JTAM Poster
•
0 likes•140 views
JTAM is a model that supports separation-of-duty for critical operations like user creation/deletion by requiring authorization from at least k-1 administrators, where k is specified when creating the operation. It uses threshold cryptography to create a digital signature on the operation details, with each administrator assigned a secret share for signing. The lifecycle of an operation like creating a user involves the system generating signature shares, combining them when k-1 administrators authorize, and verifying the final signature before execution and storage alongside the new user entry.
Report
Share
Report
Share
Download to read offline
Recommended
SCEP 2012 inside SCCM 2012

The document discusses Microsoft's antimalware management platform which provides a common antimalware platform across Microsoft clients with proactive protection against known and unknown threats while reducing complexity. It integrates features such as early-launch antimalware, measured boot, and secure boot through UEFI to prevent malware from bypassing antimalware inspection during the boot process. The platform also provides simplified administration through a single console experience for endpoint protection and management.
AlaskaAirlinesMagazine_02.16_p.39

The Sun Valley Film Festival will take place from March 2-6 in Sun Valley, ID. This year's festival will feature 60 films including world premieres, shorts, narratives and documentaries. Festival events include daily film screenings as well as special events like "Coffee Talks" with directors. Academy Award winning director Oliver Stone will be honored at this year's festival. In addition to films, the area offers skiing, food, music and the chance to win prizes through a sweepstakes including airfare and resort accommodations.
Improving Nursing Home Quality of Care

This presentation will analyze complaints made to state survey agencies about nursing home quality, the investigations into these complaints, and the deficiency citations issued to facilities as a result. It will discuss how complaints and investigations impact nursing home quality of care. The presentation will also address facility and resident factors that can provide insight into nursing home quality and how to improve resident care.
PSAC Poster

This very short document does not contain enough substantive information to summarize in 3 sentences or less in a meaningful way. It appears to contain a repeated word but no other context.
Catálogo Sol's Atelier52.pt

Este documento fornece informações sobre os produtos e serviços da SOL'S, incluindo:
1) Uma lista de produtos como camisetes, polos, calças e acessórios;
2) Detalhes sobre os valores éticos e compromissos sociais da empresa, como apoio a orfanatos e hospitais;
3) Uma descrição dos serviços de logística, qualidade e compromissos com padrões éticos e sustentabilidade.
Solutions pour l'industrie du Food Feed Palamatic Process

Solutions de manutention des poudres
Manutention des pulvérulents
Equipement de manutention
Manutention poudre
Manutention poudres
Manutention produit vrac
Manutention vracs
Process poudre
Technologies manutention poudre
Process industriels traitant des poudres
Recommended
SCEP 2012 inside SCCM 2012

The document discusses Microsoft's antimalware management platform which provides a common antimalware platform across Microsoft clients with proactive protection against known and unknown threats while reducing complexity. It integrates features such as early-launch antimalware, measured boot, and secure boot through UEFI to prevent malware from bypassing antimalware inspection during the boot process. The platform also provides simplified administration through a single console experience for endpoint protection and management.
AlaskaAirlinesMagazine_02.16_p.39

The Sun Valley Film Festival will take place from March 2-6 in Sun Valley, ID. This year's festival will feature 60 films including world premieres, shorts, narratives and documentaries. Festival events include daily film screenings as well as special events like "Coffee Talks" with directors. Academy Award winning director Oliver Stone will be honored at this year's festival. In addition to films, the area offers skiing, food, music and the chance to win prizes through a sweepstakes including airfare and resort accommodations.
Improving Nursing Home Quality of Care

This presentation will analyze complaints made to state survey agencies about nursing home quality, the investigations into these complaints, and the deficiency citations issued to facilities as a result. It will discuss how complaints and investigations impact nursing home quality of care. The presentation will also address facility and resident factors that can provide insight into nursing home quality and how to improve resident care.
PSAC Poster

This very short document does not contain enough substantive information to summarize in 3 sentences or less in a meaningful way. It appears to contain a repeated word but no other context.
Catálogo Sol's Atelier52.pt

Este documento fornece informações sobre os produtos e serviços da SOL'S, incluindo:
1) Uma lista de produtos como camisetes, polos, calças e acessórios;
2) Detalhes sobre os valores éticos e compromissos sociais da empresa, como apoio a orfanatos e hospitais;
3) Uma descrição dos serviços de logística, qualidade e compromissos com padrões éticos e sustentabilidade.
Solutions pour l'industrie du Food Feed Palamatic Process

Solutions de manutention des poudres
Manutention des pulvérulents
Equipement de manutention
Manutention poudre
Manutention poudres
Manutention produit vrac
Manutention vracs
Process poudre
Technologies manutention poudre
Process industriels traitant des poudres
hermeneutica analogica

