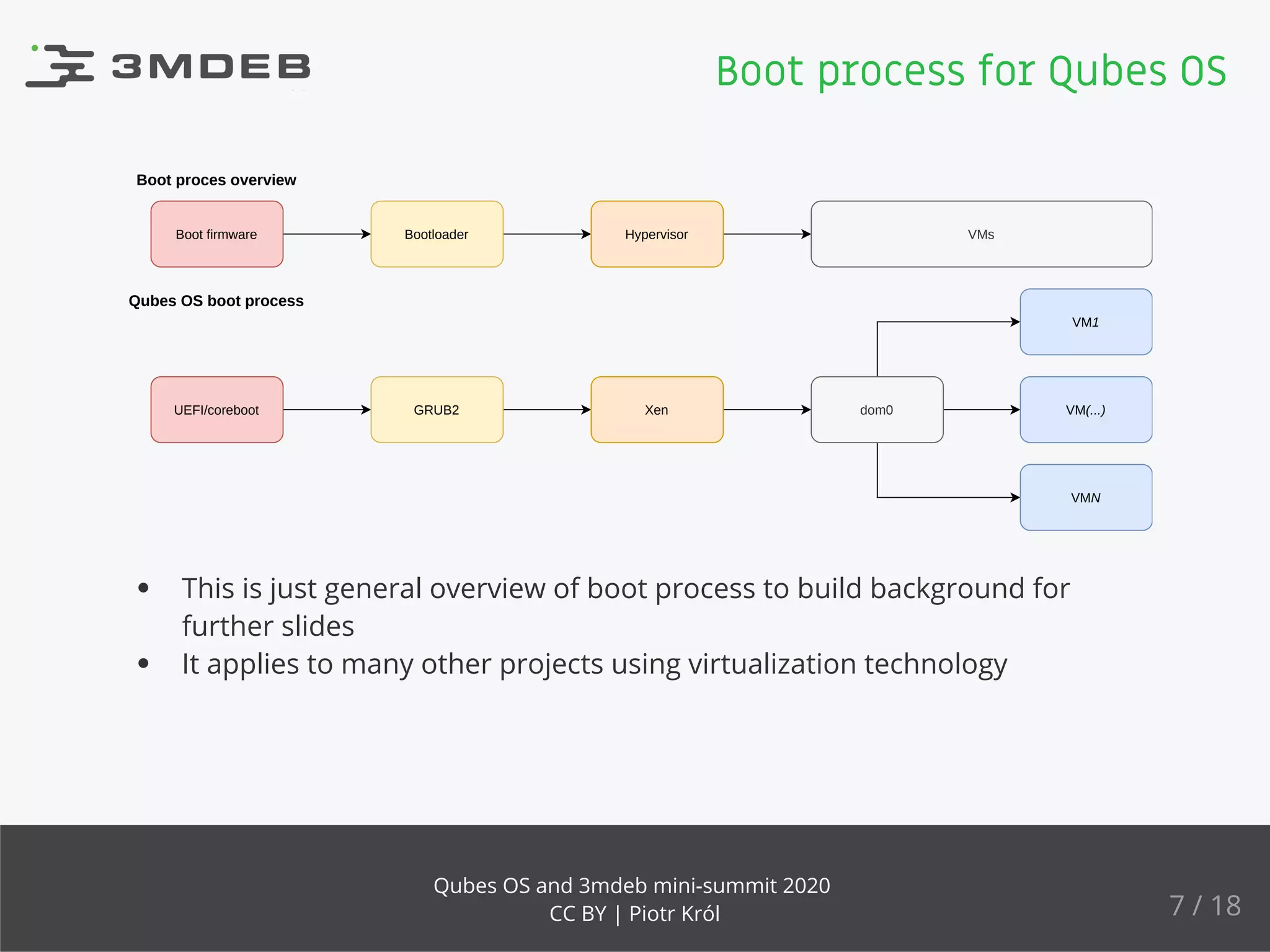
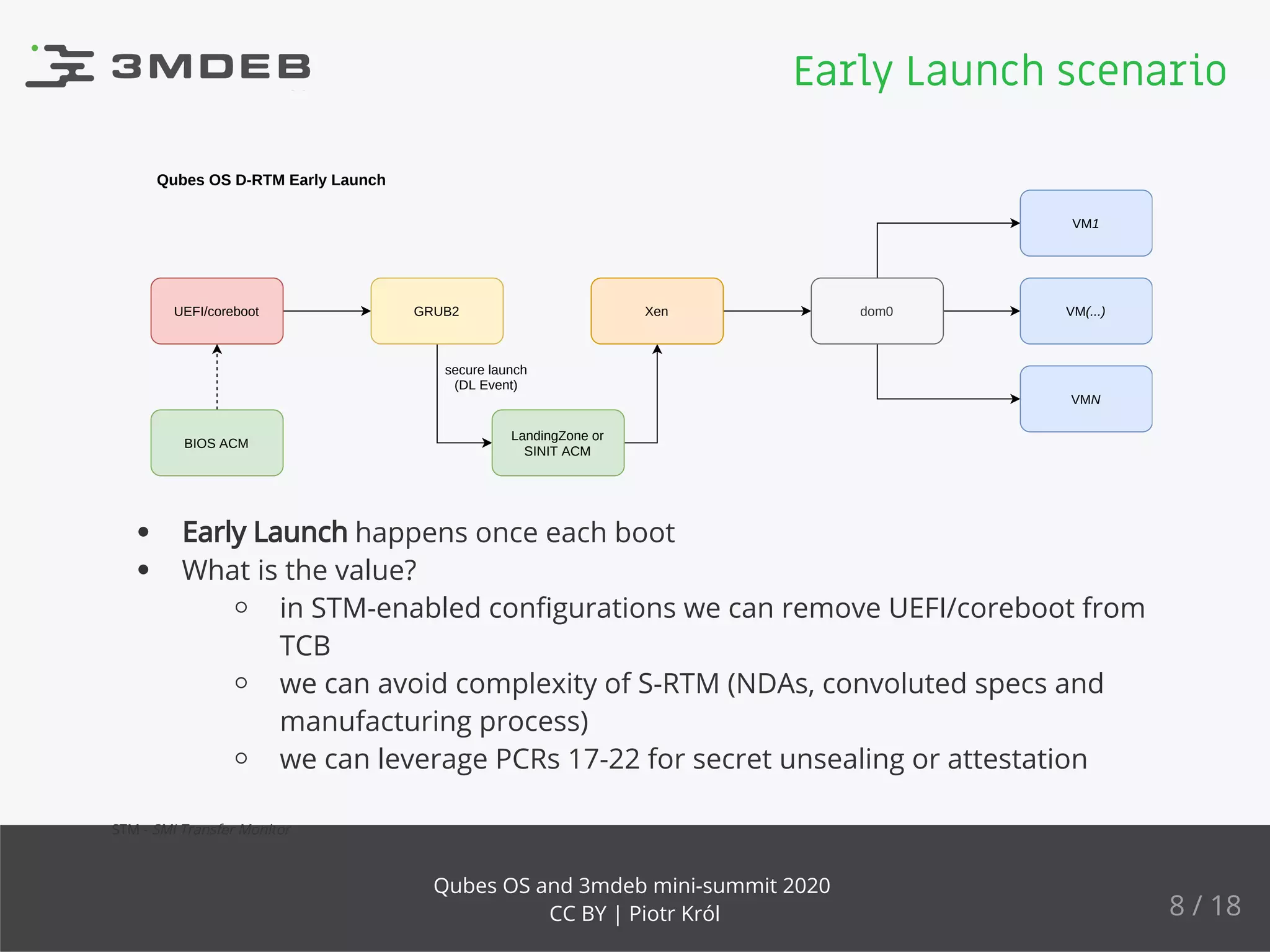
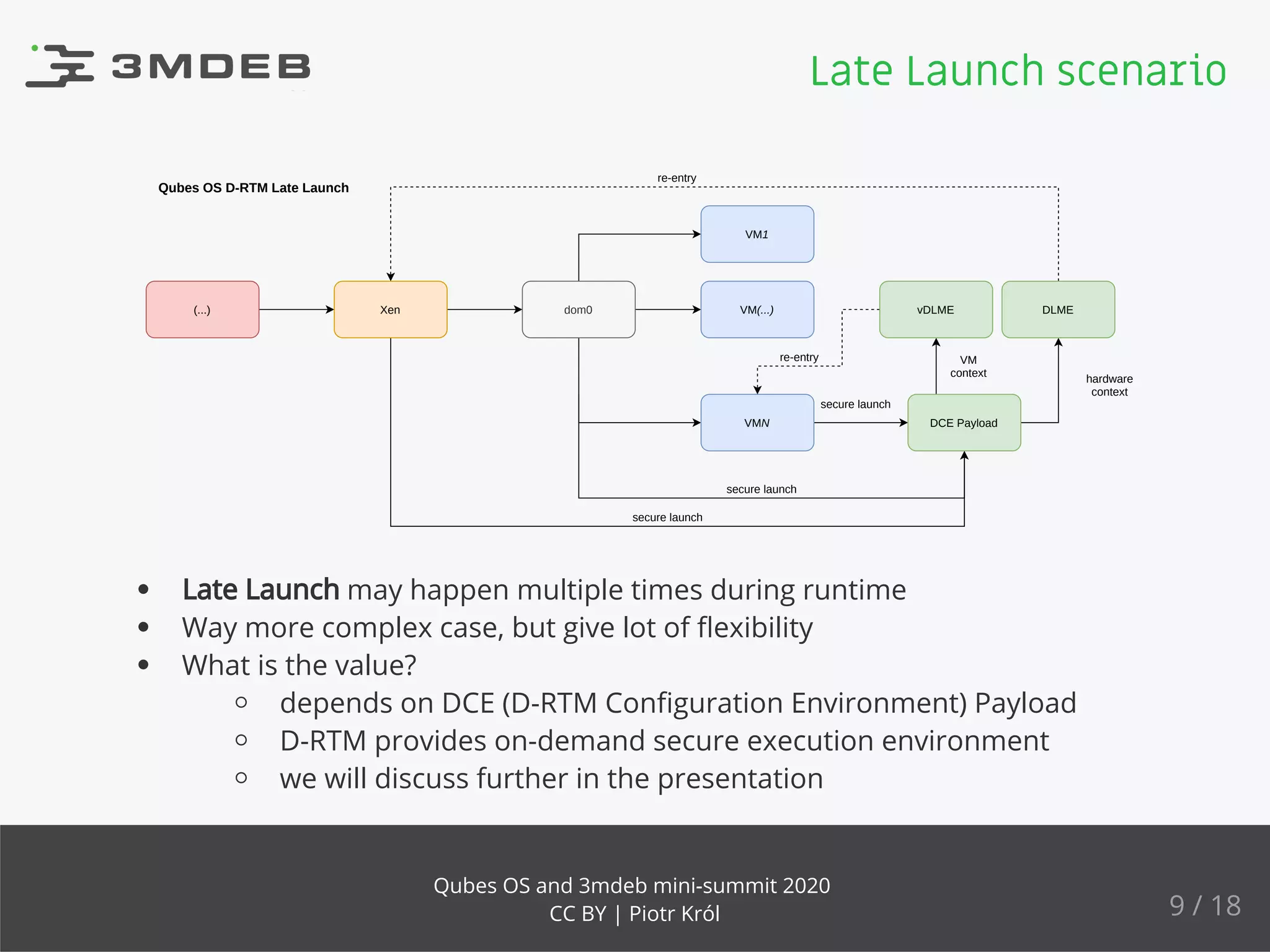
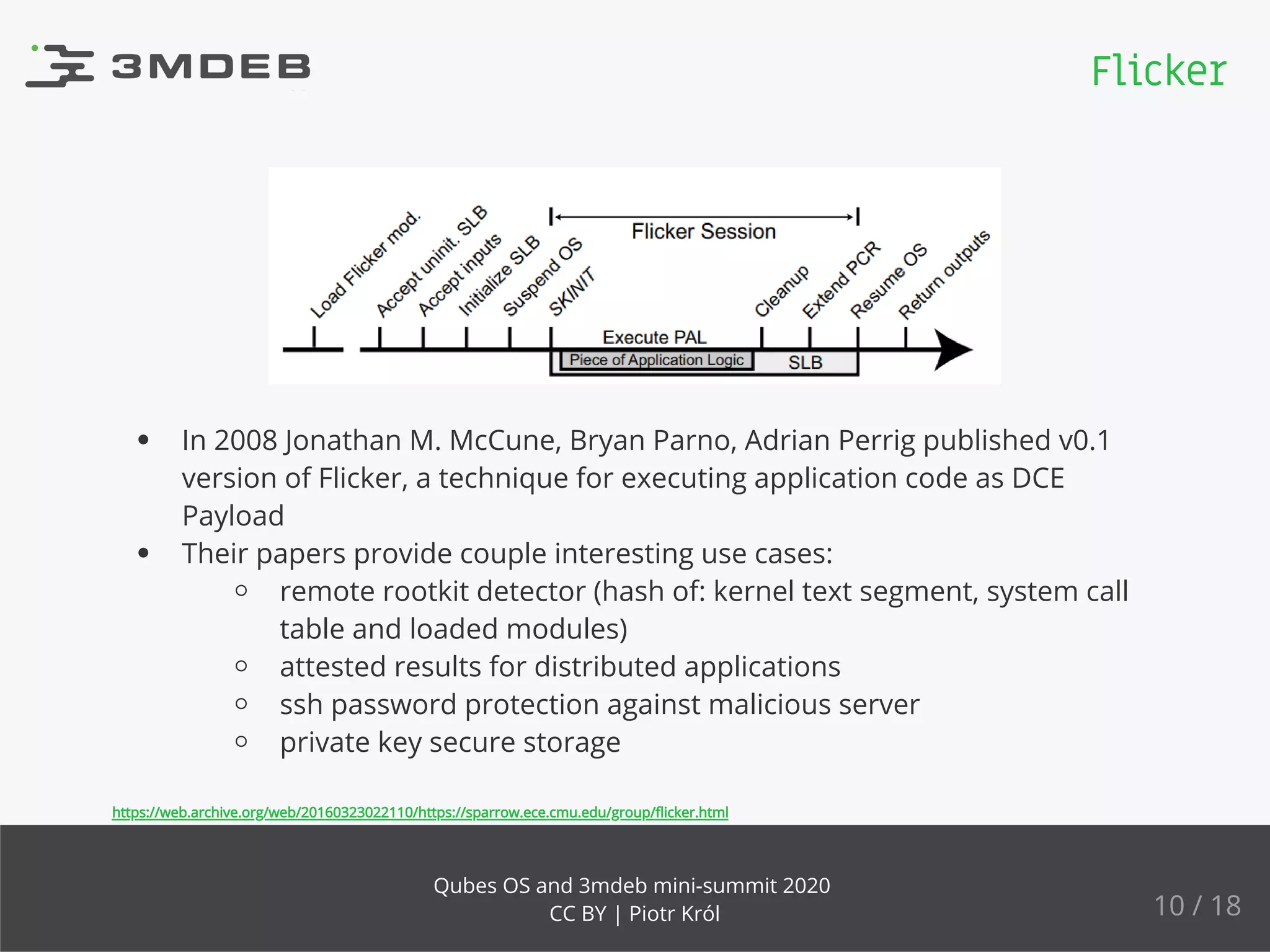
