Embed presentation


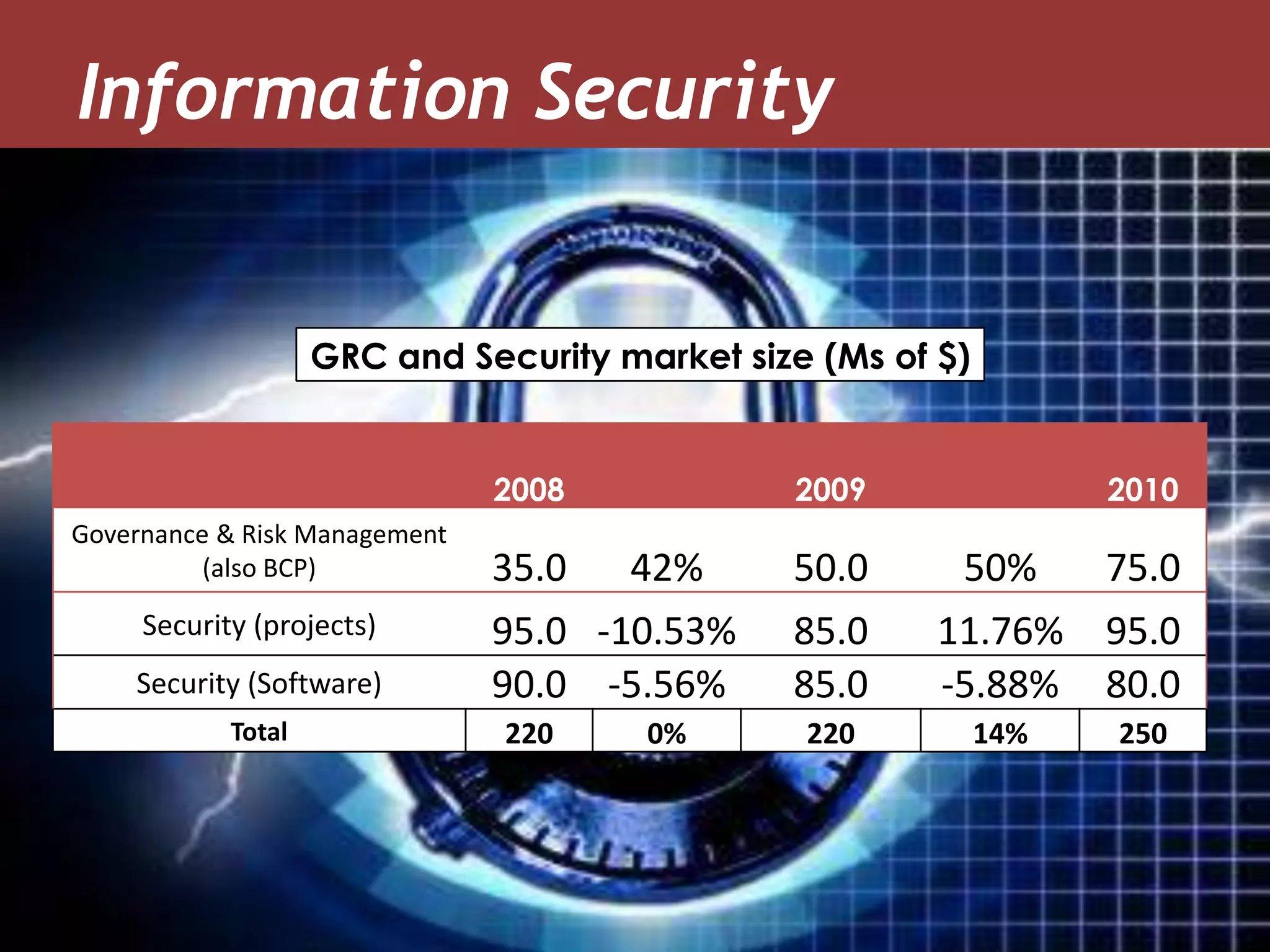

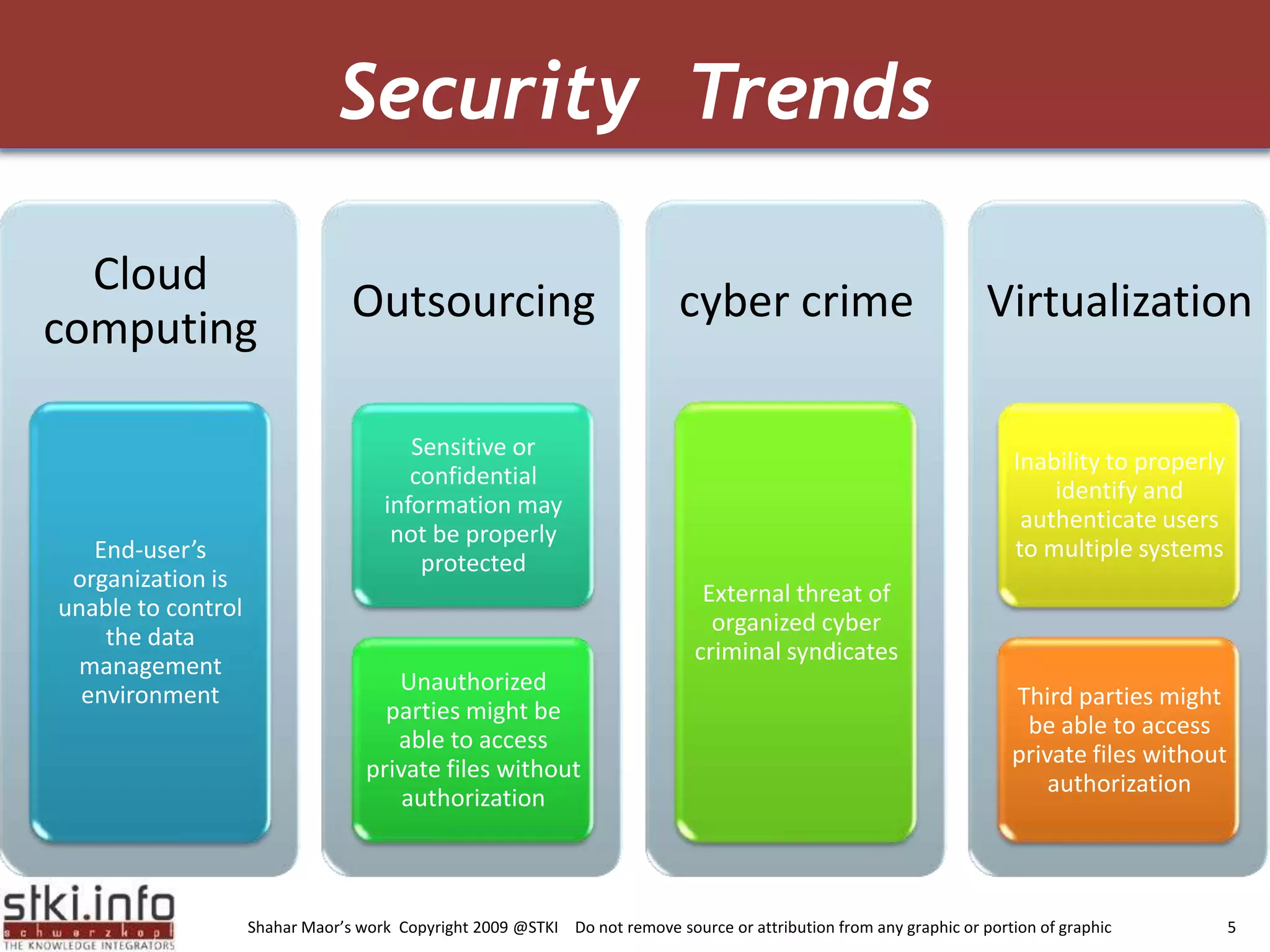
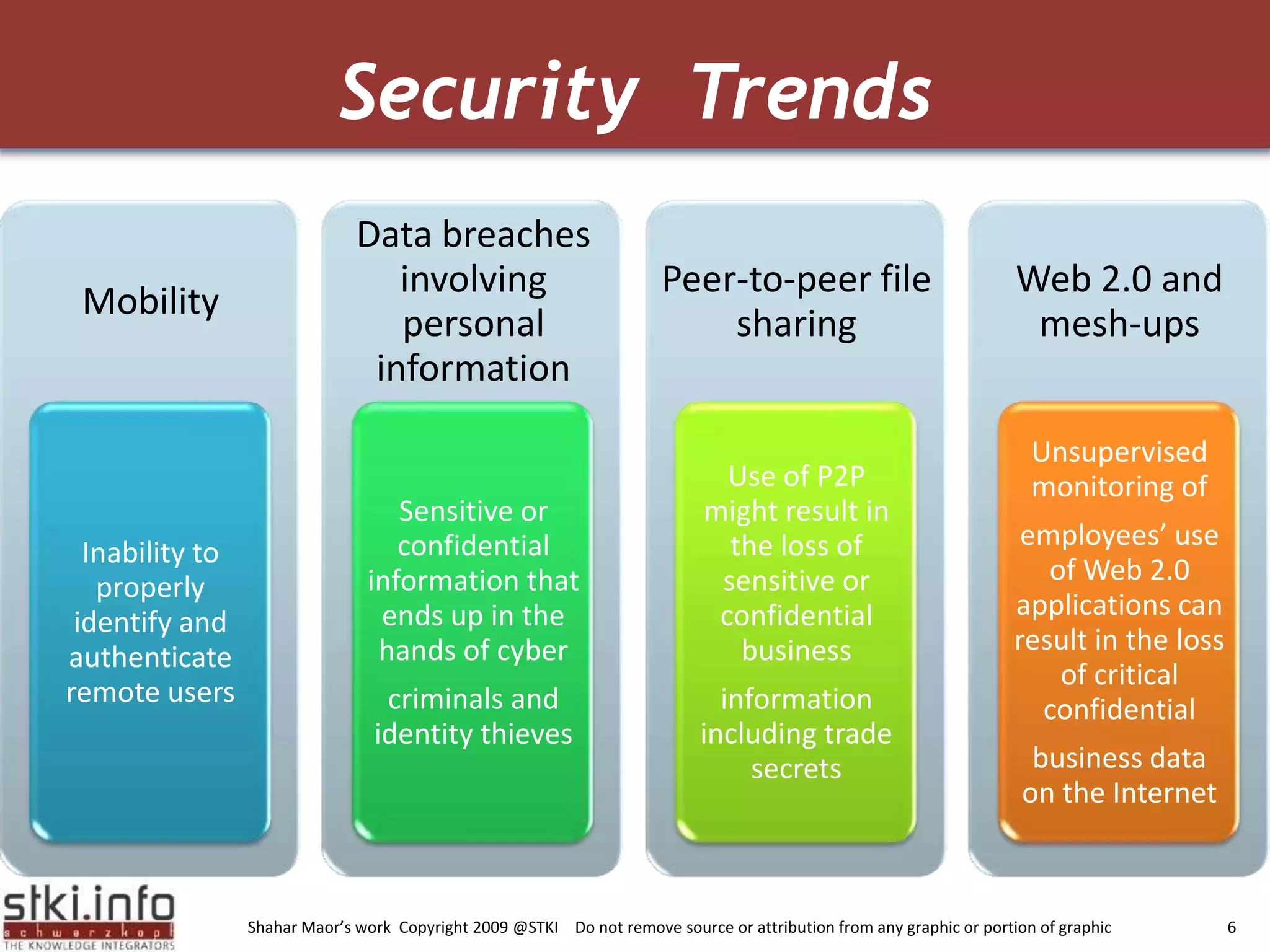

