Entity Relationship Diagram
•
0 likes•60 views
To show the relationships for a video store and chazzy table
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
More from Nicole Gaehle, MSIST
More from Nicole Gaehle, MSIST (12)
Analysis: New Threats & Countermeasure in Crime and Cyber Terrorism

Analysis: New Threats & Countermeasure in Crime and Cyber Terrorism
Analysis: Guidelines for Securing WLANS and Networks of ‘Things’

Analysis: Guidelines for Securing WLANS and Networks of ‘Things’
Recently uploaded
Recently uploaded (20)
How to Check GPS Location with a Live Tracker in Pakistan

How to Check GPS Location with a Live Tracker in Pakistan
Event-Driven Architecture Masterclass: Engineering a Robust, High-performance...

Event-Driven Architecture Masterclass: Engineering a Robust, High-performance...
Microsoft CSP Briefing Pre-Engagement - Questionnaire

Microsoft CSP Briefing Pre-Engagement - Questionnaire
JavaScript Usage Statistics 2024 - The Ultimate Guide

JavaScript Usage Statistics 2024 - The Ultimate Guide
Cyber Insurance - RalphGilot - Embry-Riddle Aeronautical University.pptx

Cyber Insurance - RalphGilot - Embry-Riddle Aeronautical University.pptx
UiPath manufacturing technology benefits and AI overview

UiPath manufacturing technology benefits and AI overview
TrustArc Webinar - Unified Trust Center for Privacy, Security, Compliance, an...

TrustArc Webinar - Unified Trust Center for Privacy, Security, Compliance, an...
Observability Concepts EVERY Developer Should Know (DevOpsDays Seattle)

Observability Concepts EVERY Developer Should Know (DevOpsDays Seattle)
Human Expert Website Manual WCAG 2.0 2.1 2.2 Audit - Digital Accessibility Au...

Human Expert Website Manual WCAG 2.0 2.1 2.2 Audit - Digital Accessibility Au...
Easier, Faster, and More Powerful – Notes Document Properties Reimagined

Easier, Faster, and More Powerful – Notes Document Properties Reimagined
Portal Kombat : extension du réseau de propagande russe

Portal Kombat : extension du réseau de propagande russe
Tales from a Passkey Provider Progress from Awareness to Implementation.pptx

Tales from a Passkey Provider Progress from Awareness to Implementation.pptx
Introduction to FIDO Authentication and Passkeys.pptx

Introduction to FIDO Authentication and Passkeys.pptx
AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)

AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)
Entity Relationship Diagram
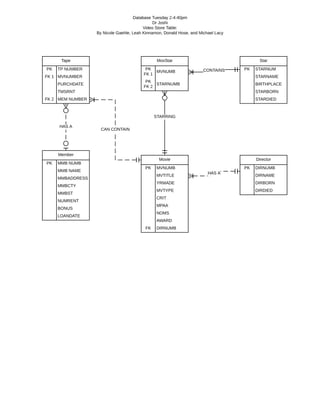
- 1. Database Tuesday 2-4:40pm Dr Joshi Video Store Table: By Nicole Gaehle, Leah Kinnamon, Donald Hose, and Michael Lacy Tape PK TP NUMBER FK 1 MVNUMBER PURCHDATE TMSRNT FK 2 MEM NUMBER MovStar PK FK 1 MVNUMB PK FK 2 STARNUMB Member PK MMB NUMB MMB NAME MMBADDRESS MMBCTY MMBST NUMRENT BONUS LOANDATE Director PK DIRNUMB DIRNAME DIRBORN DIRDIED Star PK STARNUM STARNAME BIRTHPLACE STARBORN STARDIED Movie PK MVNUMB MVTITLE YRMADE MVTYPE CRIT MPAA NOMS AWARD FK DIRNUMB HAS A CAN CONTAIN CONTAINS HAS A STARRING
- 2. Database Tuesday 2-4:40pm Dr Joshi Chazzy Table: By Nicole Gaehle, Leah Kinnamon, Donald Hose, and Michael Lacy COMPUTER PK COMPID MFGNAME MFGMODEL PROC TYPE PC PK TAGNUM FK 1 COMPID FK 2 EMPNUM LOCATION EMPLOYEE PK EMPNUM EMPNAME EMPPHONE SOFTWARE PK FK 1 PACKID PK FK 2 TAGNUM INSTDATE SOFTCOST PACKAGE PK PACKID PACKNAME PACKVER PACKTYPE PACKCOST INCLUDES USES WILL BE PROCESSED ACCESSES