Este documento presenta las reglas y advertencias de una biblioteca virtual que ofrece préstamos gratuitos de libros a personas de bajos recursos. Indica que los libros solo pueden usarse con fines educativos y deben destruirse una vez leídos para evitar su venta o distribución comercial. También recomienda comprar los libros si se puede costearlos y abstenerse de usar la biblioteca si las leyes locales lo prohíben.
25 funciones del espíritu santo

El Espíritu Santo tiene 25 funciones importantes como convencer de pecado, sellarnos para la redención, dar testimonio como hijos de Dios, dar vida, amor, frutos, poder, dones, justicia, paz y gozo, enseñanza, guía, unción, consuelo, fortaleza, recuerdo, aconsejo, interpretación espiritual, revelación, intercesión, mostrar salida de tentación, unidad al cuerpo de Cristo, glorificar a Jesús y ser imprescindible en nuestras vidas.
Mark Stonerock 2-23-16

Mark Stonerock has over 15 years of experience in financial analysis and payroll management. He currently serves as a Senior Financial Analyst for DSW Inc, where he manages a team and $2 billion in annual spend. Previously he held roles as a Payroll Manager and various financial and payroll analyst roles. He has a Bachelor's degree in Business Administration with a double major in Finance and Real Estate from The Ohio State University.
Evolucion de la tecnologia

Este documento describe los principales períodos de desarrollo tecnológico y los cambios estructurales que produjeron las invenciones más significativas en cada época, incluyendo las herramientas de piedra en el Paleolítico, los telares en el Neolítico, la escritura en las culturas antiguas de Egipto y Mesopotamia, los relojes de agua en la sociedad clásica de Grecia y Roma, la pólvora en la Edad Media, la imprenta en el Renacimiento, la
Mimikatz

Mimikatz is a tool that enables extracting plain text passwords, hashes, and Kerberos tickets from memory. It can be used to perform pass-the-hash, over-pass-the-hash, and pass-the-ticket authentication attacks. Mimikatz uses the Sekurlsa module to dump credentials stored in the Local Security Authority Subsystem Service (LSASS) process memory. It decrypts encrypted credentials using the same functions LSASS uses, allowing extraction of passwords in plain text. Pass-the-hash allows authenticating with only the NTLM hash by replacing the hash used in authentication with the target user's hash.
ObserveIT -Unix/ Linux session recording

ObserveIT captures all user sessions, for both Unix/Linux users as well as Windows users. As compared to the Windows sessions, ObserveIT includes some additional capabilities that are unique to the Unix and Linux environments.
The Unix/Linux Agent records user activity in any interactive shell running on the machine, and transfers the data to the ObserveIT Management Server. Recording begins whenever a user starts an SSH or Telnet shell login to the system.
ObserveIT captures important hidden information about each user command, by capturing the resources affected and system calls made by each command.
ID304 - Lotus® Connections 3.0 TDI, SSO, and User Life Cycle Management: What...

Presentation that I gave at Lotusphere 2011 with Jay Boyd. We talked about TDI, single sign on, and user management.
Auditing System Password Using L0phtcrack

The objective of this presentation is to help peoples to learn how to use L0htCrack tool to attain and crack the user password from any Windows Machine.
Hardware_root_trust_x86.pptx

This presentation contains details how a typcial modern x86 based PC from Intel establishes hardware root of trust for operation system and application to operate over it afterwards.
Crypto box - crypto casino

The Crypto Casino is unique, transparent and protected from bots gambling system with open-source code. The system was developed using smart contracts.
Check presentation to find more info!
Why SureLog?

SureLog is an integrated log management and next-generation SIEM solution that provides advanced correlation rules, risk calculation, taxonomy, data management, user management, threat intelligence, vulnerability assessment, and statistical reporting. It features an intuitive browser-based UI and supports custom parsers, tagging, and a distributed architecture.
Polling system solution using blockchain & Liferay

Polling system solution using block-chain and Liferay. This presentation explain about Registration, Permission Access, States of Data, Integration of the protocol, single human authentication, Transaction Security, Polling System, Delegation / Casting vote, etc.
I am expecting responses / note on the presentation for further improvement. Please feel free to write us back on info@dfrozensoft.com / sales@dfrozensoft.com / dhanraj@dfrozensoft.com
State of Nevada gaming control board minimal internal control standards_mics_...

