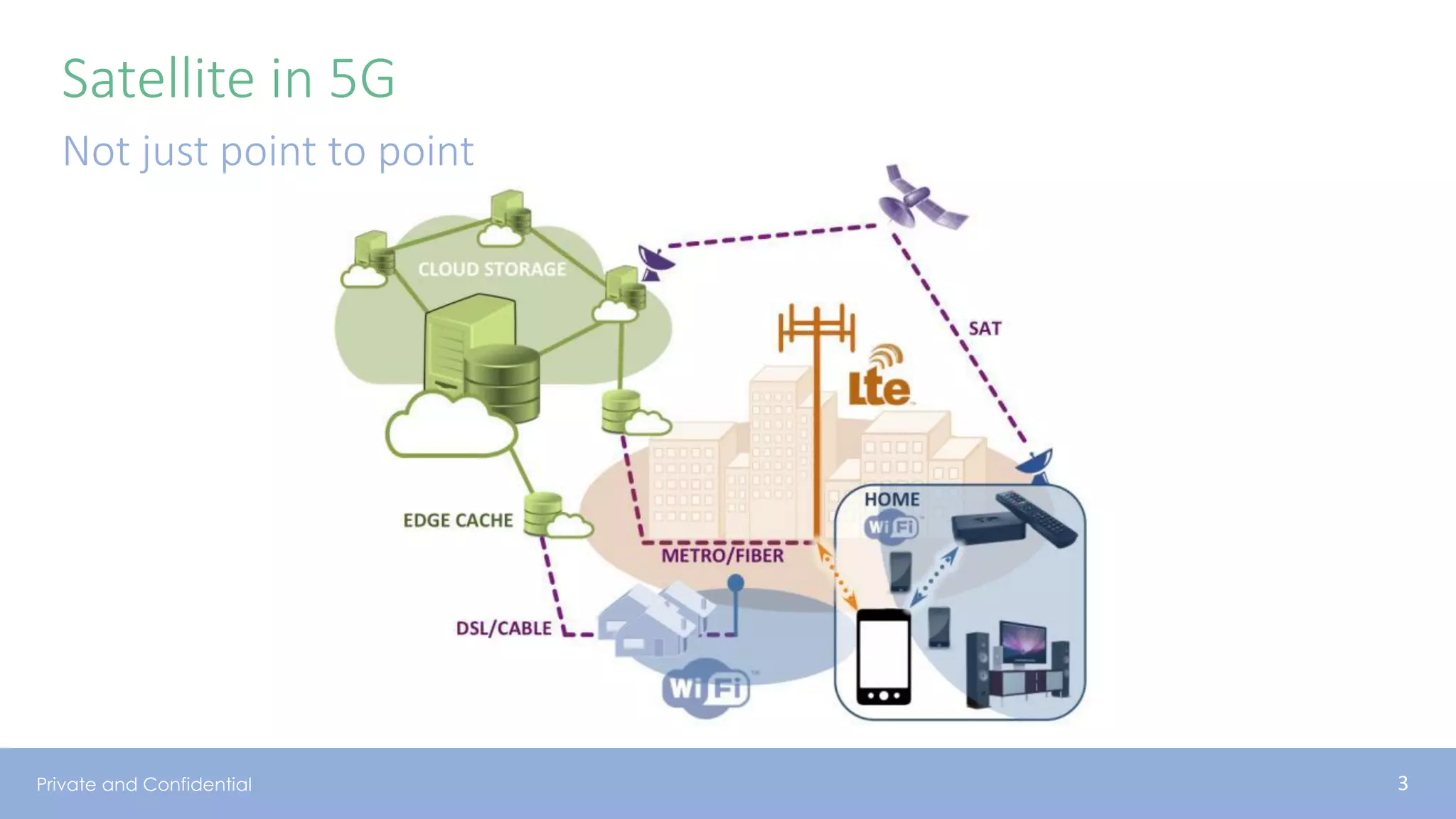
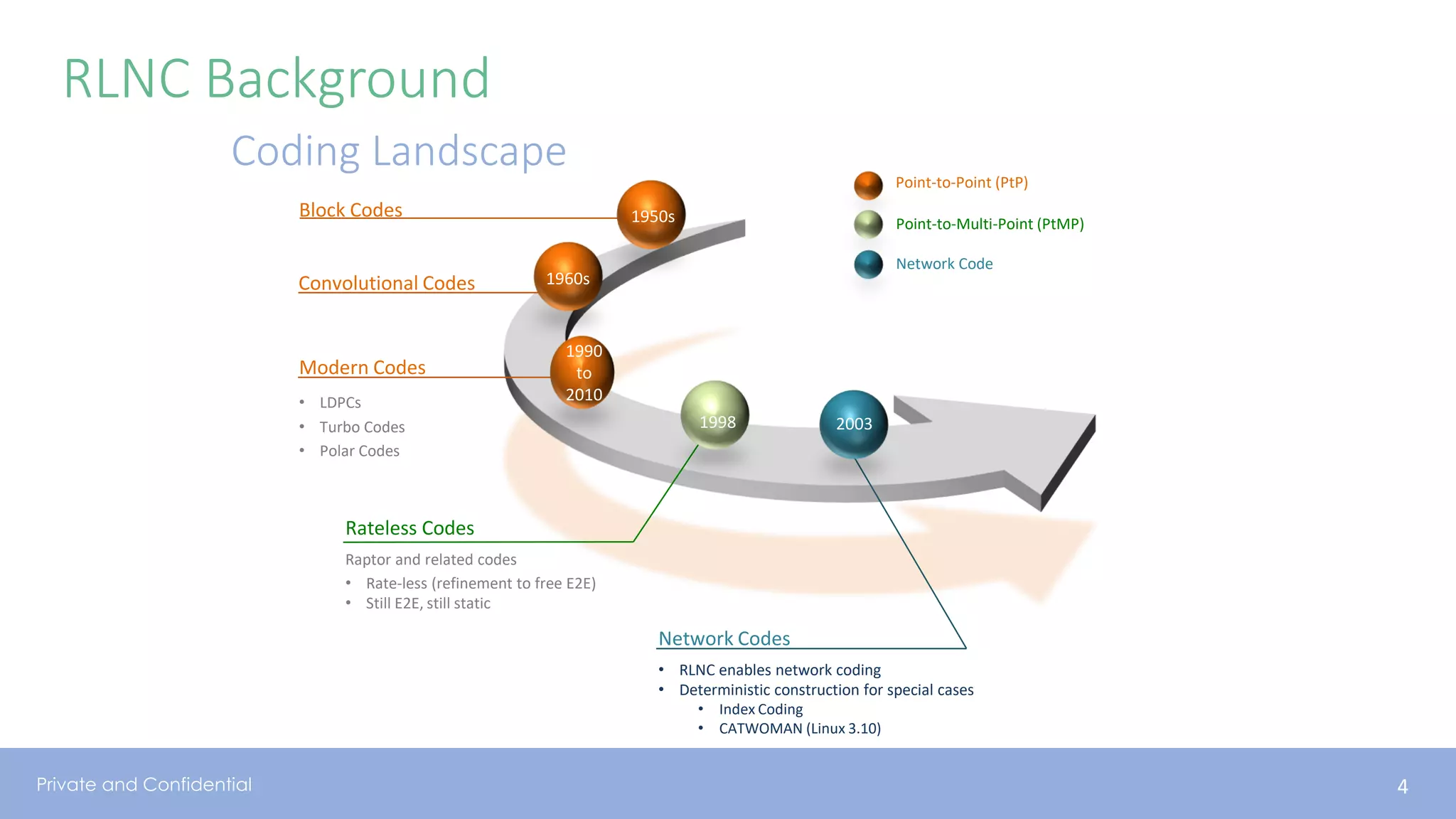
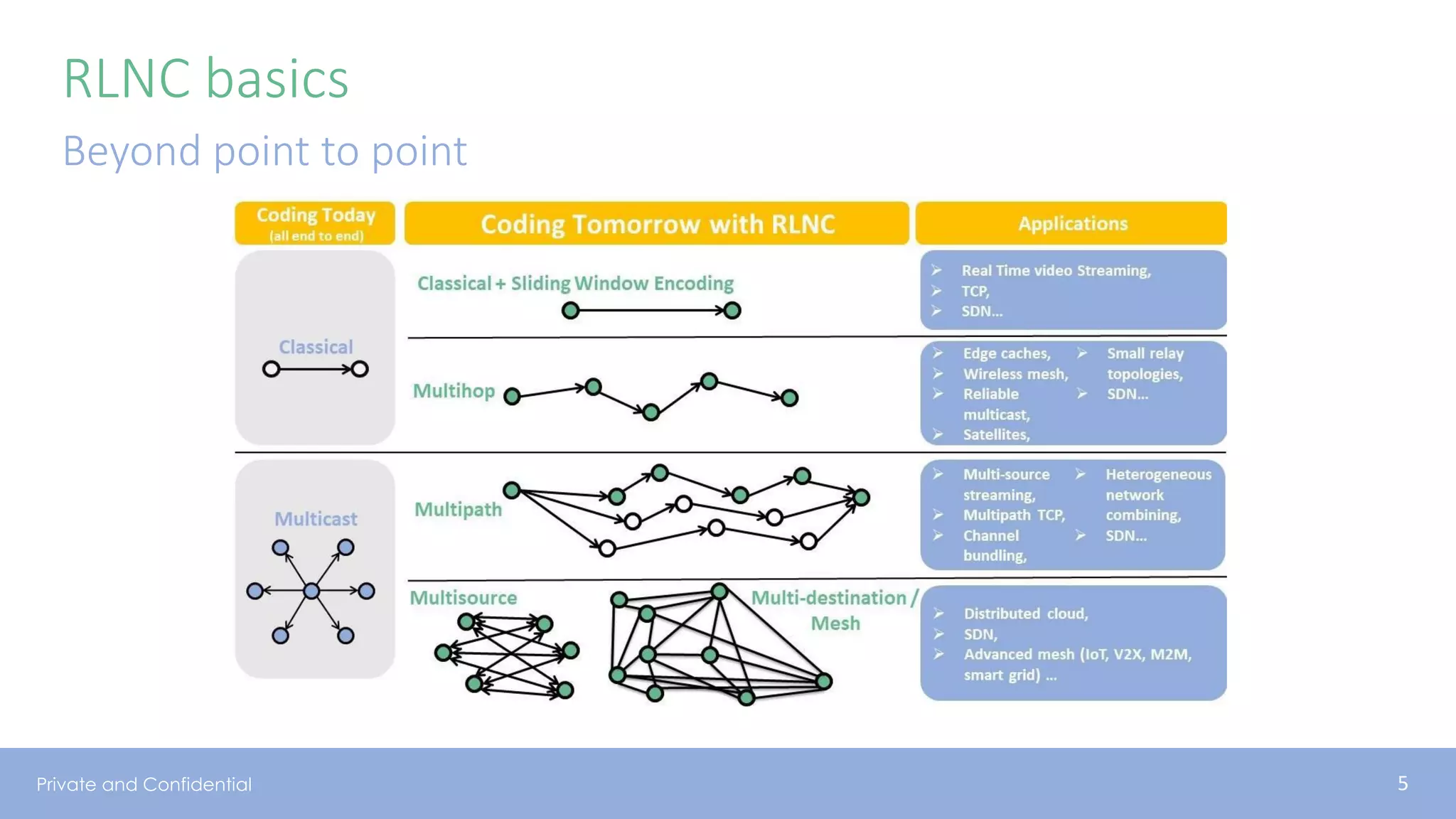
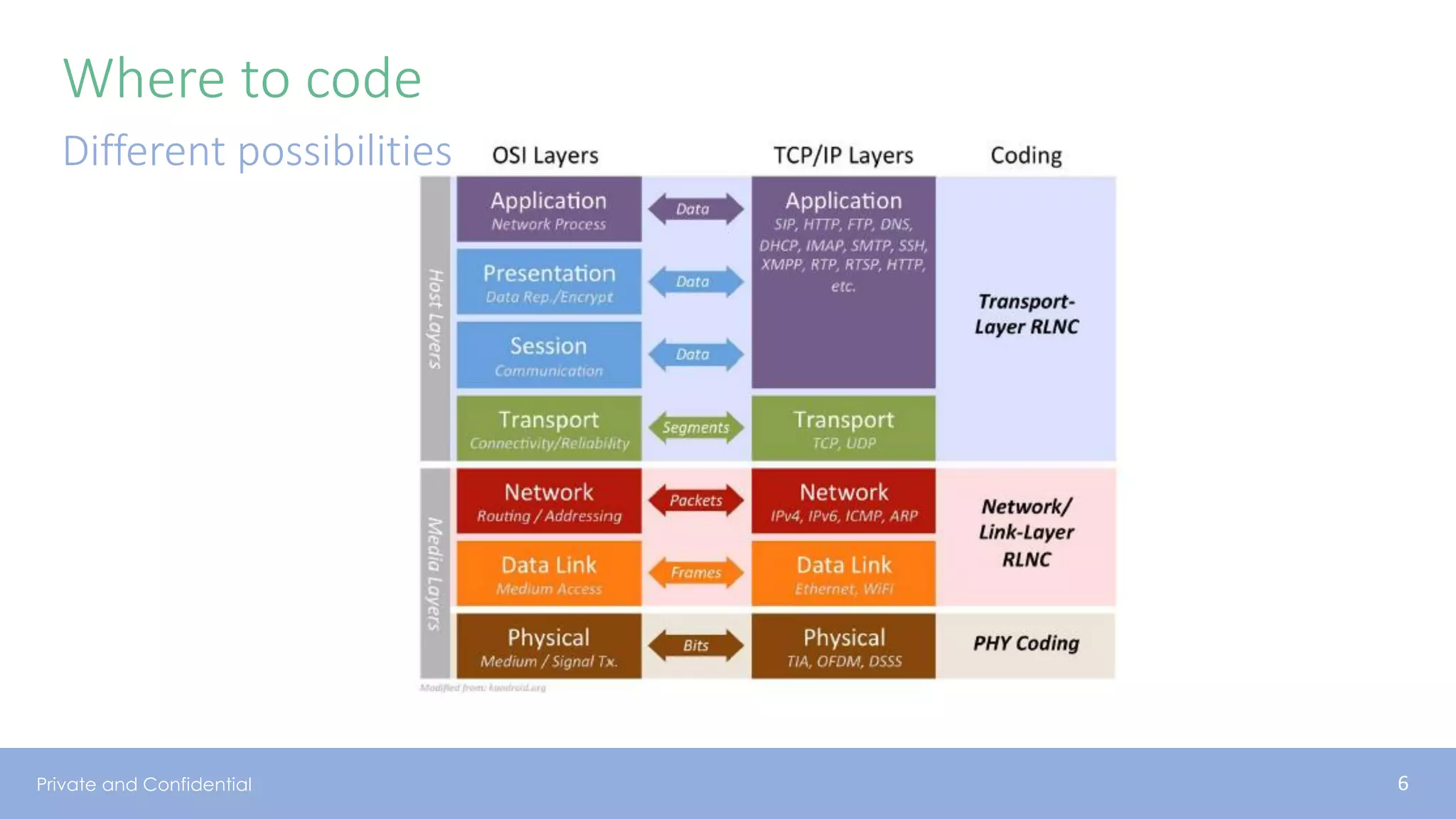
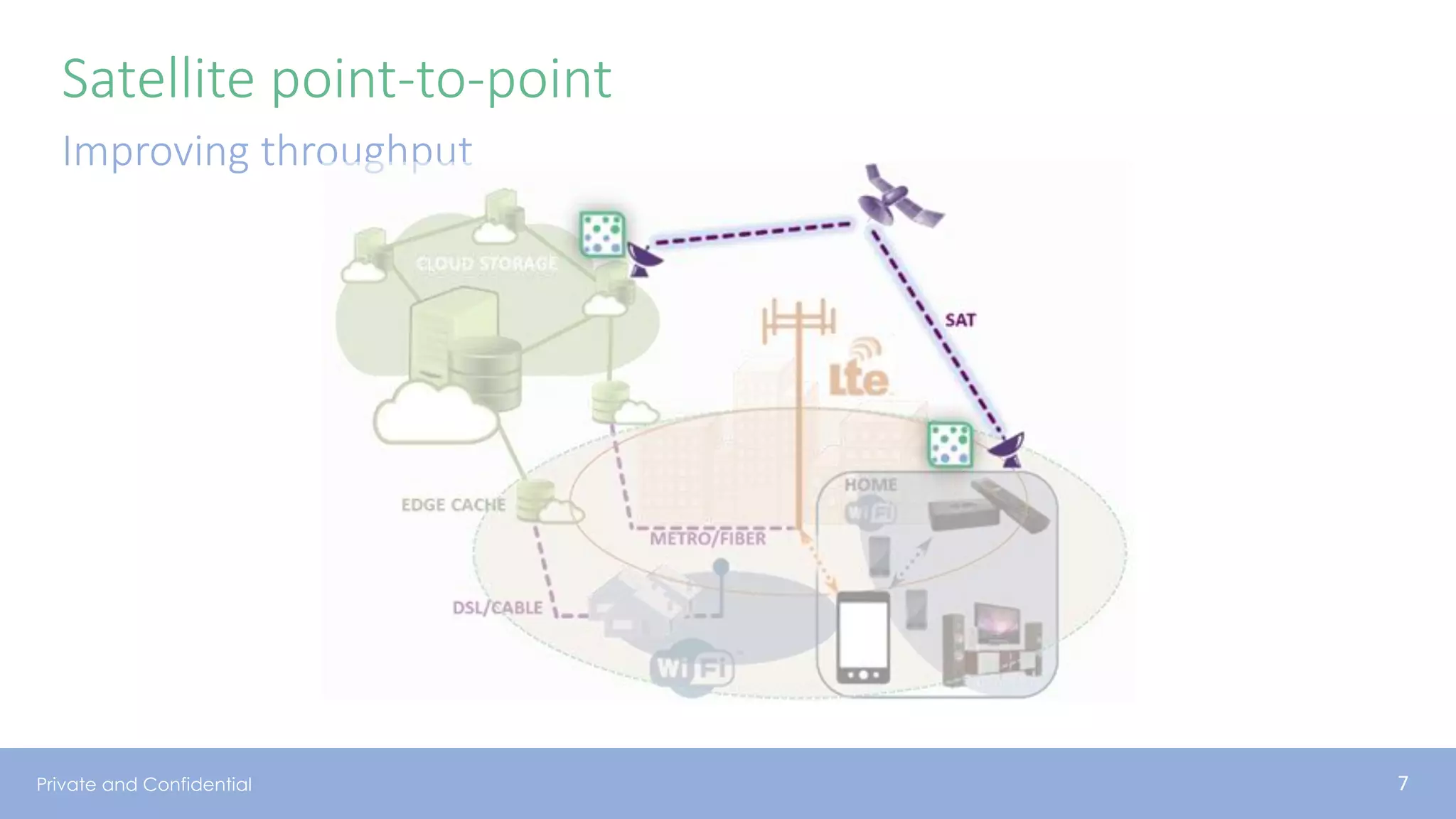
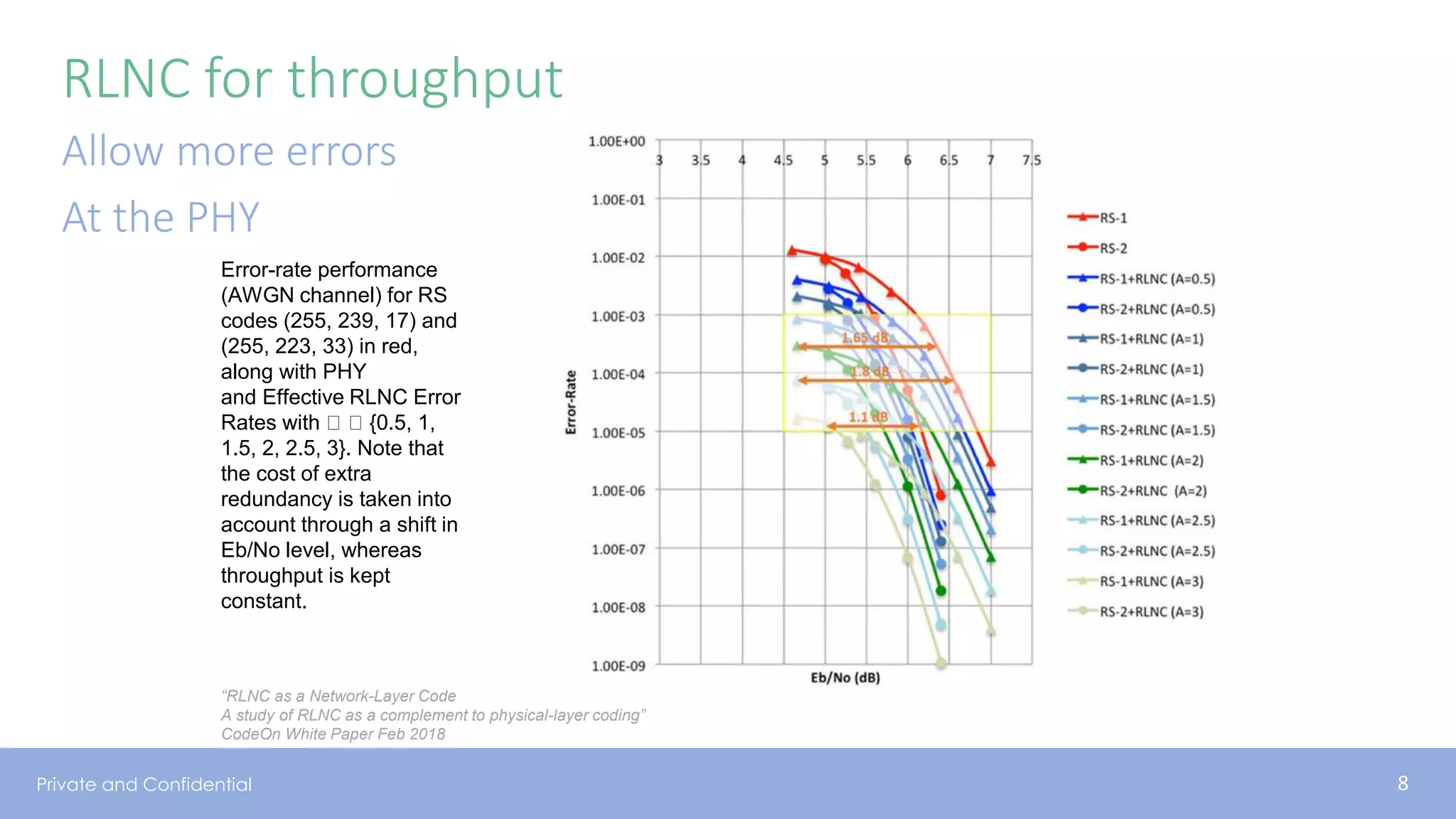
