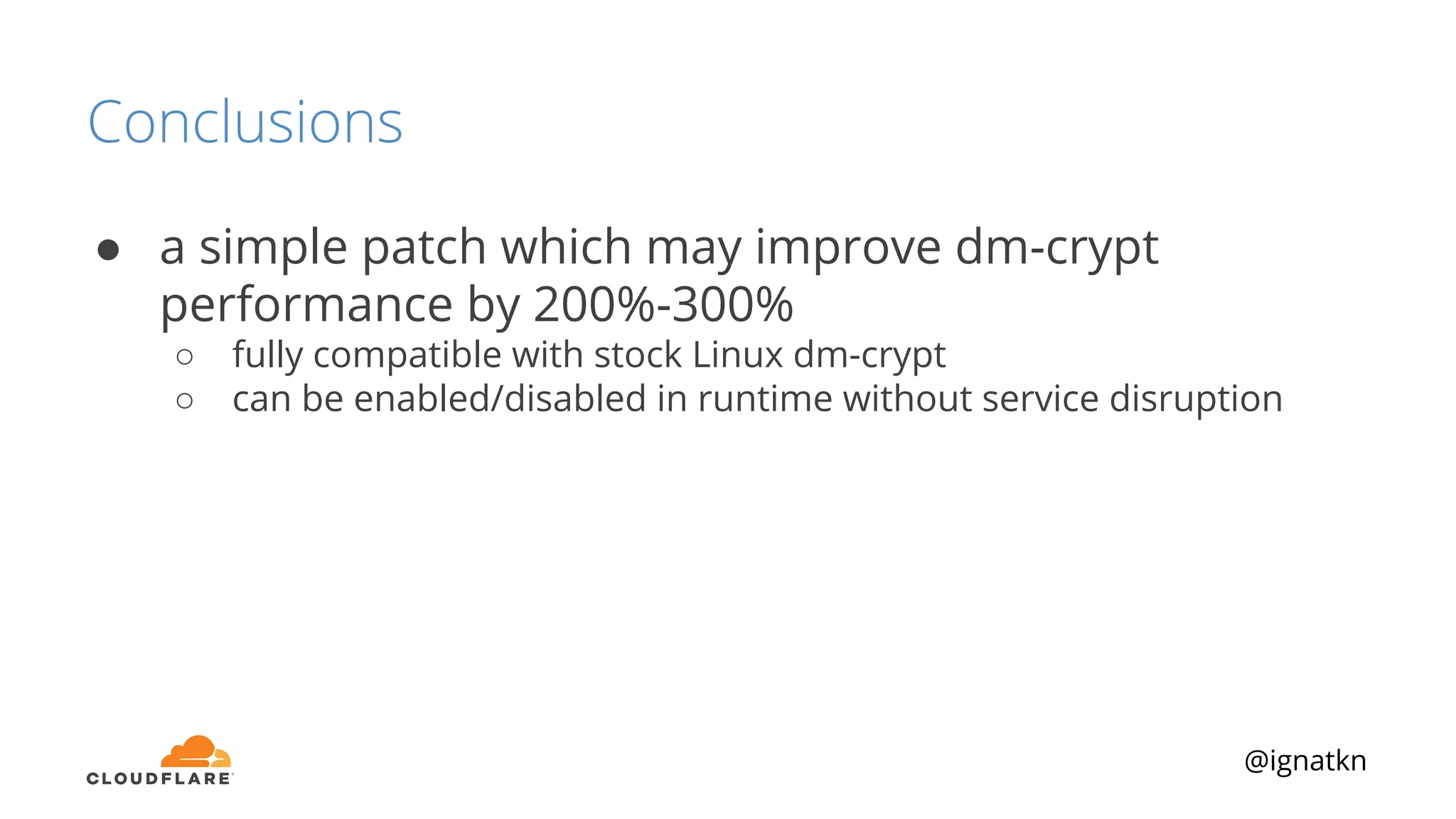
The document discusses methods to improve Linux disk encryption performance while maintaining security, focusing on different layers of encryption like storage hardware, block layer, filesystem layer, and application layer. It highlights the trade-offs between complexity, configuration, and speed for each method and offers insights into real-world testing and potential optimizations including algorithm selection and modifications to the dm-crypt module. The author emphasizes that while encryption can impact performance, modern cryptographic techniques can be efficient, especially with specific implementations like aes-xts.