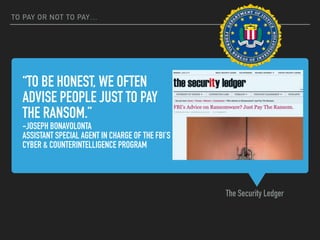
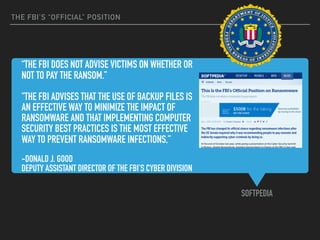
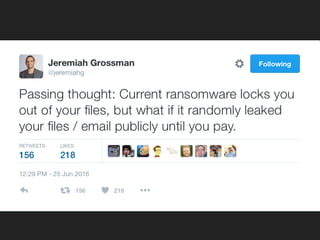
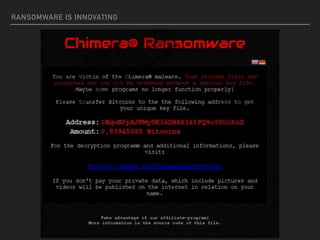
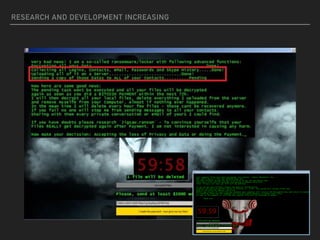
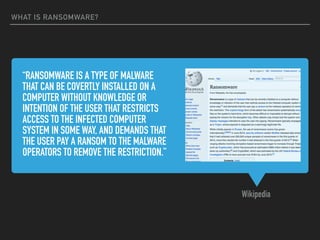
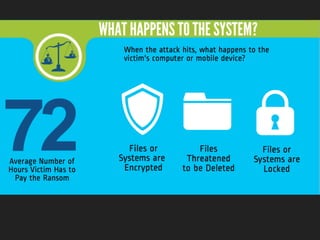
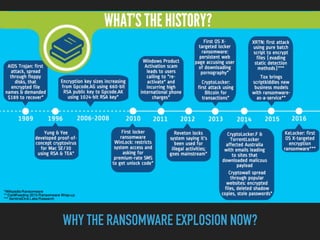
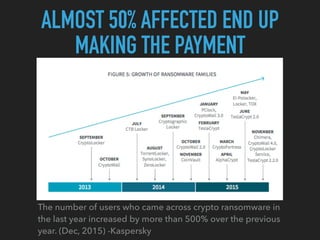
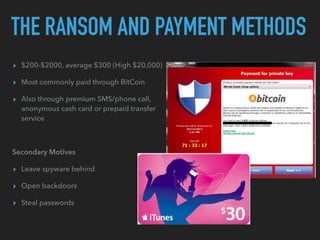
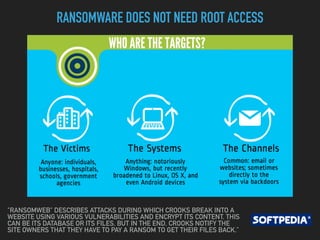
Ransomware is a malicious software that restricts access to computer systems and demands payment for restoration. The ransomware industry has exploded, with a significant increase in victims and reports, costing millions of dollars, and employing various methods to propagate and execute attacks. Payment methods commonly include Bitcoin, with many organizations facing severe disruptions due to ransomware attacks, highlighting the growing sophistication and complexity of these cyber threats.








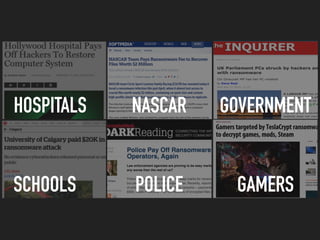
![“ON WEDNESDAY, U.S. SECURITY COMPANY KNOWBE4 SAID IT WAS RECENTLY
CONTACTED BY A HEALTH CENTER THAT PAID HACKERS NEARLY $40,000 AFTER 250
DEVICES, INCLUDING AN MRI MACHINE, BECAME INFECTED WITH RANSOMWARE,
PROMPTING THE UNNAMED ORGANIZATION TO SHUT DOWN FOR FIVE DAYS.”
“[PRIME HEALTHCARE SERVICE] SAYS IT DEFEATED THE CYBERATTACK WITHOUT
PAYING A RANSOM. BUT IT ACKNOWLEDGED SOME PATIENTS WERE TEMPORARILY
PREVENTED FROM RECEIVING RADIOLOGY TREATMENTS, AND OTHER OPERATIONS
WERE DISRUPTED BRIEFLY WHILE COMPUTER SYSTEMS WERE DOWN.”
“IN MARCH, HACKERS ENCRYPTED DATA AT MEDSTAR HEALTH, WHICH OPERATES 10
HOSPITALS IN MARYLAND AND THE DISTRICT OF COLUMBIA. THE VIRUS CAUSED
DELAYS IN SERVICE AND TREATMENT UNTIL COMPUTERS WERE BROUGHT BACK
ONLINE. THE COMPANY SAID IT DID NOT PAY A REPORTED $19,000 RANSOM DEMAND.“](https://image.slidesharecdn.com/sentinelonewebinar06-160629124721/85/Ransomware-is-Here-Fundamentals-Everyone-Needs-to-Know-16-320.jpg)