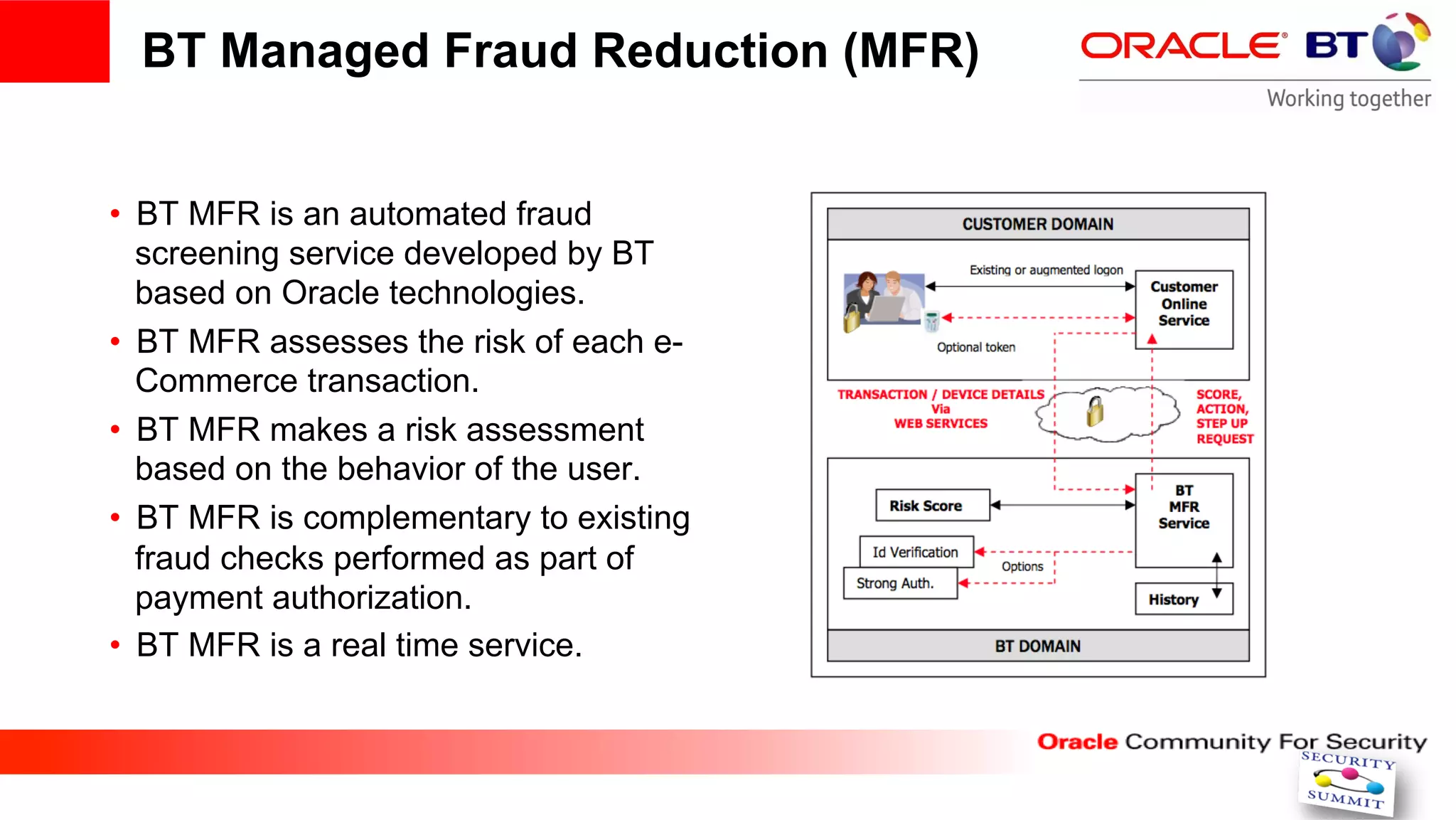
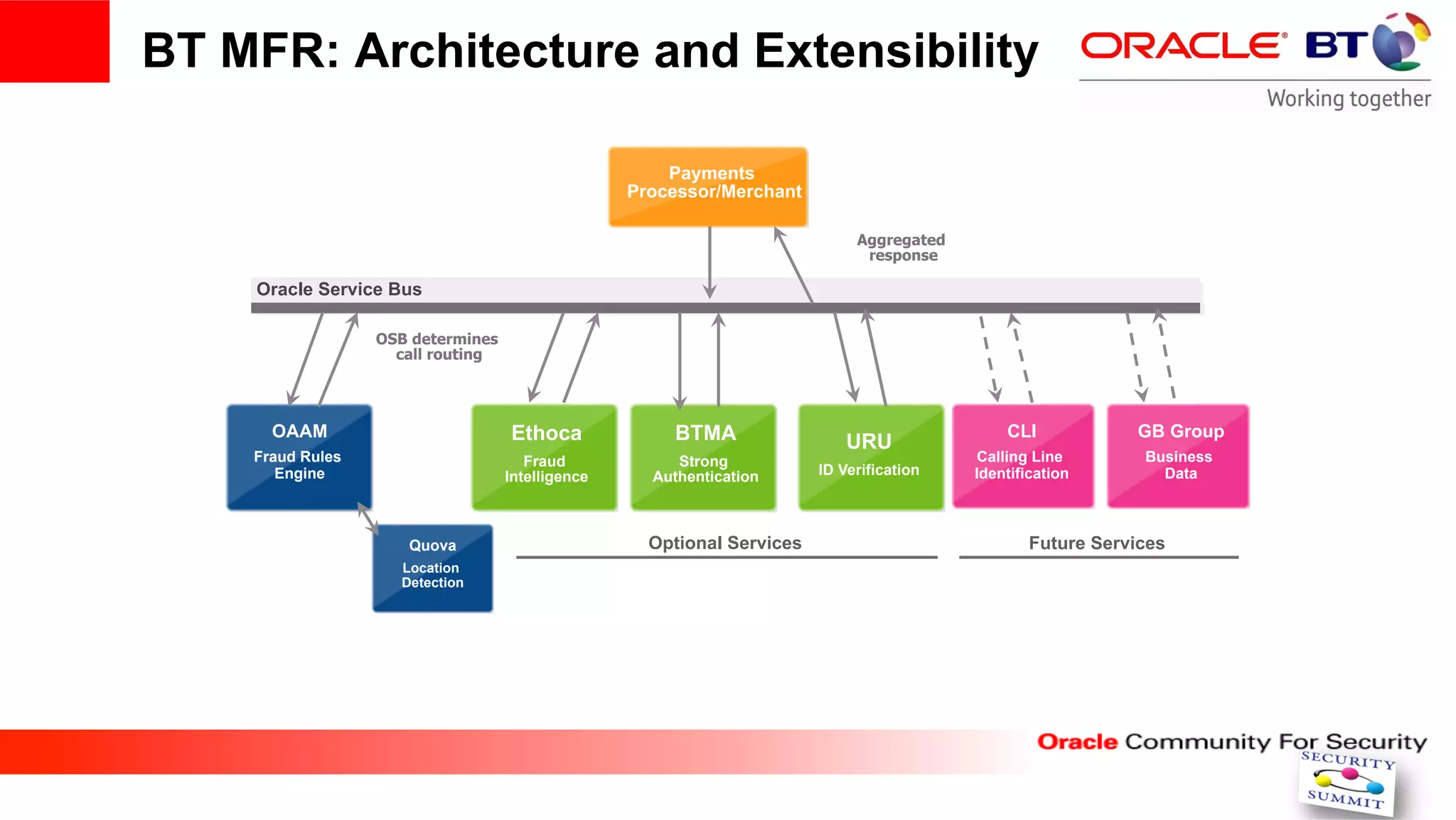
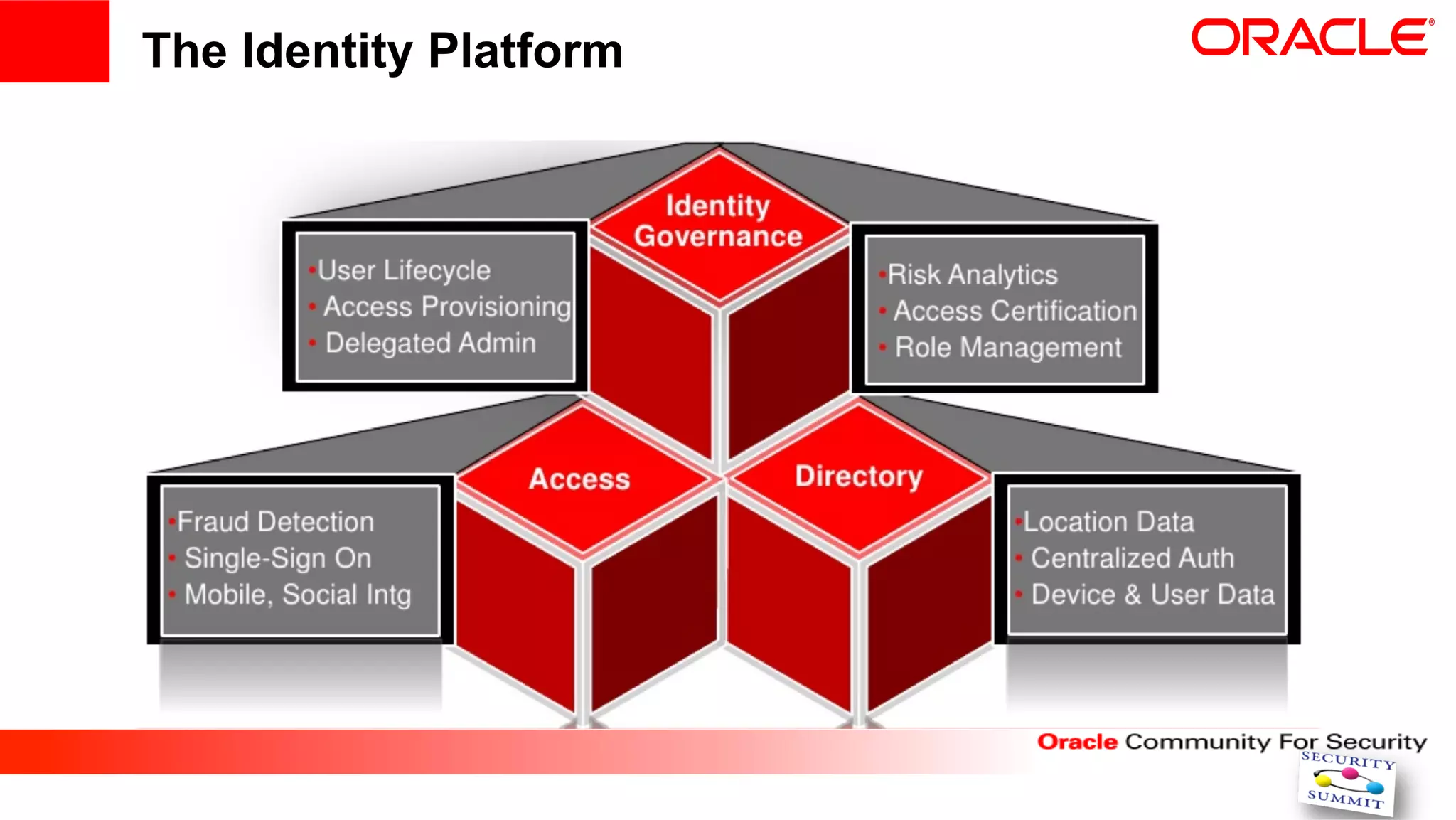
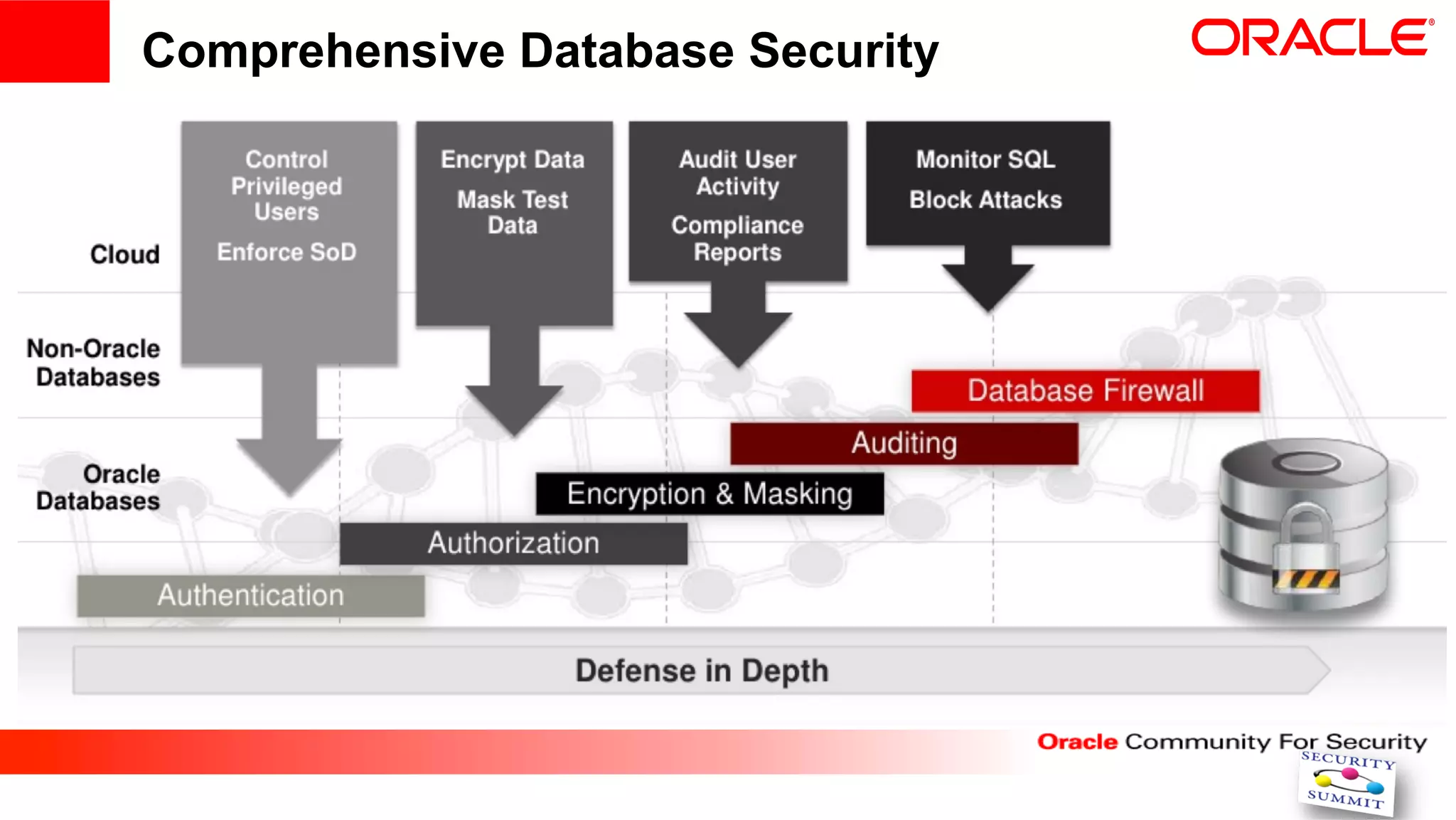
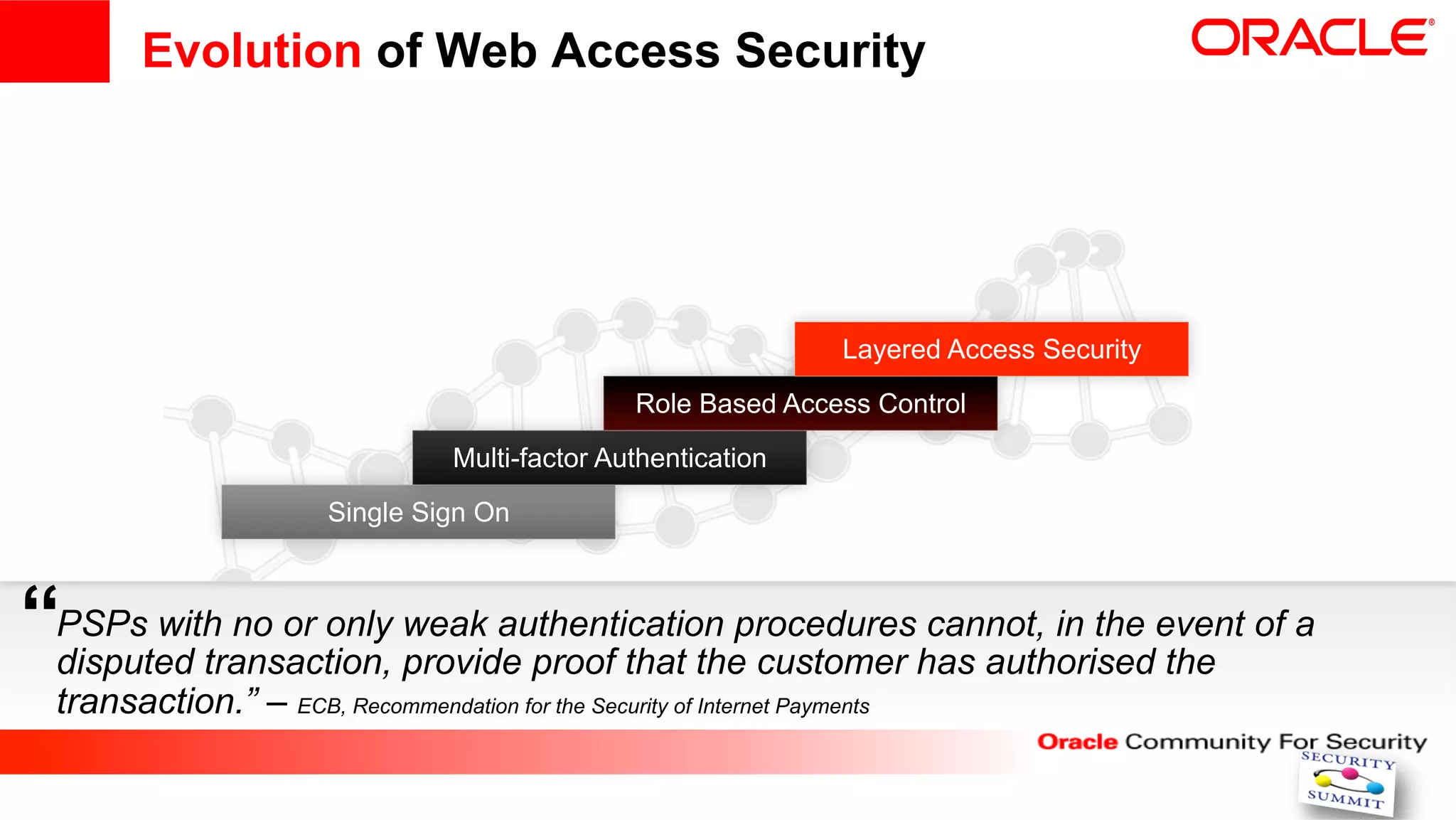
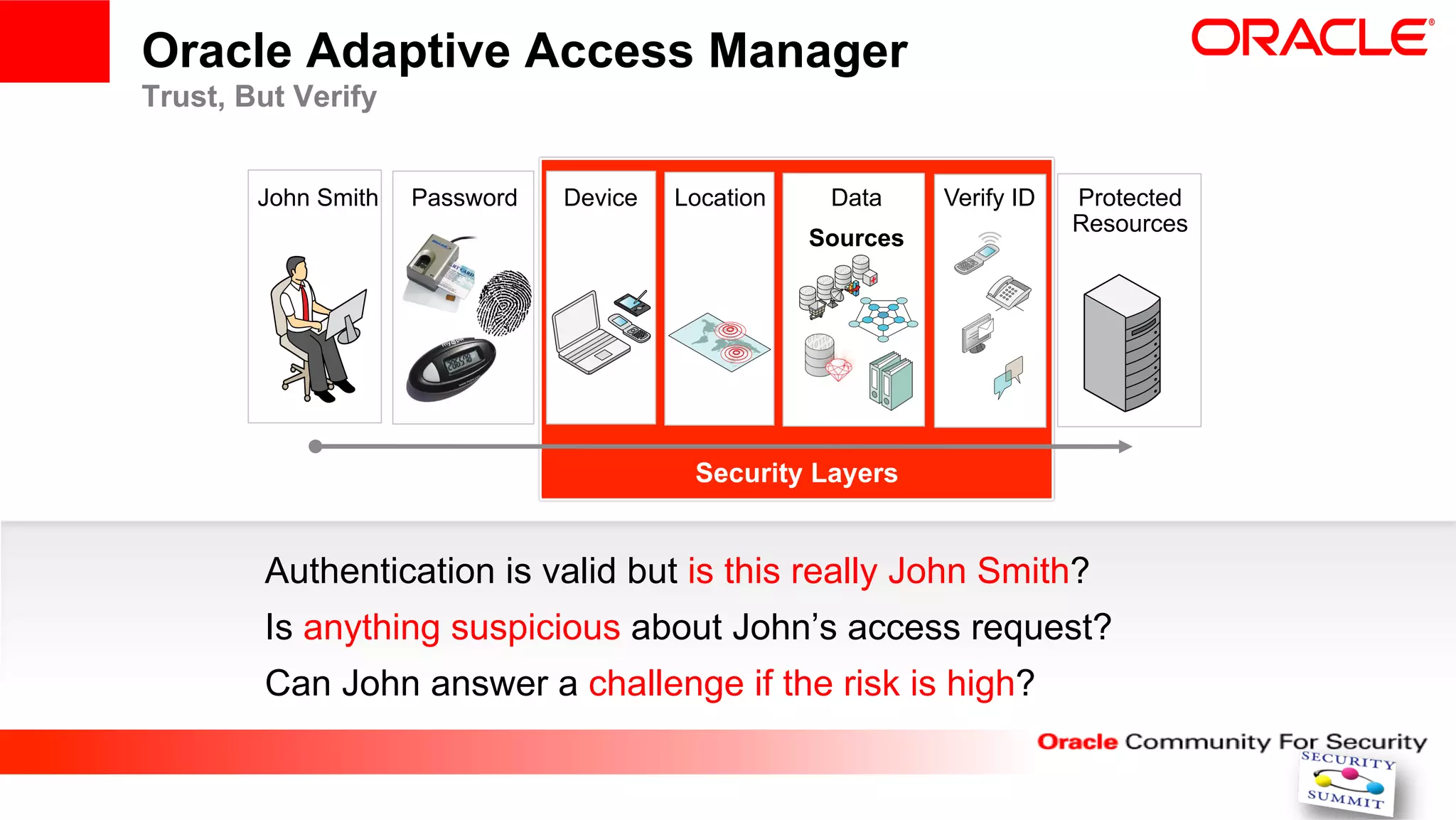
