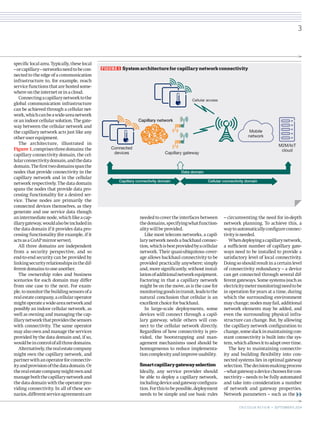
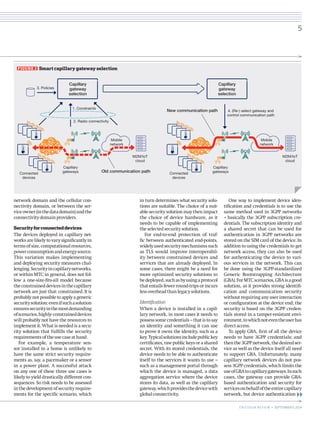
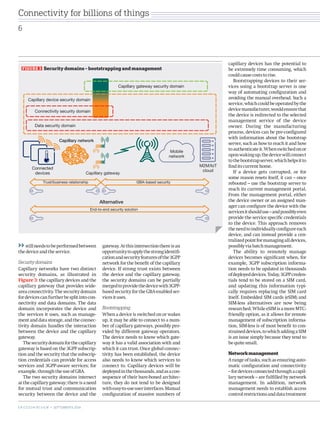
Capillary networks serve as localized, short-range communication systems that enhance connectivity for numerous devices, leveraging cellular network capabilities for efficiency and advanced functionality. These networks play a crucial role in the evolution towards machine-type communication and the Internet of Things (IoT), requiring low energy consumption and efficient gateway management for reliable operation. The document discusses the architecture, deployment challenges, and security considerations necessary for successfully integrating capillary networks into broader communication infrastructures.