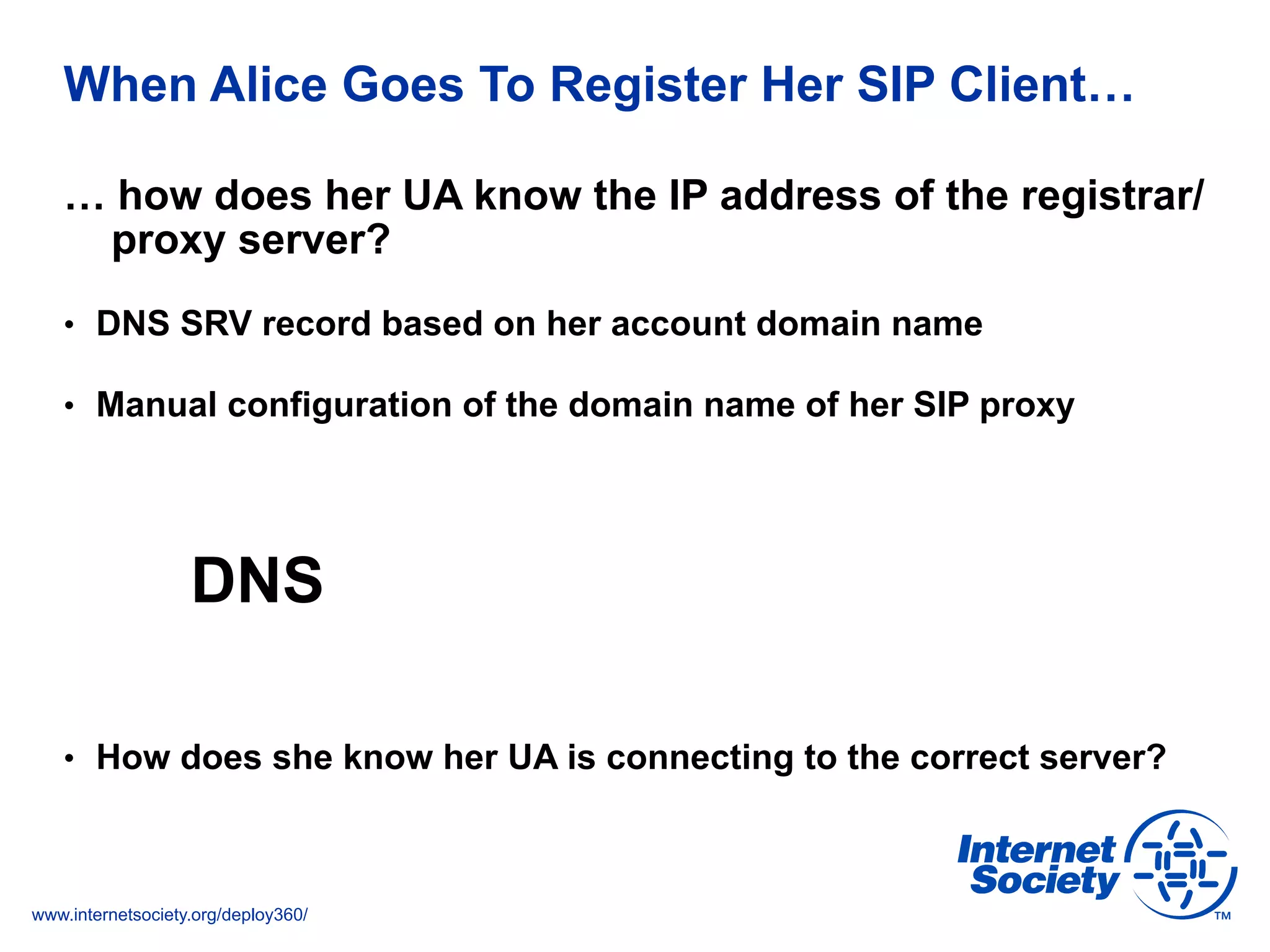
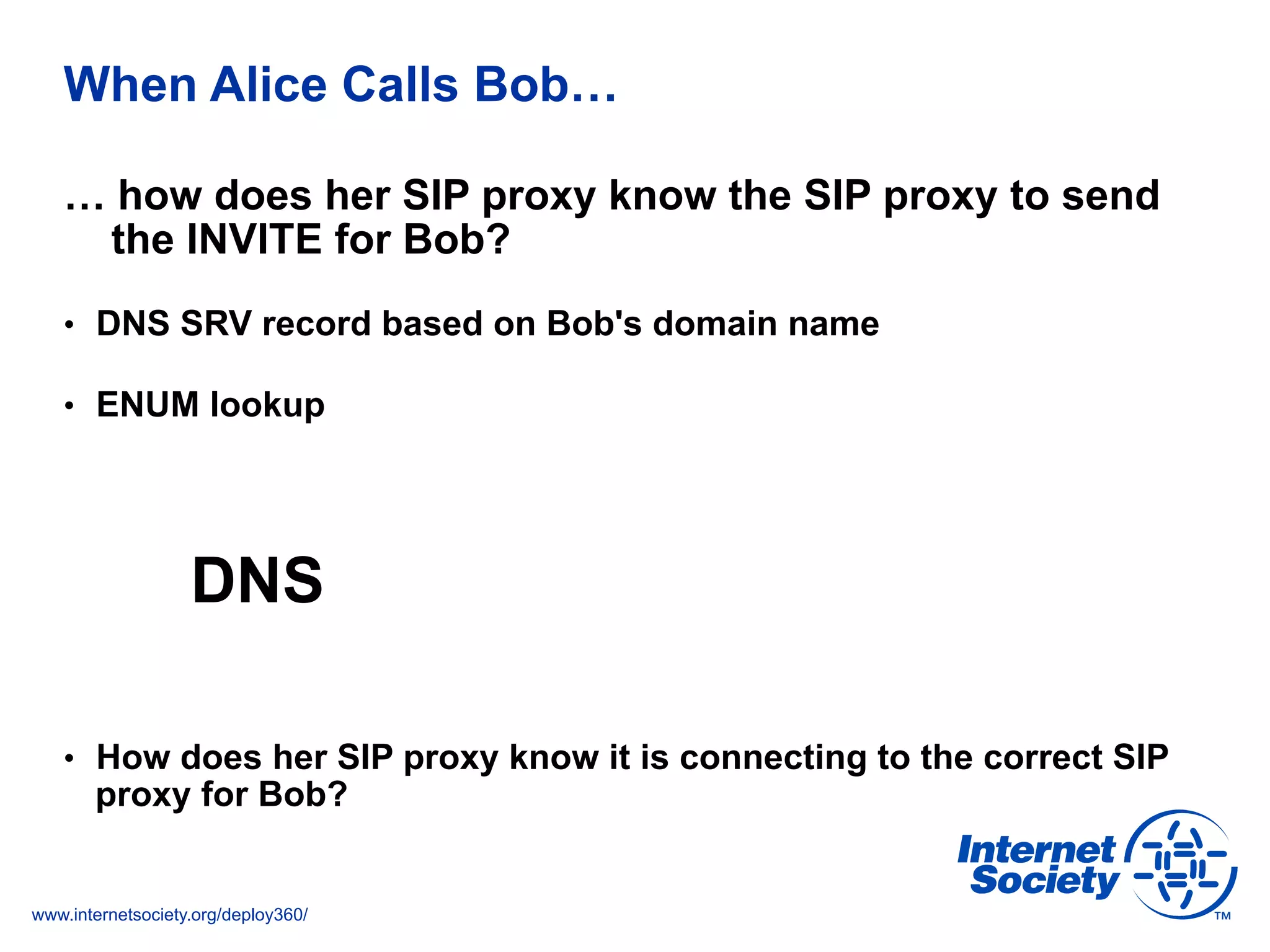
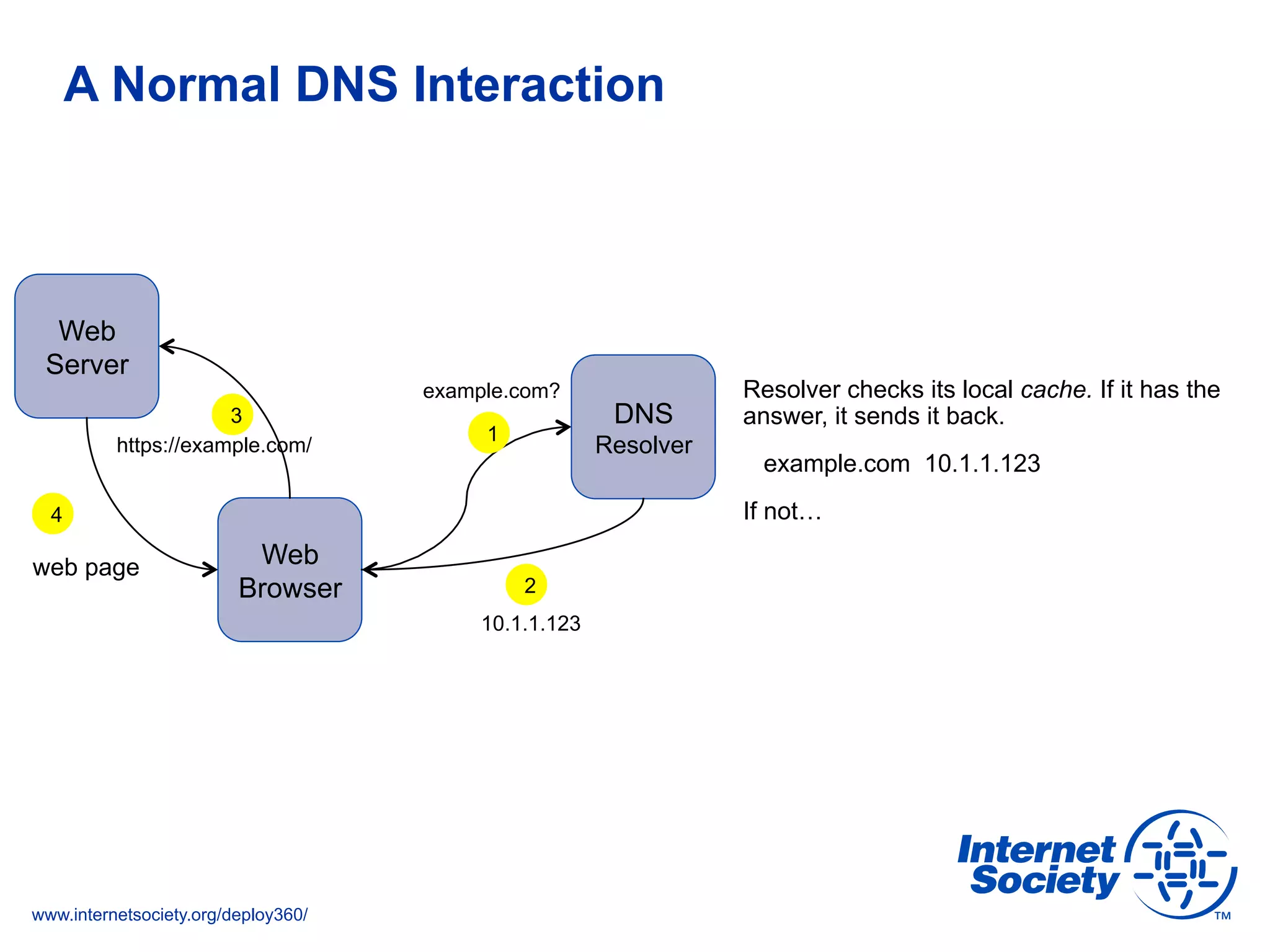
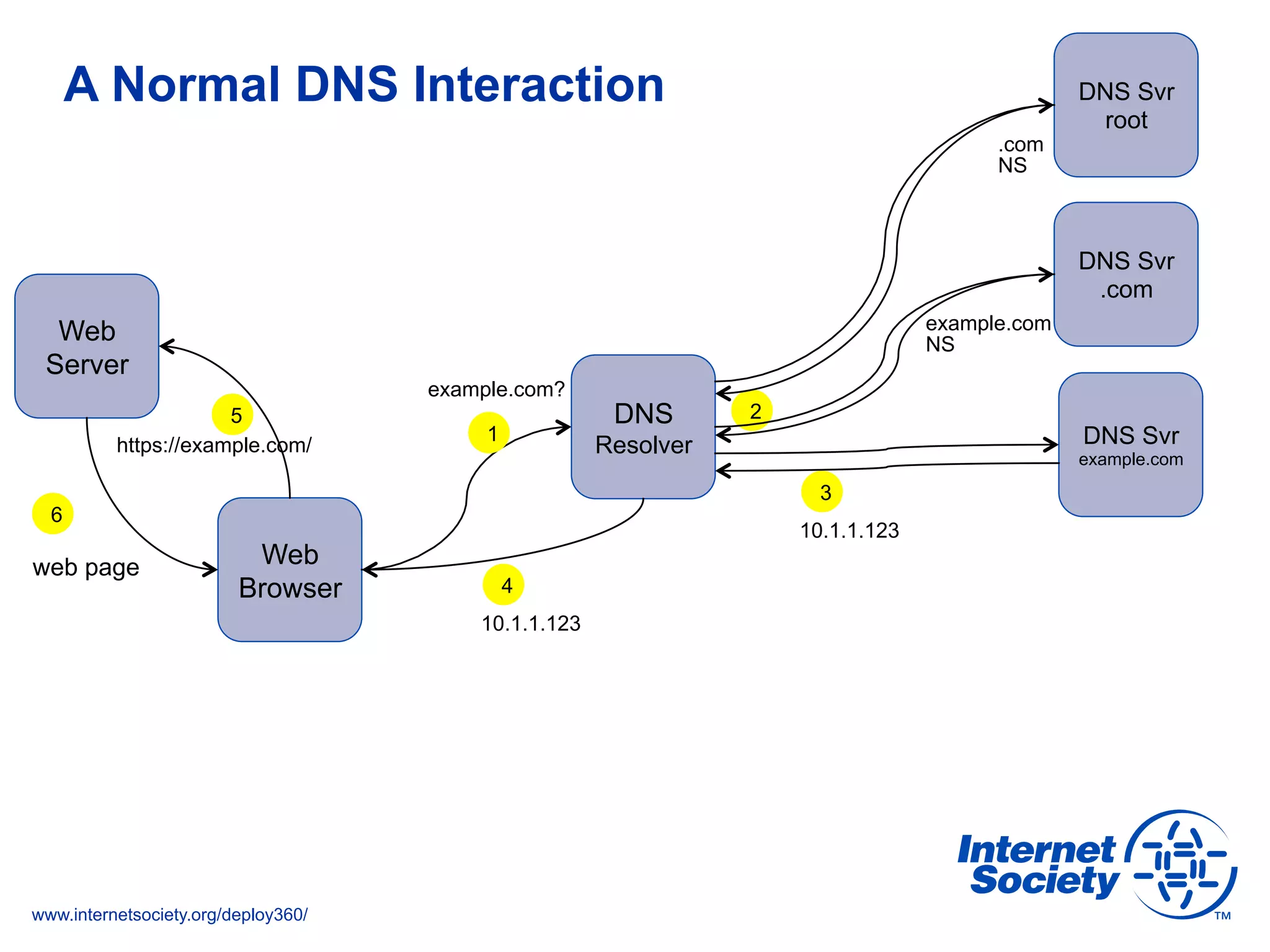
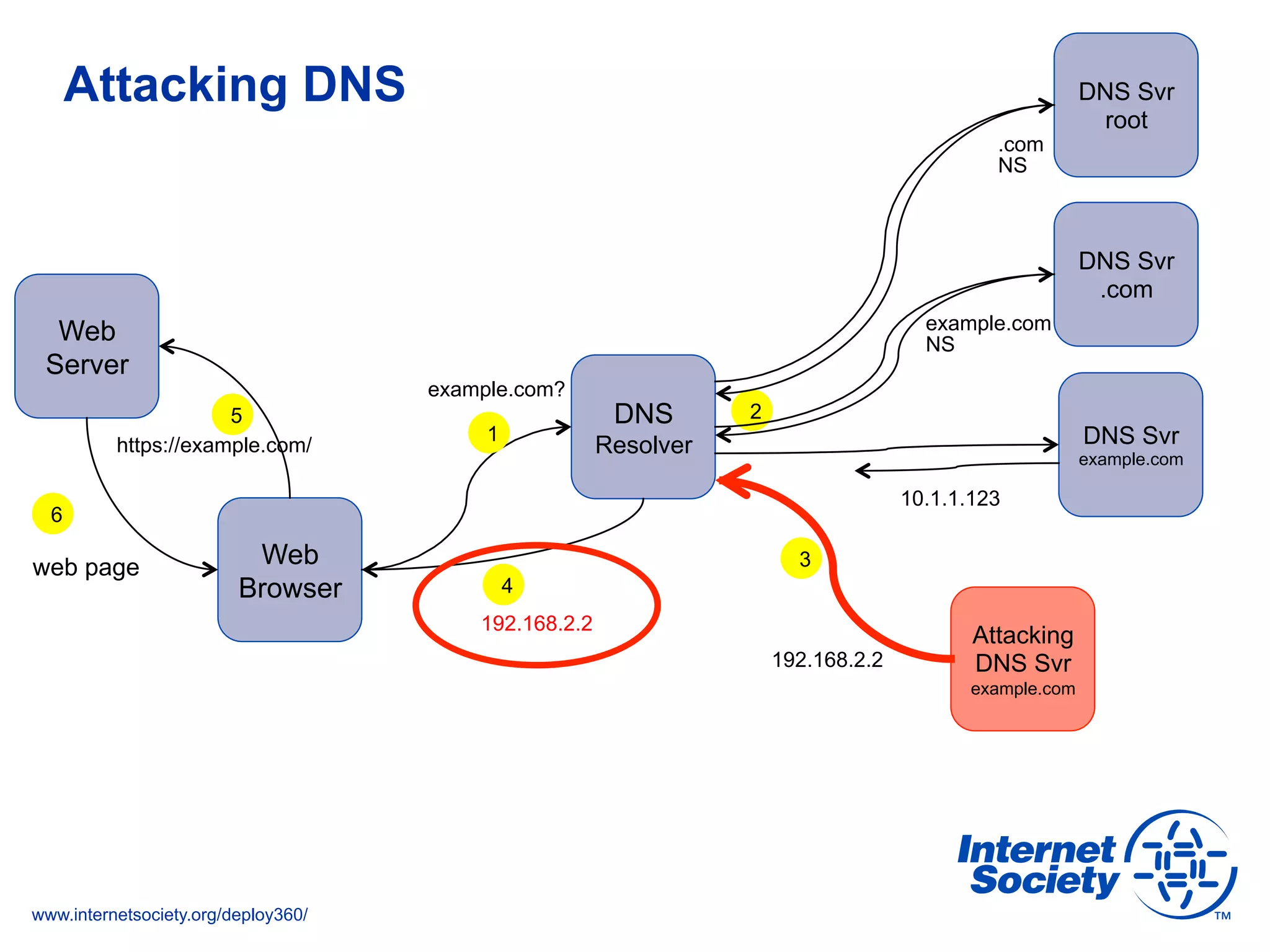
