Embed presentation
Download as PDF, PPTX





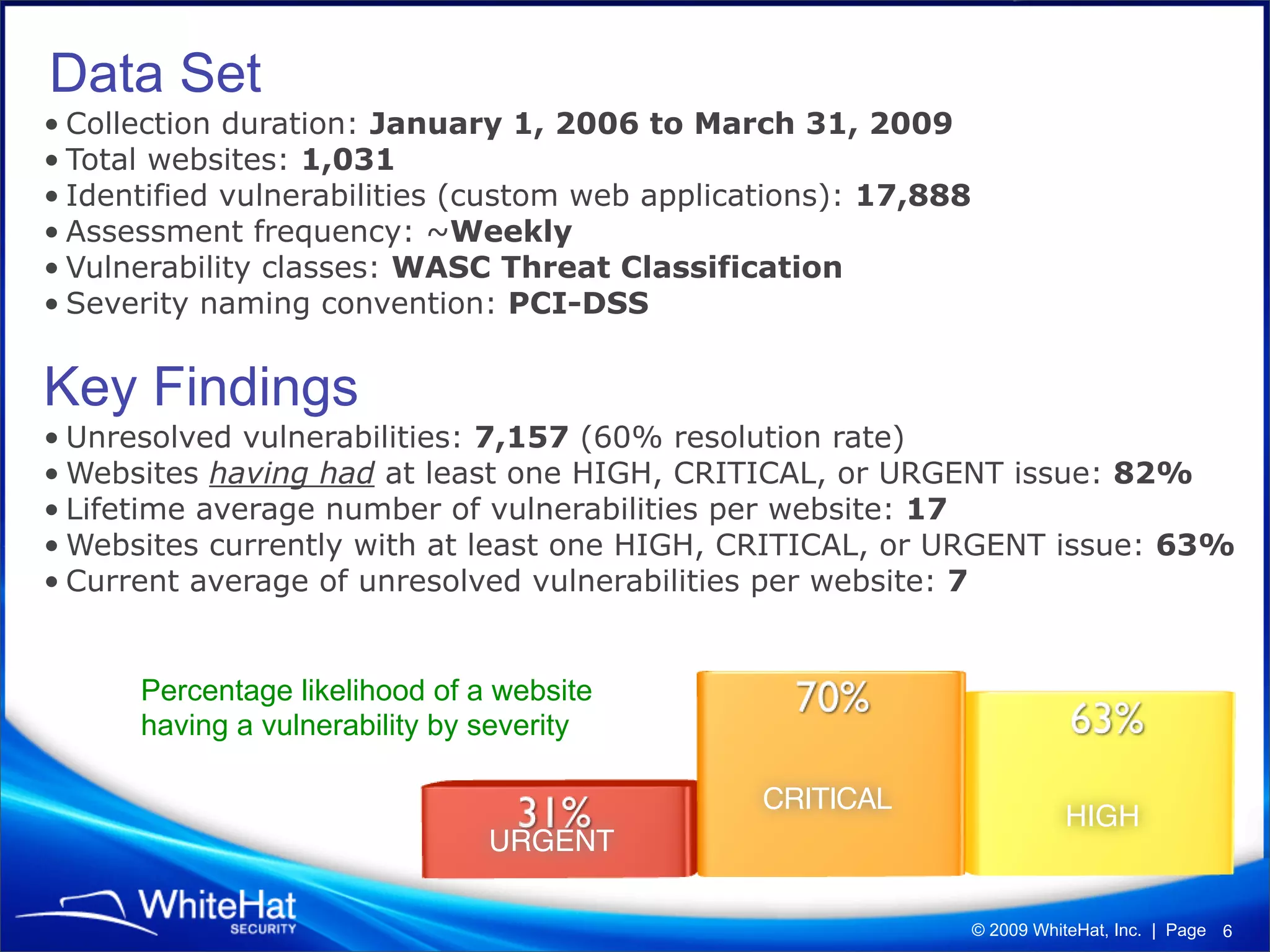
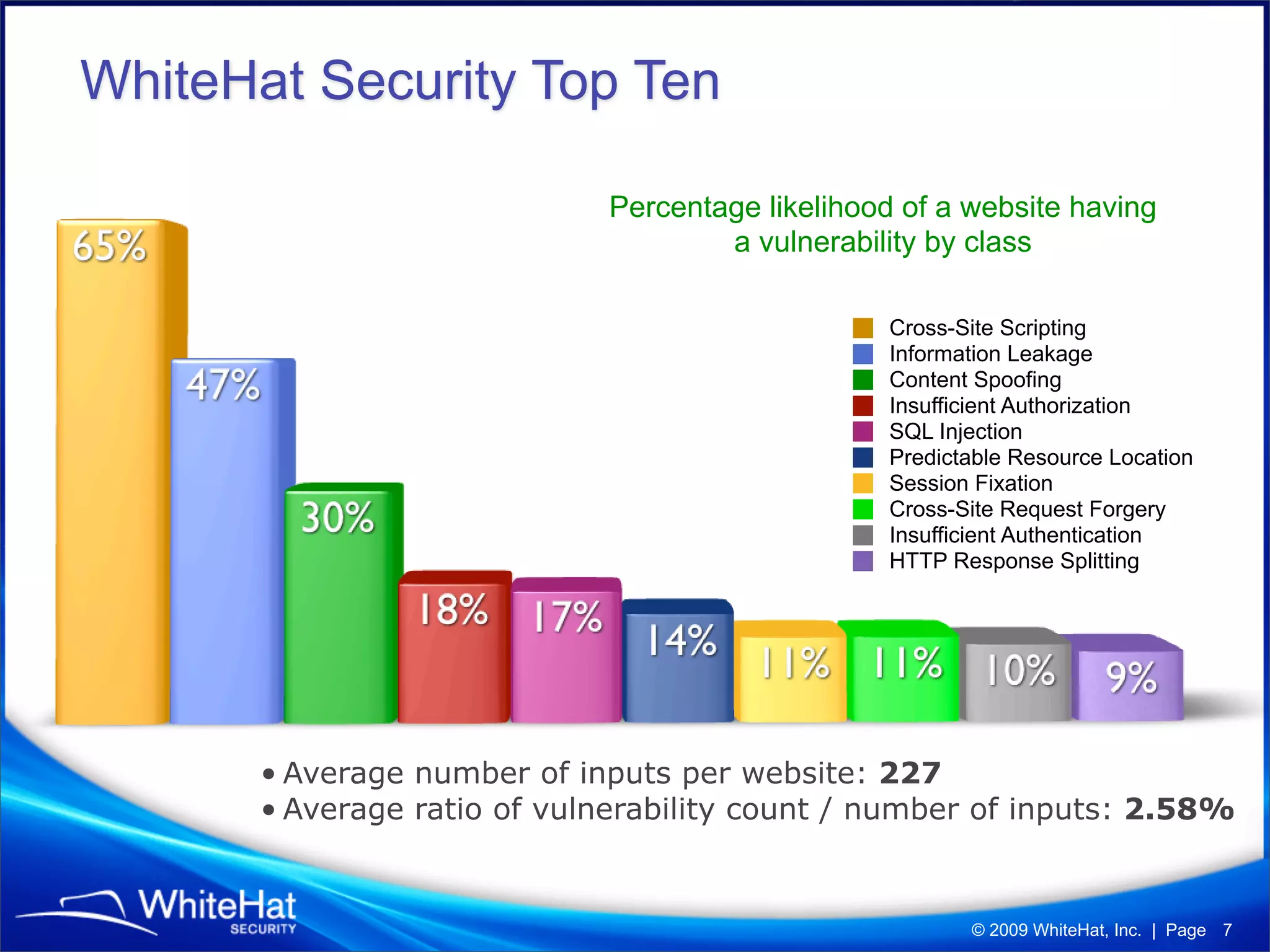