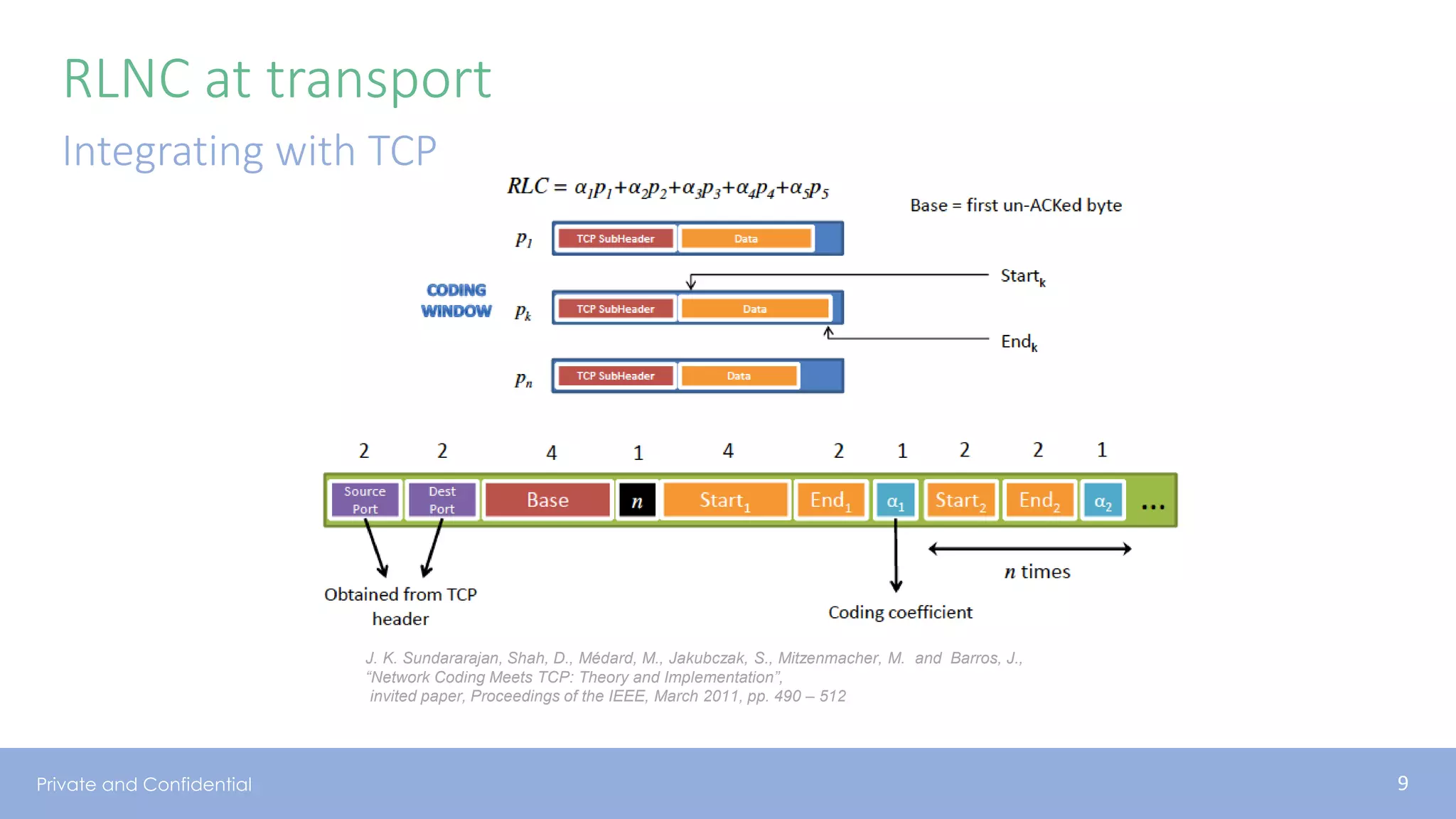
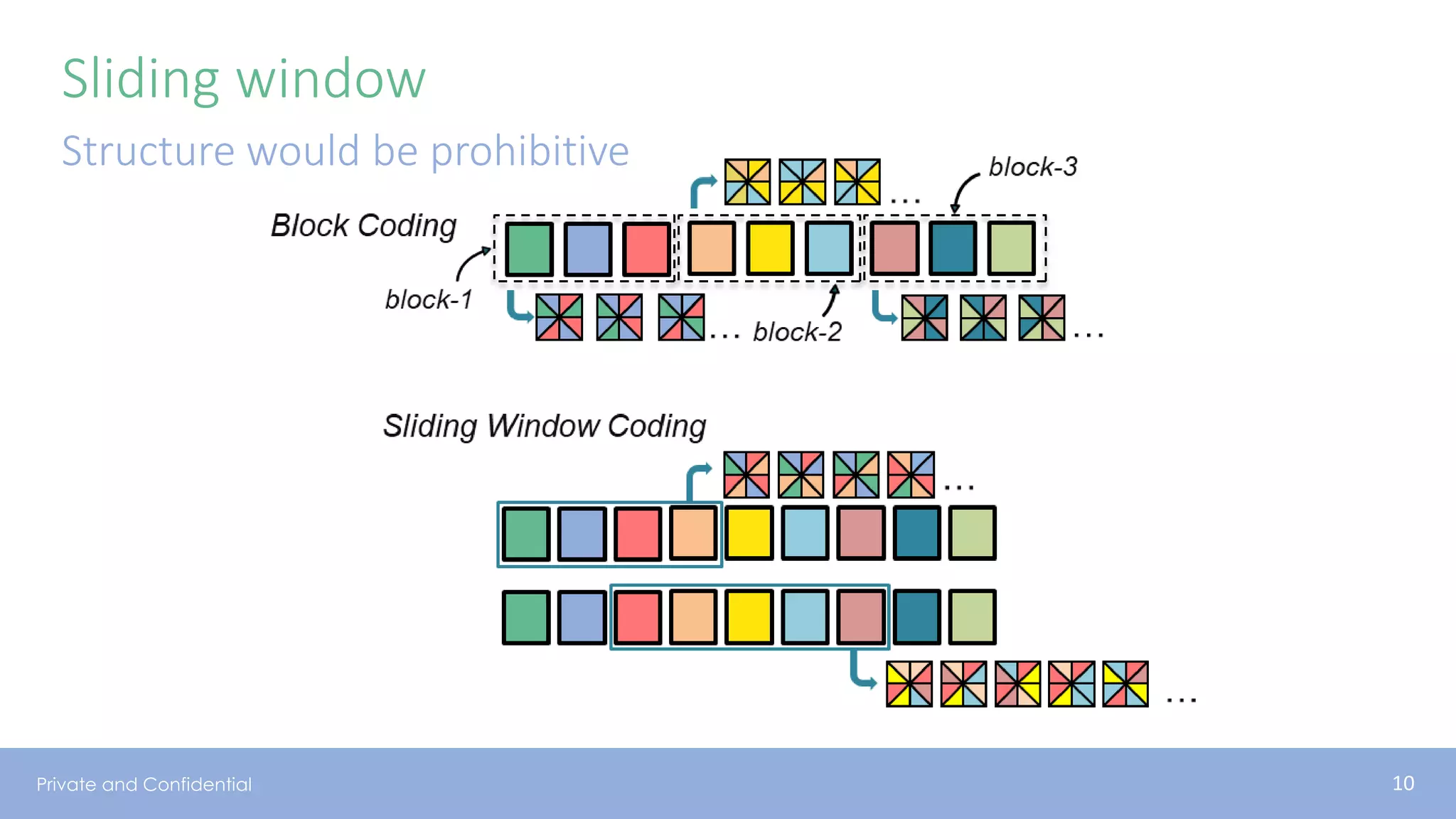
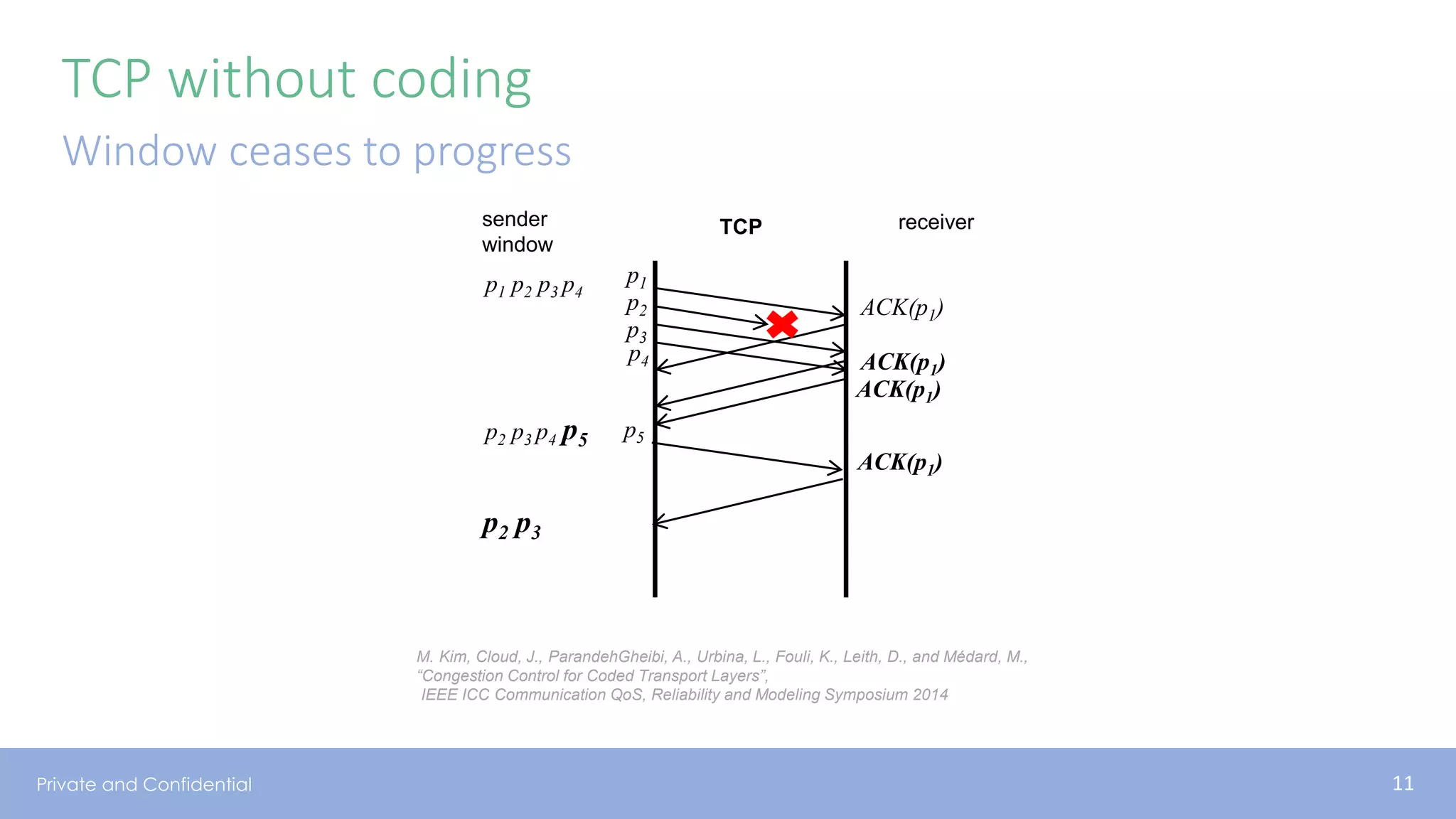
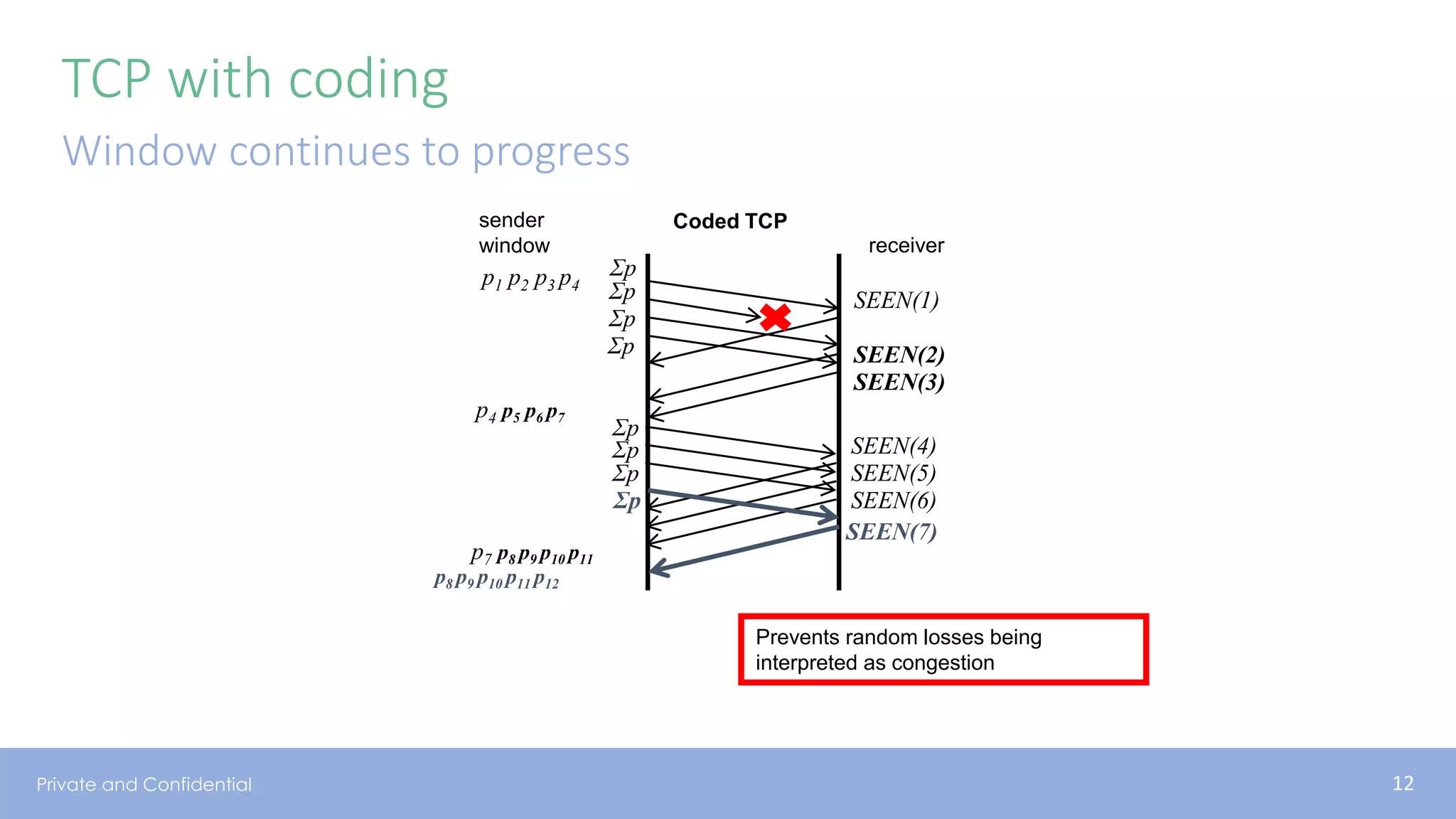
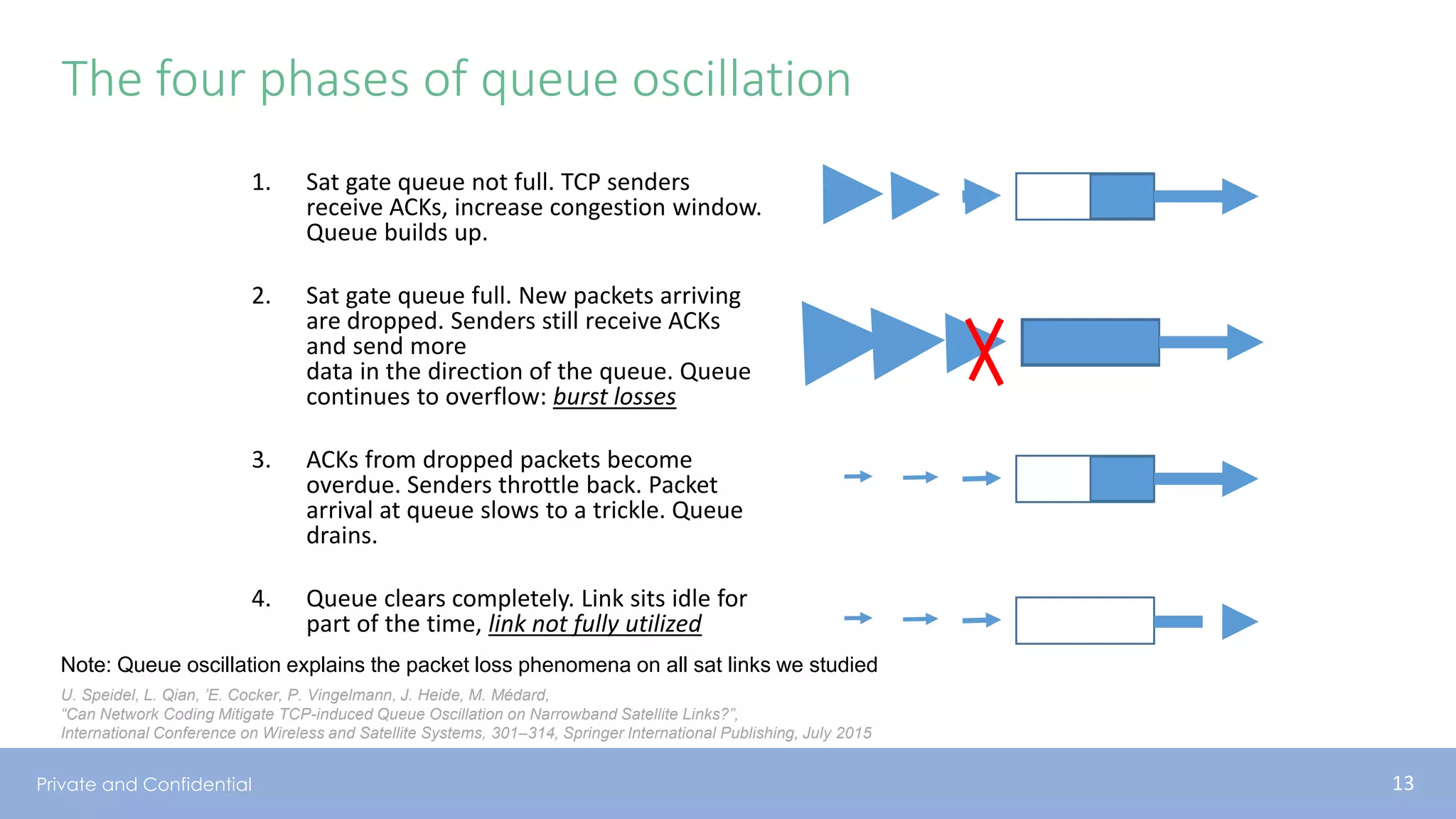
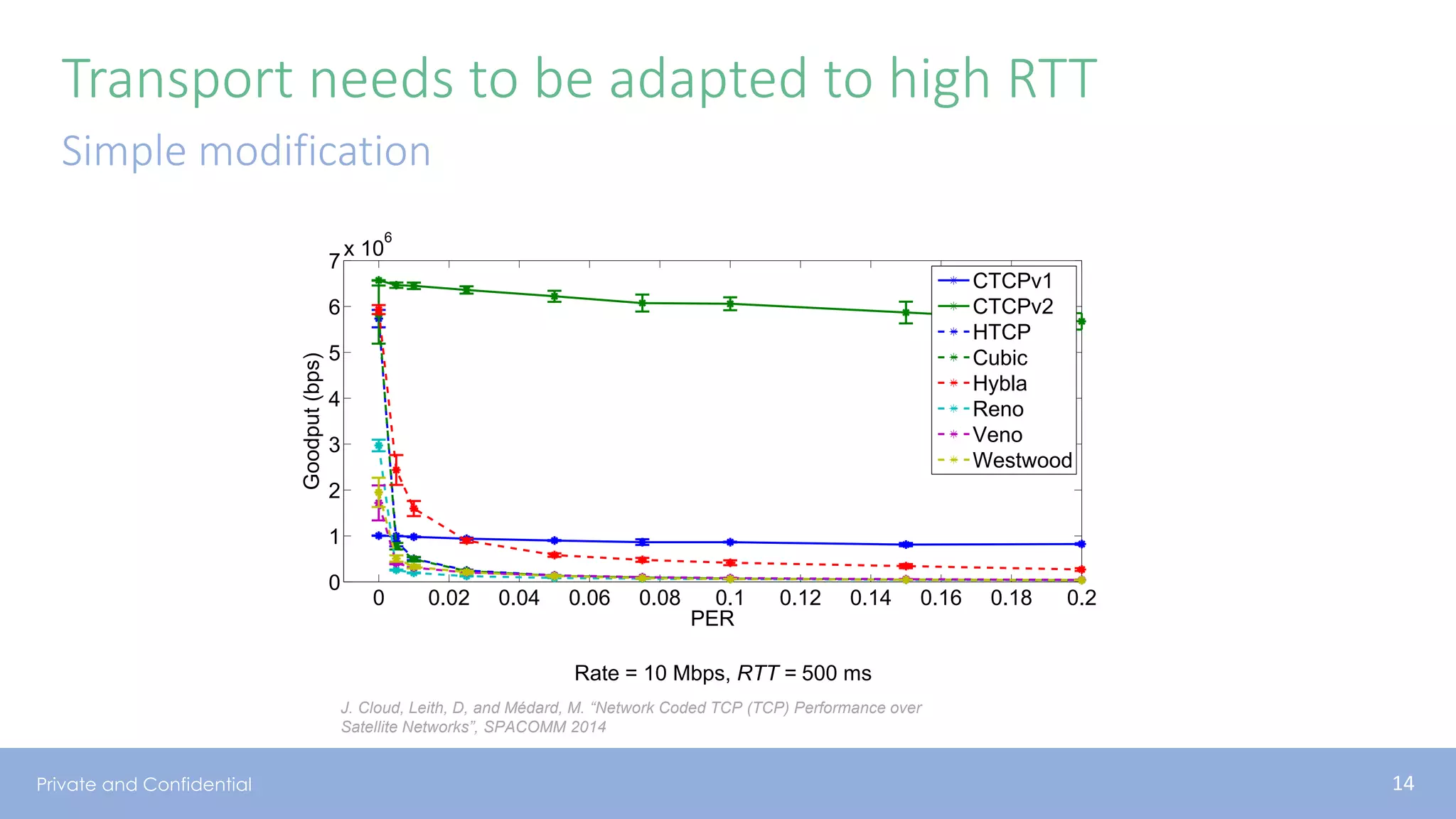
