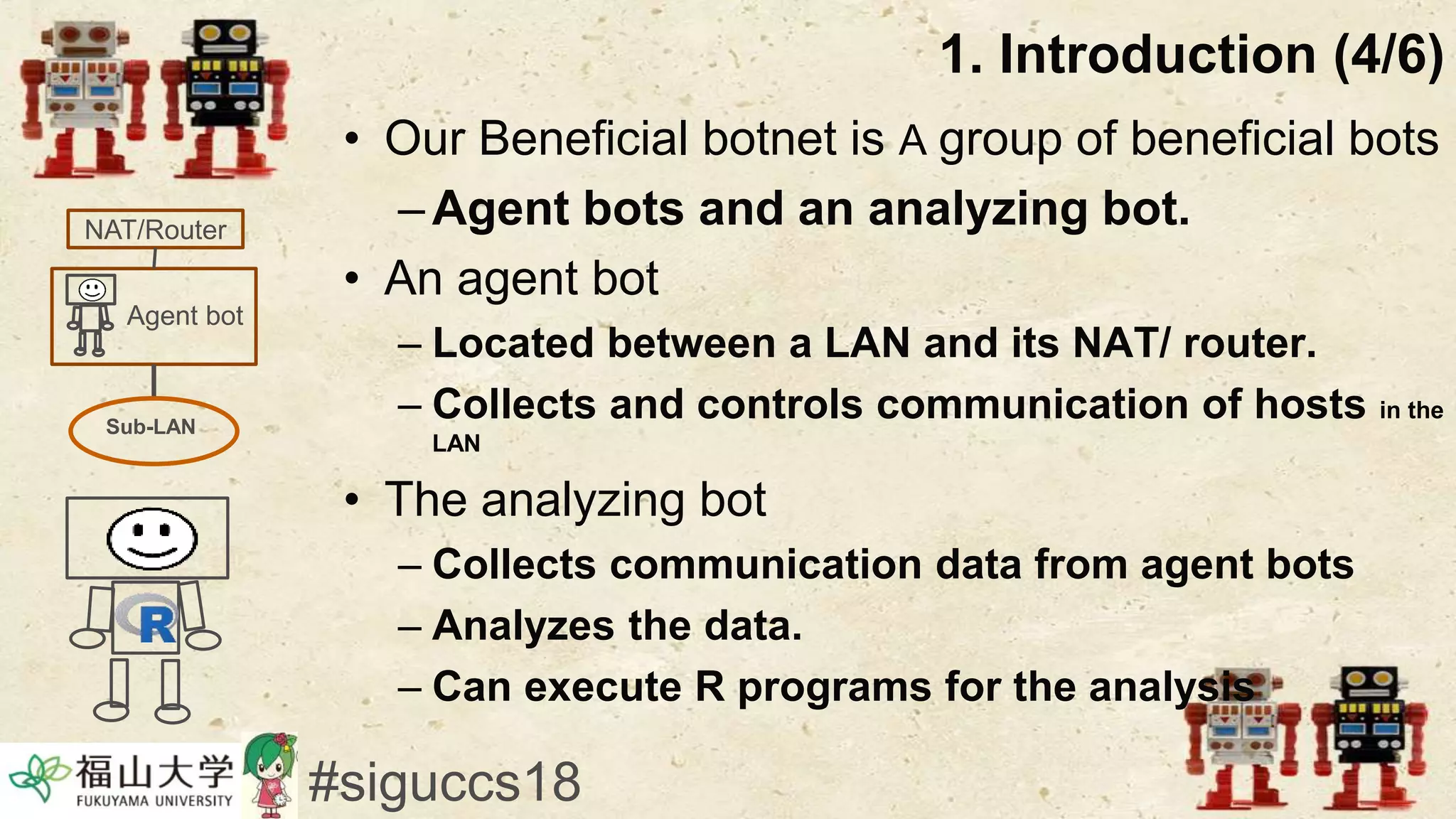
