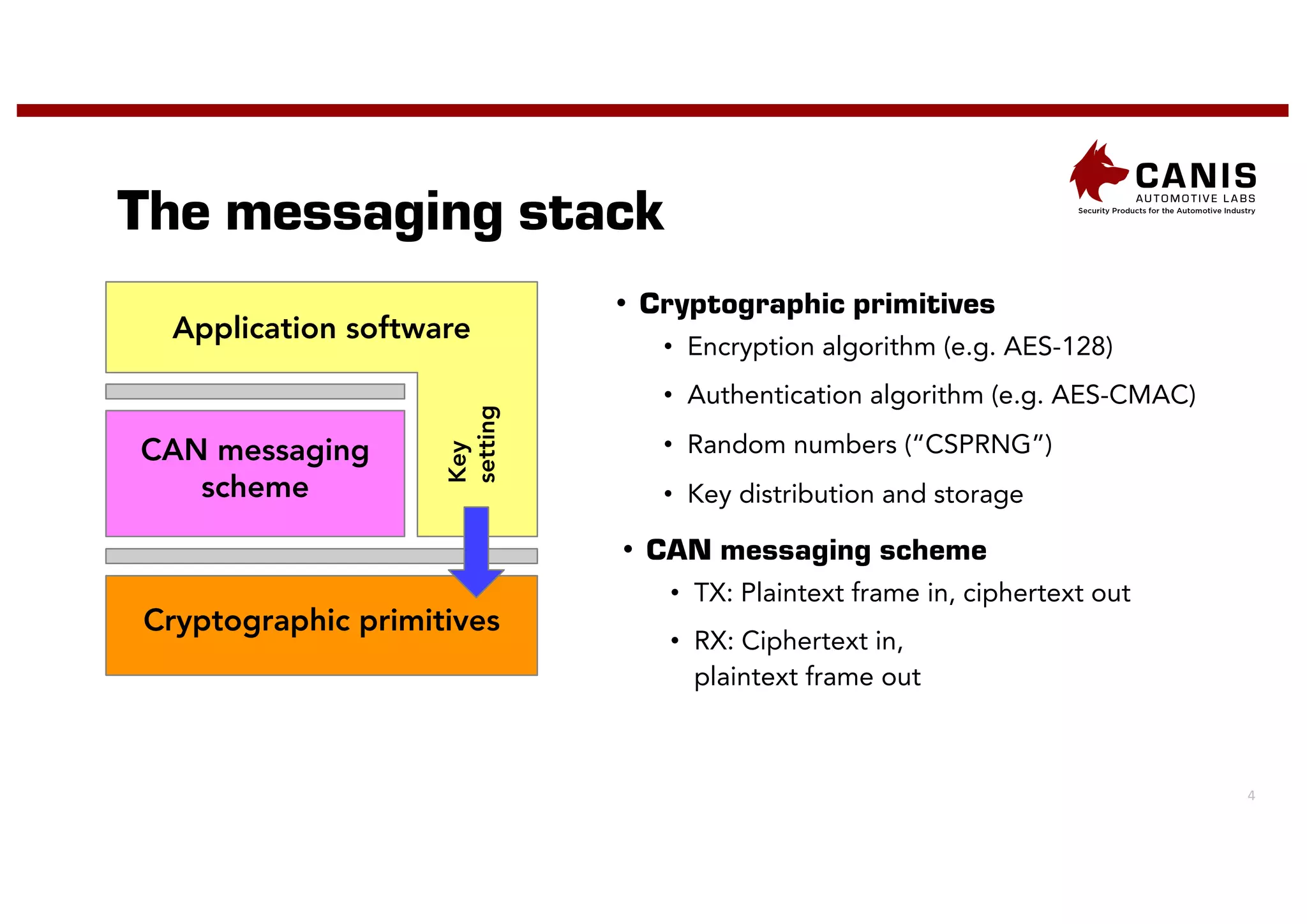
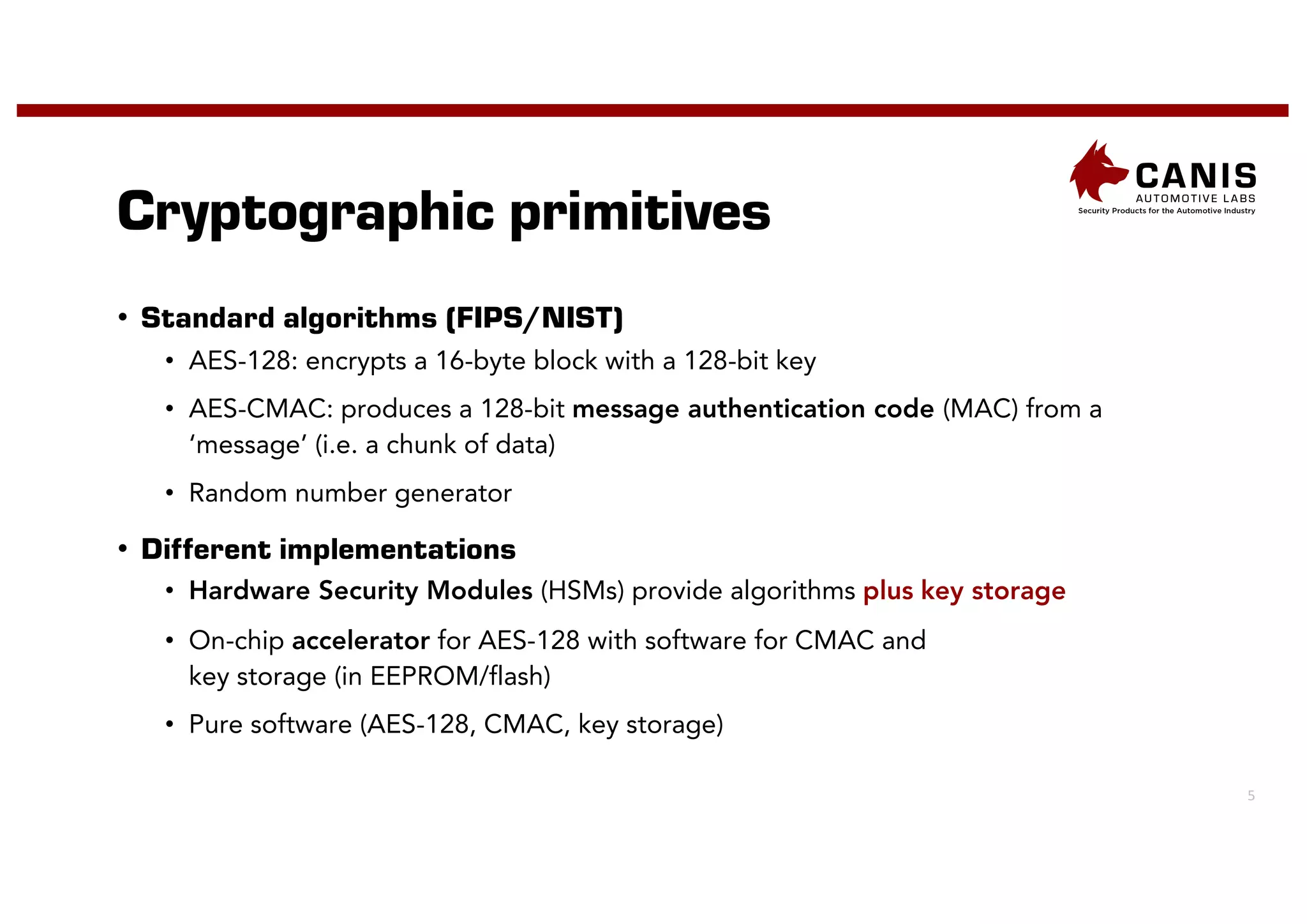
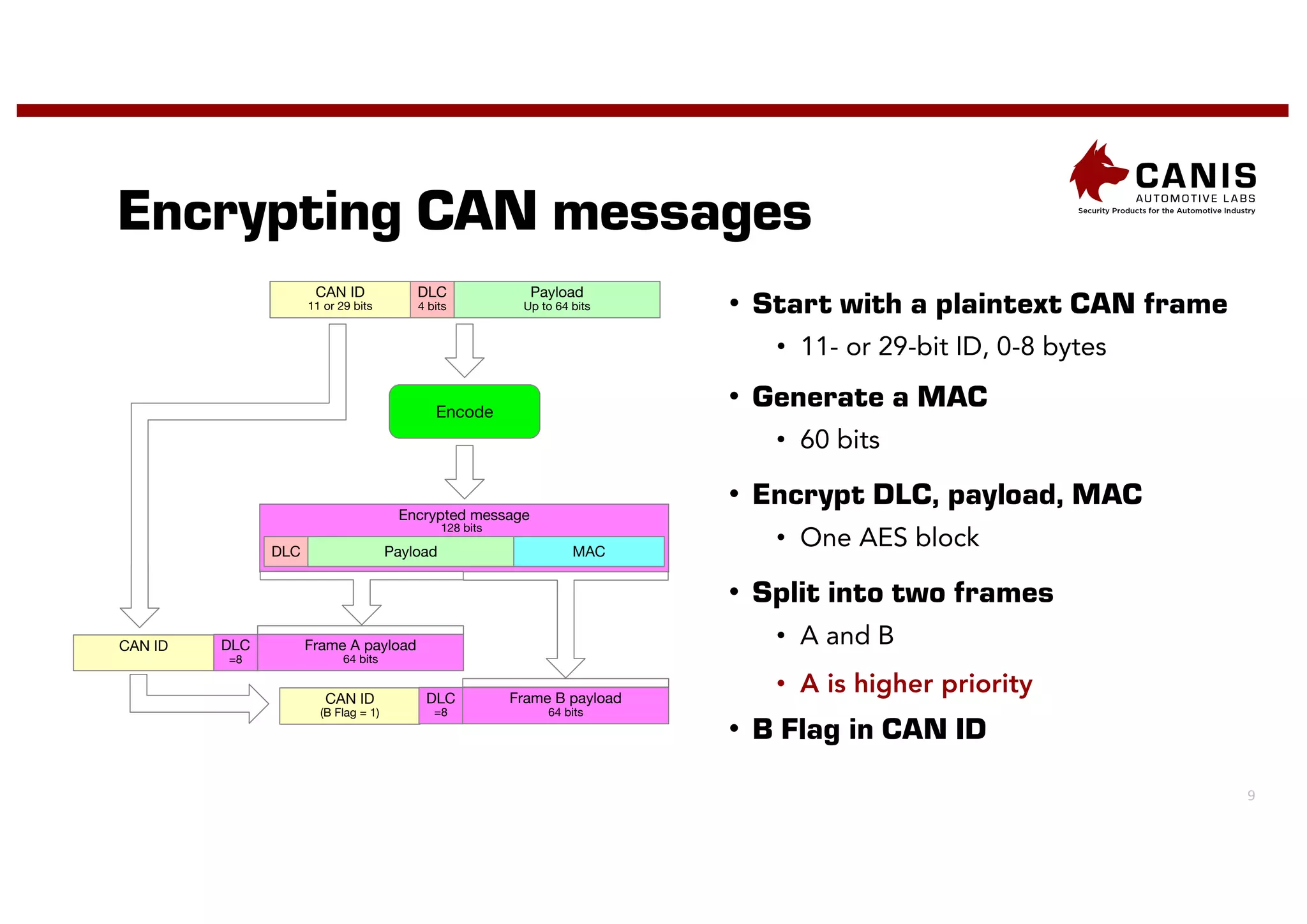
