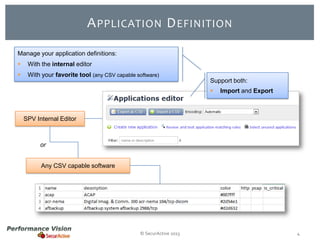
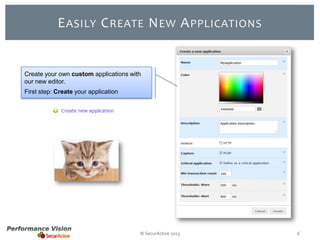
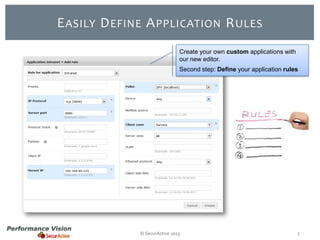
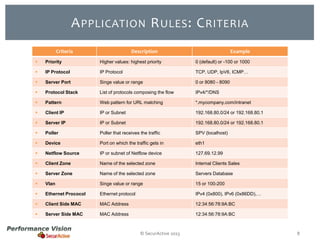
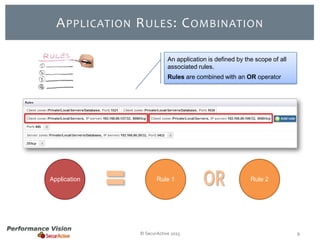
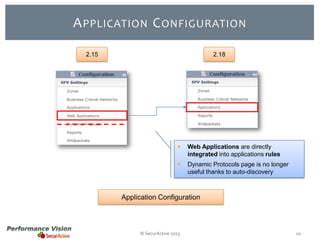
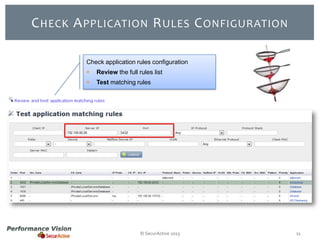
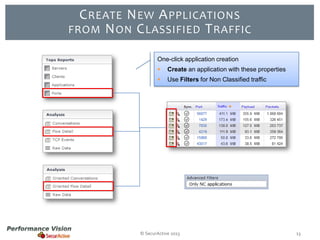
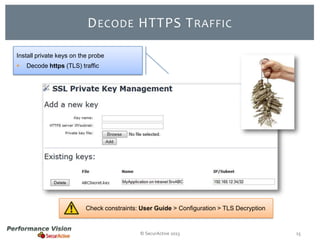
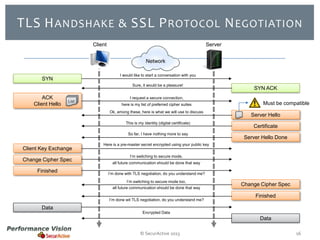
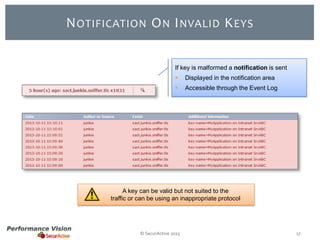
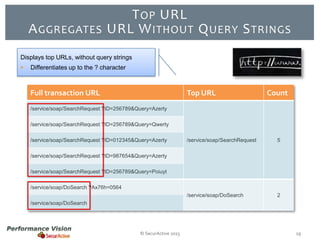
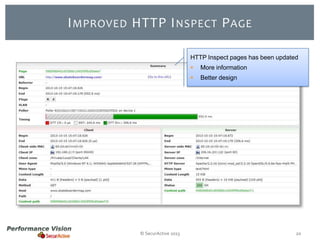
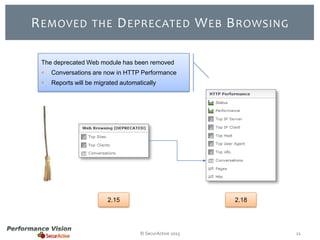
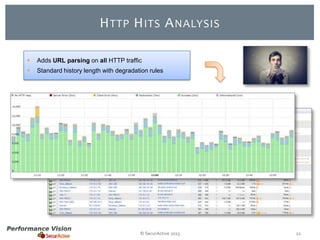
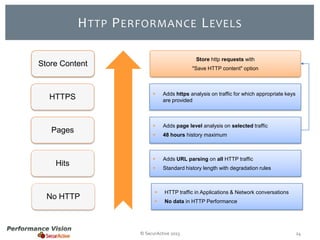
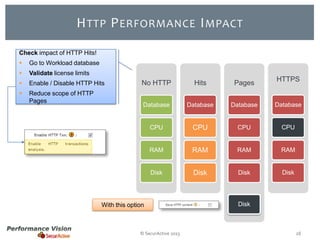
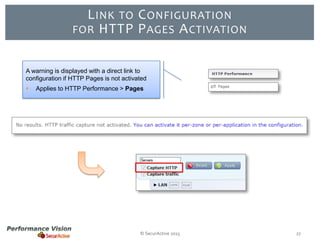
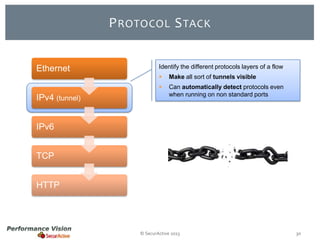
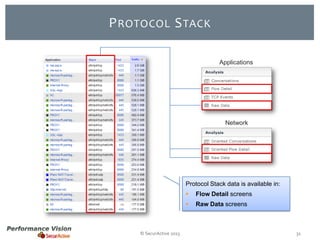
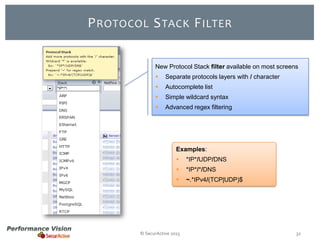
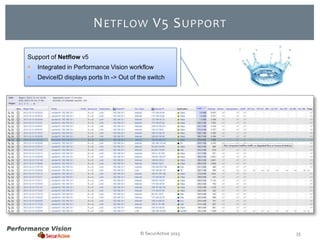
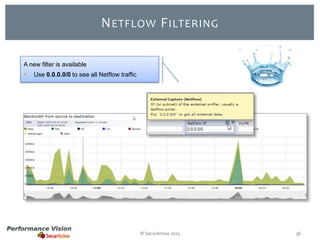
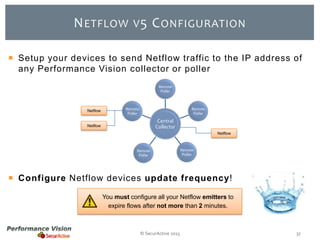
