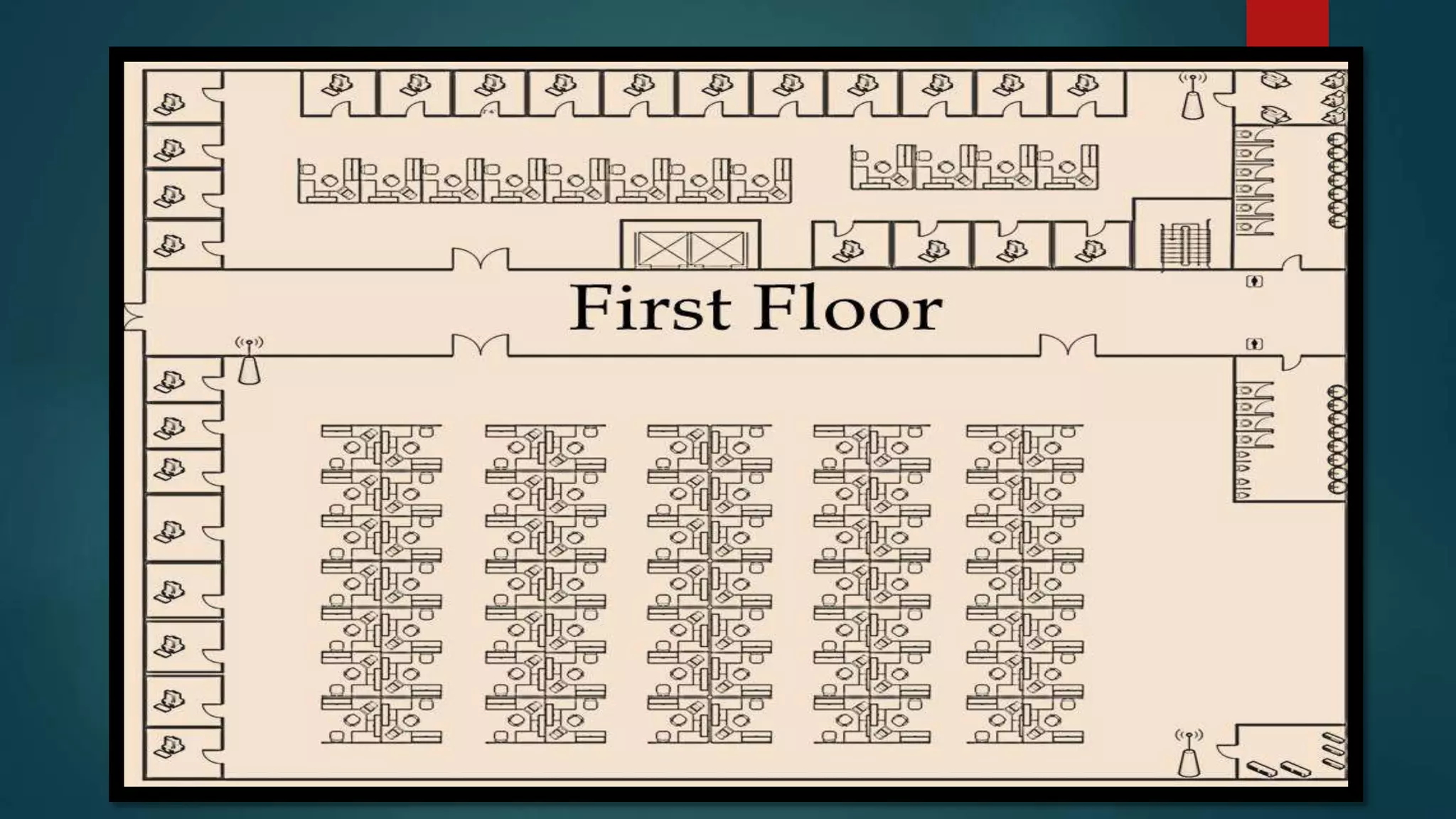
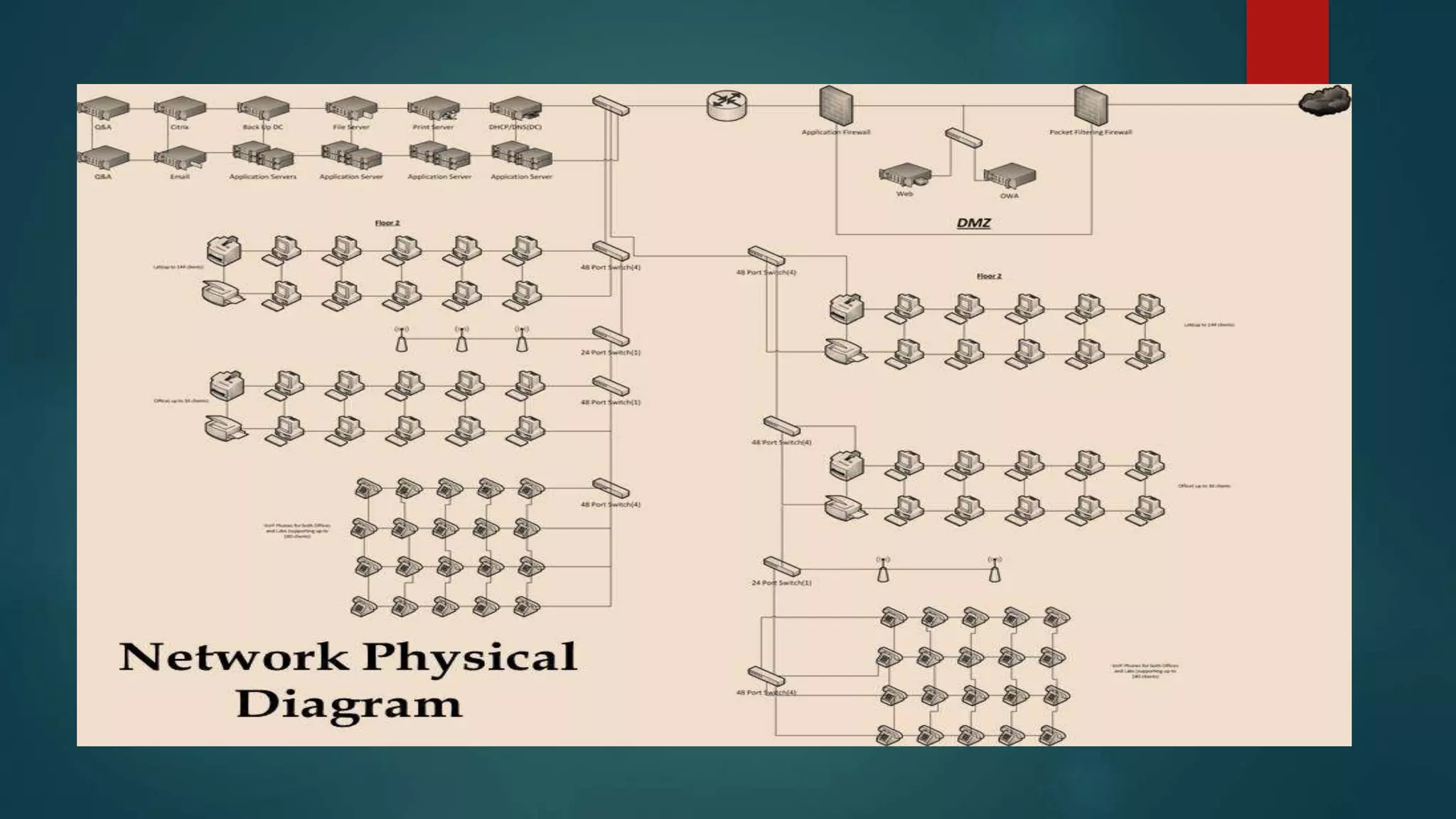
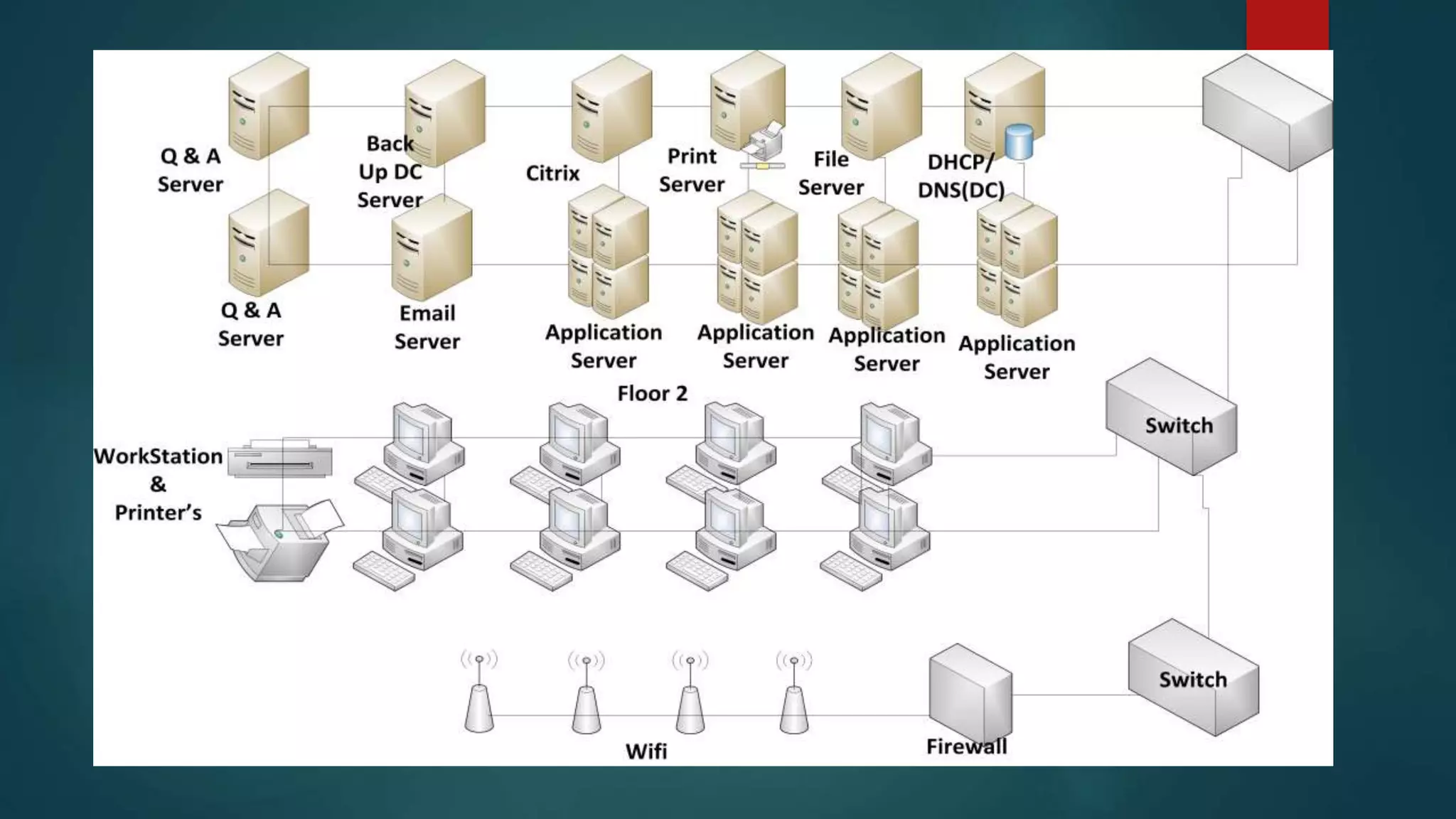