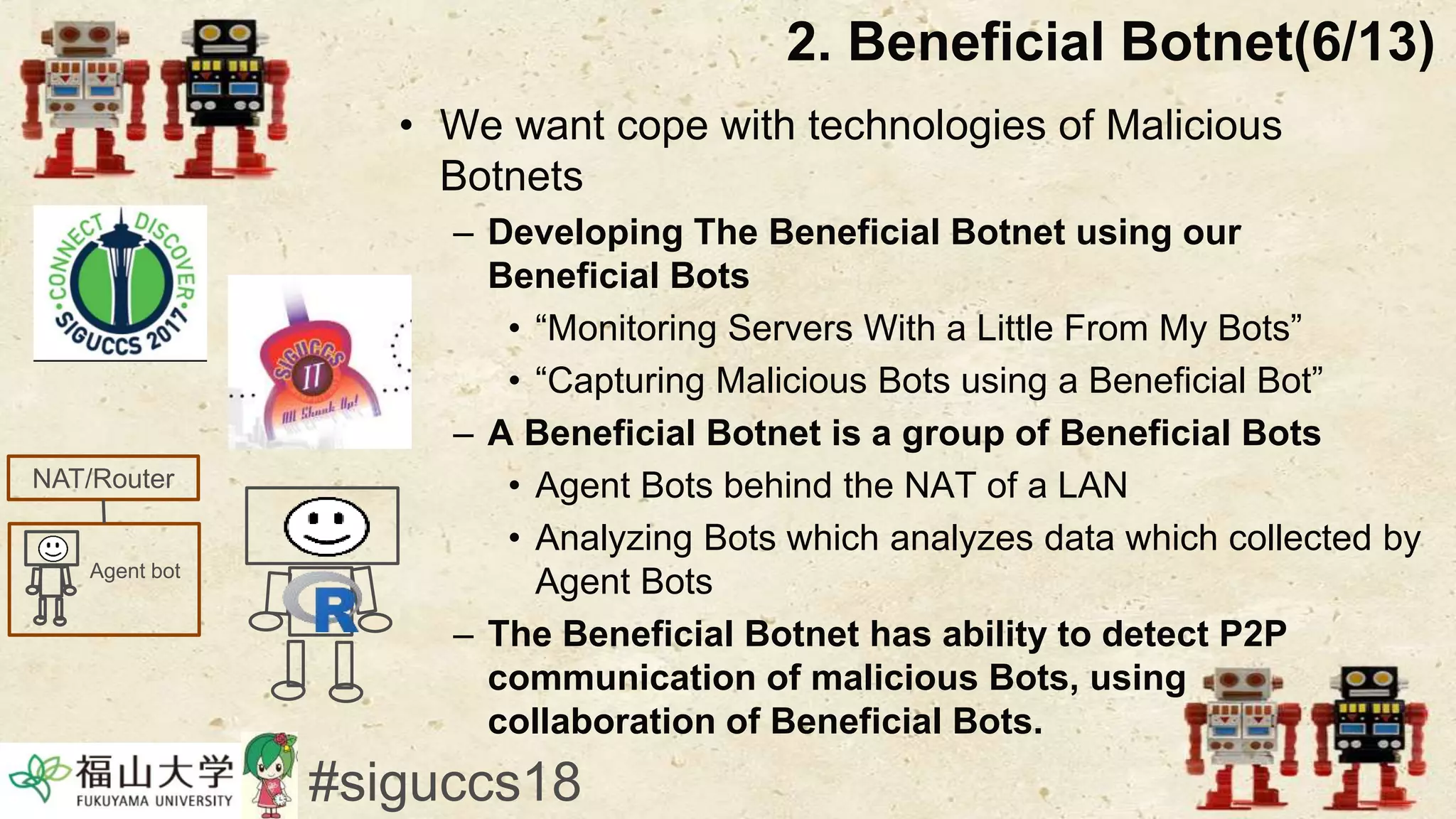
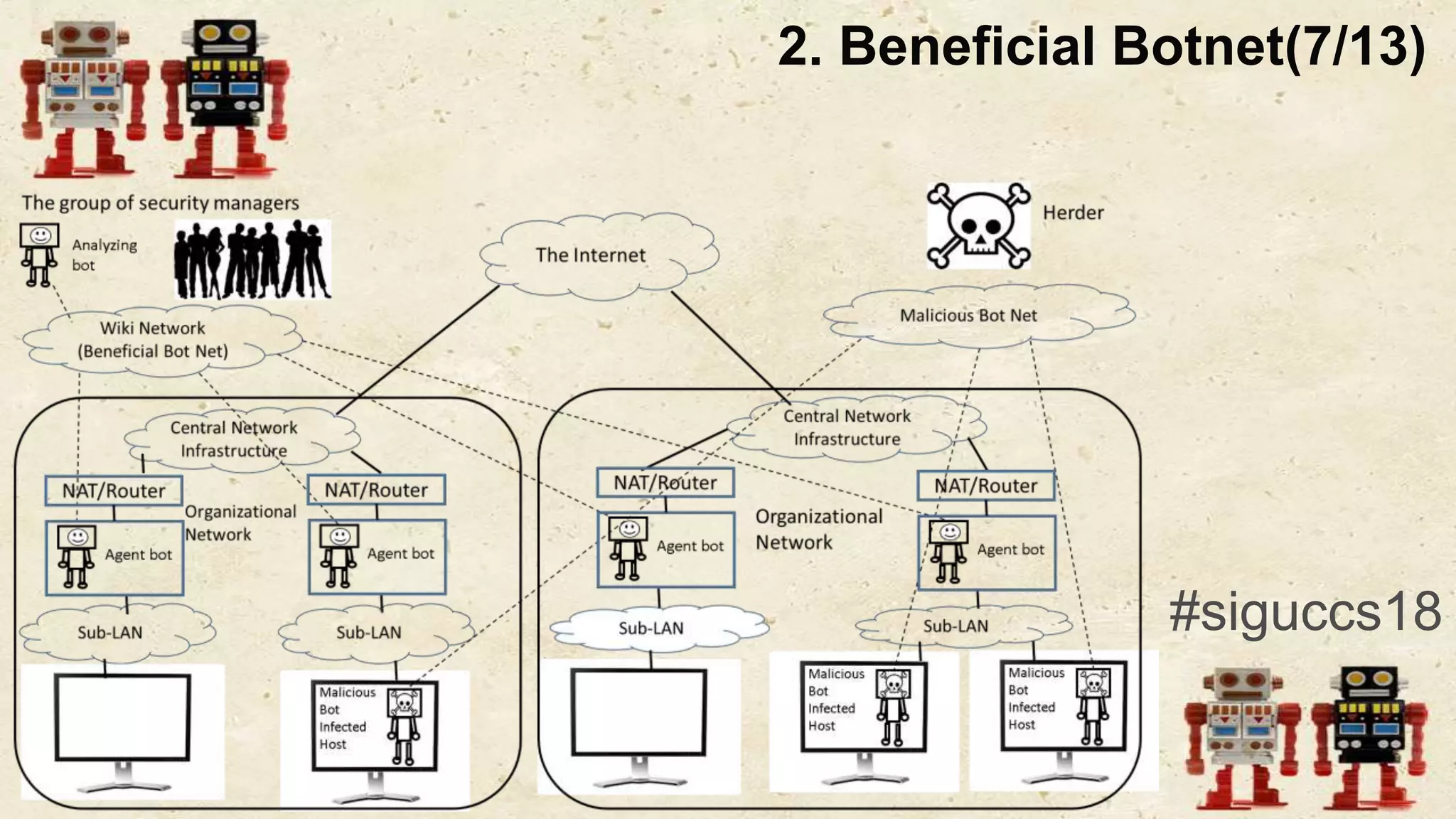
