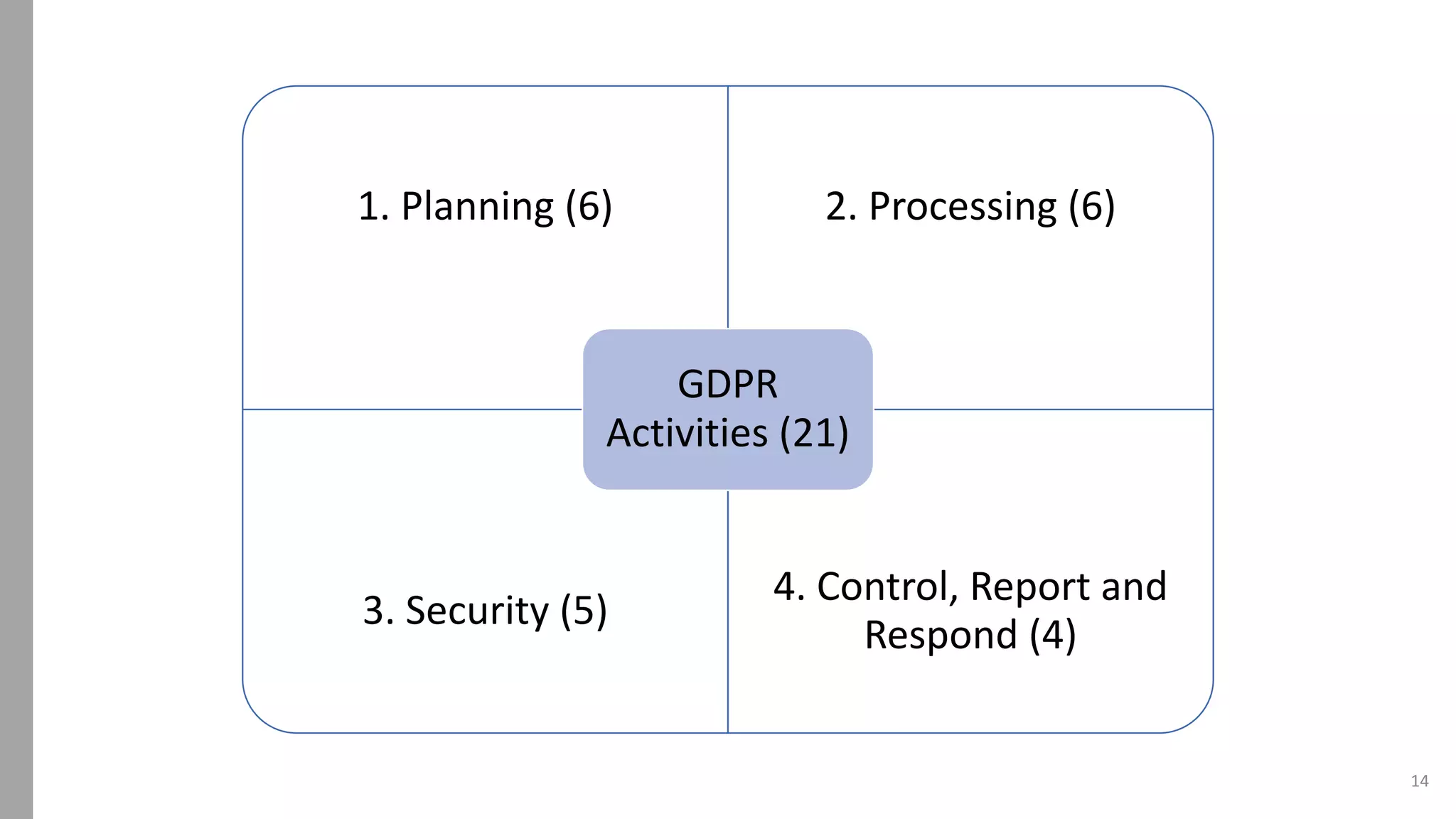
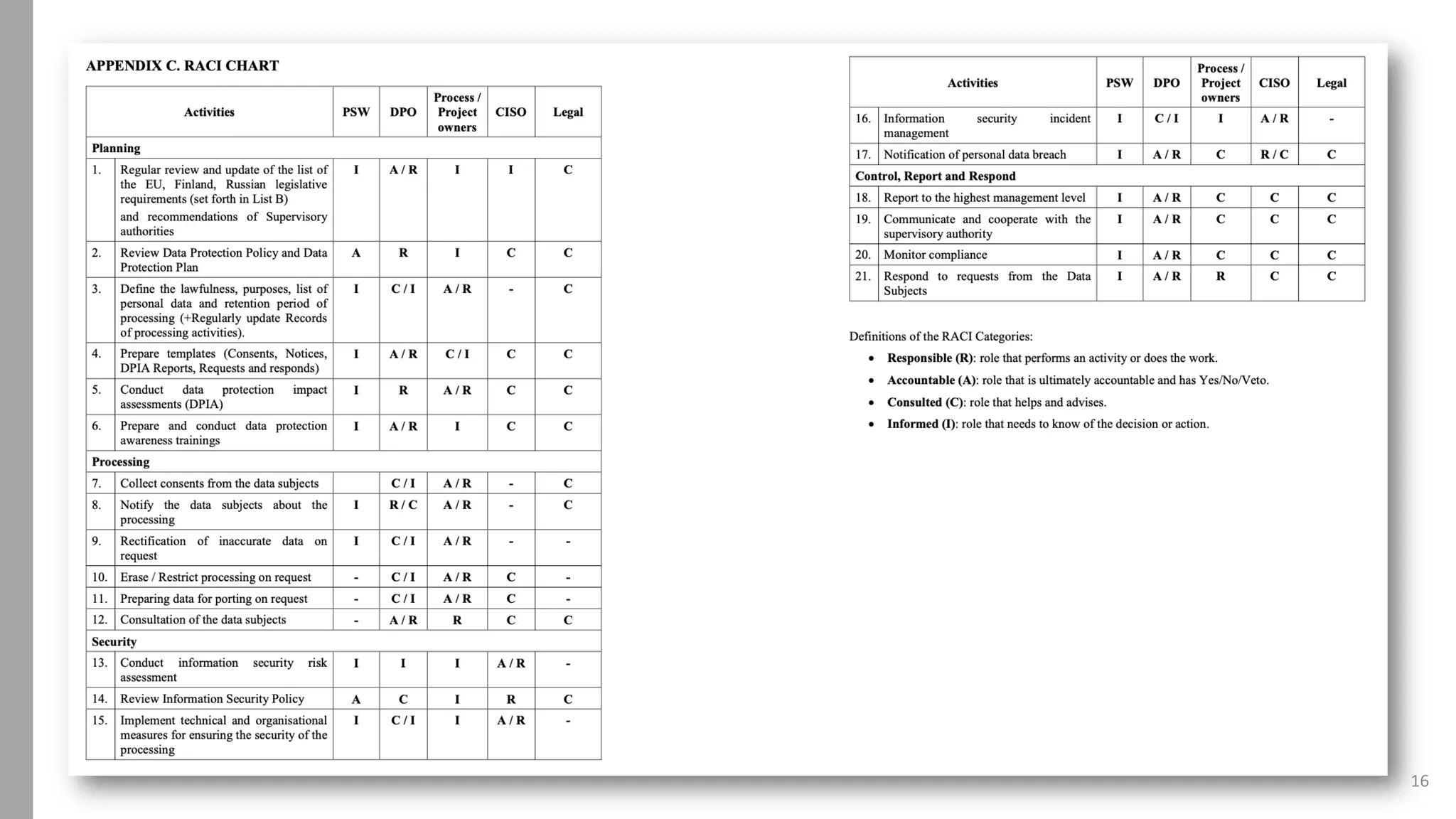
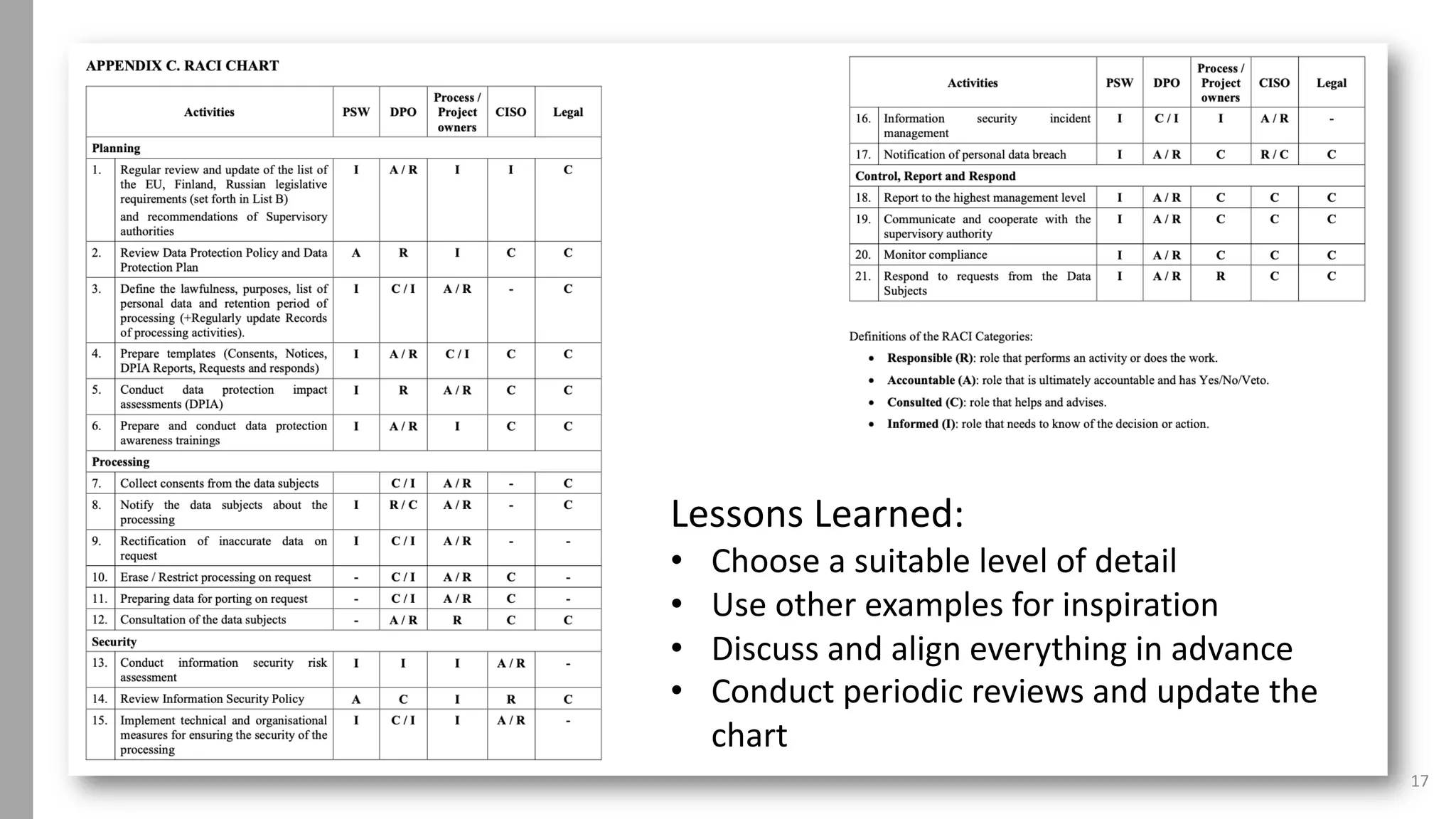
The document discusses using a RACI (Responsible, Accountable, Consulted, Informed) chart to assign roles and responsibilities for GDPR implementation. It provides an introduction to RACI charts, an example from the speaker's company that outlines its data protection framework, governance model and 21 GDPR activities, and the speaker's resulting RACI chart. The speaker advocates for RACI charts to provide a clear overview of participation in tasks and recommends periodic reviews to keep the chart updated.