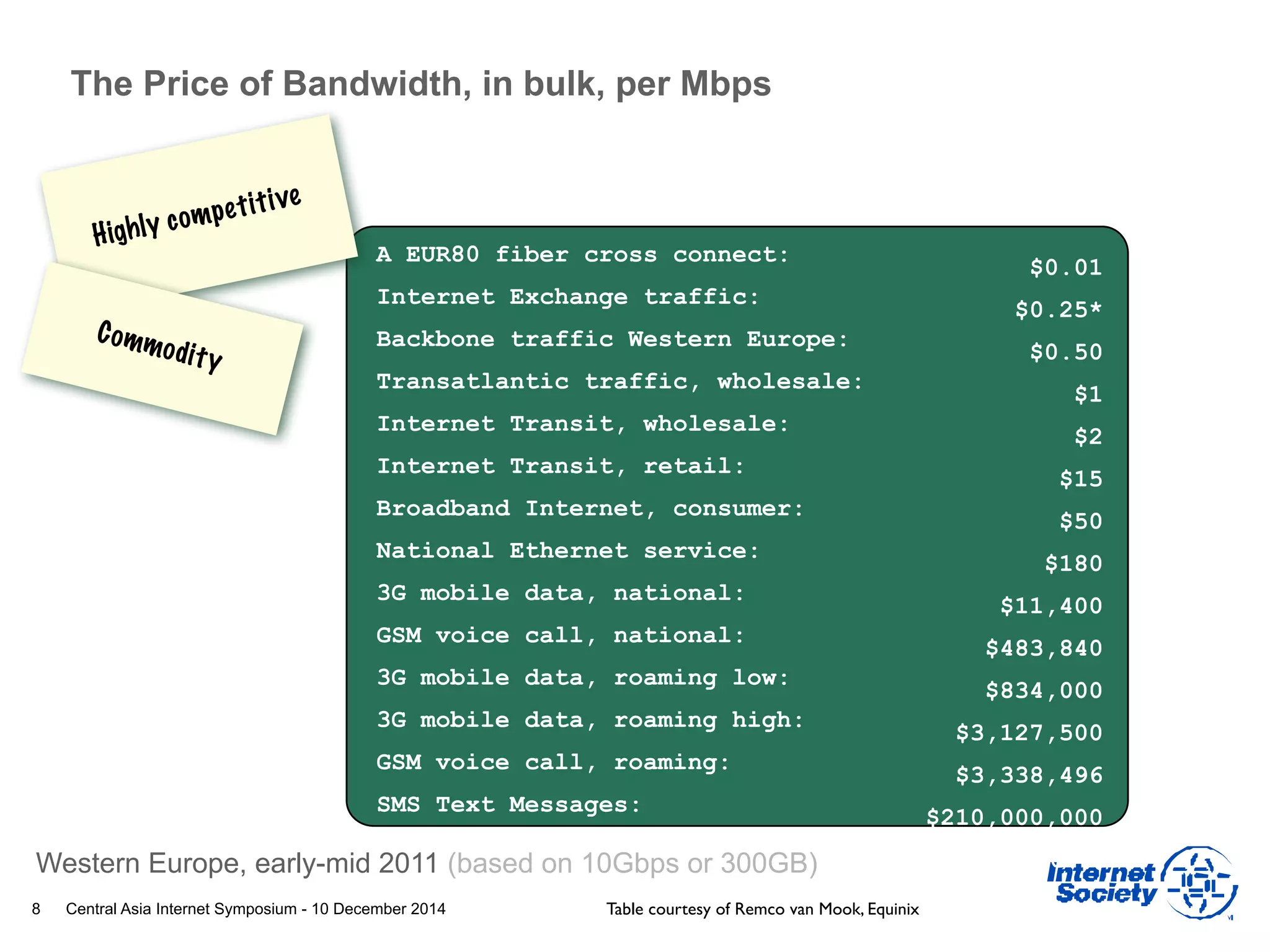
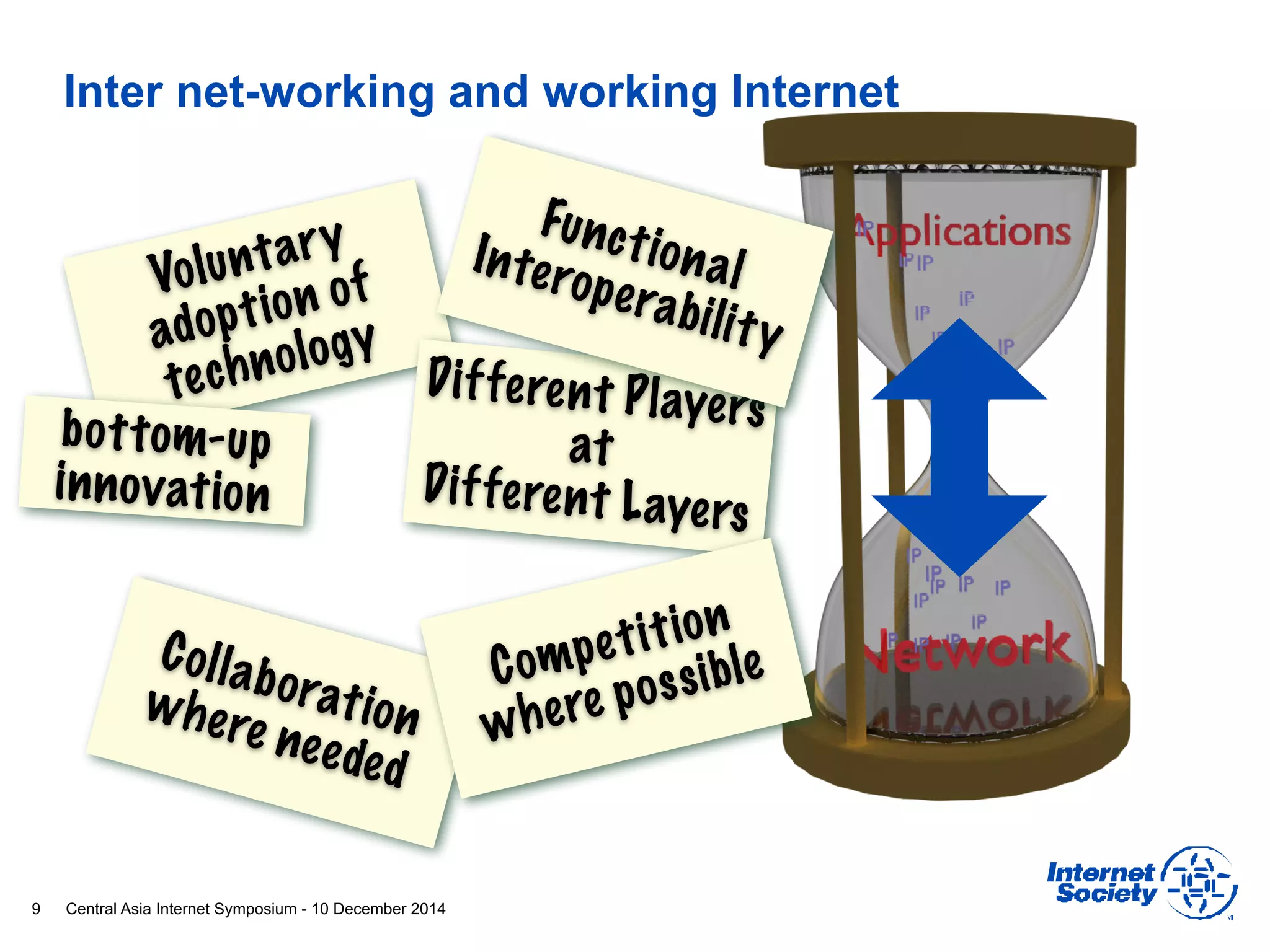
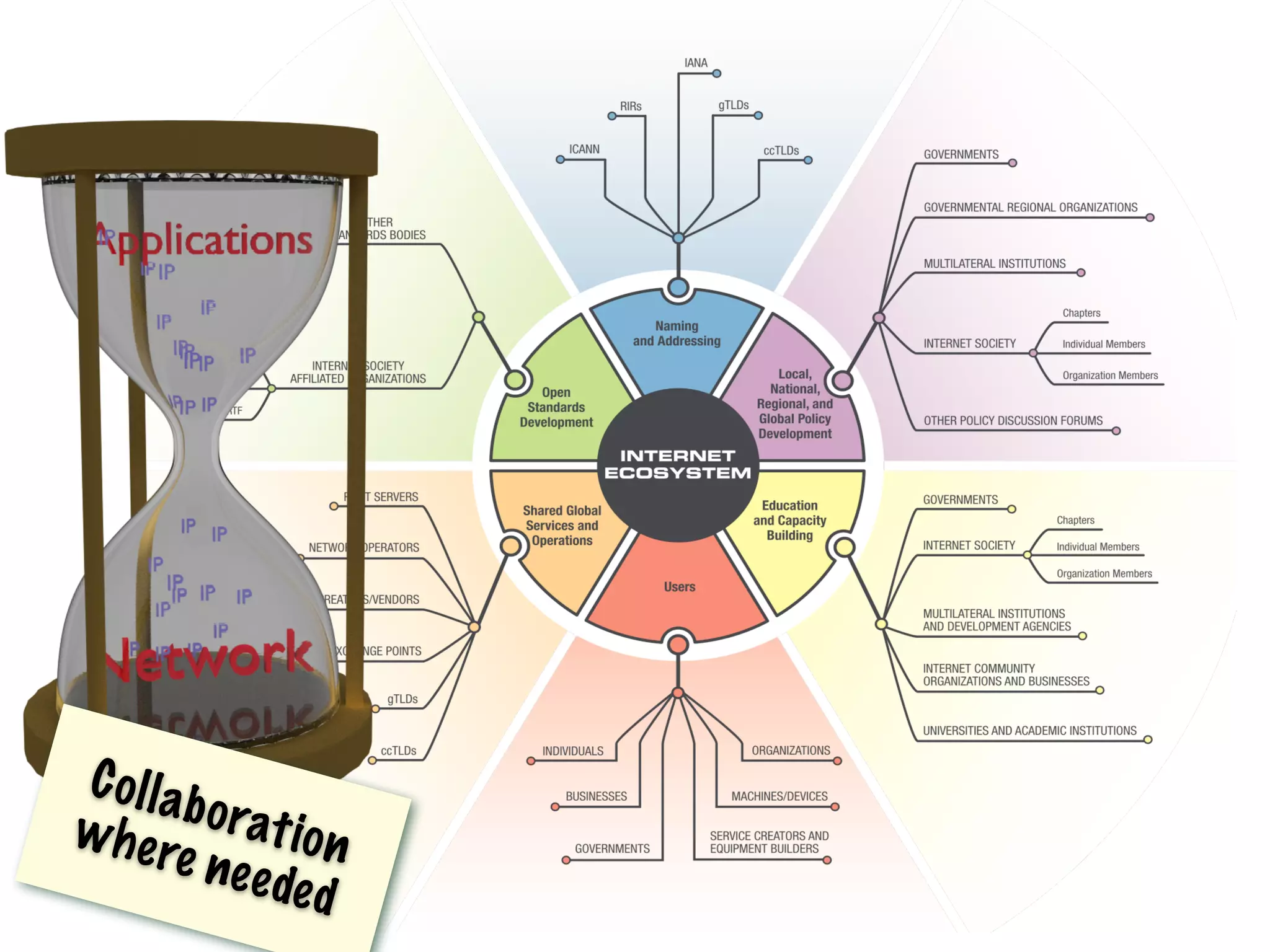
