Machine Learning
•
0 likes•29 views
VIDEO ANOMALY PREDICTION BASED ON SPATIAL AND TEMPORAL DATA
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
To Get any Project for CSE, IT ECE, EEE Contact Me @ 09666155510, 09849539085 or mail us - ieeefinalsemprojects@gmail.com-Visit Our Website: www.finalyearprojects.orgIEEE 2014 MATLAB IMAGE PROCESSING PROJECTS Designing an efficient image encr...

IEEE 2014 MATLAB IMAGE PROCESSING PROJECTS Designing an efficient image encr...IEEEBEBTECHSTUDENTPROJECTS
More Related Content
Similar to Machine Learning
To Get any Project for CSE, IT ECE, EEE Contact Me @ 09666155510, 09849539085 or mail us - ieeefinalsemprojects@gmail.com-Visit Our Website: www.finalyearprojects.orgIEEE 2014 MATLAB IMAGE PROCESSING PROJECTS Designing an efficient image encr...

IEEE 2014 MATLAB IMAGE PROCESSING PROJECTS Designing an efficient image encr...IEEEBEBTECHSTUDENTPROJECTS
Similar to Machine Learning (20)
JOINT IMAGE WATERMARKING, COMPRESSION AND ENCRYPTION BASED ON COMPRESSED SENS...

JOINT IMAGE WATERMARKING, COMPRESSION AND ENCRYPTION BASED ON COMPRESSED SENS...
Video steganography based on DCT psychovisual and object motion

Video steganography based on DCT psychovisual and object motion
Secure IoT Systems Monitor Framework using Probabilistic Image Encryption

Secure IoT Systems Monitor Framework using Probabilistic Image Encryption
IEEE 2014 MATLAB IMAGE PROCESSING PROJECTS Designing an efficient image encr...

IEEE 2014 MATLAB IMAGE PROCESSING PROJECTS Designing an efficient image encr...
Future semantic segmentation with convolutional LSTM

Future semantic segmentation with convolutional LSTM
IRJET- Human Fall Detection using Co-Saliency-Enhanced Deep Recurrent Convolu...

IRJET- Human Fall Detection using Co-Saliency-Enhanced Deep Recurrent Convolu...
International Journal of Engineering Research and Development (IJERD)

International Journal of Engineering Research and Development (IJERD)
A VIDEO COMPRESSION TECHNIQUE UTILIZING SPATIO-TEMPORAL LOWER COEFFICIENTS

A VIDEO COMPRESSION TECHNIQUE UTILIZING SPATIO-TEMPORAL LOWER COEFFICIENTS
Detecting anomalies in security cameras with 3D-convolutional neural network ...

Detecting anomalies in security cameras with 3D-convolutional neural network ...
TARGET DETECTION AND CLASSIFICATION PERFORMANCE ENHANCEMENT USING SUPERRESOLU...

TARGET DETECTION AND CLASSIFICATION PERFORMANCE ENHANCEMENT USING SUPERRESOLU...
TARGET DETECTION AND CLASSIFICATION PERFORMANCE ENHANCEMENT USING SUPERRESOLU...

TARGET DETECTION AND CLASSIFICATION PERFORMANCE ENHANCEMENT USING SUPERRESOLU...
JPM1404 Designing an Efficient Image Encryption-Then-Compression System via...

JPM1404 Designing an Efficient Image Encryption-Then-Compression System via...
An overview Survey on Various Video compressions and its importance

An overview Survey on Various Video compressions and its importance
Recently uploaded
Saudi Arabia [ Abortion pills) Jeddah/riaydh/dammam/+966572737505☎️] cytotec tablets uses abortion pills 💊💊
How effective is the abortion pill? 💊💊 +966572737505) "Abortion pills in Jeddah" how to get cytotec tablets in Riyadh " Abortion pills in dammam*💊💊
The abortion pill is very effective. If you’re taking mifepristone and misoprostol, it depends on how far along the pregnancy is, and how many doses of medicine you take:💊💊 +966572737505) how to buy cytotec pills
At 8 weeks pregnant or less, it works about 94-98% of the time. +966572737505[ 💊💊💊
At 8-9 weeks pregnant, it works about 94-96% of the time. +966572737505)
At 9-10 weeks pregnant, it works about 91-93% of the time. +966572737505)💊💊
If you take an extra dose of misoprostol, it works about 99% of the time.
At 10-11 weeks pregnant, it works about 87% of the time. +966572737505)
If you take an extra dose of misoprostol, it works about 98% of the time.
In general, taking both mifepristone and+966572737505 misoprostol works a bit better than taking misoprostol only.
+966572737505
Taking misoprostol alone works to end the+966572737505 pregnancy about 85-95% of the time — depending on how far along the+966572737505 pregnancy is and how you take the medicine.
+966572737505
The abortion pill usually works, but if it doesn’t, you can take more medicine or have an in-clinic abortion.
+966572737505
When can I take the abortion pill?+966572737505
In general, you can have a medication abortion up to 77 days (11 weeks)+966572737505 after the first day of your last period. If it’s been 78 days or more since the first day of your last+966572737505 period, you can have an in-clinic abortion to end your pregnancy.+966572737505
Why do people choose the abortion pill?
Which kind of abortion you choose all depends on your personal+966572737505 preference and situation. With+966572737505 medication+966572737505 abortion, some people like that you don’t need to have a procedure in a doctor’s office. You can have your medication abortion on your own+966572737505 schedule, at home or in another comfortable place that you choose.+966572737505 You get to decide who you want to be with during your abortion, or you can go it alone. Because+966572737505 medication abortion is similar to a miscarriage, many people feel like it’s more “natural” and less invasive. And some+966572737505 people may not have an in-clinic abortion provider close by, so abortion pills are more available to+966572737505 them.
+966572737505
Your doctor, nurse, or health center staff can help you decide which kind of abortion is best for you.
+966572737505
More questions from patients:
Saudi Arabia+966572737505
CYTOTEC Misoprostol Tablets. Misoprostol is a medication that can prevent stomach ulcers if you also take NSAID medications. It reduces the amount of acid in your stomach, which protects your stomach lining. The brand name of this medication is Cytotec®.+966573737505)
Unwanted Kit is a combination of two medicinesAbortion pills in Dammam Saudi Arabia// +966572737505 // buy cytotec

