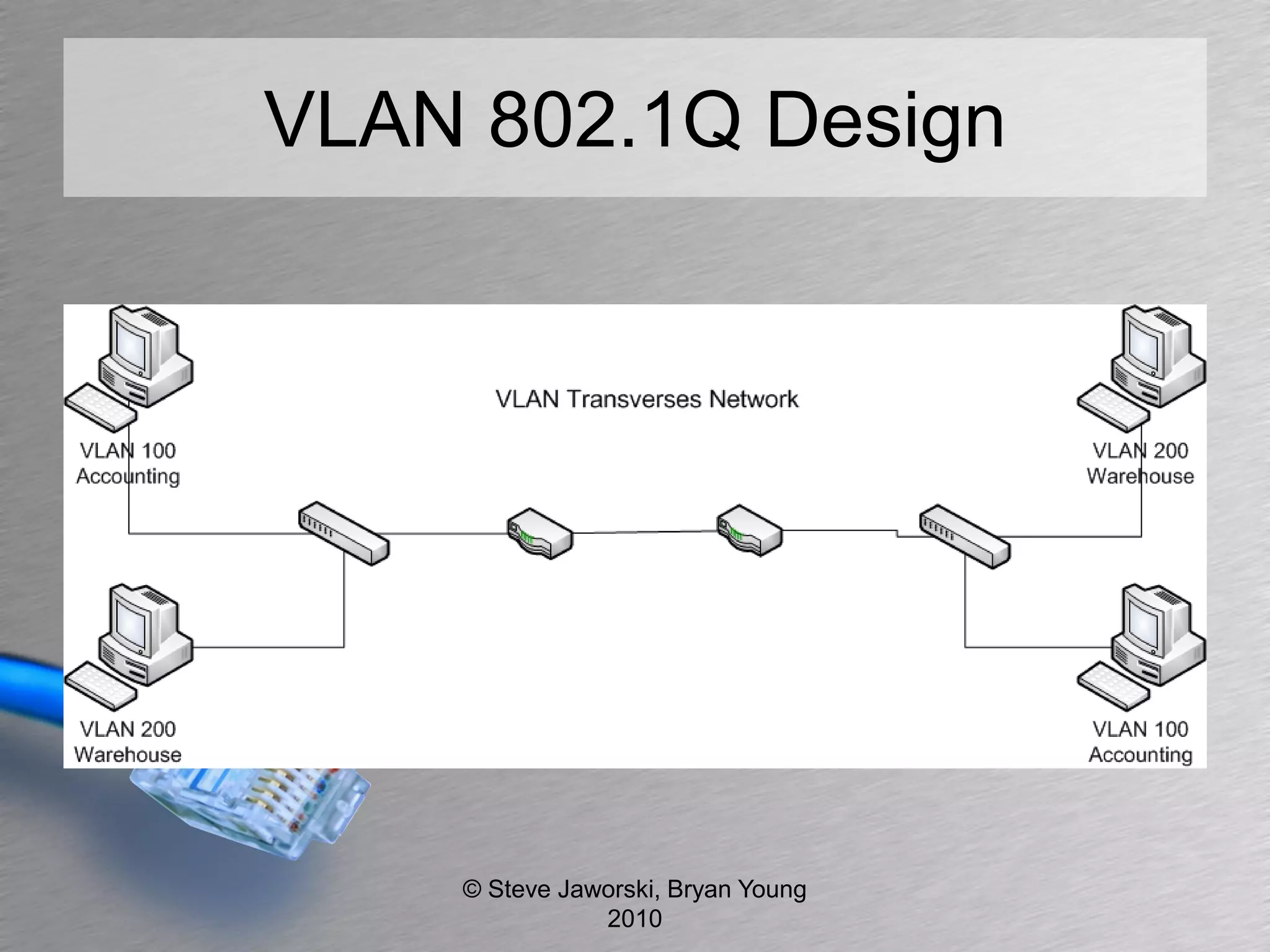
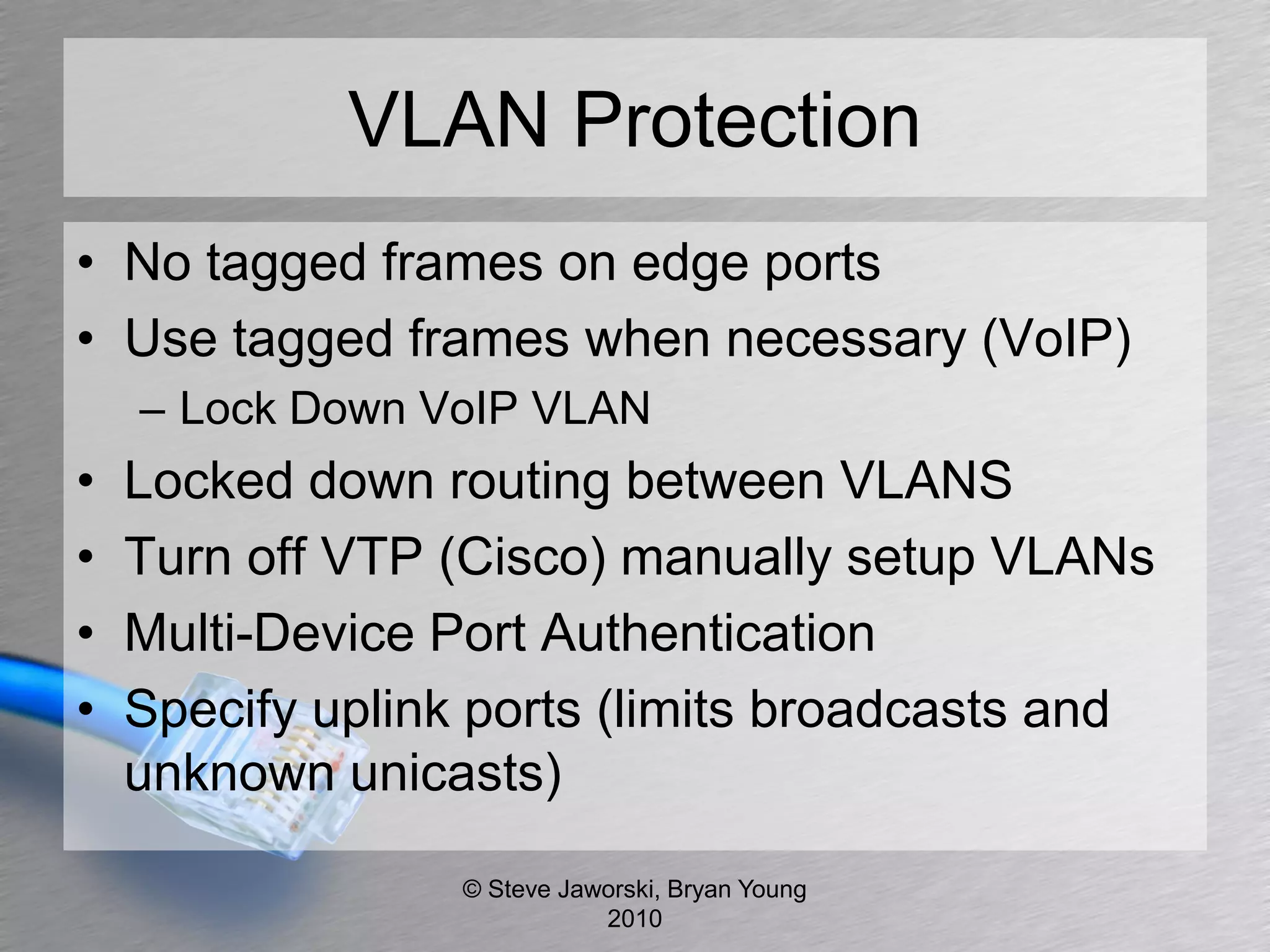
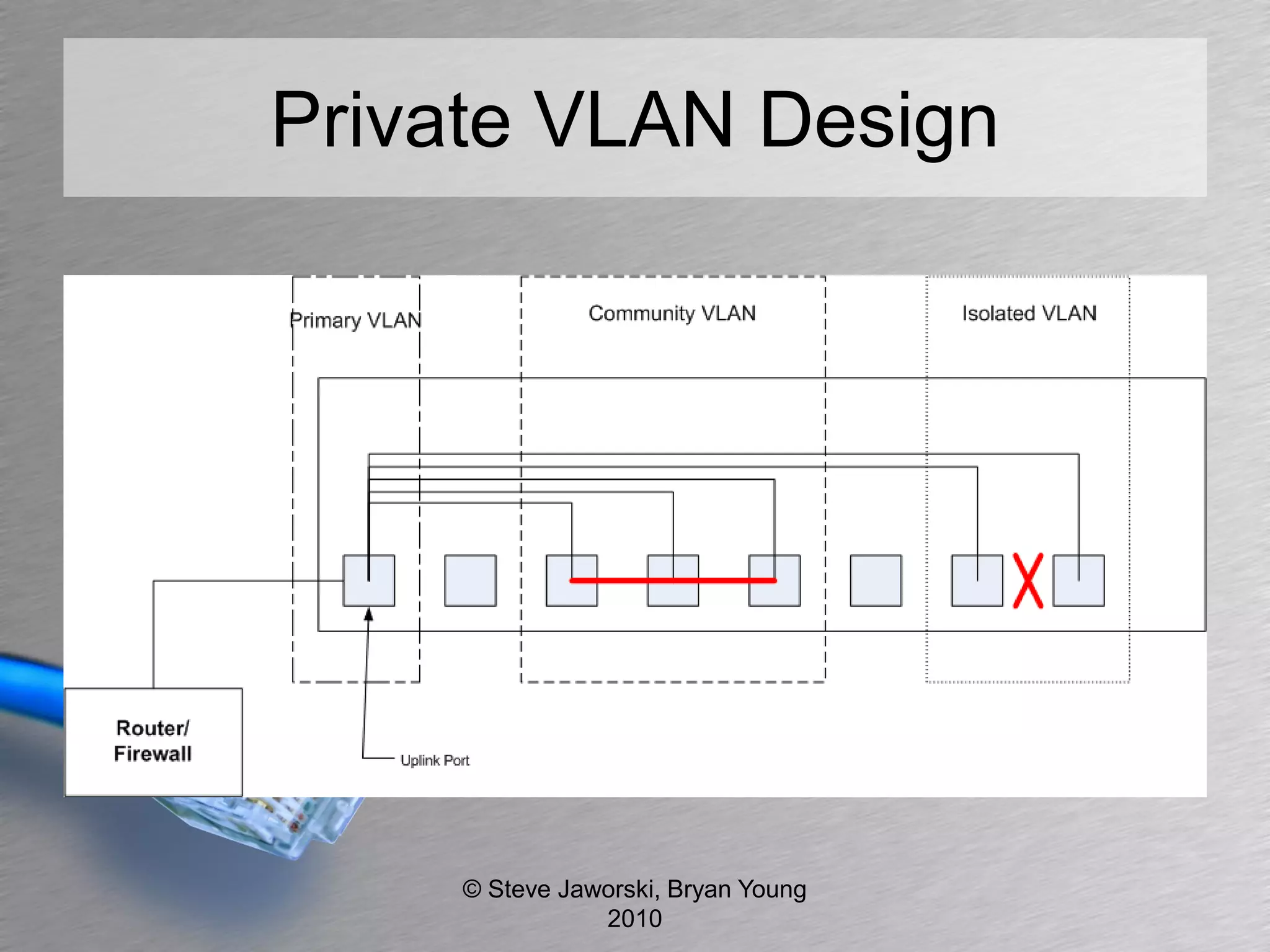