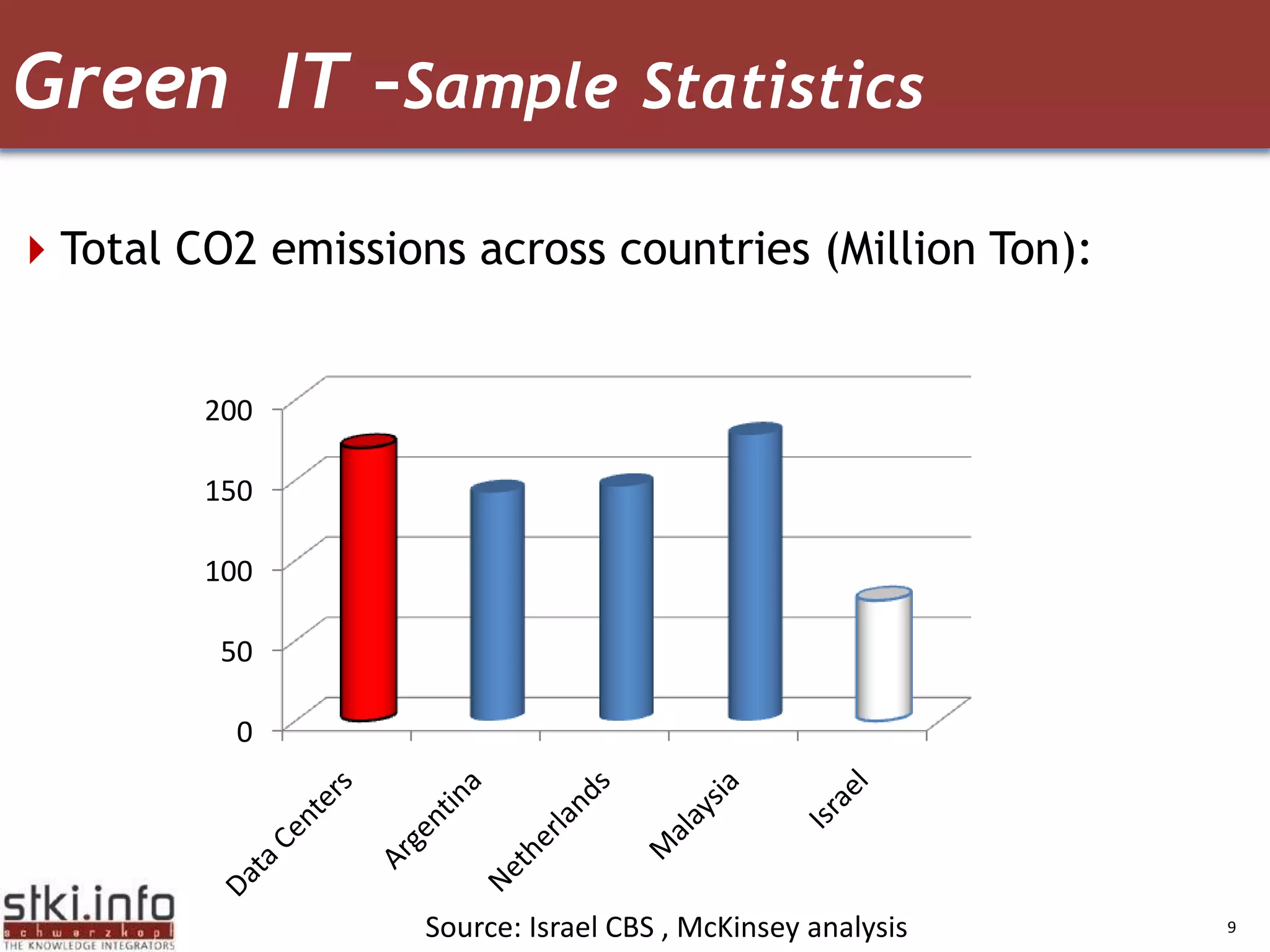
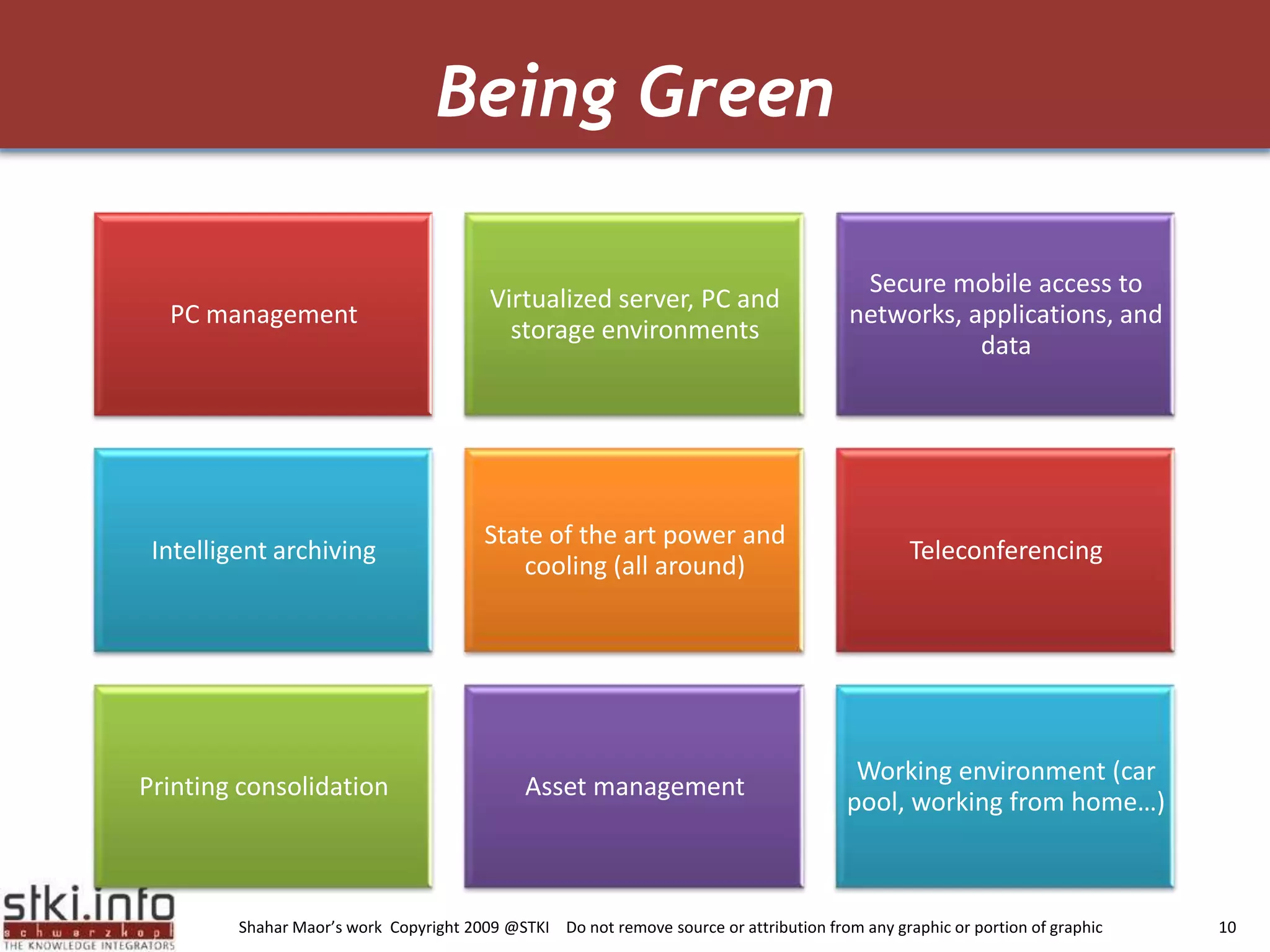
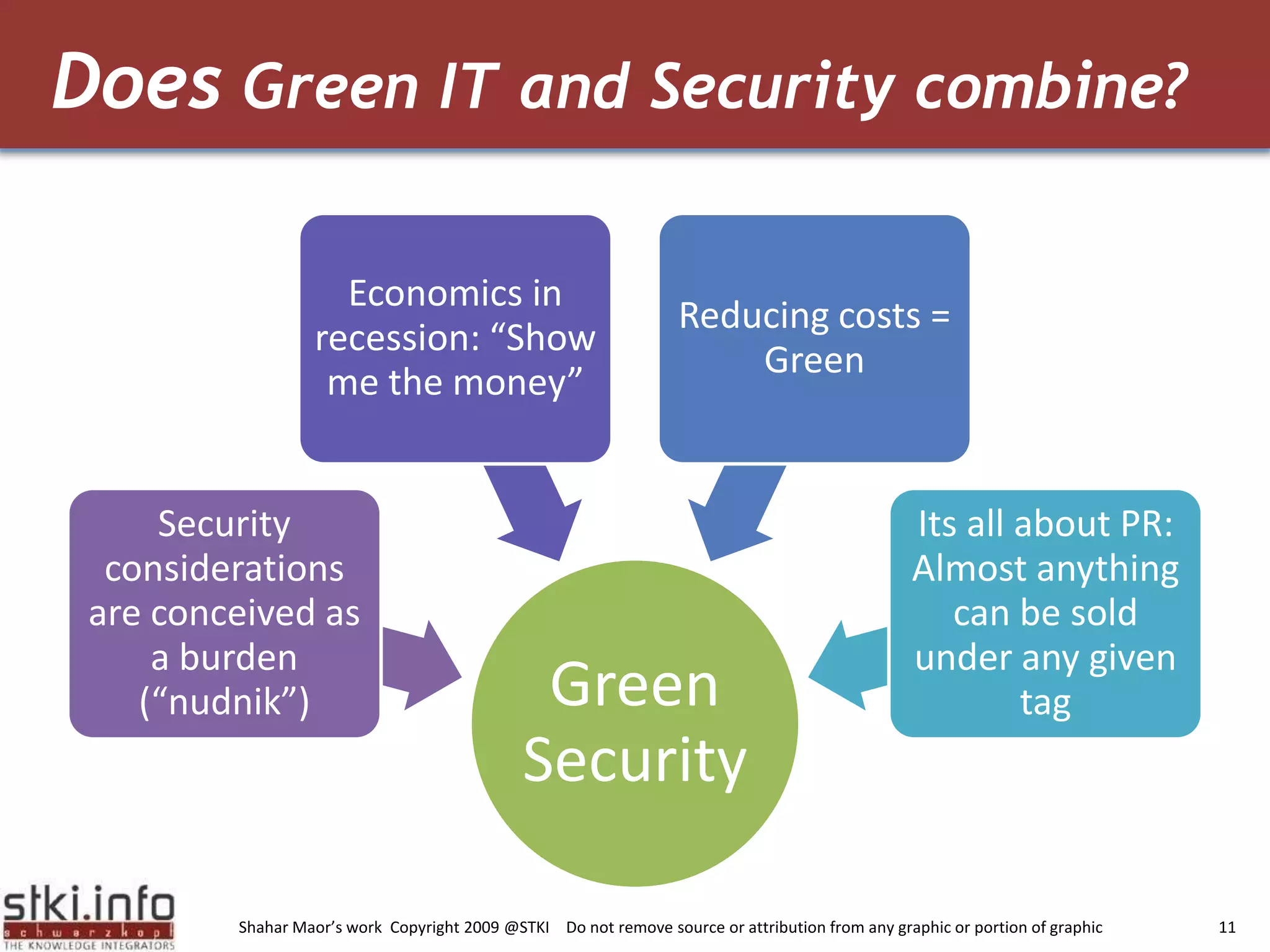
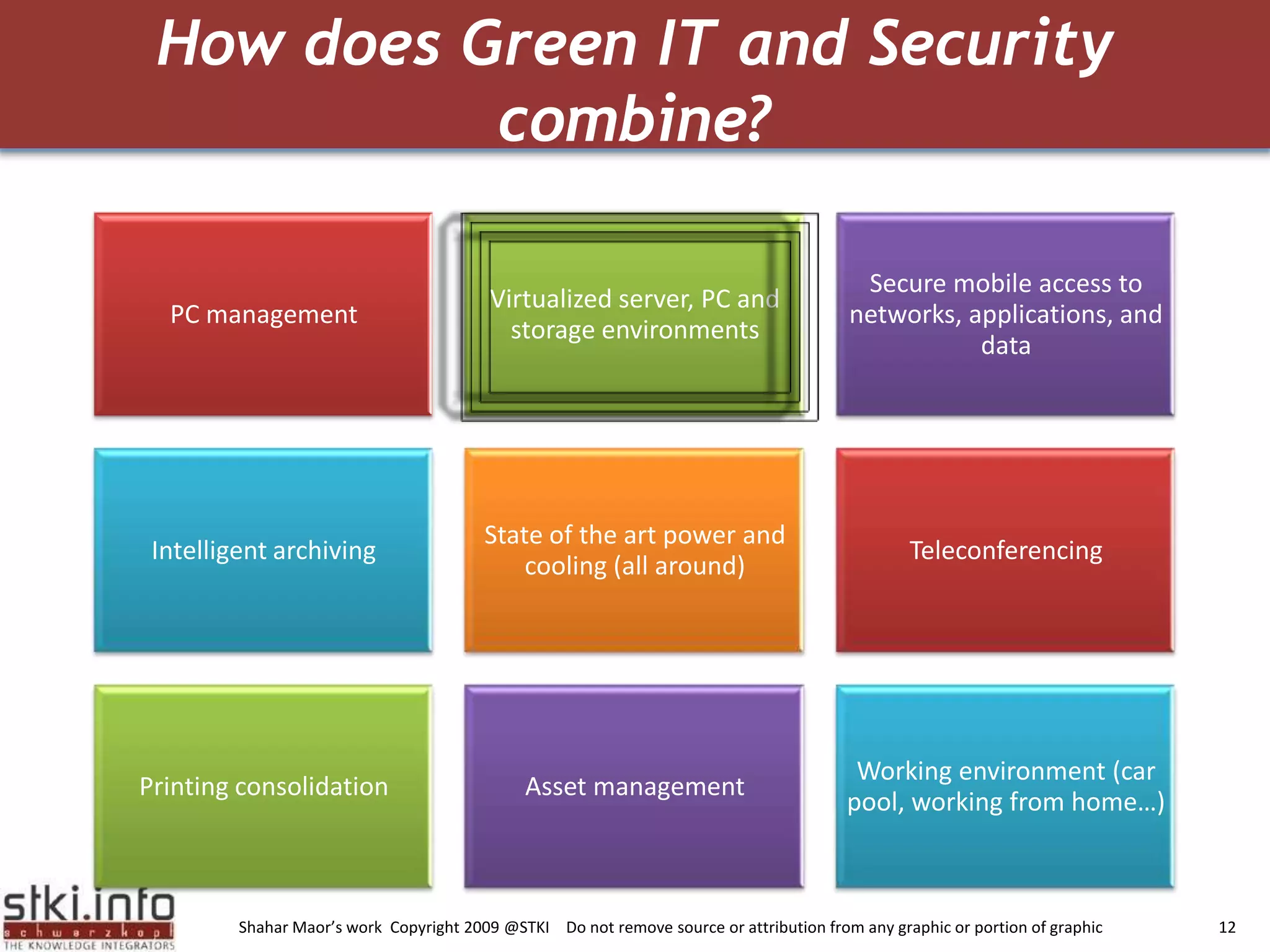
