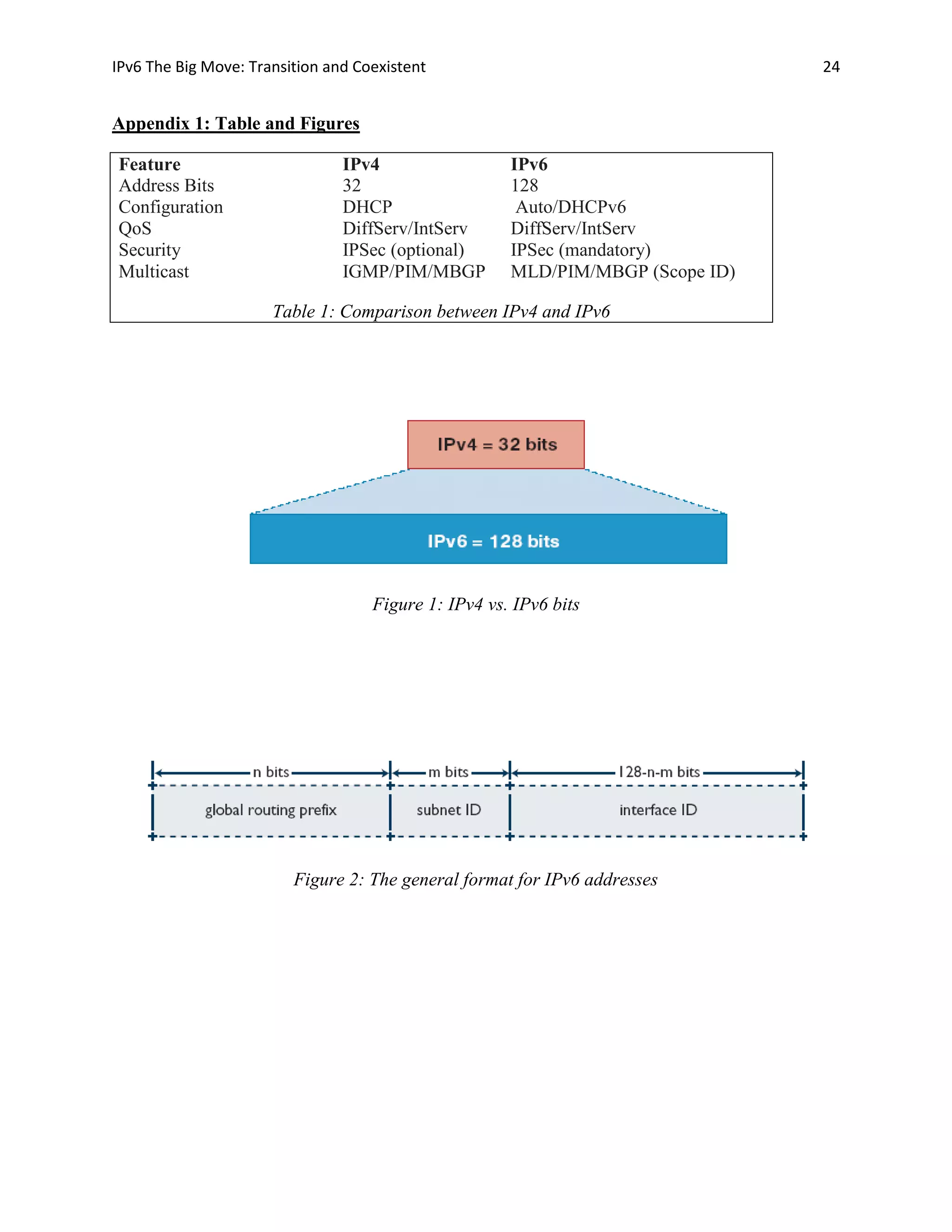
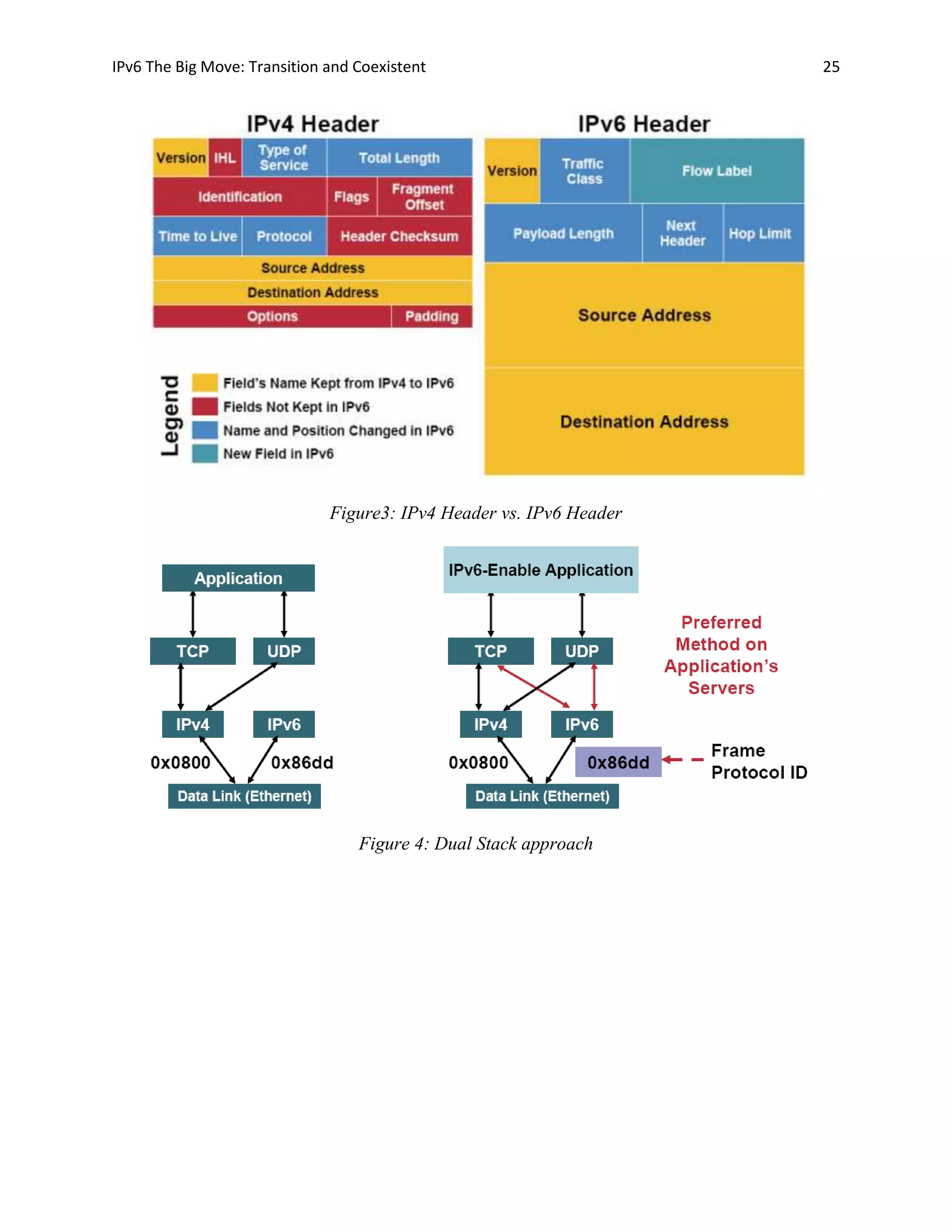
The document discusses the transition from IPv4 to IPv6. It notes that IPv4 addresses are running out due to the rapid growth of the internet. IPv6 was developed as a replacement, using a 128-bit address space to provide vastly more addresses. The document outlines some key advantages of IPv6, such as larger addresses, simpler headers, better security and quality of service support. It also examines how IPv6 and IPv4 will coexist during a long transition period, using various transition technologies.