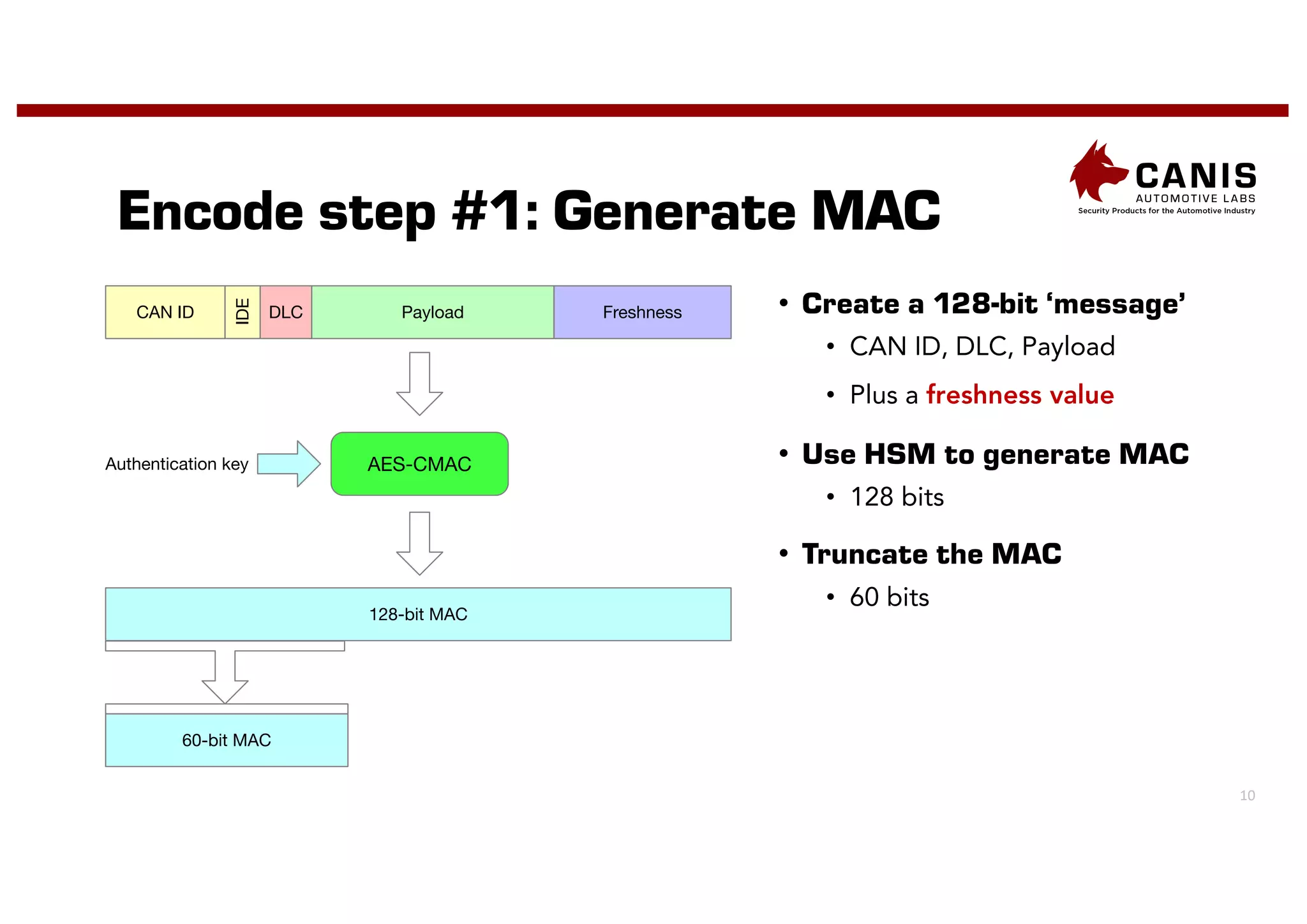
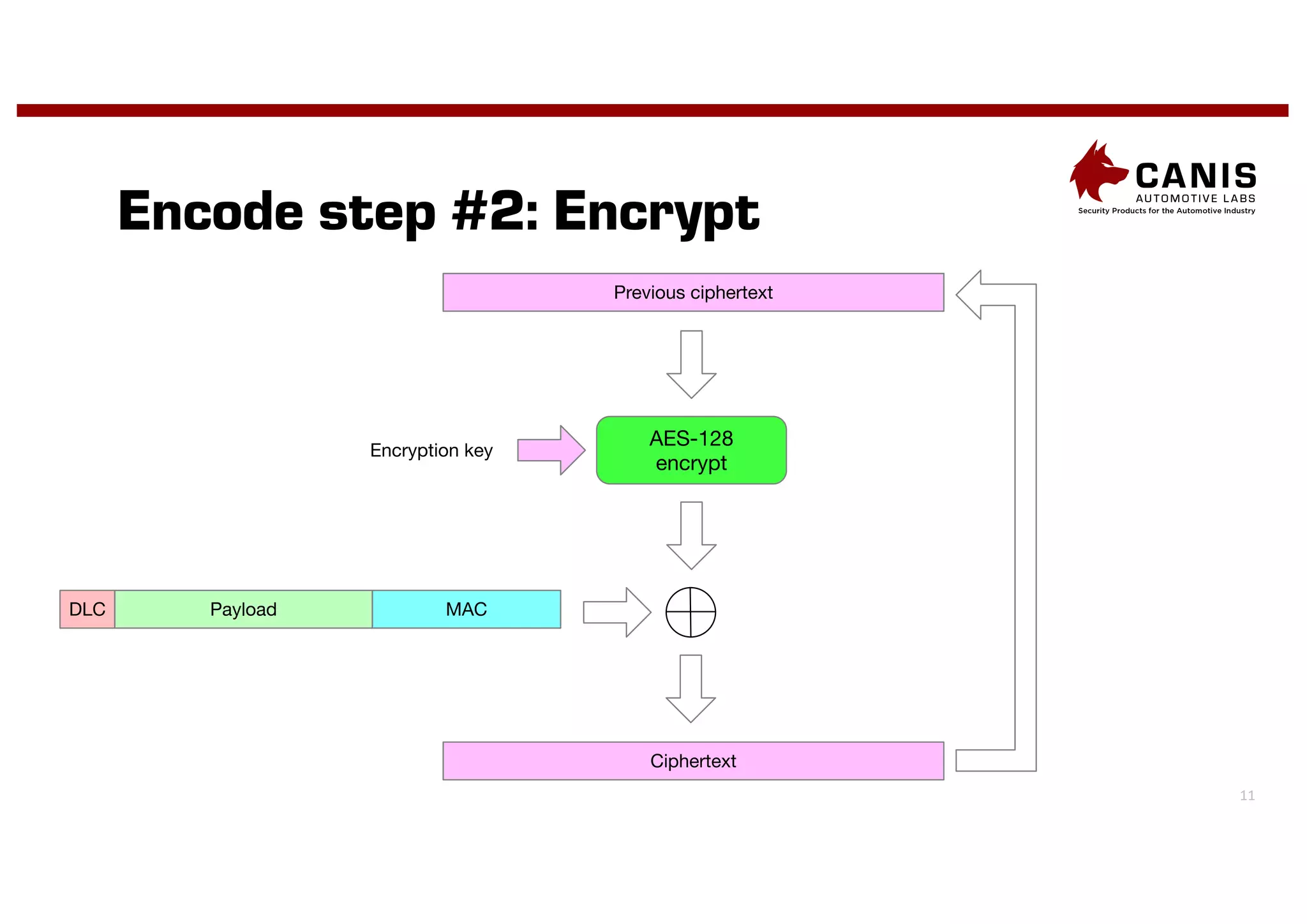
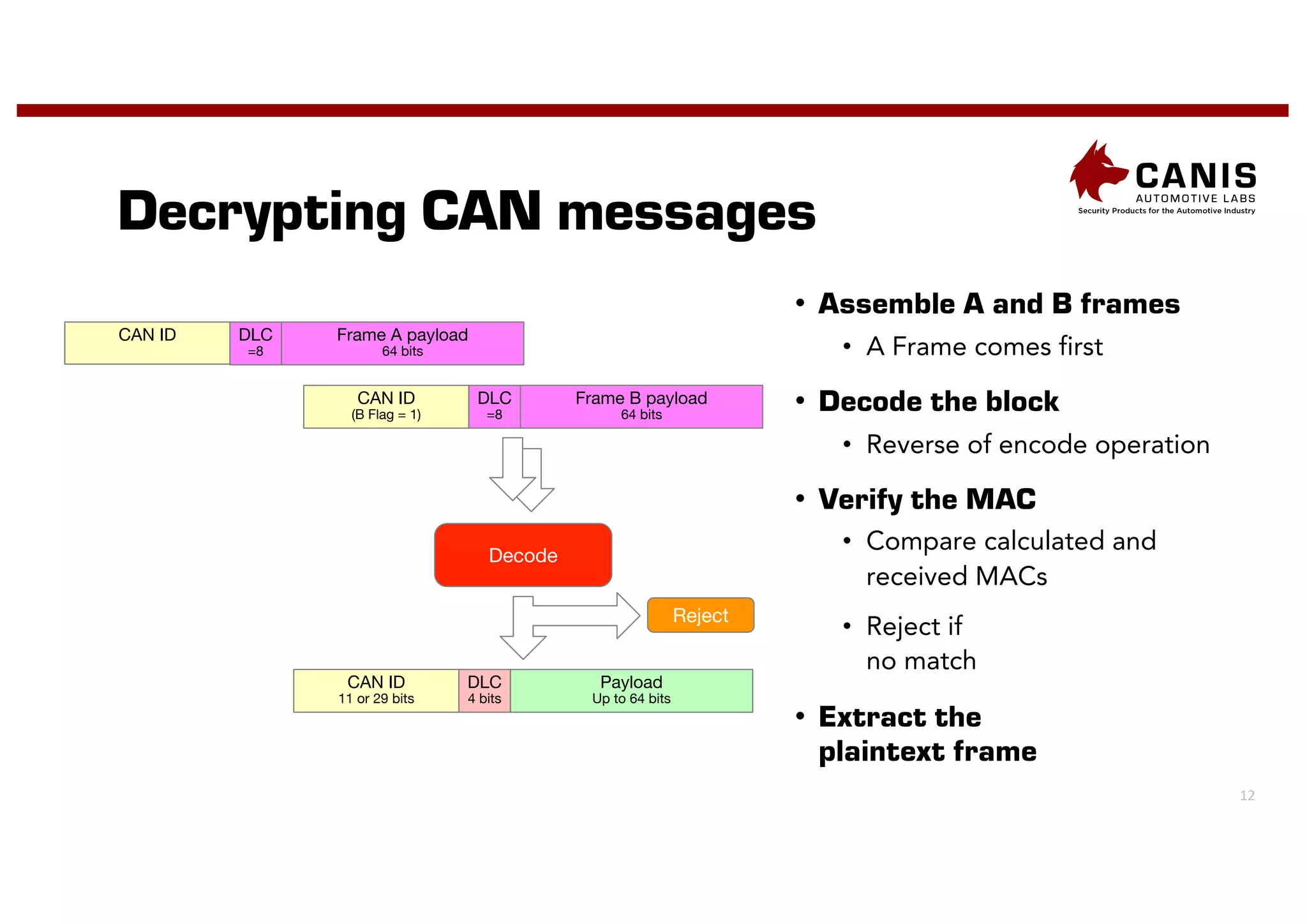
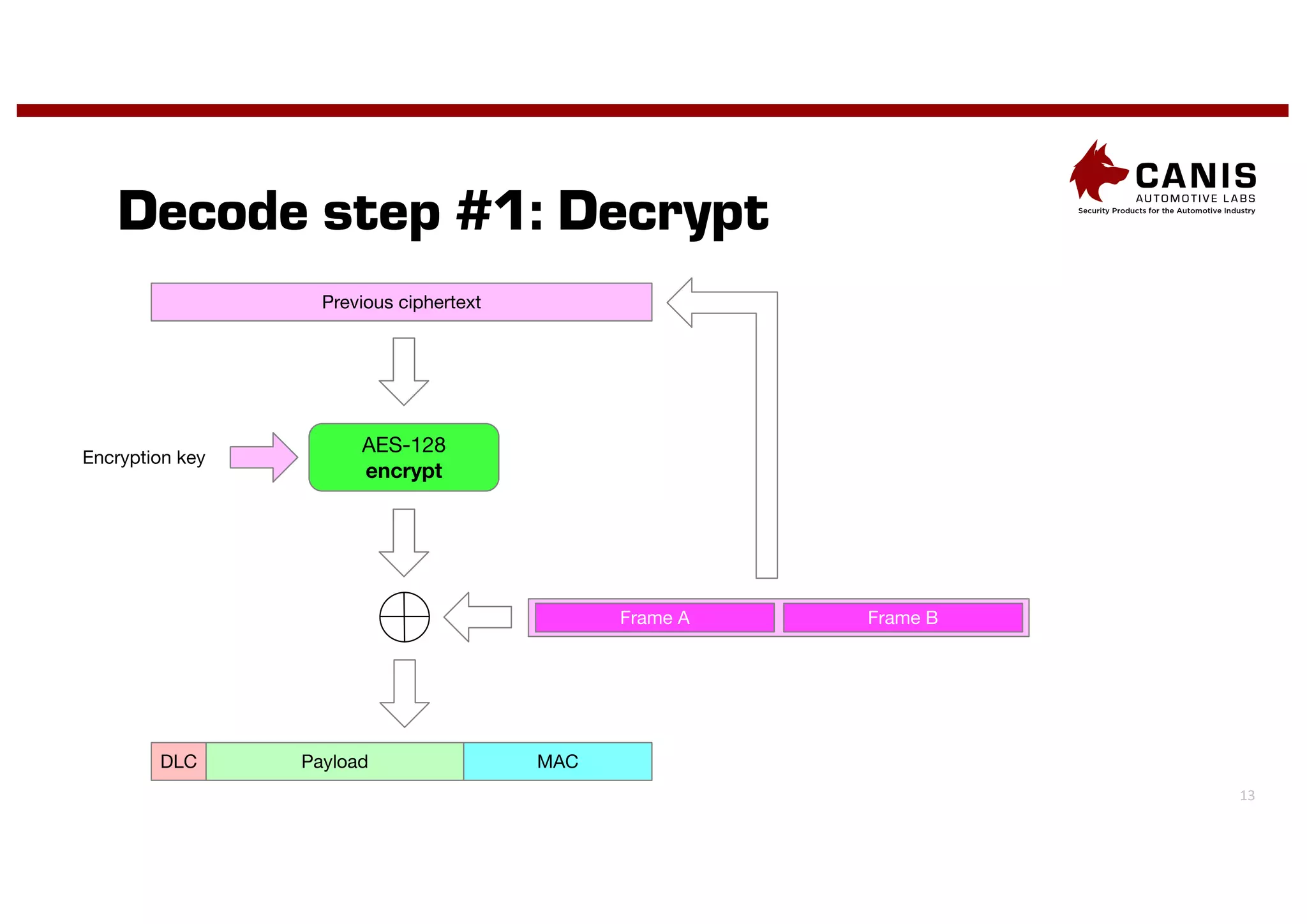
