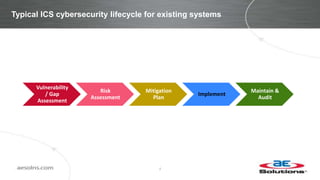
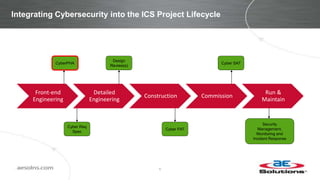
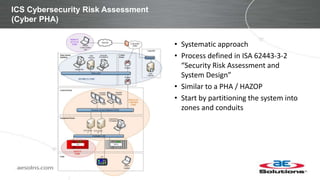
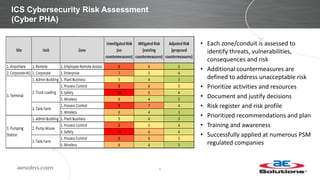
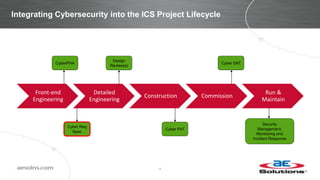
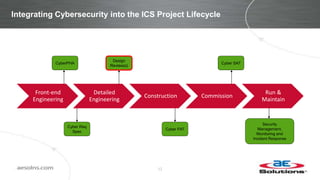
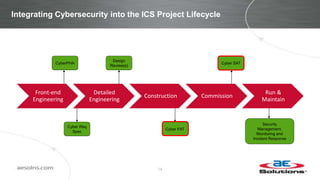
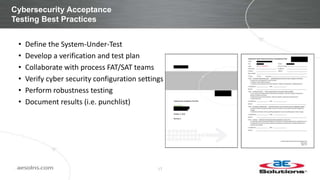
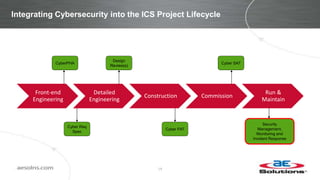
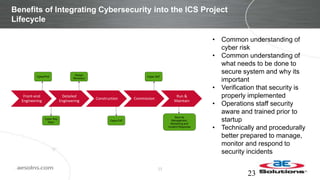
This document discusses integrating cybersecurity into the lifecycle of a new industrial control system (ICS) project. It recommends conducting a cybersecurity risk assessment early using ISA 62443 methodology. This informs developing cybersecurity requirements and reviewing designs to ensure requirements are met. It also recommends cybersecurity acceptance testing before commissioning to verify secure configurations and robustness. Maintaining security management processes is key after system handover to operations. Benefits include a common understanding of risks addressed and better preparation to manage security long-term. Critical success factors include having achievable goals and clear roles/responsibilities.