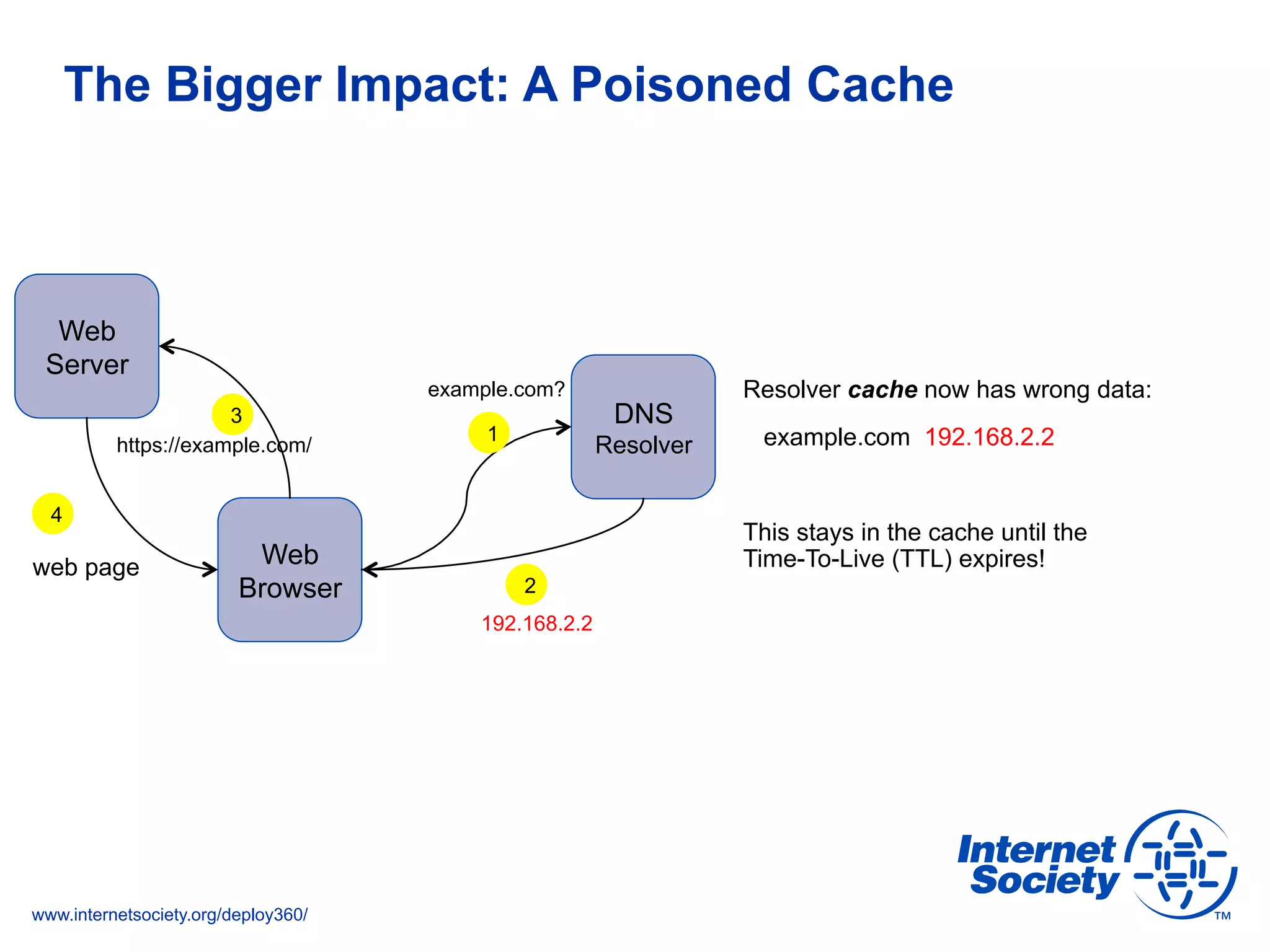
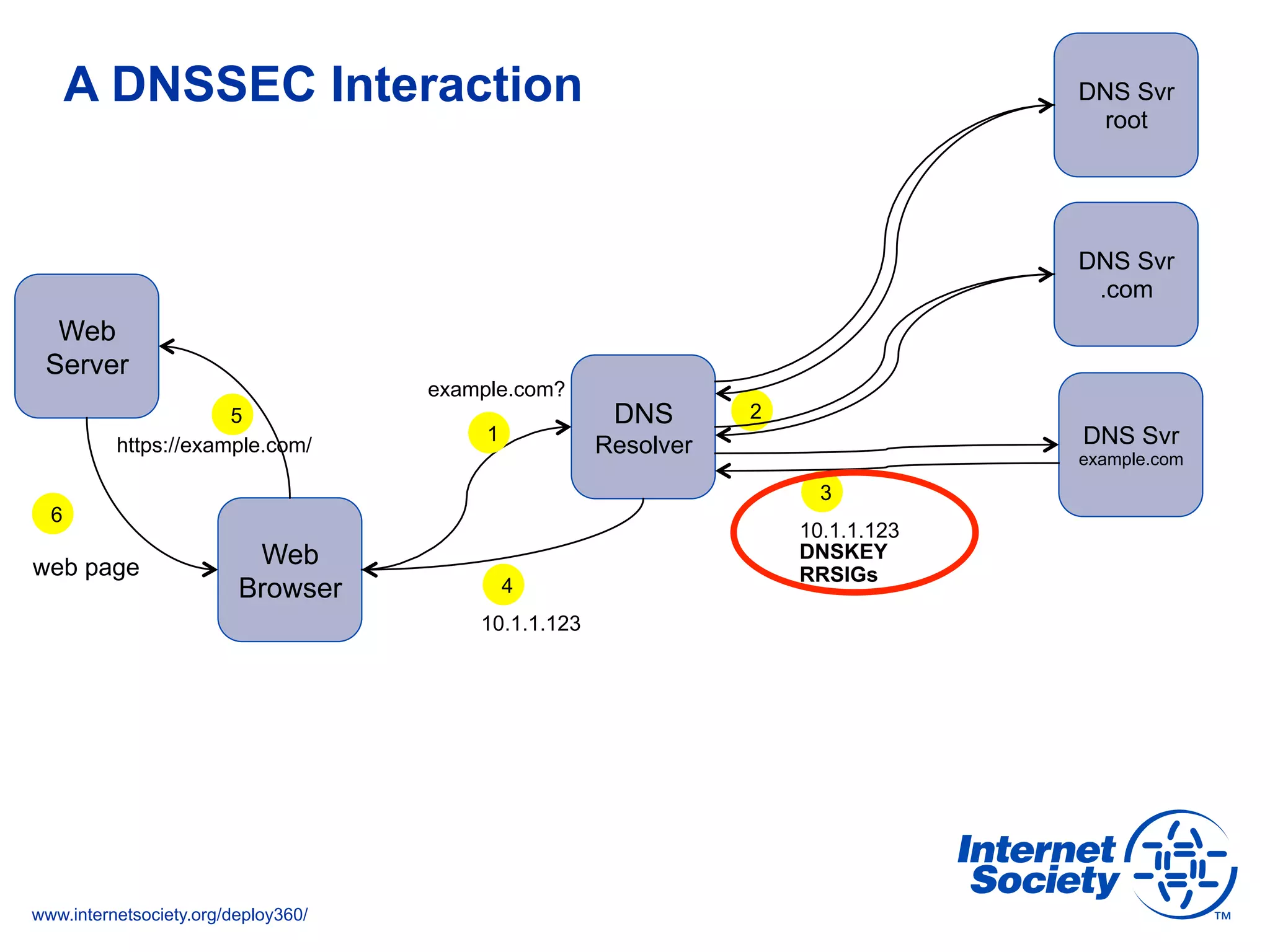
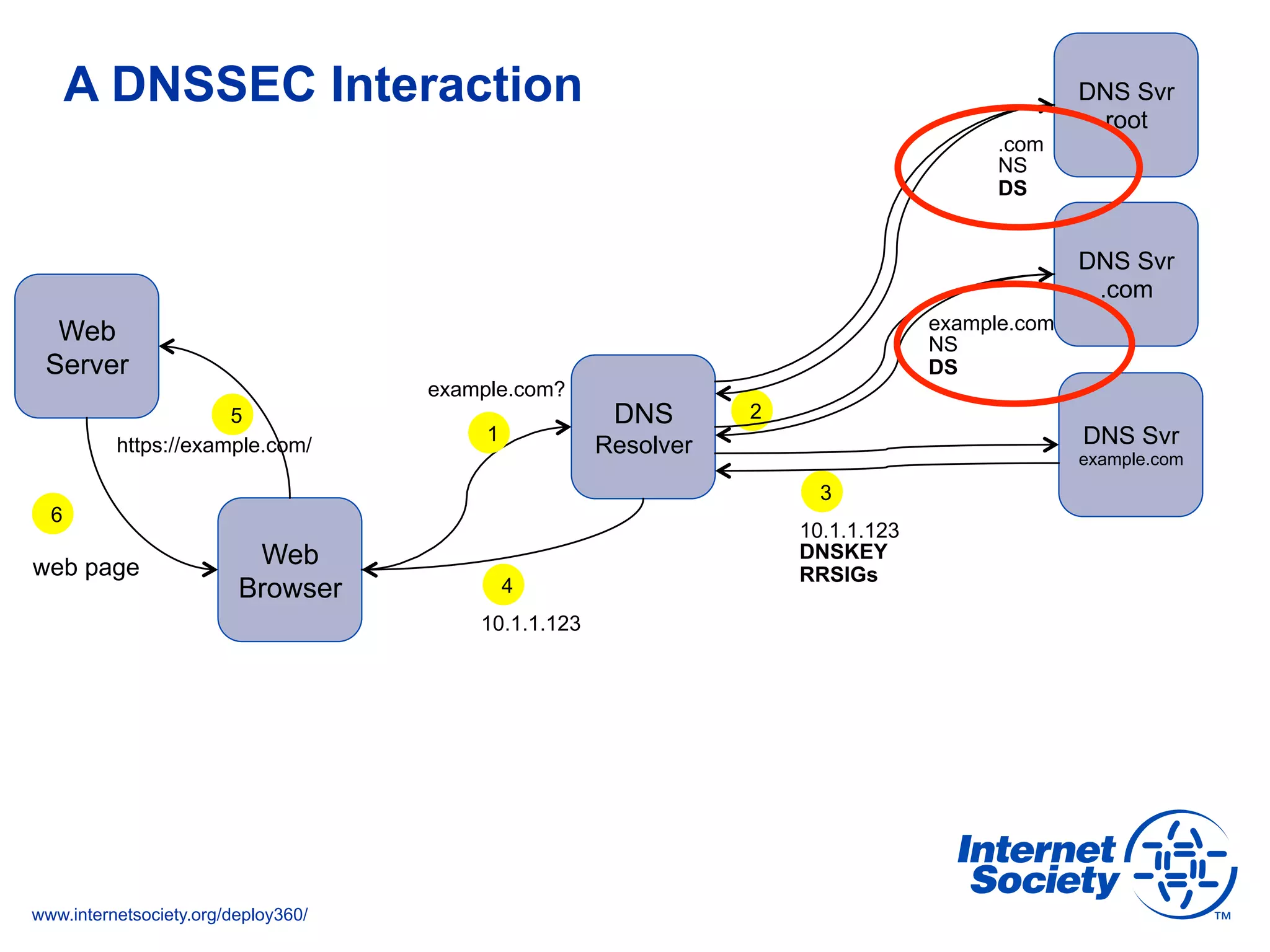
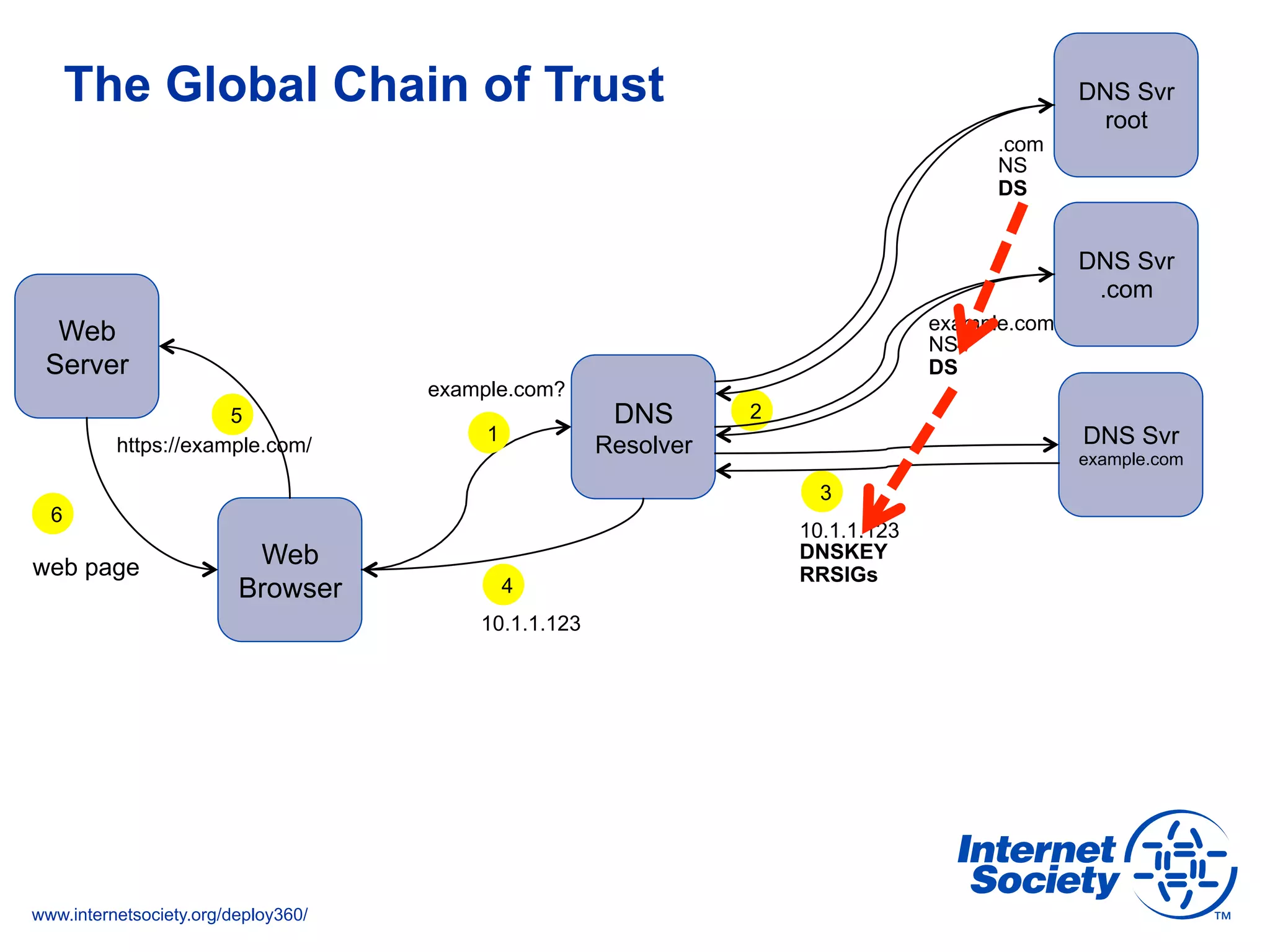
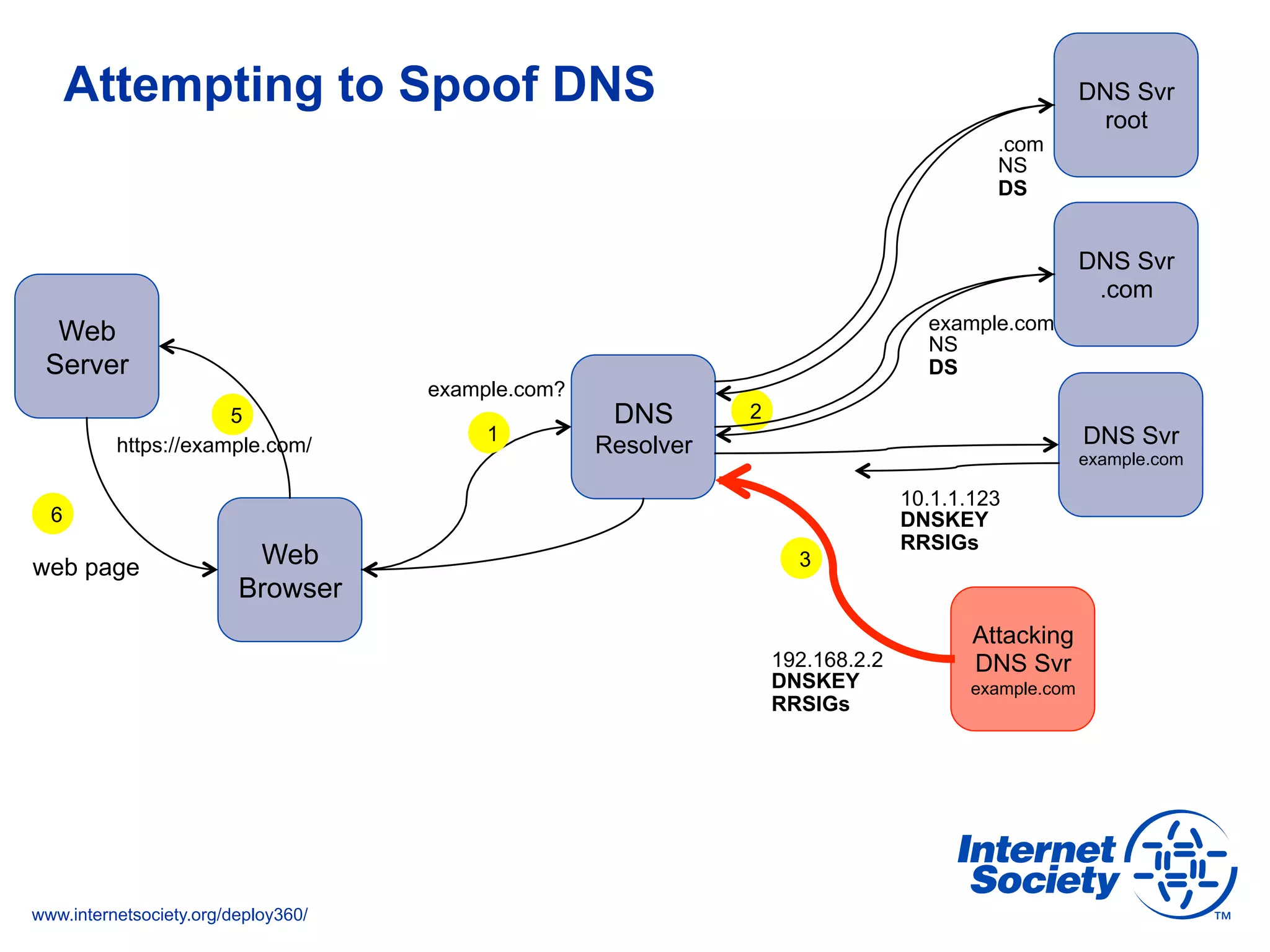