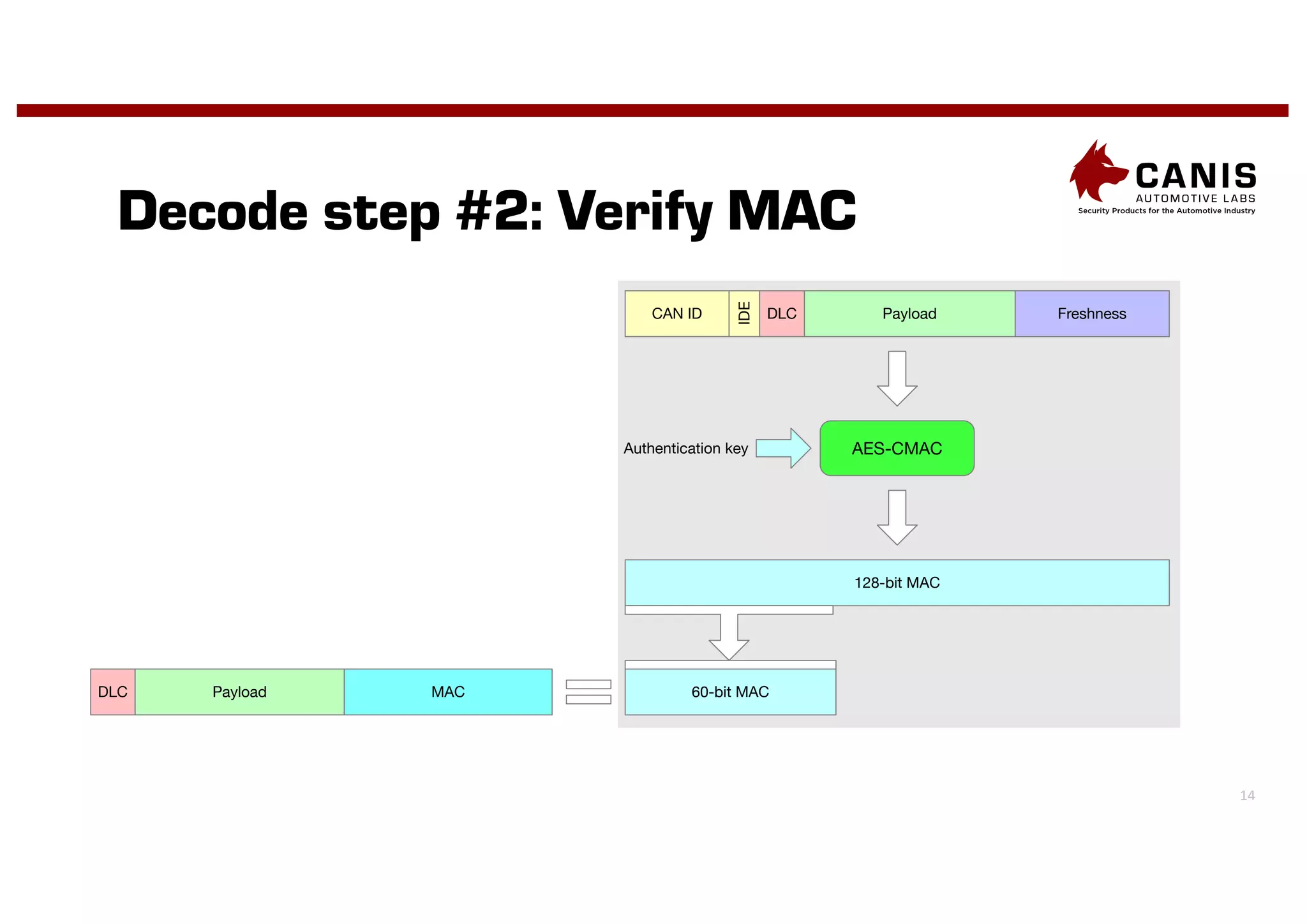
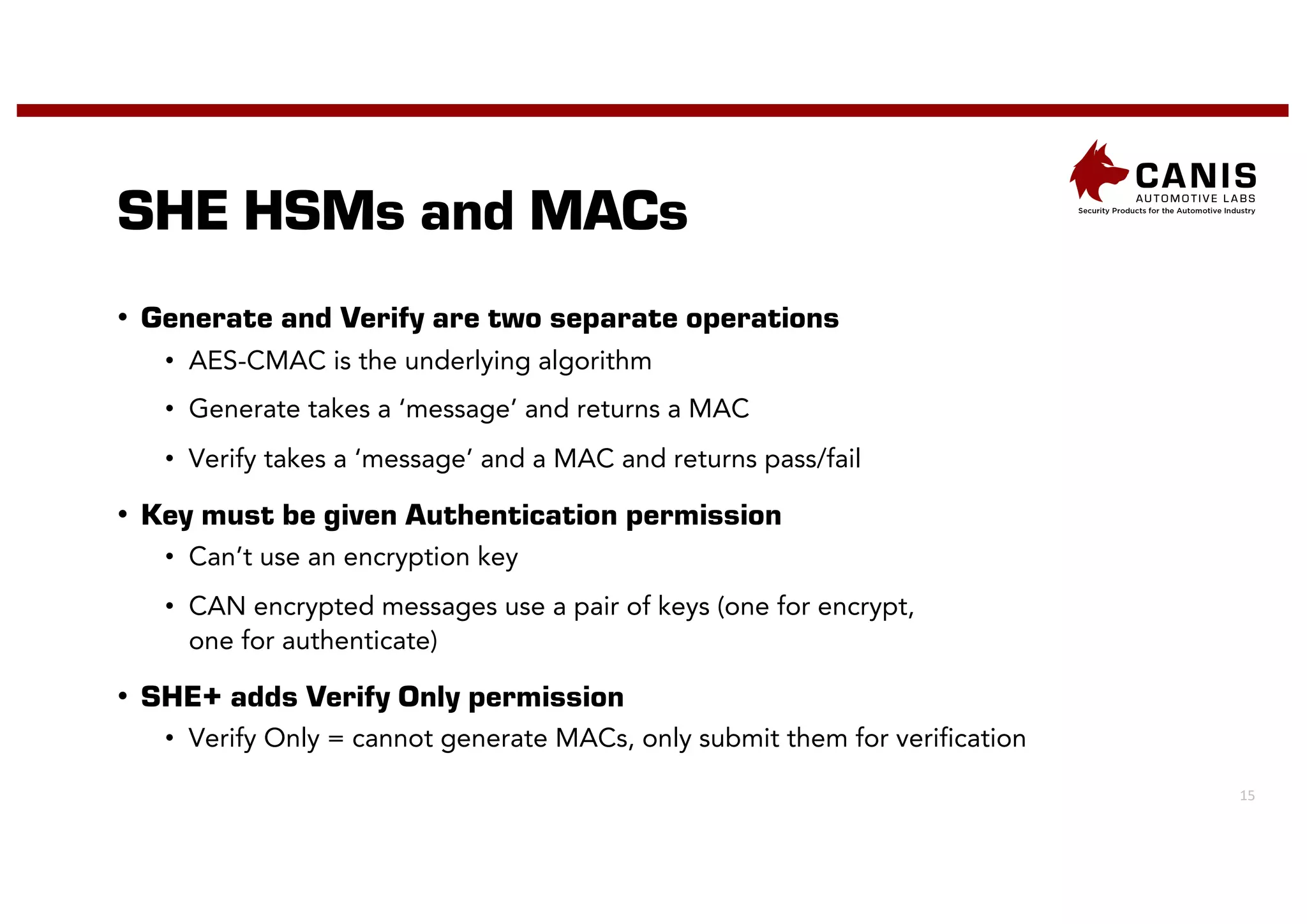
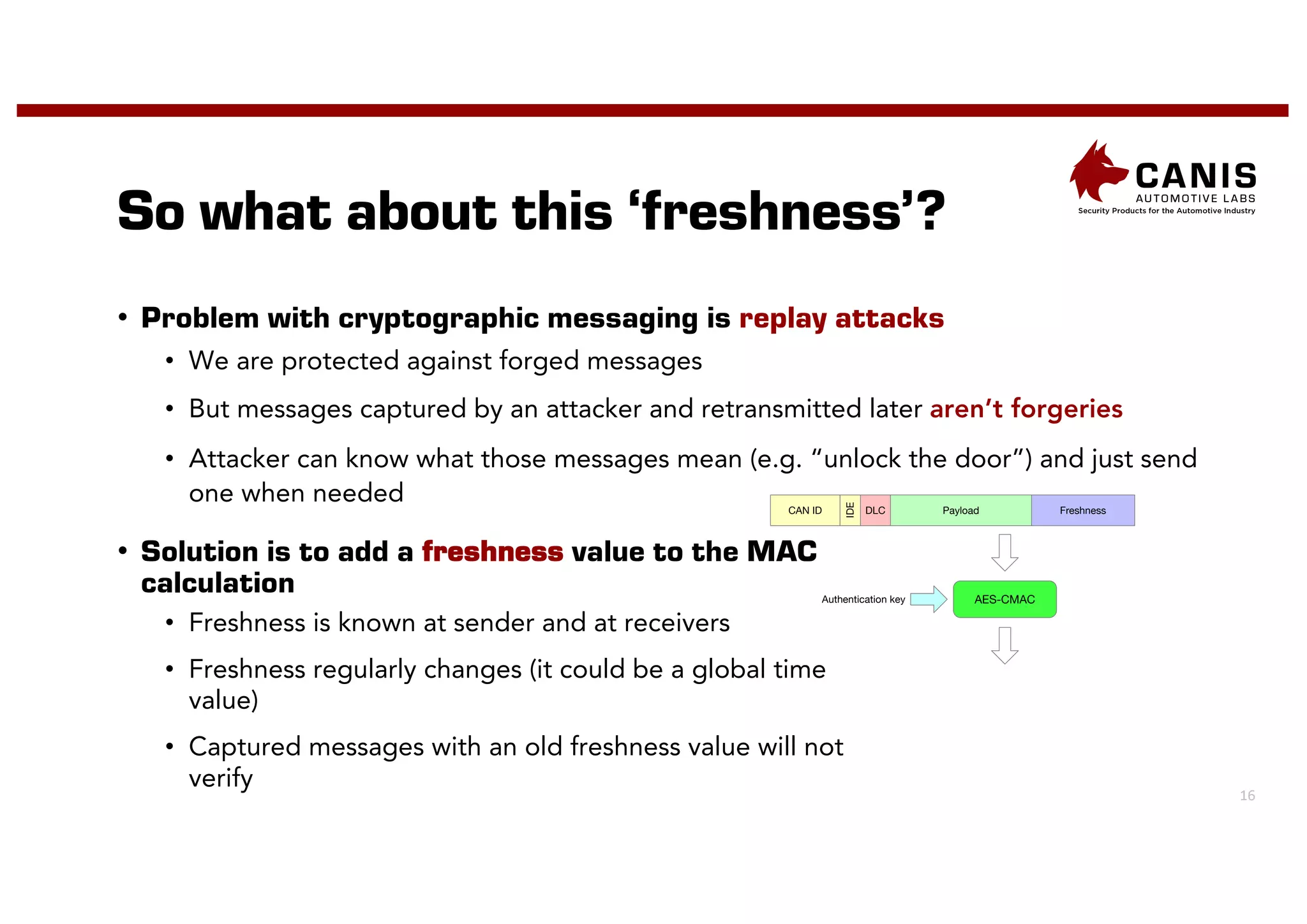