STATE OF NEVADA_GAMING CONTROL BOARD_MINIMUM INTERNAL CONTROL STANDARDS or “MICS”_V6.0_OCTOBER 20 , 2011_Contents: Information Technology for Interactive Gaming; Physical Access and Maintenance Controls; Network Security; Remote Access; System Parameters; Structure of Information Technology Department; User Accounts; Generic User Accounts; Service & Default Accounts; Backup and Recovery Procedures; Recordkeeping; Electronic Storage of Documentation; Production Environment Change Control Processes; General Operation of Interactive Gaming; Casino Account Transfers; Registering Authorized PlayersIdentification and Verification of Authorized Players; Protection of the Interactive Gaming Accounts; Interactive Gaming Engaged between Human Individuals; Responsible Interactive Gaming; Protection of Authorized Player’s Personally Identifiable Information; Closed/Inactive Accounts; Authorized Player Disputes; Contests/Tournaments; Promotional Progressive Pots and Pools; Authorized Player Promotional Account; Documentation; Accounting/Audit Standards.
Trusted computing introduction and technical overview

Trusted computing aims to increase confidence in computing platforms by enabling platforms to prove their integrity and identity. The Trusted Computing Group is developing an open standard for a trusted platform module (TPM) that can reliably measure a platform's software state, attest to its identity and properties, and protect confidential data. The TPM acts as a root of trust and provides mechanisms for platform authentication, integrity reporting, and protected storage that enable trust in remote platforms and their expected behavior.
Practical White Hat Hacker Training - Post Exploitation

This presentation part of Prisma CSI's Practical White Hat Hacker Training v1
PRISMA CSI • Cyber Security and Intelligence www.prismacsi.com
This document can be shared or used by quoted and used for commercial purposes, but can not be changed. Detailed information is available at https://creativecommons.org/licenses/by-nc-nd/4.0/legalcode.
Authentication in microservice systems - fsto 2017

This document discusses authentication in microservice systems. It begins by setting the stage and introducing relevant topics. It then builds vocabulary around OAuth2, bearer tokens, JWT, and JWK. It describes authenticating micro frontends using an identity provider, leader/follower pattern, and endpoint middleware. It covers authenticating REST API microservices using bearer token validation. Finally, it addresses authenticating asynchronous messages using client credentials grants and session IDs across message brokers and web sockets. The conclusion summarizes that securing a microservice system involves securing each micro frontend, REST API, and asynchronous flow while maintaining performance and architecture abstraction.
Post Exploitation Using Meterpreter

The document discusses using Meterpreter for post exploitation activities after gaining access to a target system. Meterpreter provides an advanced multi-function payload that injects itself into running processes to provide core and advanced command functionality through extensions in a more stealthy way than normal payloads. The document outlines how Meterpreter works and can be used for activities like enumeration, privilege escalation, information harvesting, and pivoting across a network during post exploitation.
CS304PC:Computer Organization and Architecture Session 7 Microprogrammed con...

CS304PC:Computer Organization and Architecture Session 7 Microprogrammed con...Asst.prof M.Gokilavani
This document discusses the topics covered in Session 7 of the CS304PC course on Computer Organization and Architecture. It introduces microprogrammed control, including control memory, address sequencing, microprograms, and the design of control units. It describes the organization of a microprogrammed control system with separate main and control memories. The control memory stores the microprogram consisting of microinstructions that specify internal control signals. The next address generator determines the address sequence read from control memory. Advantages of microprogrammed control are that the hardware does not need to change for different operations - only the microprogram in control memory needs to change.Control Memory.pptx

The function of the control unit in a digital computer is to initiate
sequences of micro operations.
Rapport ICO Rating

The document analyzes the security of 100 cryptocurrency exchanges across four categories: console errors, user account security, registrar and domain security, and web protocols security. Key findings include:
- 32% of exchanges have code errors, 68% have no errors
- Only 46% of exchanges meet all user account security best practices
- Only 2% use registry lock and 10% use DNSSEC for domain security
- Only 10% have all recommended web protocol security headers
The report ranks exchanges based on their scores in each category, with Coinbase Pro, Kraken, and BitMEX receiving the top three scores overall for exchange security.
More Related Content
Viewers also liked
hermeneutica analogica

Este documento presenta las reglas y advertencias de una biblioteca virtual que ofrece préstamos gratuitos de libros a personas de bajos recursos. Indica que los libros solo pueden usarse con fines educativos y deben destruirse una vez leídos para evitar su venta o distribución comercial. También recomienda comprar los libros si se puede costearlos y abstenerse de usar la biblioteca si las leyes locales lo prohíben.
25 funciones del espíritu santo

El Espíritu Santo tiene 25 funciones importantes como convencer de pecado, sellarnos para la redención, dar testimonio como hijos de Dios, dar vida, amor, frutos, poder, dones, justicia, paz y gozo, enseñanza, guía, unción, consuelo, fortaleza, recuerdo, aconsejo, interpretación espiritual, revelación, intercesión, mostrar salida de tentación, unidad al cuerpo de Cristo, glorificar a Jesús y ser imprescindible en nuestras vidas.
Mark Stonerock 2-23-16

Mark Stonerock has over 15 years of experience in financial analysis and payroll management. He currently serves as a Senior Financial Analyst for DSW Inc, where he manages a team and $2 billion in annual spend. Previously he held roles as a Payroll Manager and various financial and payroll analyst roles. He has a Bachelor's degree in Business Administration with a double major in Finance and Real Estate from The Ohio State University.
Evolucion de la tecnologia