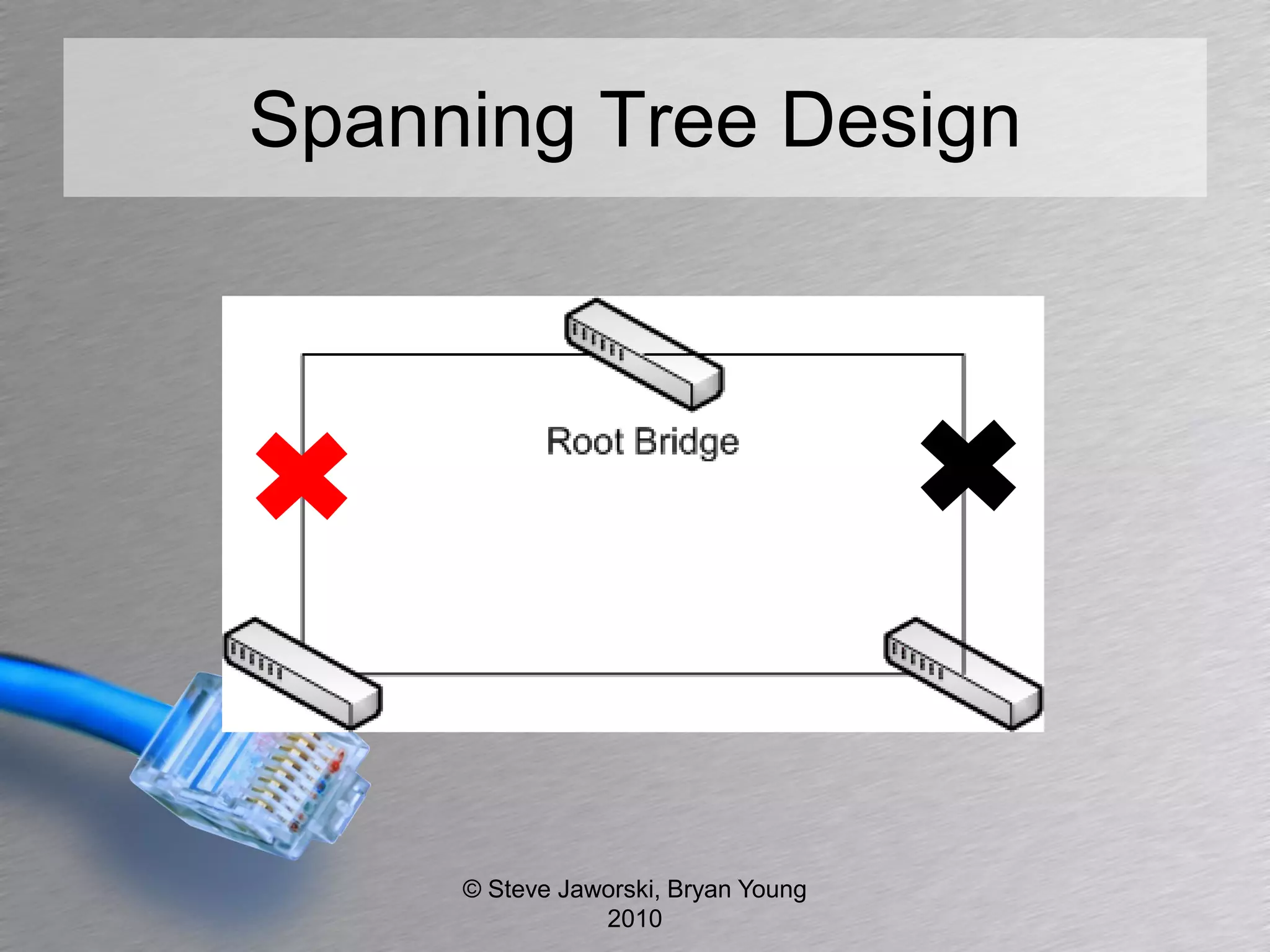
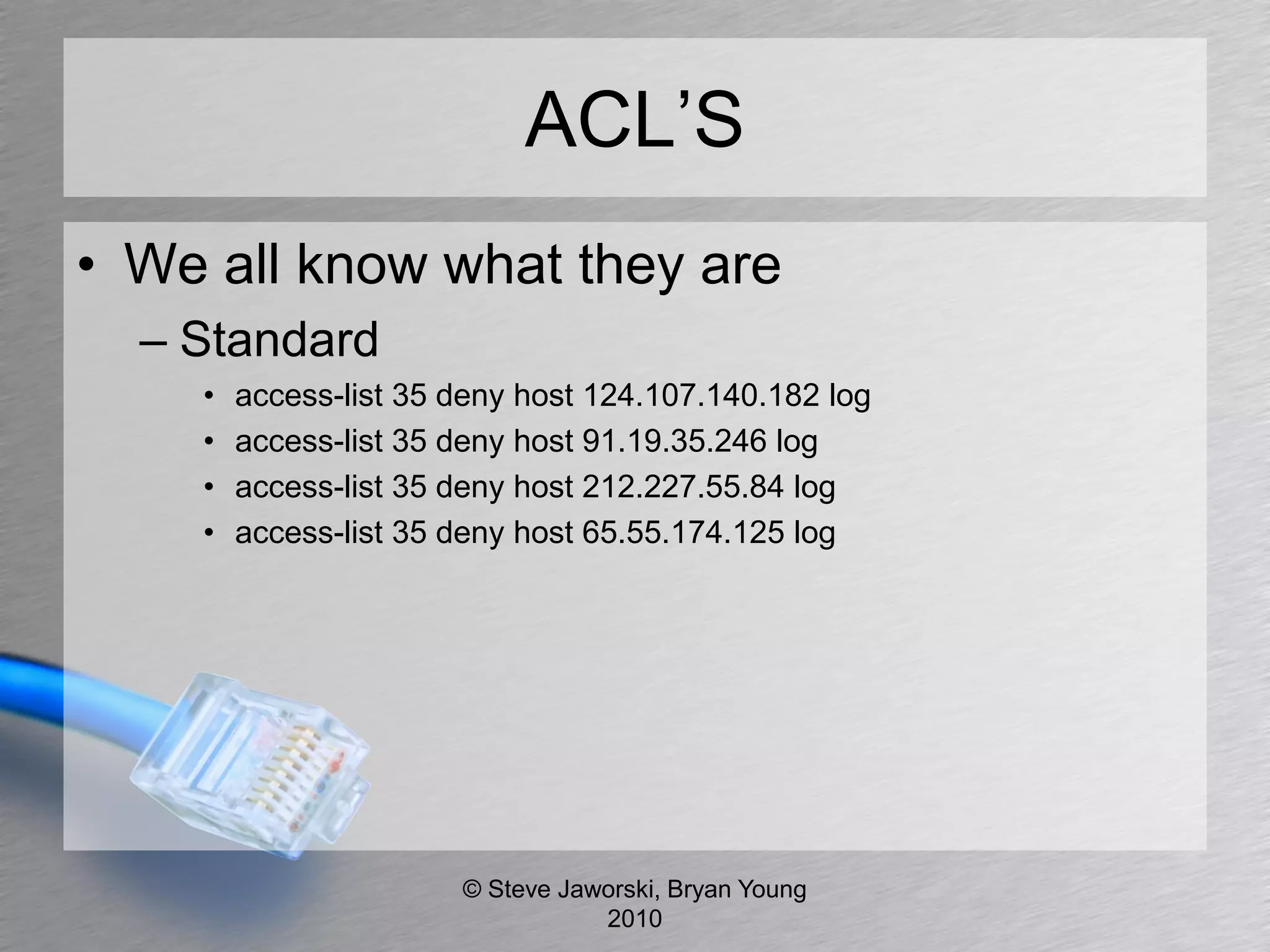
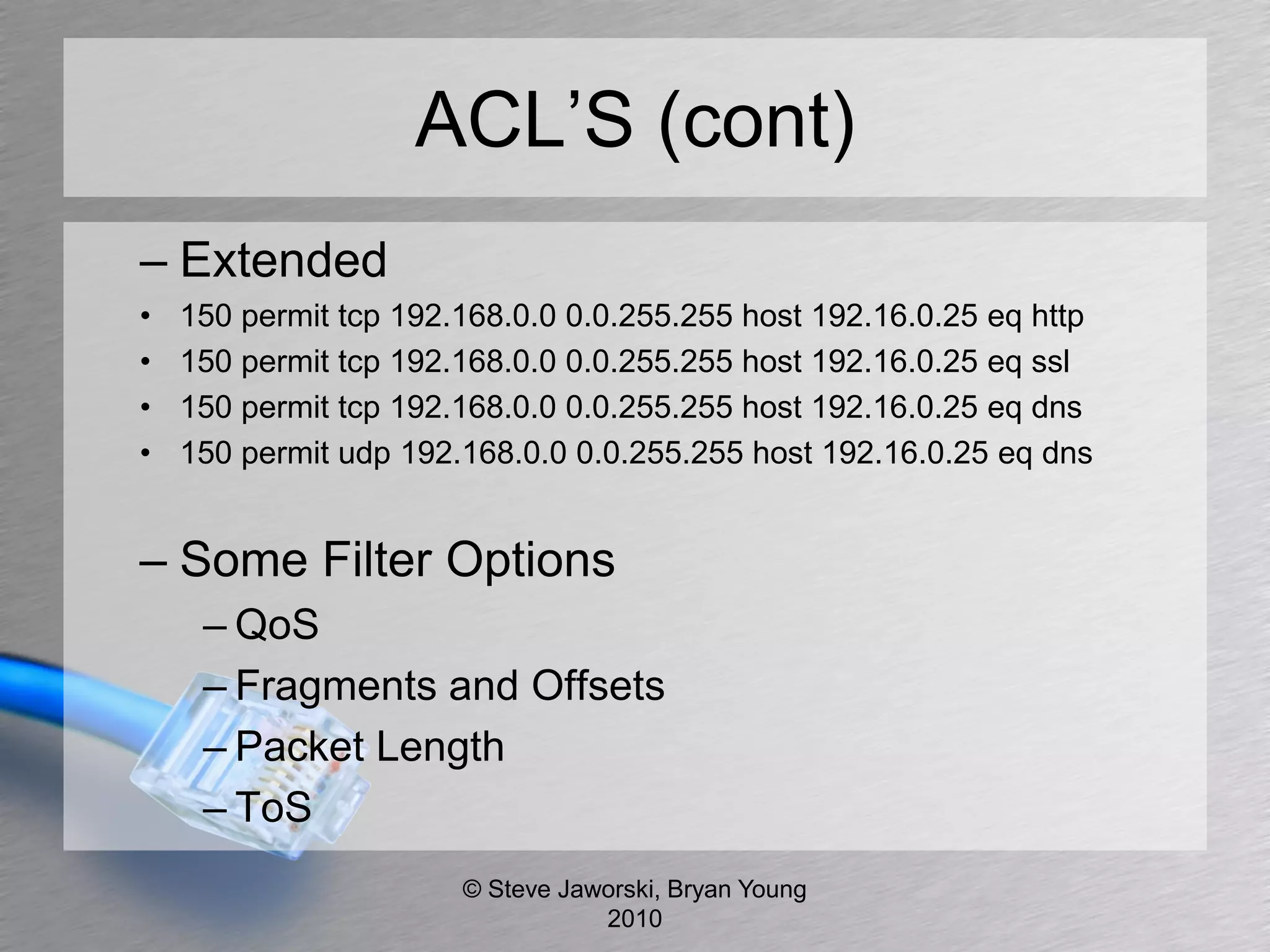
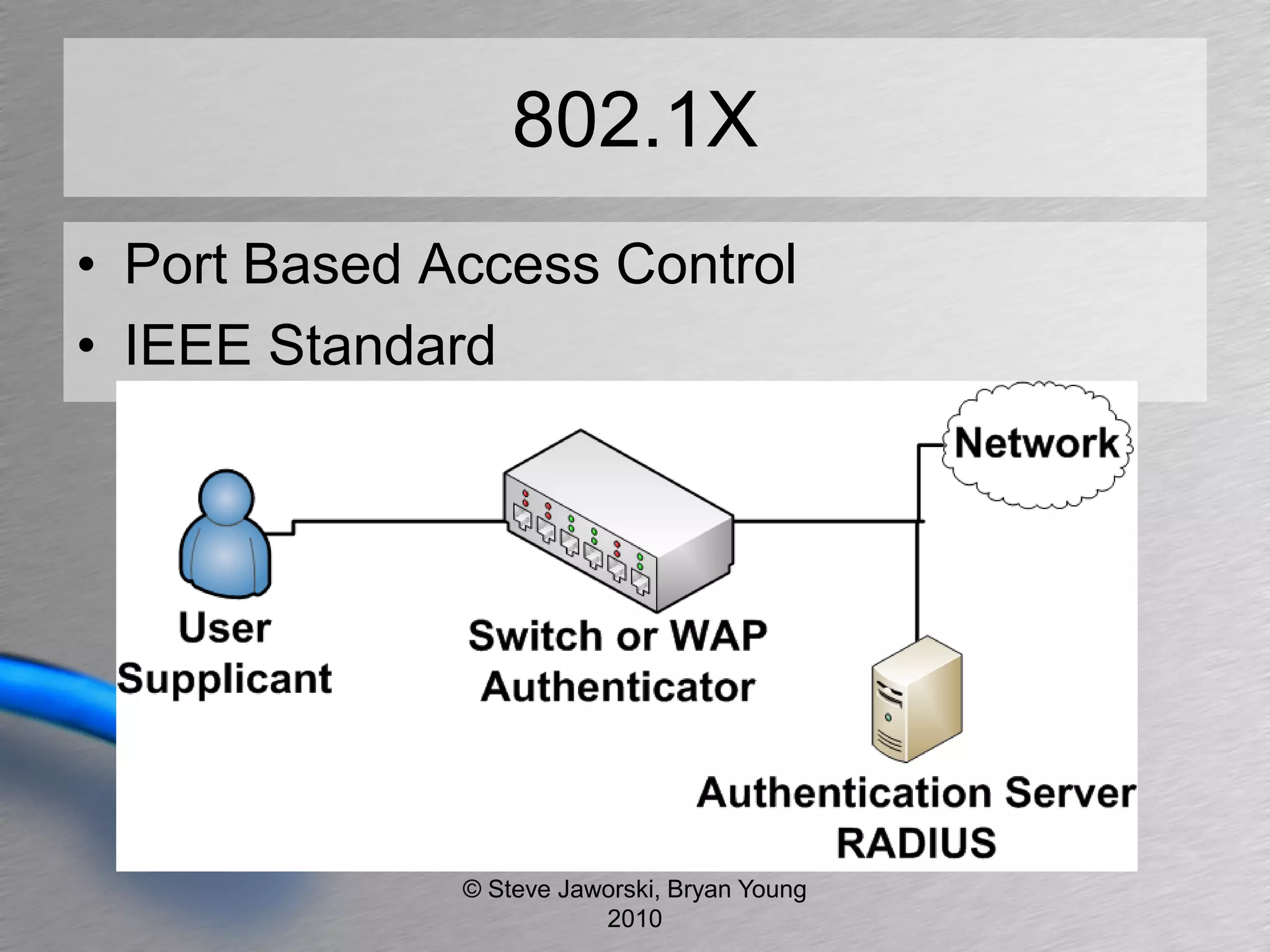
