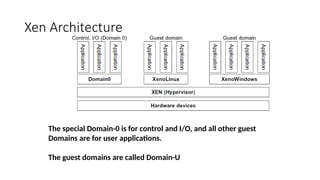
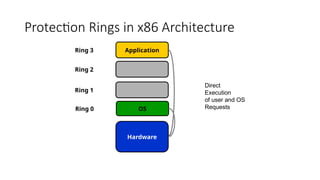
The document outlines the architecture of cloud computing, detailing the three layers: virtual servers, virtual appliances, and user interfaces/APIs, as well as central concepts like load balancing and virtualization. It describes the different types of hypervisors, virtualization methods (full virtualization, para-virtualization, hardware-assisted), and explores the benefits of cloud scaling, both vertical and horizontal. Additionally, the document highlights the advantages and disadvantages of various virtualization techniques and cloud scaling strategies for optimizing resource performance and managing workloads.