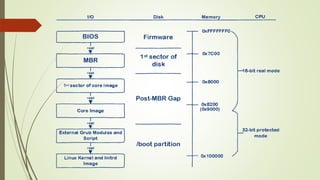
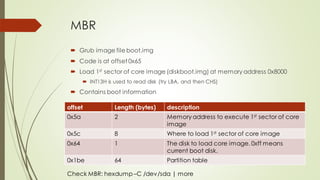
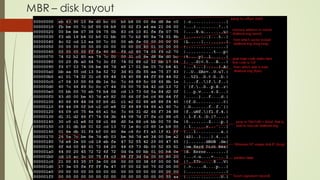
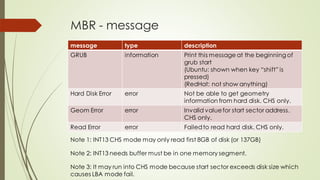
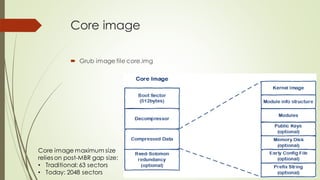
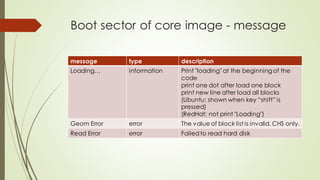
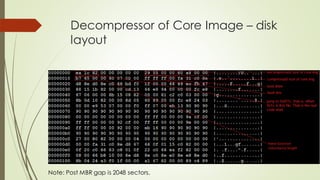
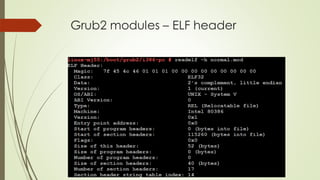
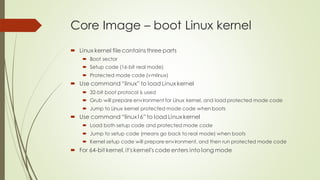
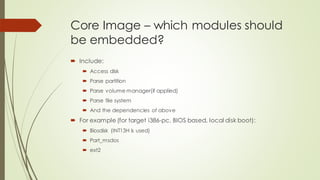
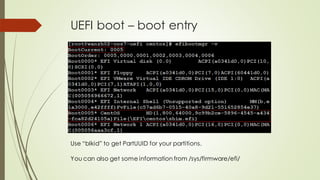
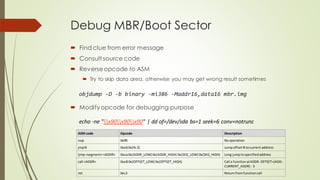
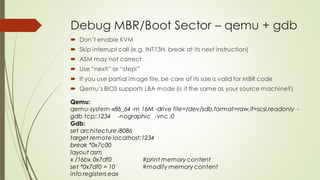
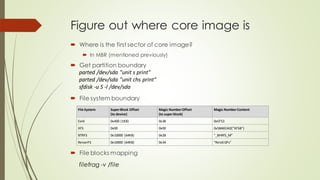
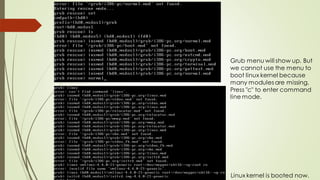
This document summarizes the Grub2 booting process. It begins with the classical BIOS booting process where the BIOS finds and loads the MBR, which contains code to load the Grub core image. The core image loads modules to access disks and file systems to load the Linux kernel. For UEFI booting, the firmware loads the bootloader from an EFI System Partition, which contains Shim and Grub files. The document outlines the key files, modules, and steps in the Grub2 booting process for both BIOS and UEFI systems.