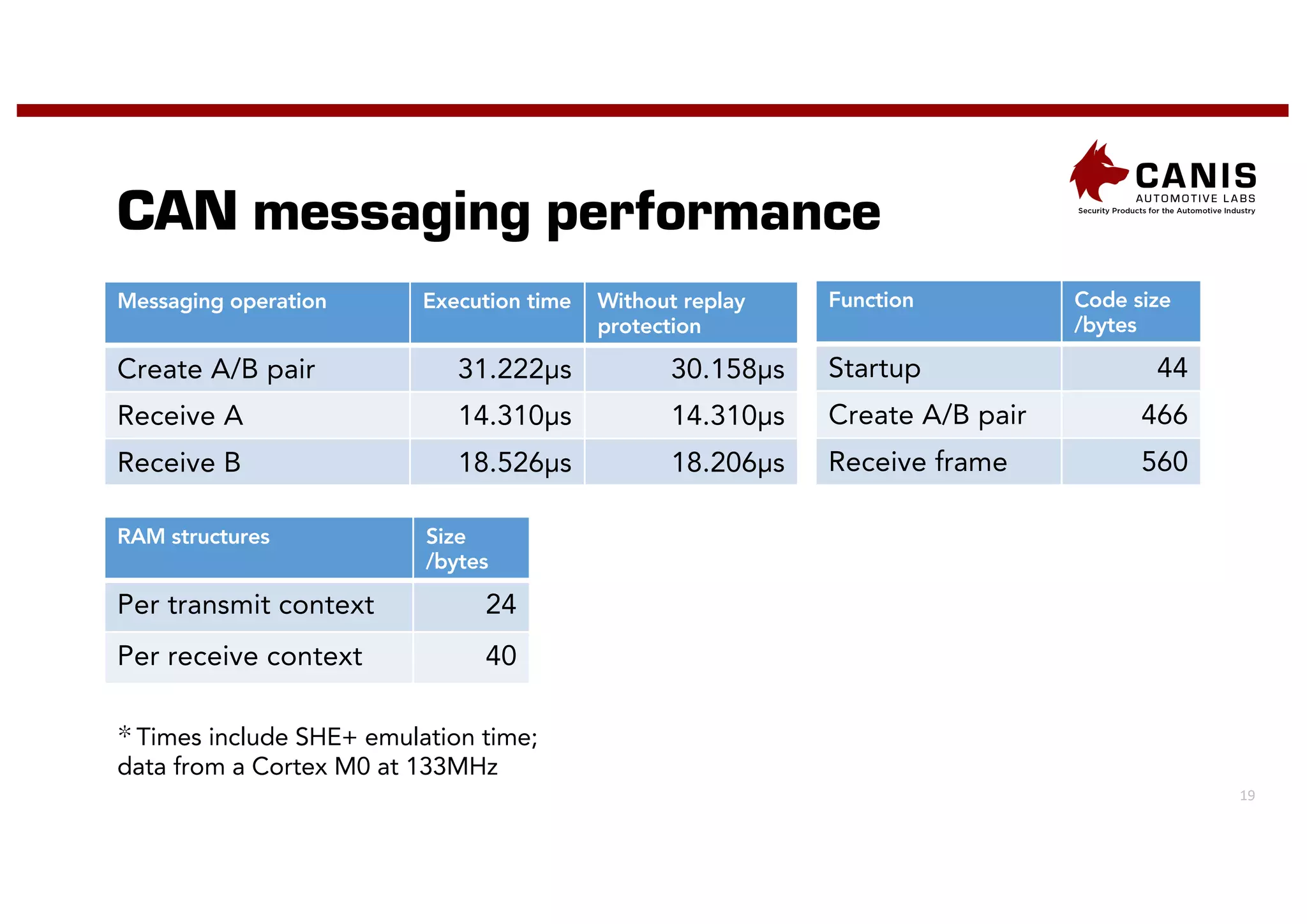
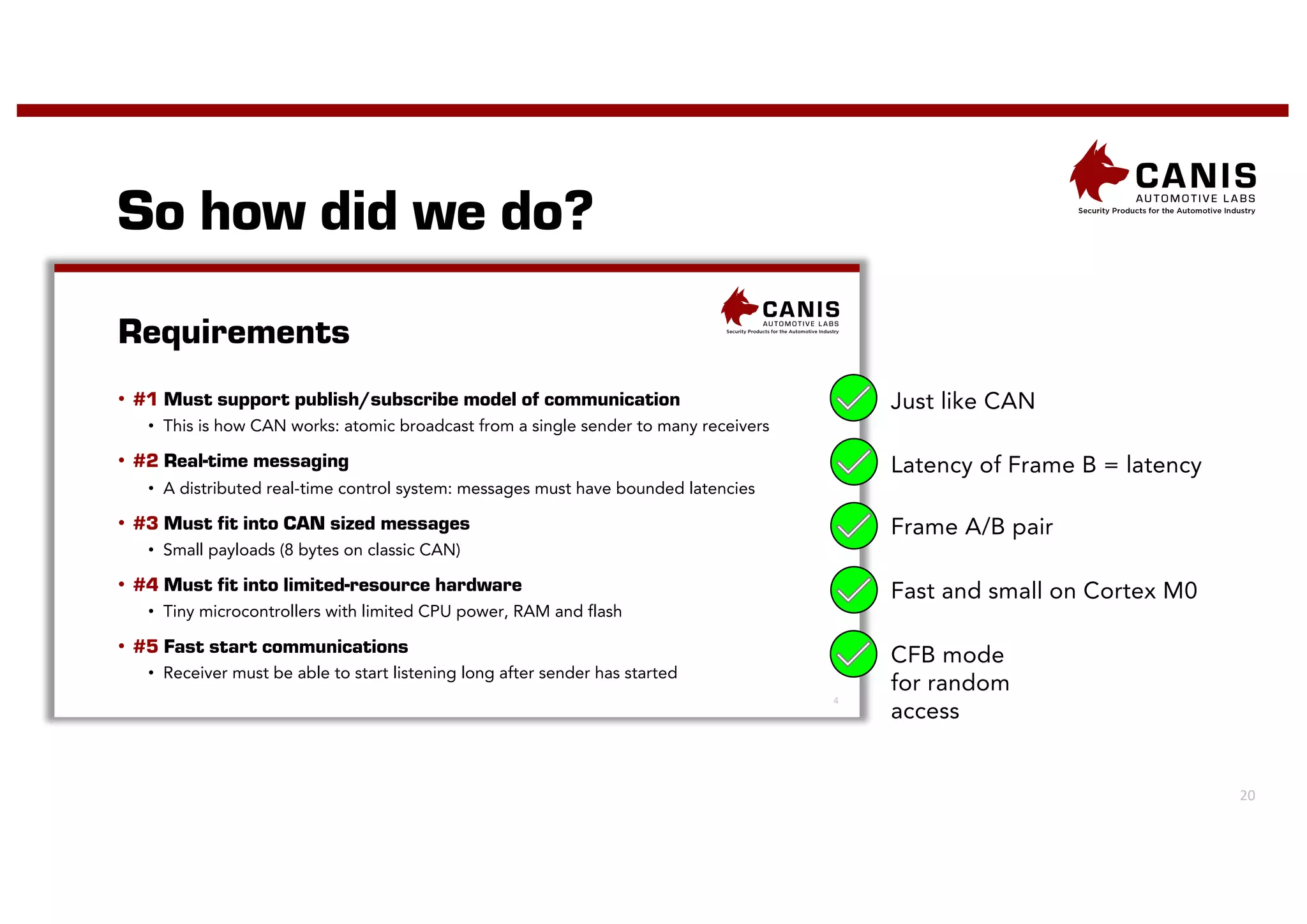
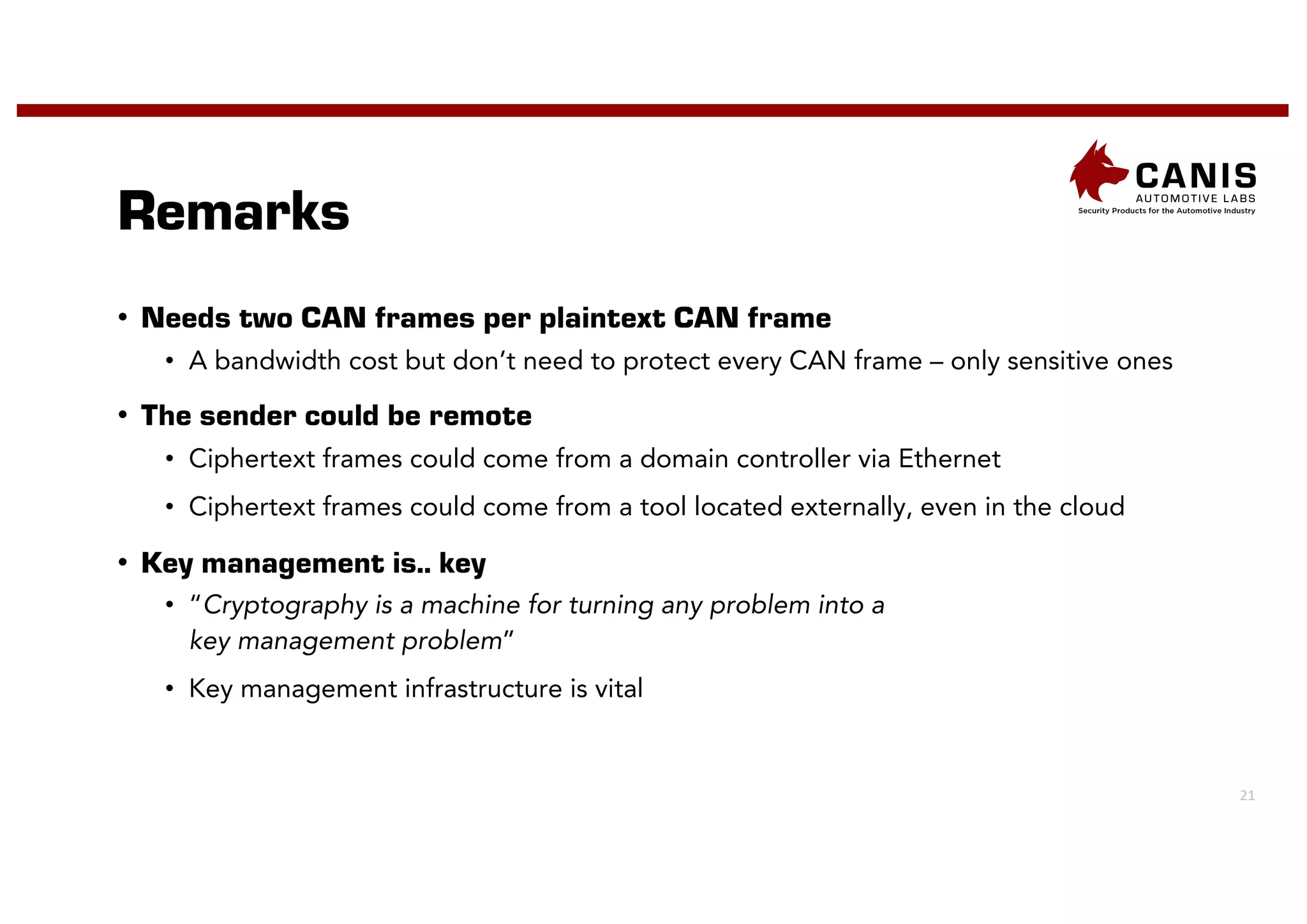
The document discusses the implementation of encryption on the CAN bus to enhance message secrecy and authenticity, addressing specific requirements for real-time communication and limited-resource hardware. It outlines cryptographic primitives used for encryption, detailing operational processes for message creation and verification, including the need for measures against replay attacks through freshness values. The document concludes with a mention of Canis Labs' Cryptocan, which implements the discussed techniques and offers a platform for evaluation and prototyping.