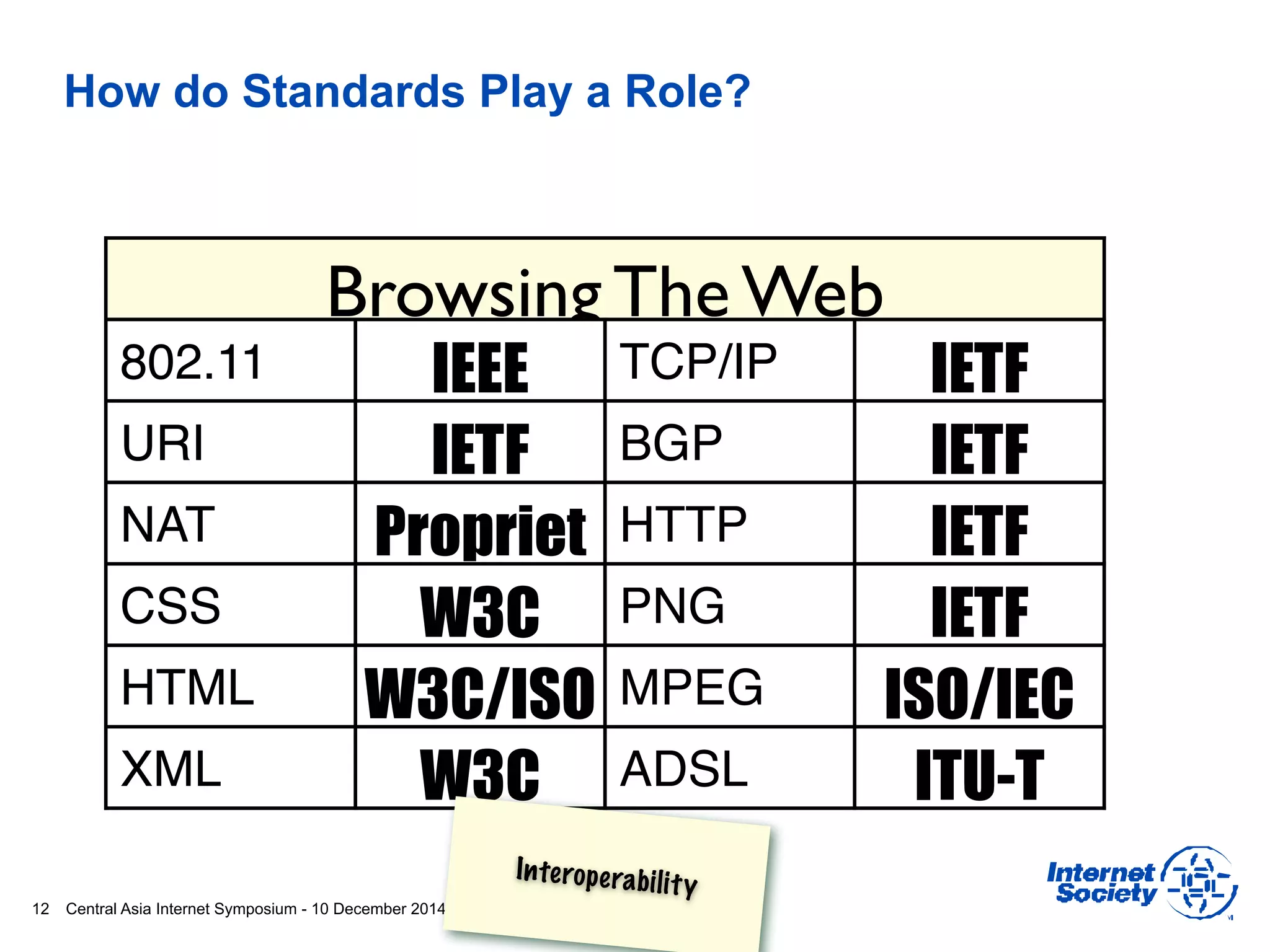
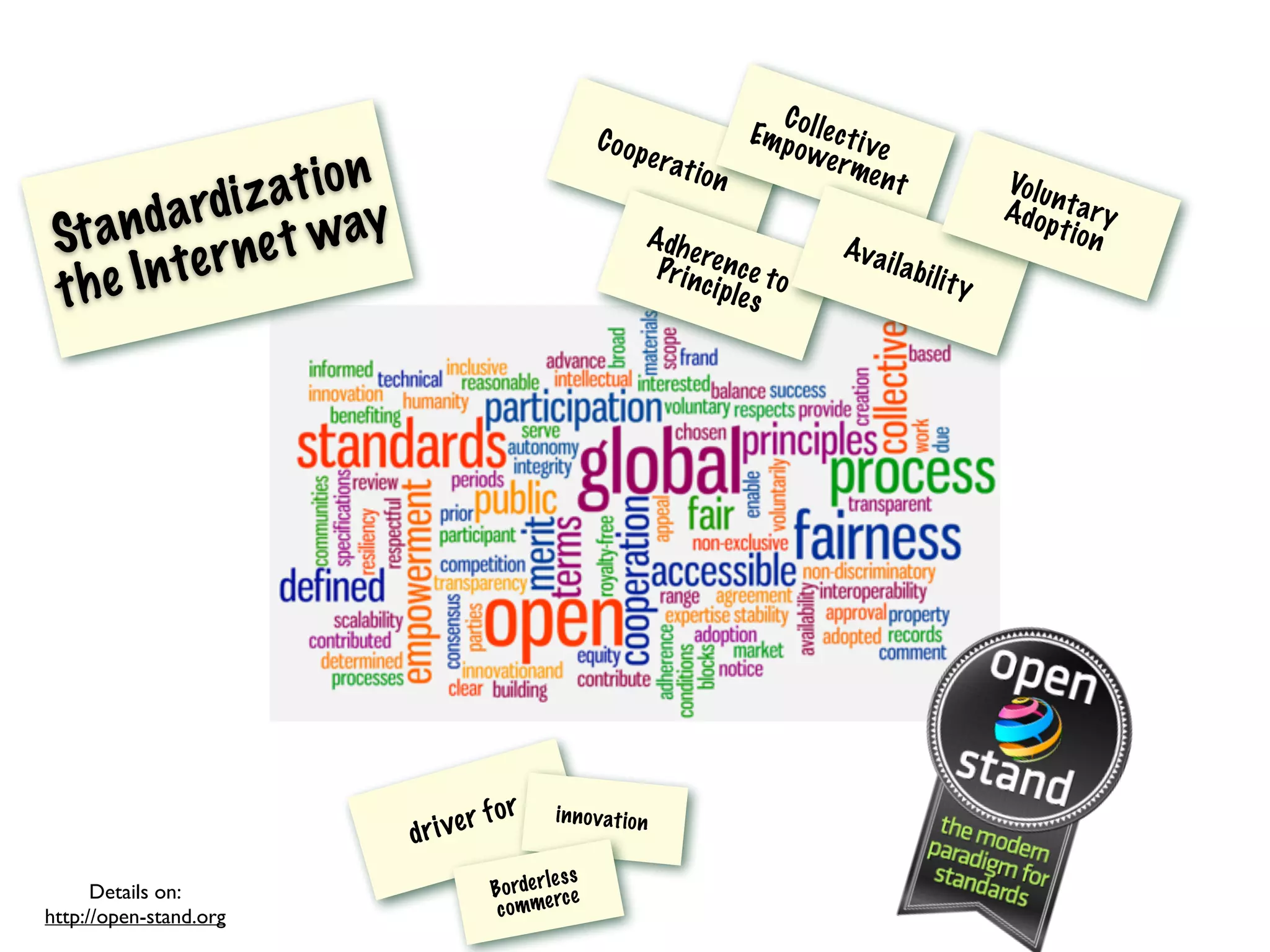
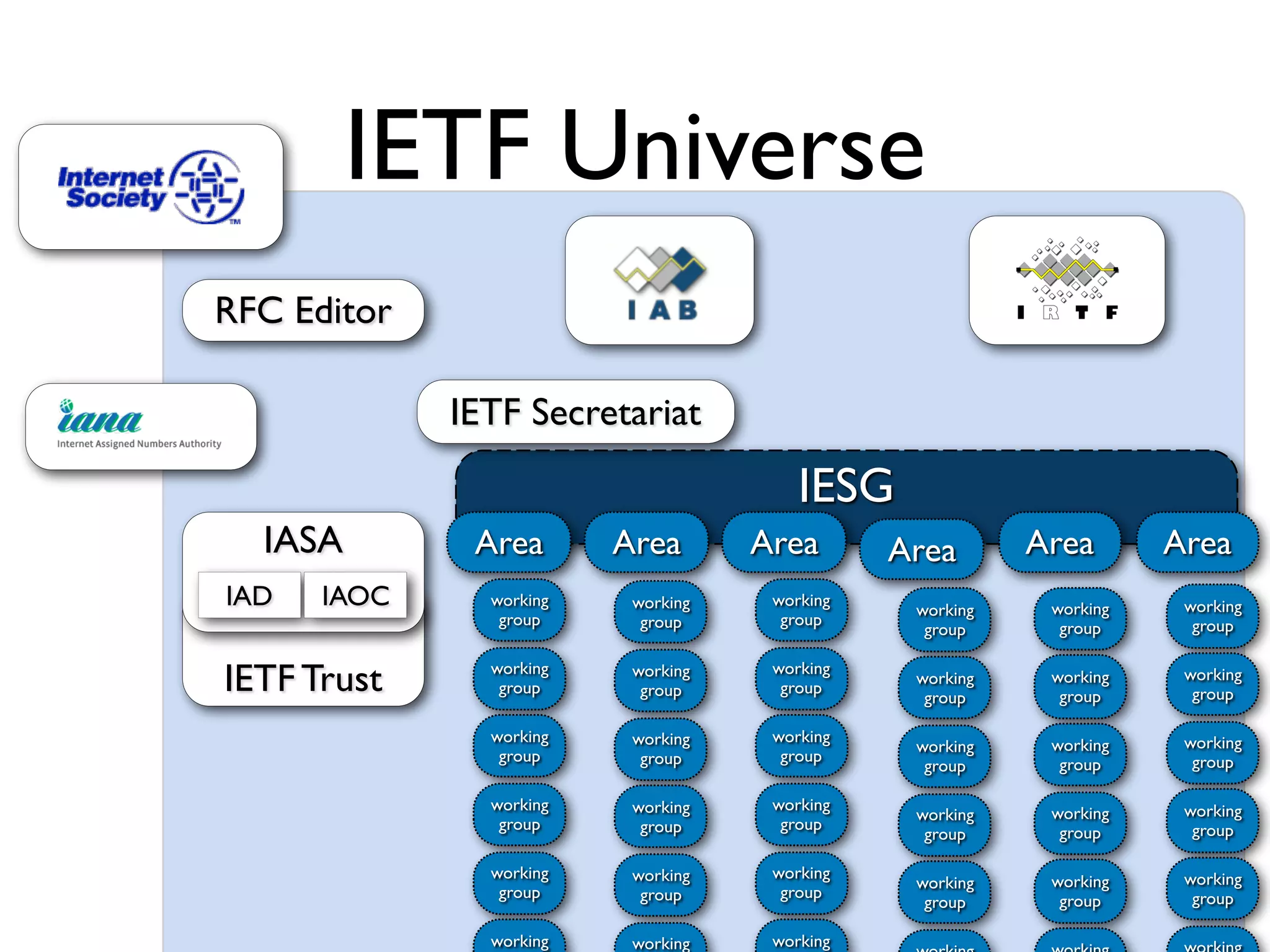