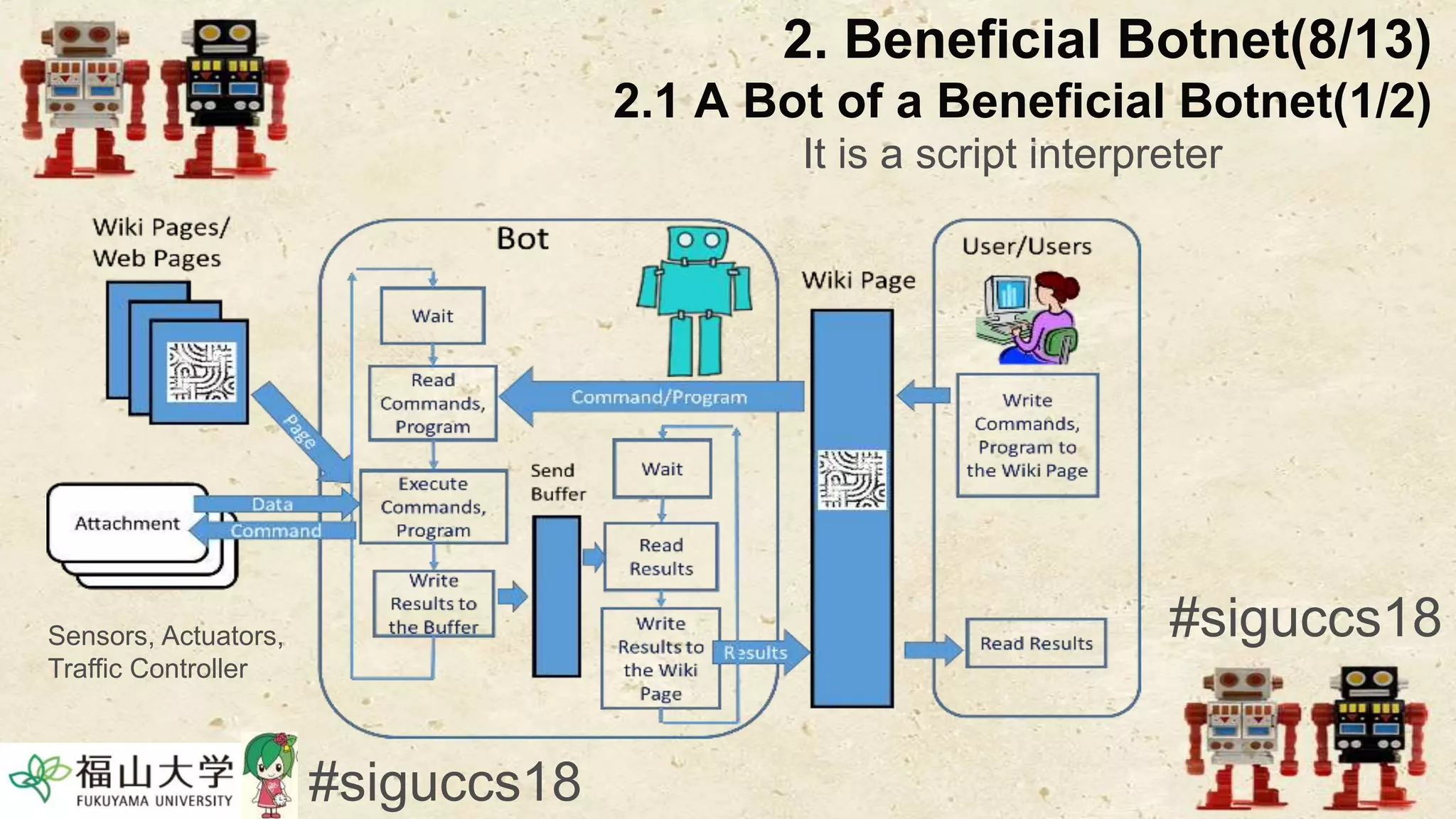