Este documento describe los principales períodos de desarrollo tecnológico y los cambios estructurales que produjeron las invenciones más significativas en cada época, incluyendo las herramientas de piedra en el Paleolítico, los telares en el Neolítico, la escritura en las culturas antiguas de Egipto y Mesopotamia, los relojes de agua en la sociedad clásica de Grecia y Roma, la pólvora en la Edad Media, la imprenta en el Renacimiento, la
Viewers also liked (6)
Similar to JTAM Poster
Mimikatz

Mimikatz is a tool that enables extracting plain text passwords, hashes, and Kerberos tickets from memory. It can be used to perform pass-the-hash, over-pass-the-hash, and pass-the-ticket authentication attacks. Mimikatz uses the Sekurlsa module to dump credentials stored in the Local Security Authority Subsystem Service (LSASS) process memory. It decrypts encrypted credentials using the same functions LSASS uses, allowing extraction of passwords in plain text. Pass-the-hash allows authenticating with only the NTLM hash by replacing the hash used in authentication with the target user's hash.
ObserveIT -Unix/ Linux session recording

ObserveIT captures all user sessions, for both Unix/Linux users as well as Windows users. As compared to the Windows sessions, ObserveIT includes some additional capabilities that are unique to the Unix and Linux environments.
The Unix/Linux Agent records user activity in any interactive shell running on the machine, and transfers the data to the ObserveIT Management Server. Recording begins whenever a user starts an SSH or Telnet shell login to the system.
ObserveIT captures important hidden information about each user command, by capturing the resources affected and system calls made by each command.
ID304 - Lotus® Connections 3.0 TDI, SSO, and User Life Cycle Management: What...

Presentation that I gave at Lotusphere 2011 with Jay Boyd. We talked about TDI, single sign on, and user management.
Auditing System Password Using L0phtcrack

The objective of this presentation is to help peoples to learn how to use L0htCrack tool to attain and crack the user password from any Windows Machine.
Hardware_root_trust_x86.pptx

This presentation contains details how a typcial modern x86 based PC from Intel establishes hardware root of trust for operation system and application to operate over it afterwards.
Crypto box - crypto casino

The Crypto Casino is unique, transparent and protected from bots gambling system with open-source code. The system was developed using smart contracts.
Check presentation to find more info!
Why SureLog?

SureLog is an integrated log management and next-generation SIEM solution that provides advanced correlation rules, risk calculation, taxonomy, data management, user management, threat intelligence, vulnerability assessment, and statistical reporting. It features an intuitive browser-based UI and supports custom parsers, tagging, and a distributed architecture.
Polling system solution using blockchain & Liferay

Polling system solution using block-chain and Liferay. This presentation explain about Registration, Permission Access, States of Data, Integration of the protocol, single human authentication, Transaction Security, Polling System, Delegation / Casting vote, etc.
I am expecting responses / note on the presentation for further improvement. Please feel free to write us back on info@dfrozensoft.com / sales@dfrozensoft.com / dhanraj@dfrozensoft.com
State of Nevada gaming control board minimal internal control standards_mics_...

STATE OF NEVADA_GAMING CONTROL BOARD_MINIMUM INTERNAL CONTROL STANDARDS or “MICS”_V6.0_OCTOBER 20 , 2011_Contents: Information Technology for Interactive Gaming; Physical Access and Maintenance Controls; Network Security; Remote Access; System Parameters; Structure of Information Technology Department; User Accounts; Generic User Accounts; Service & Default Accounts; Backup and Recovery Procedures; Recordkeeping; Electronic Storage of Documentation; Production Environment Change Control Processes; General Operation of Interactive Gaming; Casino Account Transfers; Registering Authorized PlayersIdentification and Verification of Authorized Players; Protection of the Interactive Gaming Accounts; Interactive Gaming Engaged between Human Individuals; Responsible Interactive Gaming; Protection of Authorized Player’s Personally Identifiable Information; Closed/Inactive Accounts; Authorized Player Disputes; Contests/Tournaments; Promotional Progressive Pots and Pools; Authorized Player Promotional Account; Documentation; Accounting/Audit Standards.
Trusted computing introduction and technical overview

Trusted computing aims to increase confidence in computing platforms by enabling platforms to prove their integrity and identity. The Trusted Computing Group is developing an open standard for a trusted platform module (TPM) that can reliably measure a platform's software state, attest to its identity and properties, and protect confidential data. The TPM acts as a root of trust and provides mechanisms for platform authentication, integrity reporting, and protected storage that enable trust in remote platforms and their expected behavior.
Practical White Hat Hacker Training - Post Exploitation

This presentation part of Prisma CSI's Practical White Hat Hacker Training v1
PRISMA CSI • Cyber Security and Intelligence www.prismacsi.com
This document can be shared or used by quoted and used for commercial purposes, but can not be changed. Detailed information is available at https://creativecommons.org/licenses/by-nc-nd/4.0/legalcode.
Authentication in microservice systems - fsto 2017