Abortion pills in Dammam Saudi Arabia// +966572737505 // buy cytotecAbortion pills in Riyadh +966572737505 get cytotec
Recently uploaded (20)
2024 Q2 Orange County (CA) Tableau User Group Meeting

2024 Q2 Orange County (CA) Tableau User Group Meeting
Fuzzy Sets decision making under information of uncertainty

Fuzzy Sets decision making under information of uncertainty
Supply chain analytics to combat the effects of Ukraine-Russia-conflict

Supply chain analytics to combat the effects of Ukraine-Russia-conflict
Abortion pills in Dammam Saudi Arabia// +966572737505 // buy cytotec

Abortion pills in Dammam Saudi Arabia// +966572737505 // buy cytotec
Data Visualization Exploring and Explaining with Data 1st Edition by Camm sol...

Data Visualization Exploring and Explaining with Data 1st Edition by Camm sol...
How I opened a fake bank account and didn't go to prison

How I opened a fake bank account and didn't go to prison
Artificial_General_Intelligence__storm_gen_article.pdf

Artificial_General_Intelligence__storm_gen_article.pdf
Machine Learning
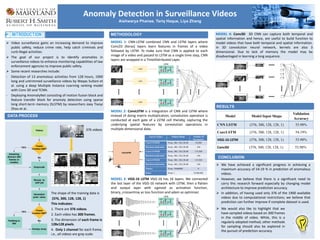
- 1. Anomaly Detection in Surveillance Videos Aishwarya Phanse, Tariq Haque, Liya Zhang Ø Video surveillance gains an increasing demand to improve public safety, reduce crime rate, help catch criminals and curb illegal activities. Ø The goal of our project is to identify anomalies in surveillance videos to enhance monitoring capabilities of law enforcement agencies to improve public safety. Ø Some recent researches include: - Detection of 13 anomalous activities from 128 hours, 1900 long and untrimmed surveillance videos by Waqas Sultani et al. using a deep Multiple Instance Learning ranking model with Conv 3D and TCNN. - Deploying AnomalyNet consisting of motion fusion block and feature transfer block for anomaly detection using sparse long short-term memory (SLSTM) by researchers Joey Tianyi Zhou et al.. 376 videos The shape of the training data is (376, 300, 128, 128, 1) This indicates: 1. There are 376 videos. 2. Each video has 300 frames. 3. The dimension of each frame is 128x128 pixels. 4. Only 1 channel for each frame, i.e., all videos are gray scale. MODEL 4: Conv3D 3D CNN can capture both temporal and spatial information and hence, are useful to build function to model videos that have both temporal and spatial information. In 3D convolution neural network, kernels are also 3 dimensional. Due to lack of memory the model may be disadvantaged in learning a long sequence. Layers (Type) Output Shape Number of Parameters ConvLSTM2D None, 300, 128,128,40 59,200 Batchnormalization None, 300, 128,128,40 160 ConvLSTM2D None, 300, 128,128,40 115,360 Batchnormalization None, 300, 128,128,40 160 ConvLSTM2D None, 300, 128,128,40 115,360 Batchnormalization None, 300, 128,128,40 160 Flatten None, 19660800 0 Dense None, 1 19,660,801 MODEL 1: CNN-LSTM combined CNN and LSTM layers where Conv2D (Keras) layers learn features in frames of a video followed by LSTM. To make sure that CNN is applied to each image of a video and passed to LSTM as a single time step, CNN layers are wrapped in a TimeDistributed Layer. MODEL 2: ConvLSTM is a integration of CNN and LSTM where instead of doing matrix multiplication, convolution operation is conducted at each gate of a LSTM cell thereby, capturing the underlying spatial features by convolution operations in multiple-dimensional data. MODEL 3: VGG-16 LSTM VGG-16 has 16 layers. We connected the last layer of the VGG-16 network with LSTM, then a flatten and output layer with sigmoid as activation function, binary_crossentroy as loss function and adam as optimizer. Ø We have achieved a significant progress in achieving a maximum accuracy of 54.19 % in prediction of anomalous videos. Ø However, we believe that there is a significant need to carry this research forward especially by changing model architecture to improve prediction accuracy. Ø In addition, of having used only 376 of the 1900 available videos due to computational restrictions; we believe that prediction can further improve if complete dataset is used. DATA PROCESS METHODOLOGY RESULTS CONCLUSION Model Model Input Shape Validation Accuracy CNN LSTM (376, 300, 128, 128, 1) 53.98% ConvLSTM (376, 300, 128, 128, 1) 54.19% VGG-16 LSTM (376, 300, 128, 128, 1) 53.98% Conv3D (376, 300, 128, 128, 1) 53.98% Ø We would also like to highlight that we have sampled videos based on 300 frames in the middle of video. While, this is a regularly adopted method, other methods for sampling should also be explored in the pursuit of prediction accuracy.