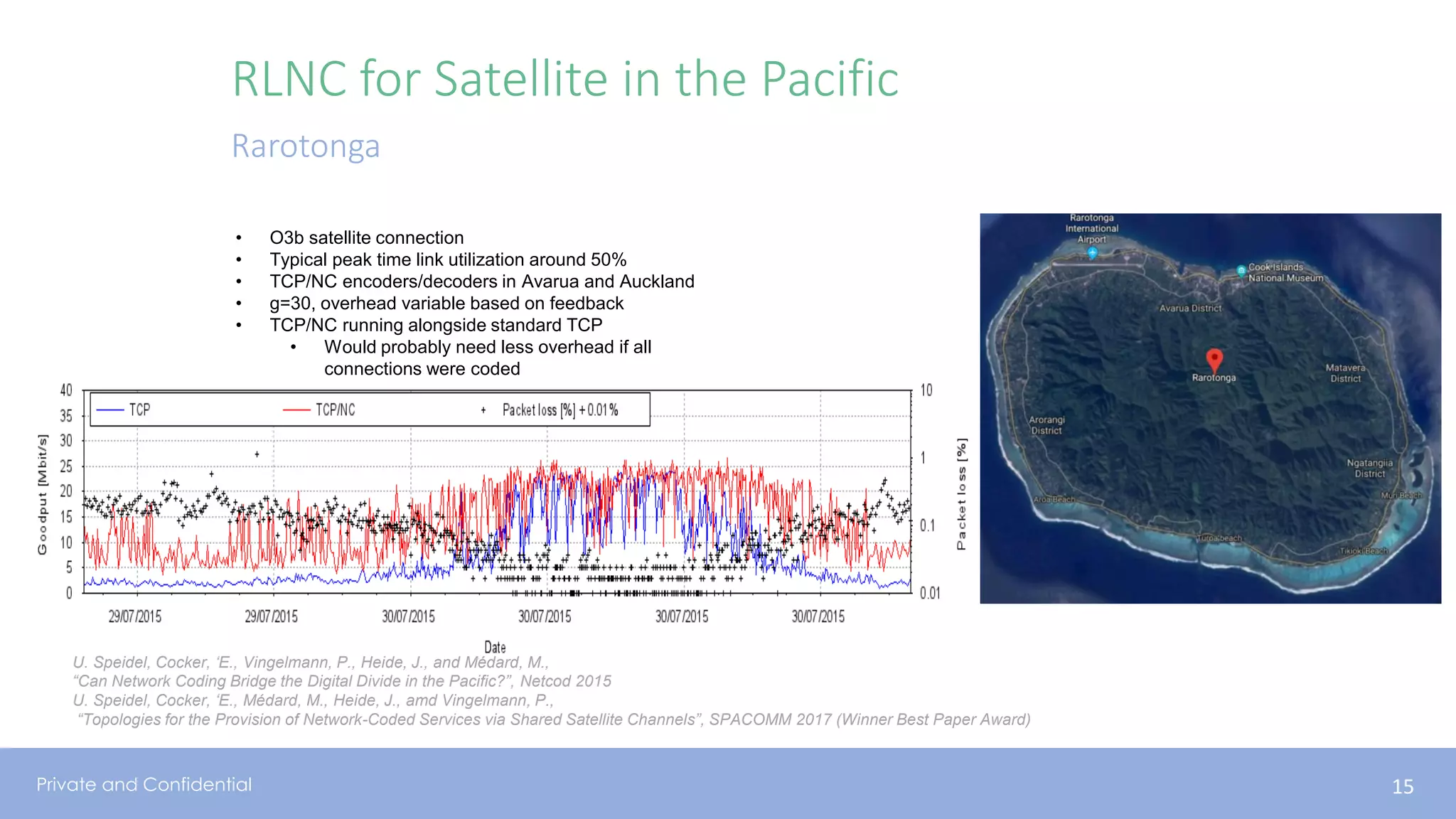
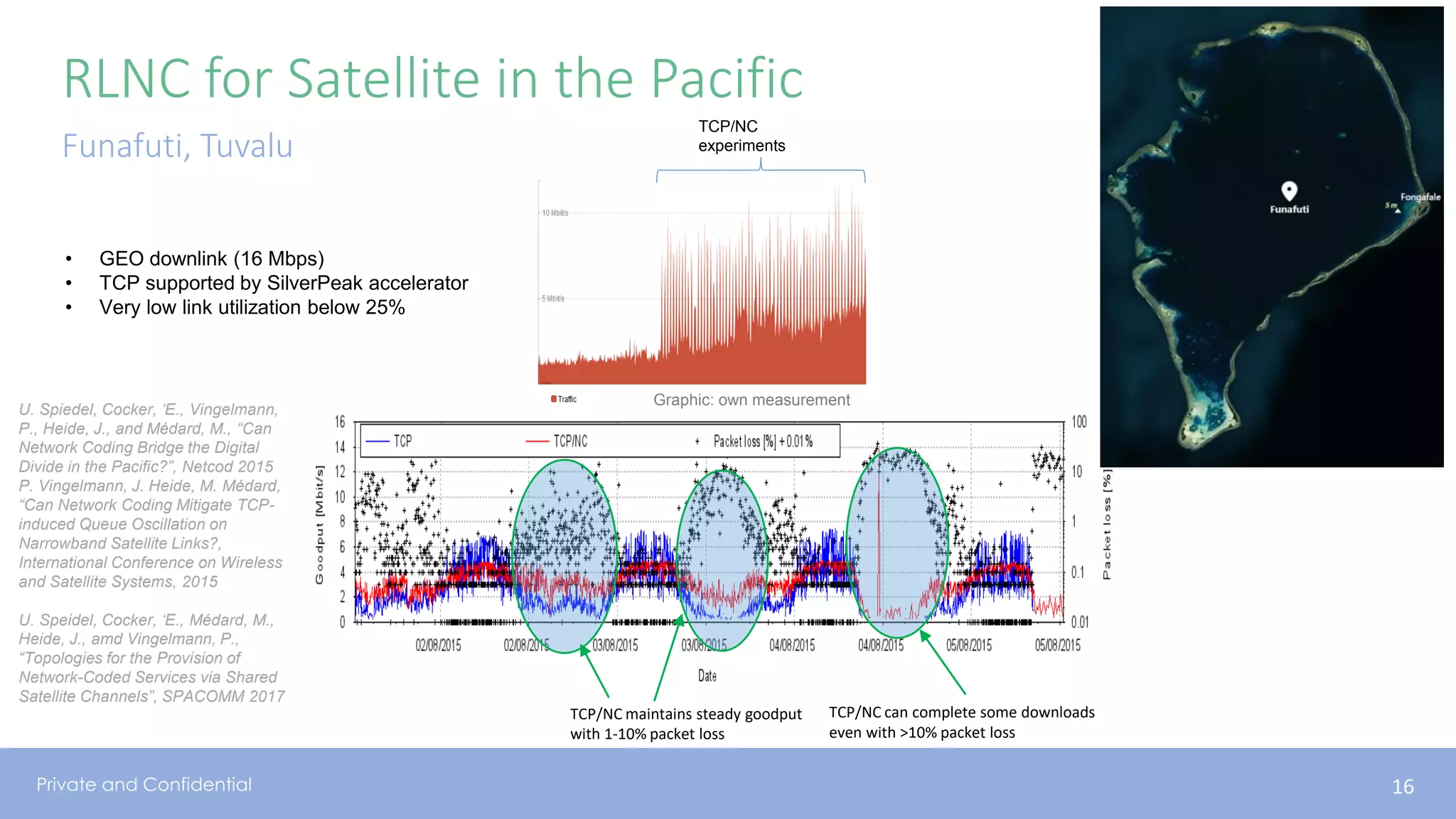
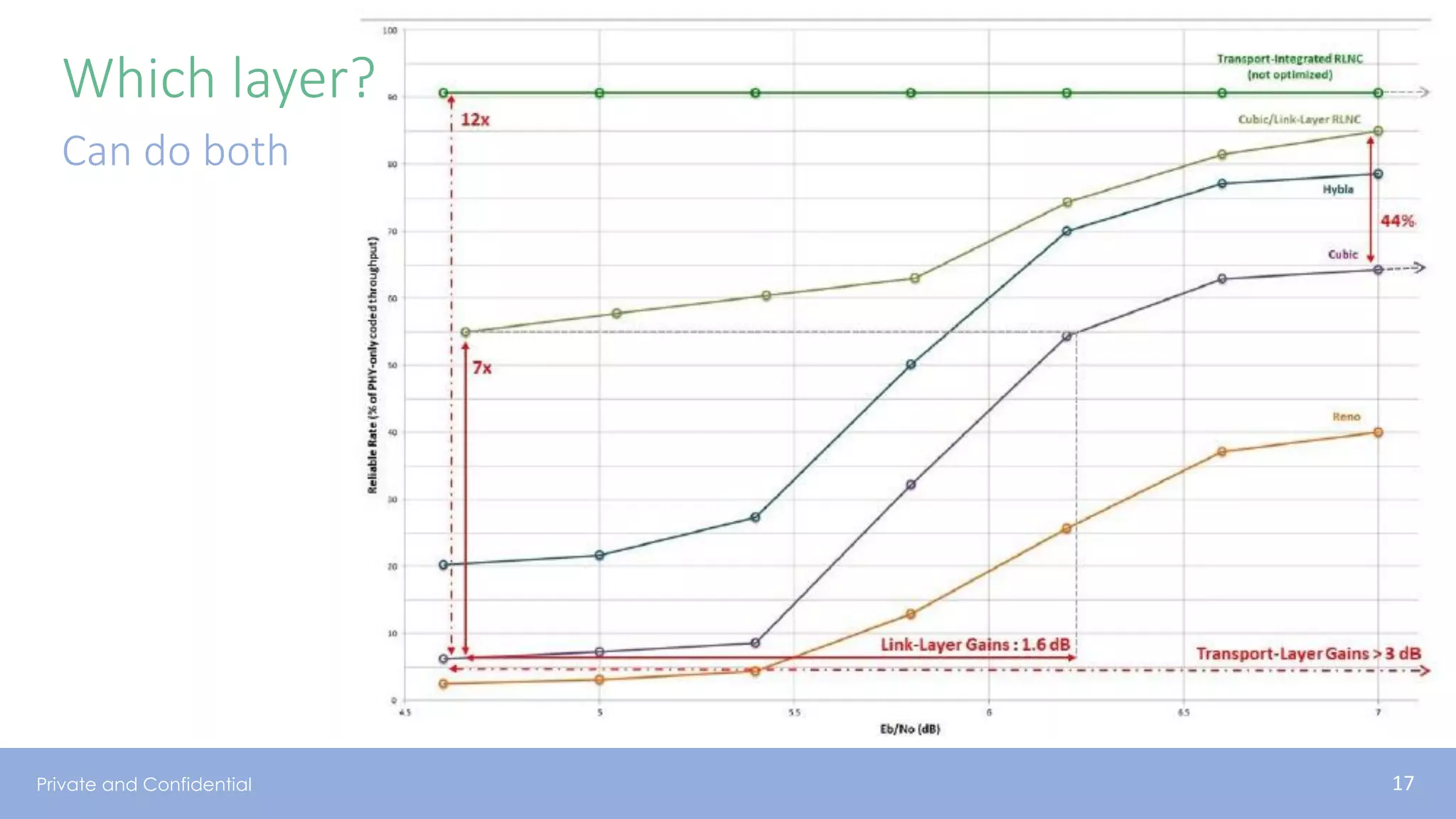
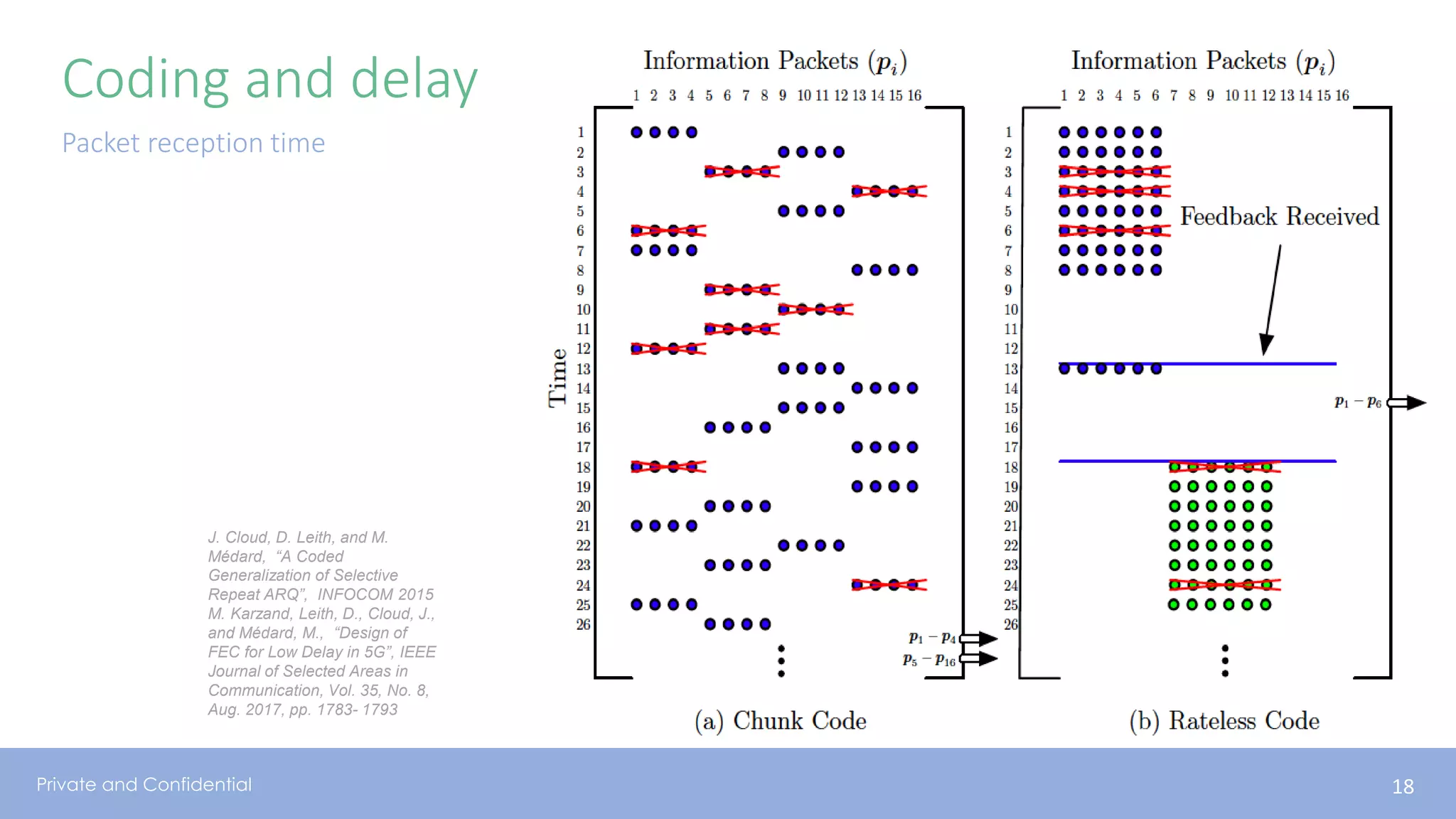
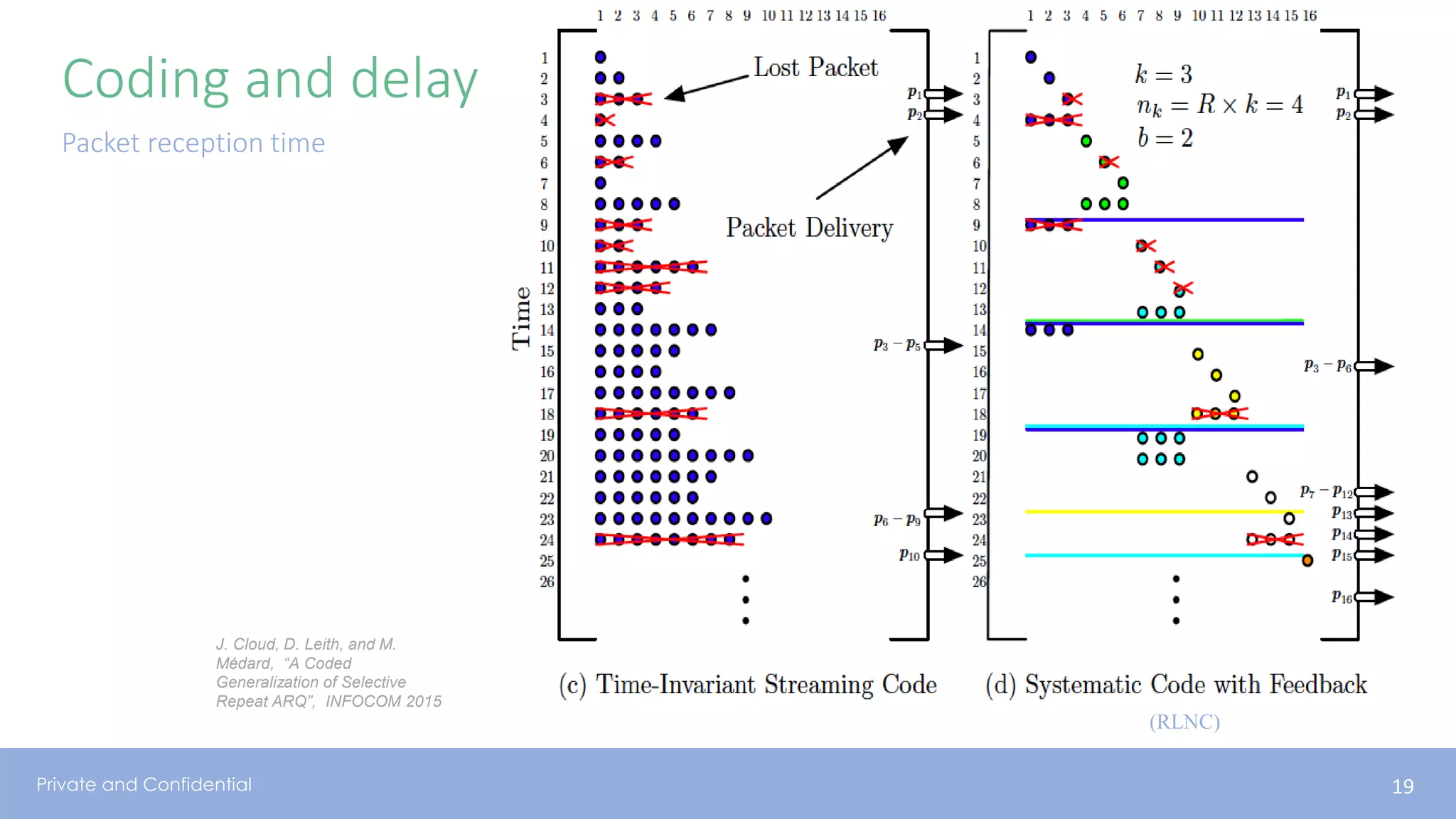
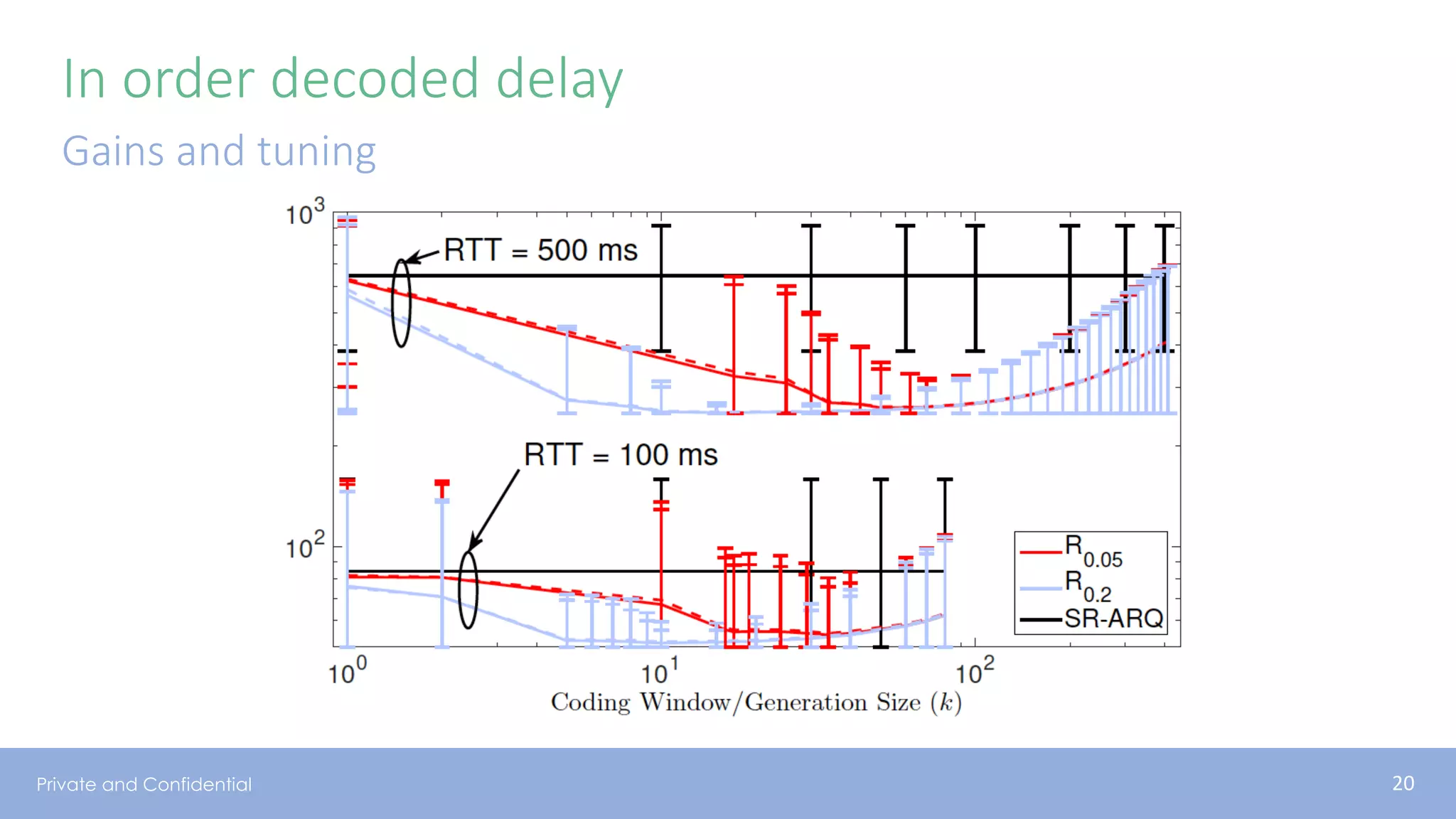
