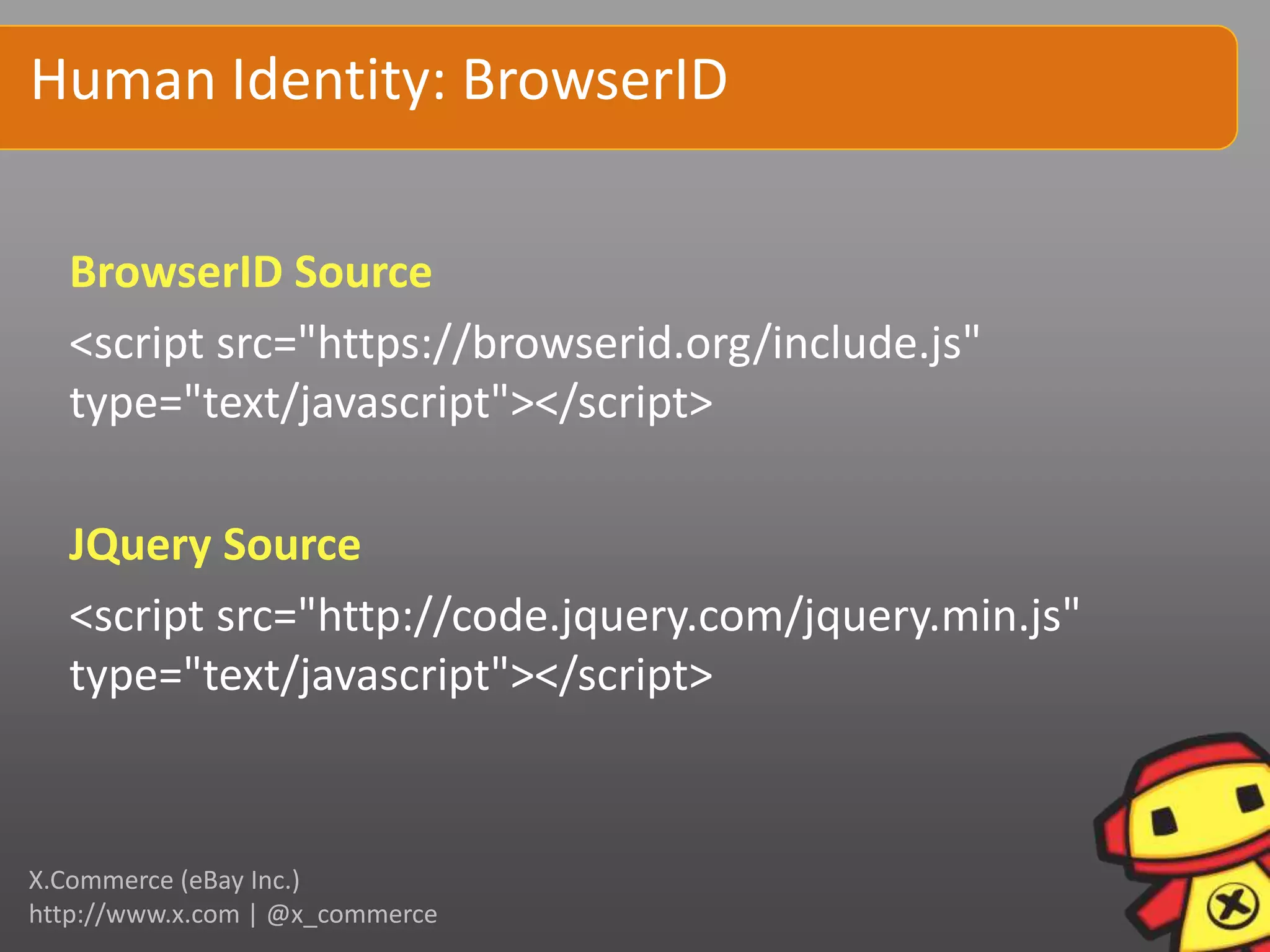
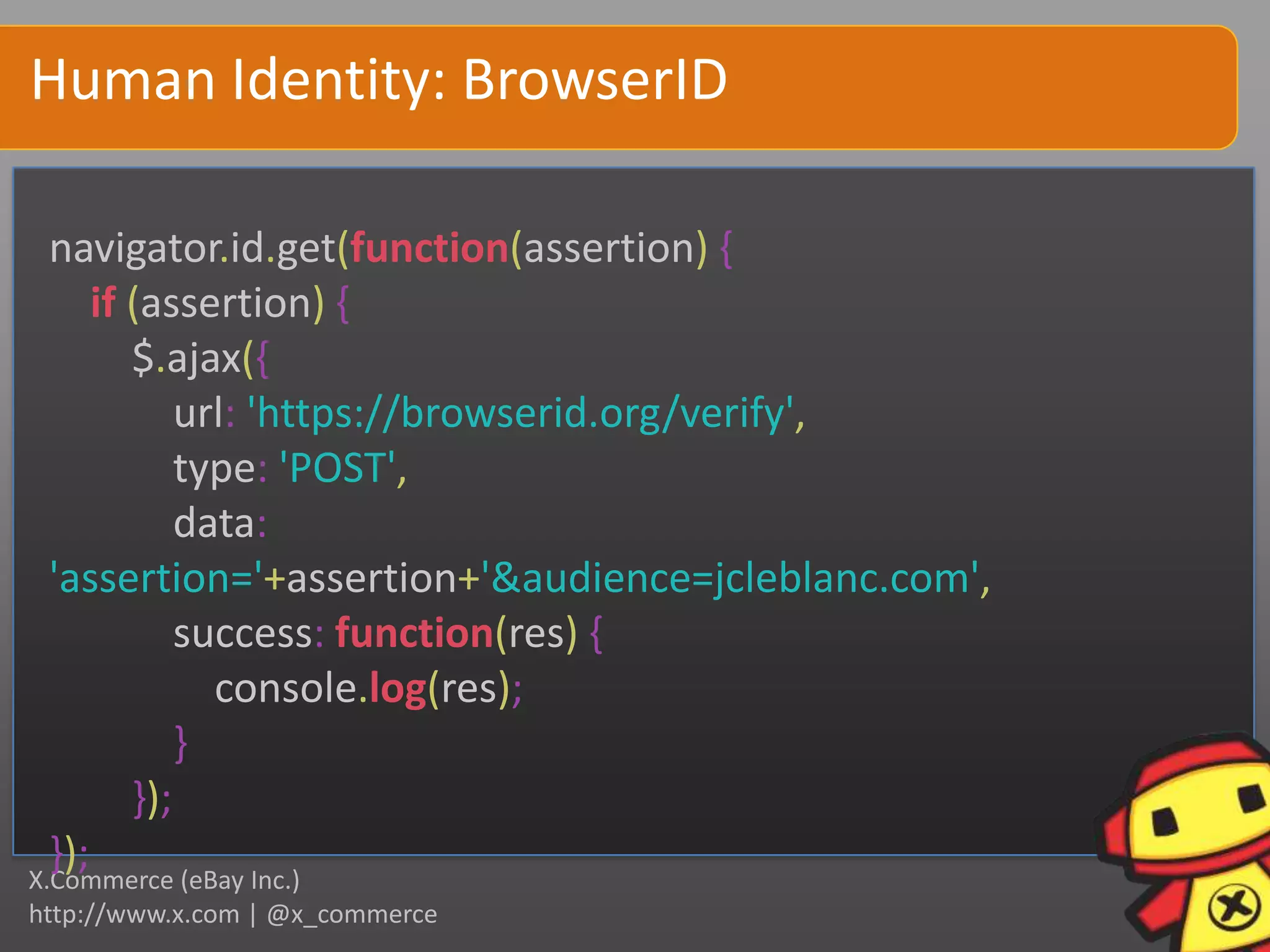
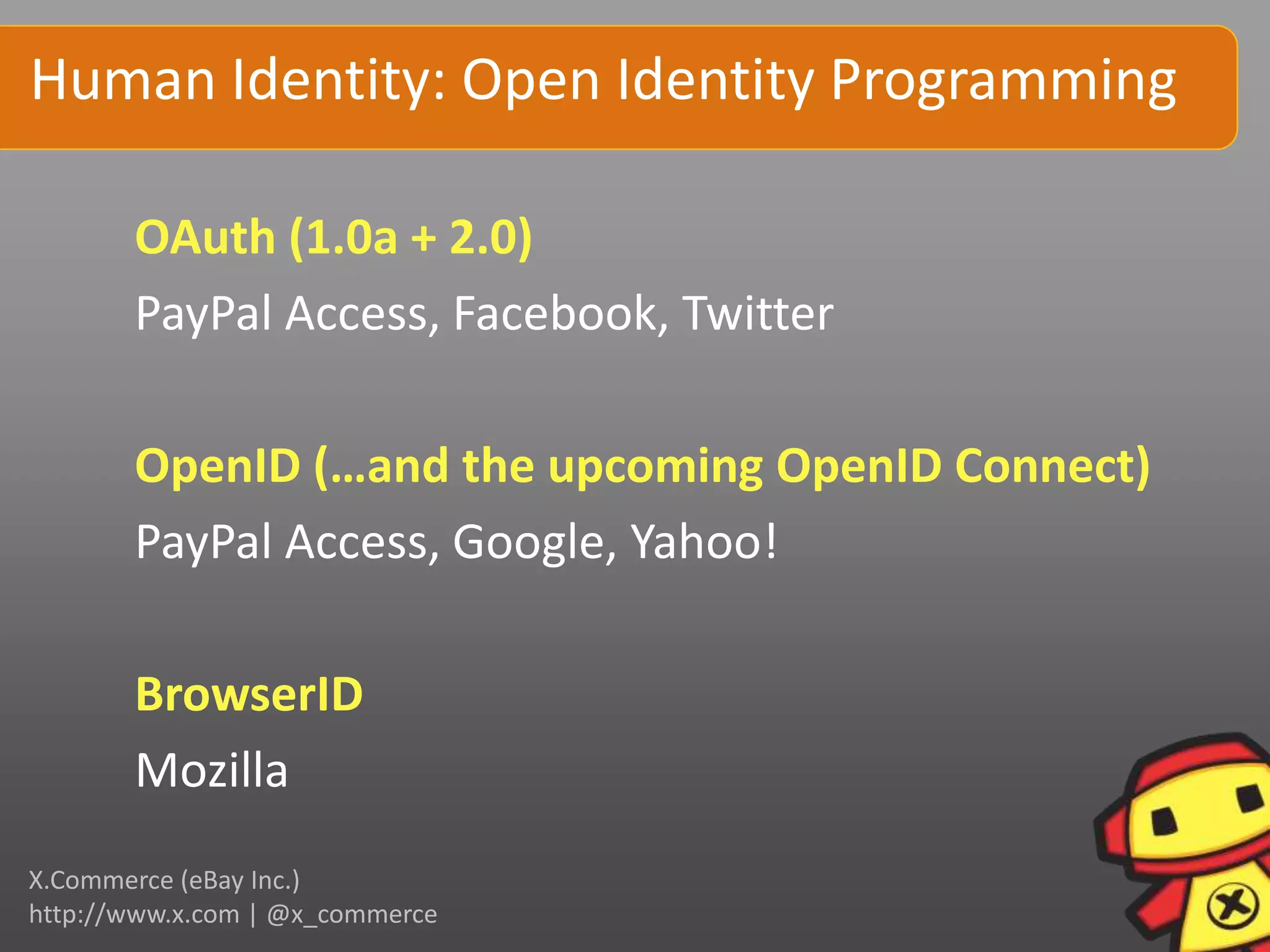
This document discusses human identity in the digital world. It covers foundational concepts of identity like tribalism and social grouping. It also discusses challenges around privacy, safety and how data can be used. Experimental identity methods are presented, like tracking anonymous users, real identity sources like BrowserID, and emerging standards like WebFinger. Programming techniques for tracking, grouping and identity are outlined. The document emphasizes that identity is complex, involving both authentication and understanding users.