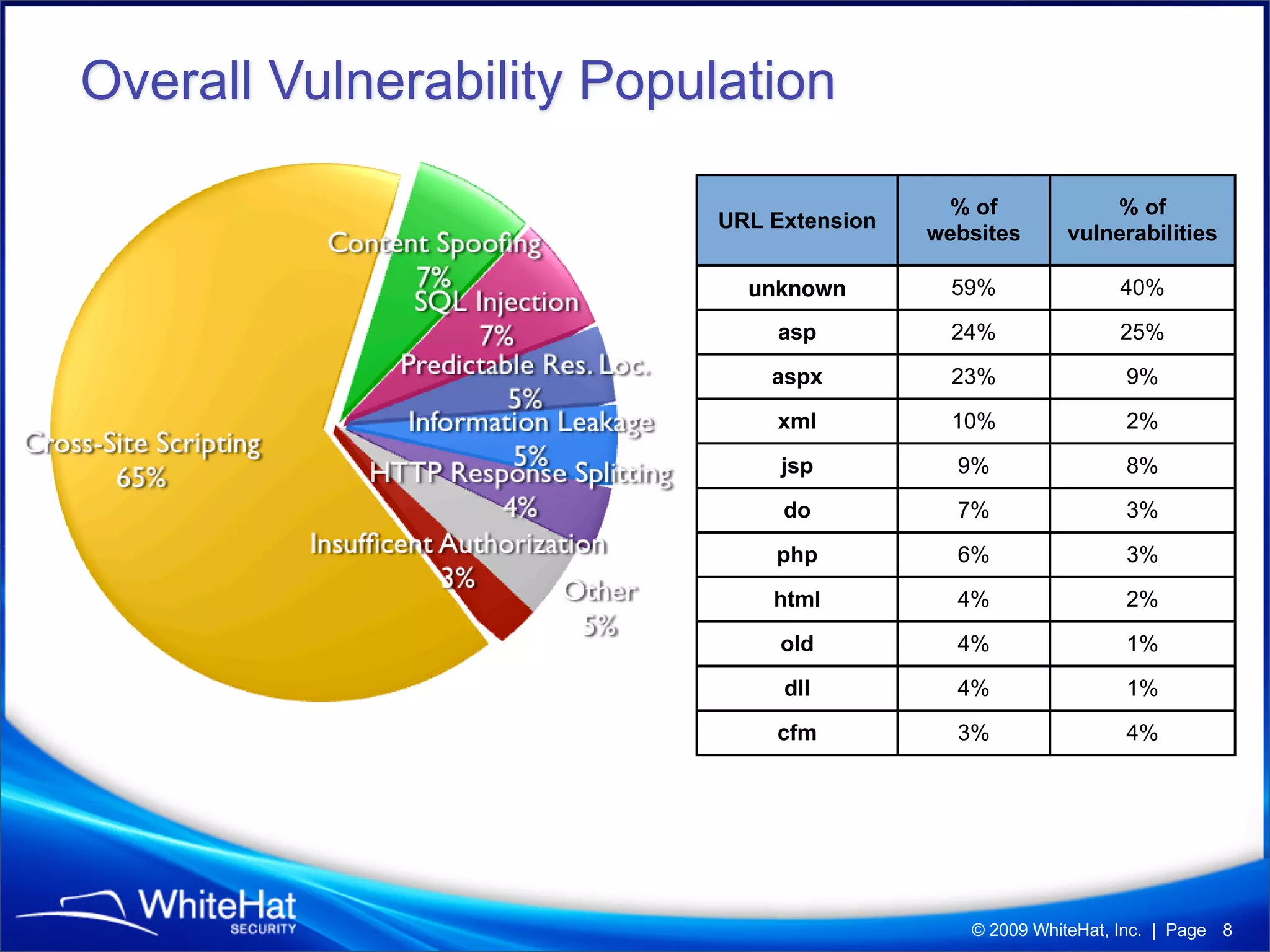
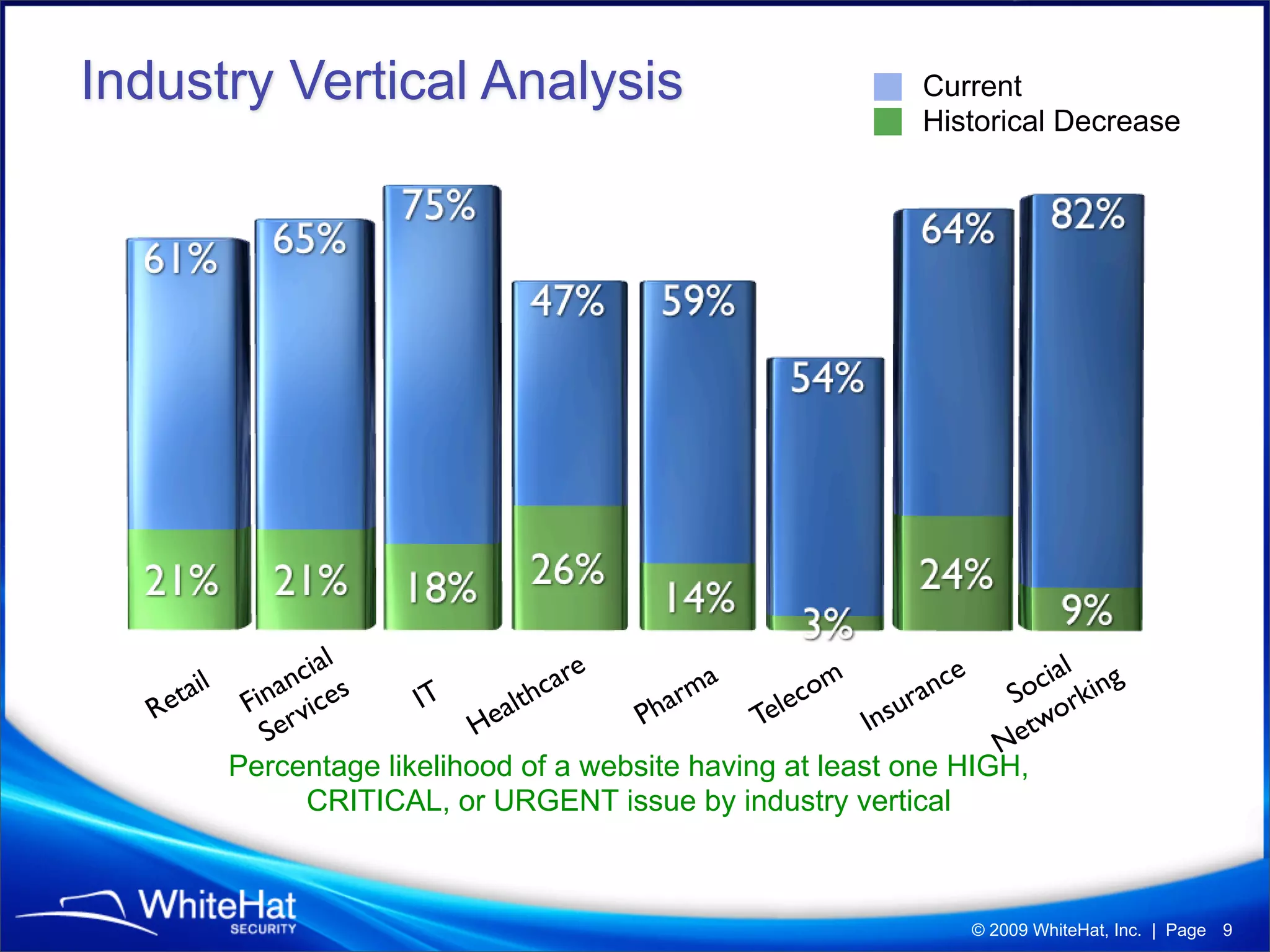
