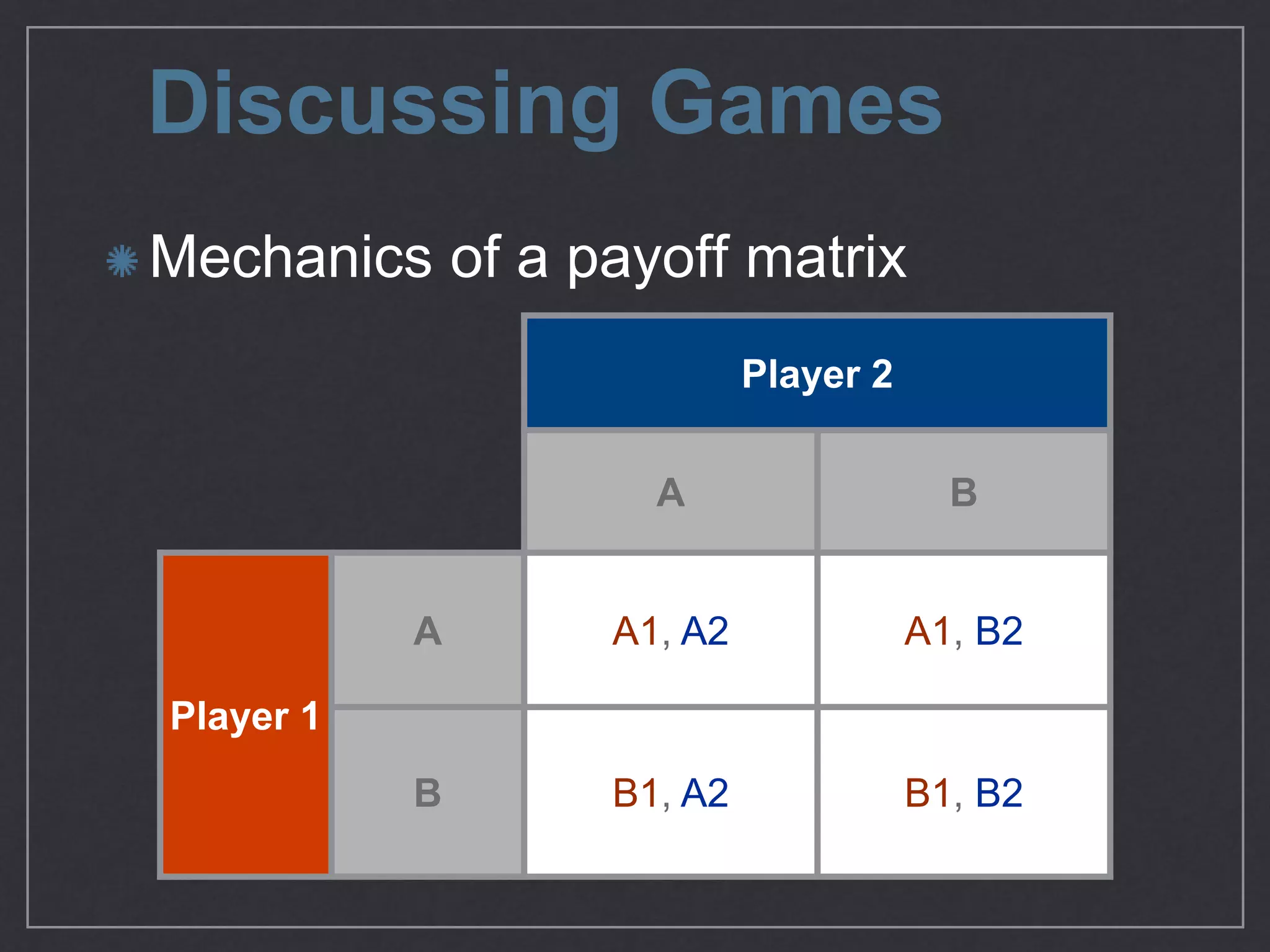
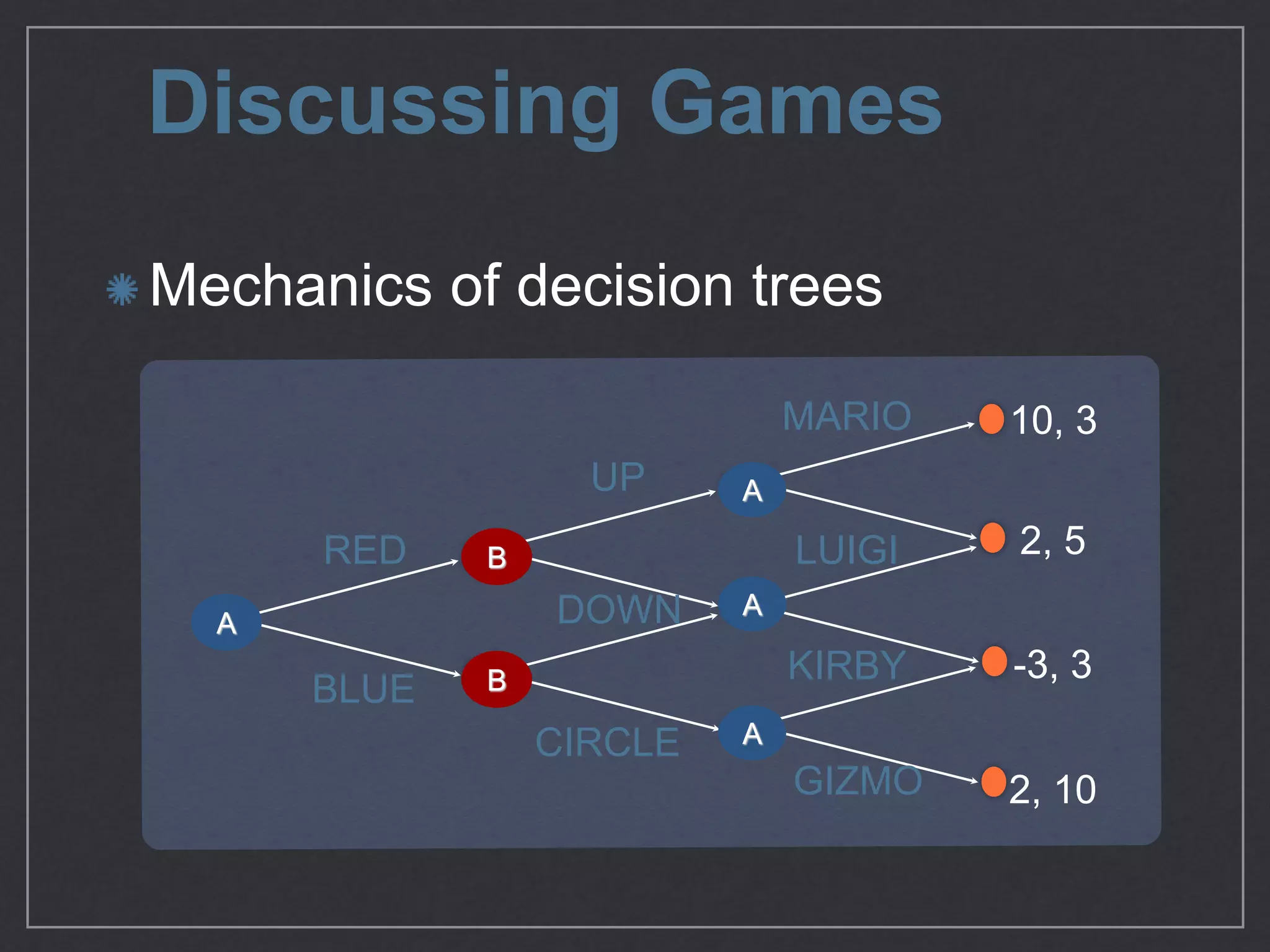
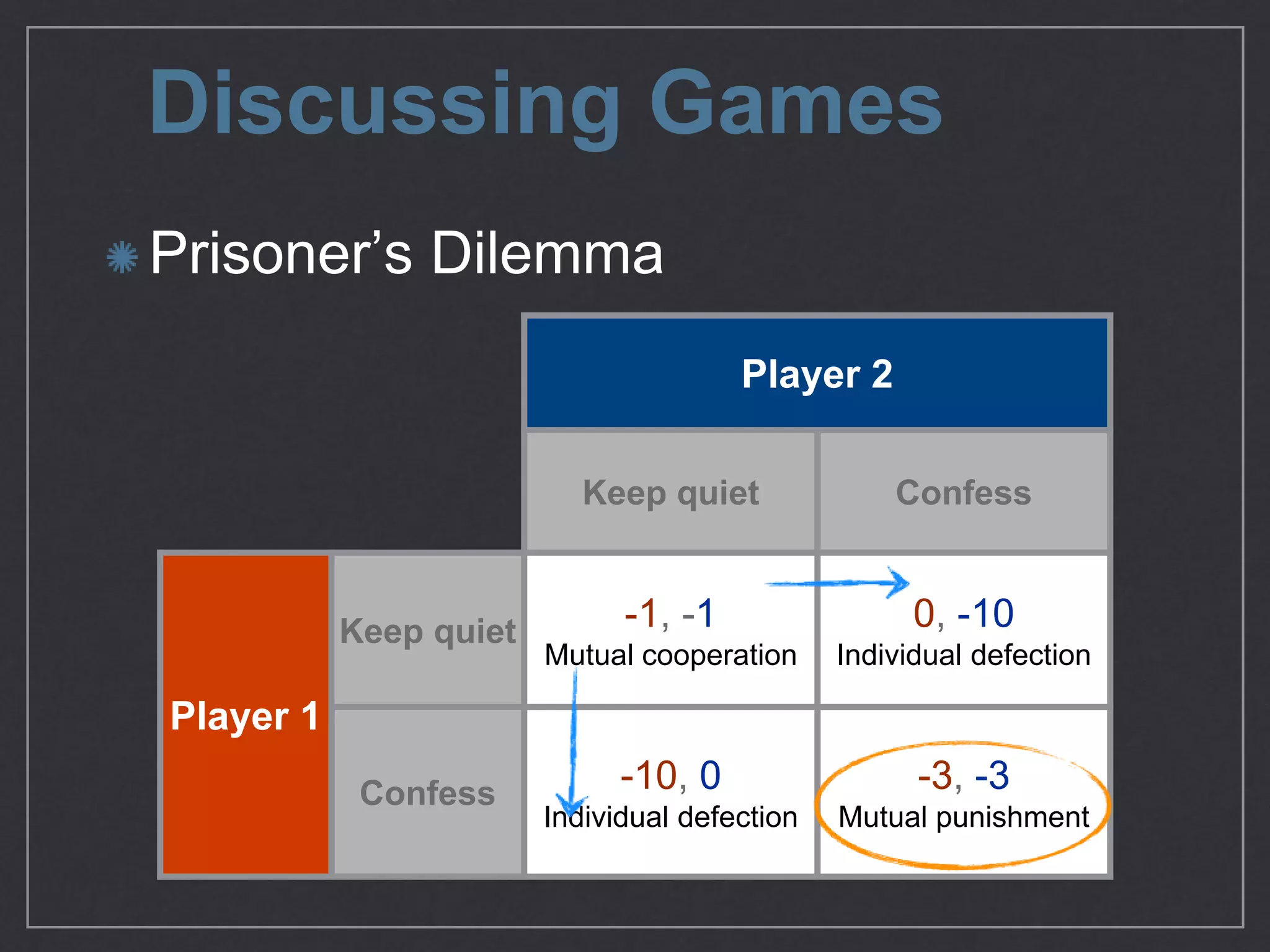