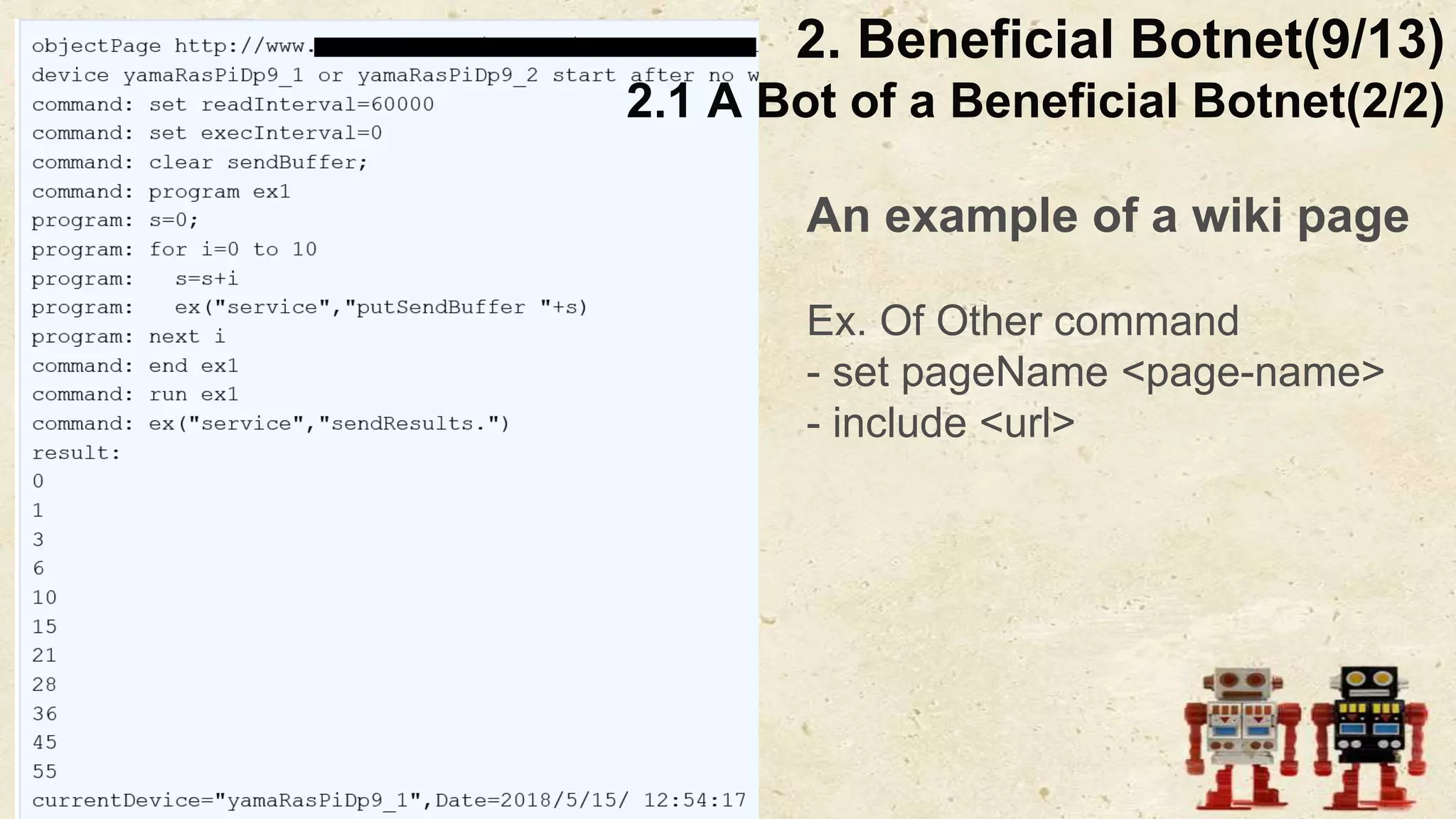
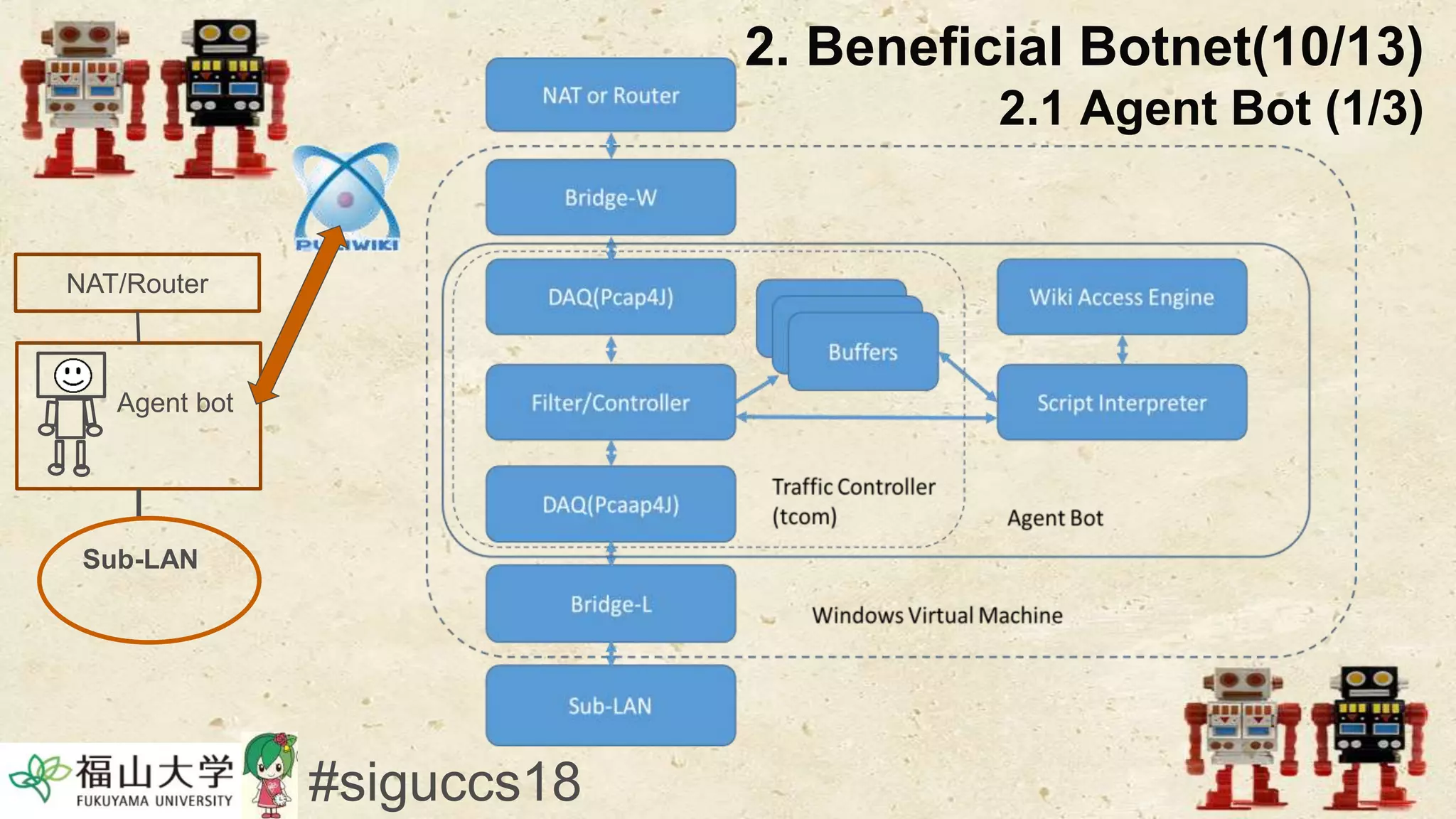