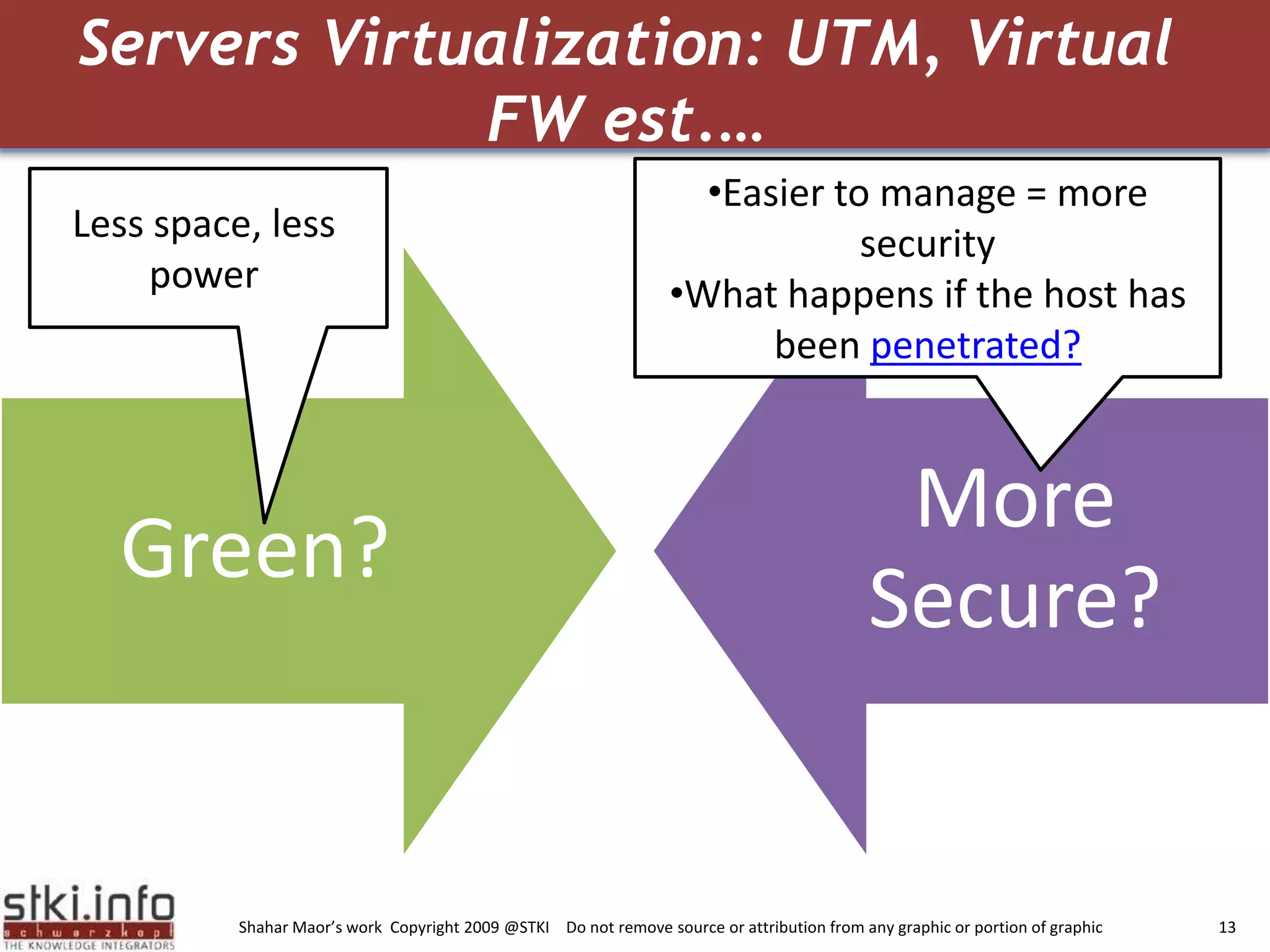
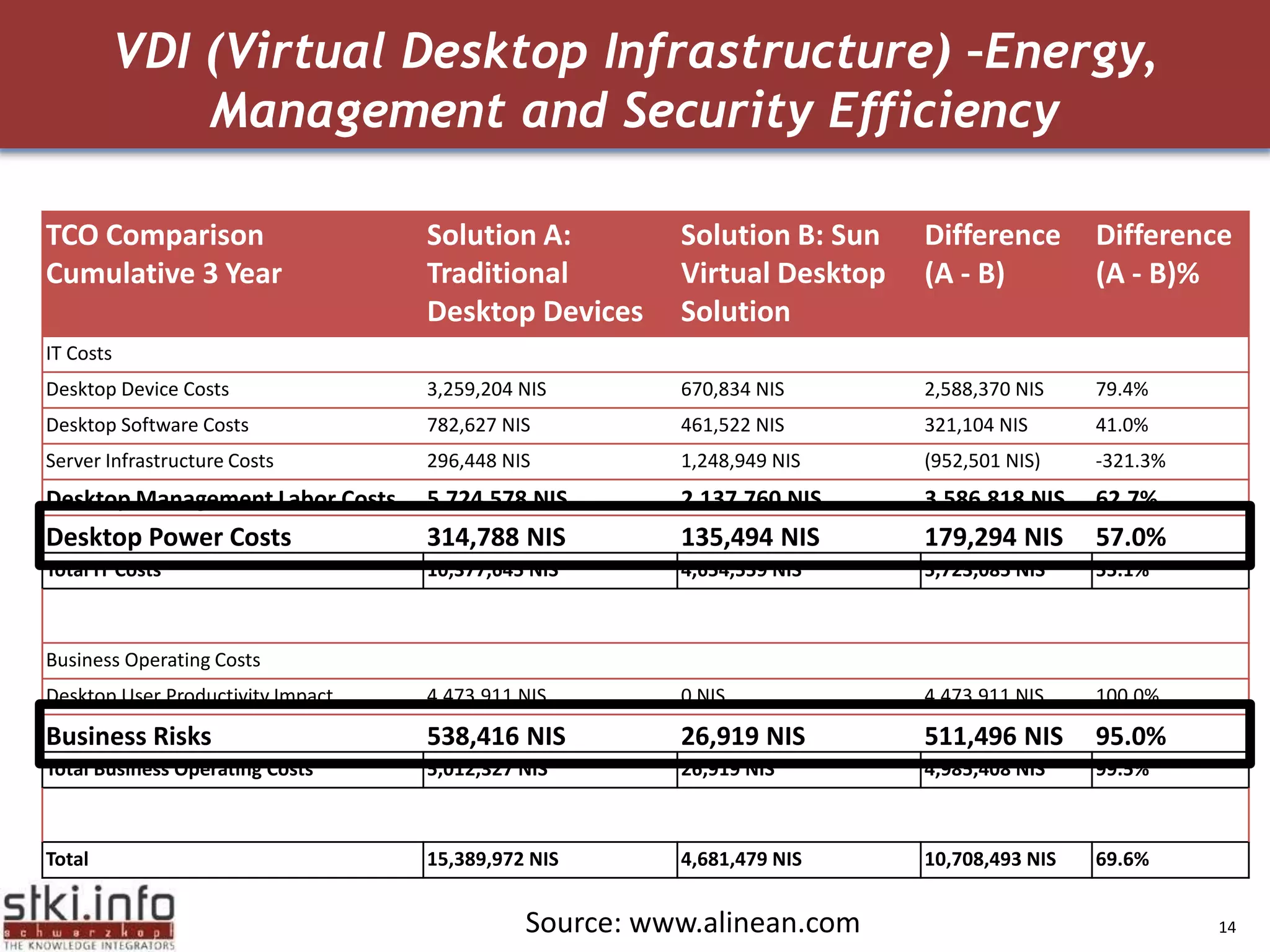
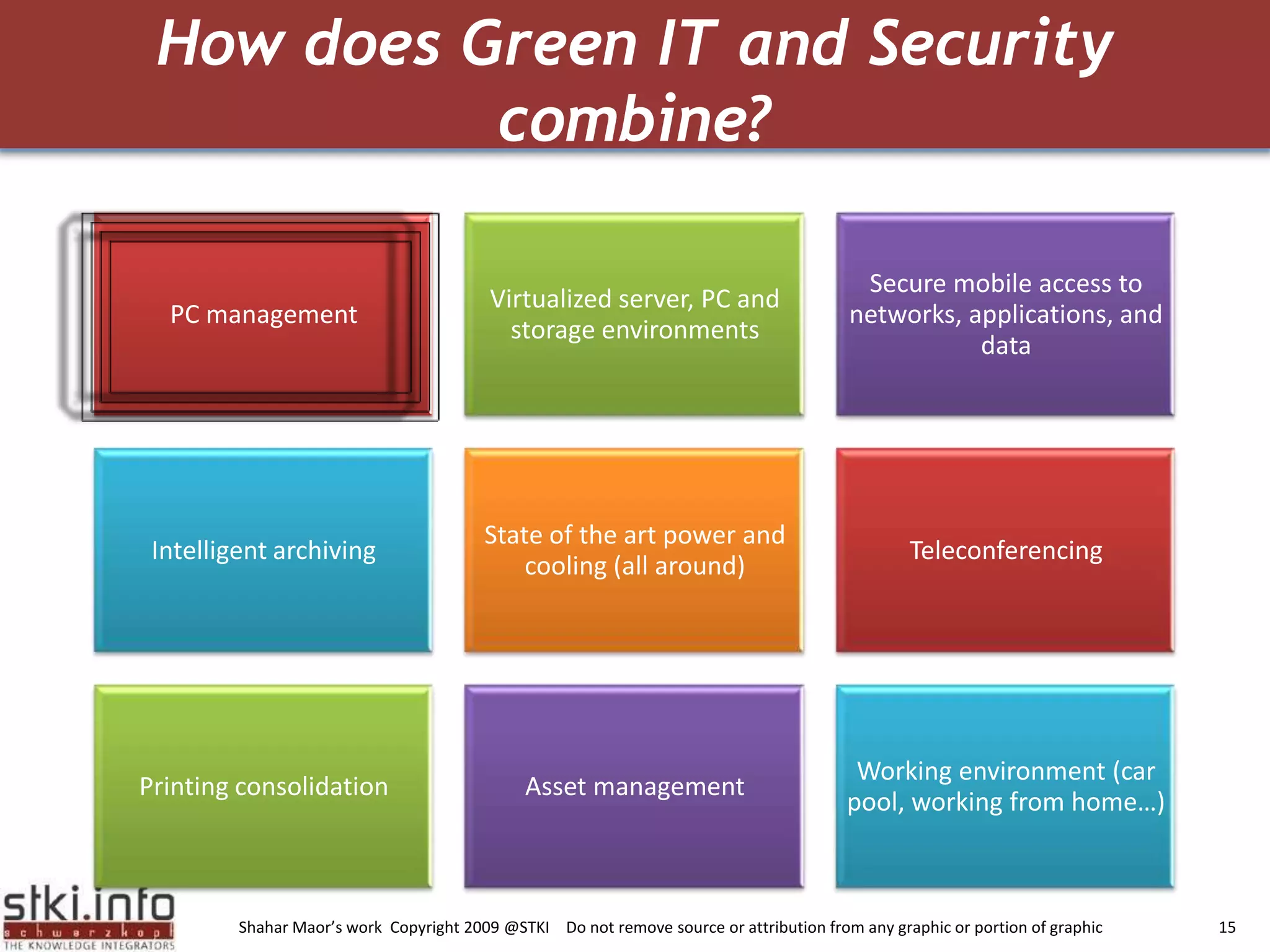
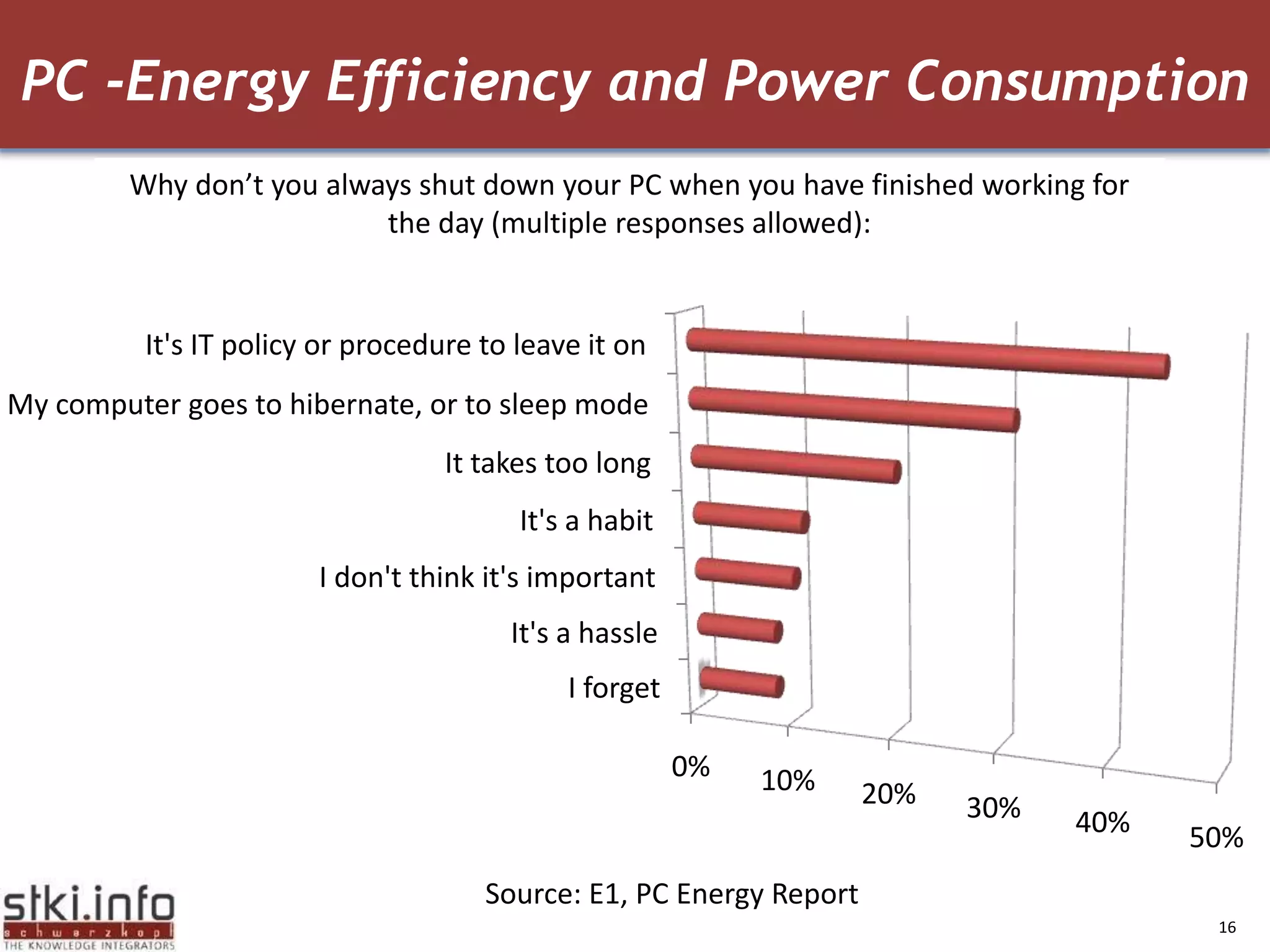
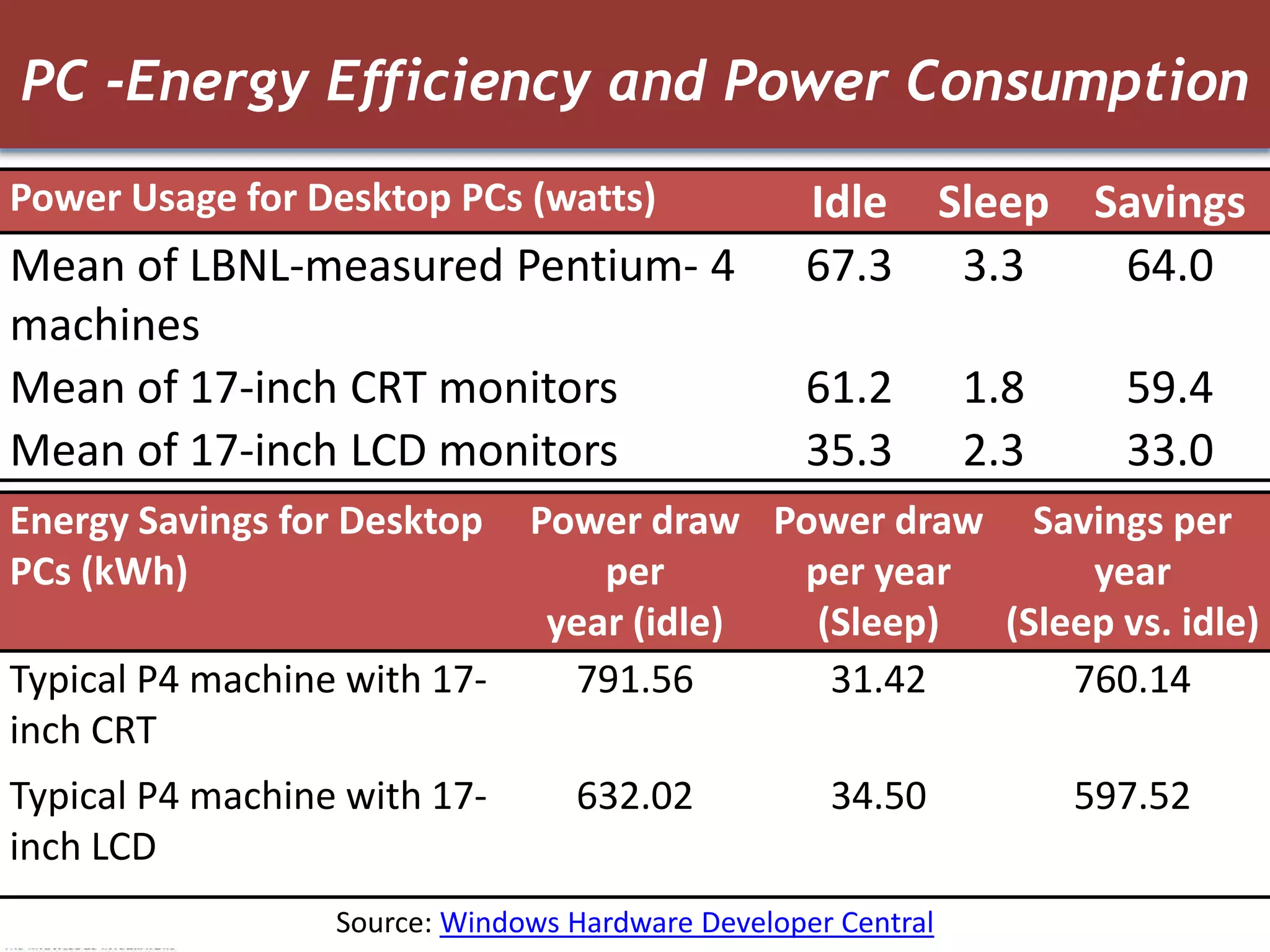