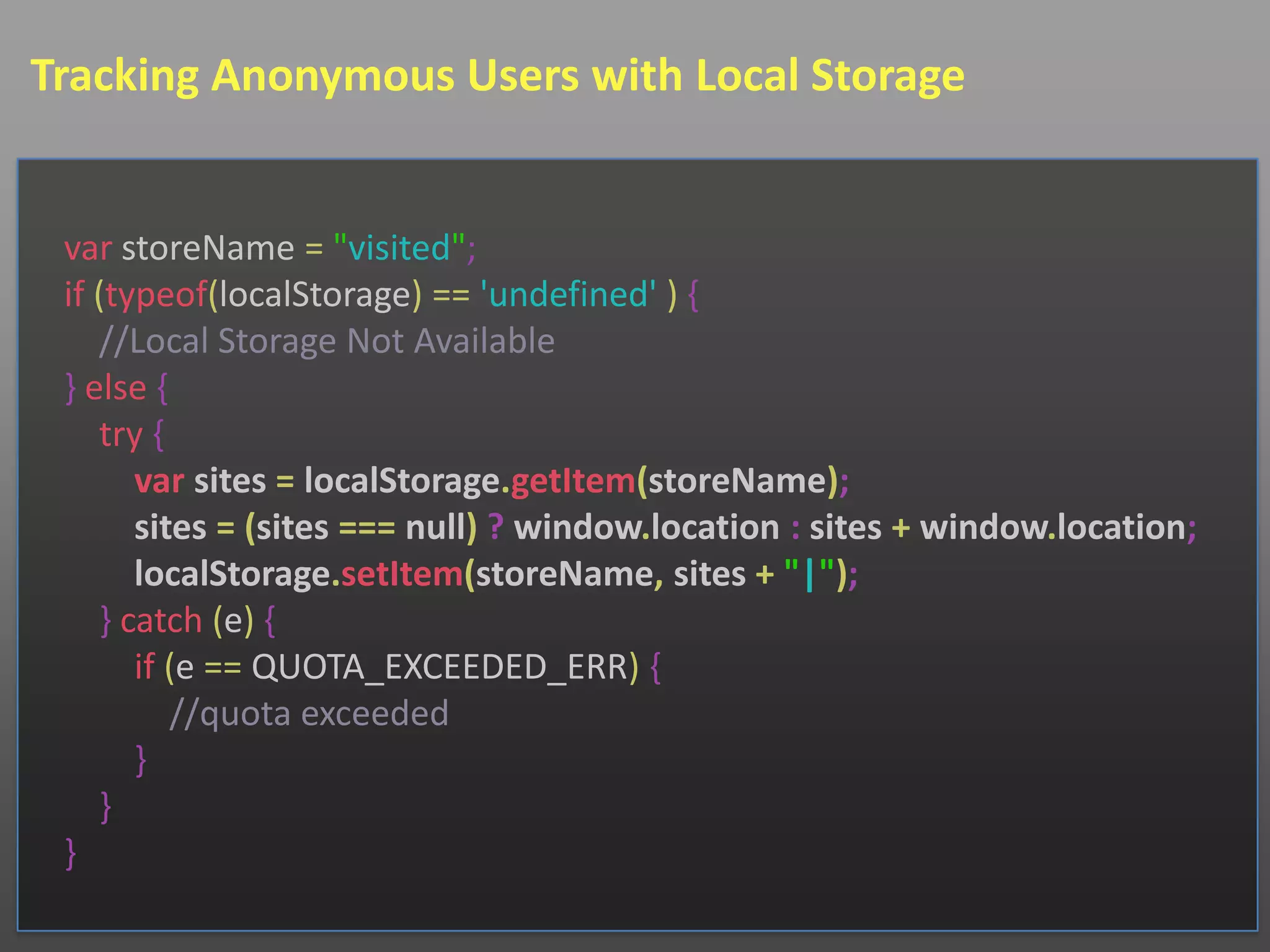
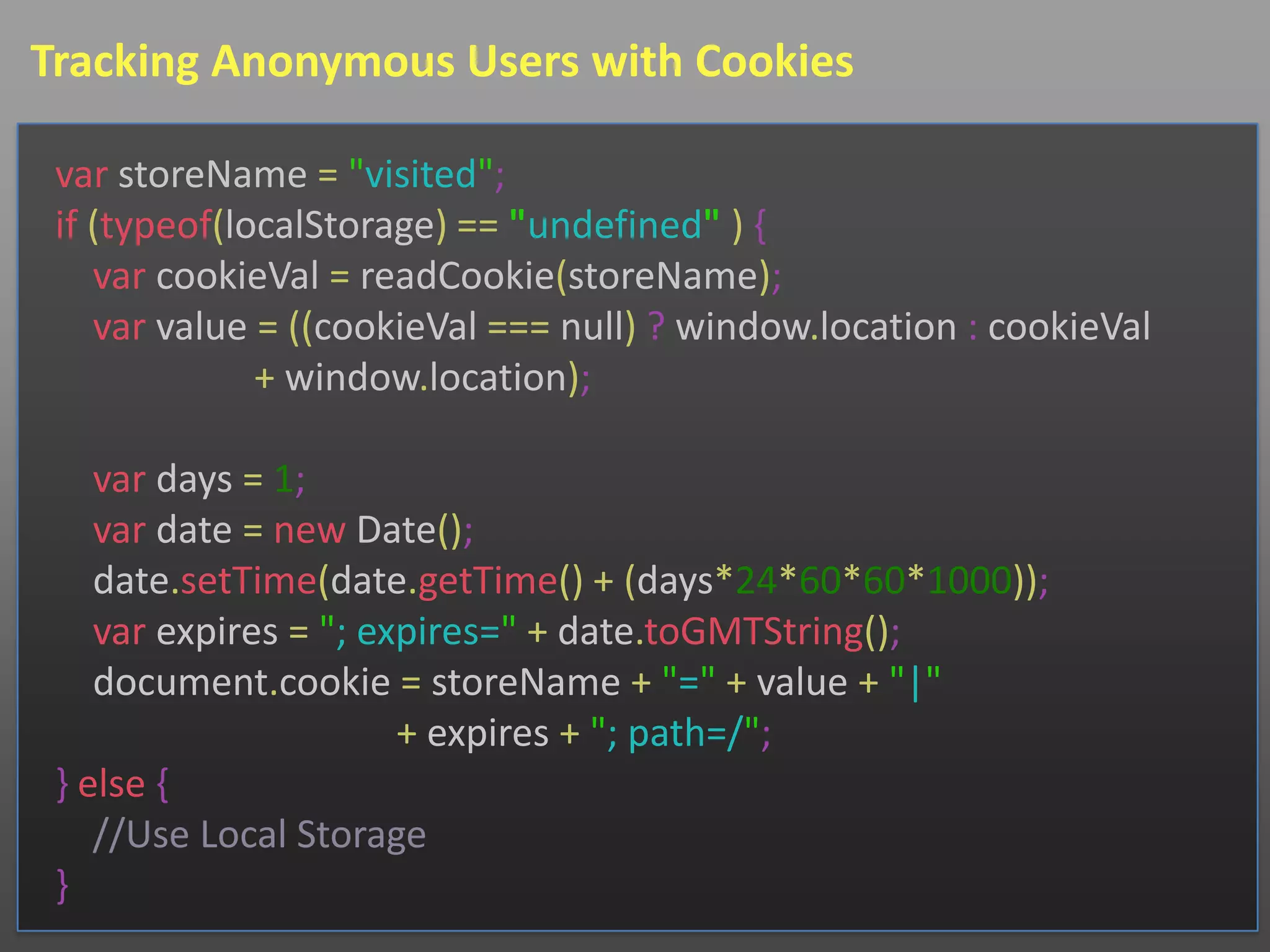
![Tracking Anonymous Users with Cookies
function readCookie(name) {
var nameEQ = name + "=";
var ca = document.cookie.split(';');
for (var i = 0; i < ca.length; i++) {
var c = ca[i];
while (c.charAt(0) == ' '){ c = c.substring(1, c.length) };
if (c.indexOf(nameEQ) == 0){
return c.substring(nameEQ.length, c.length);
}
}
return null;
}](https://image.slidesharecdn.com/2012marconfoodefiningidentity-120227141059-phpapp02/75/2012-Confoo-Defining-User-Identity-10-2048.jpg)