This document discusses authentication in microservice systems. It begins by setting the stage and introducing relevant topics. It then builds vocabulary around OAuth2, bearer tokens, JWT, and JWK. It describes authenticating micro frontends using an identity provider, leader/follower pattern, and endpoint middleware. It covers authenticating REST API microservices using bearer token validation. Finally, it addresses authenticating asynchronous messages using client credentials grants and session IDs across message brokers and web sockets. The conclusion summarizes that securing a microservice system involves securing each micro frontend, REST API, and asynchronous flow while maintaining performance and architecture abstraction.
Post Exploitation Using Meterpreter

The document discusses using Meterpreter for post exploitation activities after gaining access to a target system. Meterpreter provides an advanced multi-function payload that injects itself into running processes to provide core and advanced command functionality through extensions in a more stealthy way than normal payloads. The document outlines how Meterpreter works and can be used for activities like enumeration, privilege escalation, information harvesting, and pivoting across a network during post exploitation.
CS304PC:Computer Organization and Architecture Session 7 Microprogrammed con...

CS304PC:Computer Organization and Architecture Session 7 Microprogrammed con...Asst.prof M.Gokilavani
This document discusses the topics covered in Session 7 of the CS304PC course on Computer Organization and Architecture. It introduces microprogrammed control, including control memory, address sequencing, microprograms, and the design of control units. It describes the organization of a microprogrammed control system with separate main and control memories. The control memory stores the microprogram consisting of microinstructions that specify internal control signals. The next address generator determines the address sequence read from control memory. Advantages of microprogrammed control are that the hardware does not need to change for different operations - only the microprogram in control memory needs to change.Control Memory.pptx

The function of the control unit in a digital computer is to initiate
sequences of micro operations.
Rapport ICO Rating

The document analyzes the security of 100 cryptocurrency exchanges across four categories: console errors, user account security, registrar and domain security, and web protocols security. Key findings include:
- 32% of exchanges have code errors, 68% have no errors
- Only 46% of exchanges meet all user account security best practices
- Only 2% use registry lock and 10% use DNSSEC for domain security
- Only 10% have all recommended web protocol security headers
The report ranks exchanges based on their scores in each category, with Coinbase Pro, Kraken, and BitMEX receiving the top three scores overall for exchange security.
Managing bitlocker with MBAM

A look on Microsoft Desktop optimization Pack's MBAM for administration and management of Bitlocker computers
presentation_finals

This document discusses the development of a user-friendly application for public-key cryptosystem using OpenSSL. The application aims to allow users to securely transmit data with limited cryptographic knowledge through an easy-to-use interface. It generates key pairs, signs and verifies signatures, encrypts and decrypts data, and combines signature and encryption functions. The application was created using Java, OpenSSL crypto libraries, and supports FIPS 140-2 compliant crypto tokens for security. It provides a simple click-based interface for cryptographic tasks to reduce the effort for users.
Breaking hardware enforced security with hypervisors

"Hardware-Enforced Security is touted as the panacea solution to many modern computer security challenges. While certainly adding robust options to the defenders toolset, they are not without their own weaknesses. In this talk we will demonstrate how low-level technologies such as hypervisors can be used to subvert the claims of security made by these mechanisms. Specifically, we will show how a hypervisor rootkit can bypass Intel's Trusted Execution Environment (TXT) DRTM (dynamic root of trust measurement) and capture keys from Intel's AES-NI instructions. These attacks against TXT and AES-NI have never been published before. Trusted computing has had a varied history, to include technologies such as Trusted Execution Technology (TXT), ARM TrustZone, and now Microsoft Isolated User Mode and Intel SGX. All of these technologies attempt to protect user data from privileged processes snooping or controlling execution. These technologies claim that no elevated process, whether kernel based, System Management Mode (SMM) based, or hypervisor based will be able to compromise the user's data and execution.
This presentation will highlight the age-old problem of misconfiguration of Intel TXT by exploiting a machine through the use of another Intel technology, the Type-1 hypervisor (VT-x). Problems with these technologies have surfaced not as design issues but during implementation. Whether there remains a hardware weakness where attestation keys can be compromised, or a software and hardware combination, such as exposed DMA that permits exfiltration, and sometimes modification, of user process memory. This presentation will highlight one of these implementation flaws as exhibited by the open source tBoot project and the underlying Intel TXT technology. Summation will offer defenses against all too often pitfalls when deploying these systems, including proper deployment design using sealed storage, remote attestation, and hardware hardening."
(Source: Black Hat USA 2016, Las Vegas)
DevOps Braga #3: Admin rights, everyone gets Admin rights!