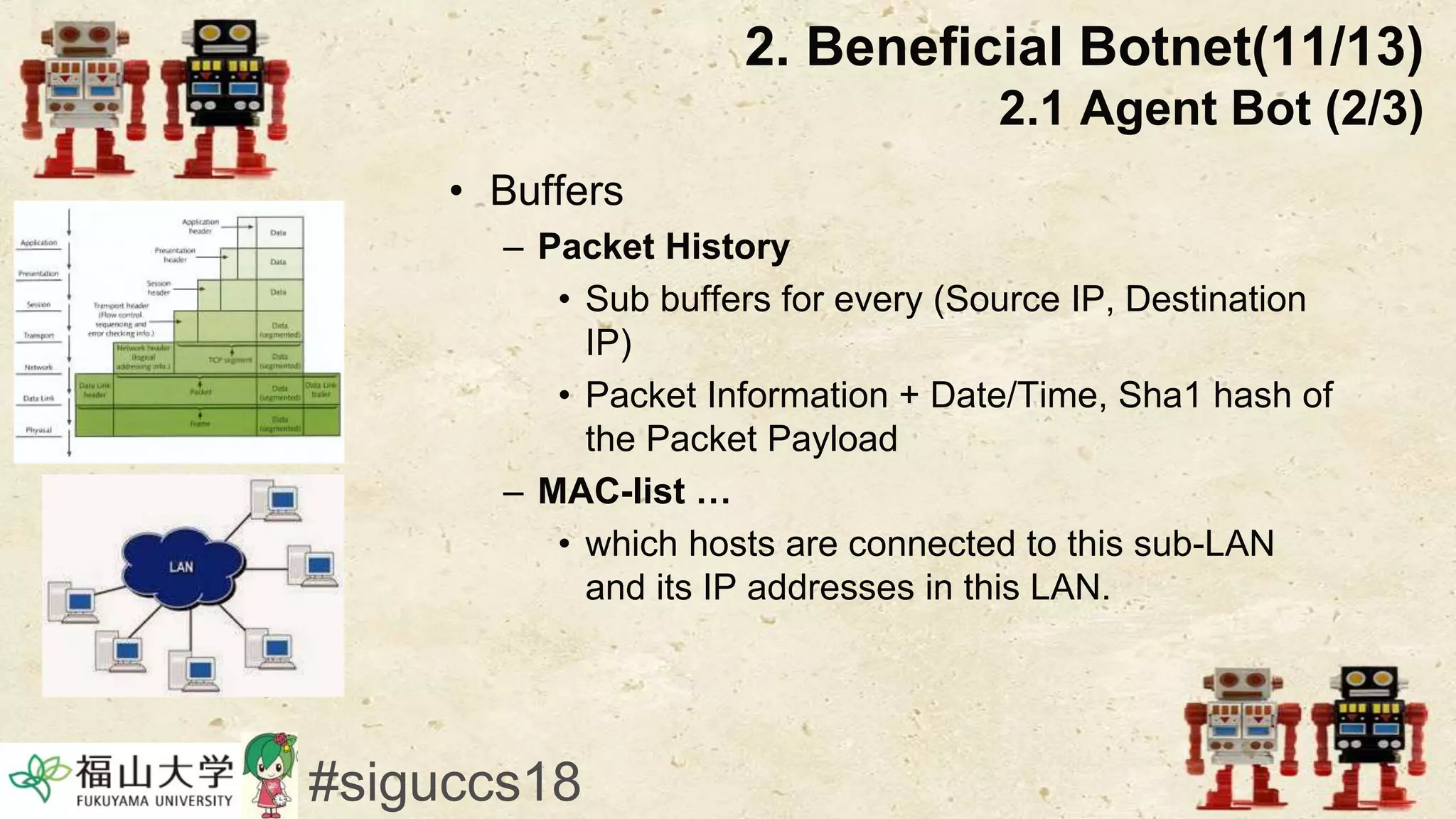