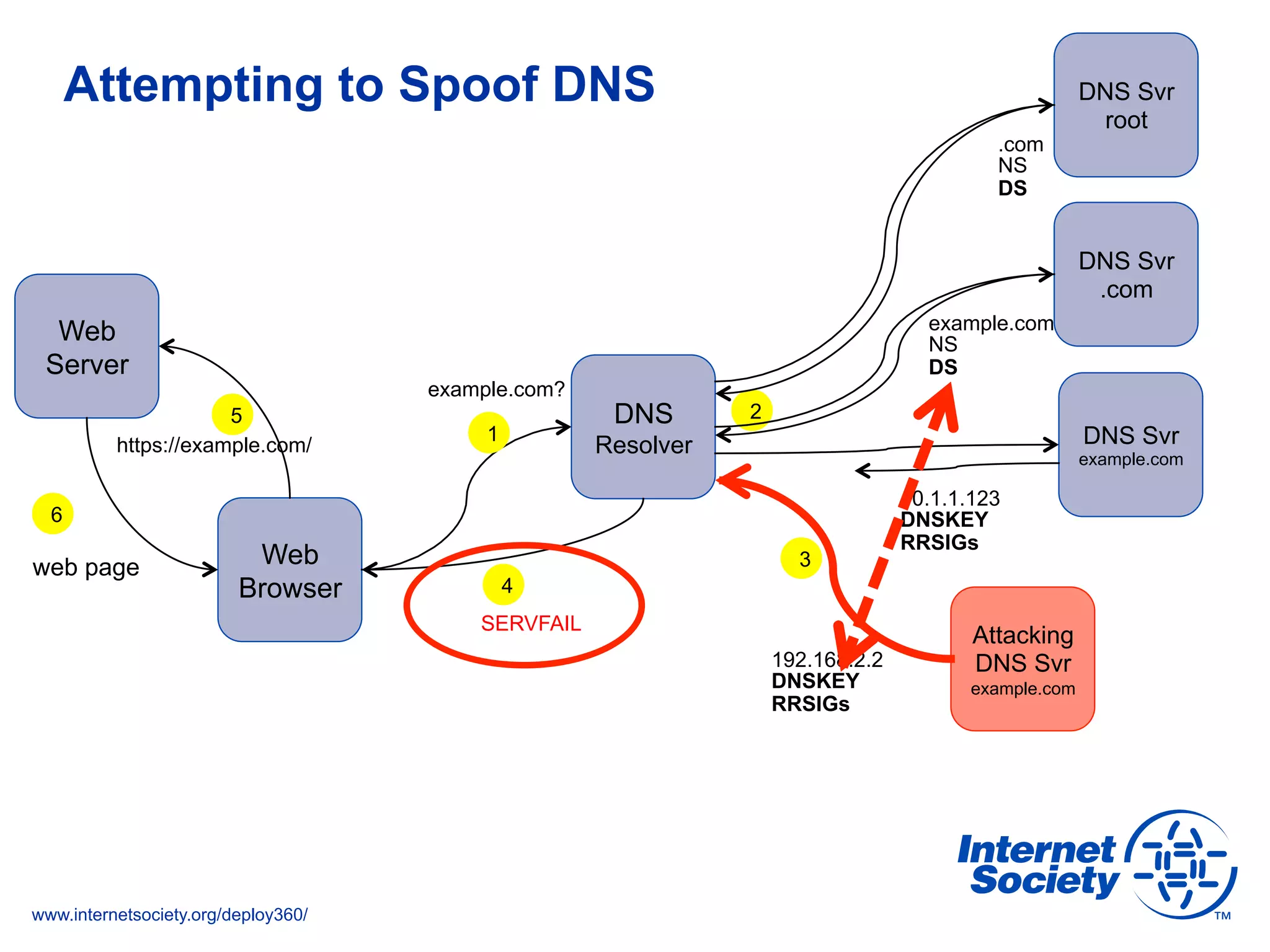
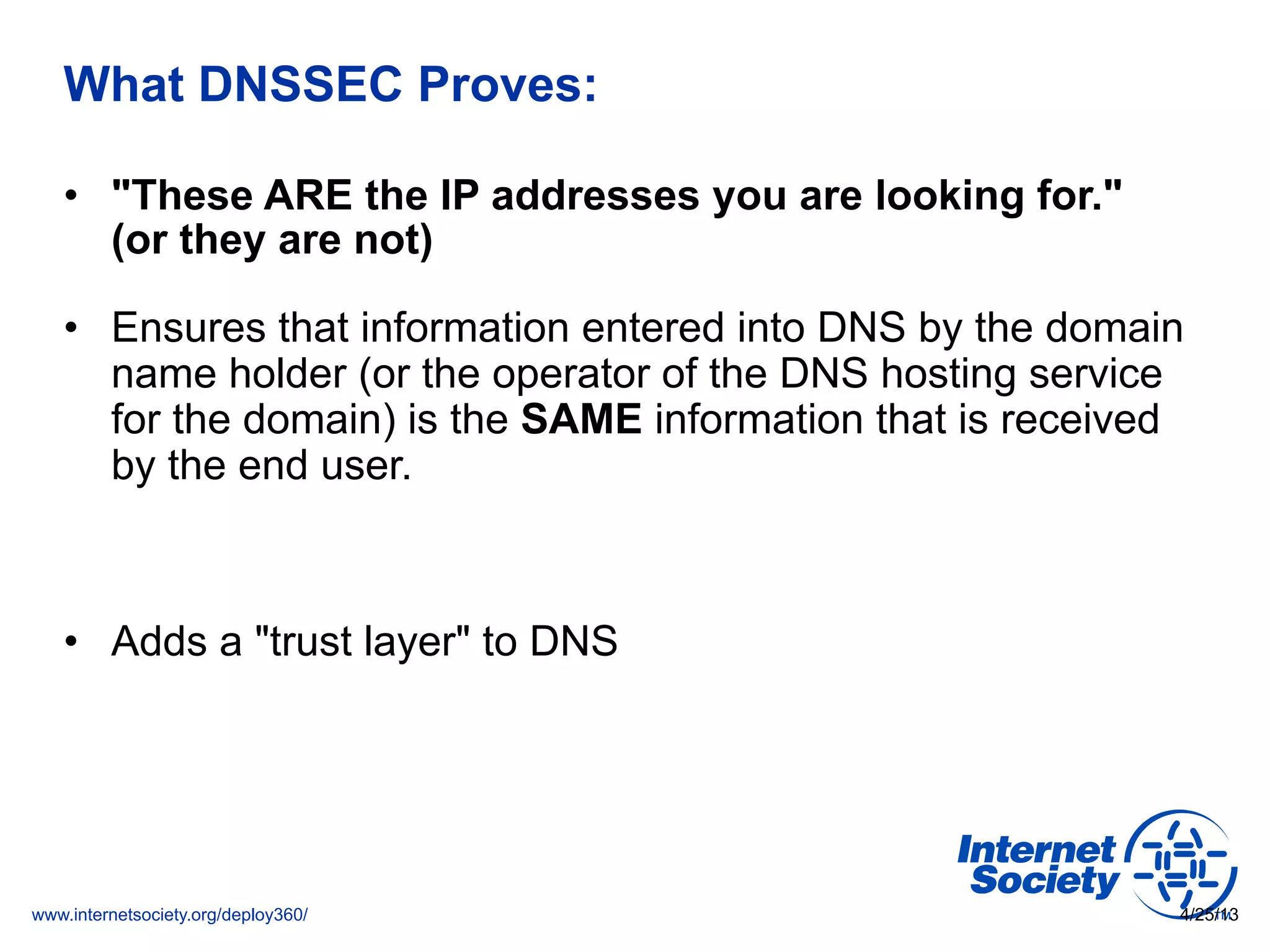
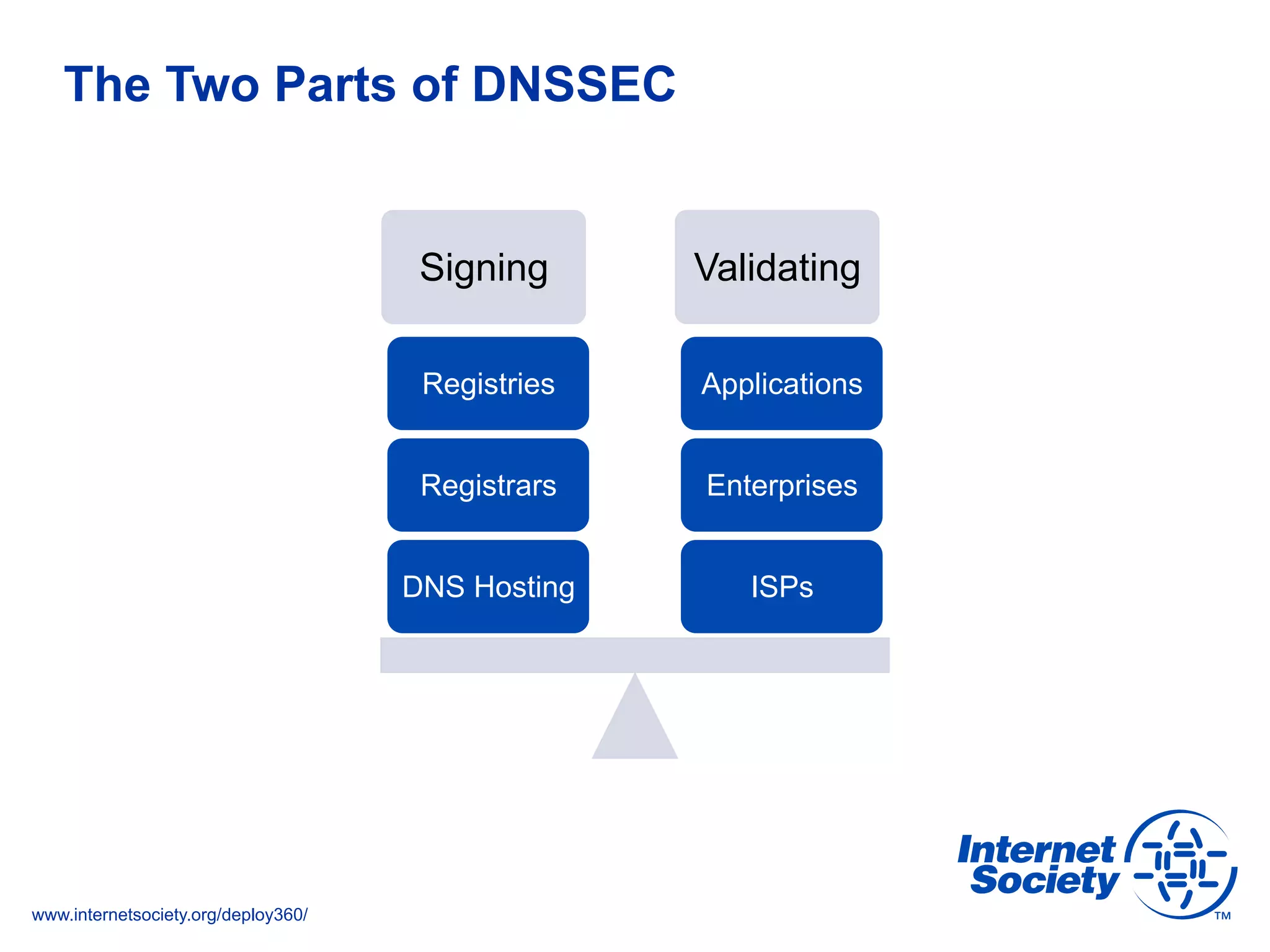
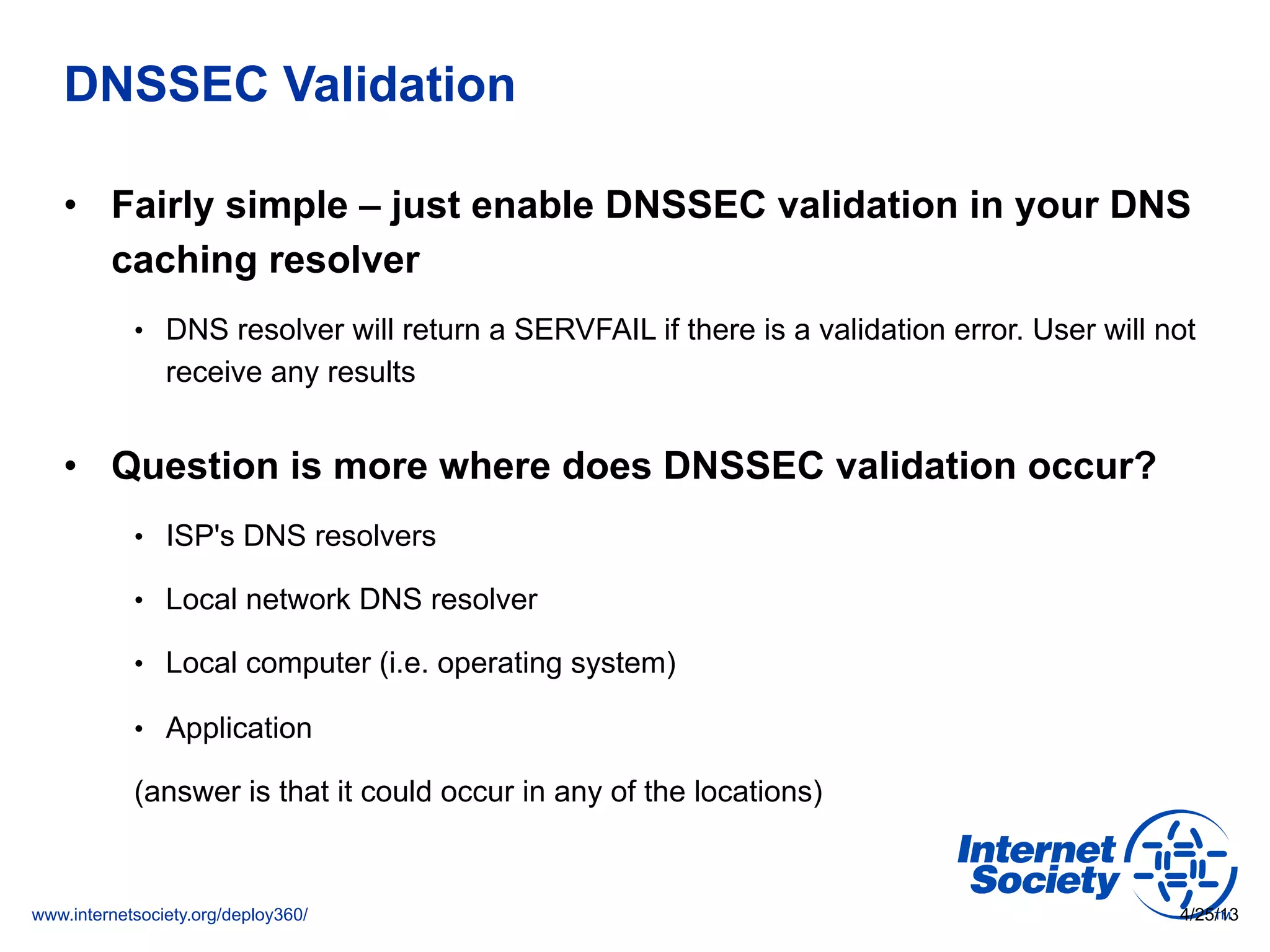
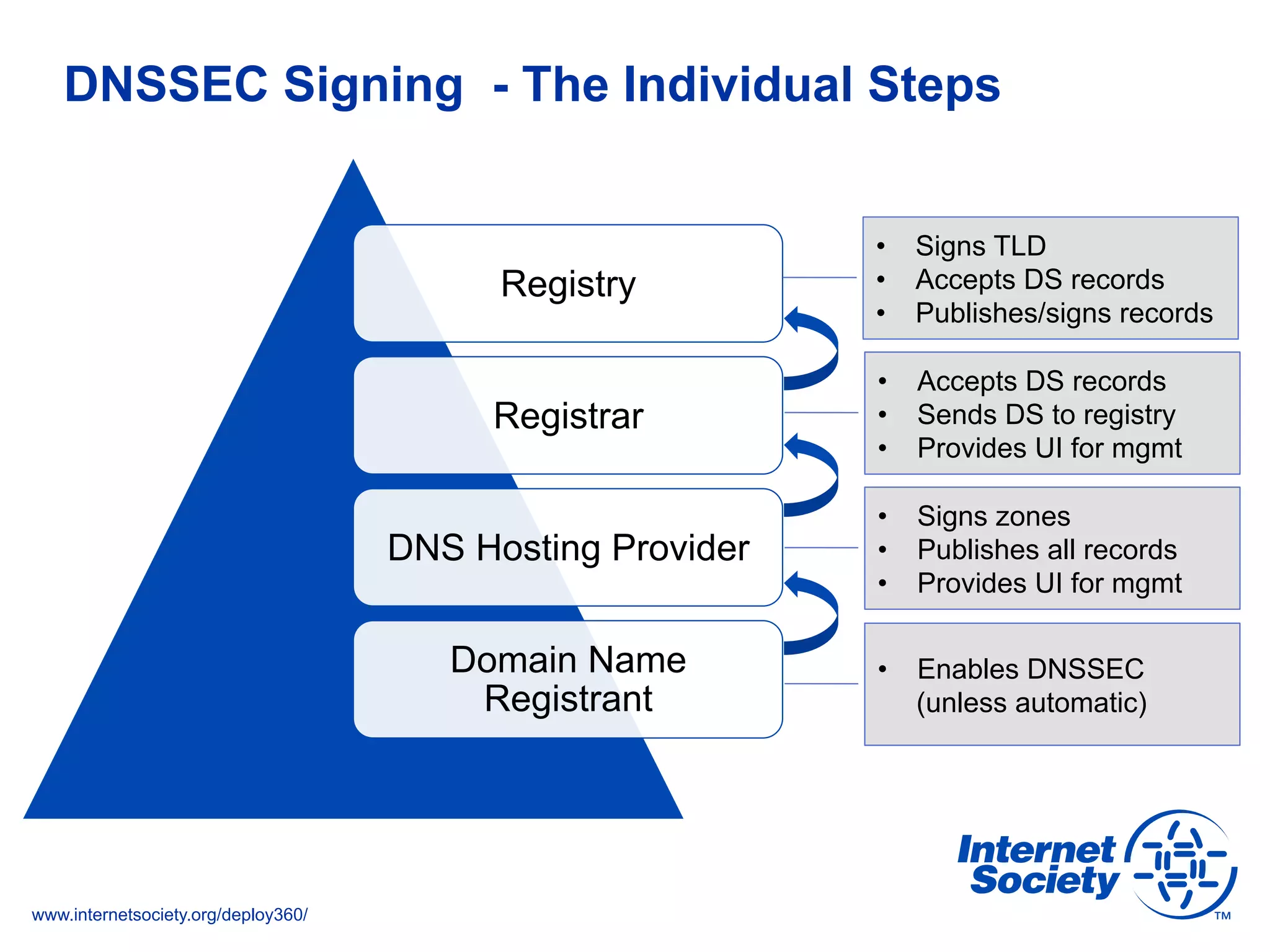