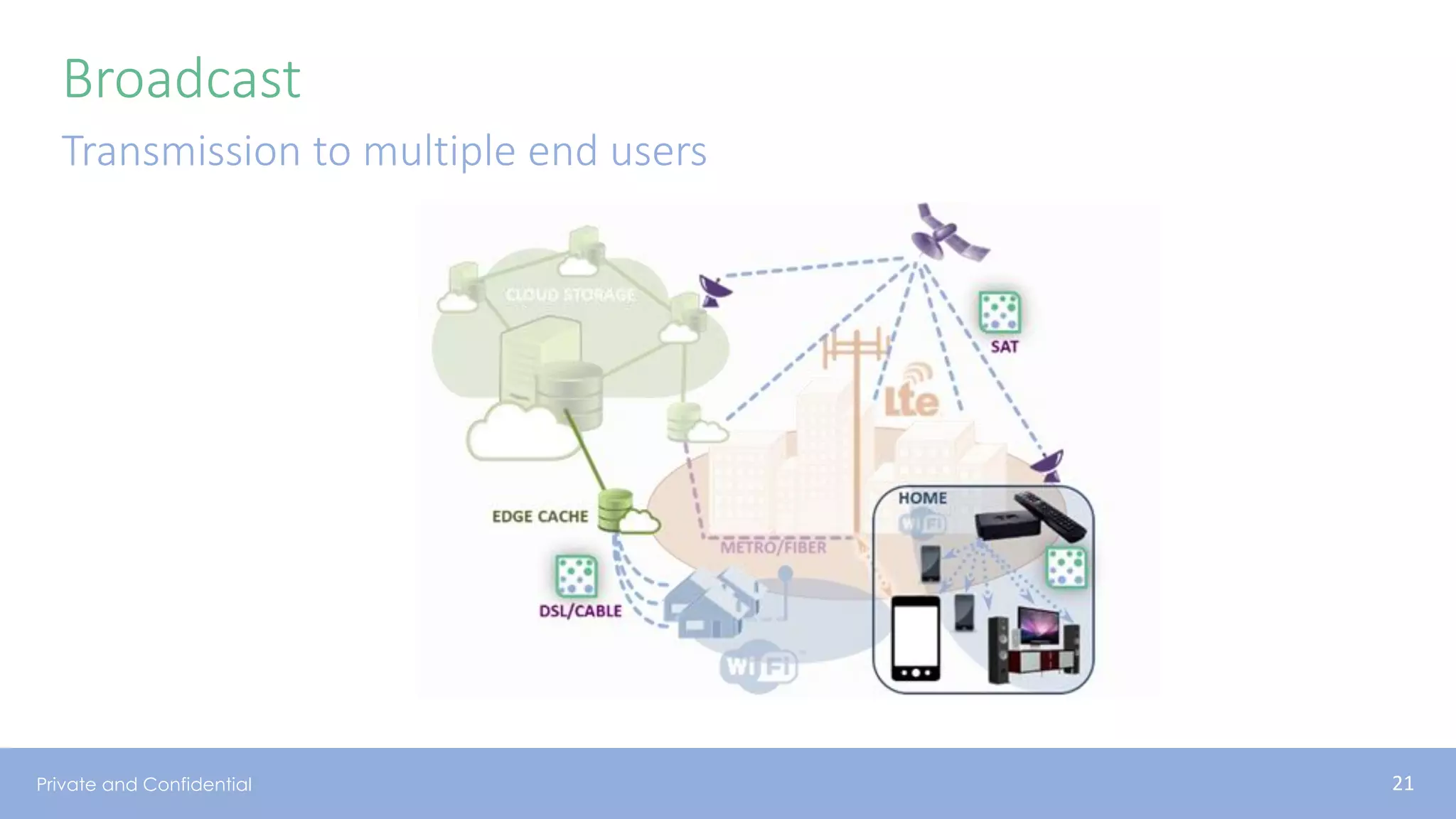
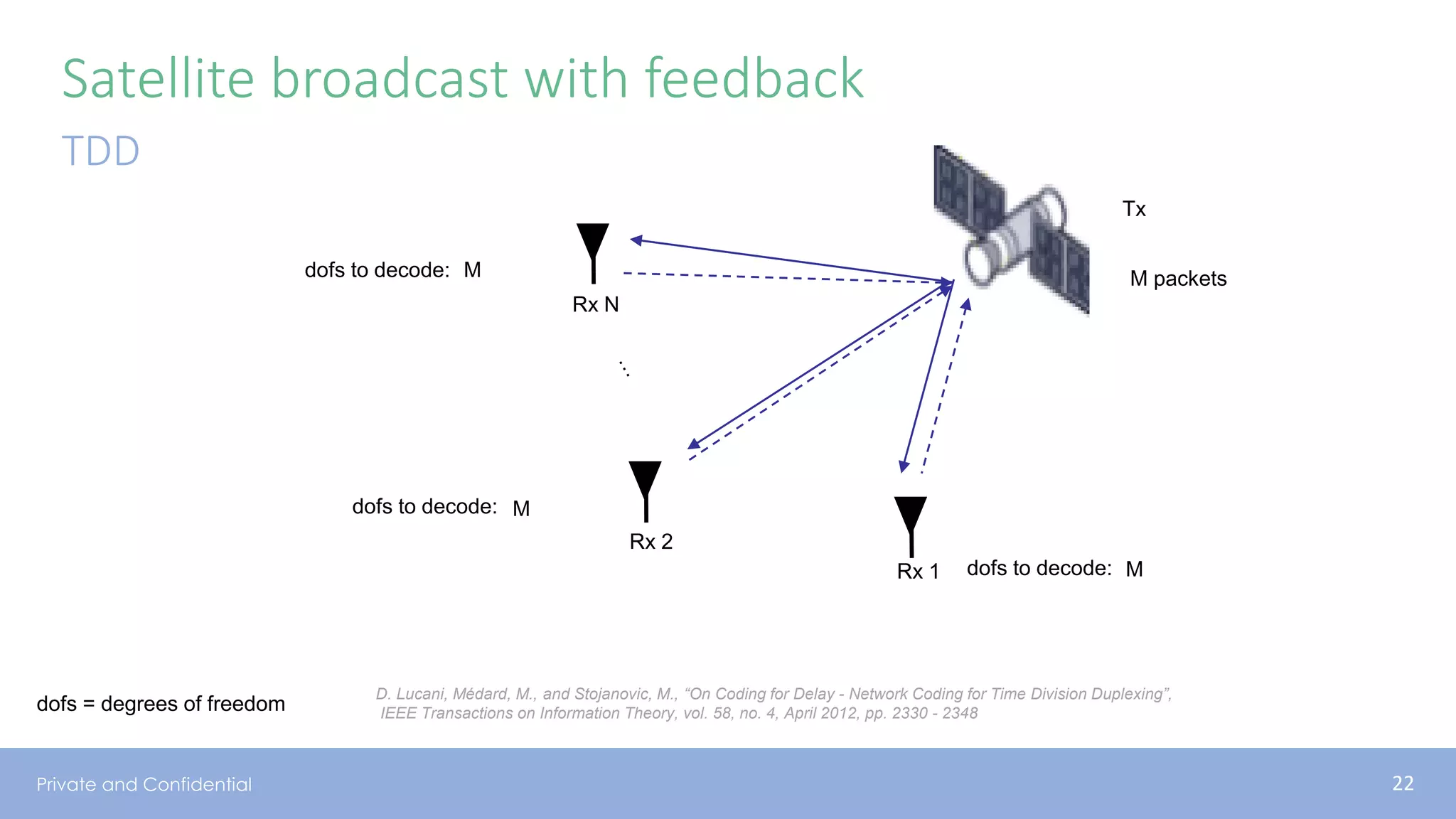
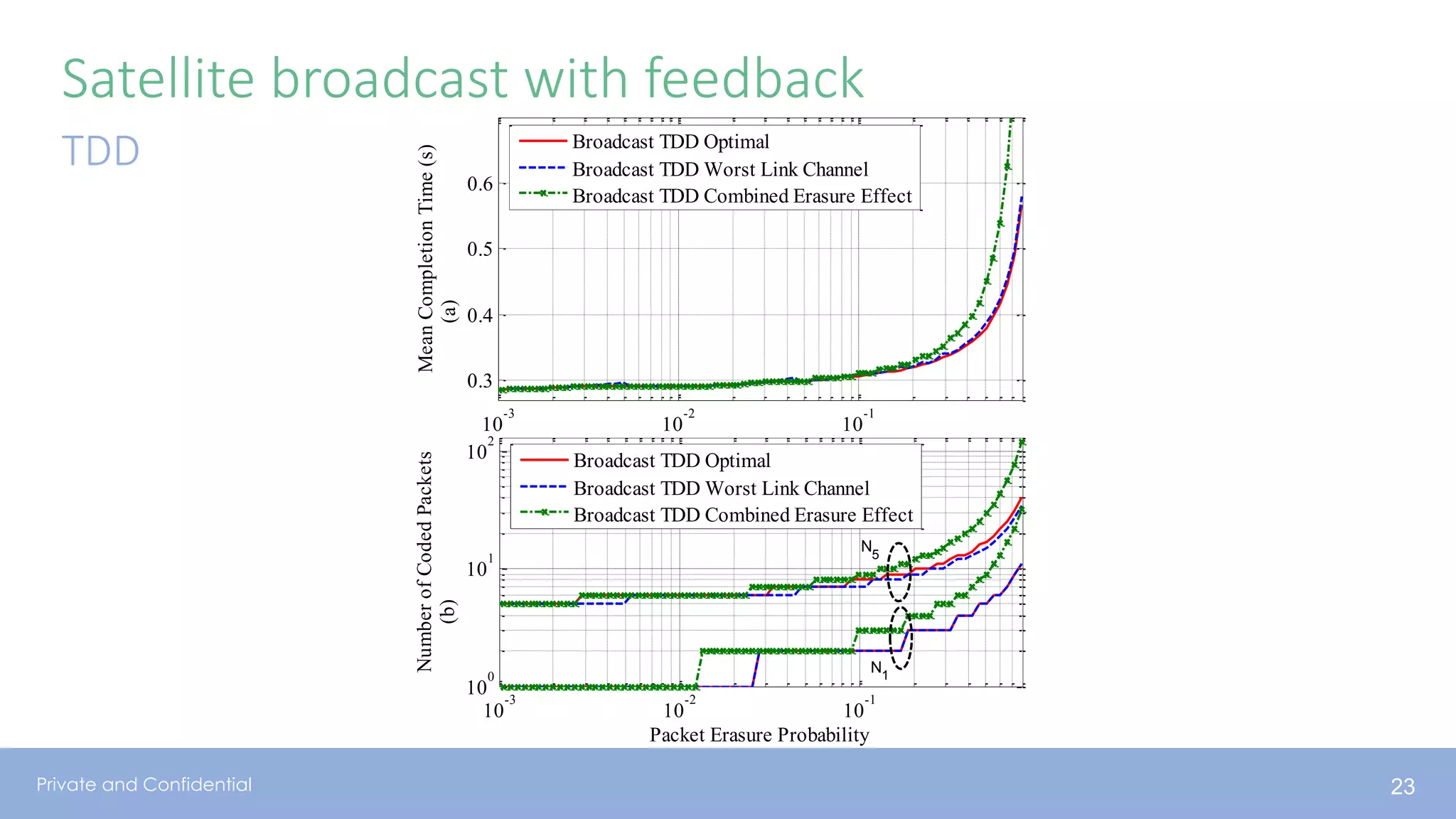
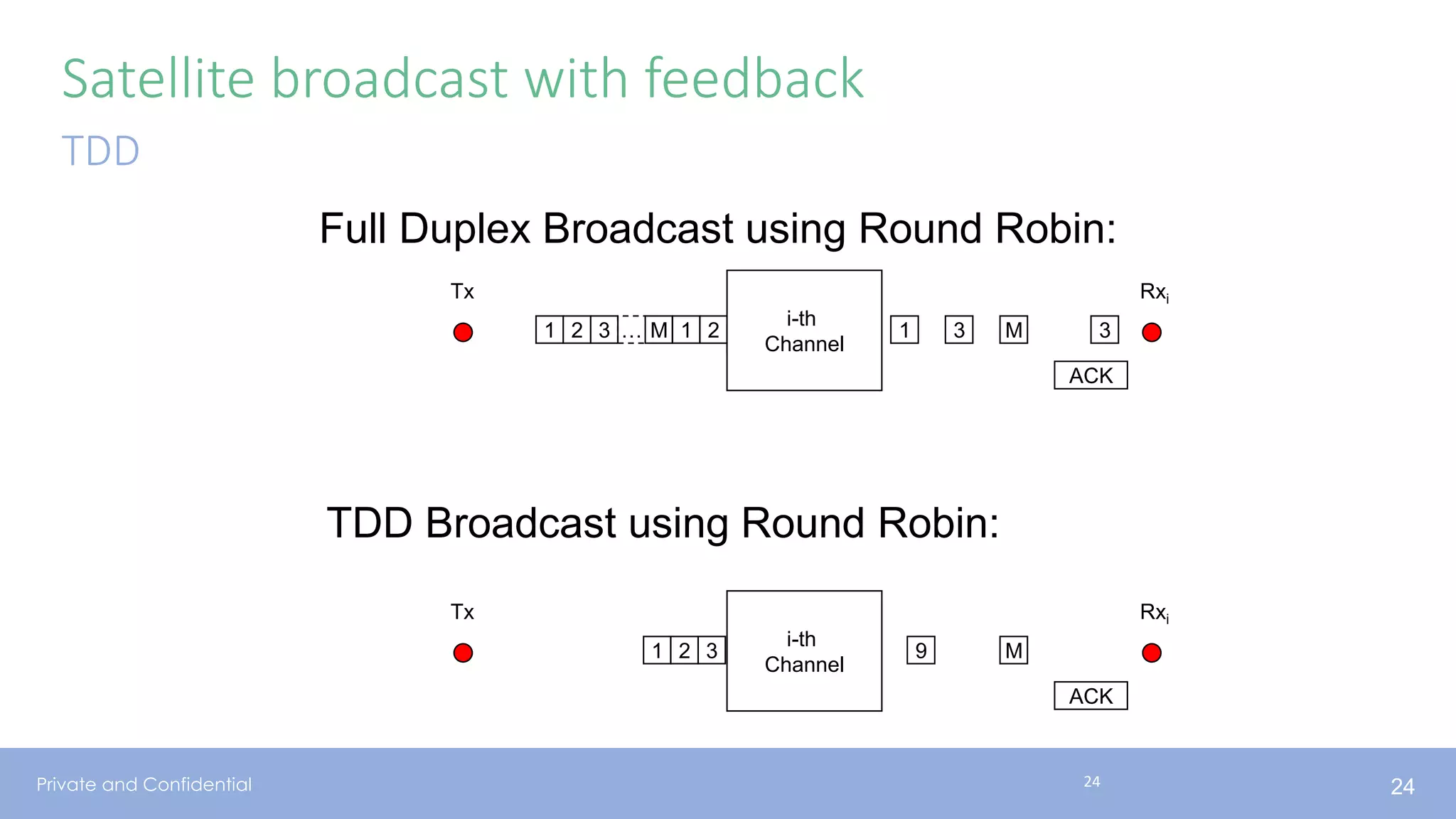
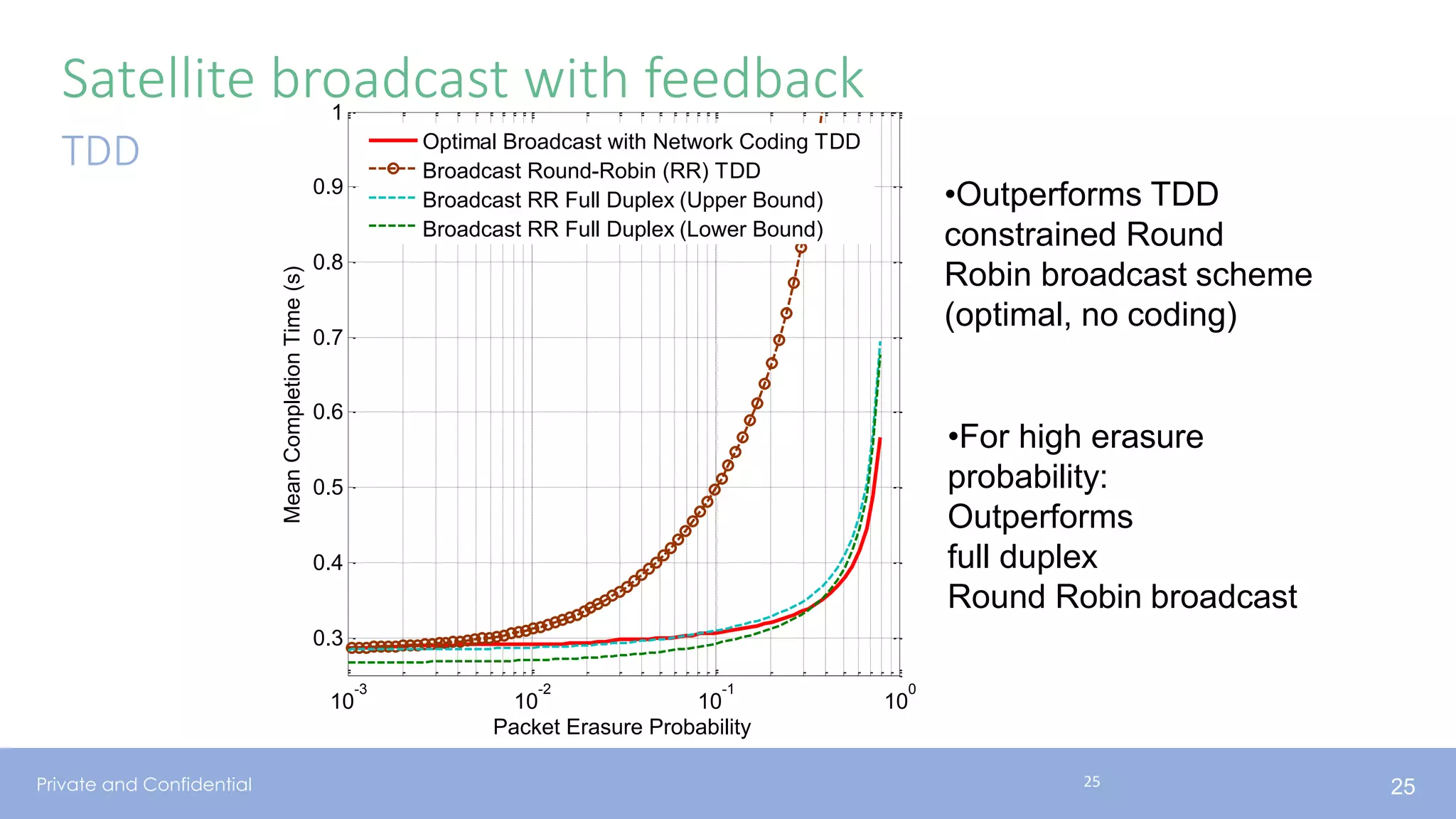
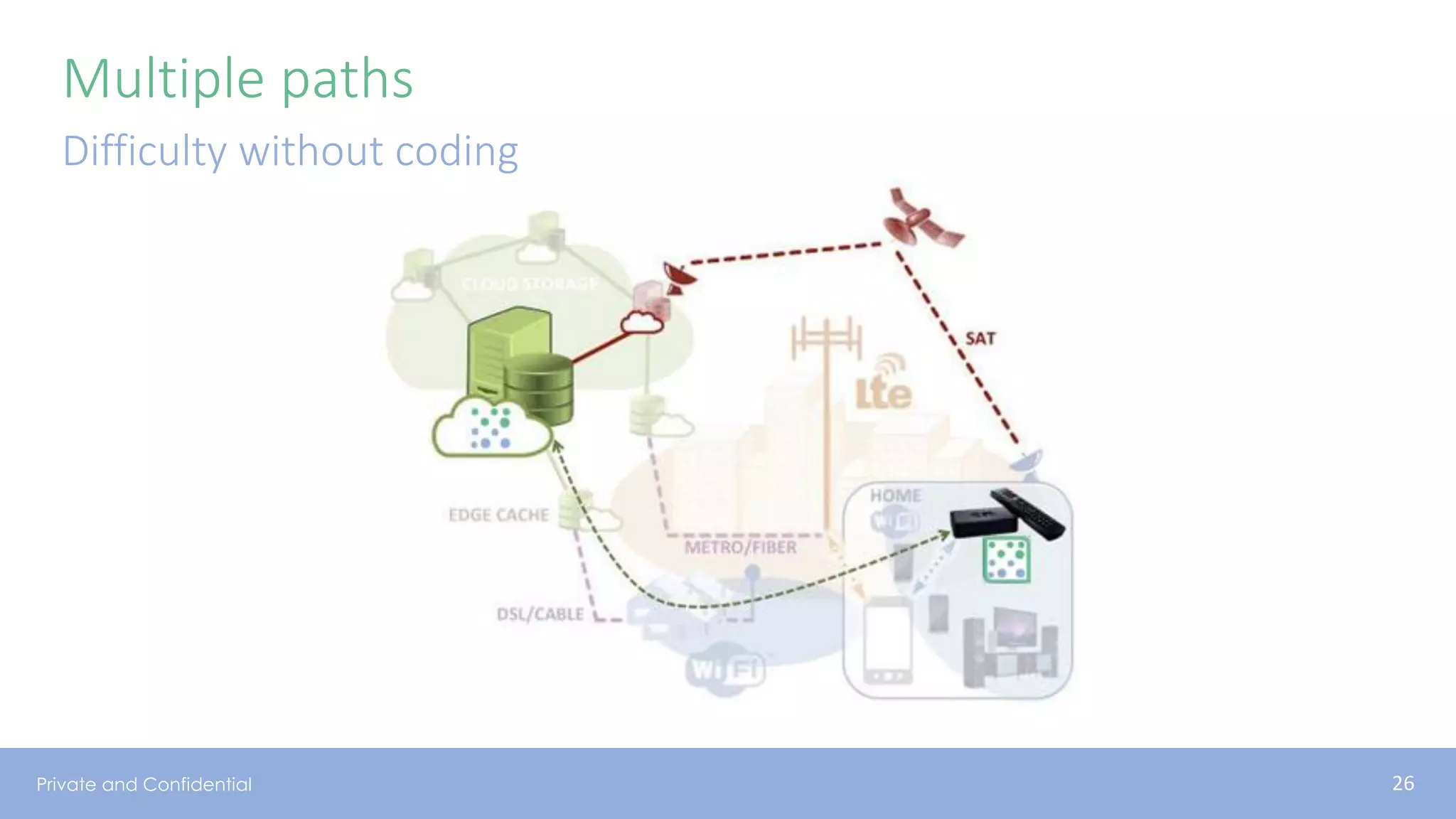
