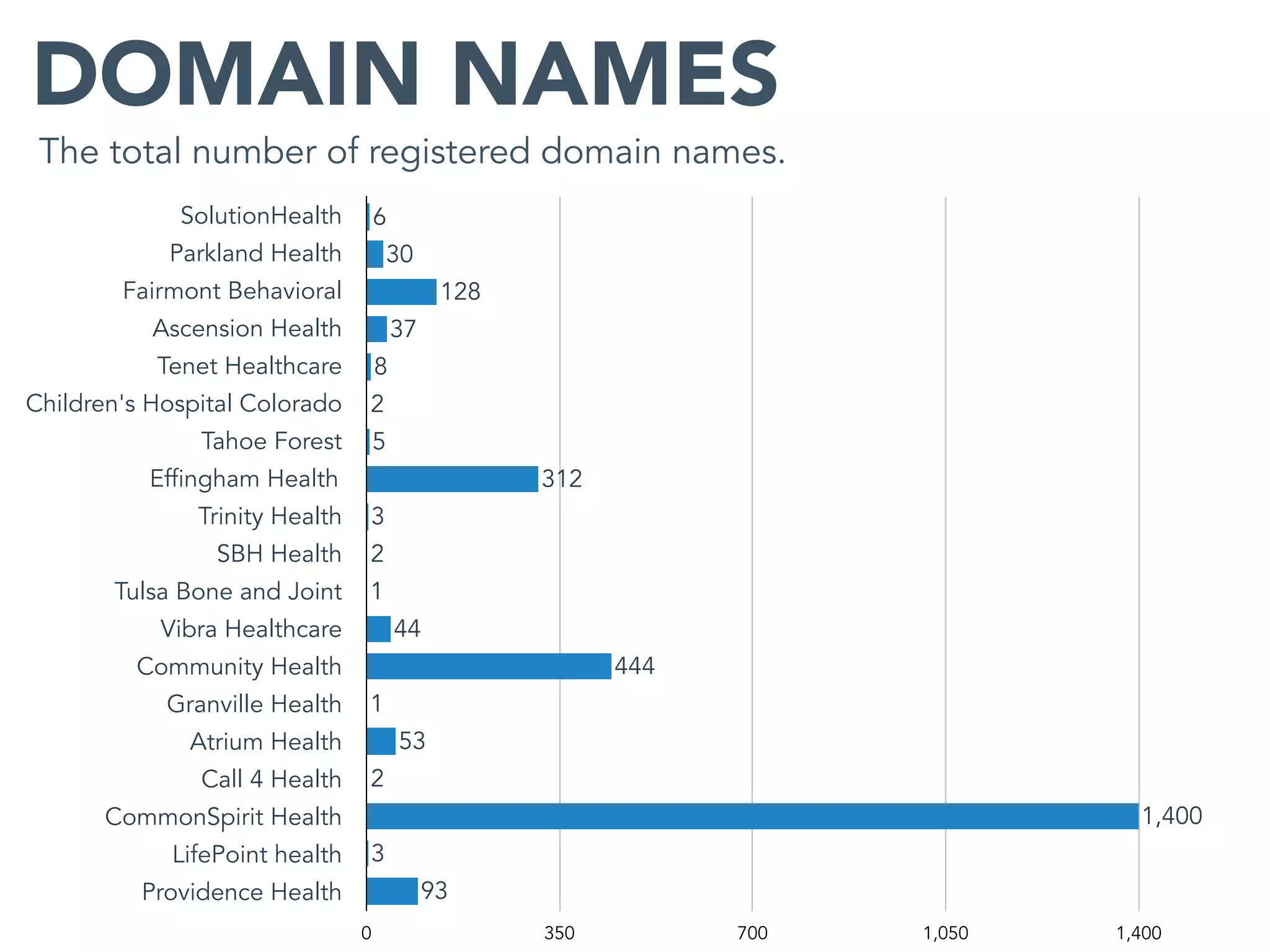
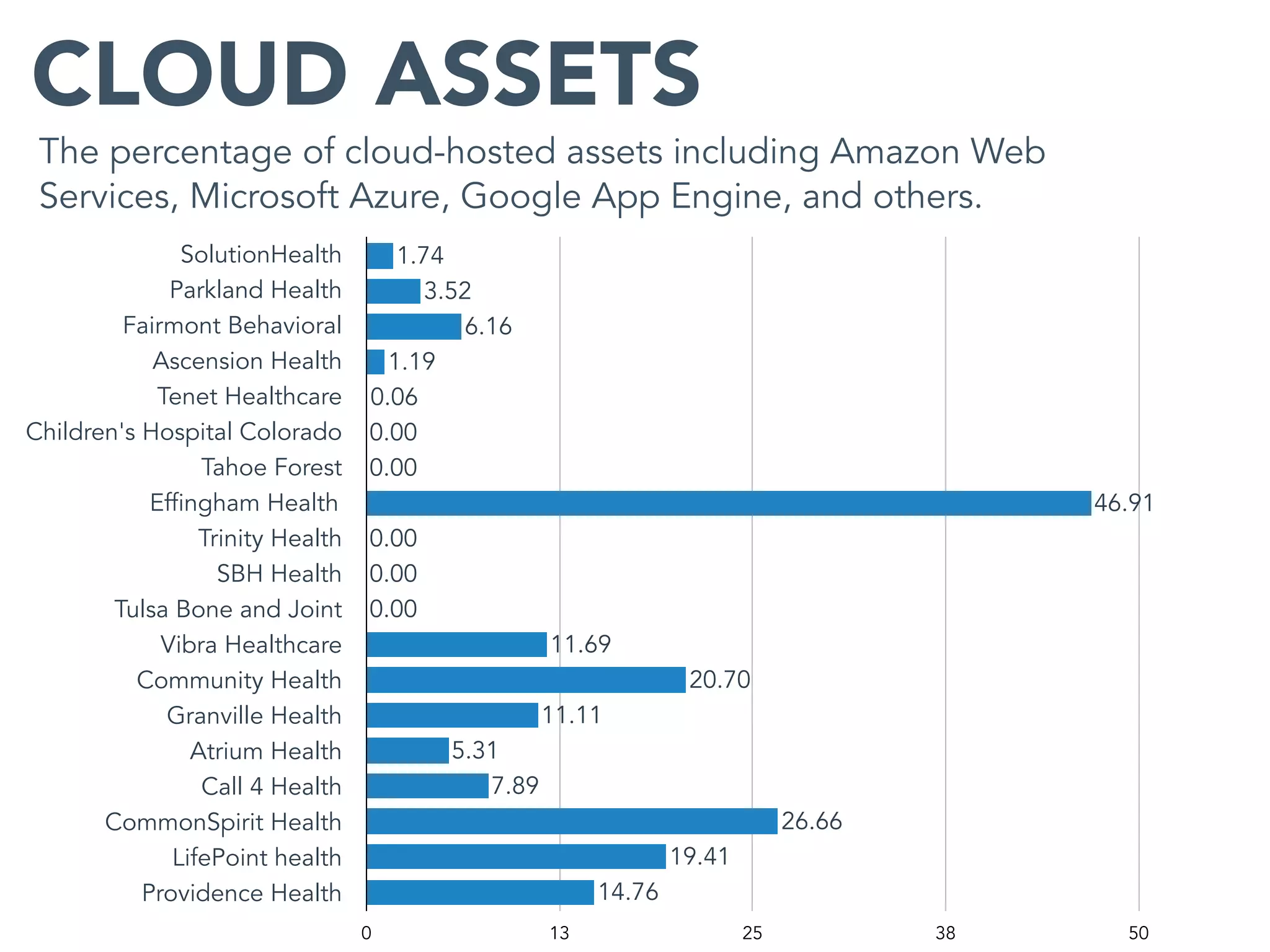
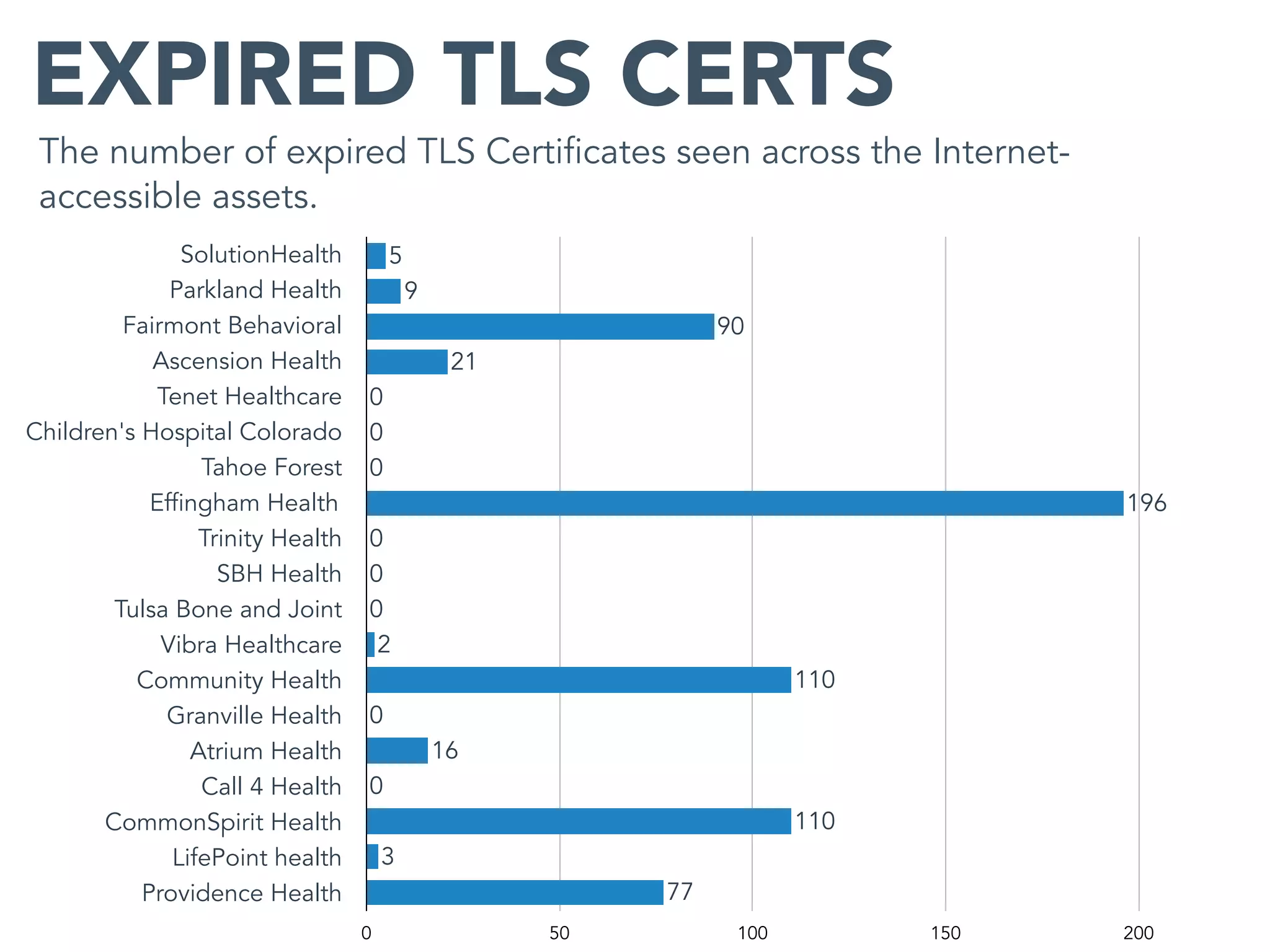
