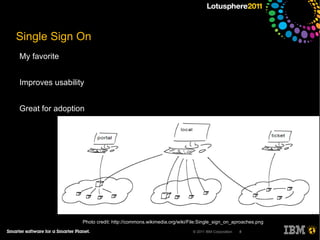
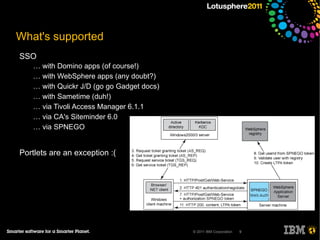
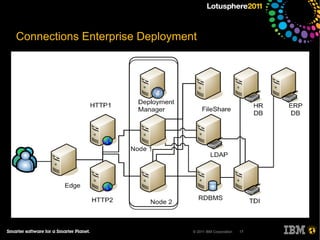
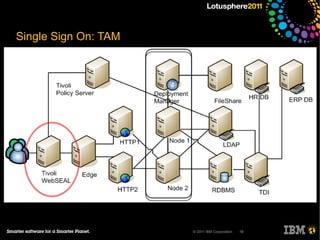
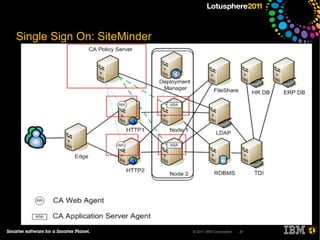
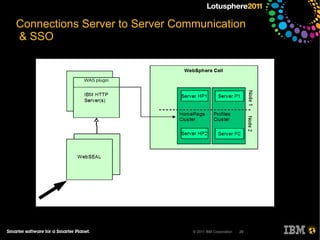
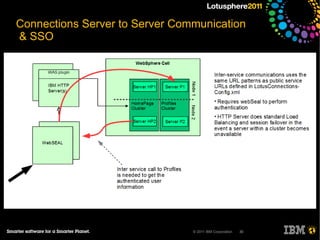
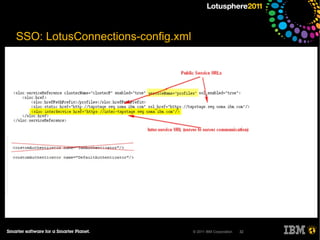
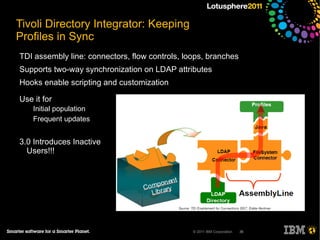
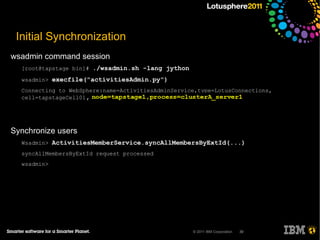
The document outlines security options and user life cycle management for IBM's Lotus Connections 3.0. It covers single sign-on (SSO) configurations using various protocols such as LTPA, SPNEGO, and Siteminder, along with troubleshooting tips and the integration of Tivoli Directory Integrator for profile synchronization. Additionally, it discusses the importance of maintaining data integrity and simplifying user management processes within the application.