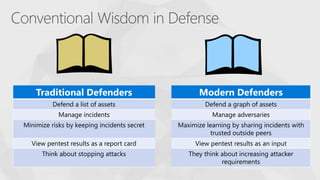
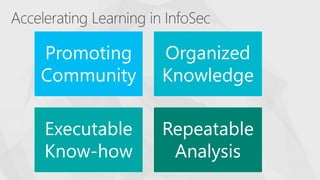
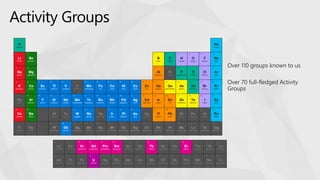
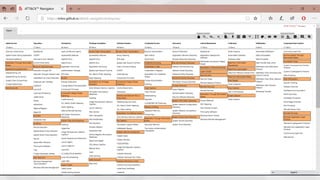
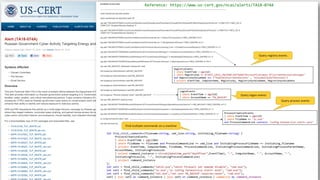
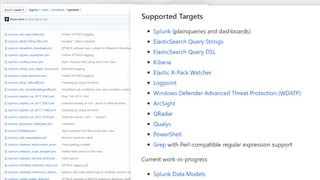
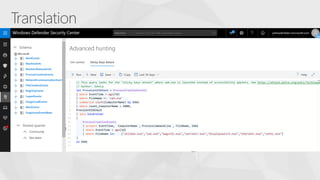
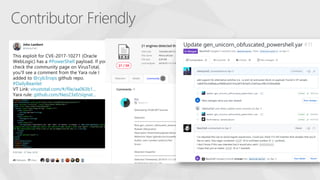
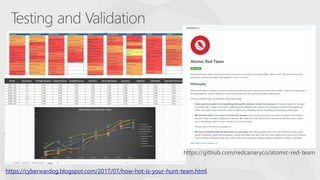
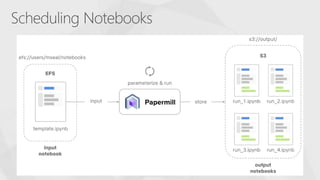
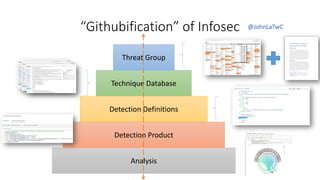
The document contrasts traditional and modern approaches to cybersecurity, emphasizing the shift from incident secrecy to community sharing for enhanced learning. It mentions how modern defenders manage adversaries and view pentesting as a means to increase attack resistance rather than just a report card. Additionally, it lists various elements and their symbols, alongside references to activity groups and resources related to cybersecurity analysis.