1) The document discusses various scenarios where an attacker could gain administrative access to a Windows domain network with only brief access to an insider computer.
2) It describes techniques like Pass the Hash, Pass the Ticket, Kerberos delegation, and DCShadow that could be used by an attacker to escalate privileges within the domain.
3) Mitigation strategies are proposed, including implementing Microsoft guidance to strengthen password and authentication security, and using a security information and event management system to monitor the Active Directory for anomalies.
Similar to JTAM Poster (20)
ID304 - Lotus® Connections 3.0 TDI, SSO, and User Life Cycle Management: What...

ID304 - Lotus® Connections 3.0 TDI, SSO, and User Life Cycle Management: What...
Polling system solution using blockchain & Liferay

Polling system solution using blockchain & Liferay
State of Nevada gaming control board minimal internal control standards_mics_...

State of Nevada gaming control board minimal internal control standards_mics_...
Trusted computing introduction and technical overview

Trusted computing introduction and technical overview
Practical White Hat Hacker Training - Post Exploitation

Practical White Hat Hacker Training - Post Exploitation
Authentication in microservice systems - fsto 2017

Authentication in microservice systems - fsto 2017
CS304PC:Computer Organization and Architecture Session 7 Microprogrammed con...

CS304PC:Computer Organization and Architecture Session 7 Microprogrammed con...
Breaking hardware enforced security with hypervisors

Breaking hardware enforced security with hypervisors
DevOps Braga #3: Admin rights, everyone gets Admin rights!

DevOps Braga #3: Admin rights, everyone gets Admin rights!
Recently uploaded
dbms calicut university B. sc Cs 4th sem.pdf

Its a seminar ppt on database management system using sql
Best 20 SEO Techniques To Improve Website Visibility In SERP

Boost your website's visibility with proven SEO techniques! Our latest blog dives into essential strategies to enhance your online presence, increase traffic, and rank higher on search engines. From keyword optimization to quality content creation, learn how to make your site stand out in the crowded digital landscape. Discover actionable tips and expert insights to elevate your SEO game.
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Simplify your search for a reliable Python development partner! This list presents the top 10 trusted US providers offering comprehensive Python development services, ensuring your project's success from conception to completion.
Freshworks Rethinks NoSQL for Rapid Scaling & Cost-Efficiency

Freshworks creates AI-boosted business software that helps employees work more efficiently and effectively. Managing data across multiple RDBMS and NoSQL databases was already a challenge at their current scale. To prepare for 10X growth, they knew it was time to rethink their database strategy. Learn how they architected a solution that would simplify scaling while keeping costs under control.
TrustArc Webinar - 2024 Global Privacy Survey

How does your privacy program stack up against your peers? What challenges are privacy teams tackling and prioritizing in 2024?
In the fifth annual Global Privacy Benchmarks Survey, we asked over 1,800 global privacy professionals and business executives to share their perspectives on the current state of privacy inside and outside of their organizations. This year’s report focused on emerging areas of importance for privacy and compliance professionals, including considerations and implications of Artificial Intelligence (AI) technologies, building brand trust, and different approaches for achieving higher privacy competence scores.
See how organizational priorities and strategic approaches to data security and privacy are evolving around the globe.
This webinar will review:
- The top 10 privacy insights from the fifth annual Global Privacy Benchmarks Survey
- The top challenges for privacy leaders, practitioners, and organizations in 2024
- Key themes to consider in developing and maintaining your privacy program
Generating privacy-protected synthetic data using Secludy and Milvus

During this demo, the founders of Secludy will demonstrate how their system utilizes Milvus to store and manipulate embeddings for generating privacy-protected synthetic data. Their approach not only maintains the confidentiality of the original data but also enhances the utility and scalability of LLMs under privacy constraints. Attendees, including machine learning engineers, data scientists, and data managers, will witness first-hand how Secludy's integration with Milvus empowers organizations to harness the power of LLMs securely and efficiently.
JavaLand 2024: Application Development Green Masterplan