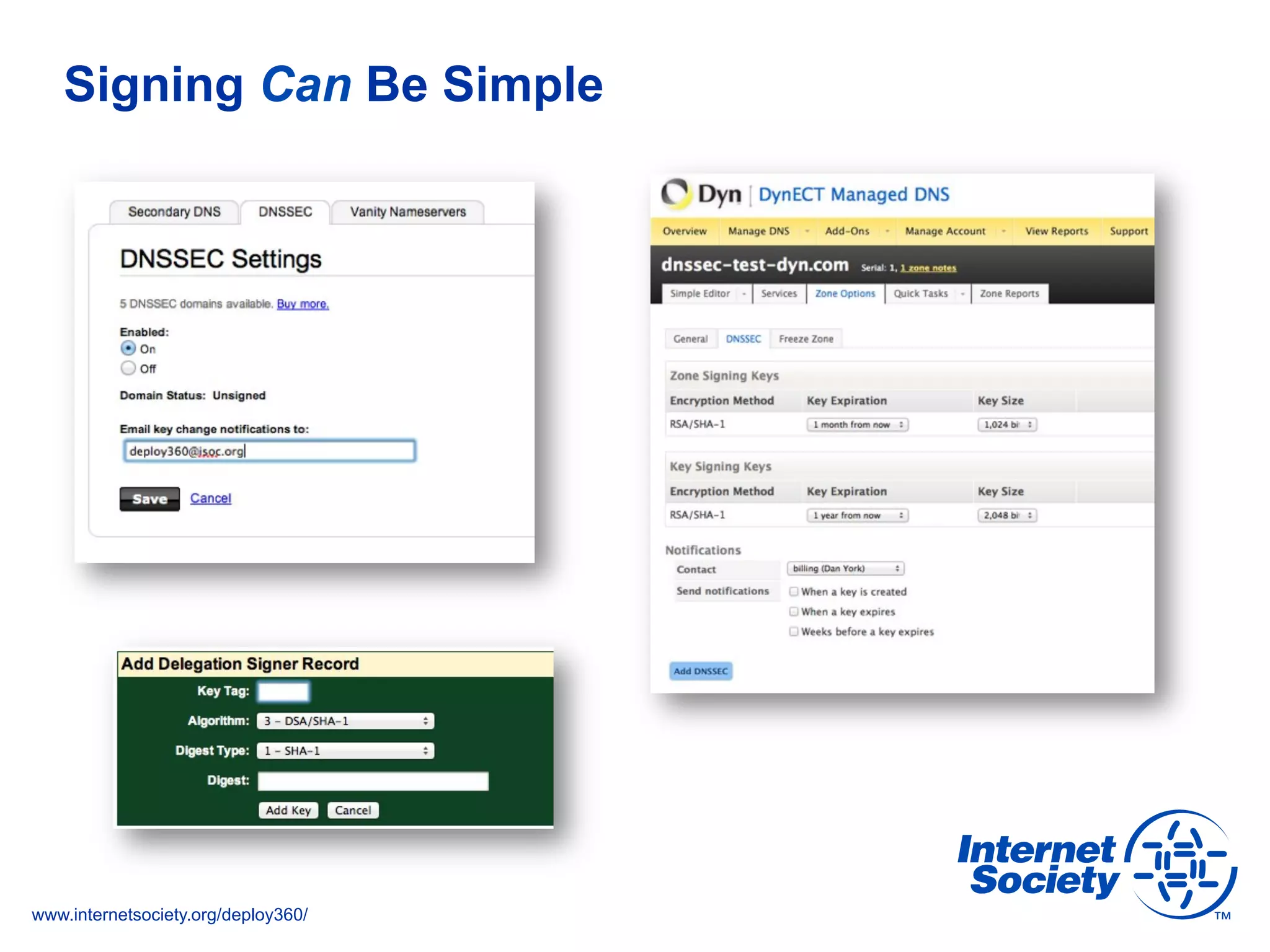
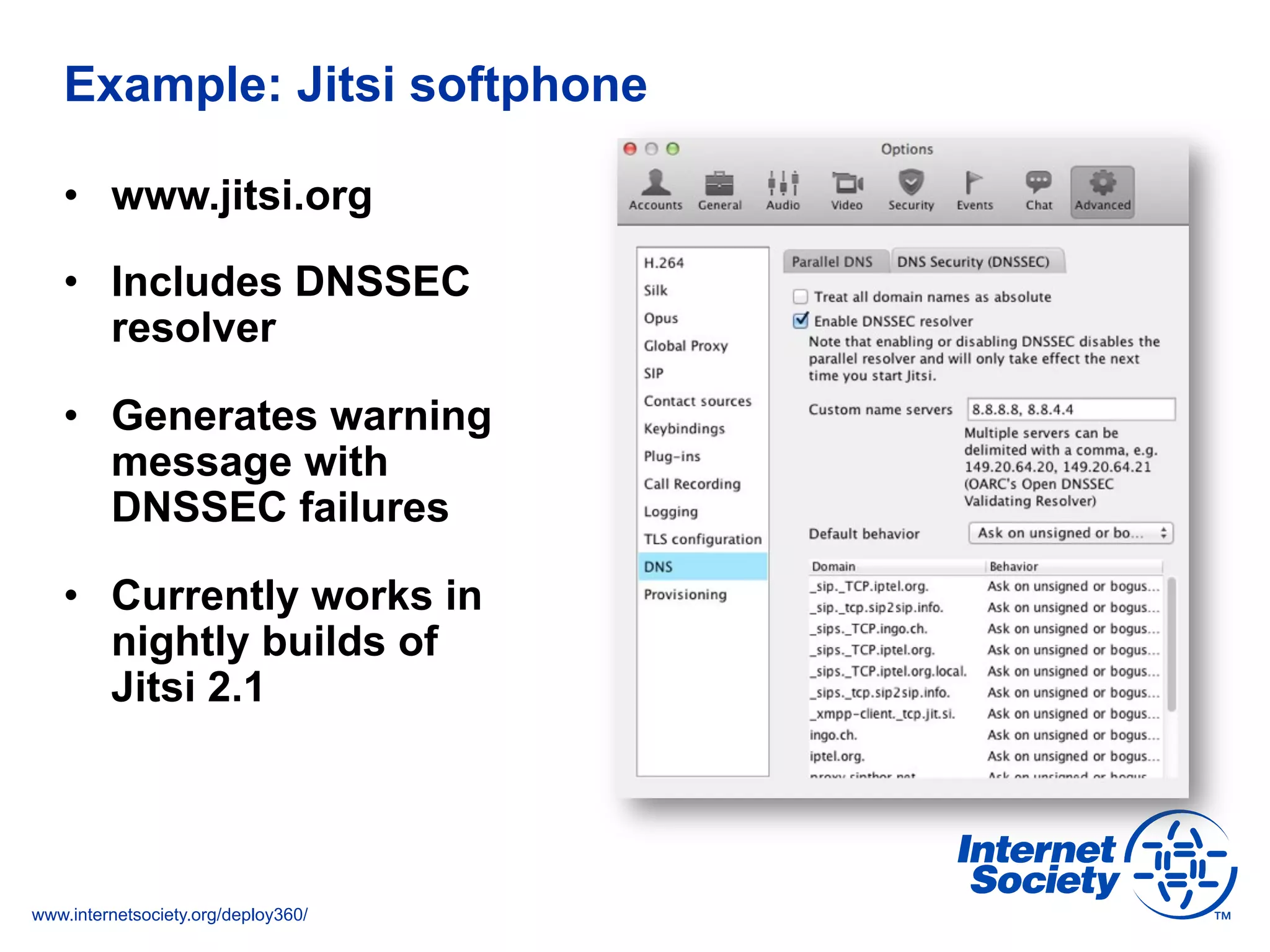
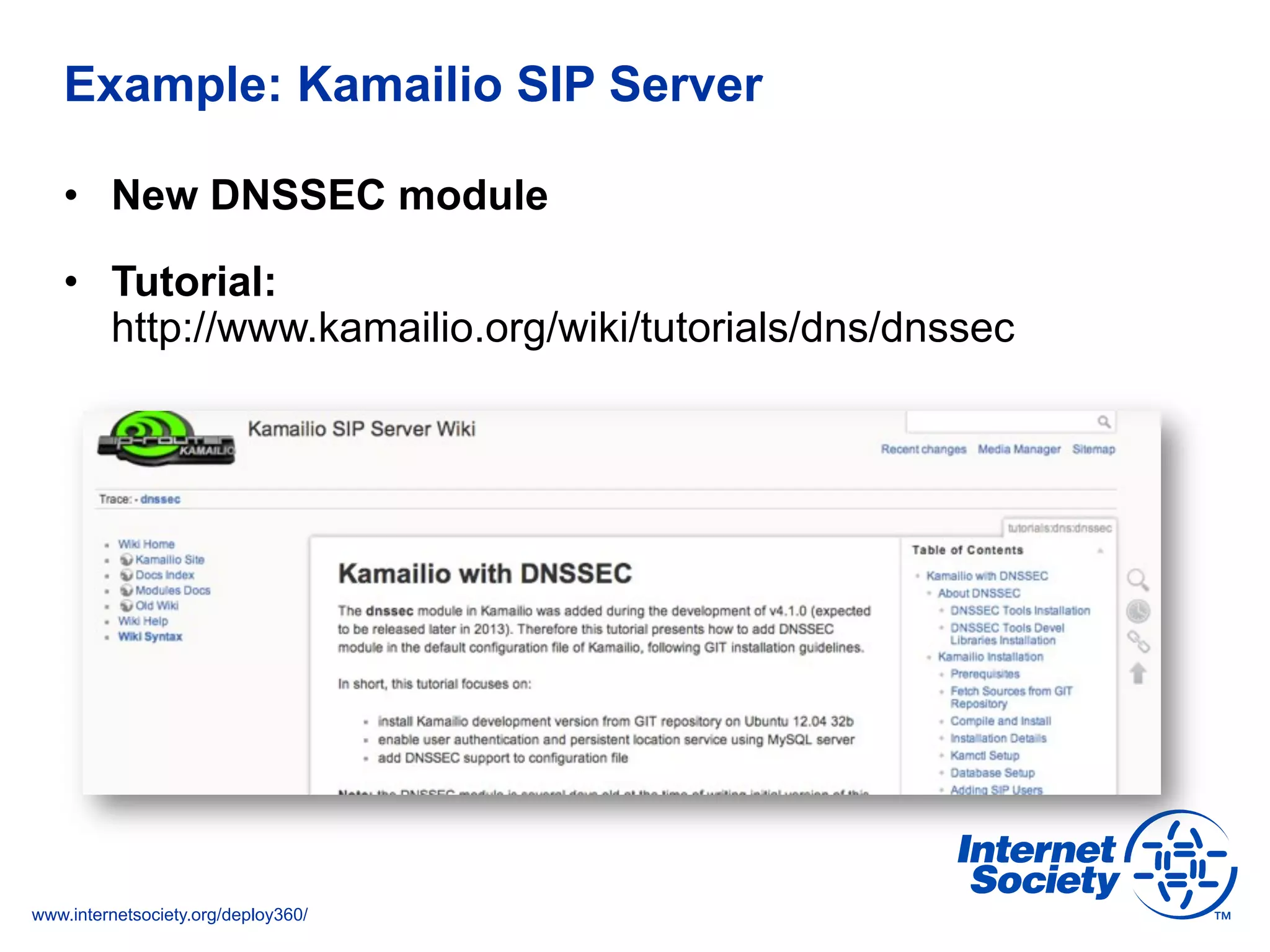
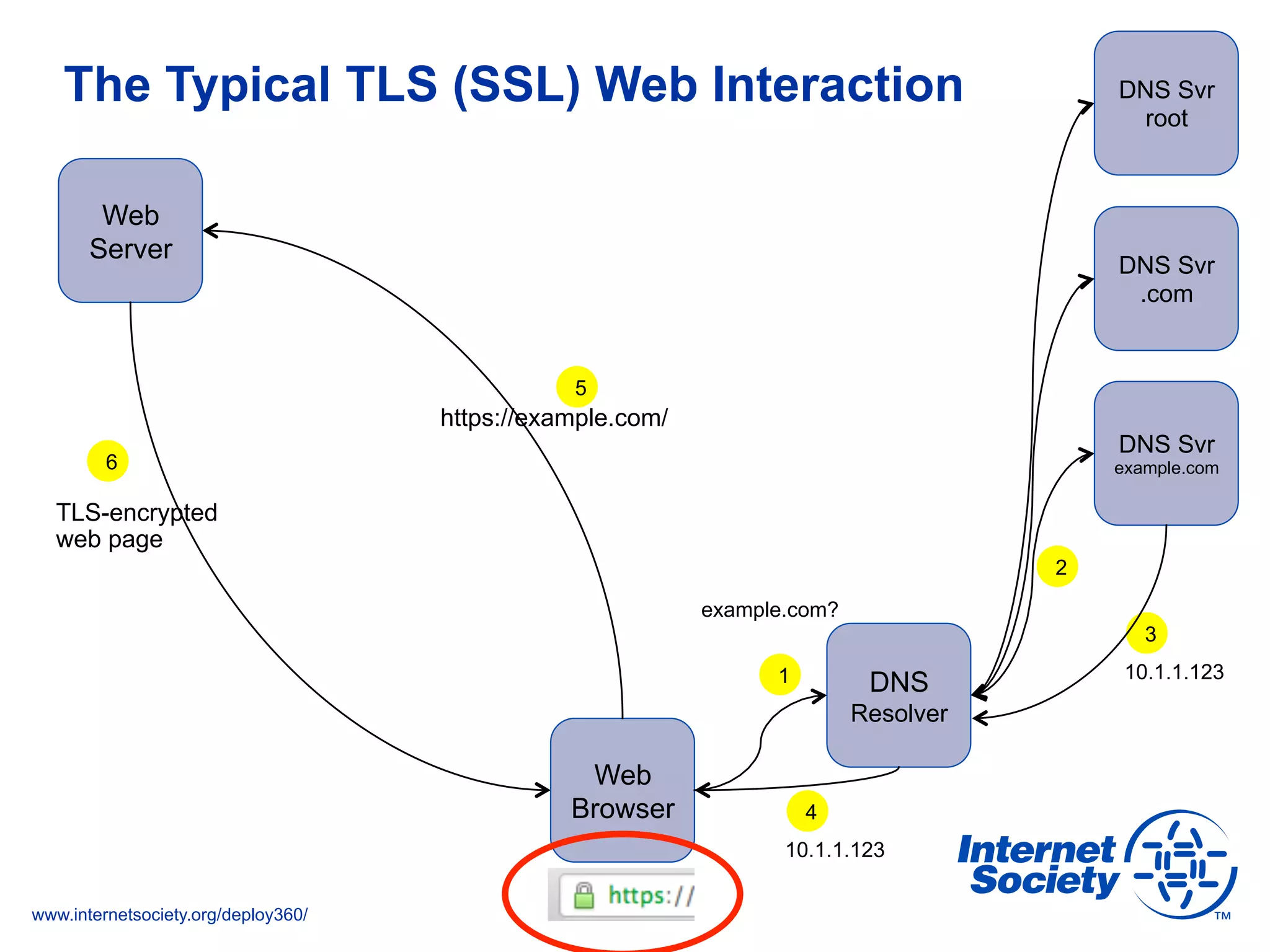
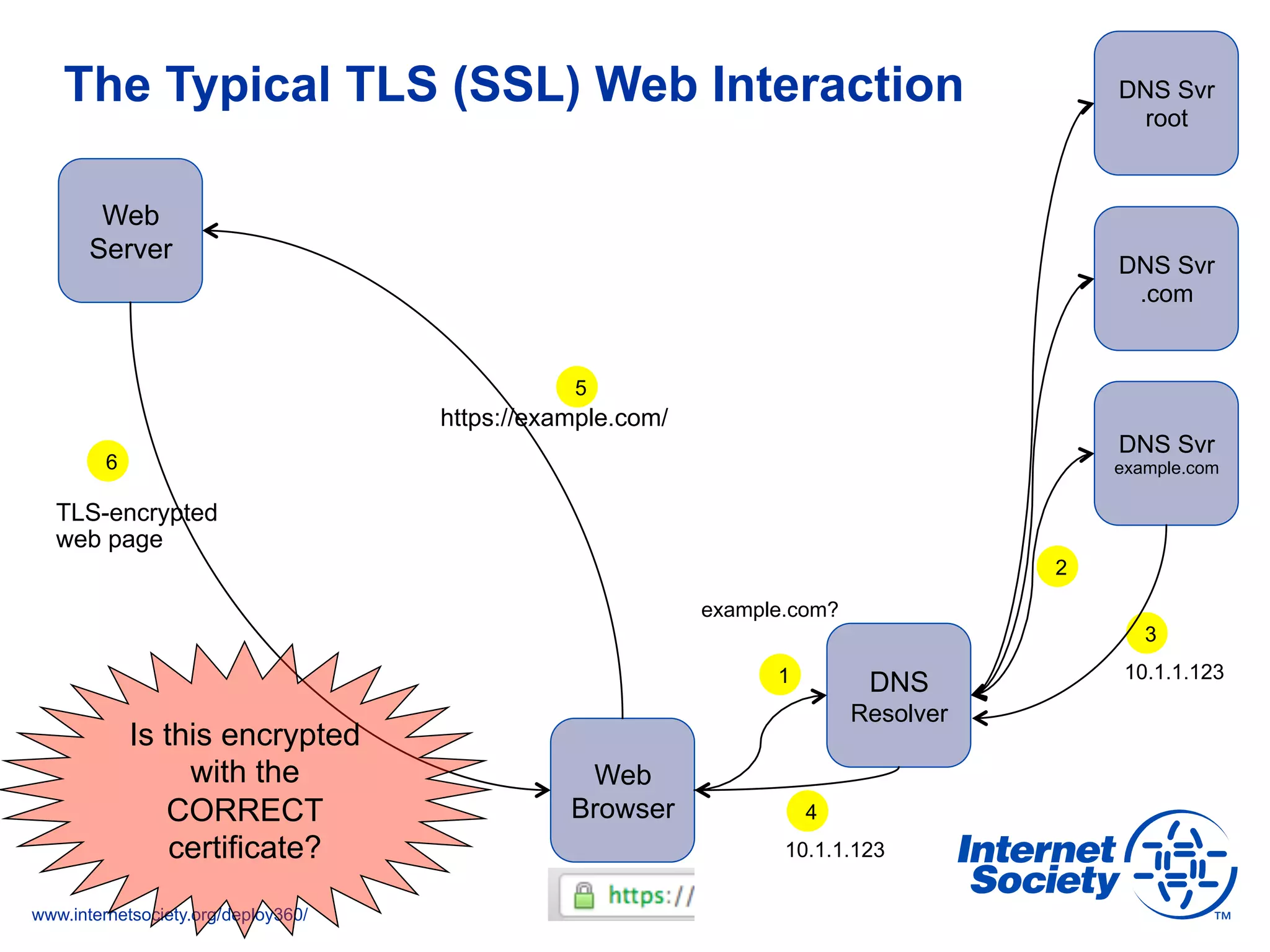
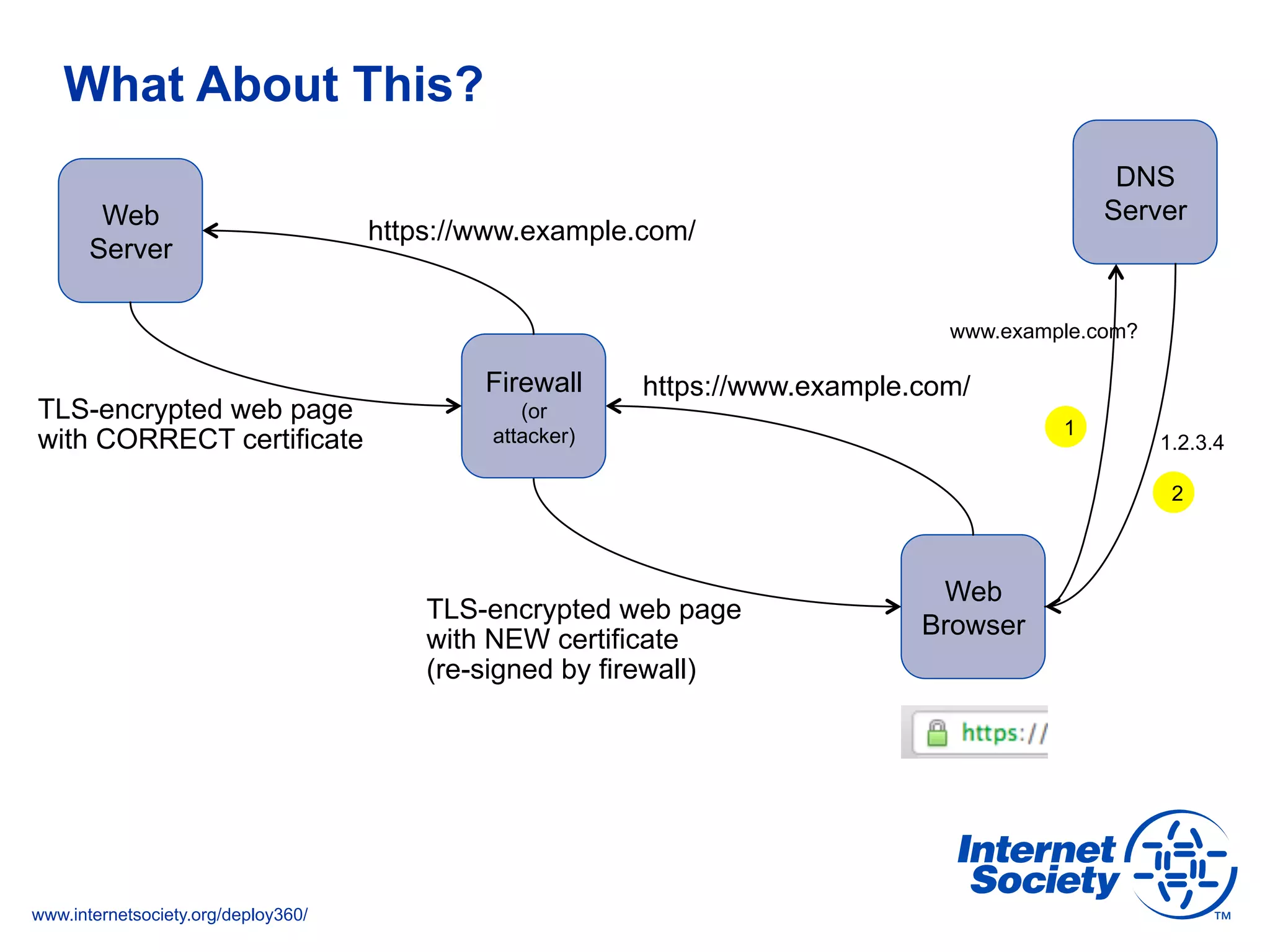