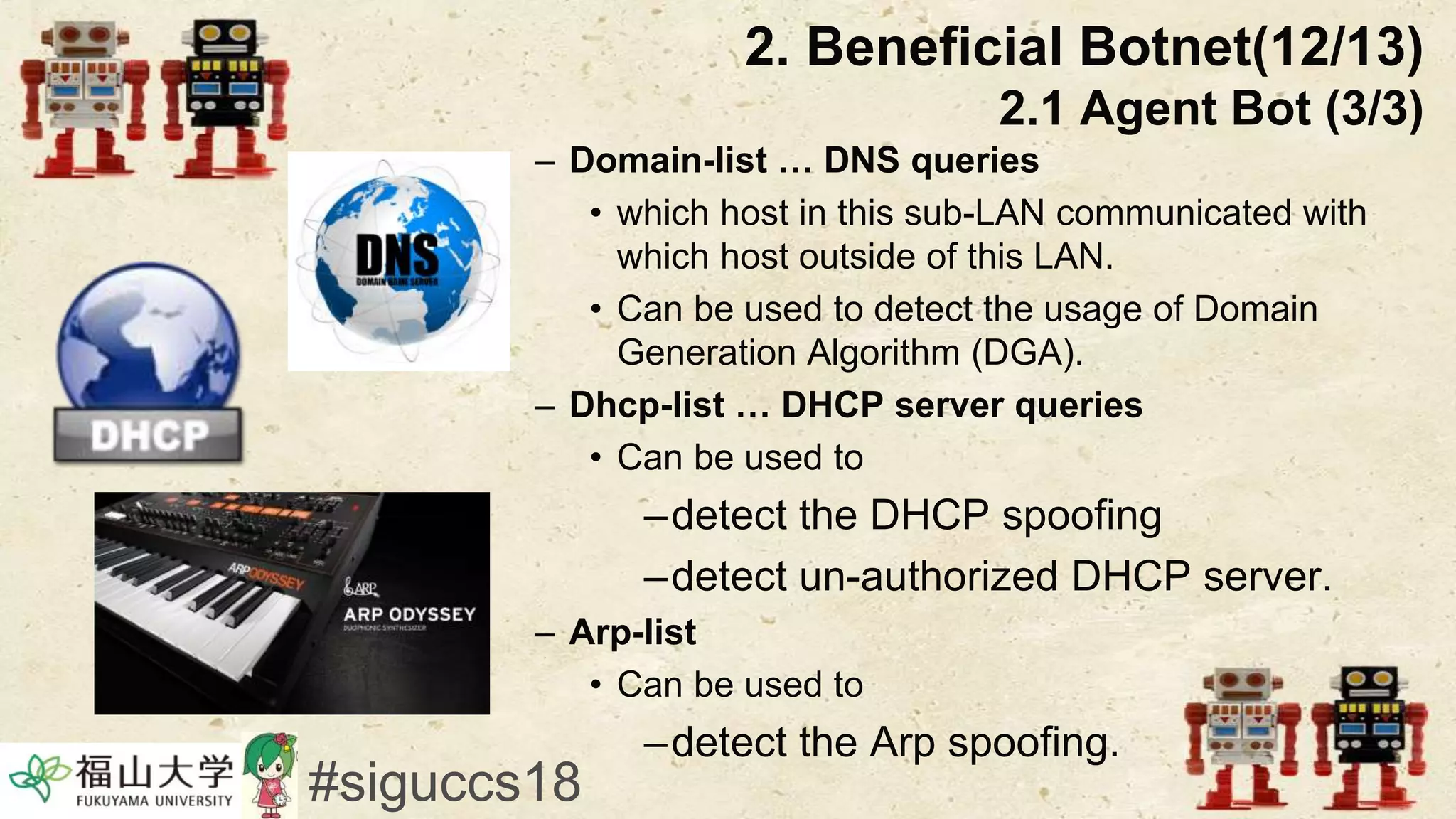