My presentation slides I used at JavaLand 2024
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-und-domino-lizenzkostenreduzierung-in-der-welt-von-dlau/
DLAU und die Lizenzen nach dem CCB- und CCX-Modell sind für viele in der HCL-Community seit letztem Jahr ein heißes Thema. Als Notes- oder Domino-Kunde haben Sie vielleicht mit unerwartet hohen Benutzerzahlen und Lizenzgebühren zu kämpfen. Sie fragen sich vielleicht, wie diese neue Art der Lizenzierung funktioniert und welchen Nutzen sie Ihnen bringt. Vor allem wollen Sie sicherlich Ihr Budget einhalten und Kosten sparen, wo immer möglich. Das verstehen wir und wir möchten Ihnen dabei helfen!
Wir erklären Ihnen, wie Sie häufige Konfigurationsprobleme lösen können, die dazu führen können, dass mehr Benutzer gezählt werden als nötig, und wie Sie überflüssige oder ungenutzte Konten identifizieren und entfernen können, um Geld zu sparen. Es gibt auch einige Ansätze, die zu unnötigen Ausgaben führen können, z. B. wenn ein Personendokument anstelle eines Mail-Ins für geteilte Mailboxen verwendet wird. Wir zeigen Ihnen solche Fälle und deren Lösungen. Und natürlich erklären wir Ihnen das neue Lizenzmodell.
Nehmen Sie an diesem Webinar teil, bei dem HCL-Ambassador Marc Thomas und Gastredner Franz Walder Ihnen diese neue Welt näherbringen. Es vermittelt Ihnen die Tools und das Know-how, um den Überblick zu bewahren. Sie werden in der Lage sein, Ihre Kosten durch eine optimierte Domino-Konfiguration zu reduzieren und auch in Zukunft gering zu halten.
Diese Themen werden behandelt
- Reduzierung der Lizenzkosten durch Auffinden und Beheben von Fehlkonfigurationen und überflüssigen Konten
- Wie funktionieren CCB- und CCX-Lizenzen wirklich?
- Verstehen des DLAU-Tools und wie man es am besten nutzt
- Tipps für häufige Problembereiche, wie z. B. Team-Postfächer, Funktions-/Testbenutzer usw.
- Praxisbeispiele und Best Practices zum sofortigen Umsetzen
GNSS spoofing via SDR (Criptored Talks 2024)

In the realm of cybersecurity, offensive security practices act as a critical shield. By simulating real-world attacks in a controlled environment, these techniques expose vulnerabilities before malicious actors can exploit them. This proactive approach allows manufacturers to identify and fix weaknesses, significantly enhancing system security.
This presentation delves into the development of a system designed to mimic Galileo's Open Service signal using software-defined radio (SDR) technology. We'll begin with a foundational overview of both Global Navigation Satellite Systems (GNSS) and the intricacies of digital signal processing.
The presentation culminates in a live demonstration. We'll showcase the manipulation of Galileo's Open Service pilot signal, simulating an attack on various software and hardware systems. This practical demonstration serves to highlight the potential consequences of unaddressed vulnerabilities, emphasizing the importance of offensive security practices in safeguarding critical infrastructure.
June Patch Tuesday

Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
Fueling AI with Great Data with Airbyte Webinar

This talk will focus on how to collect data from a variety of sources, leveraging this data for RAG and other GenAI use cases, and finally charting your course to productionalization.
Astute Business Solutions | Oracle Cloud Partner |

Your goto partner for Oracle Cloud, PeopleSoft, E-Business Suite, and Ellucian Banner. We are a firm specialized in managed services and consulting.
Azure API Management to expose backend services securely

How to use Azure API Management to expose backend service securely
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Discover the seamless integration of RPA (Robotic Process Automation), COMPOSER, and APM with AWS IDP enhanced with Slack notifications. Explore how these technologies converge to streamline workflows, optimize performance, and ensure secure access, all while leveraging the power of AWS IDP and real-time communication via Slack notifications.
A Comprehensive Guide to DeFi Development Services in 2024

DeFi represents a paradigm shift in the financial industry. Instead of relying on traditional, centralized institutions like banks, DeFi leverages blockchain technology to create a decentralized network of financial services. This means that financial transactions can occur directly between parties, without intermediaries, using smart contracts on platforms like Ethereum.
In 2024, we are witnessing an explosion of new DeFi projects and protocols, each pushing the boundaries of what’s possible in finance.
In summary, DeFi in 2024 is not just a trend; it’s a revolution that democratizes finance, enhances security and transparency, and fosters continuous innovation. As we proceed through this presentation, we'll explore the various components and services of DeFi in detail, shedding light on how they are transforming the financial landscape.
At Intelisync, we specialize in providing comprehensive DeFi development services tailored to meet the unique needs of our clients. From smart contract development to dApp creation and security audits, we ensure that your DeFi project is built with innovation, security, and scalability in mind. Trust Intelisync to guide you through the intricate landscape of decentralized finance and unlock the full potential of blockchain technology.
Ready to take your DeFi project to the next level? Partner with Intelisync for expert DeFi development services today!
Skybuffer SAM4U tool for SAP license adoption

Manage and optimize your license adoption and consumption with SAM4U, an SAP free customer software asset management tool.
SAM4U, an SAP complimentary software asset management tool for customers, delivers a detailed and well-structured overview of license inventory and usage with a user-friendly interface. We offer a hosted, cost-effective, and performance-optimized SAM4U setup in the Skybuffer Cloud environment. You retain ownership of the system and data, while we manage the ABAP 7.58 infrastructure, ensuring fixed Total Cost of Ownership (TCO) and exceptional services through the SAP Fiori interface.
leewayhertz.com-AI in predictive maintenance Use cases technologies benefits ...