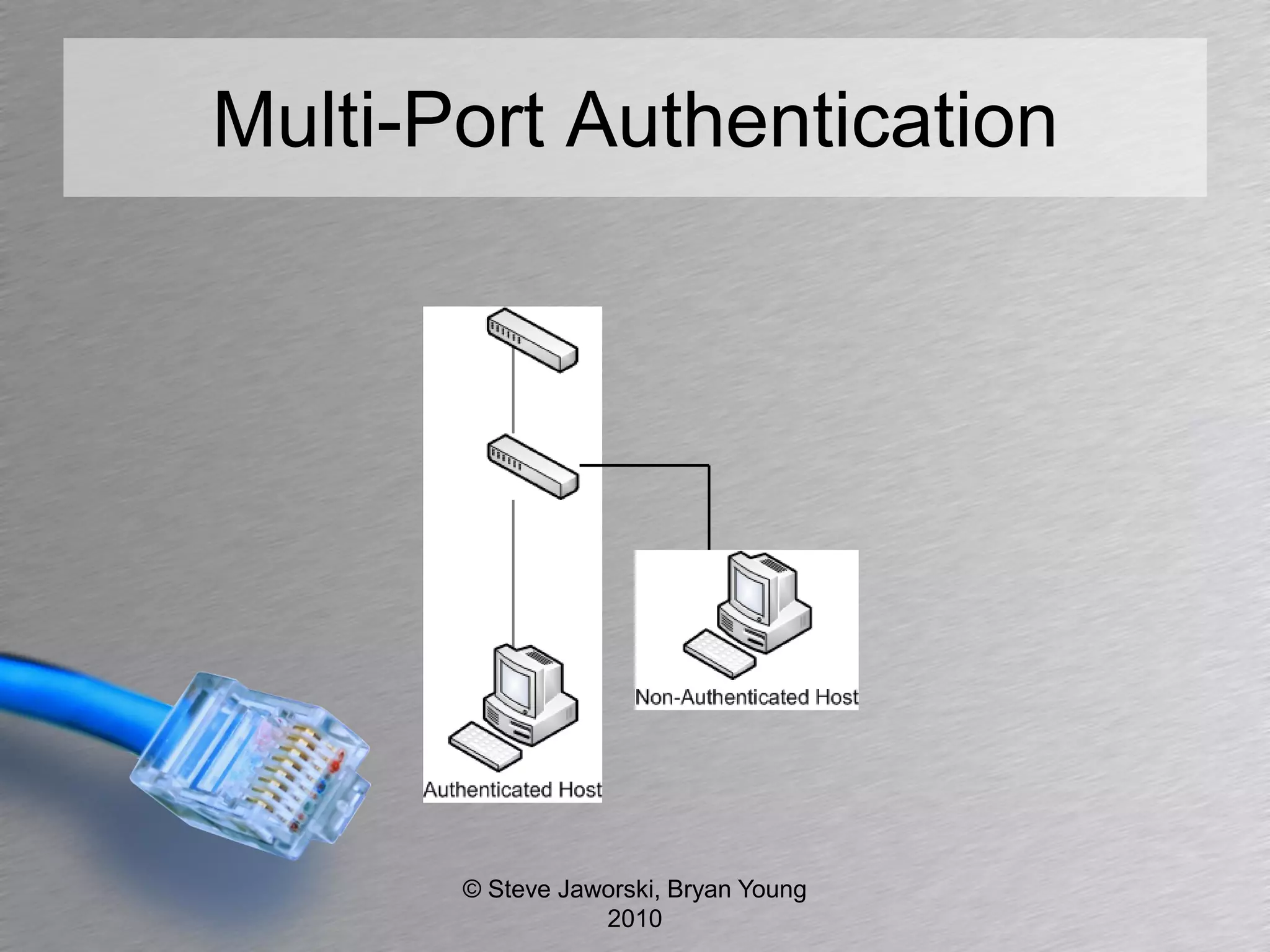
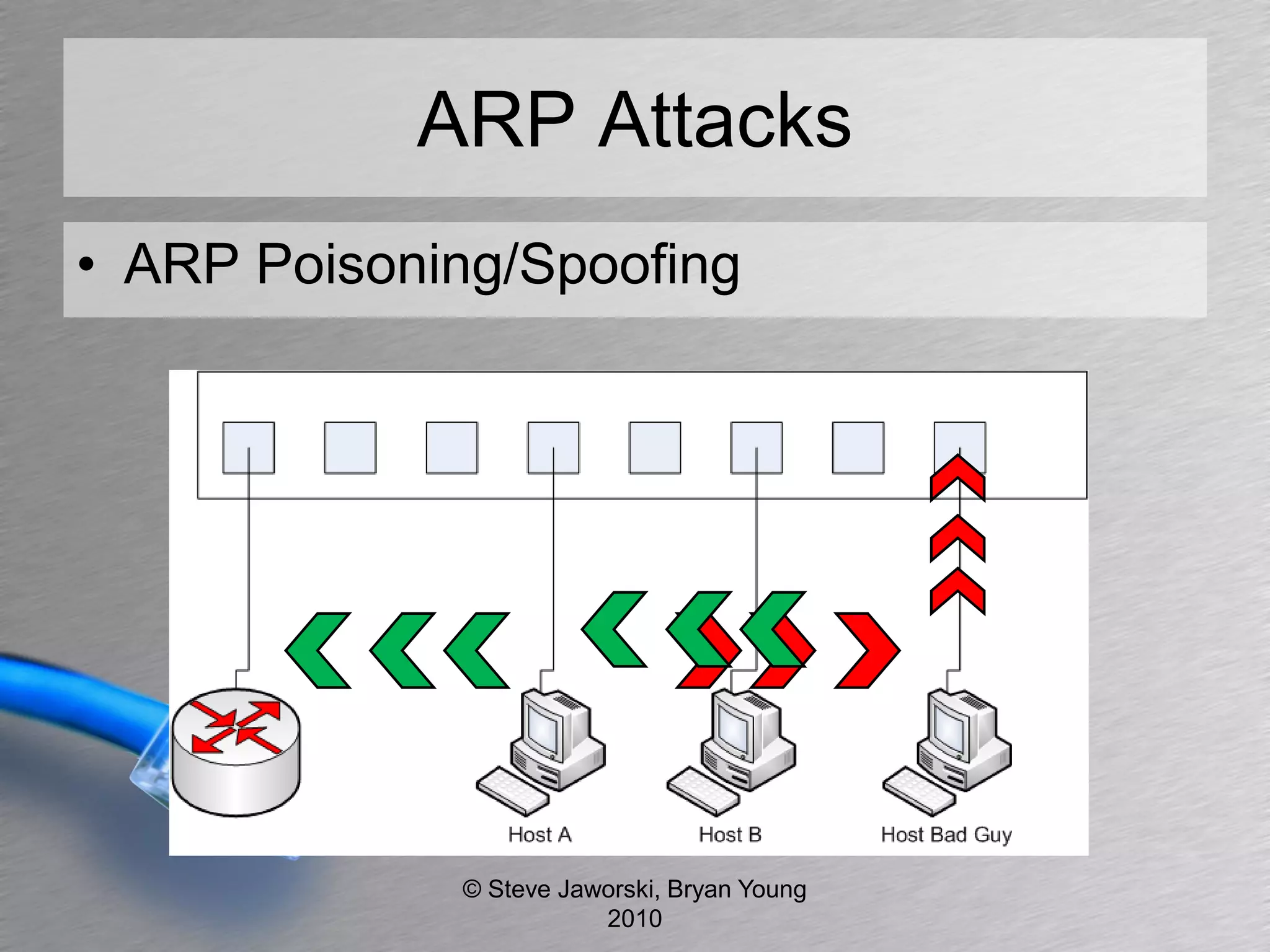
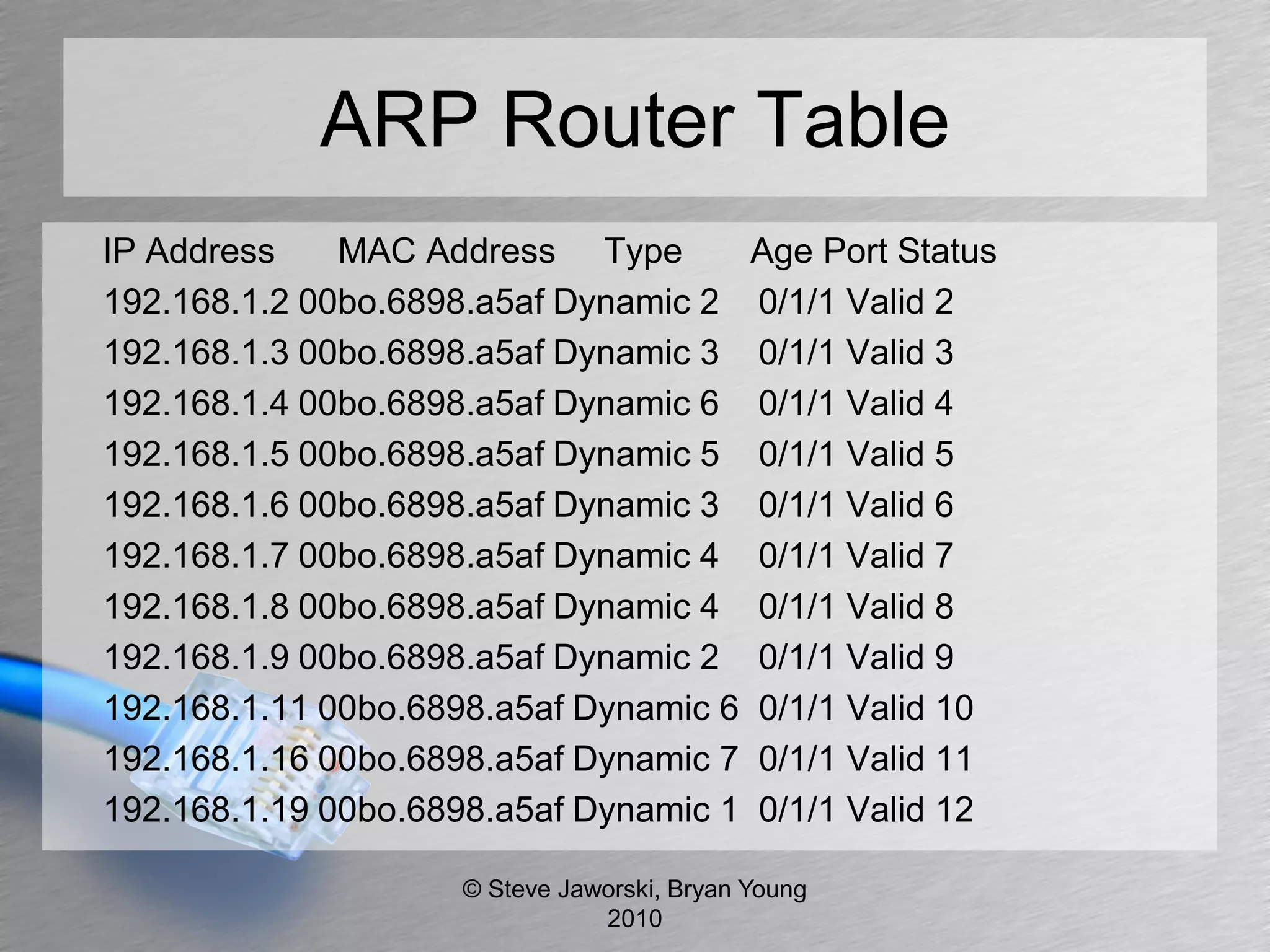
