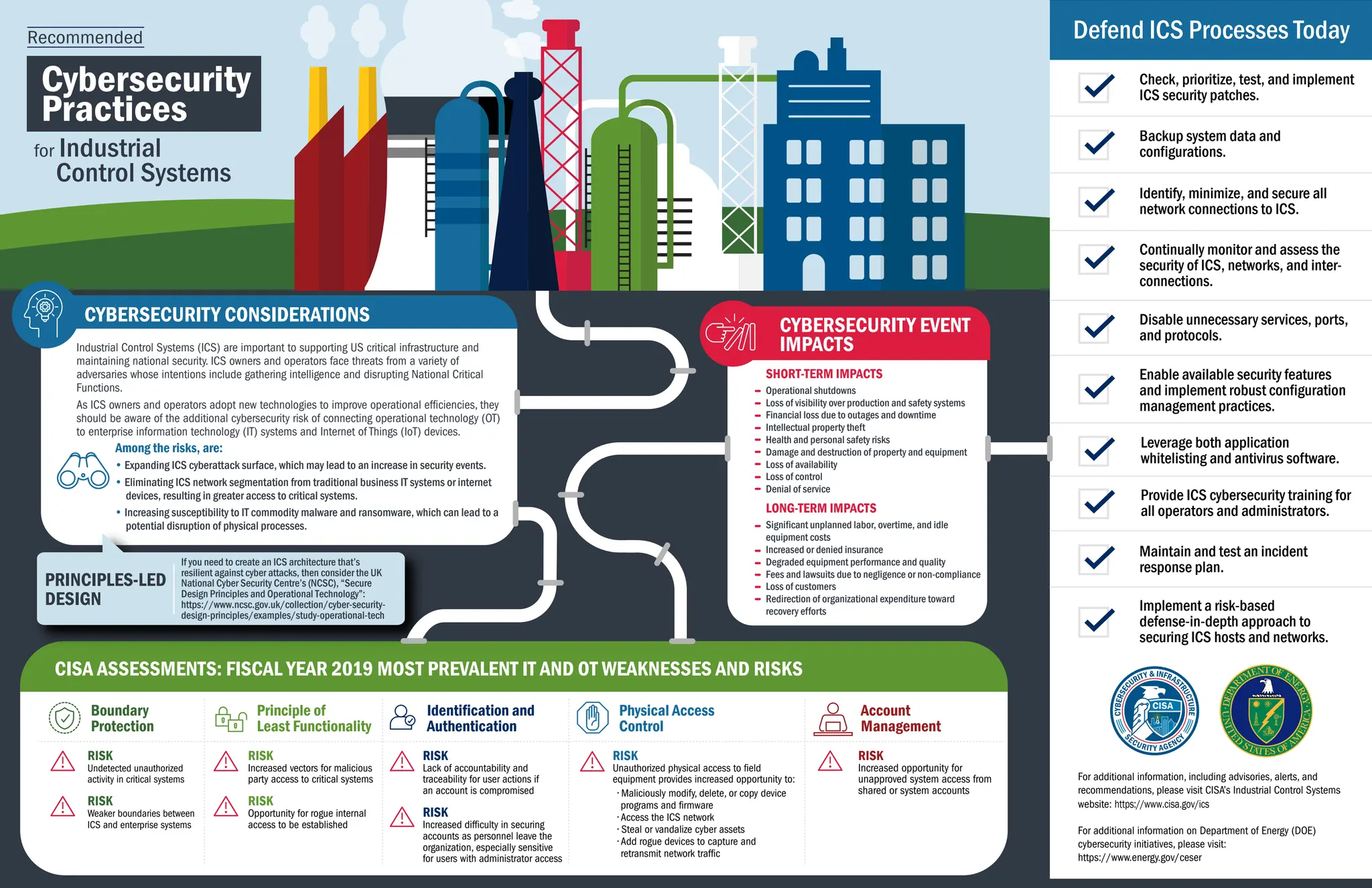
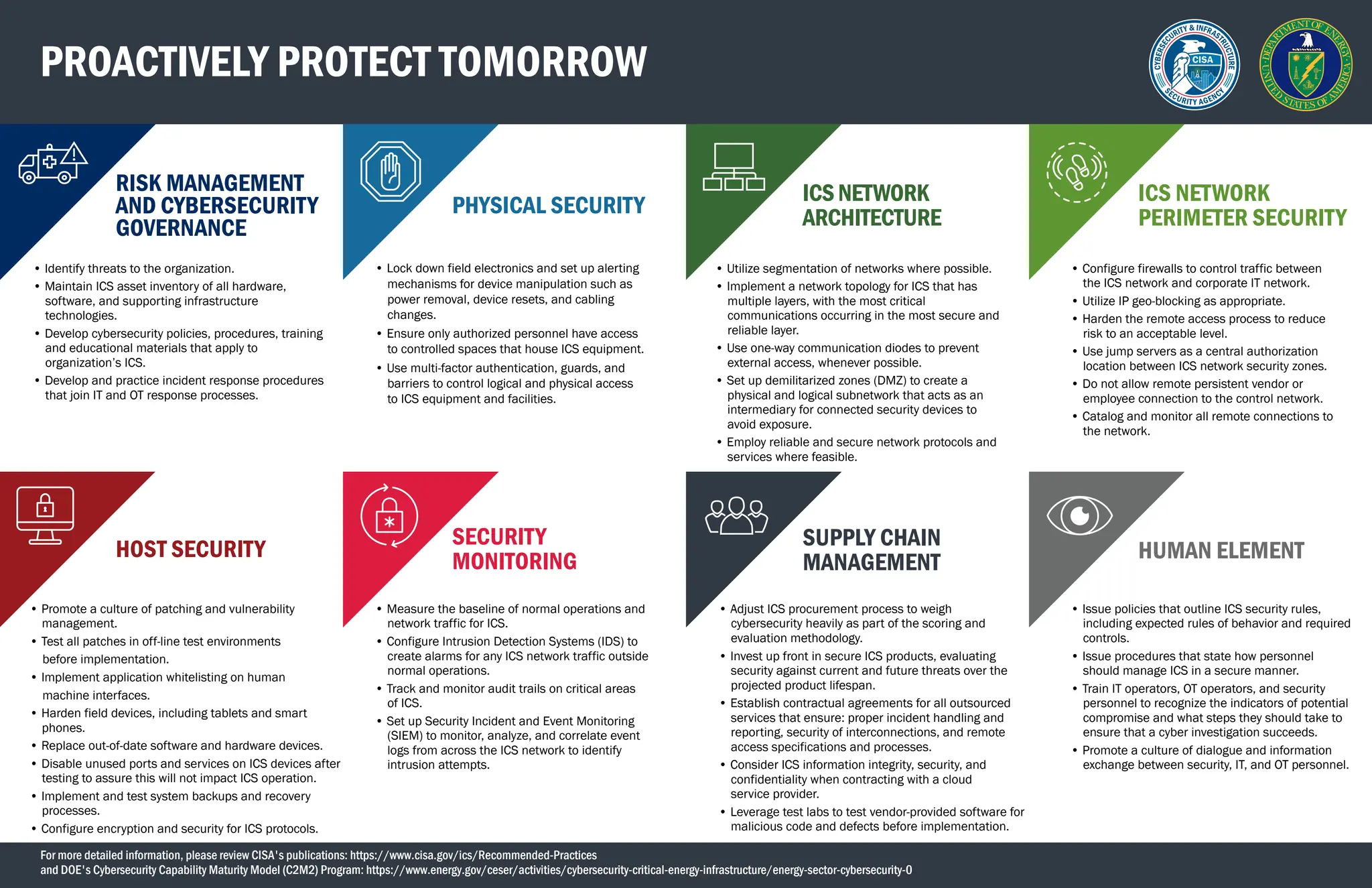
The document outlines recommended cybersecurity practices for industrial control systems (ICS), emphasizing the importance of safeguarding these systems due to their critical role in national security and infrastructure. It details various risks associated with integrating operational technology with enterprise IT systems, offers guidance on creating resilient ICS architectures, and suggests comprehensive security measures including risk management, incident response, and personnel training. The document also highlights the need for effective monitoring, patch management, and secure procurement in order to mitigate potential cyber threats.