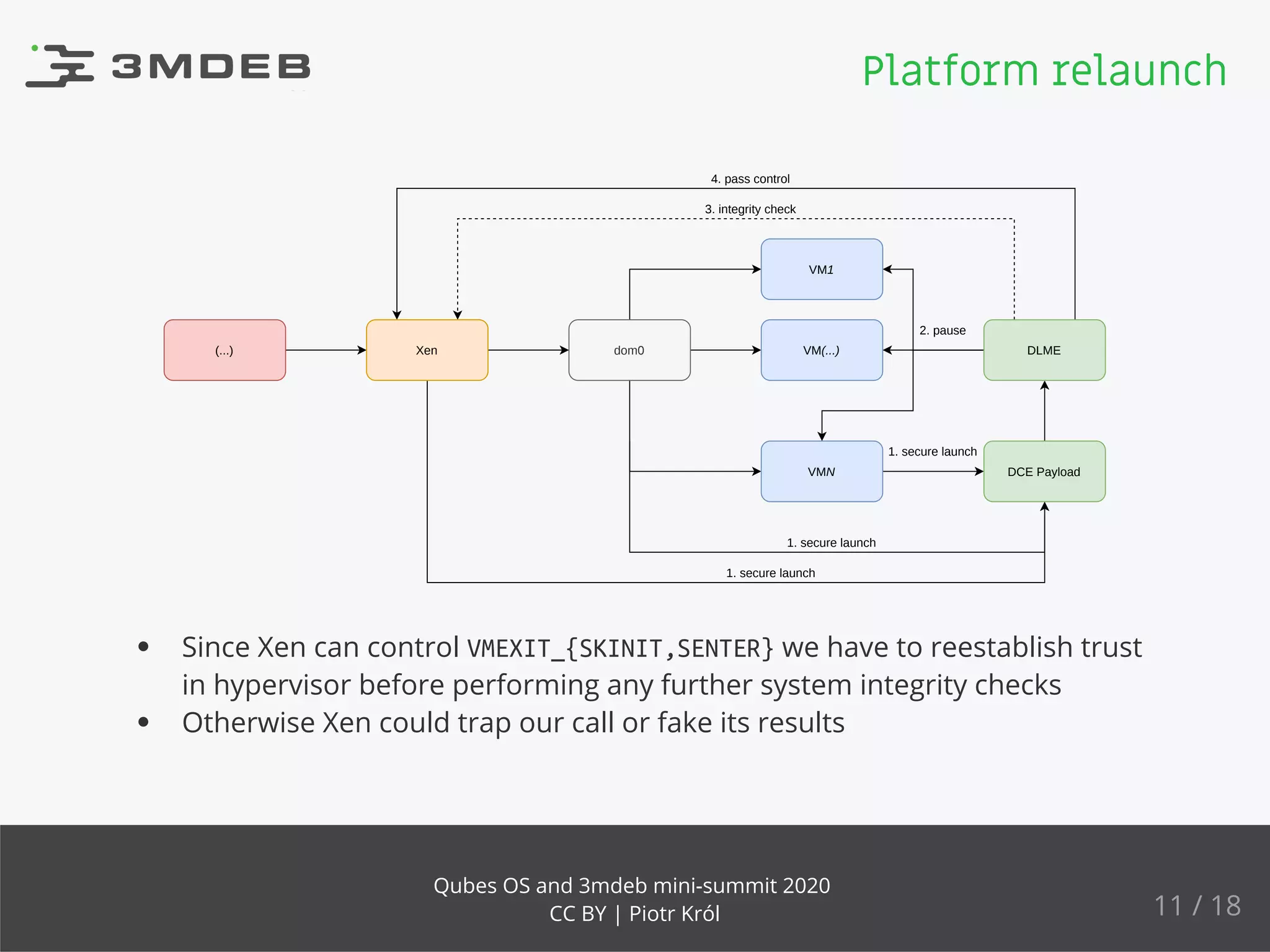
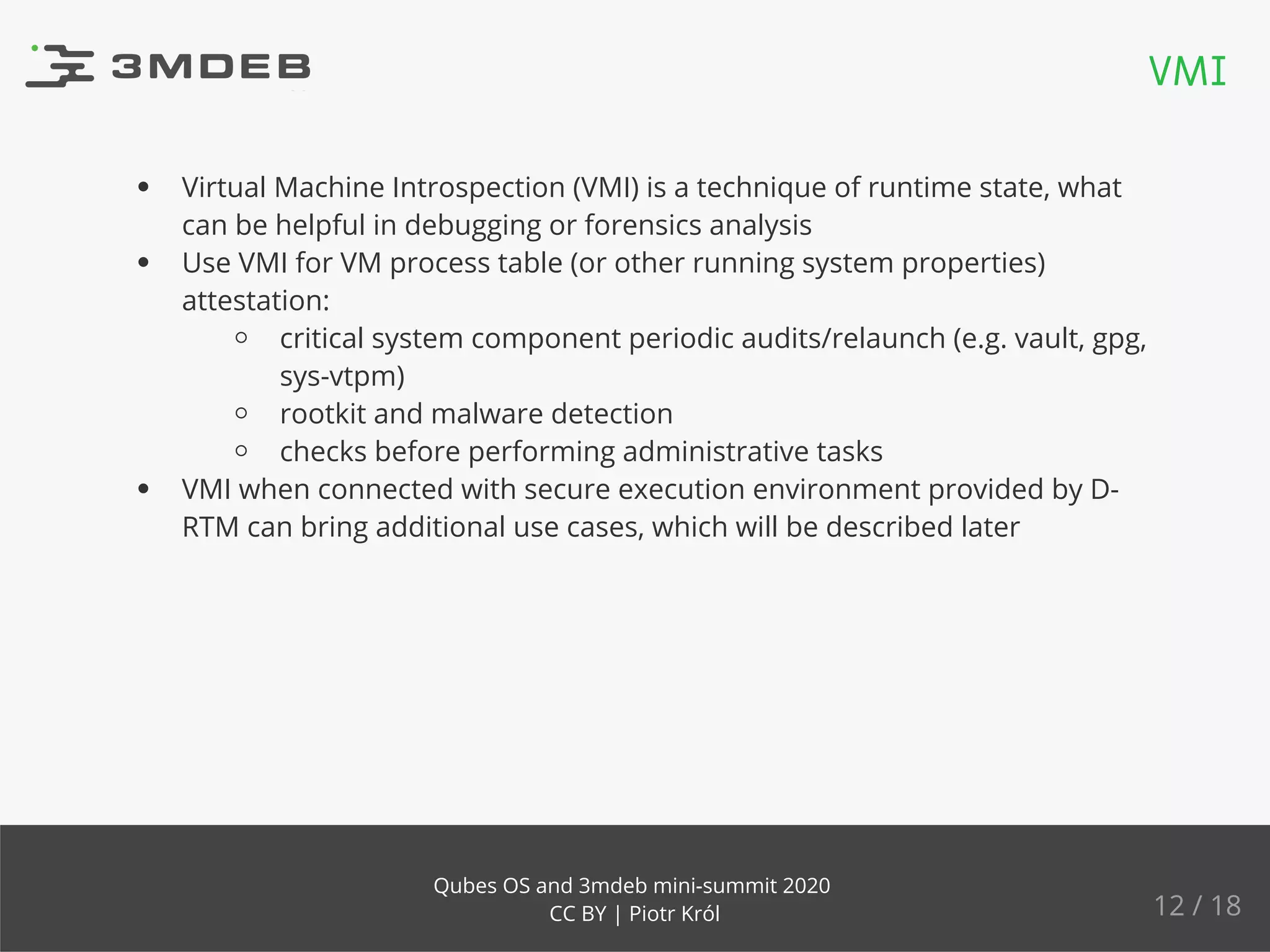
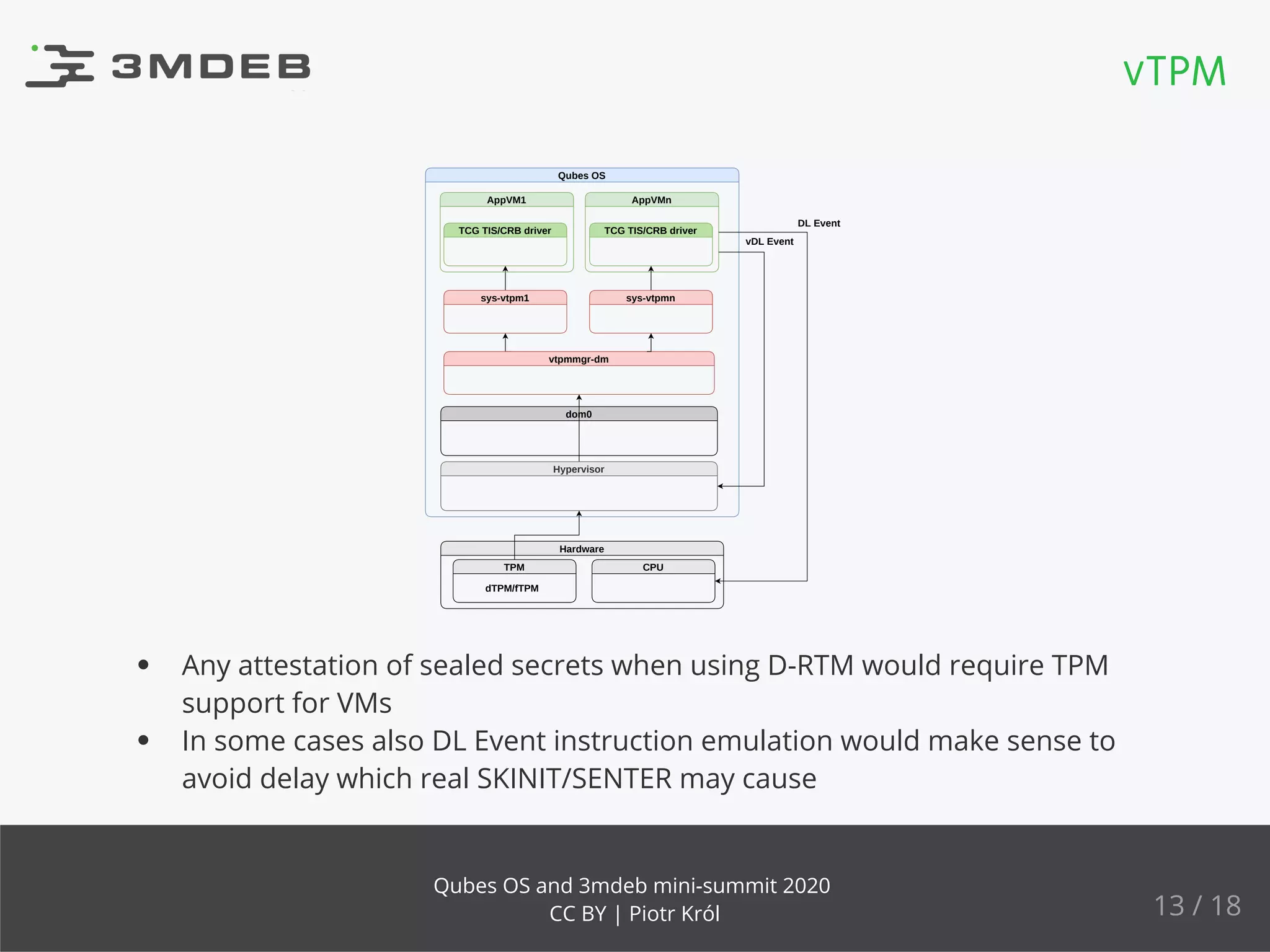
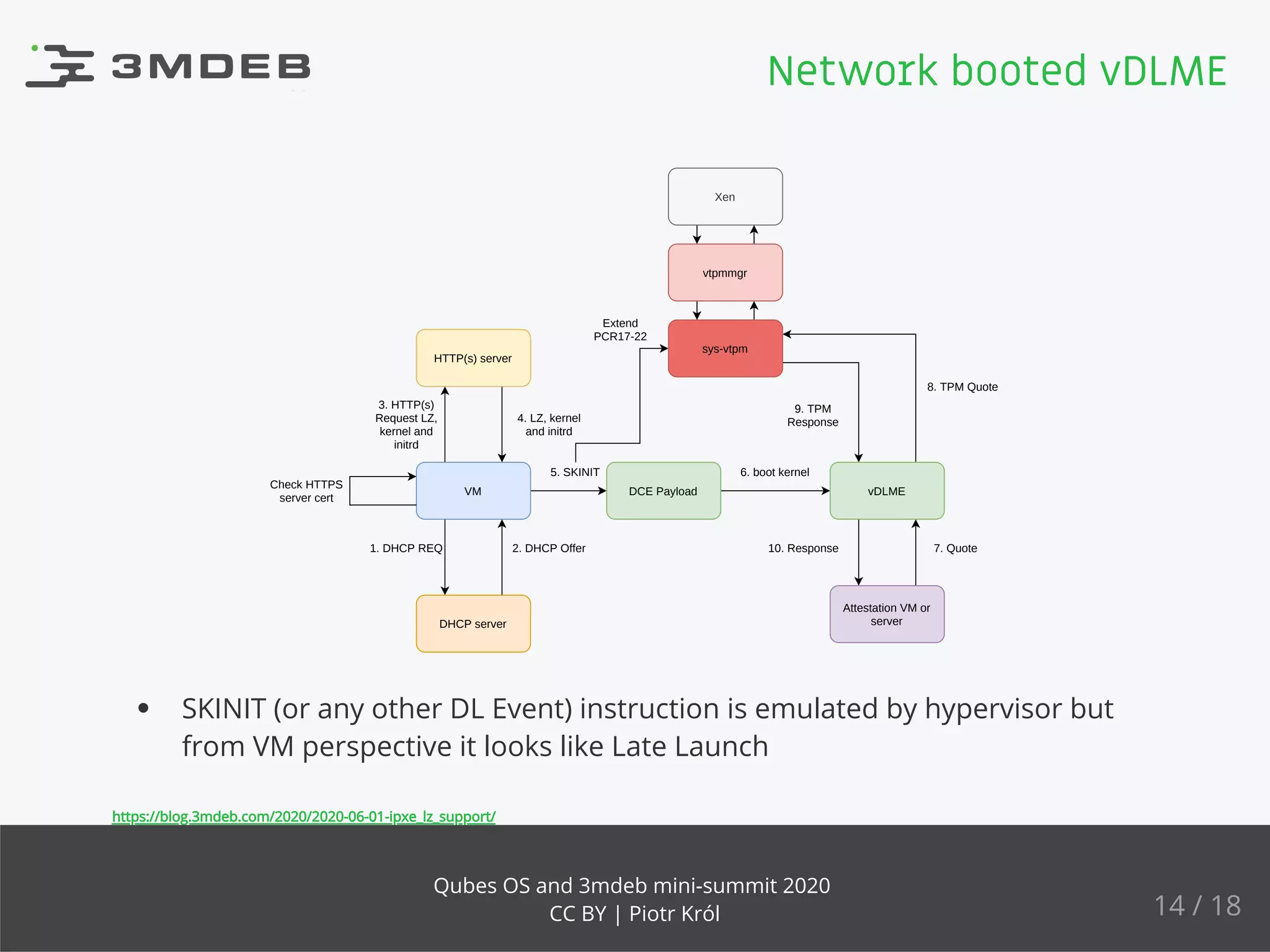