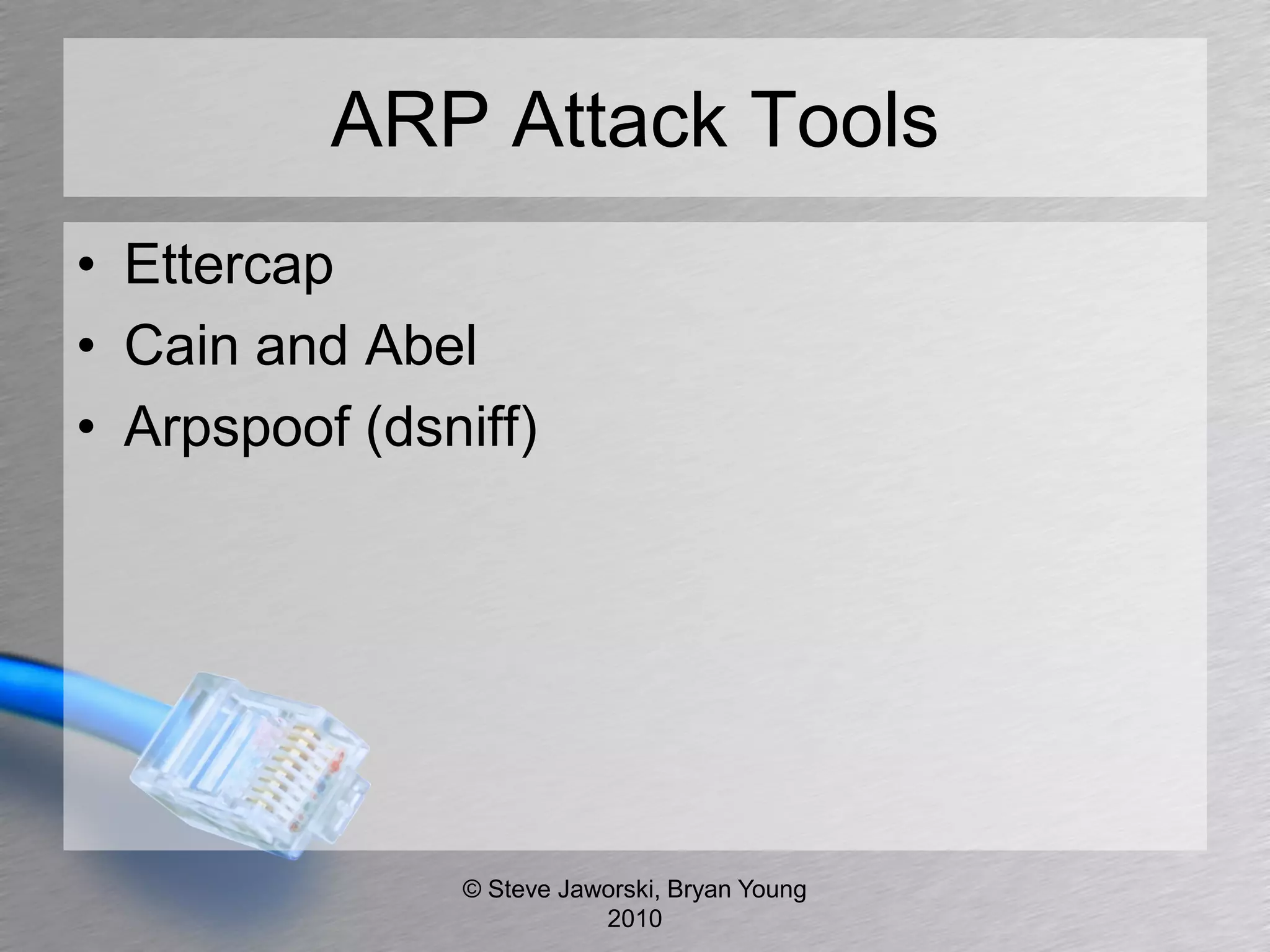
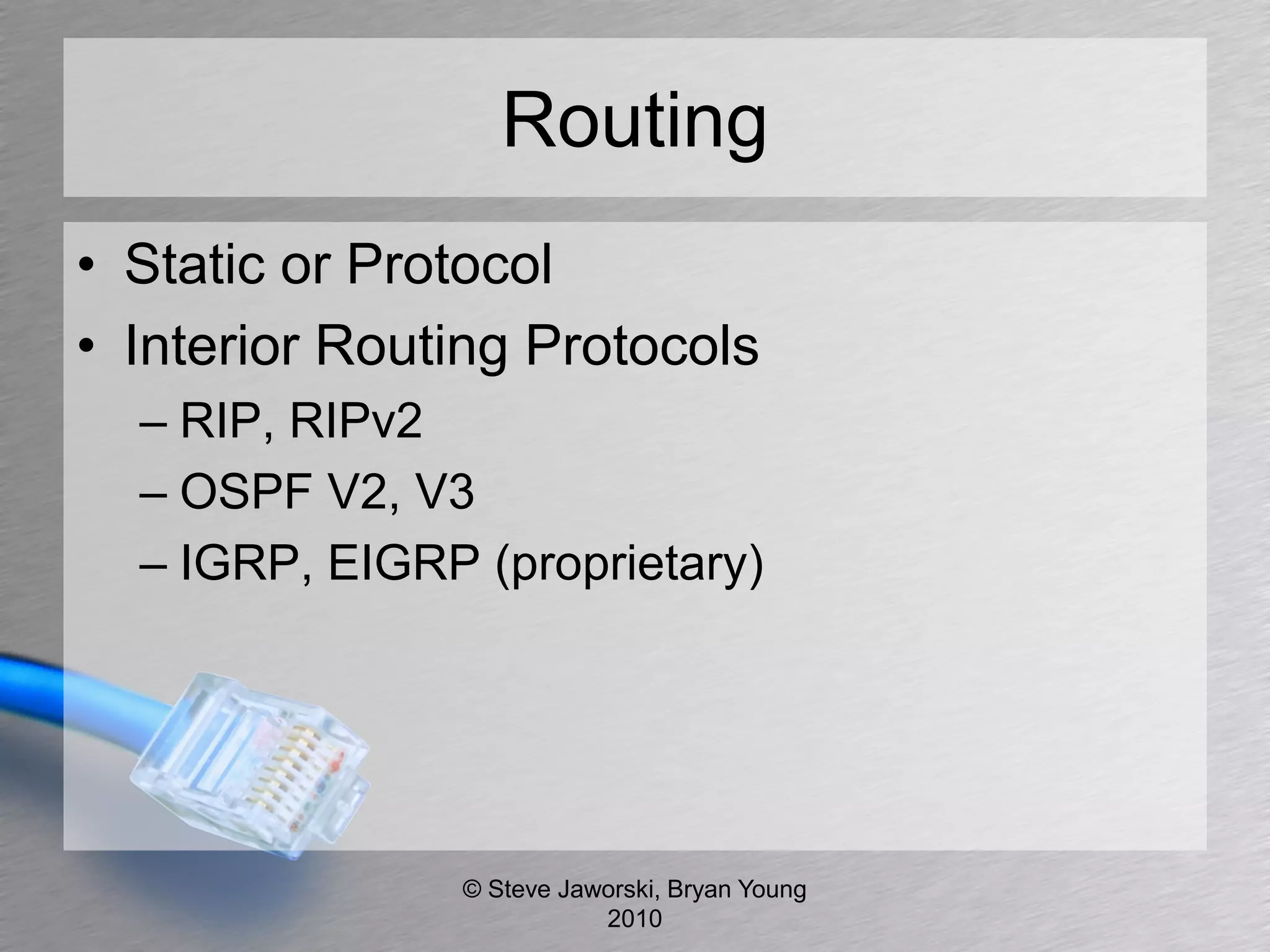
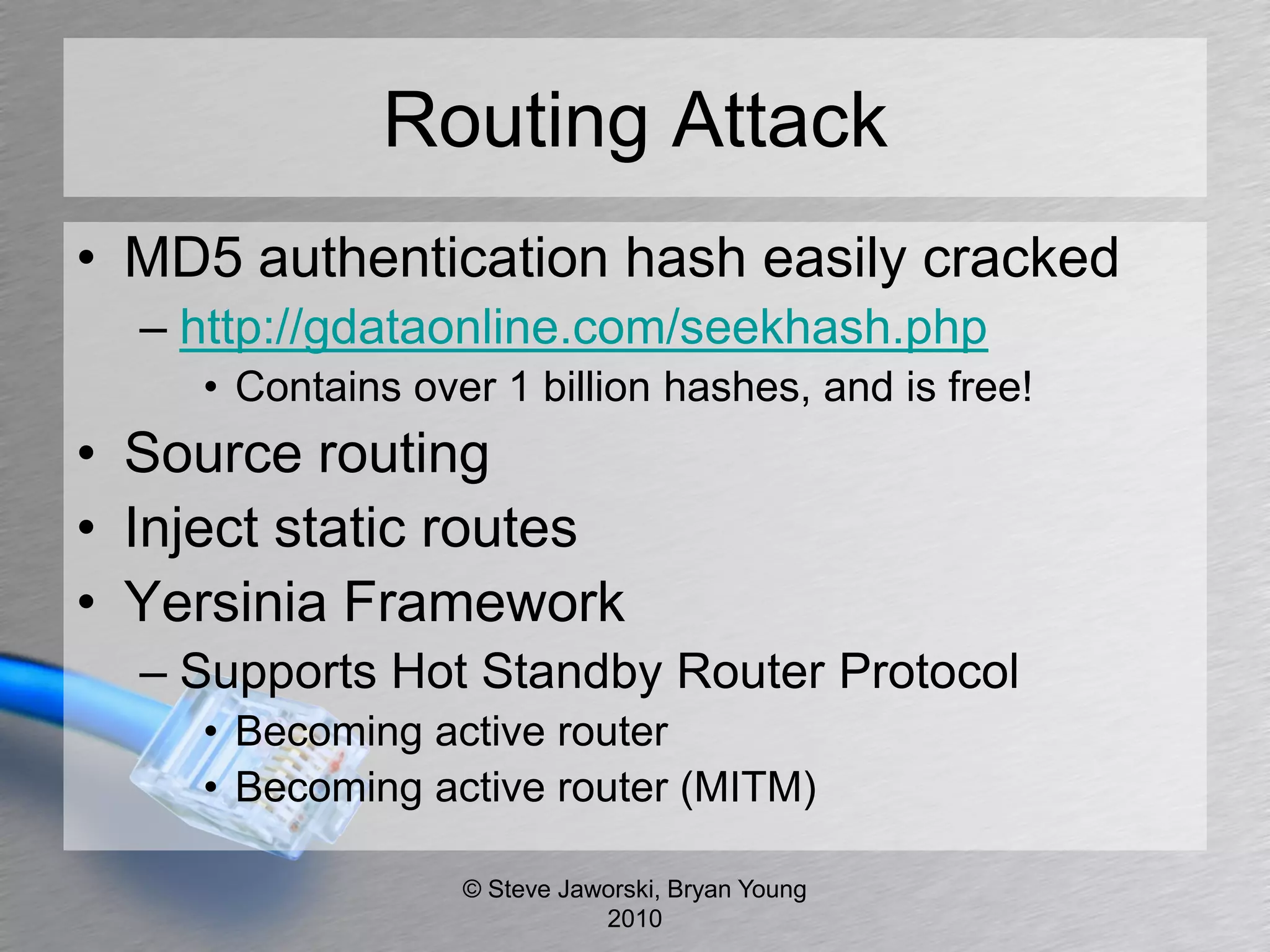
