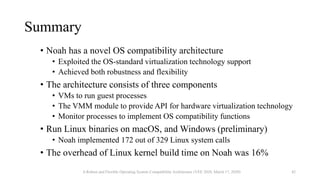
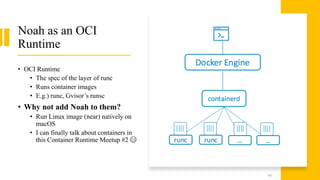
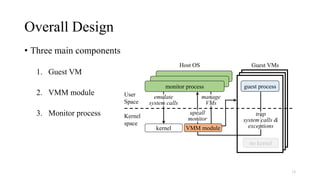
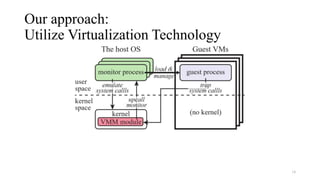
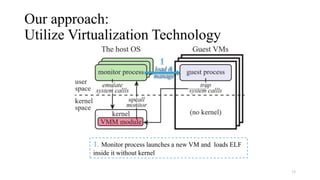
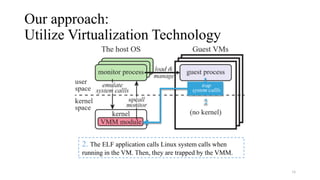
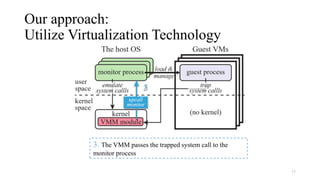
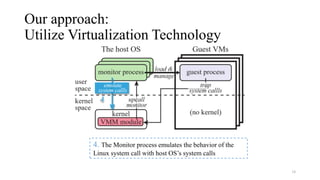
Noah is a user-space Linux compatibility layer for macOS that utilizes virtualization technology to run Linux applications without a kernel, ensuring both robustness and flexibility. The architecture consists of components such as guest virtual machines, a virtual machine monitor (VMM), and monitor processes that emulate Linux system calls. Noah has demonstrated the ability to implement a large portion of the Linux ABI and serves as an OCI runtime for more seamless container management on macOS.








![Noah’s OS Compatibility Architecture
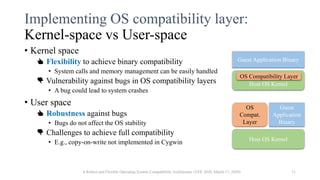
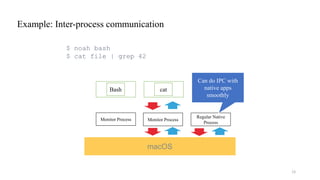
• Running each guest process in a VM (without its OS kernel)
👍 Robustness
• Most part of OS compatibility layers can be implemented in user space
• Bugs do not cause kernel crashes
👍 Flexibility
• Hardware virtualization technology provides low-layer event handling functionalities
• E.g., trapping system calls and page faults, manipulating page tables, …
12
Host OS Kernel
OS Compatibility Layer
VMHost Process
Standardized Virtualization Interface
Guest Application Process
CPUHardware Virtualization Function
⇒ Published as papers for its academic novelty
[T.Saeki, Y.Nishiwaki, T.Shinagawa, S.Honiden]
• A robust and flexible operating system compatibility architecture,
in VEE 2020
• Bash on Ubuntu on macOS, in APSys 2017](https://image.slidesharecdn.com/slides-200822030350/85/Noah-Robust-and-Flexible-Operating-System-Compatibility-Architecture-Container-runtime-meetup-2-12-320.jpg)
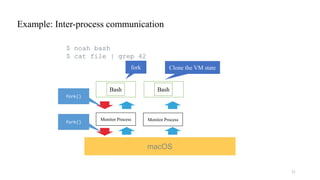
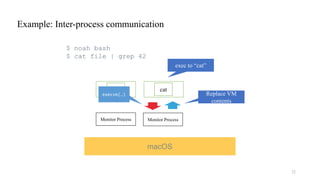
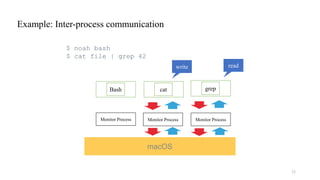







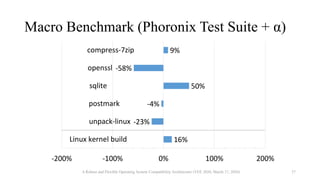
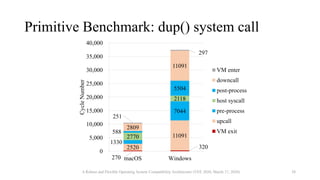
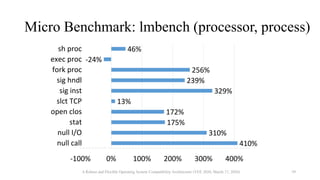
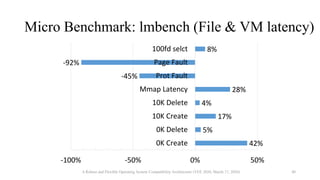
![Comparison of OS Compatibility Layers
Benchmark NoahW Cygwin WSL1
dup2() [call per second] 36,723 556,453 693,309
write() [call per second] 0.30 0.56 0.57
fork() (0 MiB array) [ms] 106.4 219.4 2.06
fork() (512 MiB array) [ms] 338.9 789.9 32.51
fork() (1 GiB array) [ms] 458.4 1531.8 62.66
A Robust and Flexible Operating System Compatibility Architecture (VEE 2020, March 17, 2020) 41](https://image.slidesharecdn.com/slides-200822030350/85/Noah-Robust-and-Flexible-Operating-System-Compatibility-Architecture-Container-runtime-meetup-2-39-320.jpg)