Report
Share
Download to read offline
Recommended
Recommended
CS304PC : Computer Organization and Architecture CS304PC:Computer Organization and Architecture Session 7 Microprogrammed con...

CS304PC:Computer Organization and Architecture Session 7 Microprogrammed con...Asst.prof M.Gokilavani
More Related Content
Viewers also liked
Viewers also liked (6)
Similar to JTAM Poster
CS304PC : Computer Organization and Architecture CS304PC:Computer Organization and Architecture Session 7 Microprogrammed con...

CS304PC:Computer Organization and Architecture Session 7 Microprogrammed con...Asst.prof M.Gokilavani
Similar to JTAM Poster (20)
ID304 - Lotus® Connections 3.0 TDI, SSO, and User Life Cycle Management: What...

ID304 - Lotus® Connections 3.0 TDI, SSO, and User Life Cycle Management: What...
Polling system solution using blockchain & Liferay

Polling system solution using blockchain & Liferay
State of Nevada gaming control board minimal internal control standards_mics_...

State of Nevada gaming control board minimal internal control standards_mics_...
Trusted computing introduction and technical overview

Trusted computing introduction and technical overview
Practical White Hat Hacker Training - Post Exploitation

Practical White Hat Hacker Training - Post Exploitation
Authentication in microservice systems - fsto 2017

Authentication in microservice systems - fsto 2017
CS304PC:Computer Organization and Architecture Session 7 Microprogrammed con...

CS304PC:Computer Organization and Architecture Session 7 Microprogrammed con...
Breaking hardware enforced security with hypervisors

Breaking hardware enforced security with hypervisors
DevOps Braga #3: Admin rights, everyone gets Admin rights!

DevOps Braga #3: Admin rights, everyone gets Admin rights!
Recently uploaded
Recently uploaded (20)
Frisco Automating Purchase Orders with MuleSoft IDP- May 10th, 2024.pptx.pdf

Frisco Automating Purchase Orders with MuleSoft IDP- May 10th, 2024.pptx.pdf
How to Check CNIC Information Online with Pakdata cf

How to Check CNIC Information Online with Pakdata cf
Cyber Insurance - RalphGilot - Embry-Riddle Aeronautical University.pptx

Cyber Insurance - RalphGilot - Embry-Riddle Aeronautical University.pptx
ChatGPT and Beyond - Elevating DevOps Productivity

ChatGPT and Beyond - Elevating DevOps Productivity
Intro to Passkeys and the State of Passwordless.pptx

Intro to Passkeys and the State of Passwordless.pptx
TrustArc Webinar - Unified Trust Center for Privacy, Security, Compliance, an...

TrustArc Webinar - Unified Trust Center for Privacy, Security, Compliance, an...
WebRTC and SIP not just audio and video @ OpenSIPS 2024

WebRTC and SIP not just audio and video @ OpenSIPS 2024
Microsoft CSP Briefing Pre-Engagement - Questionnaire

Microsoft CSP Briefing Pre-Engagement - Questionnaire
Revolutionizing SAP® Processes with Automation and Artificial Intelligence

Revolutionizing SAP® Processes with Automation and Artificial Intelligence
“Iamnobody89757” Understanding the Mysterious of Digital Identity.pdf

“Iamnobody89757” Understanding the Mysterious of Digital Identity.pdf
Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx

Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx
JTAM Poster
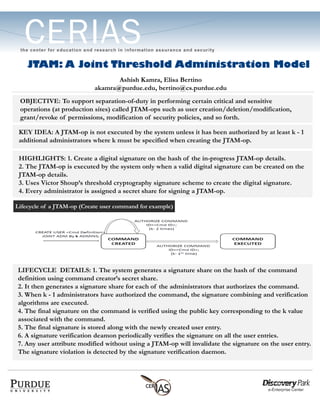
- 1. JTAM: A Joint Threshold Administration ModelJTAM: A Joint Threshold Administration Model Ashish Kamra, Elisa Bertino akamra@purdue.edu, bertino@cs.purdue.edu OBJECTIVE: To support separation-of-duty in performing certain critical and sensitive operations (at production sites) called JTAM-ops such as user creation/deletion/modification, grant/revoke of permissions, modification of security policies, and so forth. KEY IDEA: A JTAM-op is not executed by the system unless it has been authorized by at least k - 1 additional administrators where k must be specified when creating the JTAM-op. HIGHLIGHTS: 1. Create a digital signature on the hash of the in-progress JTAM-op details. 2. The JTAM-op is executed by the system only when a valid digital signature can be created on the JTAM-op details. 3. Uses Victor Shoup’s threshold cryptography signature scheme to create the digital signature. 4. Every administrator is assigned a secret share for signing a JTAM-op. Lifecycle of a JTAM-op (Create user command for example)Lifecycle of a JTAM-op (Create user command for example) LIFECYCLE DETAILS: 1. The system generates a signature share on the hash of the command definition using command creator’s secret share. 2. It then generates a signature share for each of the administrators that authorizes the command. 3. When k - 1 administrators have authorized the command, the signature combining and verification algorithms are executed. 4. The final signature on the command is verified using the public key corresponding to the k value associated with the command. 5. The final signature is stored along with the newly created user entry. 6. A signature verification deamon periodically verifies the signature on all the user entries. 7. Any user attribute modified without using a JTAM-op will invalidate the signature on the user entry. The signature violation is detected by the signature verification daemon.