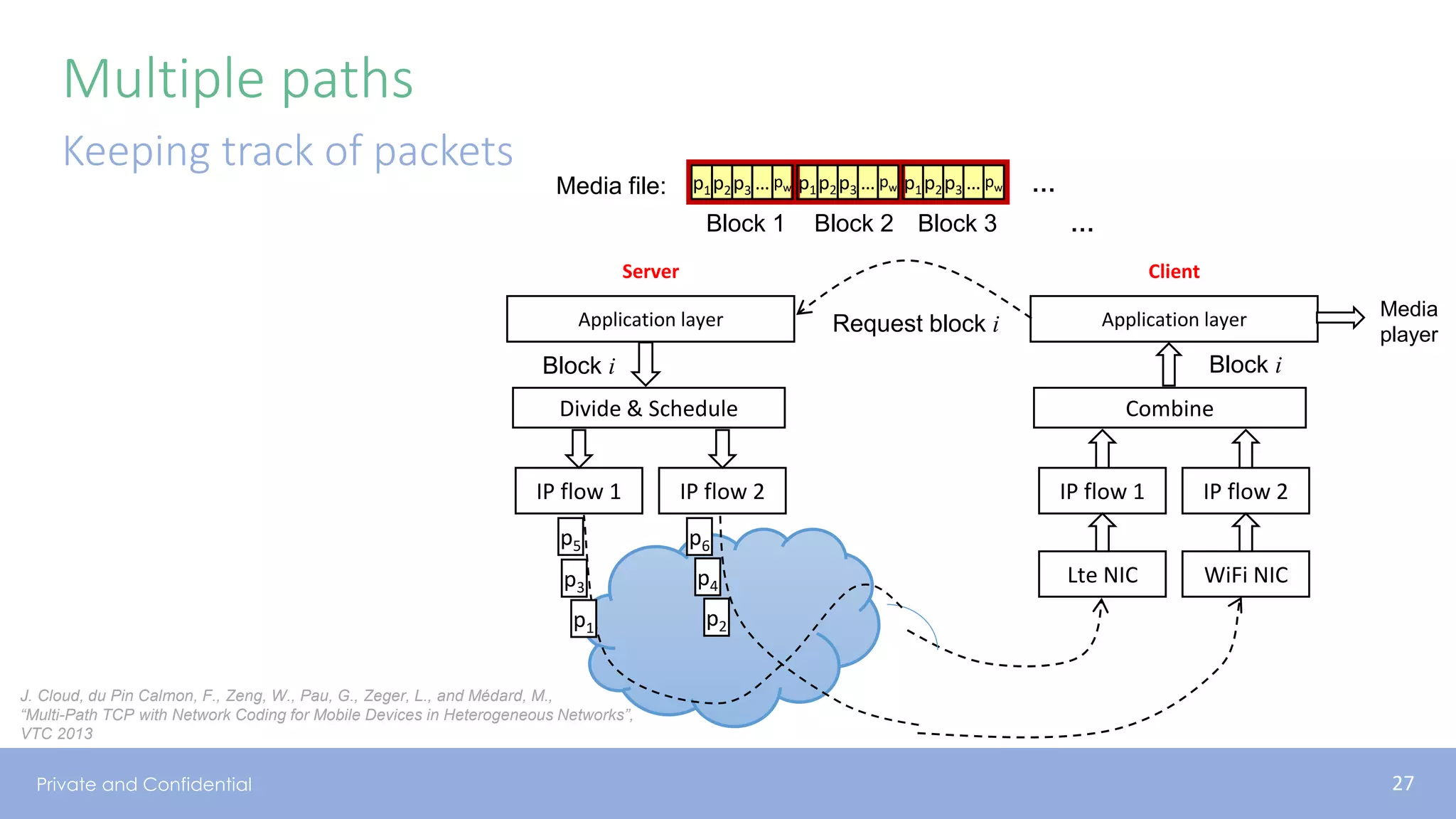
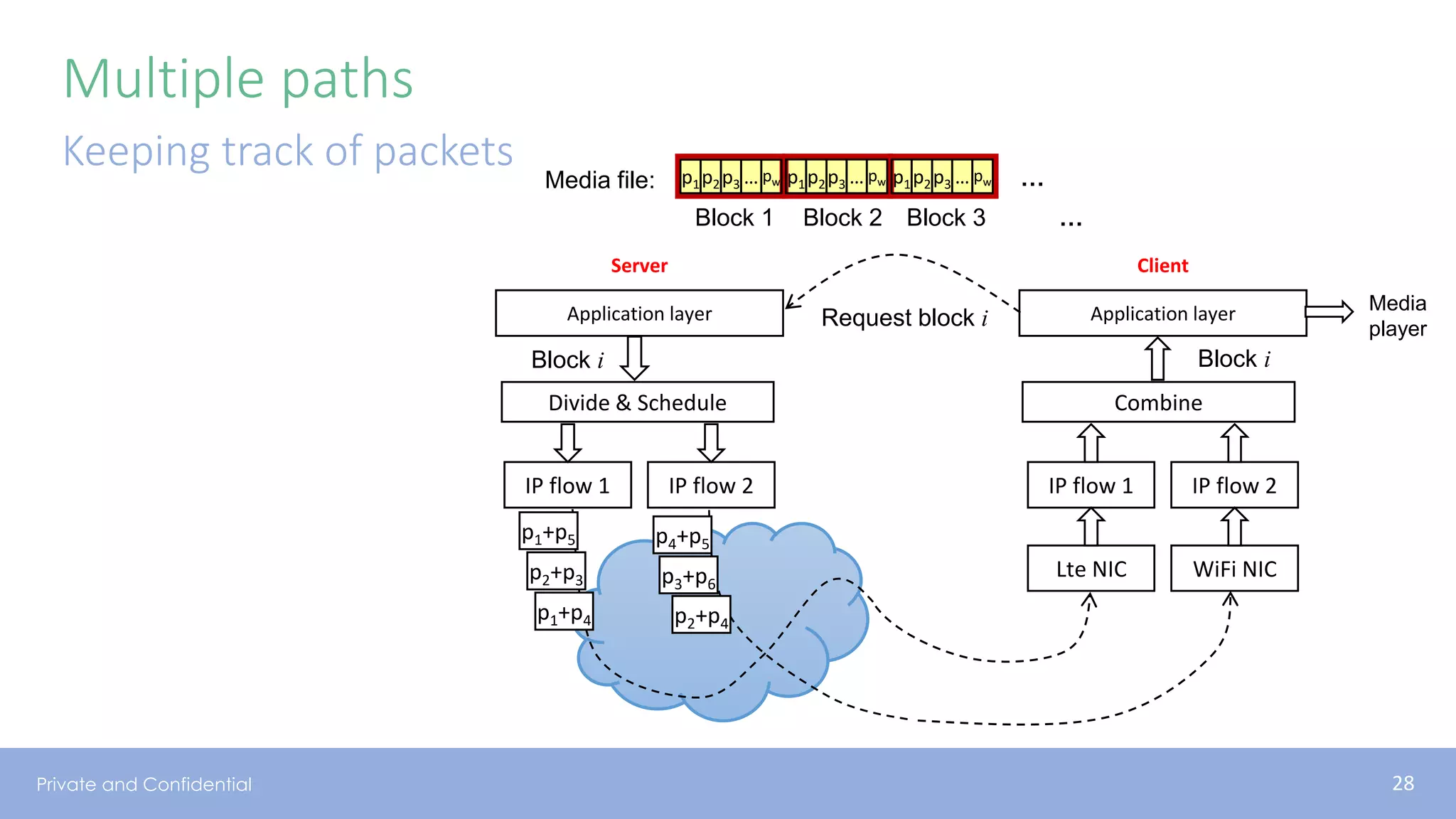
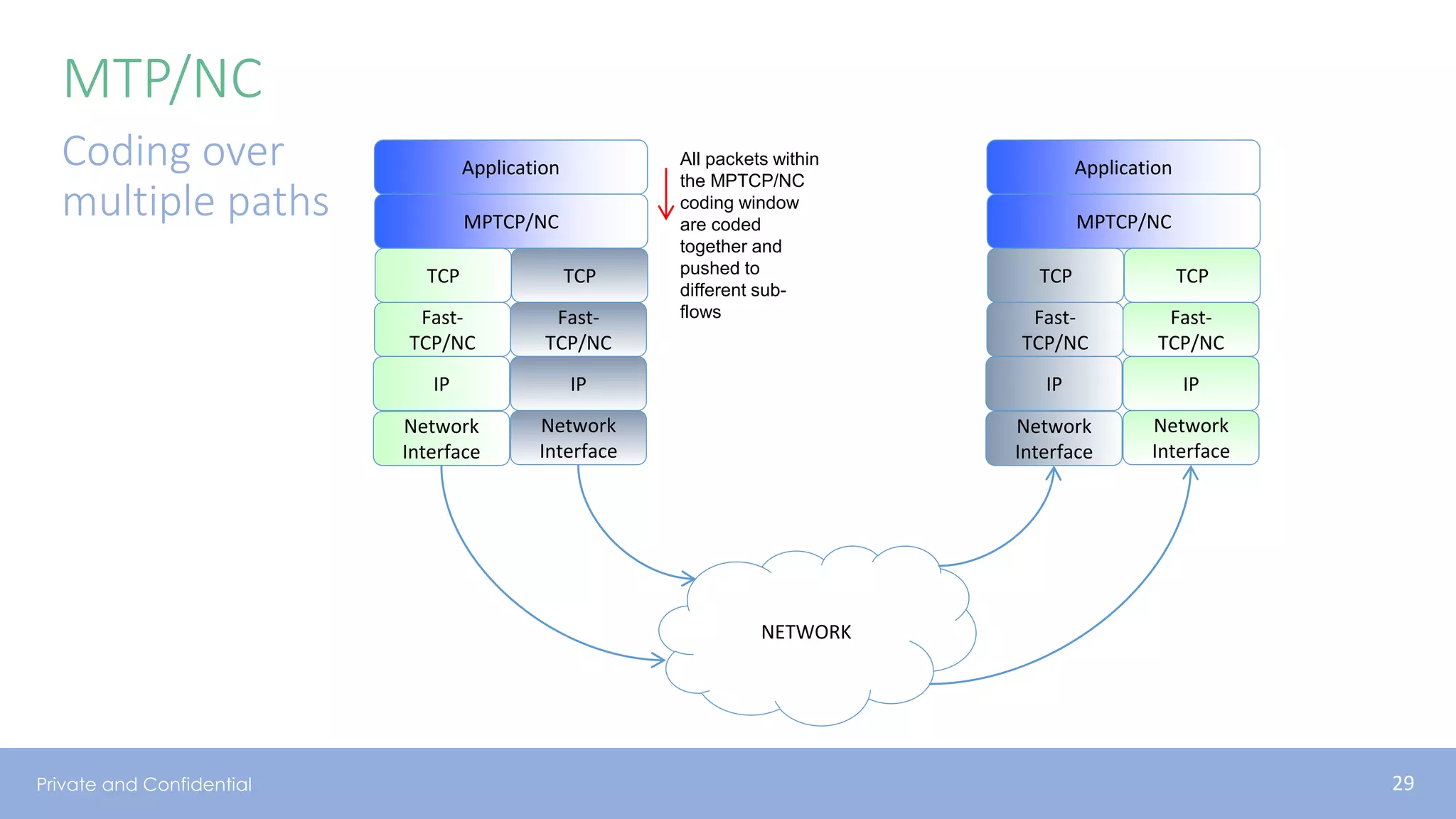
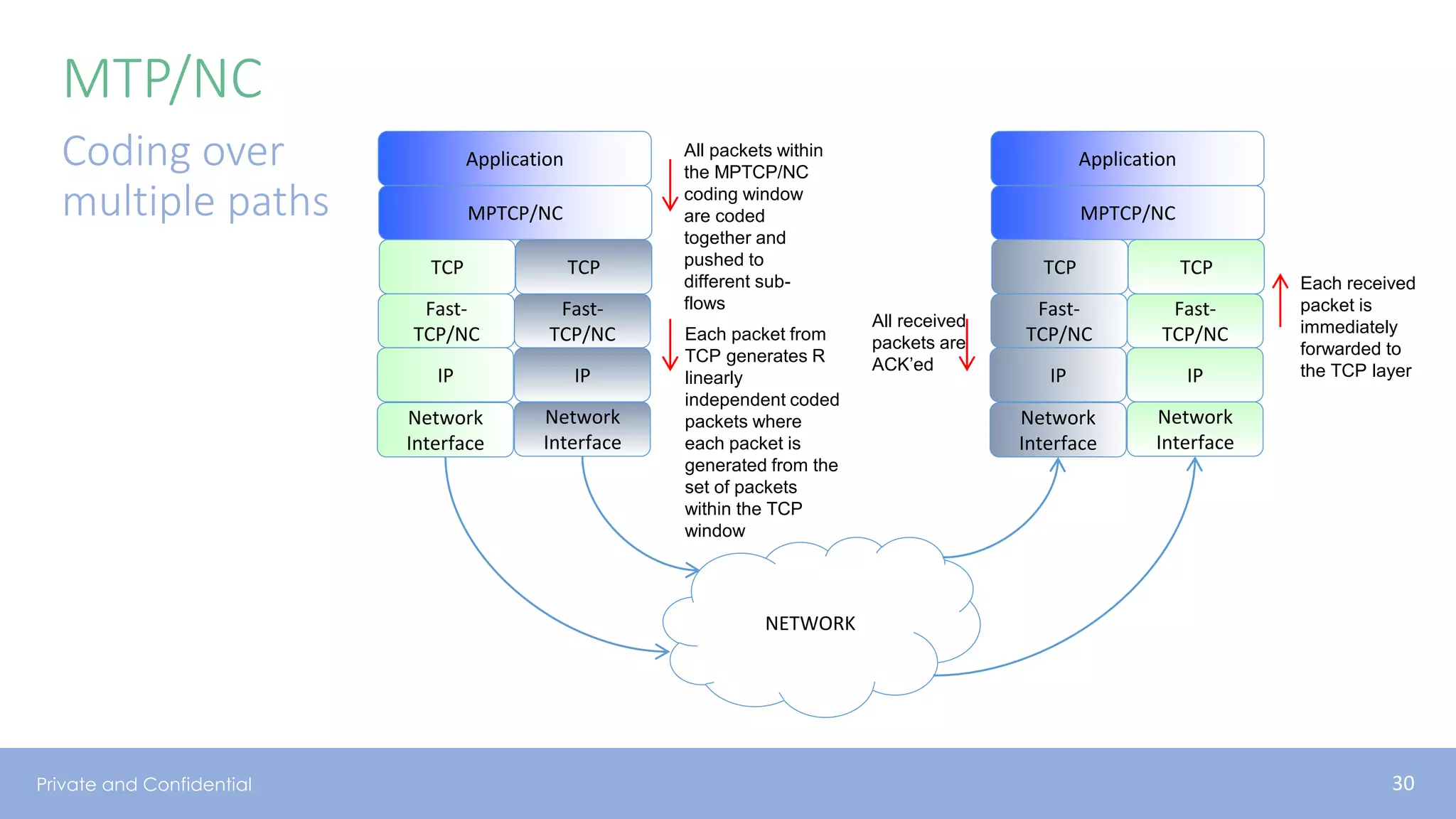
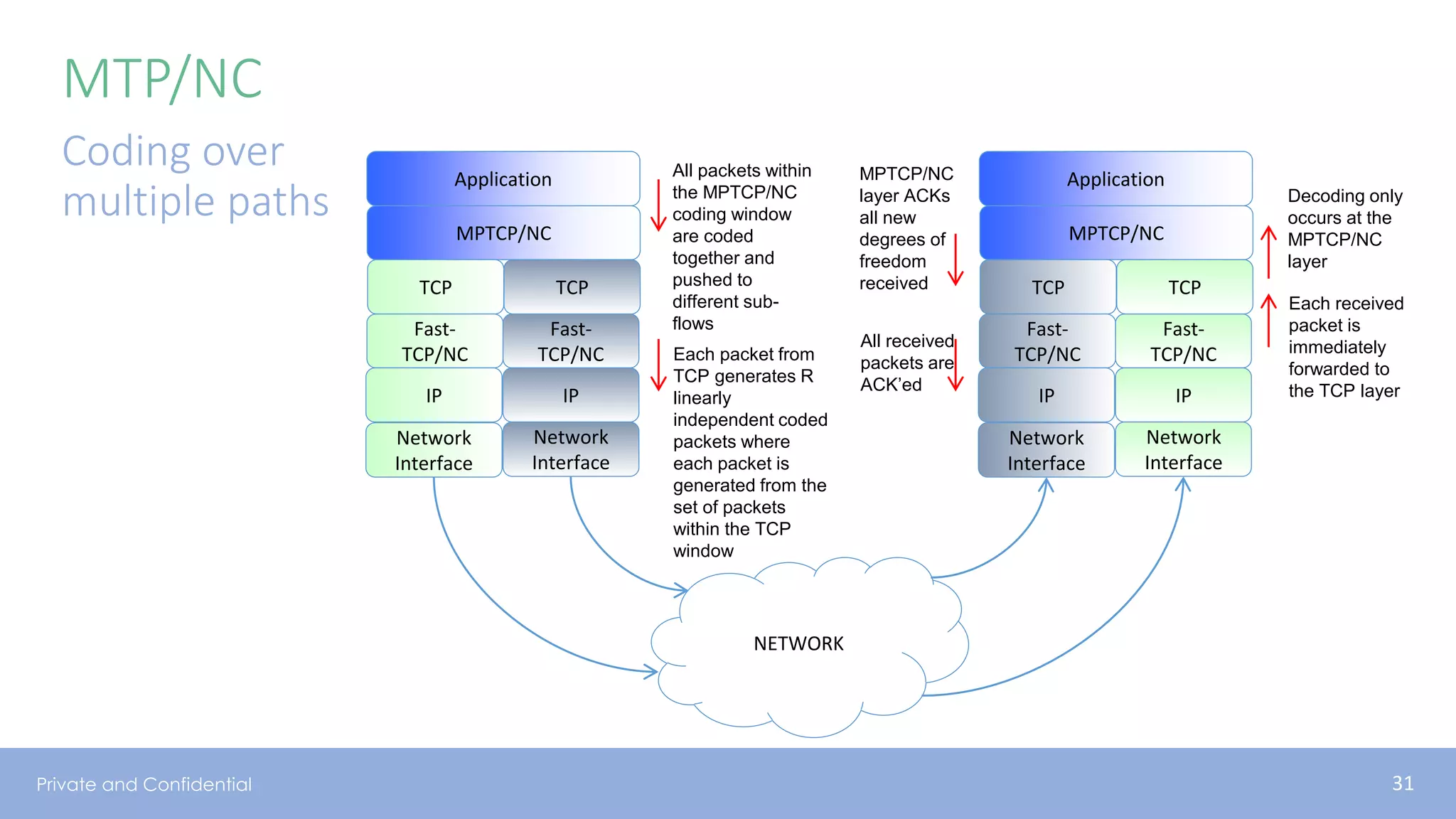
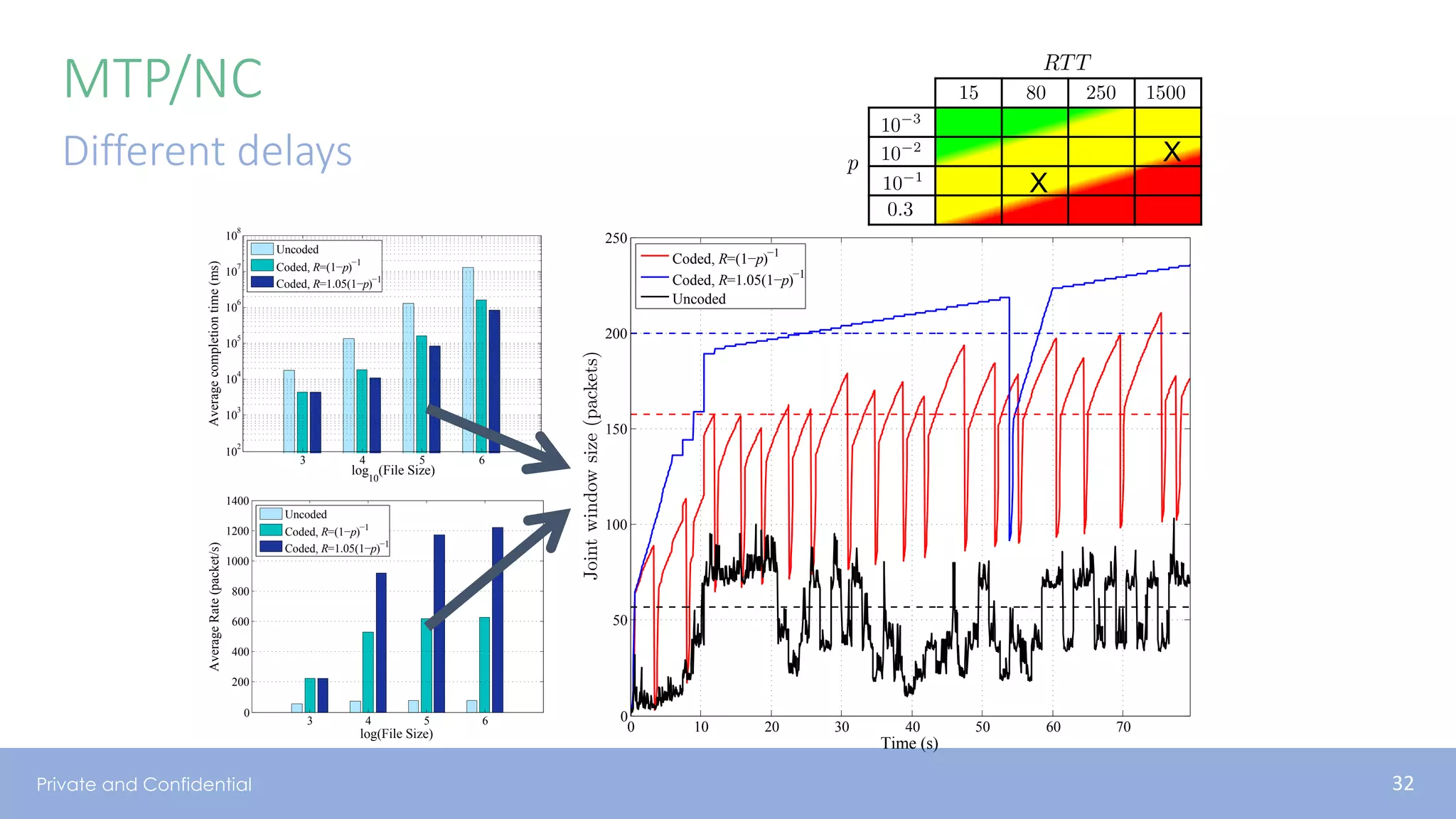