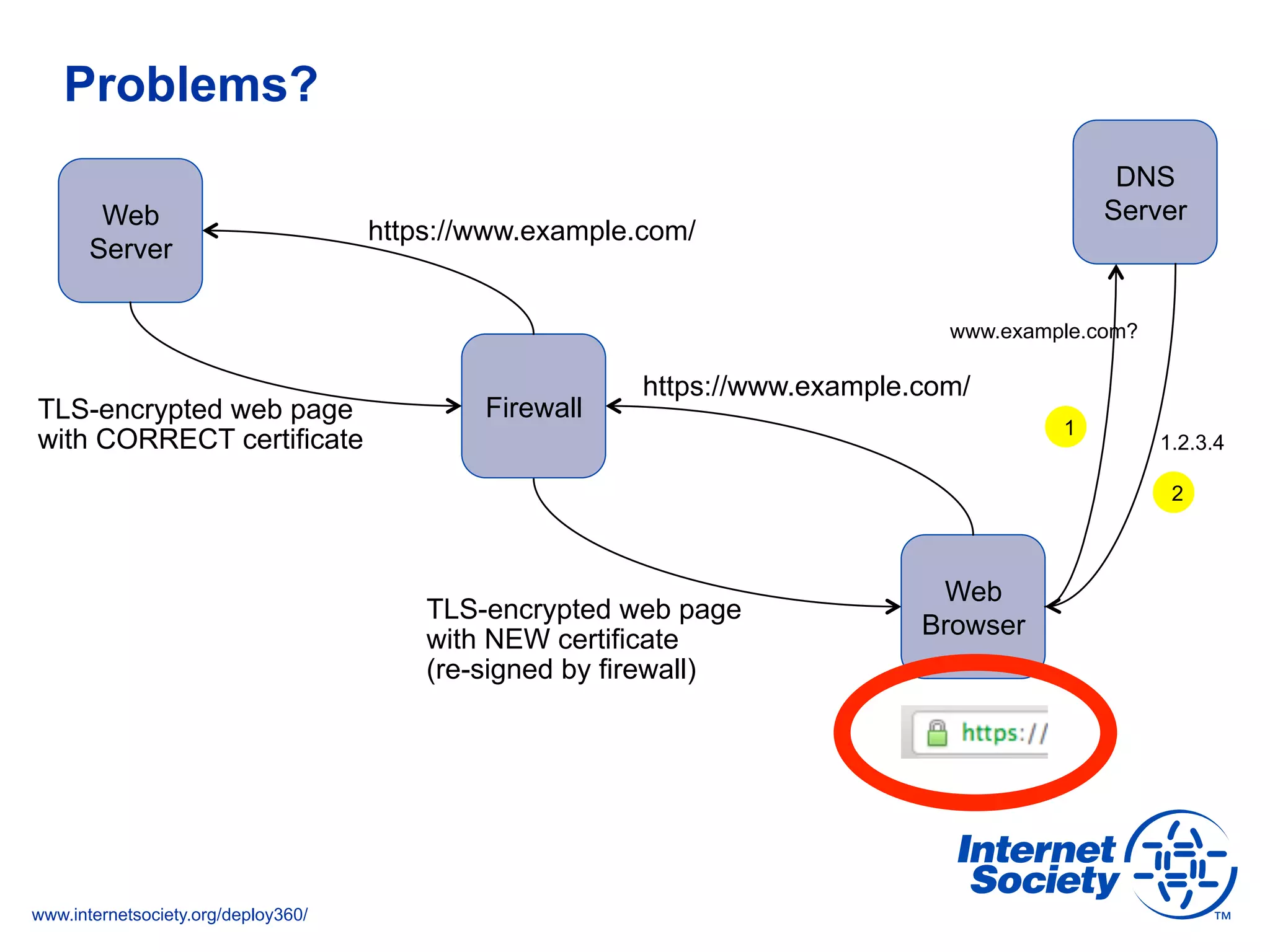
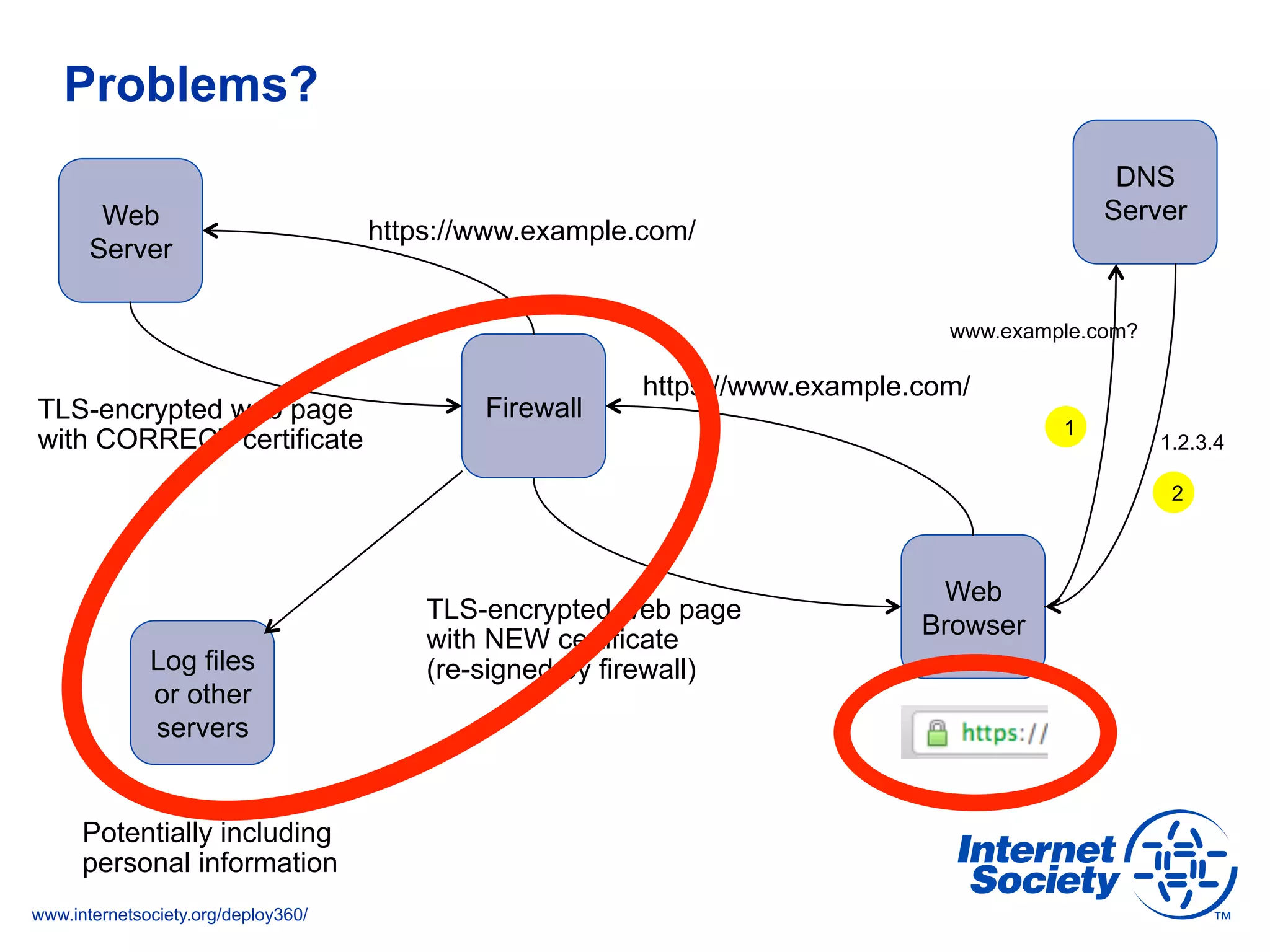
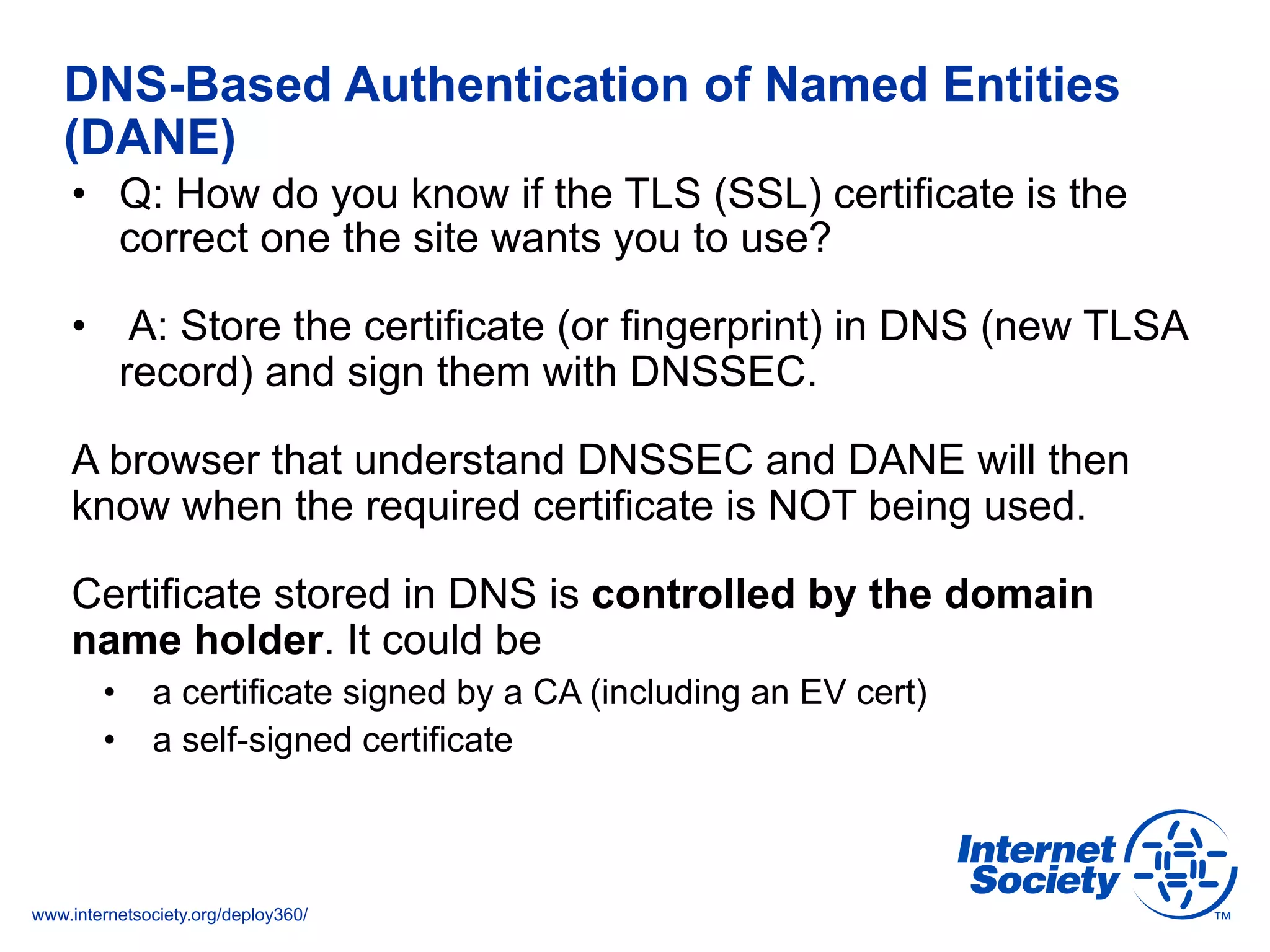
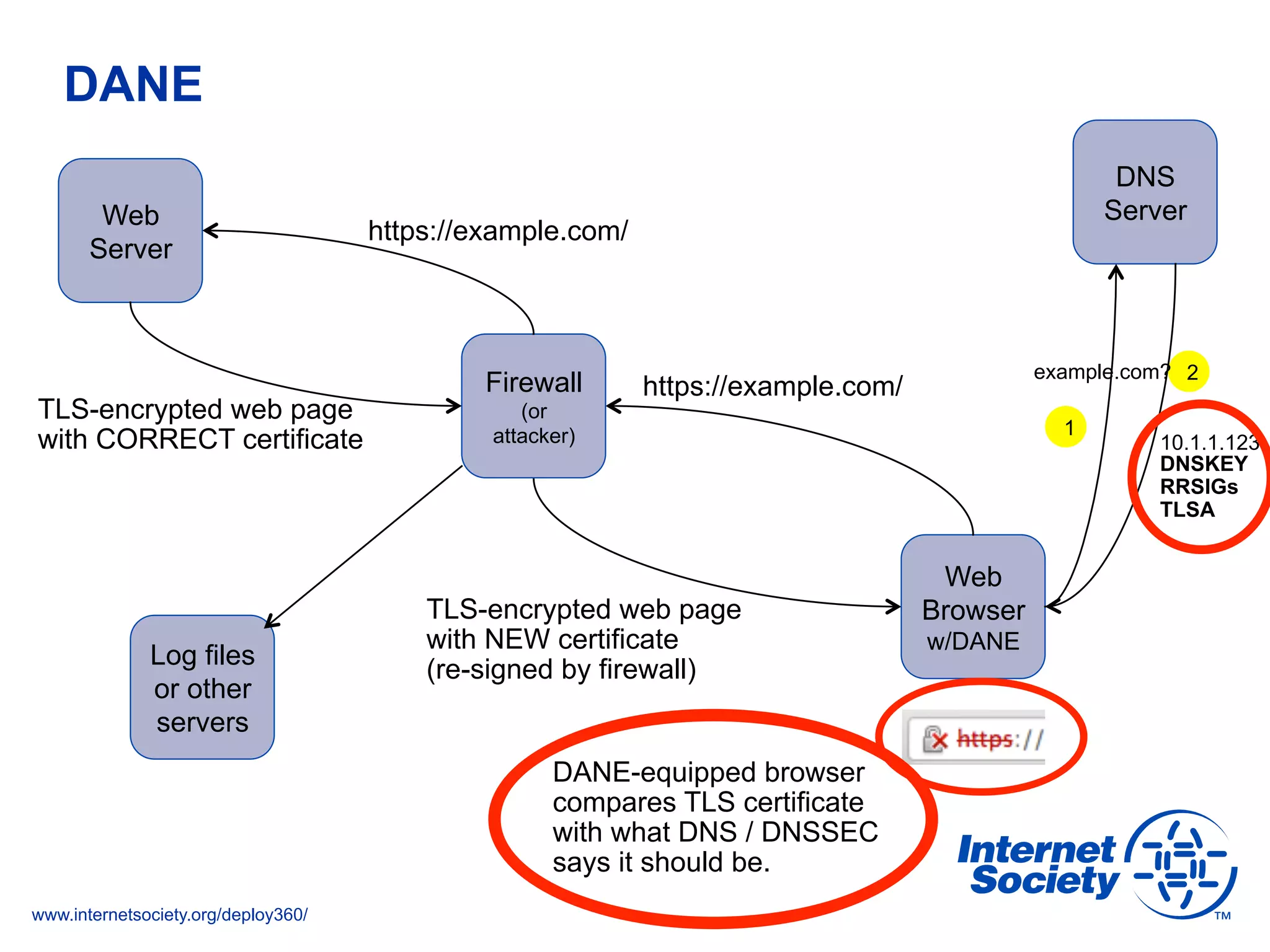
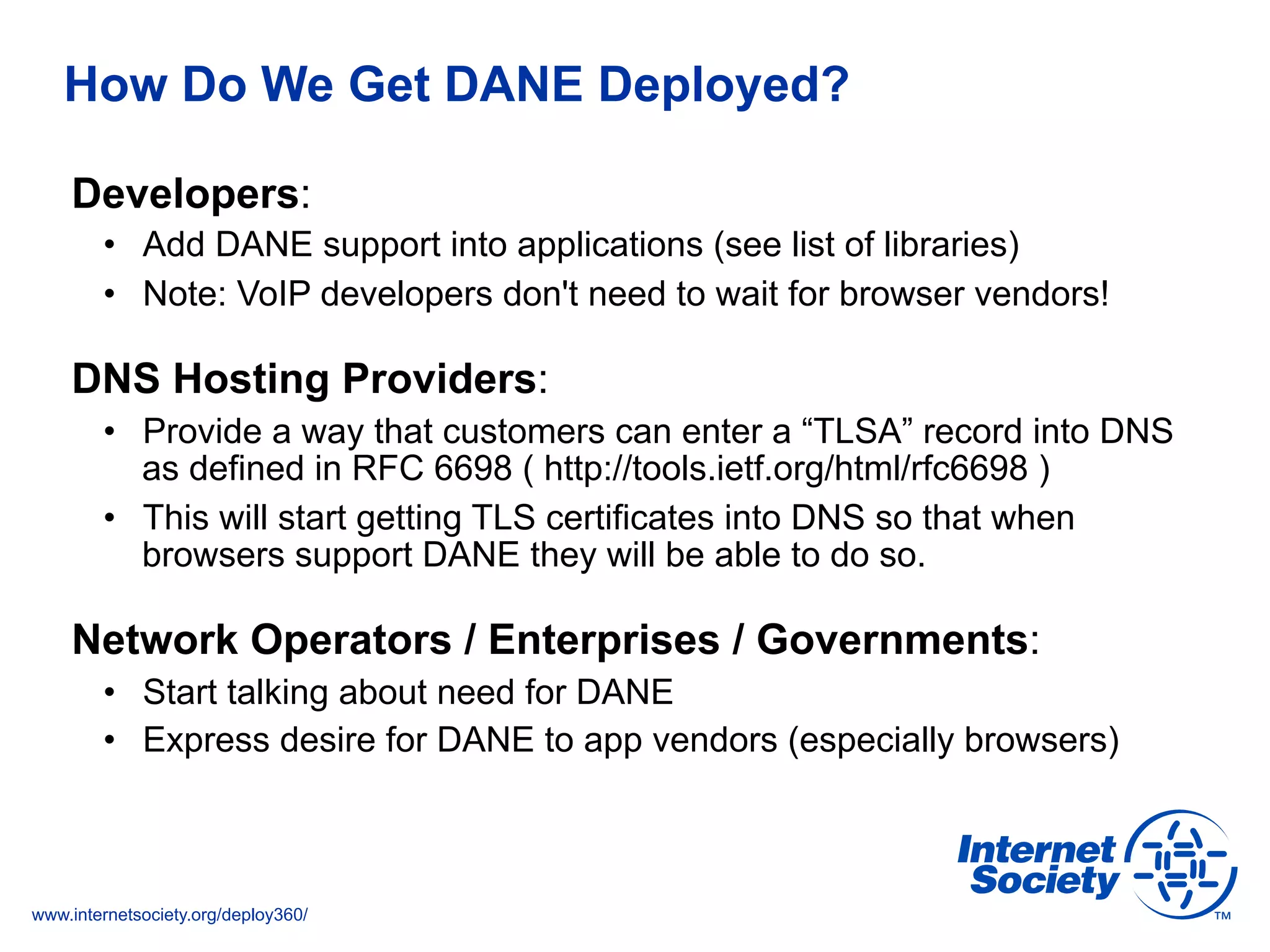