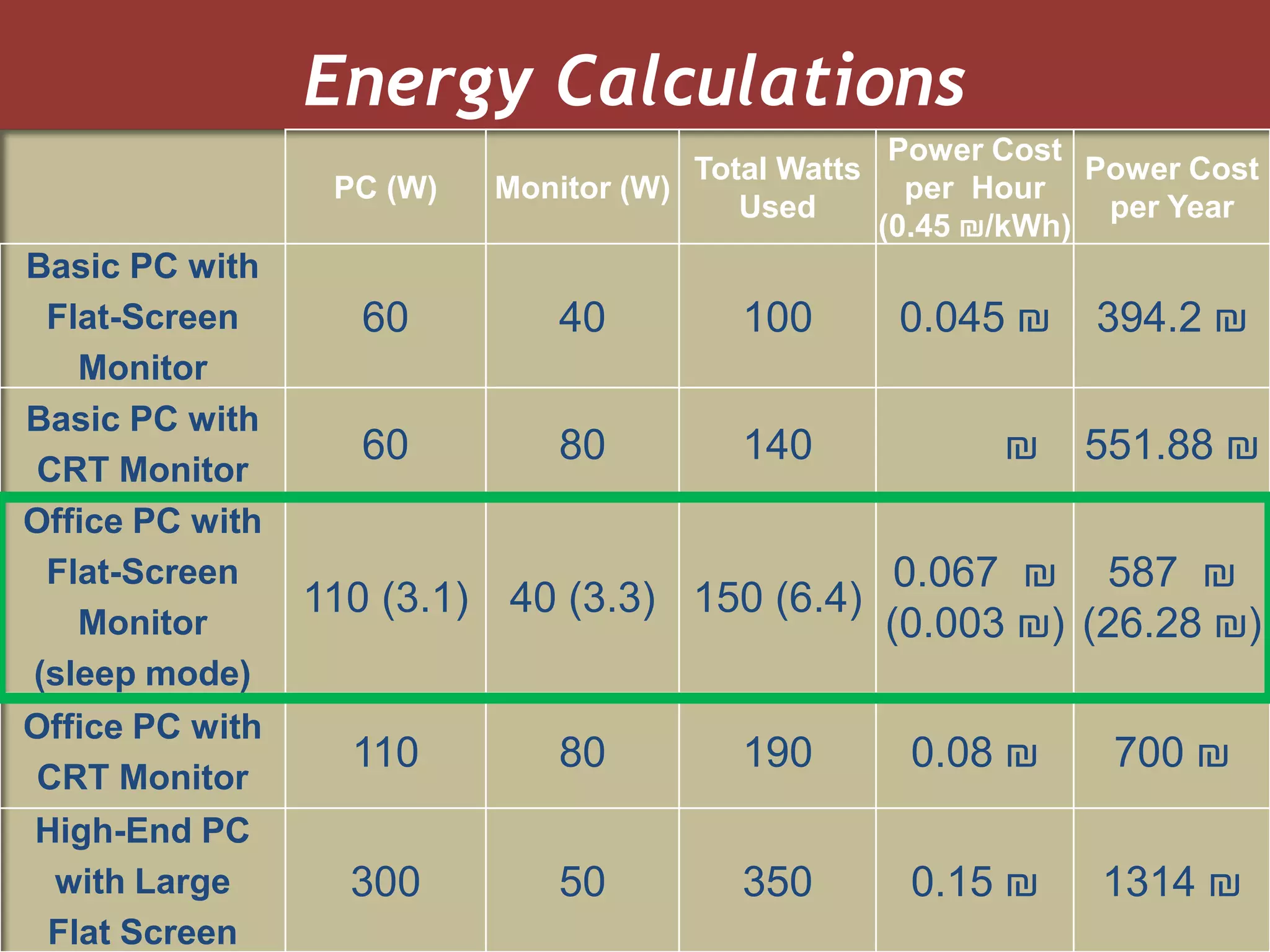
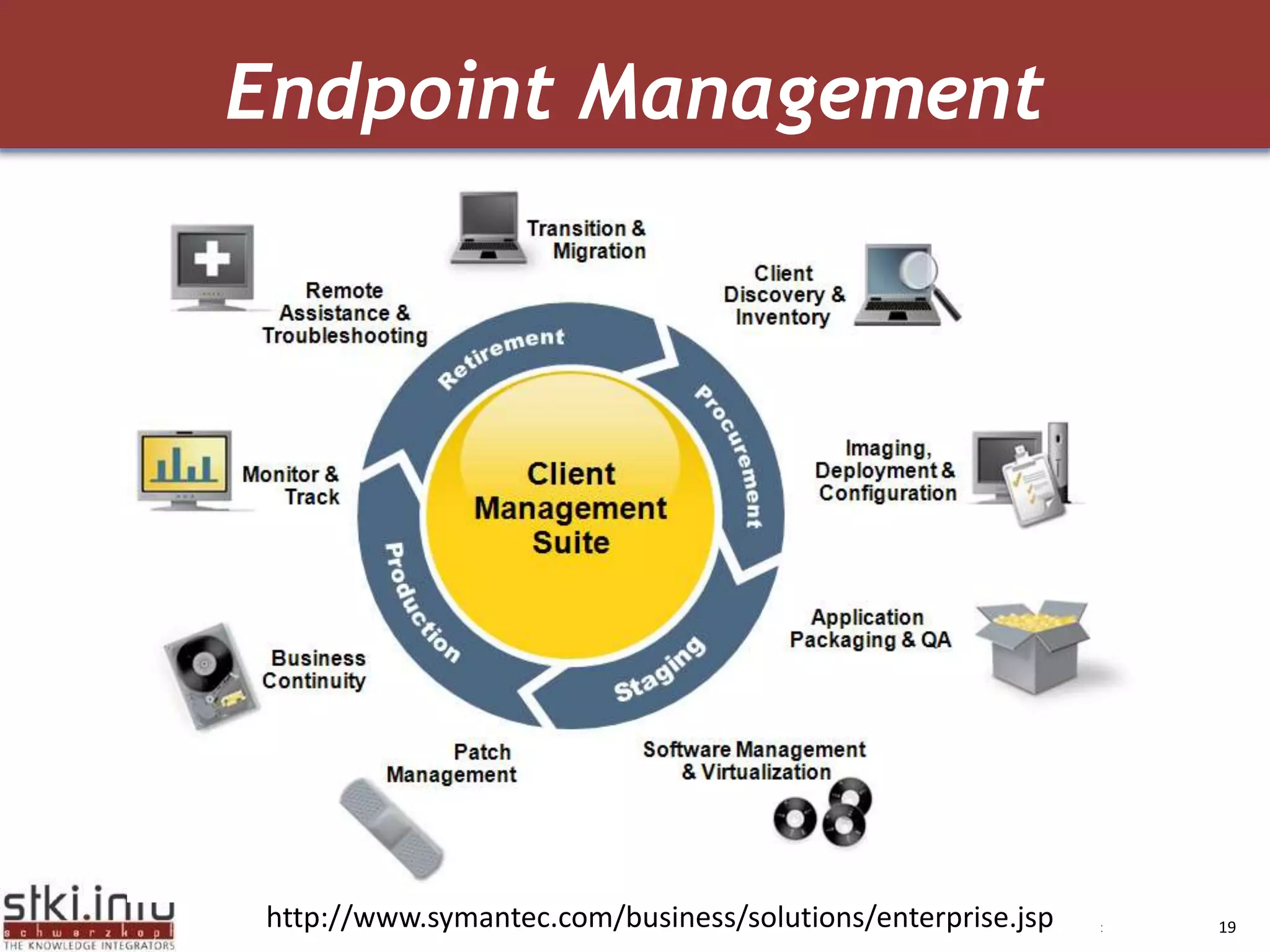
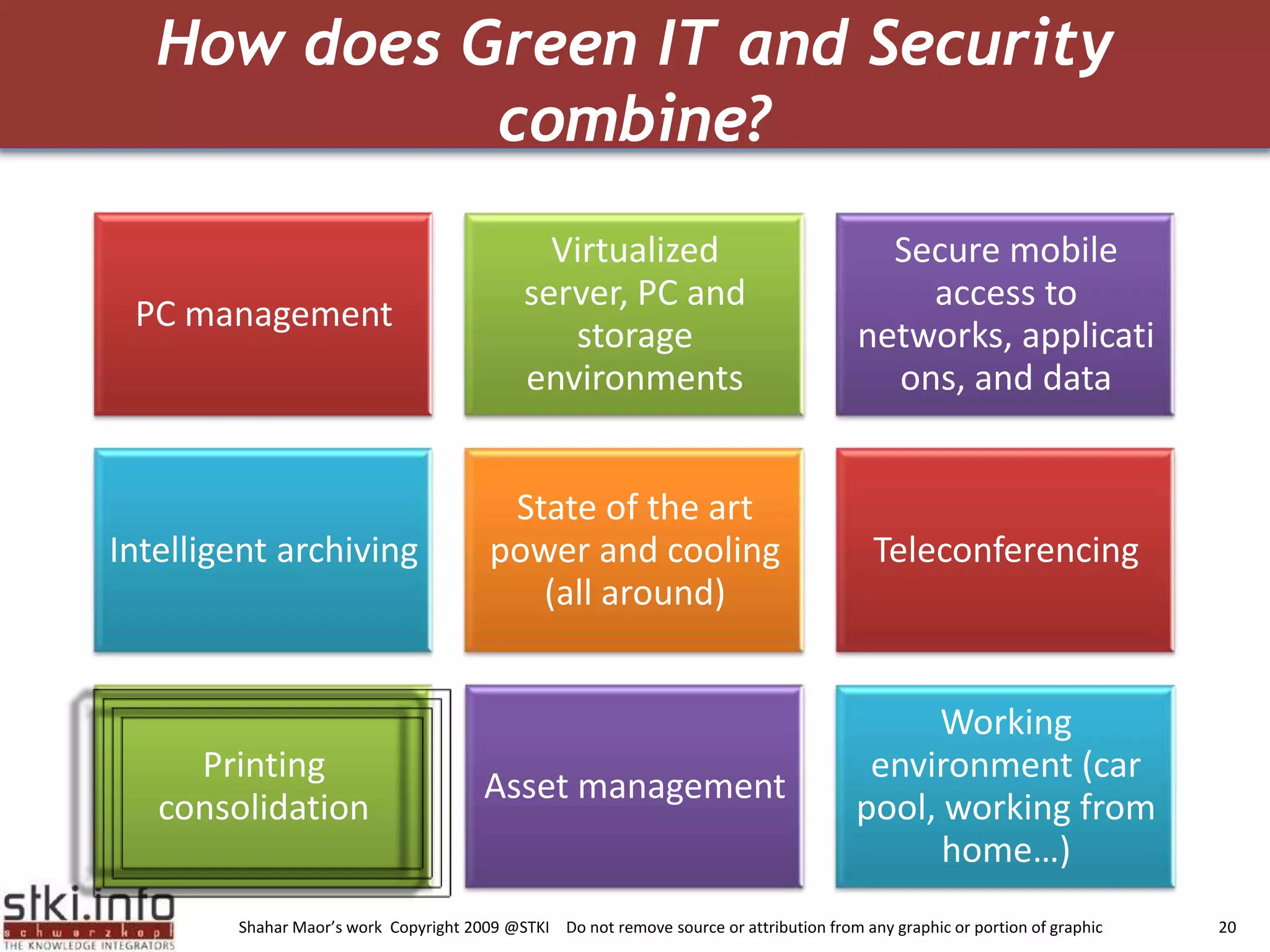
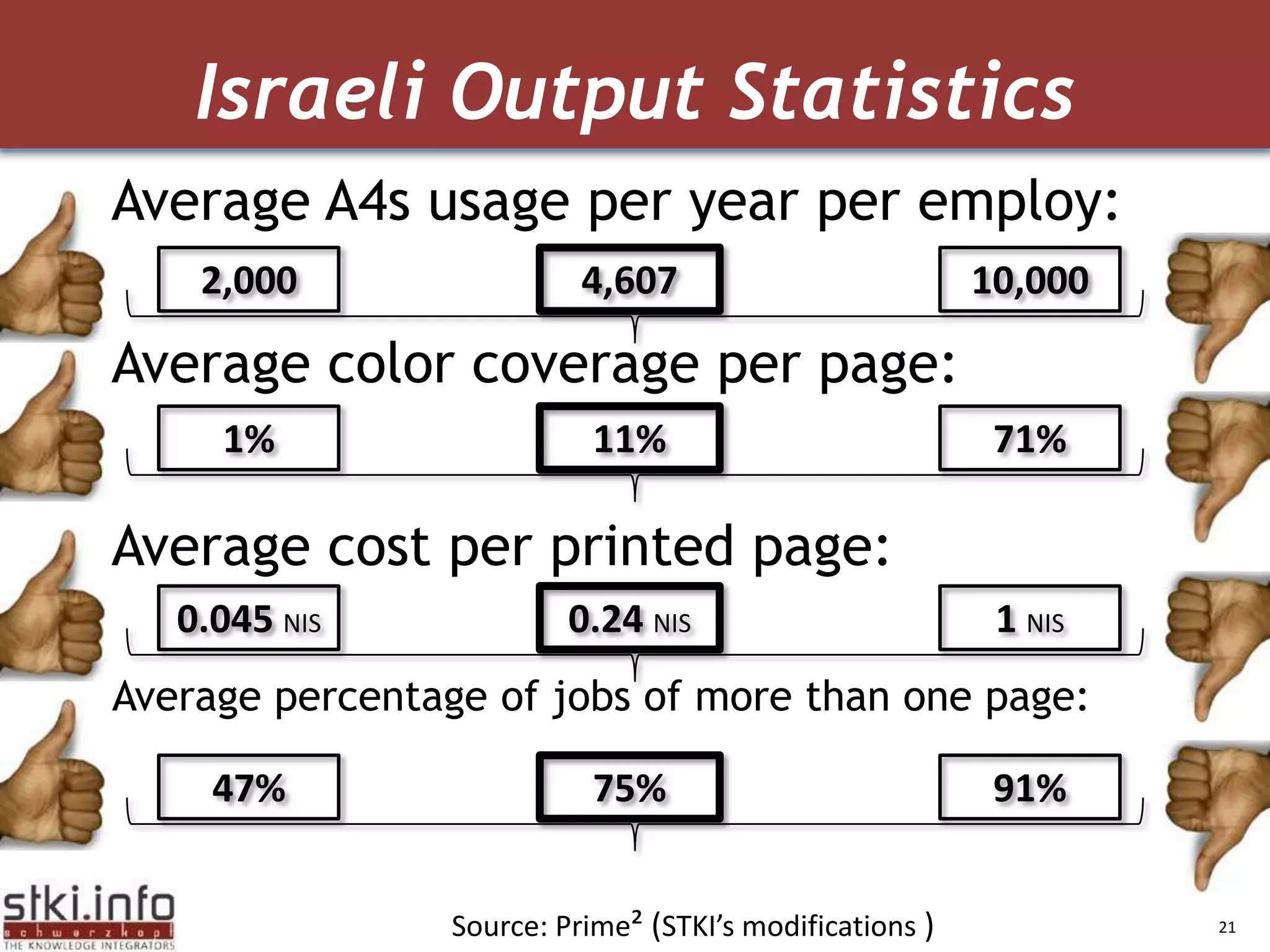

