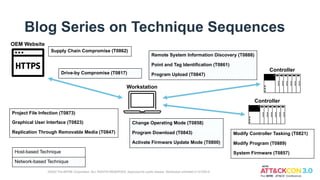
The document discusses updates to the ATT&CK for ICS framework. It summarizes two recent incidents, the Colonial Pipeline ransomware attack and the Oldsmar water treatment plant hack, and highlights techniques used in each. It previews upcoming additions to ATT&CK for ICS in April 2022 and beyond, including new mapped mitigation objects, integration with other frameworks, mapping of ICS attacks to the enterprise ATT&CK, and the addition of detections for techniques. Future plans outlined include revisions to asset definitions based on ICS verticals and a blog series on technique sequences.