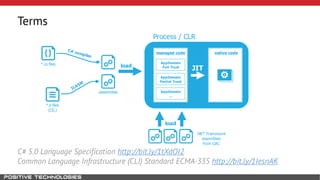
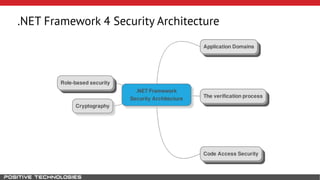
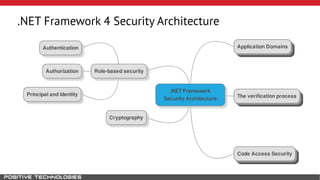
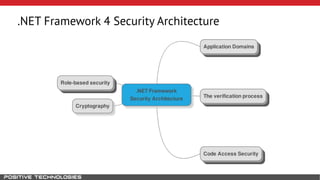
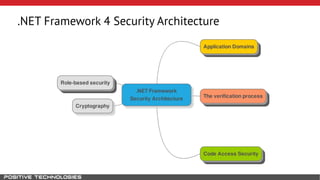
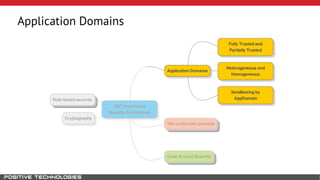
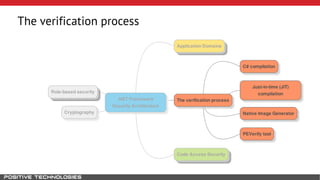
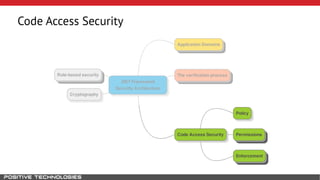
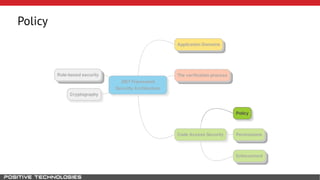
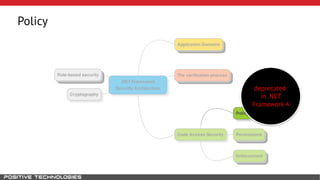
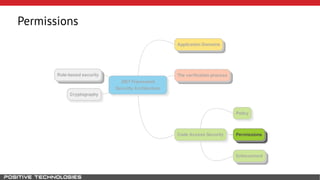
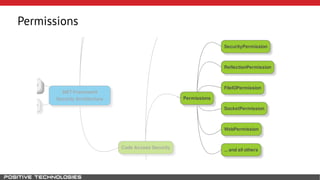
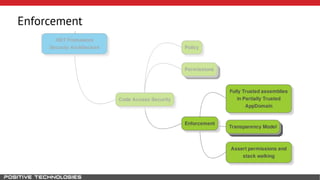
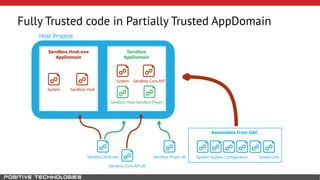
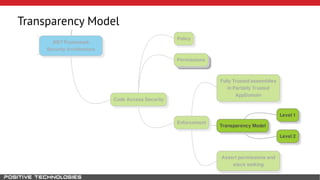
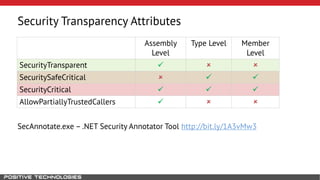
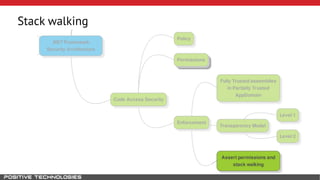
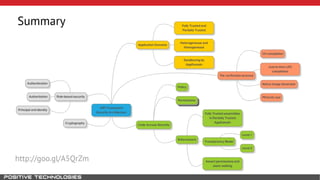
Mikhail Shcherbakov, a senior software developer at Positive Technologies, discusses the security model in the .NET Framework. He outlines how the .NET Framework uses application domains, code access security, and a transparency model to provide sandboxing of code through verification, permissions, and security attributes. The security architecture has evolved over time from .NET Framework 4 to address issues like partial trust applications and trusted chain attacks.