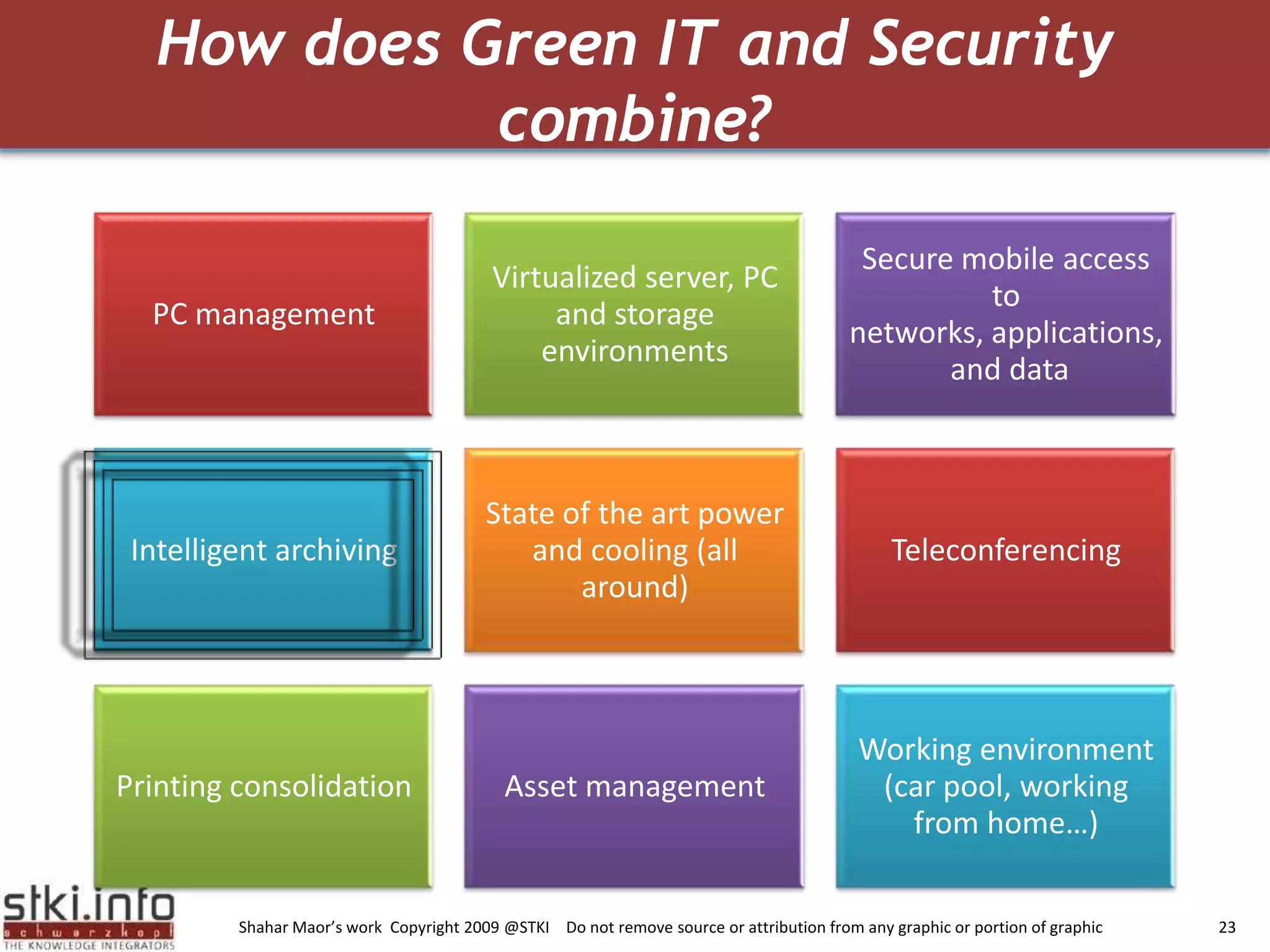
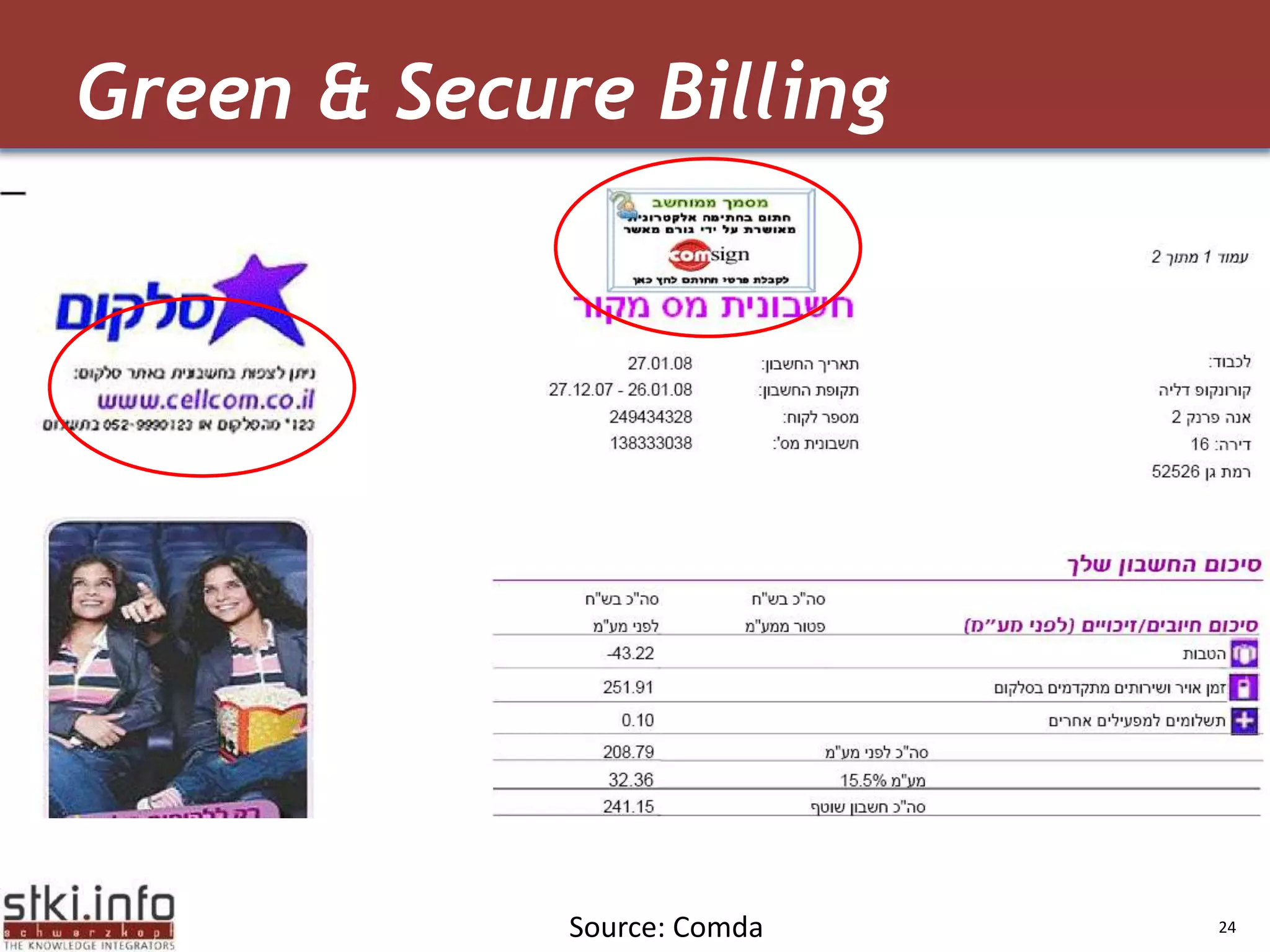
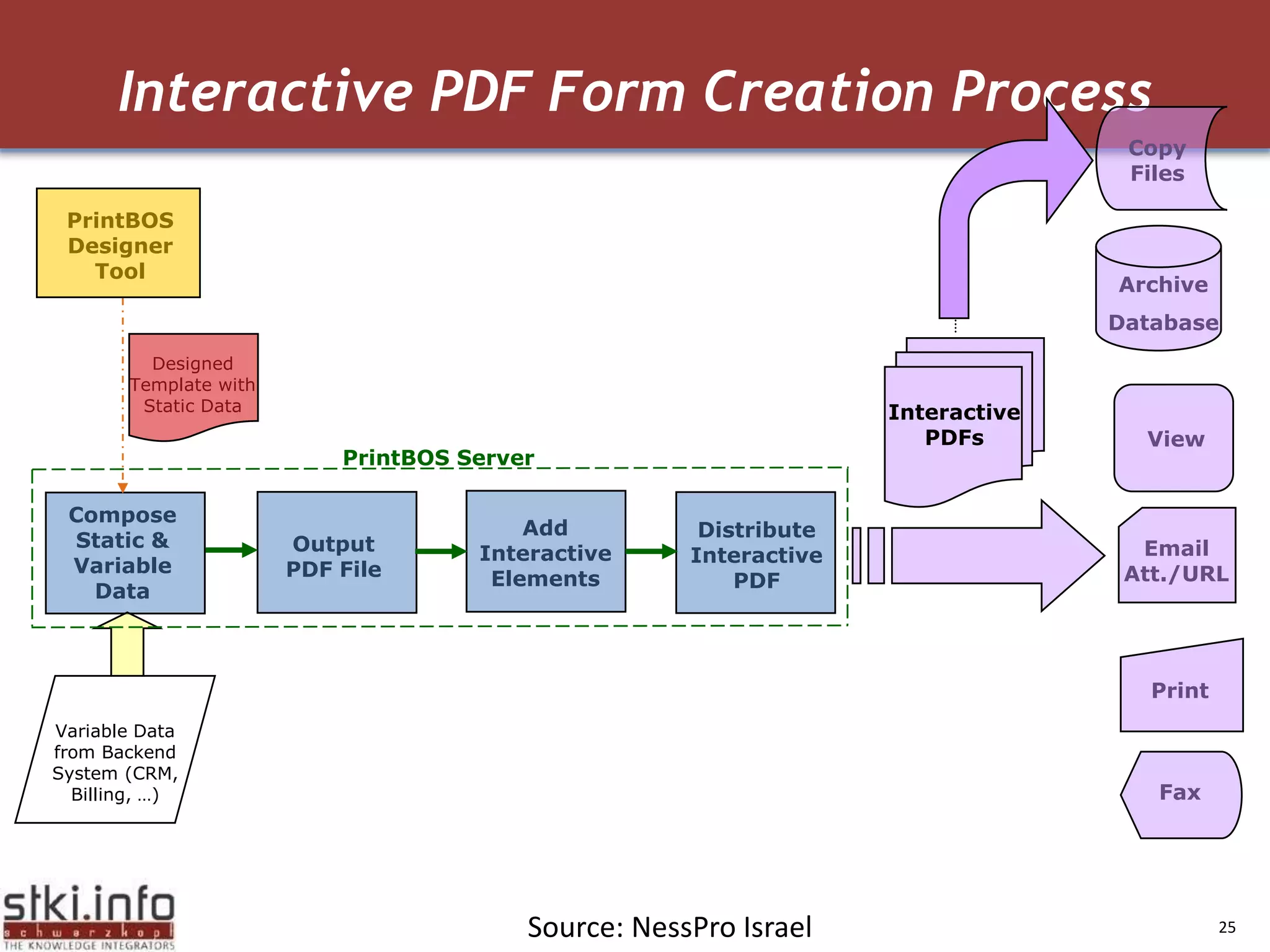
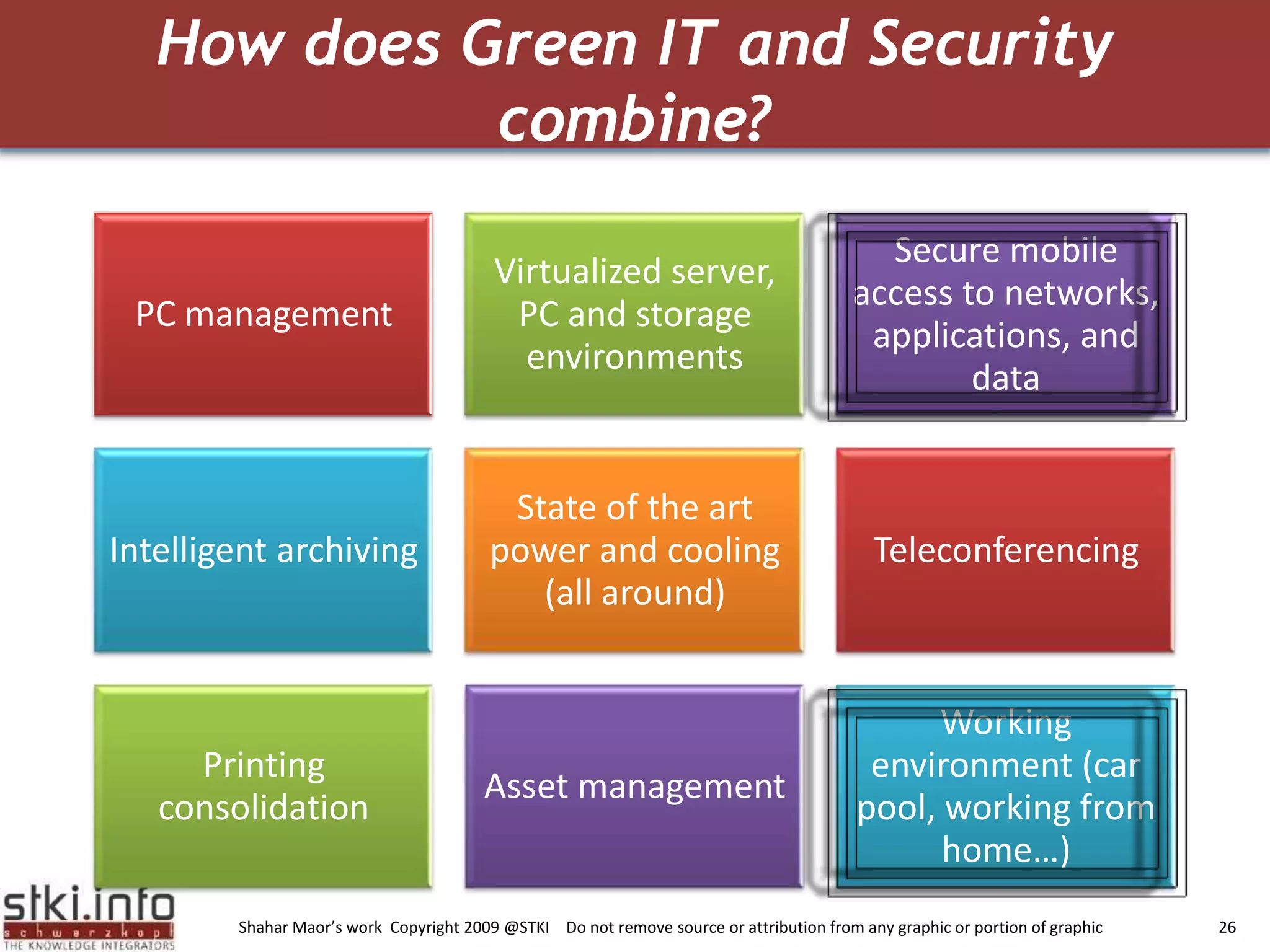