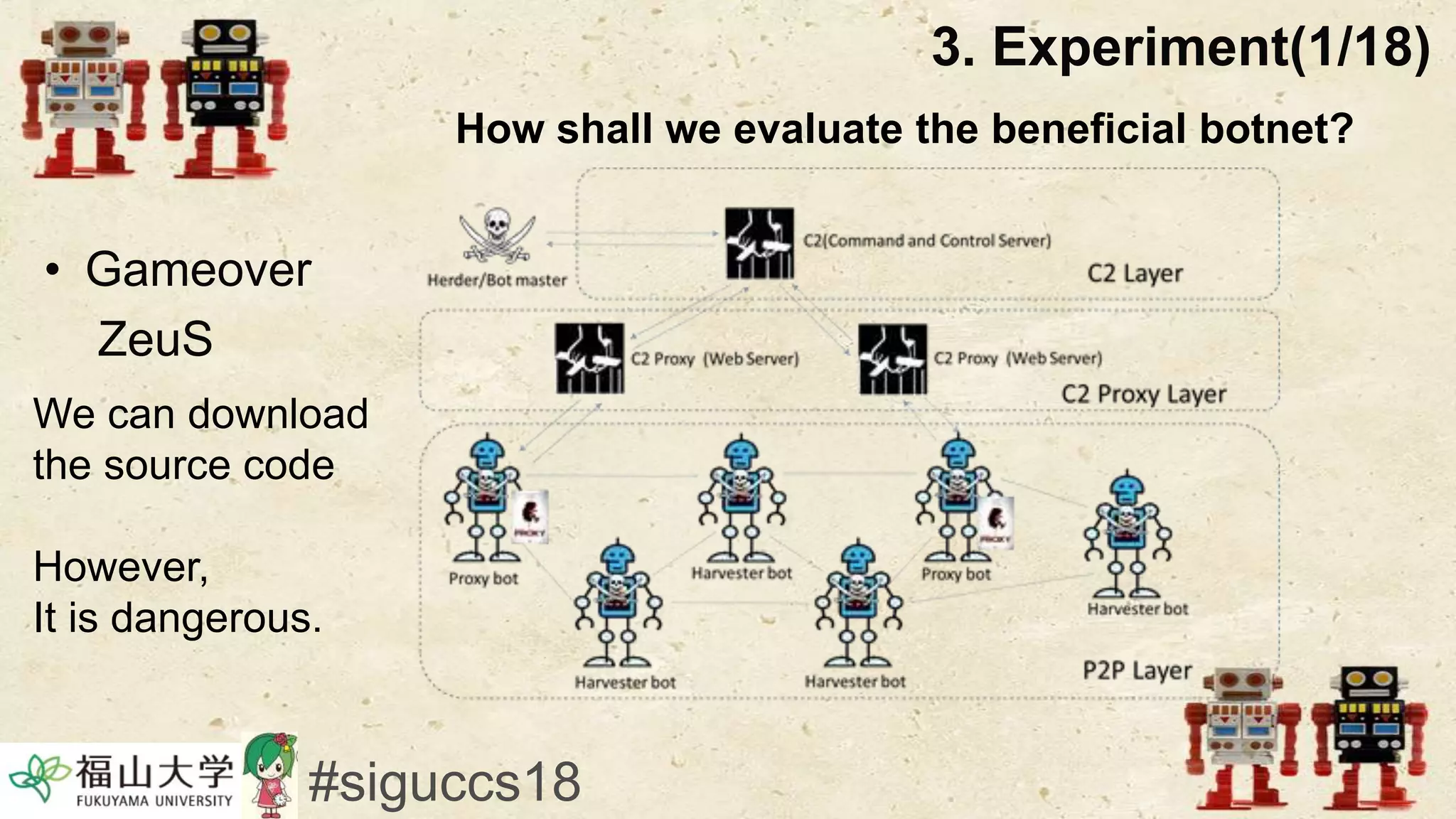
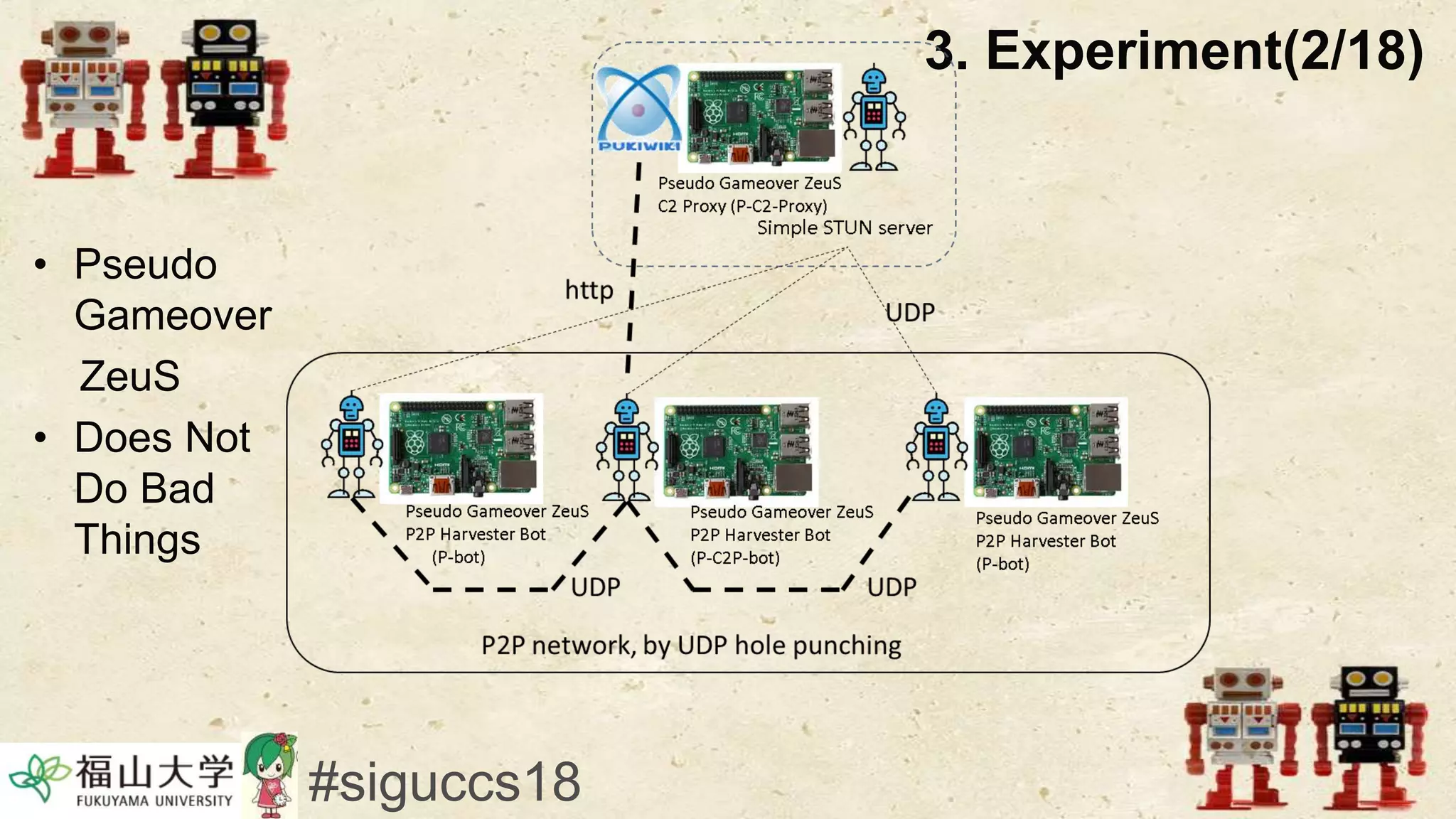
