Database: PC and Employee
•Download as DOCX, PDF•
0 likes•78 views
To find the product, join, left outer join, right outer join, and a venn diagram.
Report
Share
Report
Share
Recommended
More Related Content
Similar to Database: PC and Employee
Similar to Database: PC and Employee (20)
HOME AUTOMATION USING MOBILE PHONES GIRISH HARMUKH AND NEERAJ YADAV

HOME AUTOMATION USING MOBILE PHONES GIRISH HARMUKH AND NEERAJ YADAV
More from Nicole Gaehle, MSIST
More from Nicole Gaehle, MSIST (19)
Analysis: New Threats & Countermeasure in Crime and Cyber Terrorism

Analysis: New Threats & Countermeasure in Crime and Cyber Terrorism
Analysis: Guidelines for Securing WLANS and Networks of ‘Things’

Analysis: Guidelines for Securing WLANS and Networks of ‘Things’
Recently uploaded
Recently uploaded (20)
Design and Development of a Provenance Capture Platform for Data Science

Design and Development of a Provenance Capture Platform for Data Science
Intro to Passkeys and the State of Passwordless.pptx

Intro to Passkeys and the State of Passwordless.pptx
Cyber Insurance - RalphGilot - Embry-Riddle Aeronautical University.pptx

Cyber Insurance - RalphGilot - Embry-Riddle Aeronautical University.pptx
The Zero-ETL Approach: Enhancing Data Agility and Insight

The Zero-ETL Approach: Enhancing Data Agility and Insight
WebRTC and SIP not just audio and video @ OpenSIPS 2024

WebRTC and SIP not just audio and video @ OpenSIPS 2024
Extensible Python: Robustness through Addition - PyCon 2024

Extensible Python: Robustness through Addition - PyCon 2024
(Explainable) Data-Centric AI: what are you explaininhg, and to whom?

(Explainable) Data-Centric AI: what are you explaininhg, and to whom?
ChatGPT and Beyond - Elevating DevOps Productivity

ChatGPT and Beyond - Elevating DevOps Productivity
How to Check CNIC Information Online with Pakdata cf

How to Check CNIC Information Online with Pakdata cf
Portal Kombat : extension du réseau de propagande russe

Portal Kombat : extension du réseau de propagande russe
TrustArc Webinar - Unified Trust Center for Privacy, Security, Compliance, an...

TrustArc Webinar - Unified Trust Center for Privacy, Security, Compliance, an...
JavaScript Usage Statistics 2024 - The Ultimate Guide

JavaScript Usage Statistics 2024 - The Ultimate Guide
Human Expert Website Manual WCAG 2.0 2.1 2.2 Audit - Digital Accessibility Au...

Human Expert Website Manual WCAG 2.0 2.1 2.2 Audit - Digital Accessibility Au...
UiPath manufacturing technology benefits and AI overview

UiPath manufacturing technology benefits and AI overview
Event-Driven Architecture Masterclass: Engineering a Robust, High-performance...

Event-Driven Architecture Masterclass: Engineering a Robust, High-performance...
Database: PC and Employee
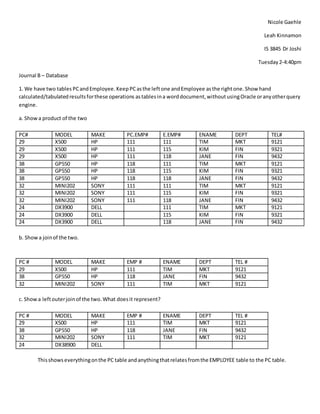
- 1. Nicole Gaehle Leah Kinnamon IS 3845 Dr Joshi Tuesday2-4:40pm Journal B – Database 1. We have two tables PCandEmployee. KeepPCasthe leftone andEmployee asthe rightone.Show hand calculated/tabulatedresultsforthese operations astables ina worddocument,withoutusingOracle oranyotherquery engine. a. Showa product of the two PC# MODEL MAKE PC.EMP# E.EMP# ENAME DEPT TEL# 29 X500 HP 111 111 TIM MKT 9121 29 X500 HP 111 115 KIM FIN 9321 29 X500 HP 111 118 JANE FIN 9432 38 GP550 HP 118 111 TIM MKT 9121 38 GP550 HP 118 115 KIM FIN 9321 38 GP550 HP 118 118 JANE FIN 9432 32 MINI202 SONY 111 111 TIM MKT 9121 32 MINI202 SONY 111 115 KIM FIN 9321 32 MINI202 SONY 111 118 JANE FIN 9432 24 DX3900 DELL 111 TIM MKT 9121 24 DX3900 DELL 115 KIM FIN 9321 24 DX3900 DELL 118 JANE FIN 9432 b. Showa joinof the two. PC # MODEL MAKE EMP # ENAME DEPT TEL # 29 X500 HP 111 TIM MKT 9121 38 GP550 HP 118 JANE FIN 9432 32 MINI202 SONY 111 TIM MKT 9121 c. Showa leftouterjoinof the two.What doesit represent? PC # MODEL MAKE EMP # ENAME DEPT TEL # 29 X500 HP 111 TIM MKT 9121 38 GP550 HP 118 JANE FIN 9432 32 MINI202 SONY 111 TIM MKT 9121 24 DX38900 DELL Thisshowseverythingonthe PC table andanythingthatrelatesfromthe EMPLOYEE table to the PC table.
- 2. d. Showa rightouter joinof the two.What doesit represent? PC # MODEL MAKE EMP # ENAME DEPT TEL # 29 X500 HP 111 TIM MKT 9121 32 MINI202 SONY 111 TIM MKT 9121 115 KIM FIN 9321 38 GP550 HP 118 JANE FIN 9432 Thisshowseverythingonthe EMPLOYEE table andanythingthat relatesfromthe PCtable to the EMPLOYEE table. e.Draw set diagramcirclesshowing EMP#from eachsetthat are commonand the onesthat are notcommon but exclusivetoone setor the other.
- 3. Prepare the answerstothese forclassdiscussion –Don’t needtoturn themin. 1. List all the rulesapplicable tothe use of Group BY statementinSQLqueries. Difference betweenWhere andHaving. 2. Which differentconnectorscanbe used(listall) tolinkthe resultsof asubquerytoa mainquery(withitscolumn)? Can youuse a columnof outerqueryinside asubqueryandvice versa,i.e., canyouuse a columnof the subqueryinthe outerquery? 3. How wouldyouadd twocolumnsgivingatotal column?Andhow wouldyouadd the contentsof a columngivingthe total. PC PC# Model Make Emp# 29 X500 HP 111 38 GP550 HP 118 32 Mini202 Sony 111 24 DX3900 Dell Employee Emp# Ename Dept Tel# 111 Tim MKT 9121 115 Kim FIN 9321 118 Jane FIN 9432