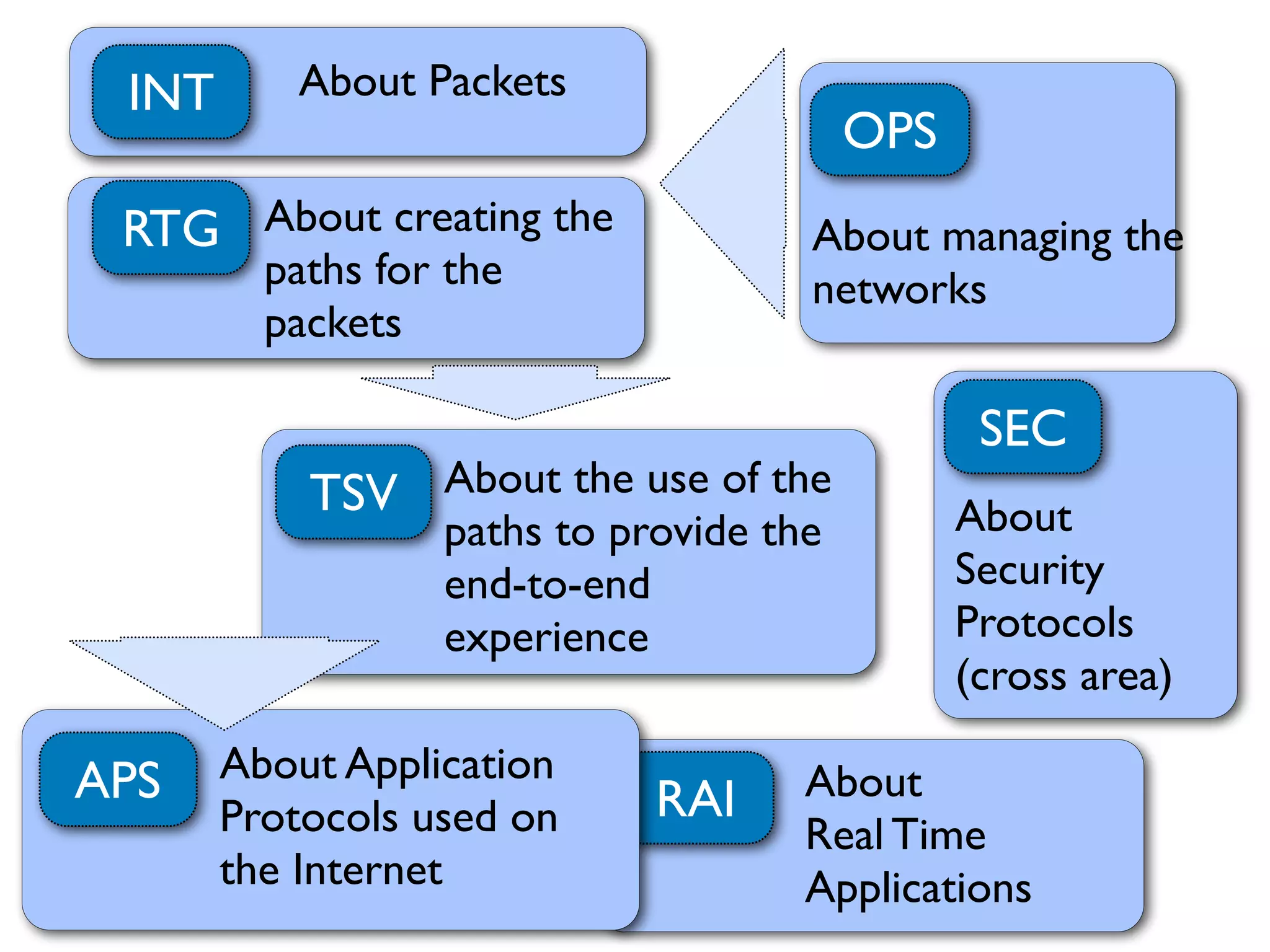
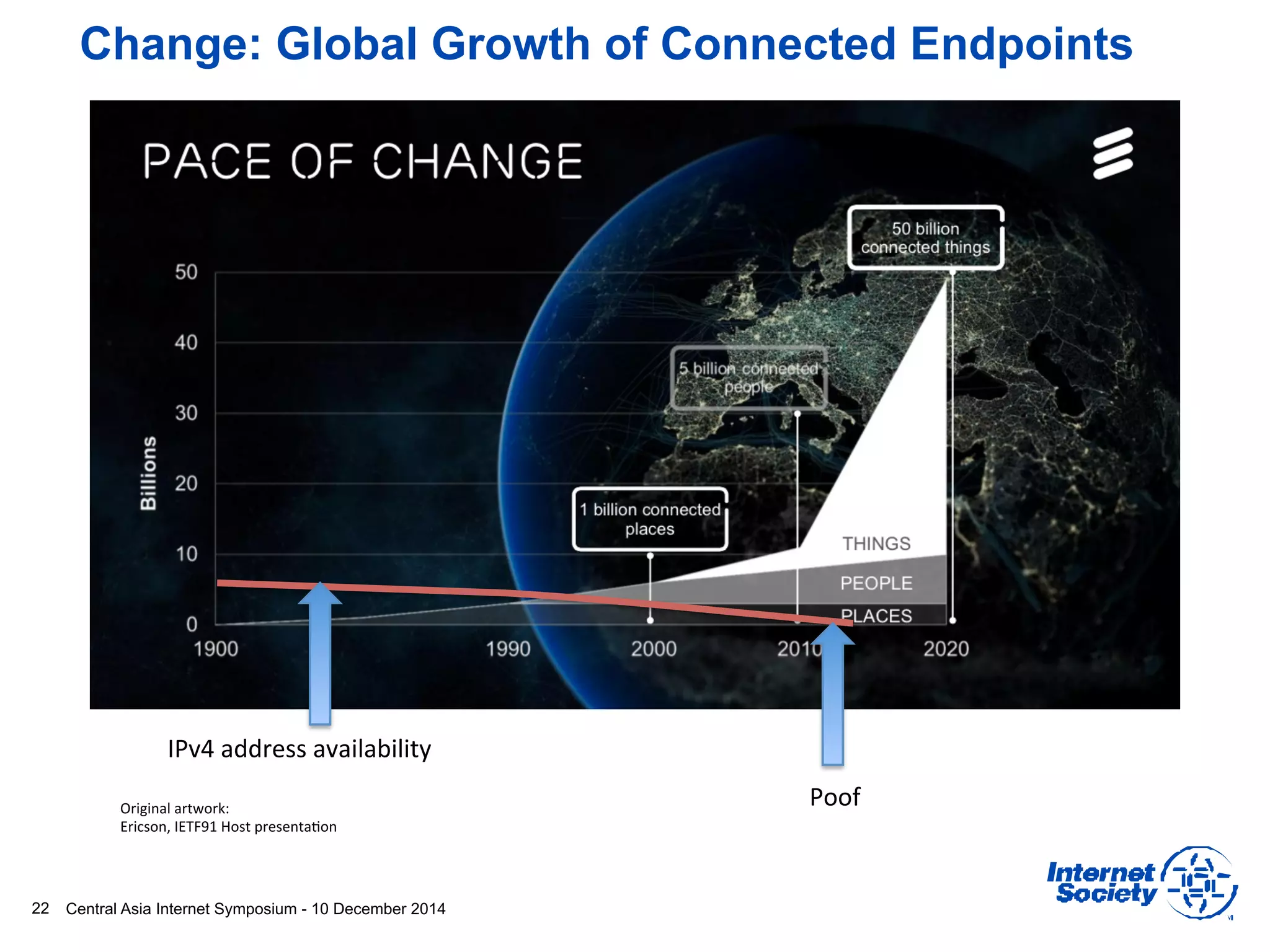
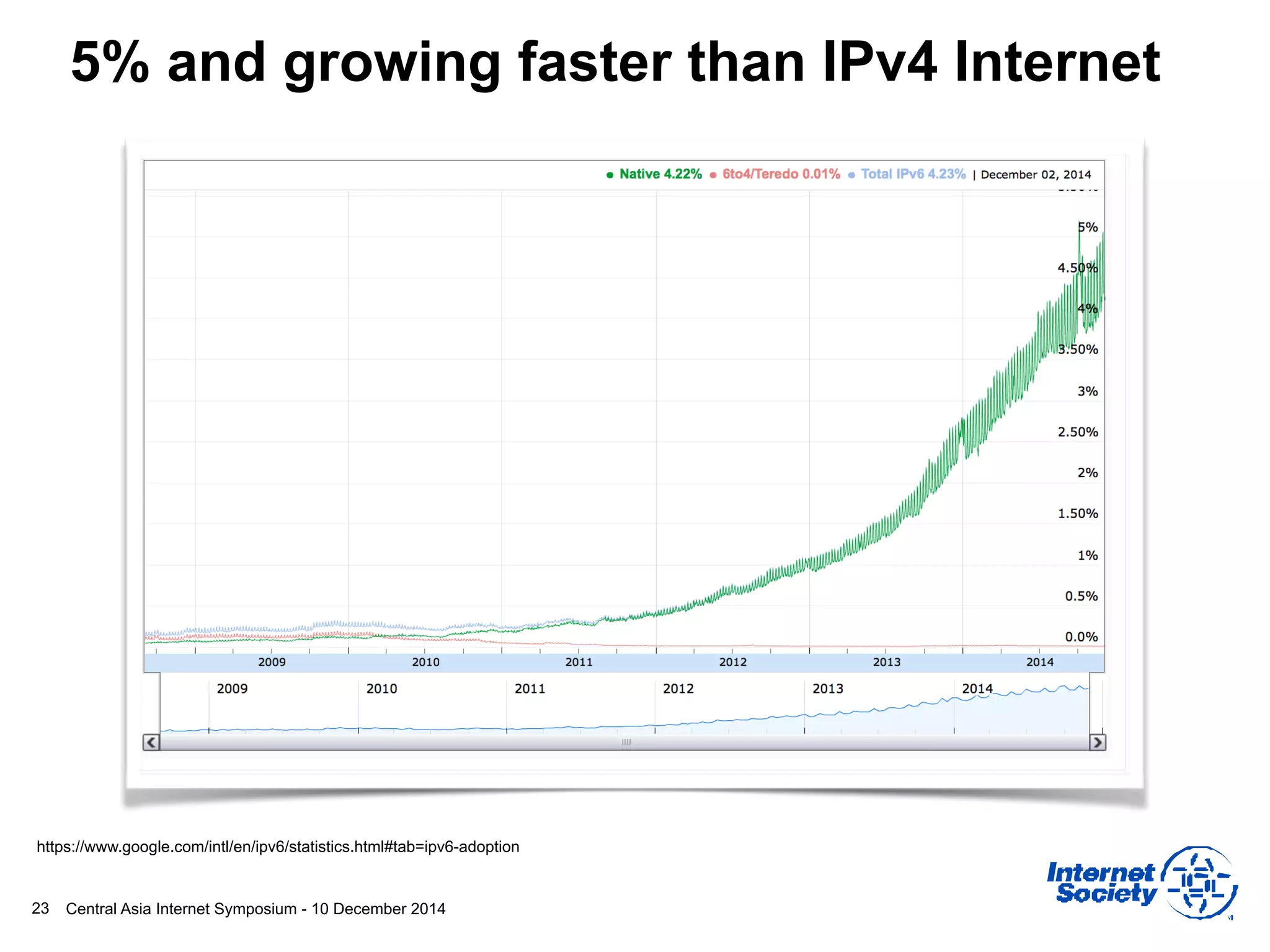