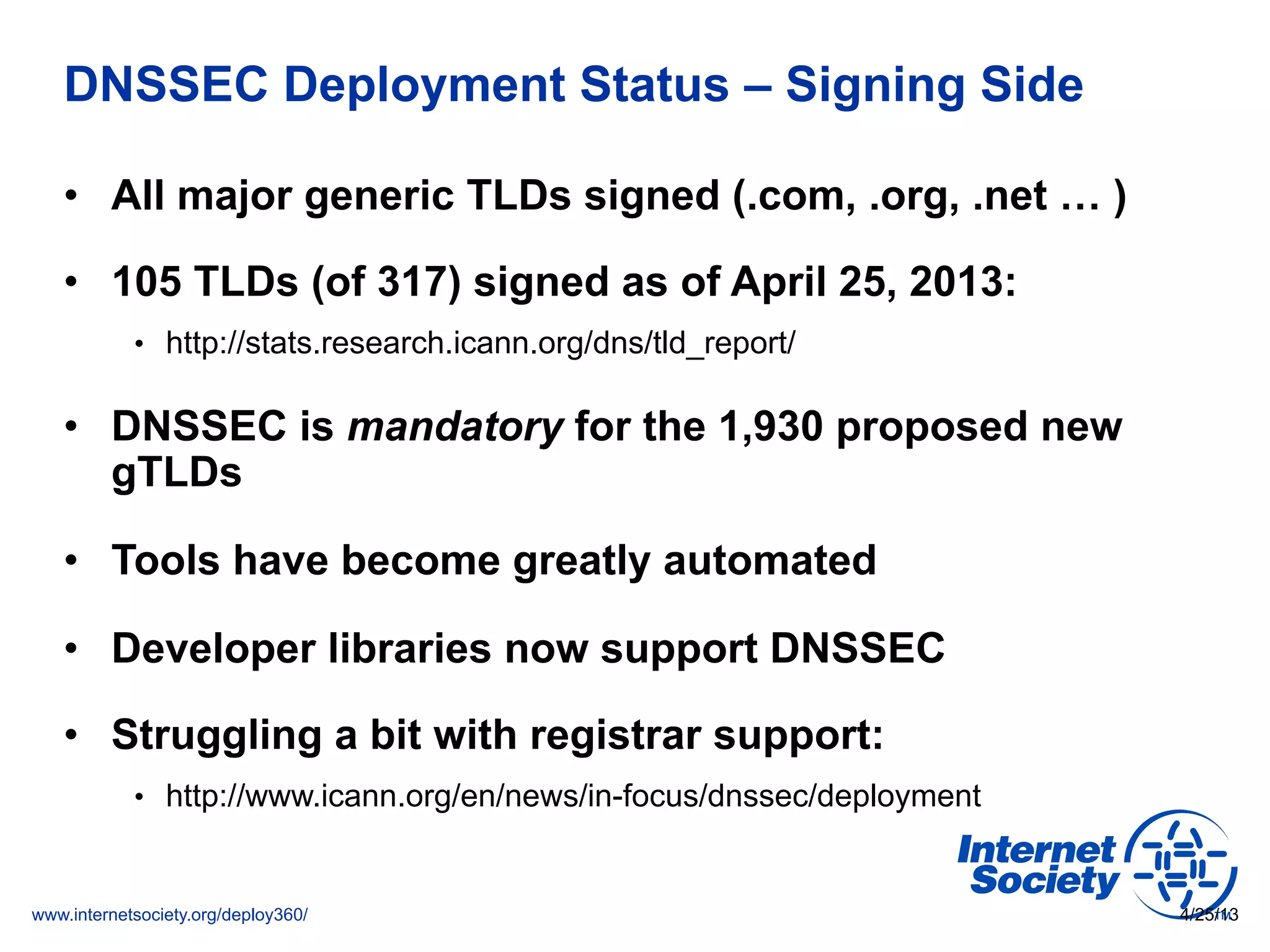
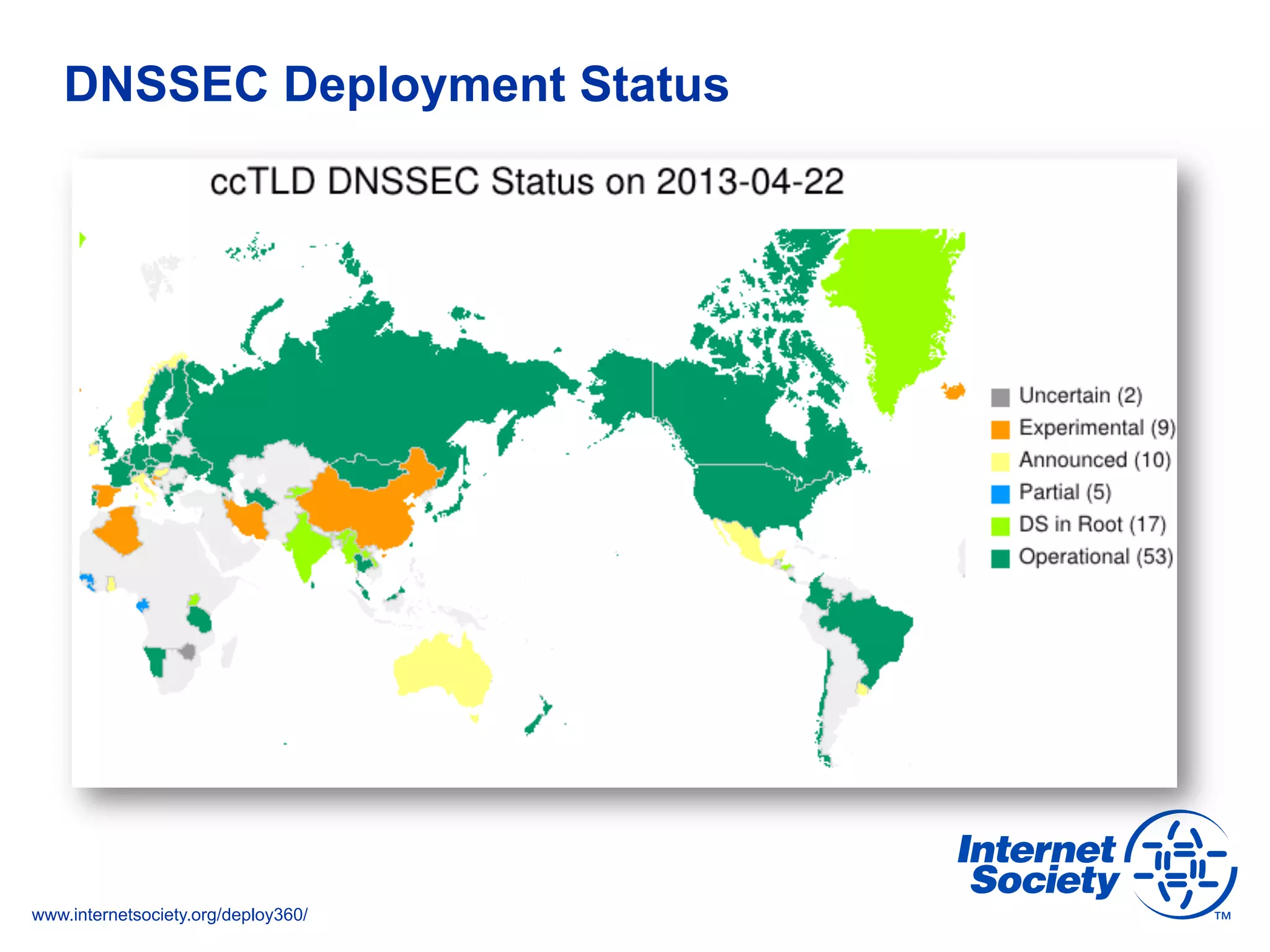
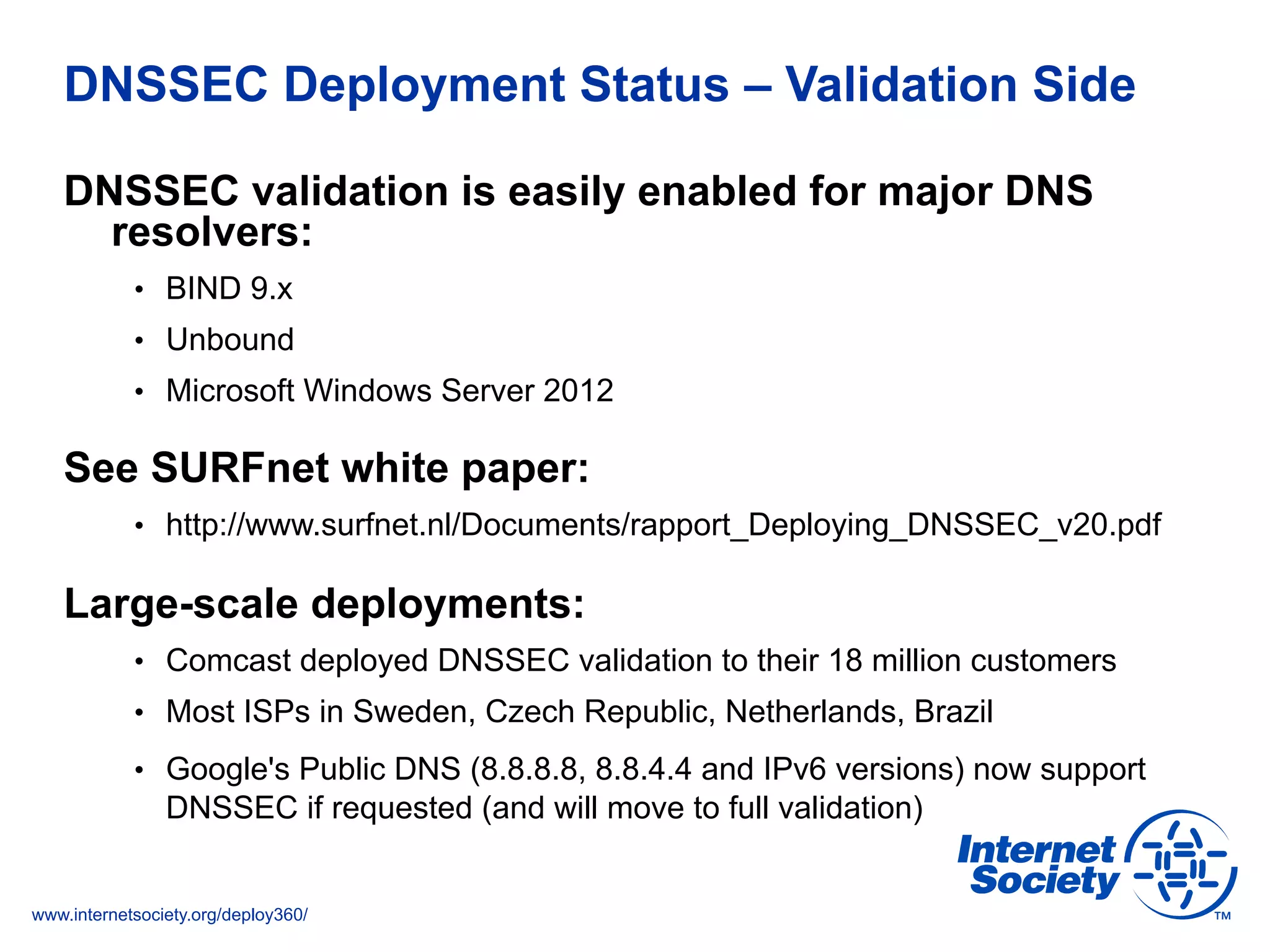
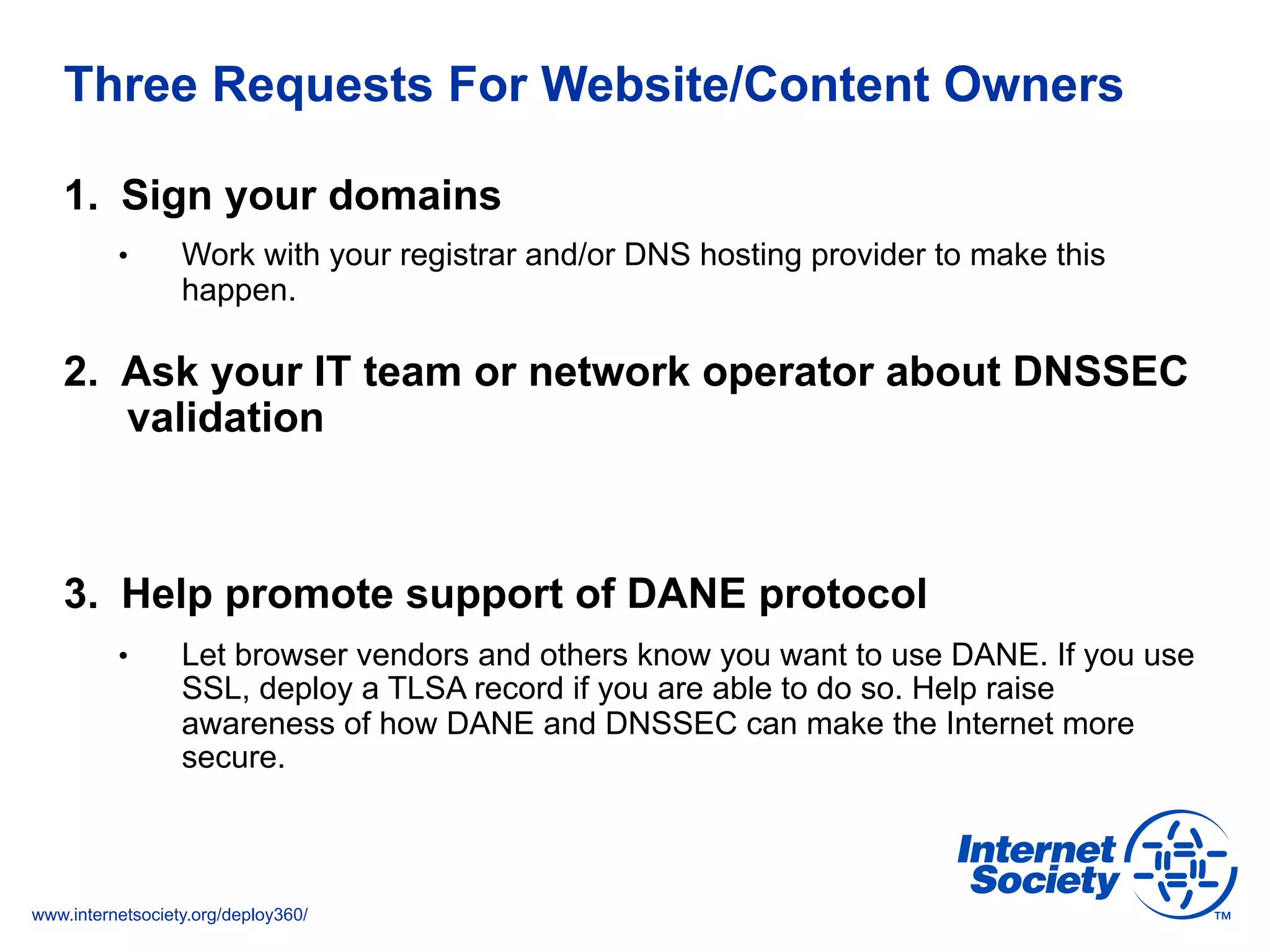
This document discusses the importance of DNSSEC (DNS Security Extensions) in ensuring the integrity of DNS transactions, particularly for applications like VoIP. It explains how DNSSEC can prevent attackers from spoofing DNS records and emphasizes the need for a global chain of trust through delegation signer (DS) records. Additionally, the document outlines implementation strategies for DNSSEC and its integration with TLS/SSL to enhance security online.