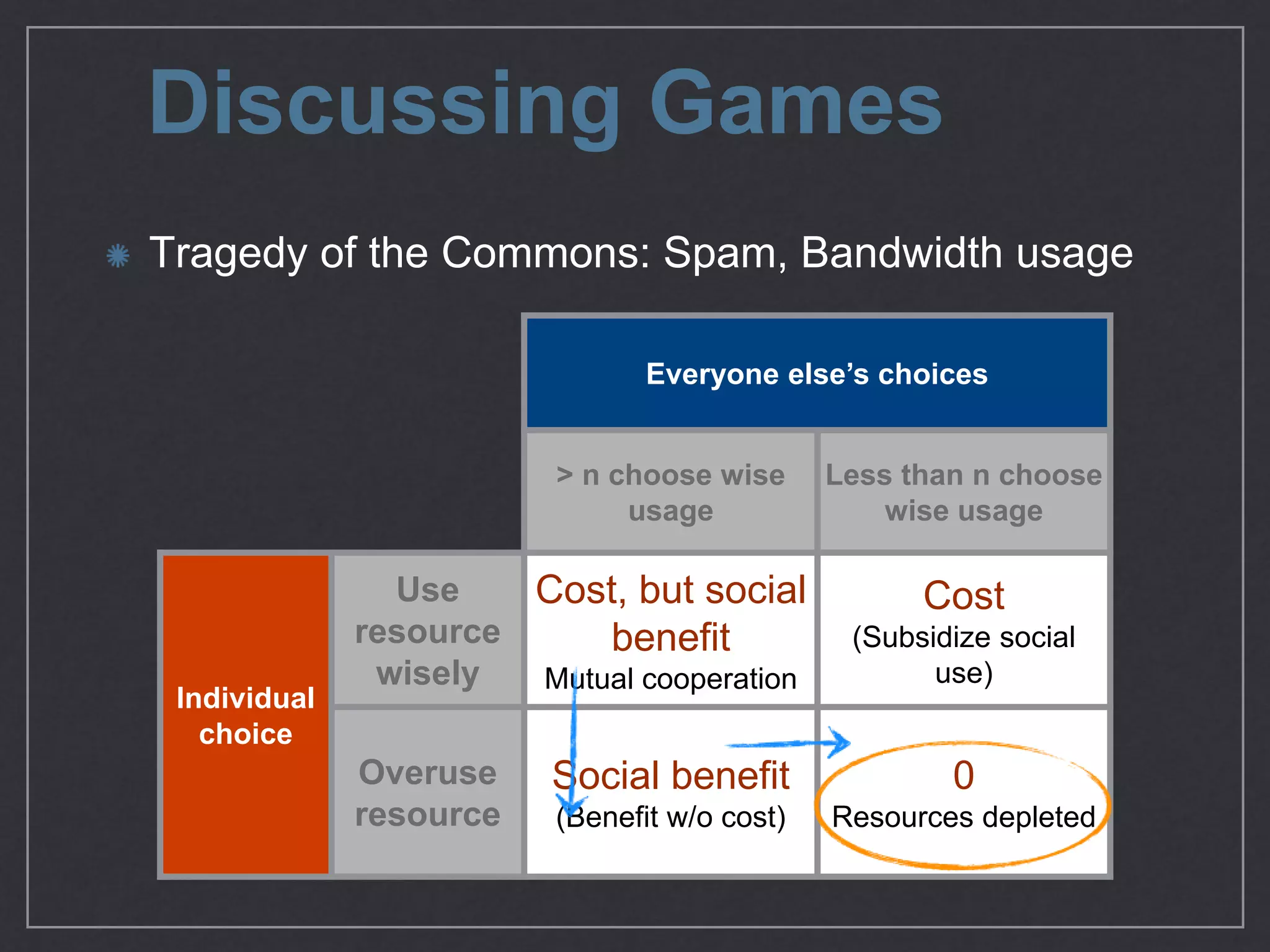
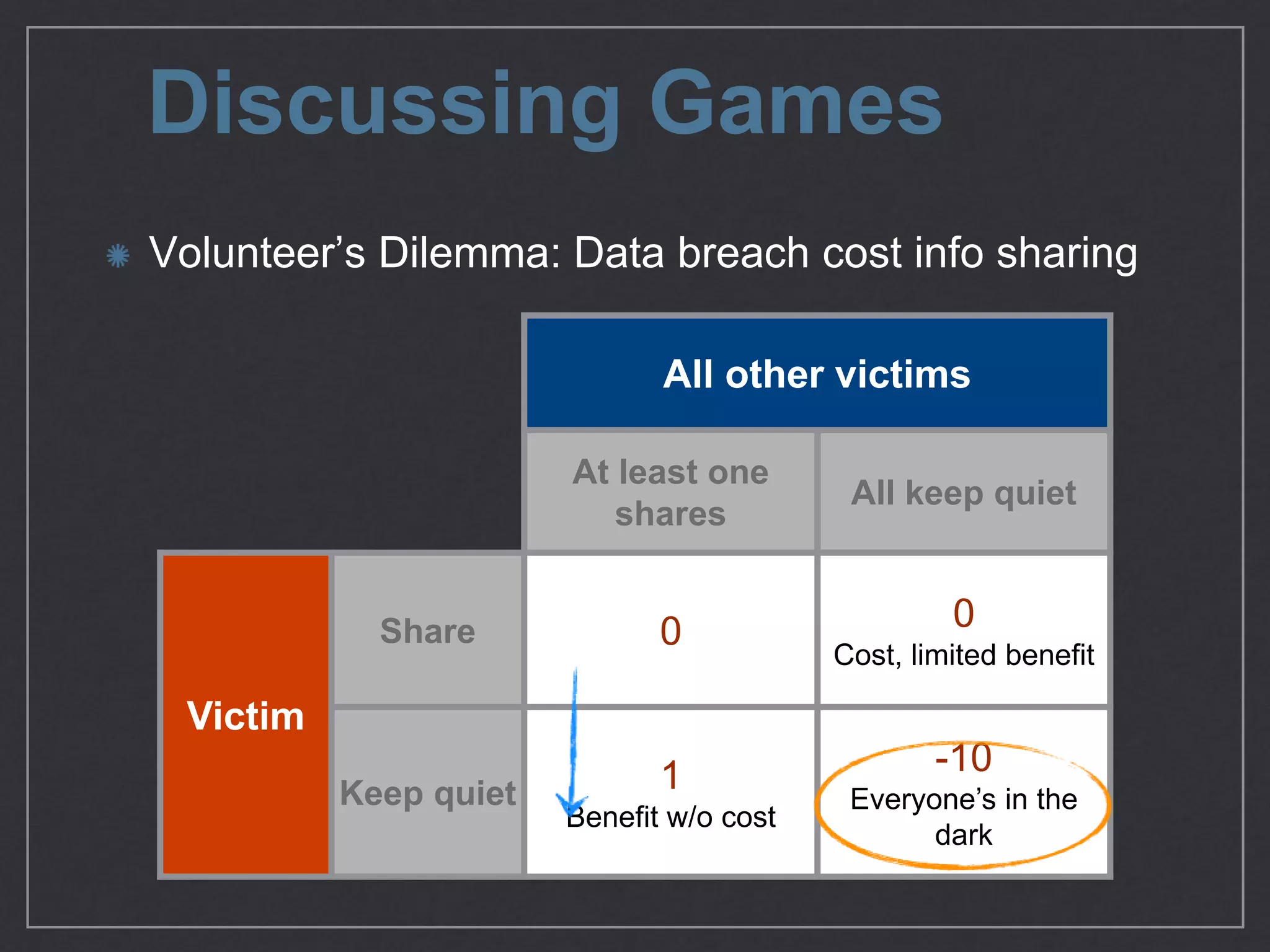
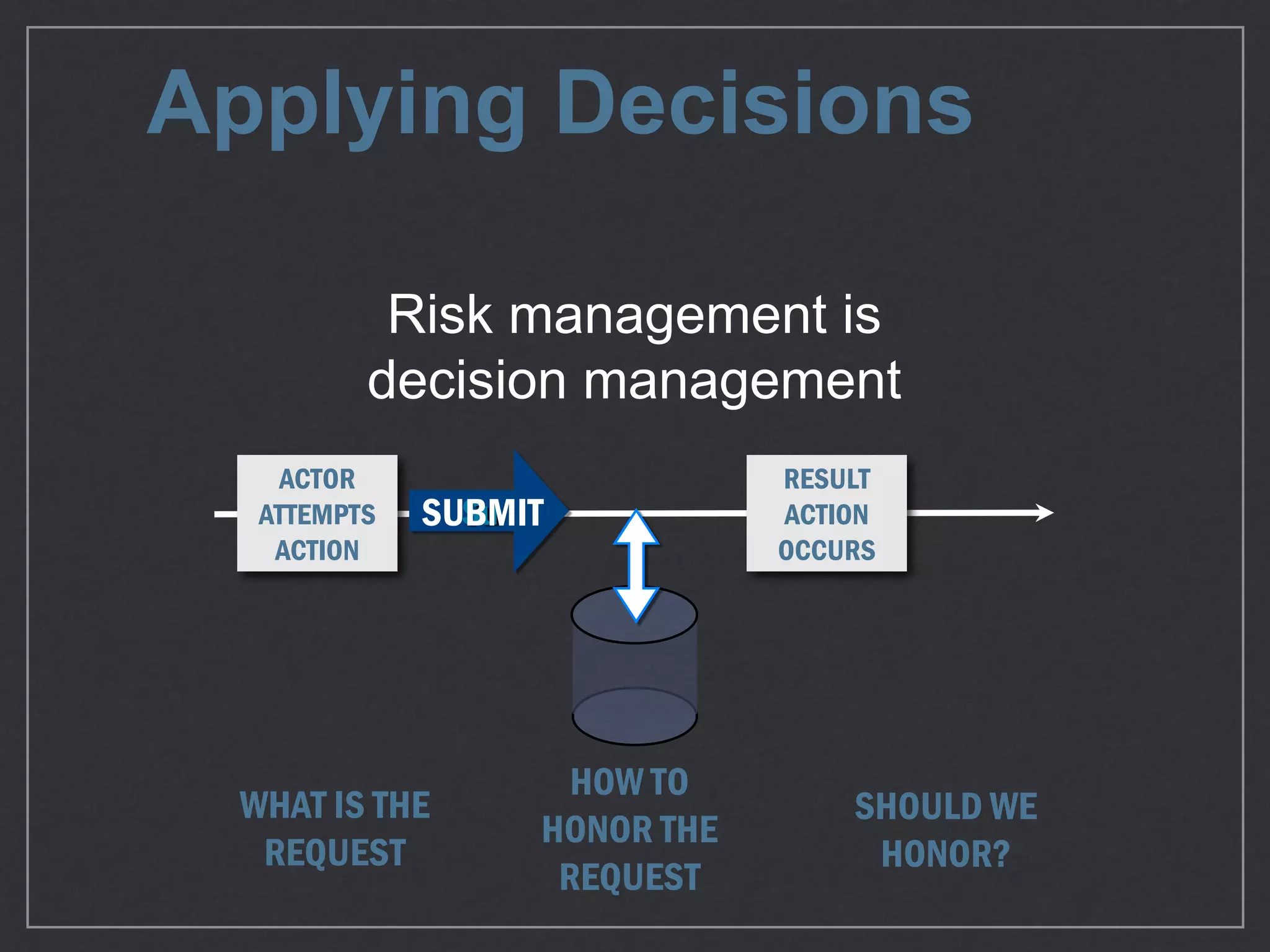