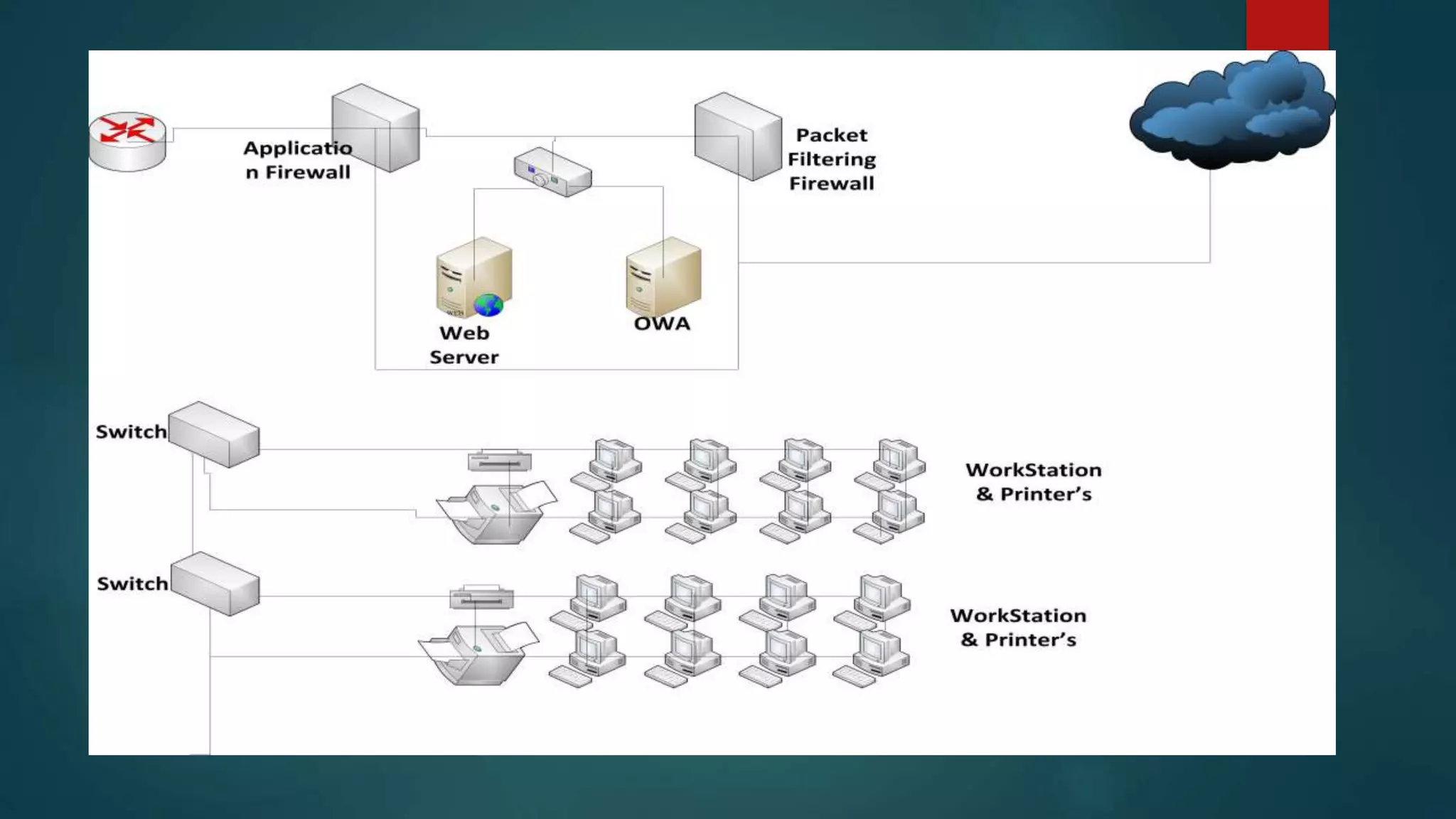
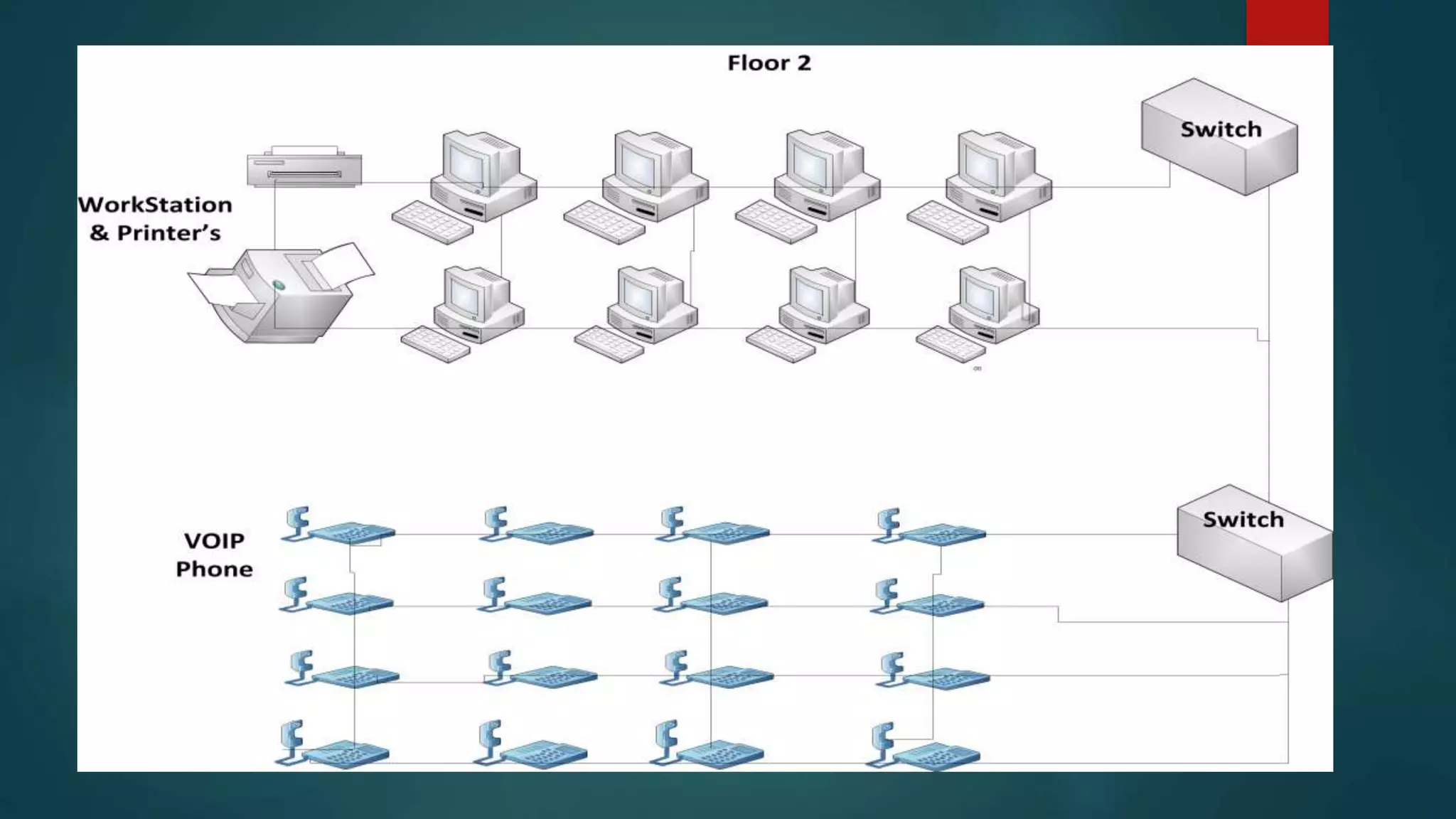
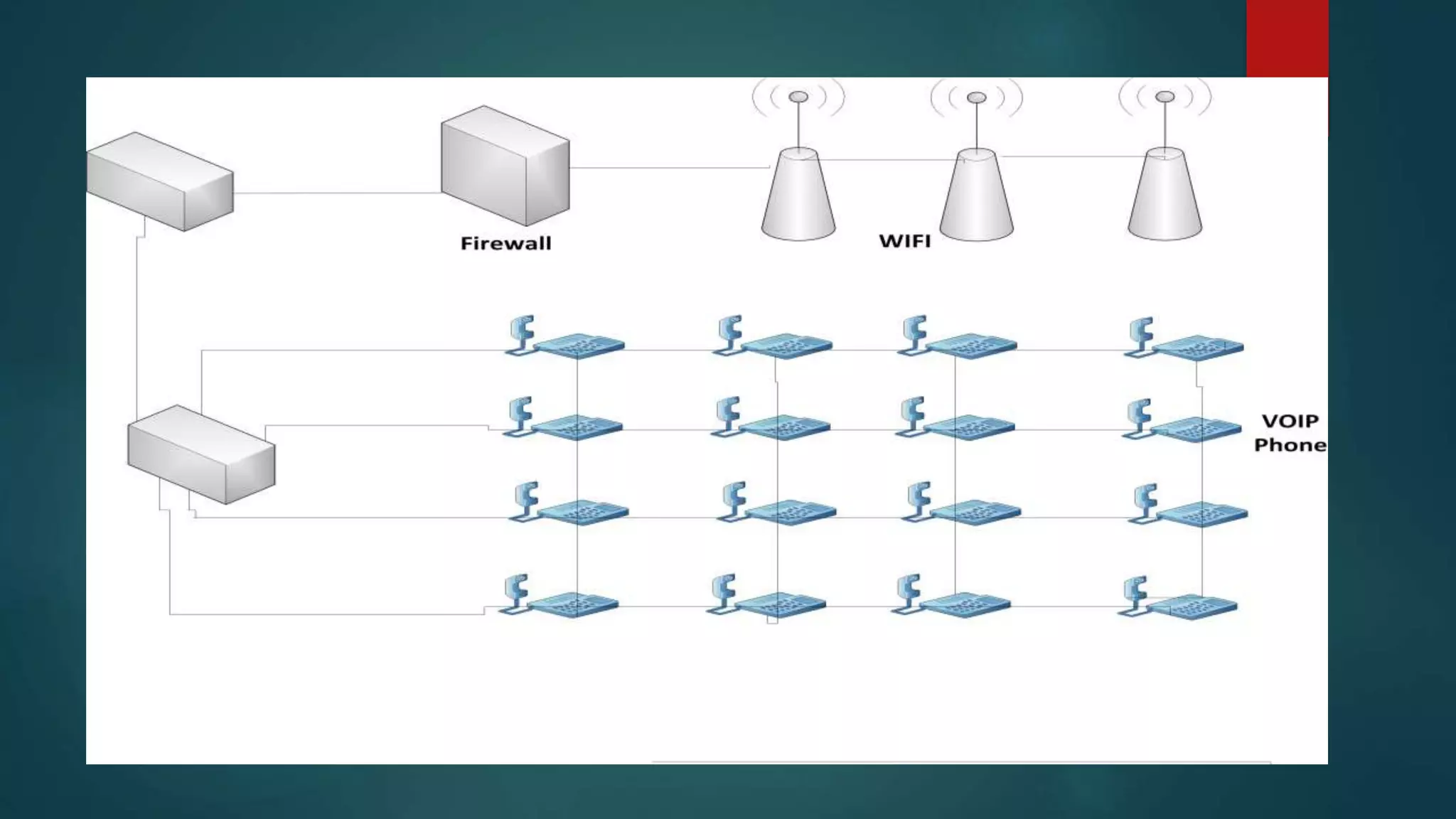