Predictive maintenance is a proactive approach that anticipates equipment failures before they happen. At the forefront of this innovative strategy is Artificial Intelligence (AI), which brings unprecedented precision and efficiency. AI in predictive maintenance is transforming industries by reducing downtime, minimizing costs, and enhancing productivity.
AWS Cloud Cost Optimization Presentation.pptx

This presentation provides valuable insights into effective cost-saving techniques on AWS. Learn how to optimize your AWS resources by rightsizing, increasing elasticity, picking the right storage class, and choosing the best pricing model. Additionally, discover essential governance mechanisms to ensure continuous cost efficiency. Whether you are new to AWS or an experienced user, this presentation provides clear and practical tips to help you reduce your cloud costs and get the most out of your budget.
Building Production Ready Search Pipelines with Spark and Milvus

Spark is the widely used ETL tool for processing, indexing and ingesting data to serving stack for search. Milvus is the production-ready open-source vector database. In this talk we will show how to use Spark to process unstructured data to extract vector representations, and push the vectors to Milvus vector database for search serving.
Main news related to the CCS TSI 2023 (2023/1695)

An English 🇬🇧 translation of a presentation to the speech I gave about the main changes brought by CCS TSI 2023 at the biggest Czech conference on Communications and signalling systems on Railways, which was held in Clarion Hotel Olomouc from 7th to 9th November 2023 (konferenceszt.cz). Attended by around 500 participants and 200 on-line followers.
The original Czech 🇨🇿 version of the presentation can be found here: https://www.slideshare.net/slideshow/hlavni-novinky-souvisejici-s-ccs-tsi-2023-2023-1695/269688092 .
The videorecording (in Czech) from the presentation is available here: https://youtu.be/WzjJWm4IyPk?si=SImb06tuXGb30BEH .
Recently uploaded (20)
Best 20 SEO Techniques To Improve Website Visibility In SERP

Best 20 SEO Techniques To Improve Website Visibility In SERP
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Your One-Stop Shop for Python Success: Top 10 US Python Development Providers
Freshworks Rethinks NoSQL for Rapid Scaling & Cost-Efficiency

Freshworks Rethinks NoSQL for Rapid Scaling & Cost-Efficiency
Generating privacy-protected synthetic data using Secludy and Milvus

Generating privacy-protected synthetic data using Secludy and Milvus
JavaLand 2024: Application Development Green Masterplan

JavaLand 2024: Application Development Green Masterplan
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU
Astute Business Solutions | Oracle Cloud Partner |

Astute Business Solutions | Oracle Cloud Partner |
Azure API Management to expose backend services securely

Azure API Management to expose backend services securely
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack
A Comprehensive Guide to DeFi Development Services in 2024

A Comprehensive Guide to DeFi Development Services in 2024
leewayhertz.com-AI in predictive maintenance Use cases technologies benefits ...

leewayhertz.com-AI in predictive maintenance Use cases technologies benefits ...
Building Production Ready Search Pipelines with Spark and Milvus

Building Production Ready Search Pipelines with Spark and Milvus
JTAM Poster
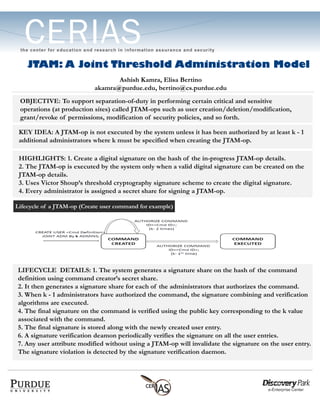
- 1. JTAM: A Joint Threshold Administration ModelJTAM: A Joint Threshold Administration Model Ashish Kamra, Elisa Bertino akamra@purdue.edu, bertino@cs.purdue.edu OBJECTIVE: To support separation-of-duty in performing certain critical and sensitive operations (at production sites) called JTAM-ops such as user creation/deletion/modification, grant/revoke of permissions, modification of security policies, and so forth. KEY IDEA: A JTAM-op is not executed by the system unless it has been authorized by at least k - 1 additional administrators where k must be specified when creating the JTAM-op. HIGHLIGHTS: 1. Create a digital signature on the hash of the in-progress JTAM-op details. 2. The JTAM-op is executed by the system only when a valid digital signature can be created on the JTAM-op details. 3. Uses Victor Shoup’s threshold cryptography signature scheme to create the digital signature. 4. Every administrator is assigned a secret share for signing a JTAM-op. Lifecycle of a JTAM-op (Create user command for example)Lifecycle of a JTAM-op (Create user command for example) LIFECYCLE DETAILS: 1. The system generates a signature share on the hash of the command definition using command creator’s secret share. 2. It then generates a signature share for each of the administrators that authorizes the command. 3. When k - 1 administrators have authorized the command, the signature combining and verification algorithms are executed. 4. The final signature on the command is verified using the public key corresponding to the k value associated with the command. 5. The final signature is stored along with the newly created user entry. 6. A signature verification deamon periodically verifies the signature on all the user entries. 7. Any user attribute modified without using a JTAM-op will invalidate the signature on the user entry. The signature violation is detected by the signature verification daemon.