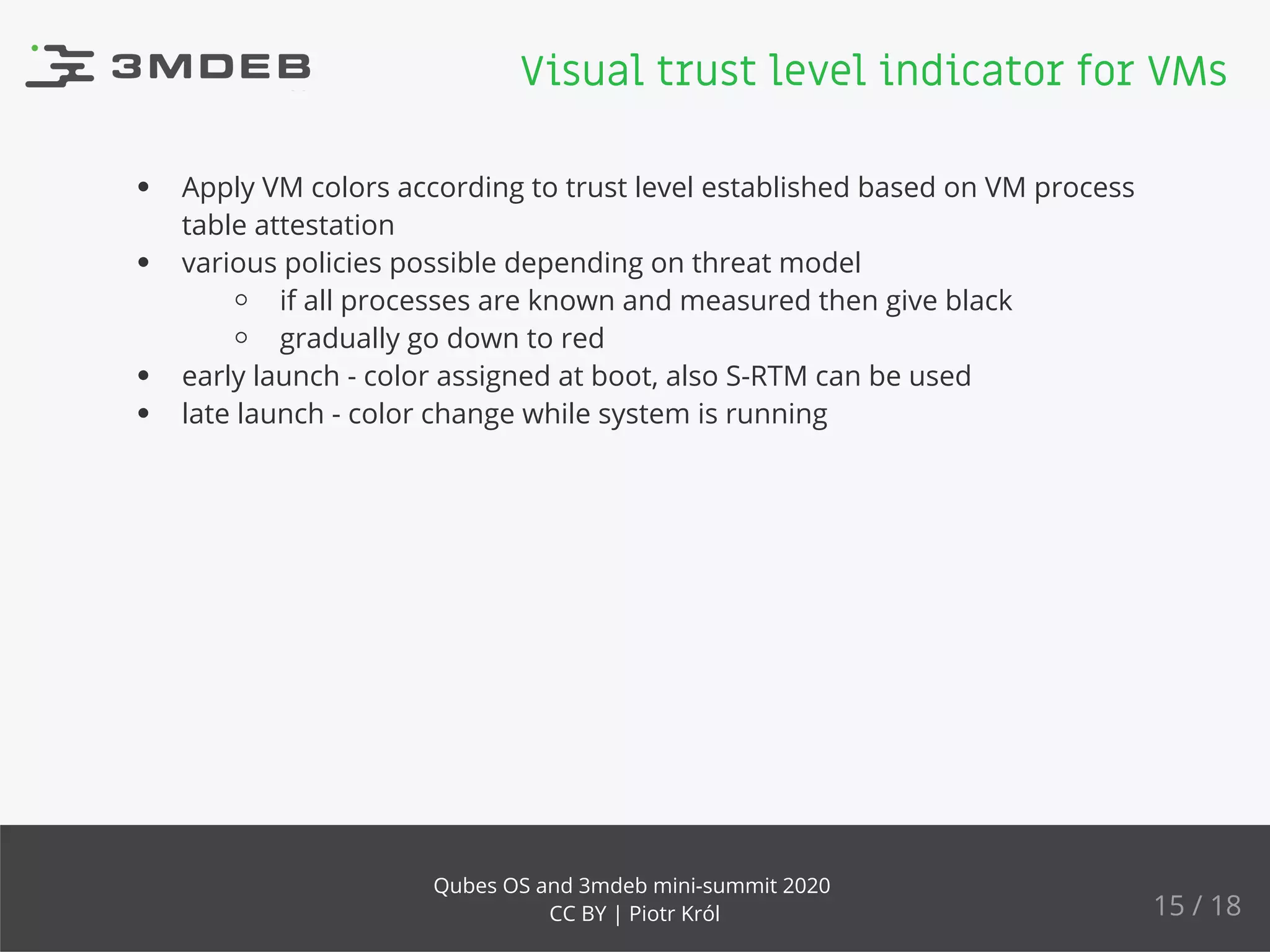
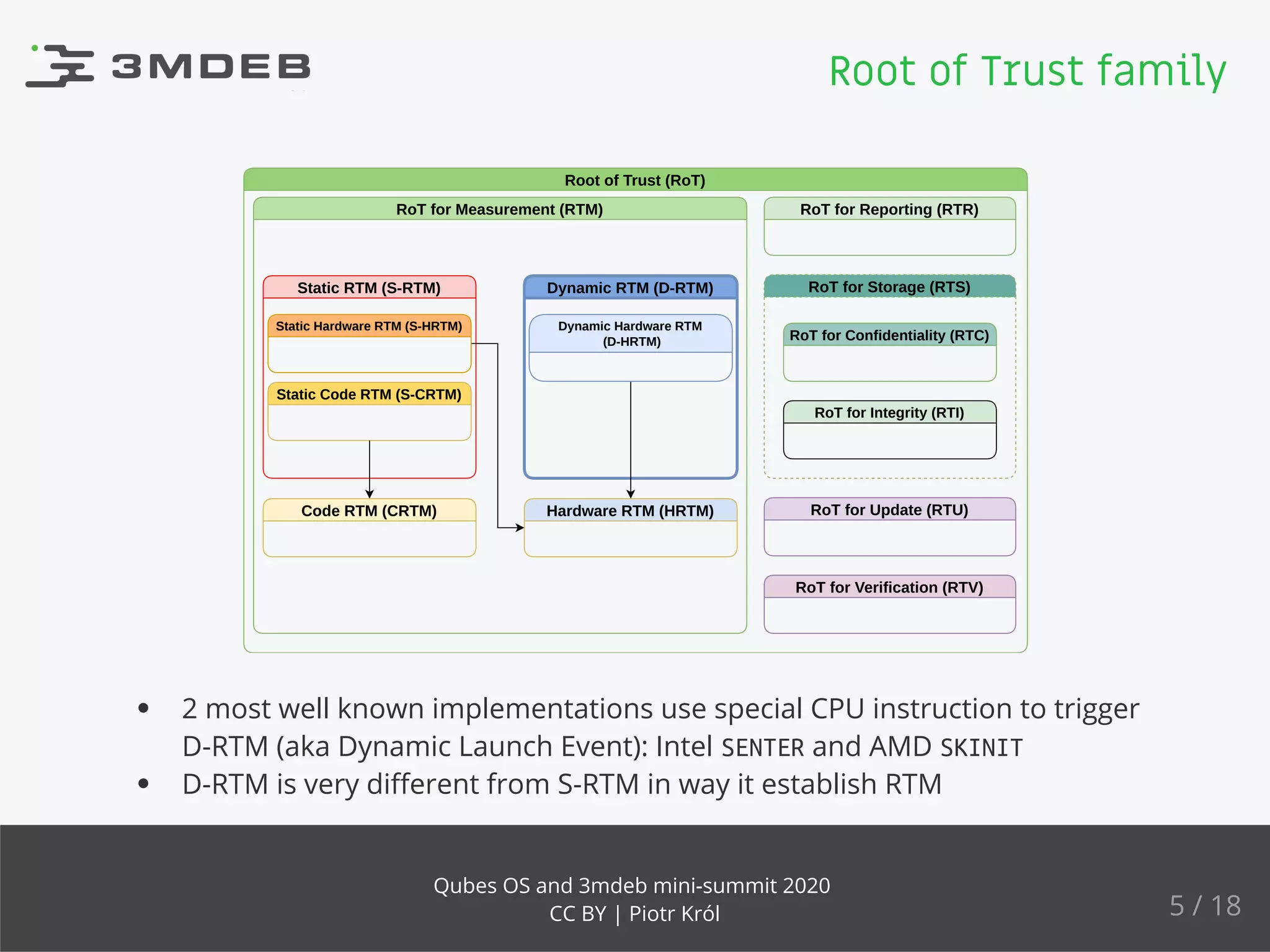
The document discusses the implementation and benefits of dynamic root of trust measurement (d-rtm) in Qubes OS, focusing on its architecture, launch processes, and advanced security features. It emphasizes the use of d-rtm for establishing a secure execution environment and virtual machine introspection while addressing potential complexities in implementation. Future ideas and discussion points include enhancing trust levels and attestation processes without relying on network connectivity.


![DRTM start when Dynamic Launch event call executes
DL Event controls PCRs 17-22, those are initialized with value -1
DL Event change PCRs value to 0 and immediately extends with DCE hash
Any attempt to reset TPM will set PCR[17] to -1 (TPM reset attack
immunity)
TCG D-RTM Architecture v1.0.0
Terminology
6 / 18
Qubes OS and 3mdeb mini-summit 2020
CC BY | Piotr Król](https://image.slidesharecdn.com/d-rtmforqubesosvms-200616134733/75/D-RTM-for-Qubes-OS-VMs-6-2048.jpg)