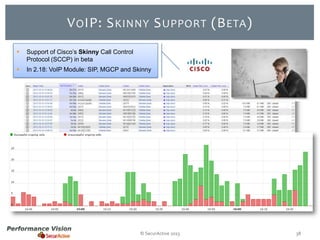
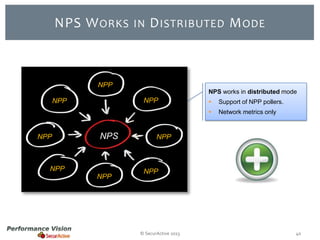
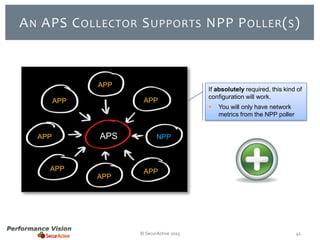
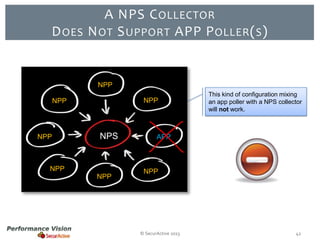
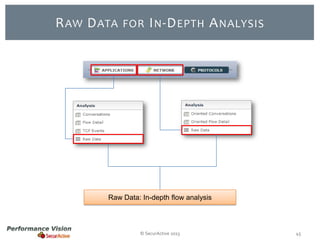
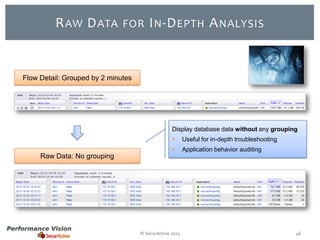
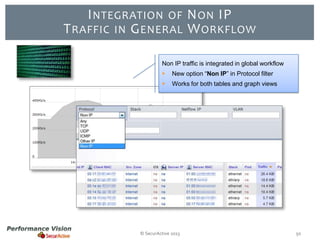
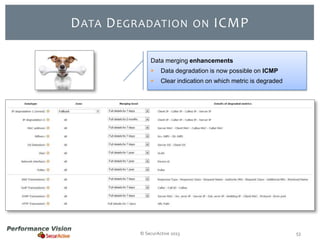
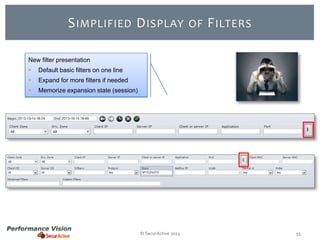
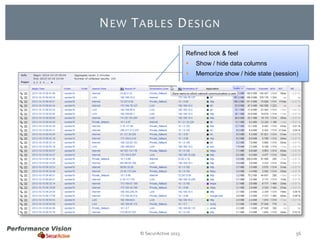
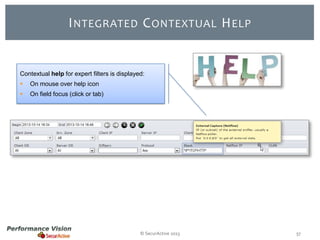
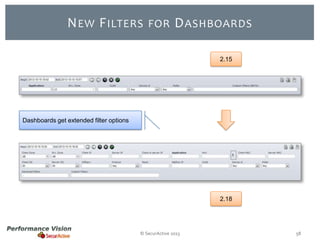
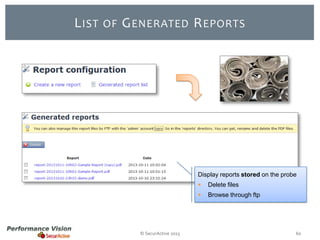
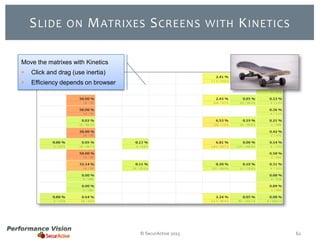
The document provides an overview of new features and improvements in Performance Vision version 2.18. Key updates include improved application definition and rules, protocol stack analysis showing layered protocols, support for Netflow v5 and Skinny protocols, enhanced HTTP analysis and filtering, and performance optimizations. Flexibility is increased through an enterprise licensing agreement allowing custom allocation of credits to licenses.