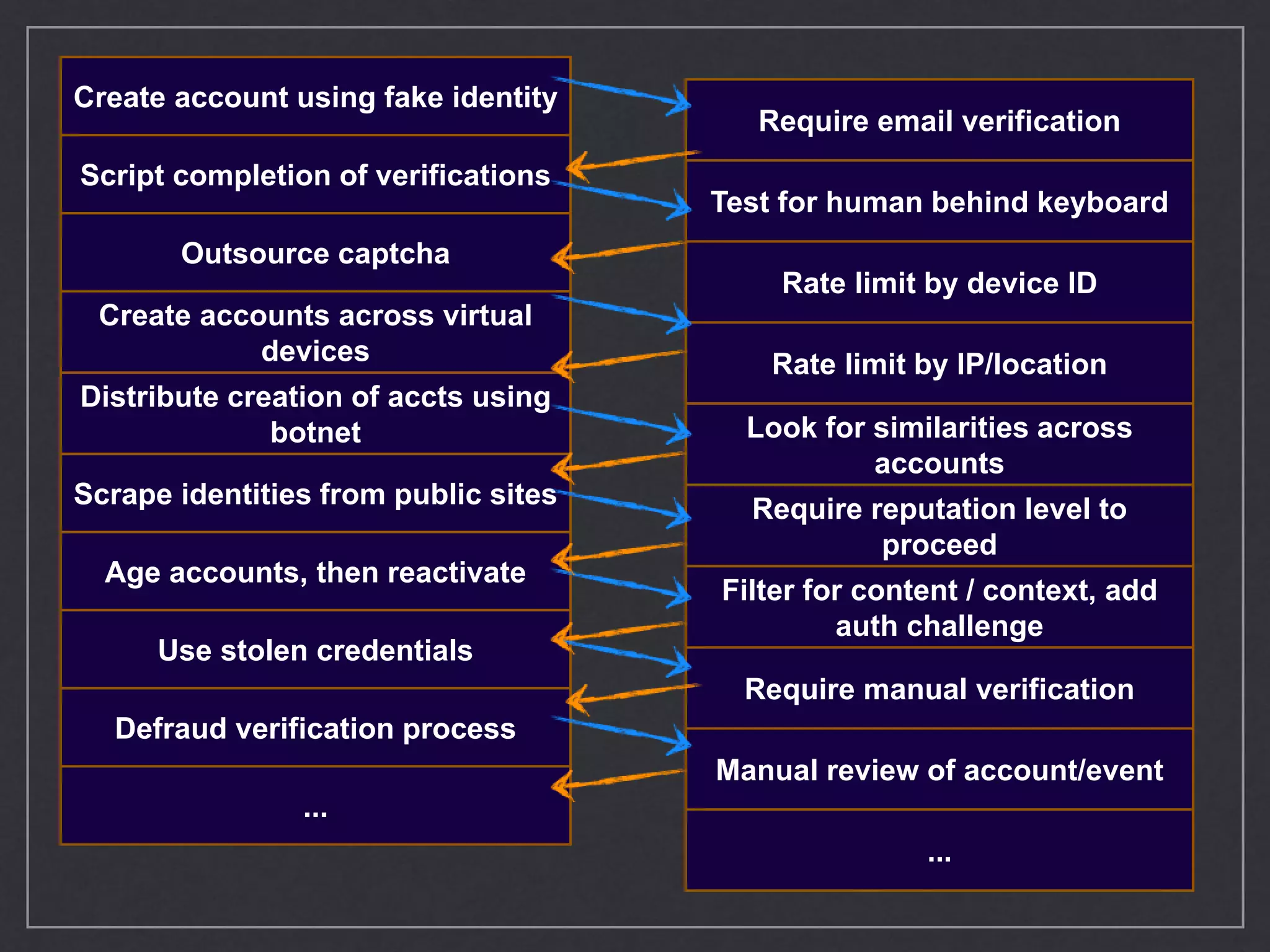
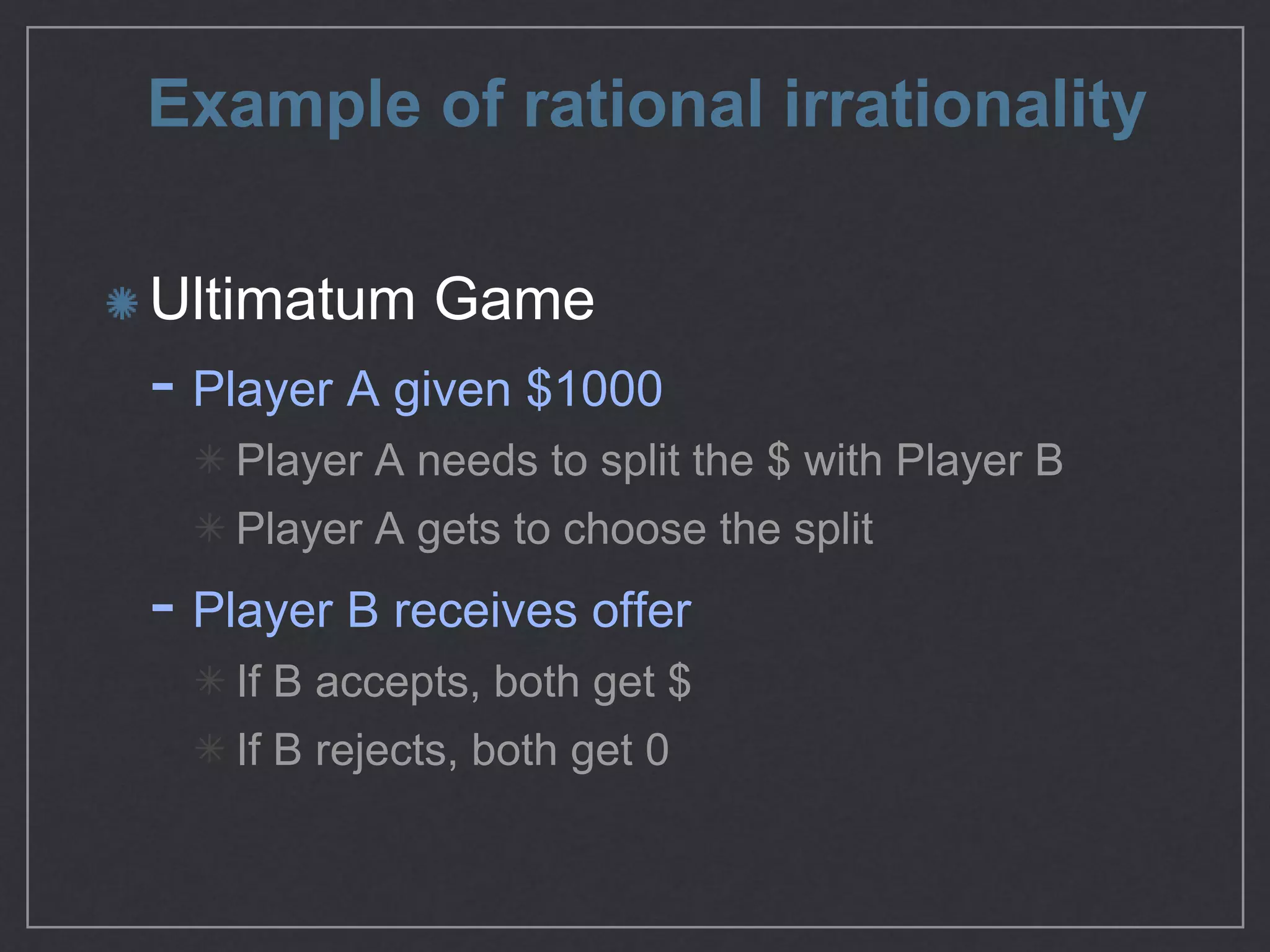
This document provides an overview of game theory concepts and how they can be applied to information security issues. It discusses how security situations can be framed as games with defensive and offensive players making strategic decisions based on potential costs and benefits. Examples of typical game theory models are explained like the Prisoner's Dilemma. The document also notes that real-world behavior may not always match rational models, and that understanding human biases is important for developing effective defense strategies. Overall, it argues that risk management involves managing decisions in a game-like framework where outcomes depend on the choices of multiple players.