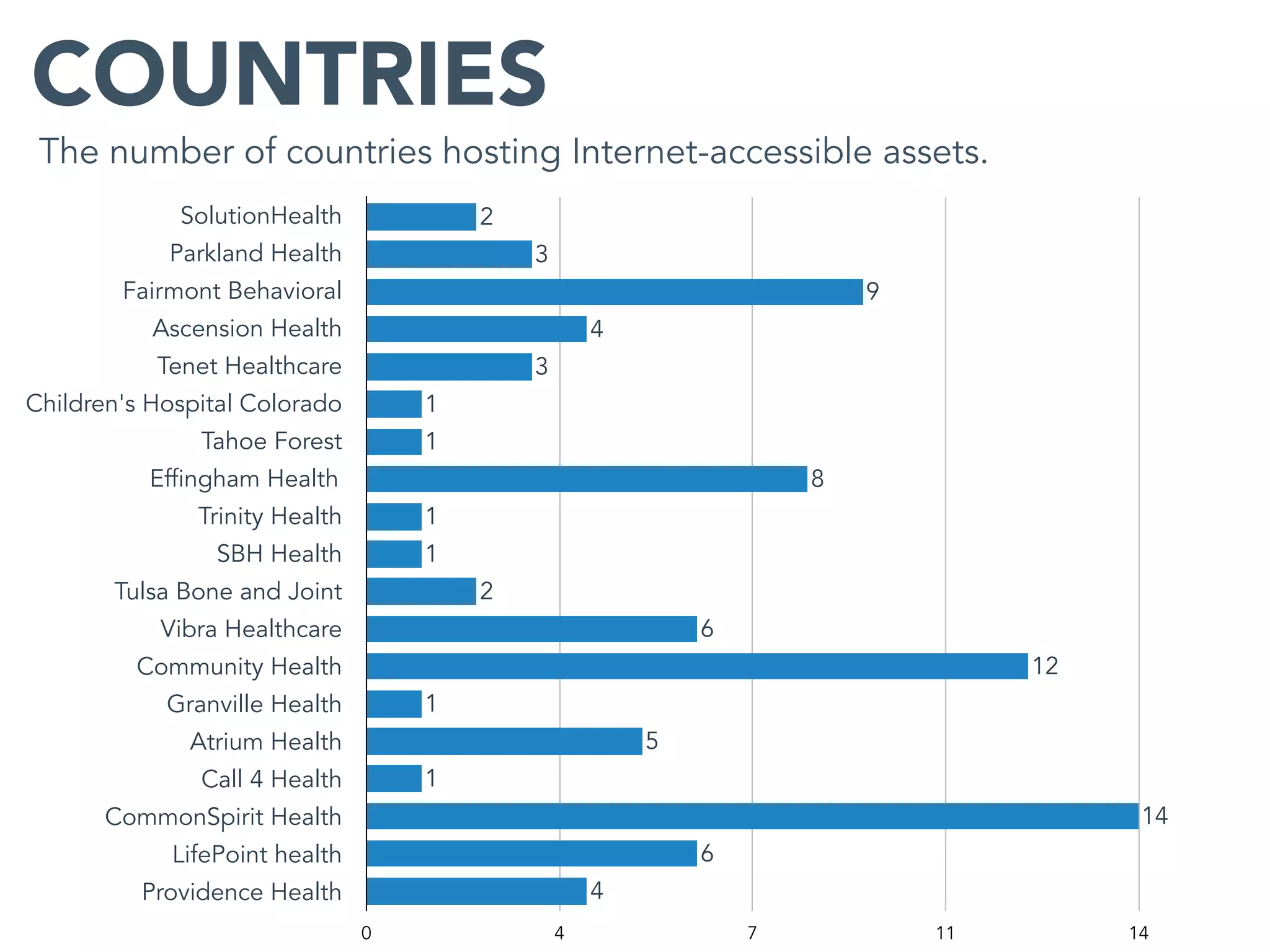
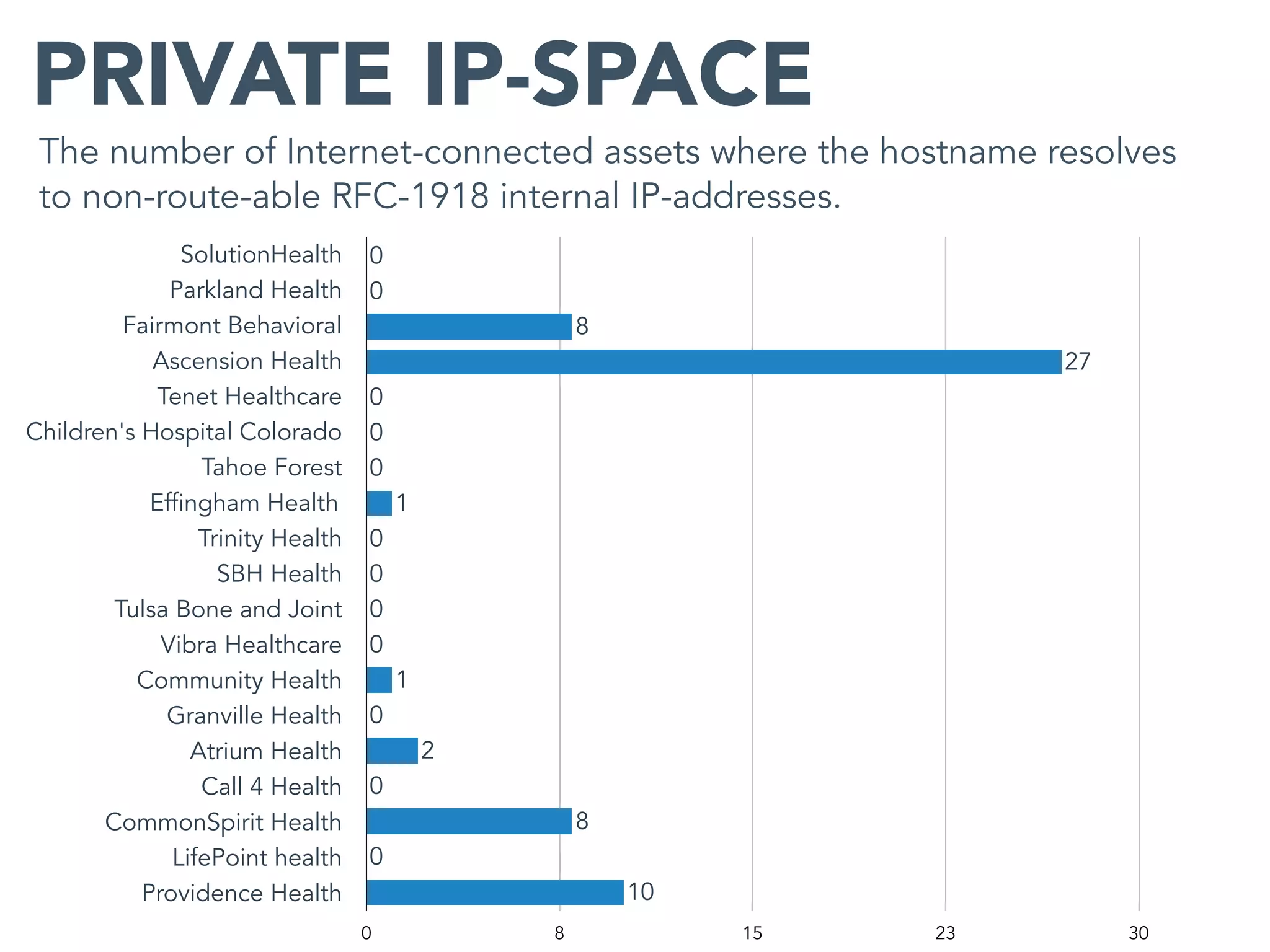
This document provides an analysis of the attack surface for 19 major healthcare organizations based on data collected by Bit Discovery from public sources on the internet. It includes statistics on each organization's total assets, domain names, cloud assets, use of content delivery networks, certificate authorities, expired certificates, geographic distribution, private IP addresses, WordPress vulnerabilities, and recommendations for building a security program around mapping the attack surface.