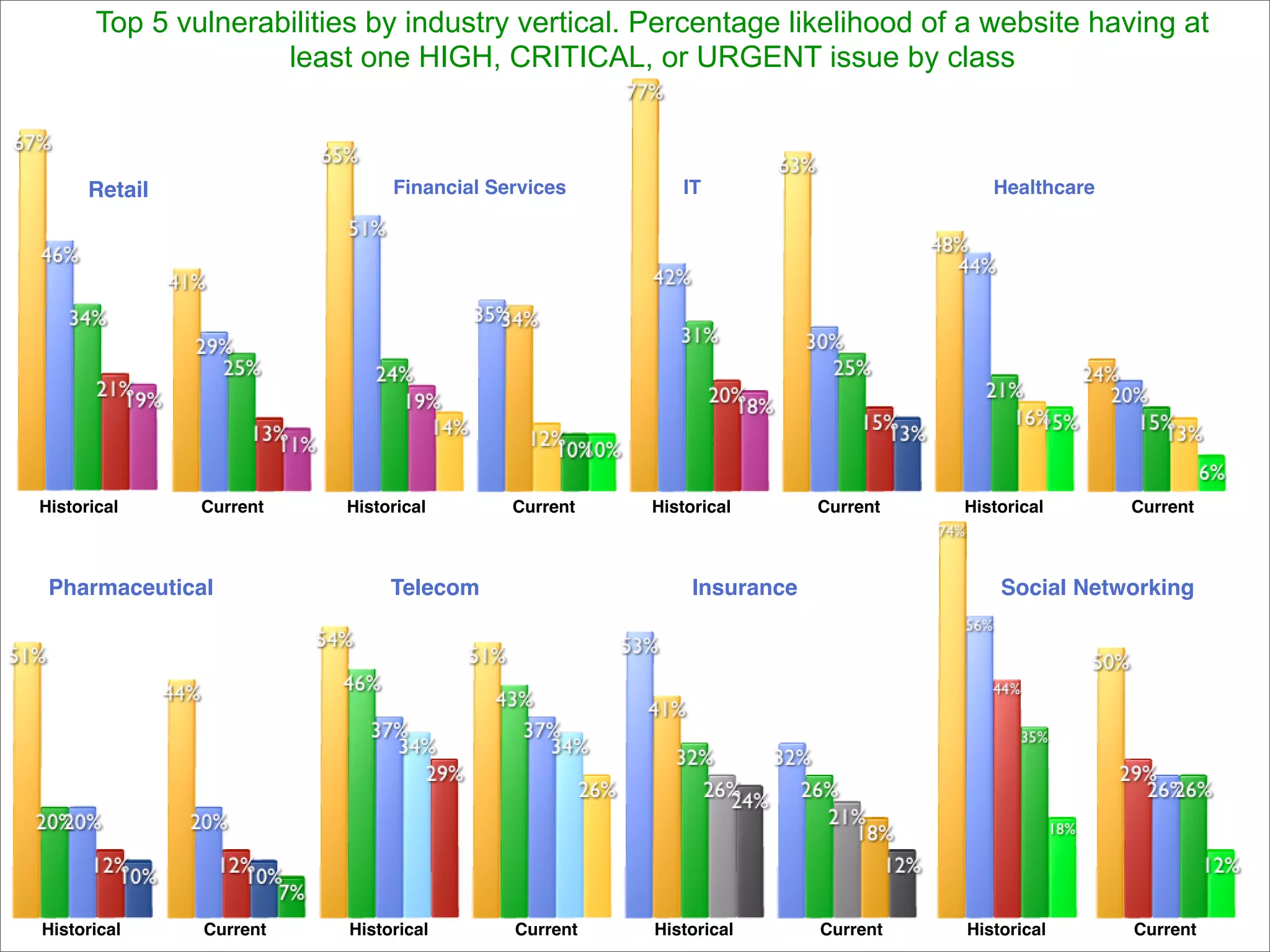
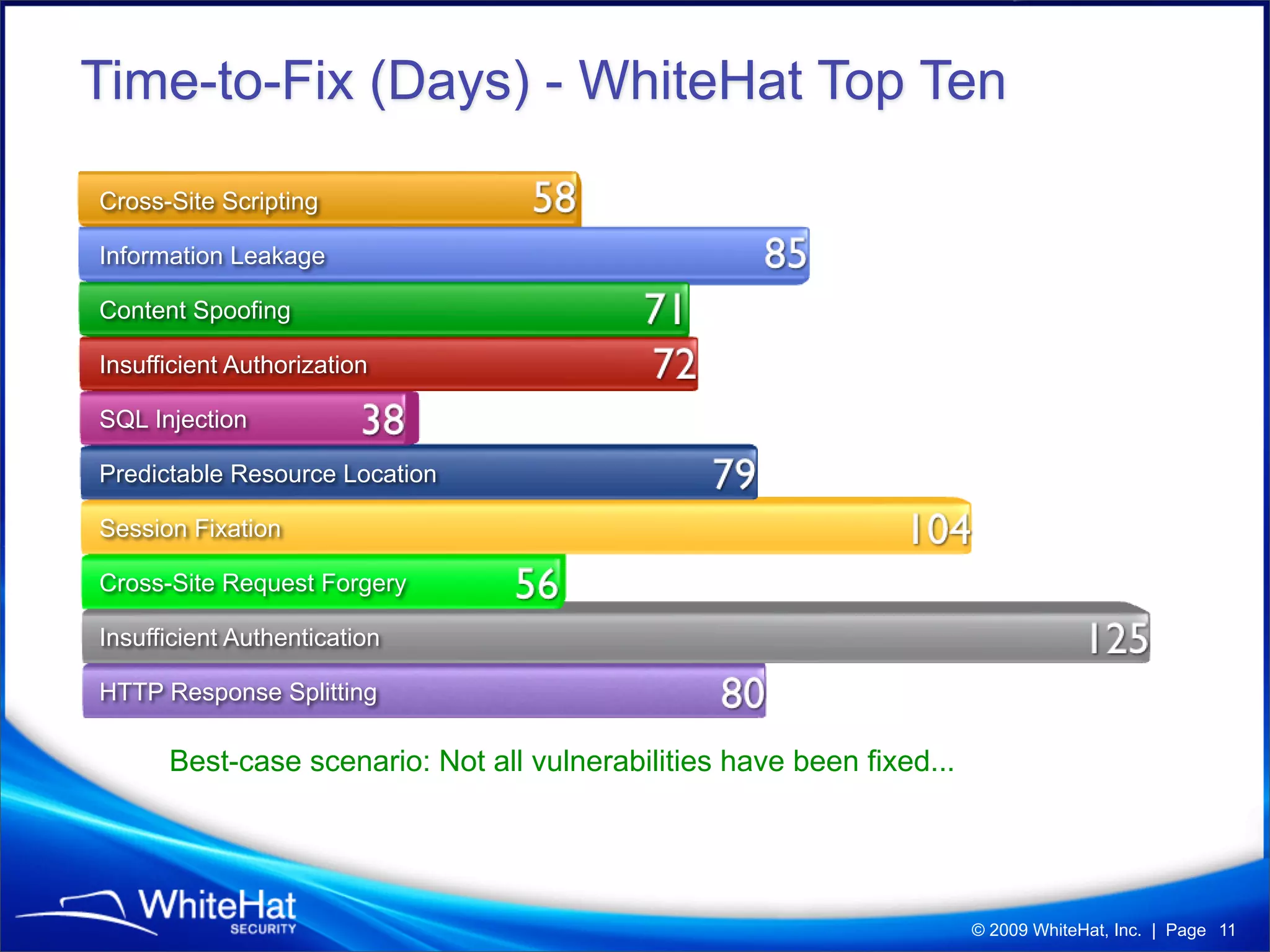
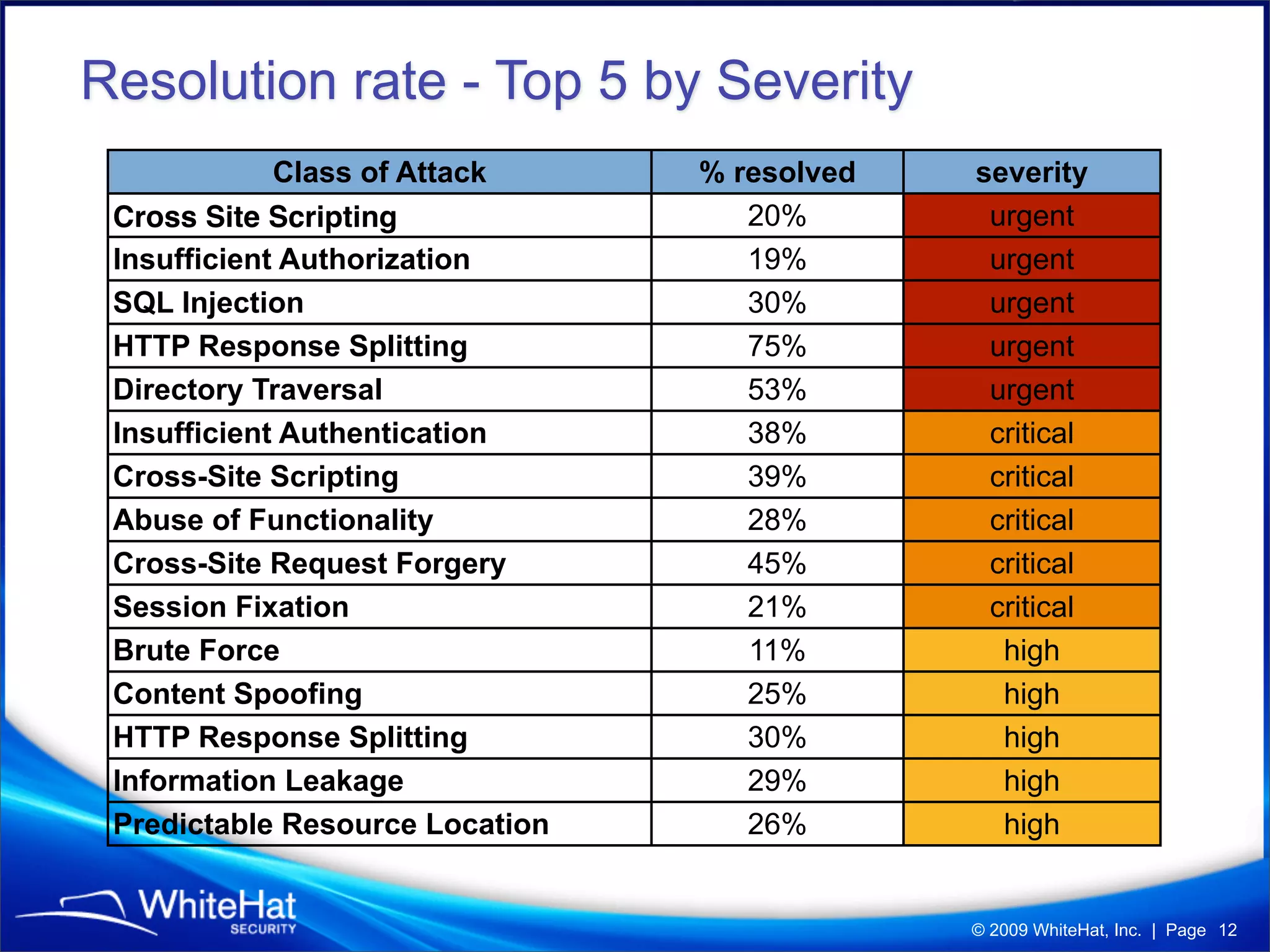
