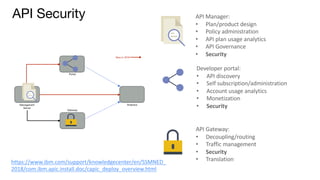
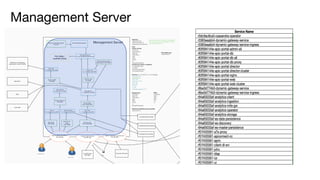
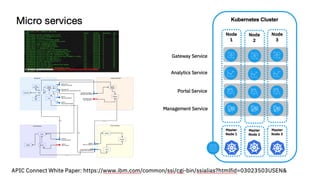
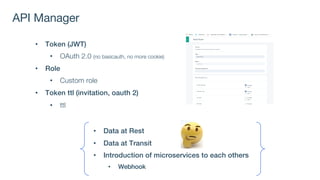
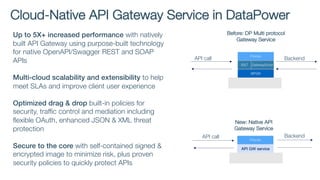
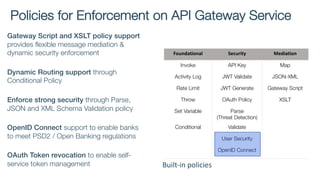
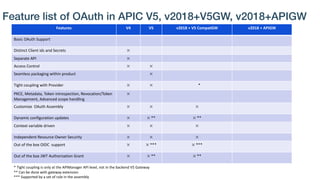
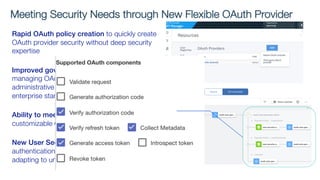
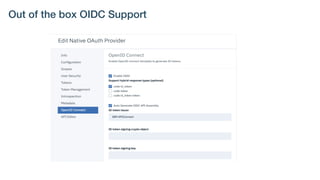
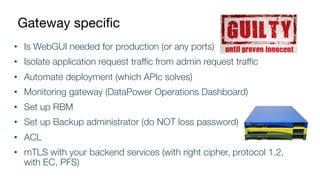
The document details best practices for security using IBM's API Connect and DataPower, emphasizing the importance of confidentiality and performance metrics. It outlines various security mechanisms, including API management, authentication methods, and the integration of advanced threat detection technologies. Additionally, it highlights features such as OAuth support and blockchain compliance for API security, accompanied by guidelines for monitoring and deploying secure APIs.