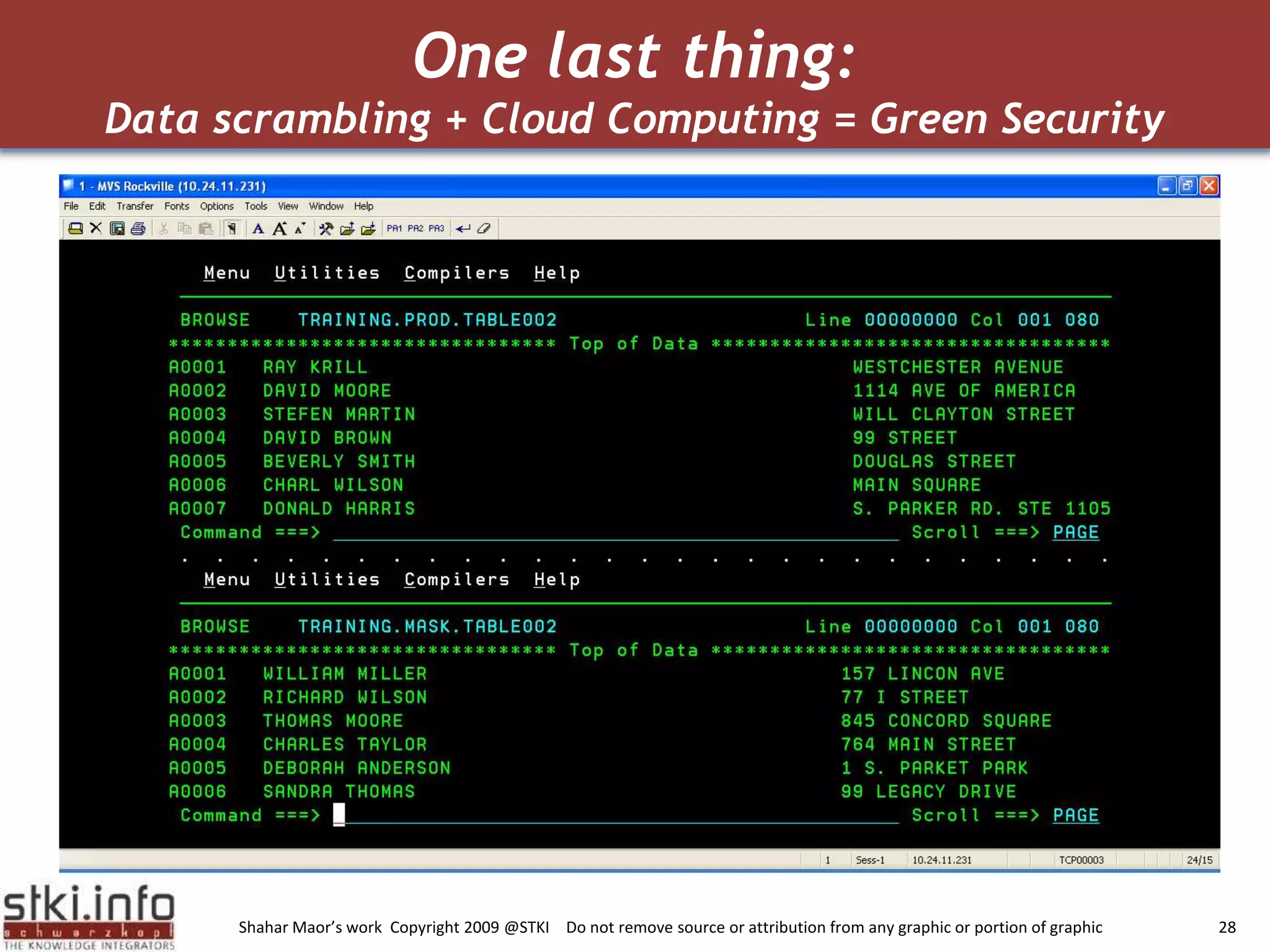


The document discusses how green IT and information security can be combined. It provides examples of how virtualizing servers and storage, implementing intelligent archiving, printing consolidation, and asset management can both reduce costs and energy usage while also improving security. Remote access via VPNs and data scrambling with cloud computing are presented as ways to achieve green security.




