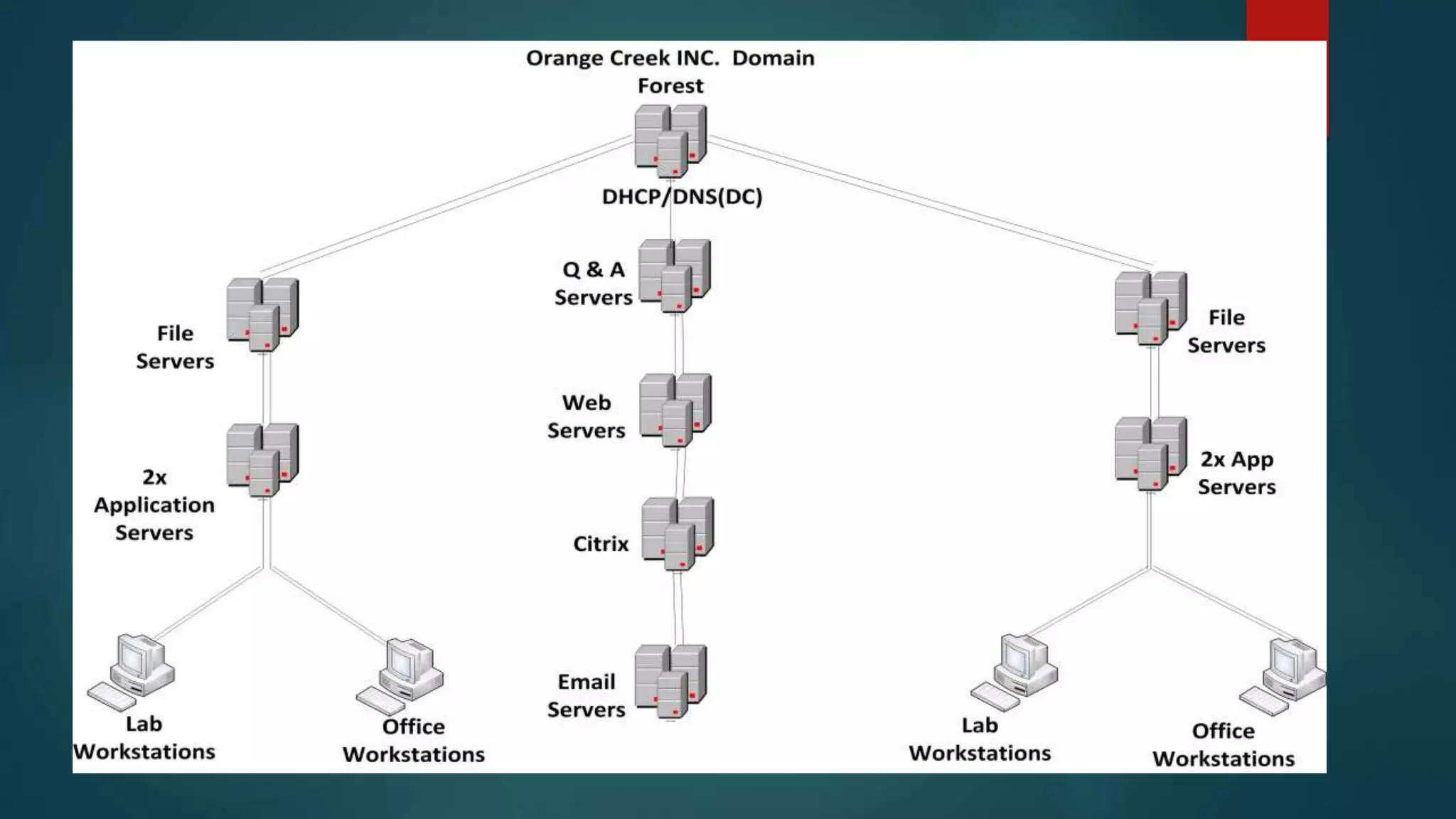
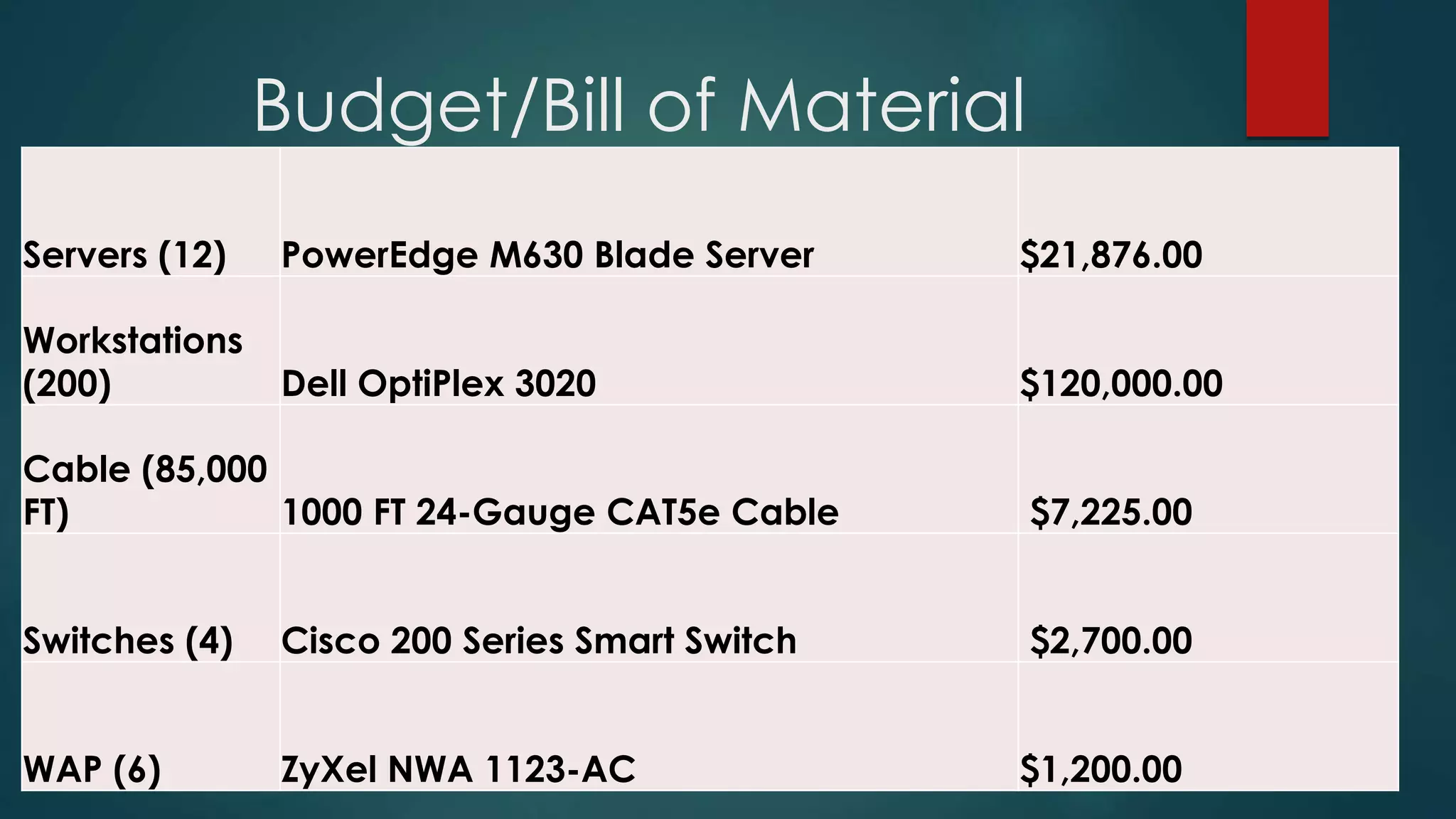
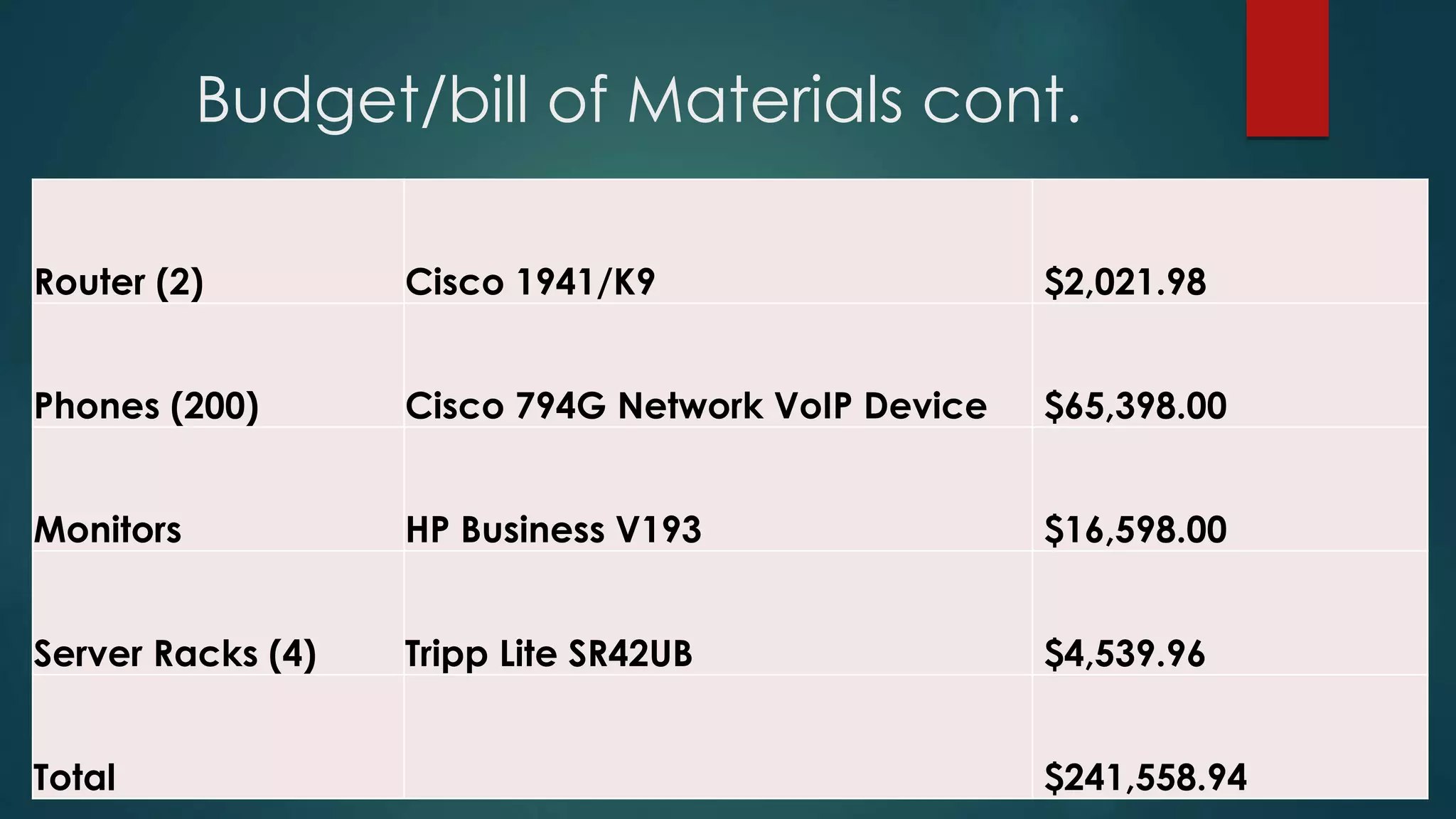