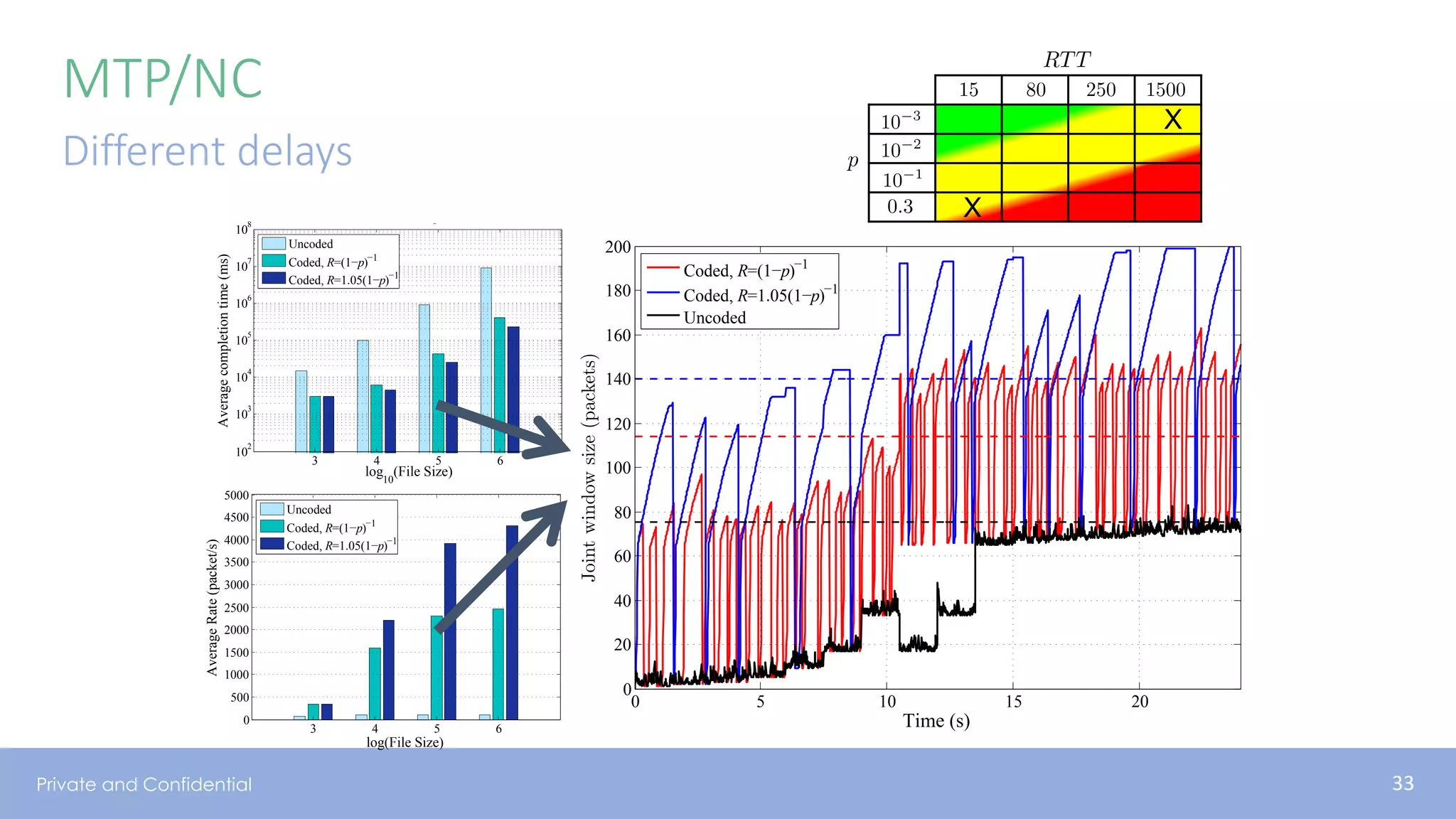
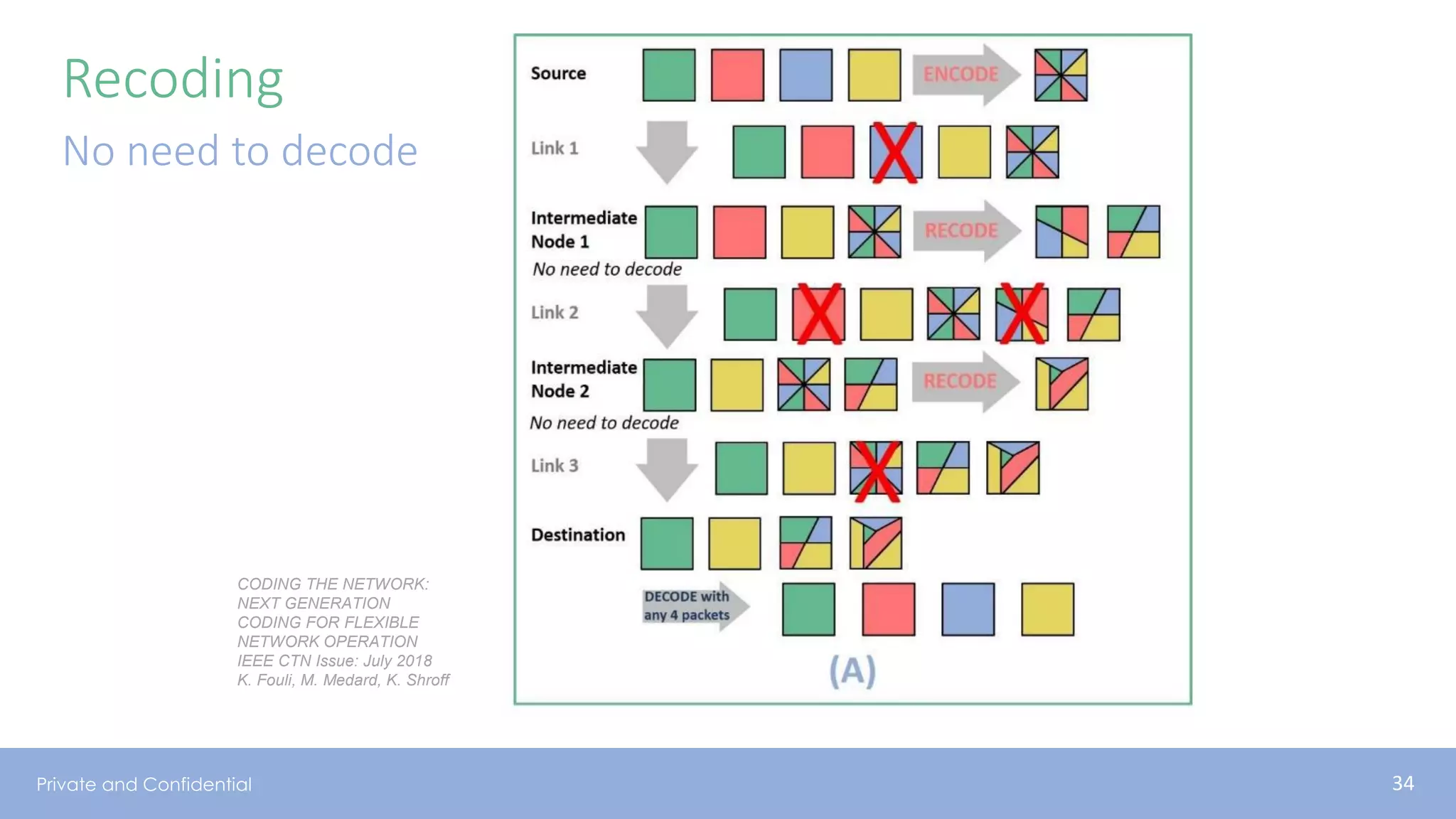
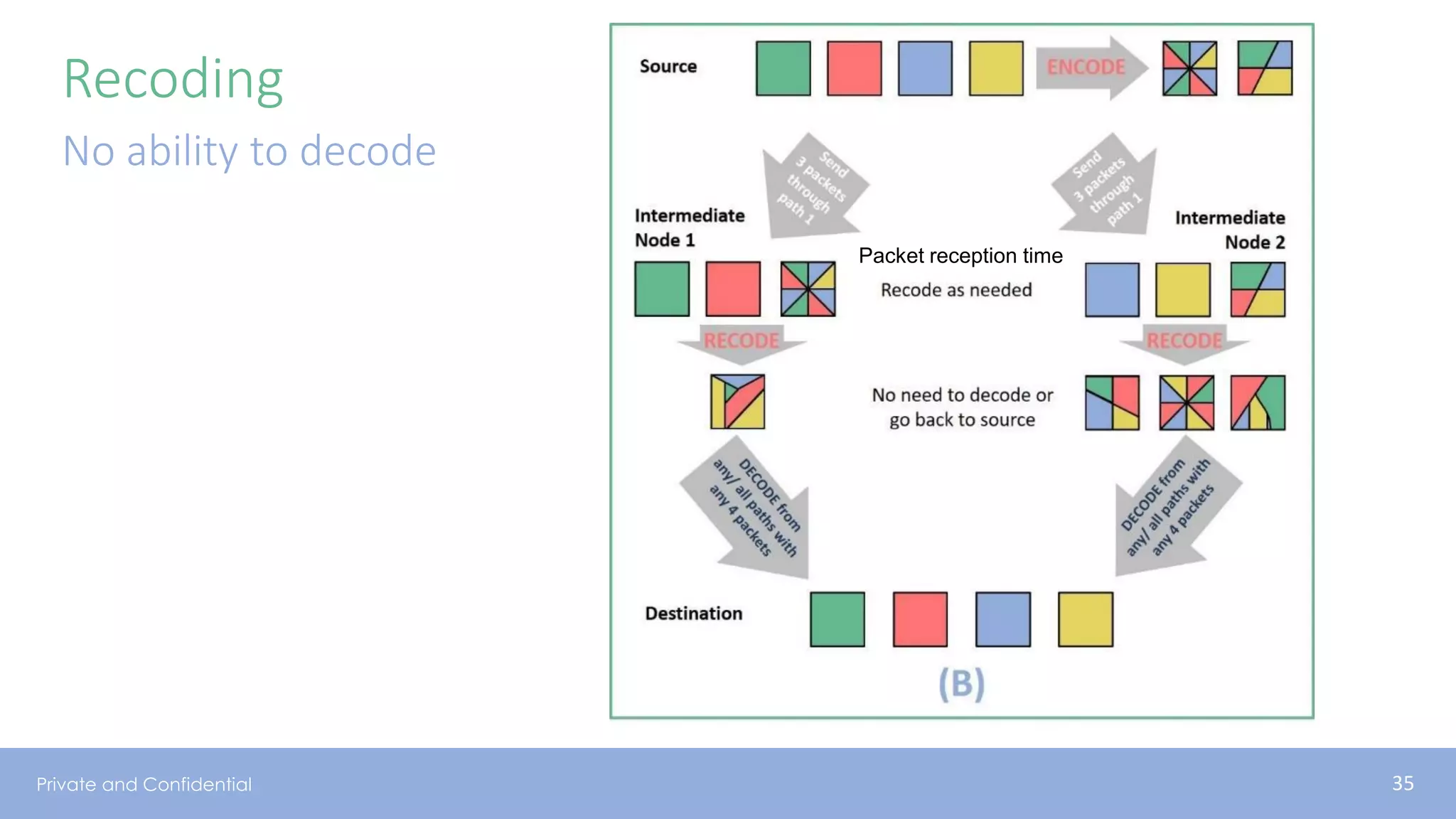
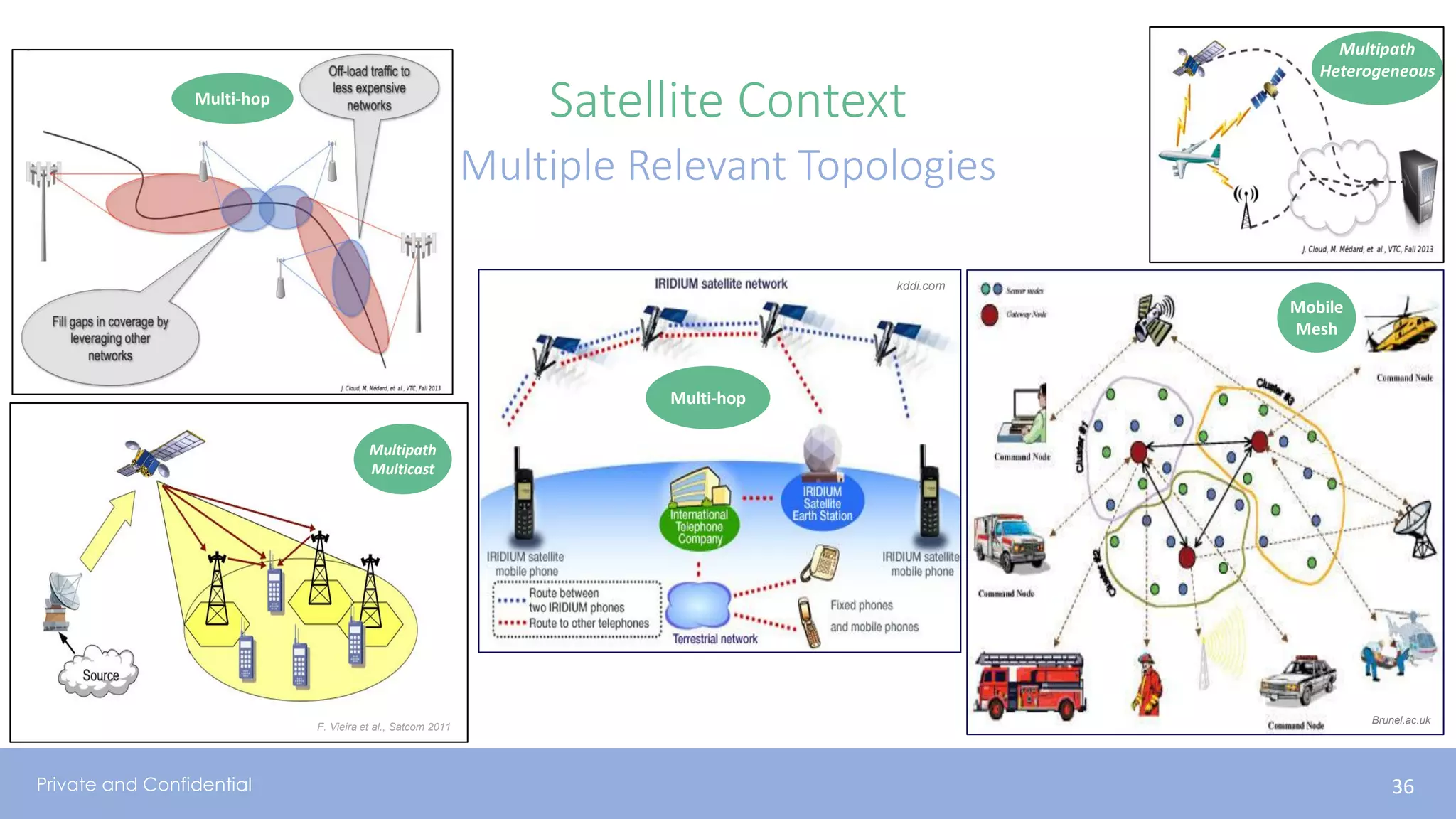
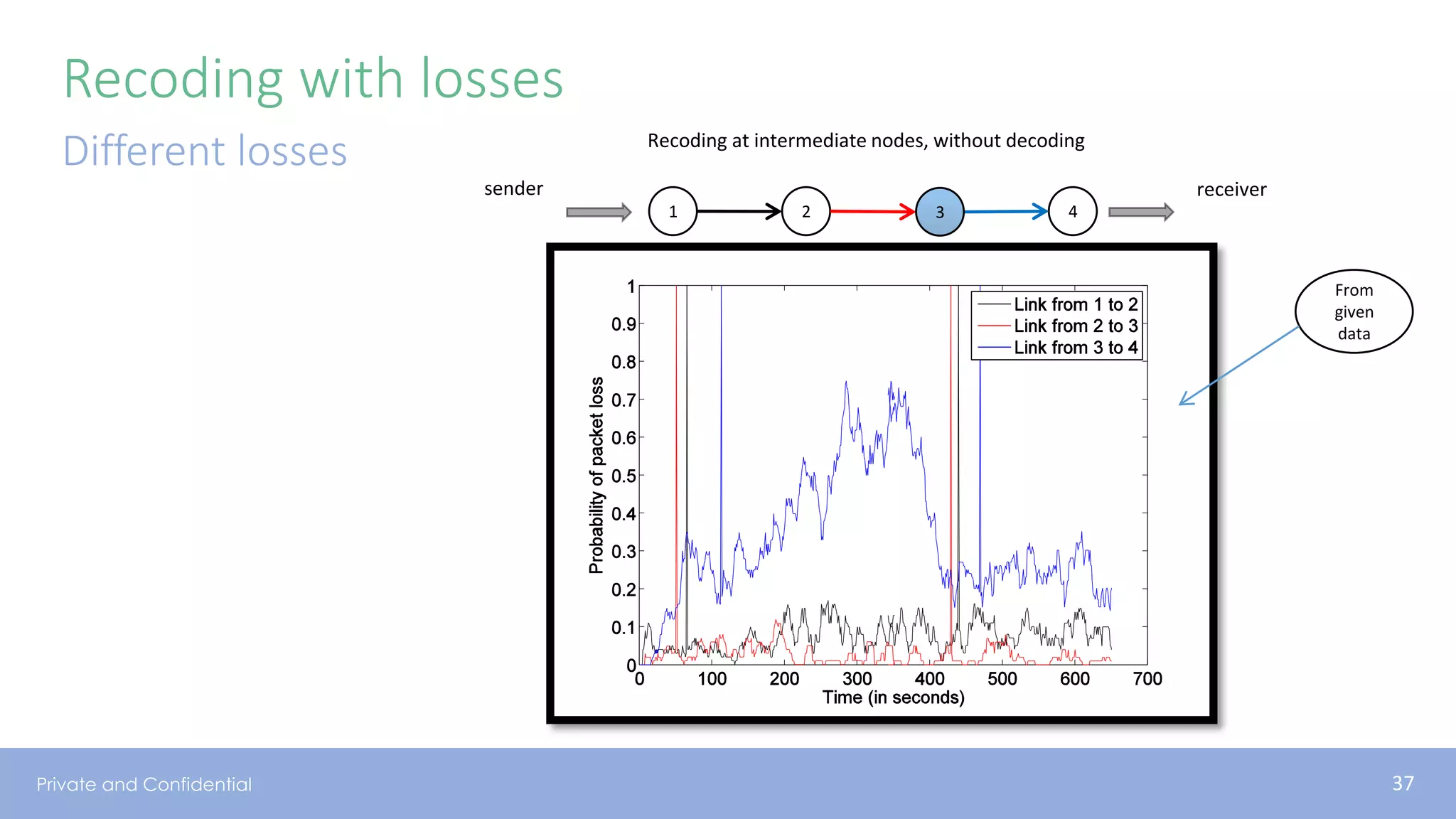
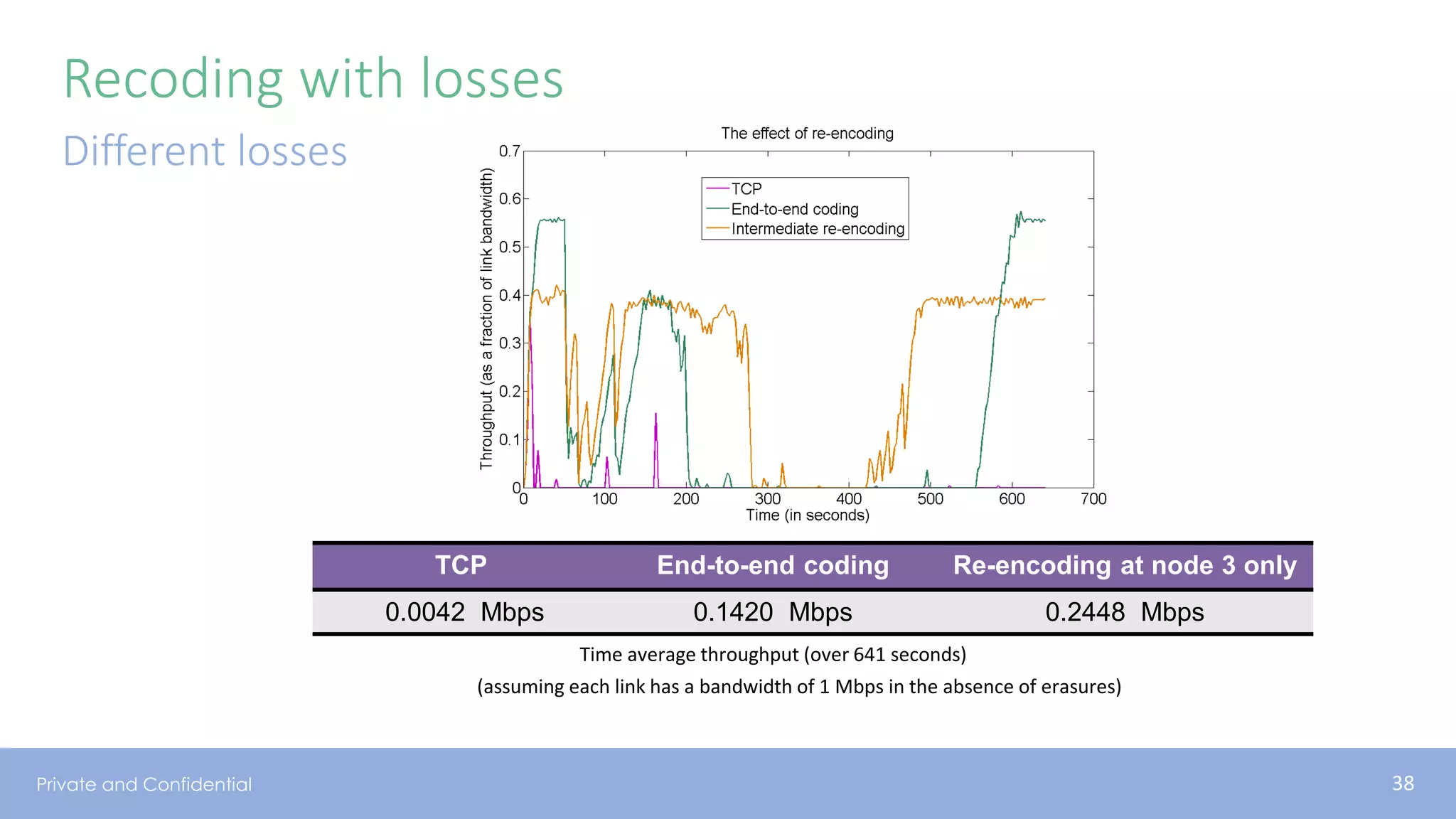
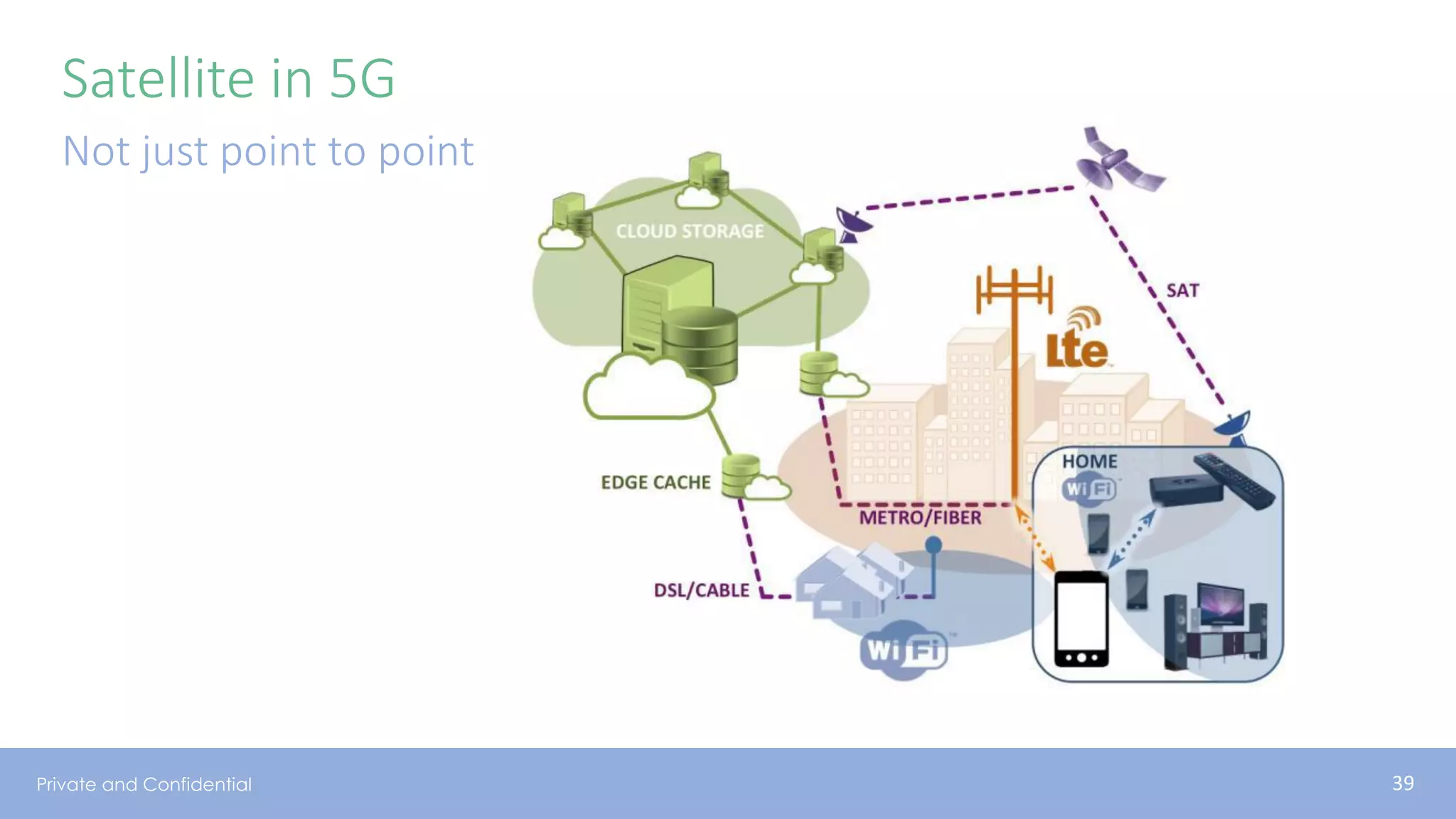
The document presents various aspects of network coding, particularly in satellite communications, emphasizing its benefits for throughput and error management in challenging environments like 5G. It discusses practical implementations of random linear network coding (RLNC), TCP modifications, and performance metrics related to satellite link utilization. Additionally, it explores future opportunities for coding applications, including edge caching and secure coding strategies.