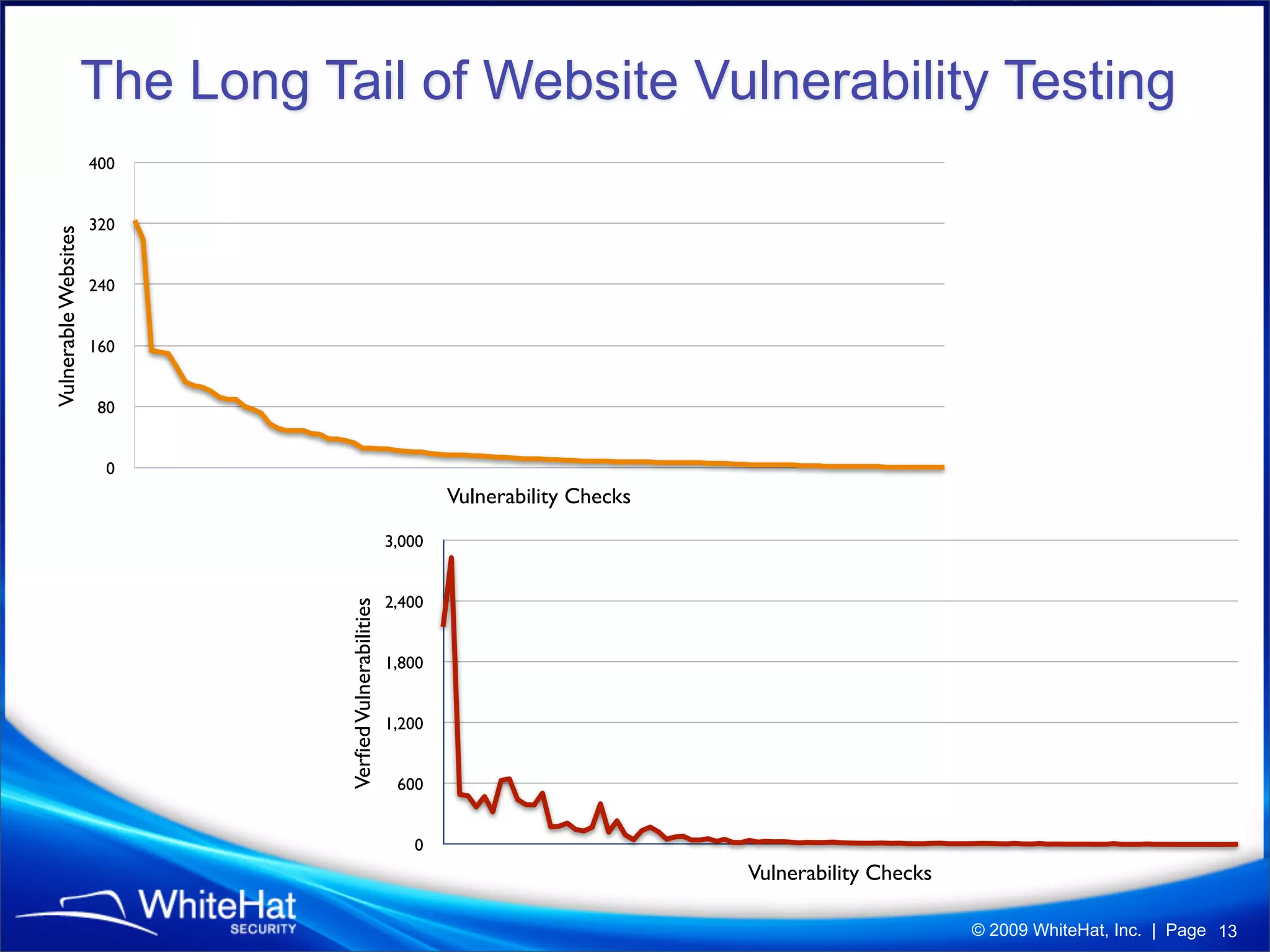



The 7th website security statistics report highlights that 82% of websites have experienced security issues, with 63% still vulnerable to high, critical, or urgent threats. It emphasizes the necessity for web application security compliance, particularly under PCI DSS regulations, as well as the increasing number of malicious website breaches. WhiteHat Security's services provide comprehensive vulnerability assessments for various levels of risk across a large number of enterprise customers.
















