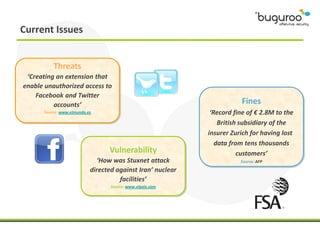
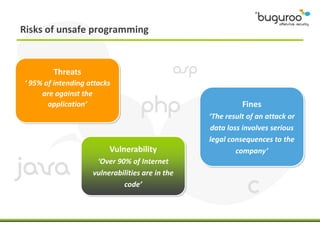
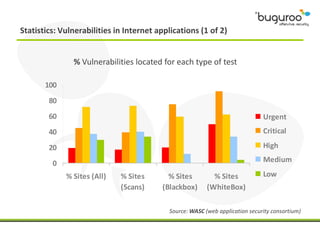
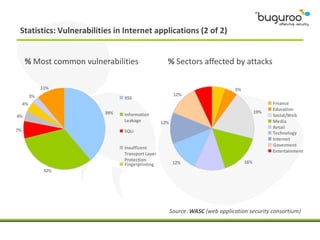
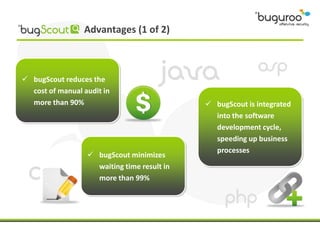
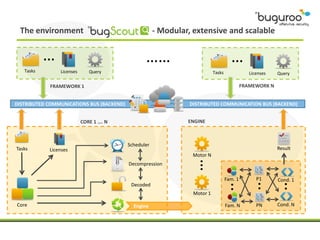
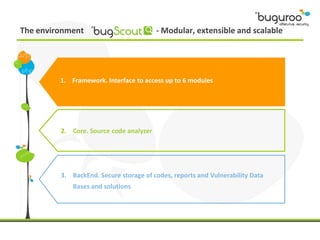
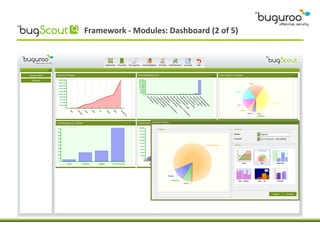
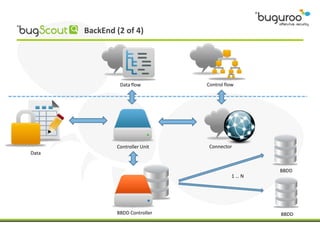
The document discusses the current issues in information security, particularly the threats posed by unauthorized access to social media accounts and the consequences of data loss. It introduces Buguroo's Bugscout, a managed service designed to analyze vulnerabilities in source code, boasting automatic detection of over 94% of vulnerabilities and the ability to operate in decentralized cloud environments. Bugscout integrates with software development cycles, minimizes manual audit costs, and enables real-time correction of errors, while addressing limitations of traditional auditing methods.