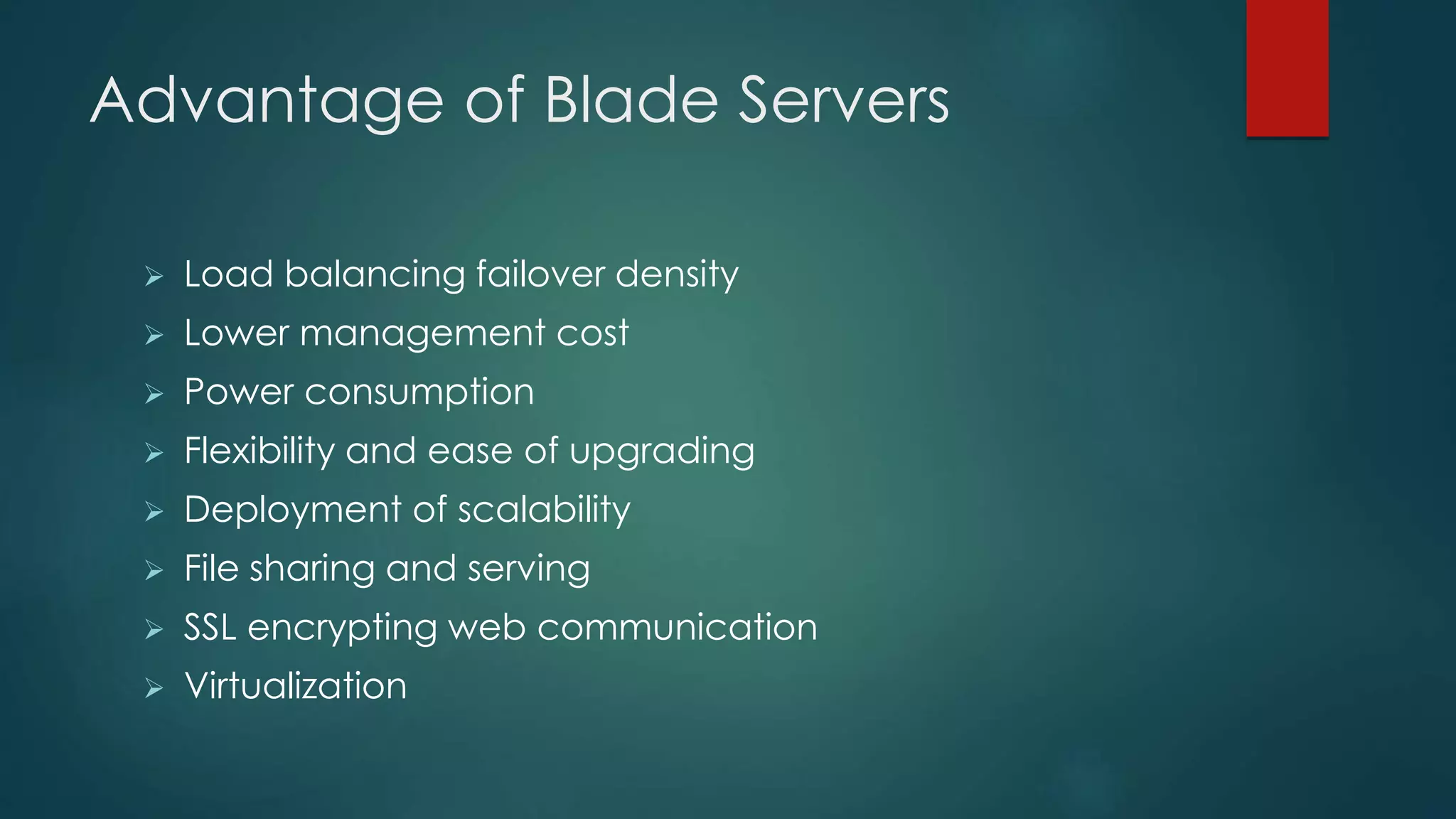
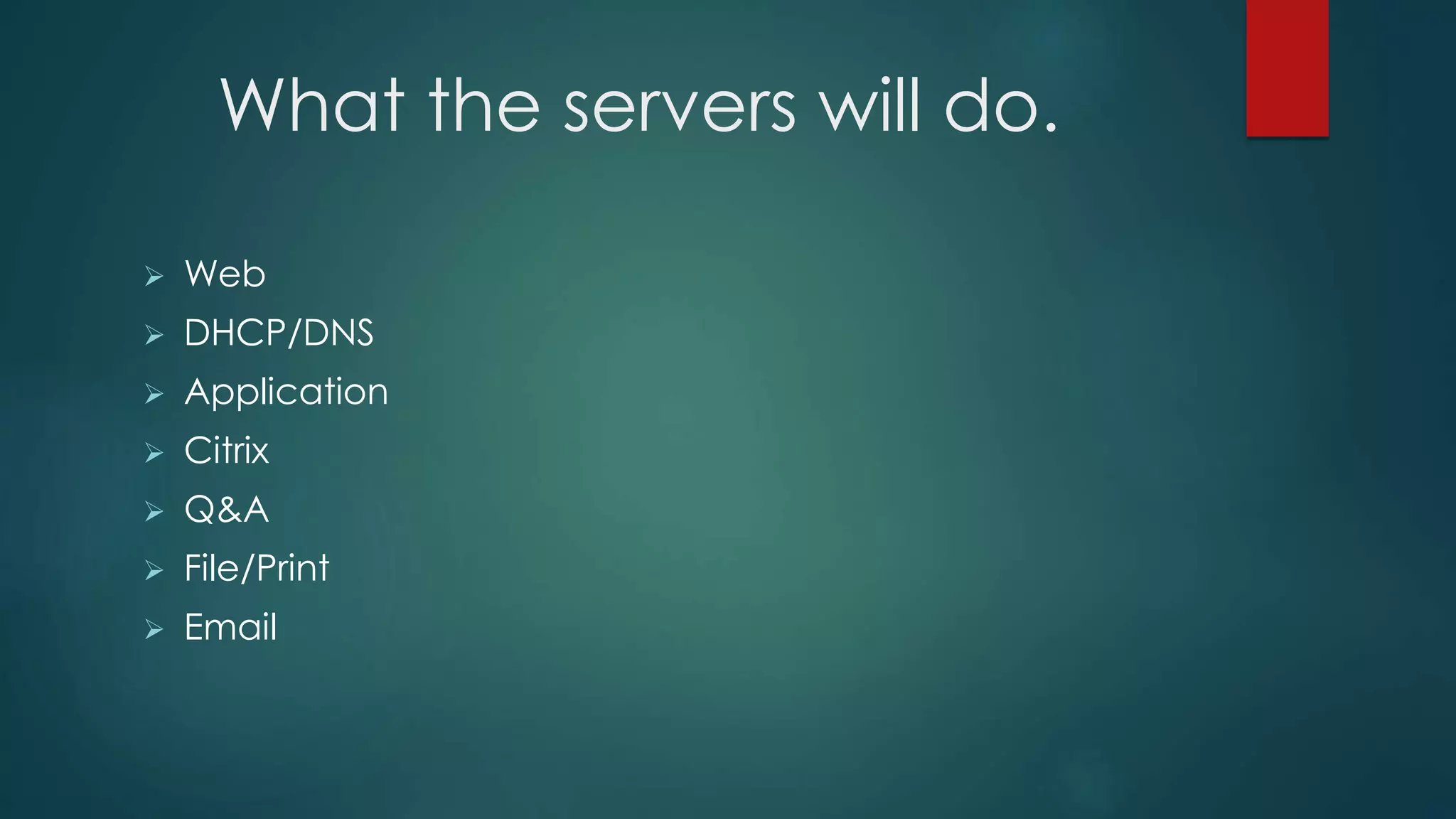
This document provides details about a network infrastructure project proposal for a banking software company called Orange Creek Inc. that is moving to a new building. The proposal includes setting up a network with 200 workstations, VoIP phones, secure WiFi, servers, switches, and other equipment across two floors housing 75-100 employees each. The scope involves physical setup, security, and providing a network schema within budget. Risks and disaster recovery plans are also outlined.