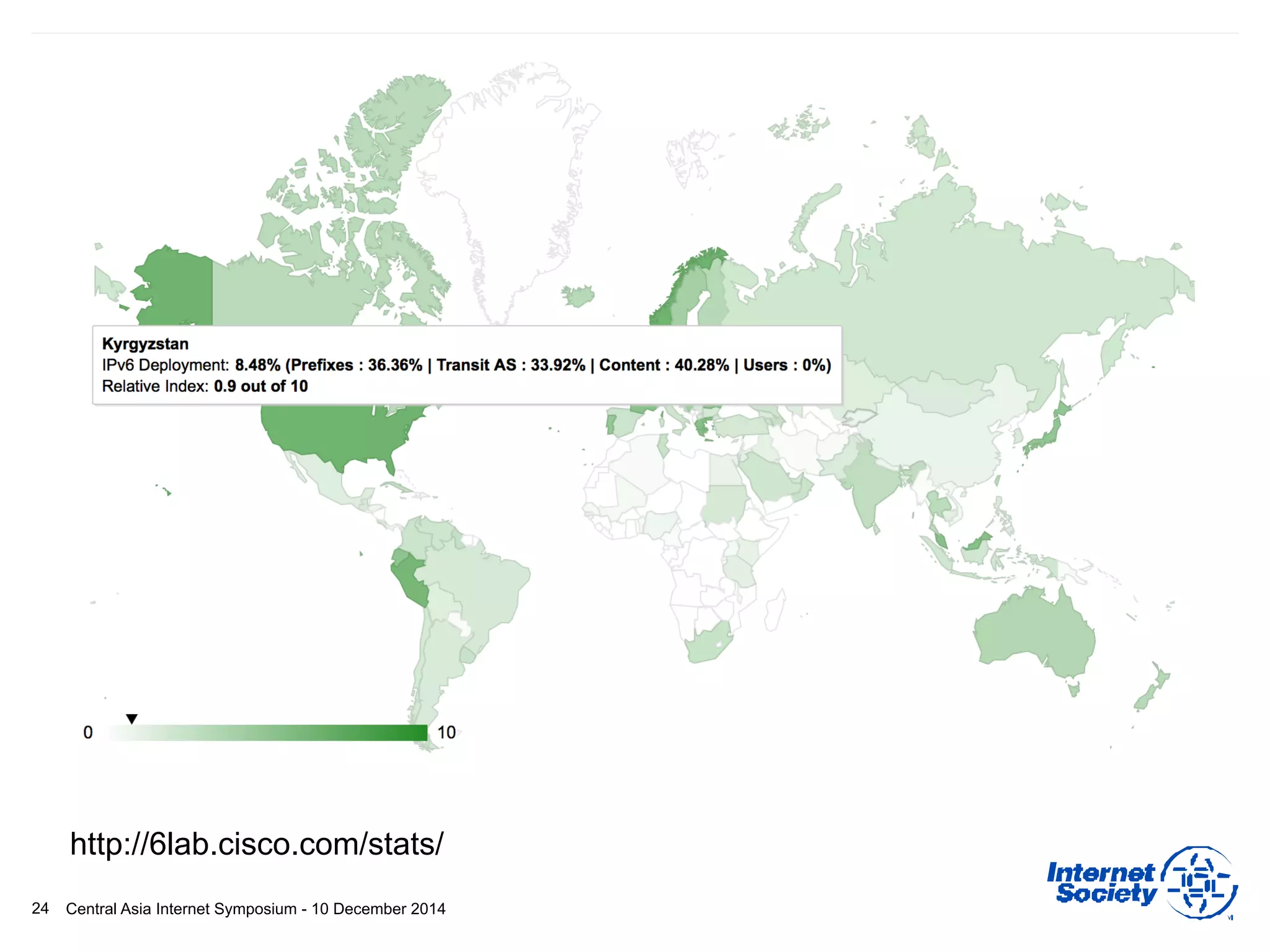
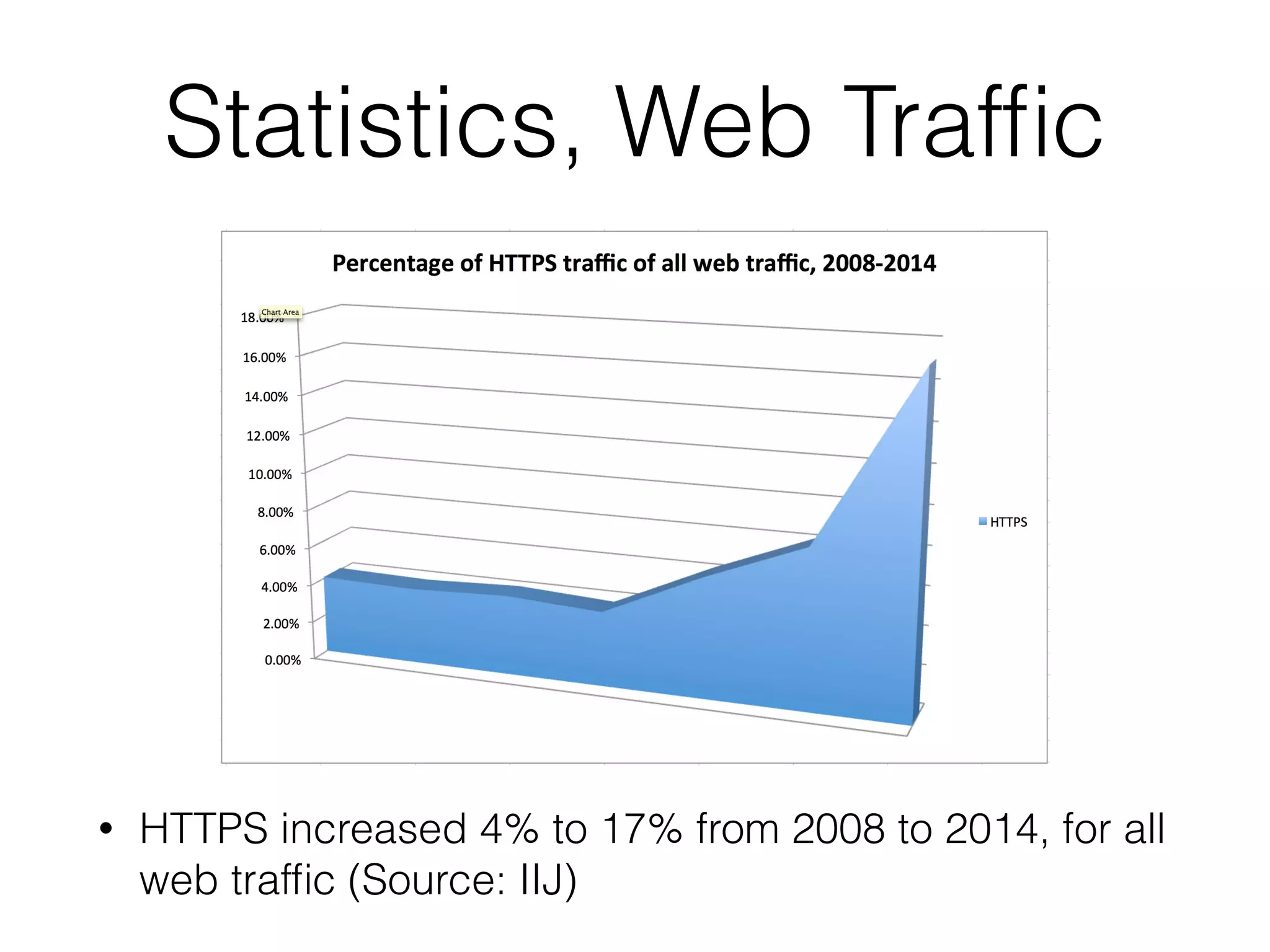
This document discusses different aspects of internet infrastructure and standards. It describes the layers of the internet including the application layer, network access layer, and IP layer. It discusses various players that operate networks and exchange IP packets. It provides an overview of the Internet Engineering Task Force (IETF) and some of the key technologies they develop including IPv6, encryption, and protocols like BGP, SIP, and HTTP. It emphasizes how cooperation, open standards, and voluntary adoption have contributed to the growth and success of the internet.