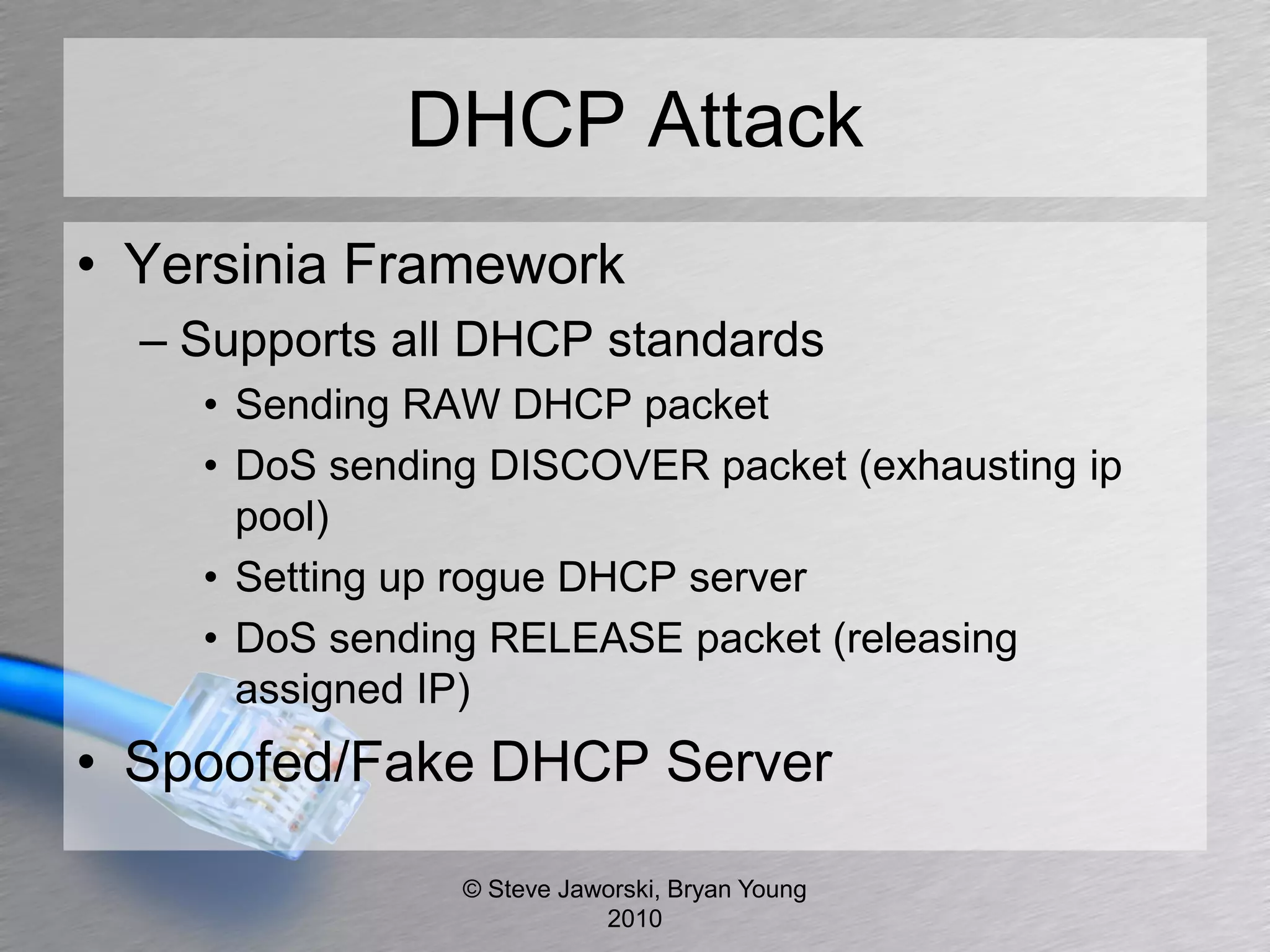
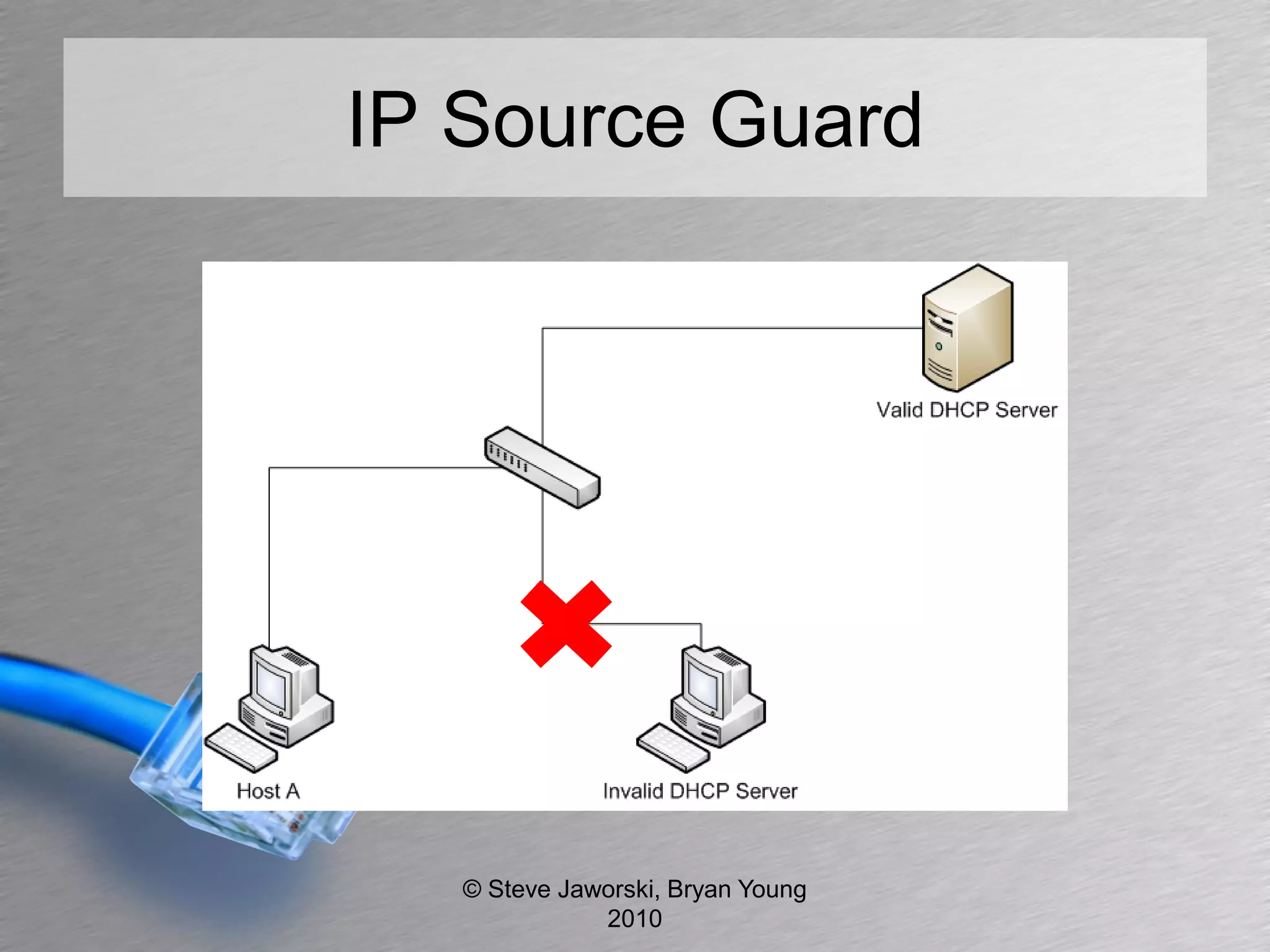
The document discusses various network security topics related to Layer 2 and Layer 3, including discovery protocols, attacks, and protection strategies. It emphasizes the importance of questioning vendors about their products and the need for specific configurations to safeguard against various vulnerabilities like spoofing and denial-of-service attacks. Key areas covered include VLAN security, authentication methods, ARP protection, and routing best practices.