This document discusses securing internet payment systems. It begins with discussing trends in online payments and cybercrime threats to the financial sector. It then outlines security measures recommended by the ECB, including strong customer authentication and protection of sensitive payment data. The document discusses Oracle's approach to security, including layered access security and adaptive access management. It provides an example use case of BT's managed fraud reduction service which is based on Oracle technologies and provides real-time fraud screening.







![Data Relationships
First Class Entities Transaction Data Rule A
[ User, Device, IP, Etc. ] [ Dollar Amount ] [ If a purchase
HTTP [ Item Quantities ] originates from a
Address country not matching
[ Item Numbers ]
[ Street Number ] the country in the billing
SQL [ Coupon Code ] address then create an
[ Street Name ] [ Shipping Priority ] alert. ]
[ Apt. Number ]
Files Entity Instances
[ City ]
[ State ] Rule B
JMS [ Shipping Address ]
[ ZIP Code ] [ If an item has been
Credit Card
[ Country ] purchased more than
[ First Name ] twice in the last week
WS
[ Last Name ] [ Billing Address ] from a single device,
[ Middle Initial ] each using a different
credit card then create
[ Number ] an alert. ]
[ Security Code ] [ Credit Card ]
[ Expiration ]](https://image.slidesharecdn.com/oracle-securepayment-catalanov3-120607063659-phpapp02/75/Securing-Internet-Payment-Systems-19-2048.jpg)