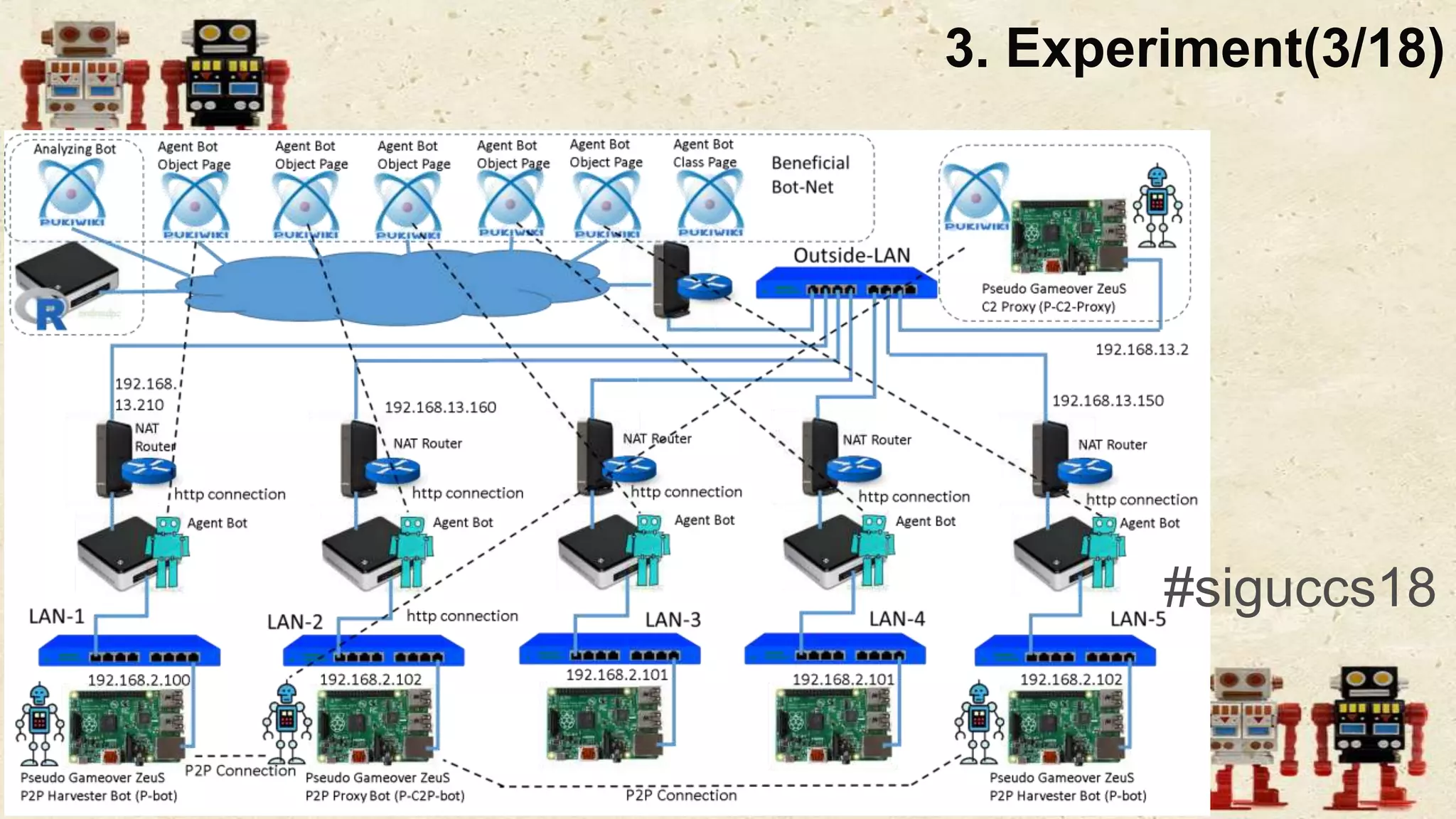
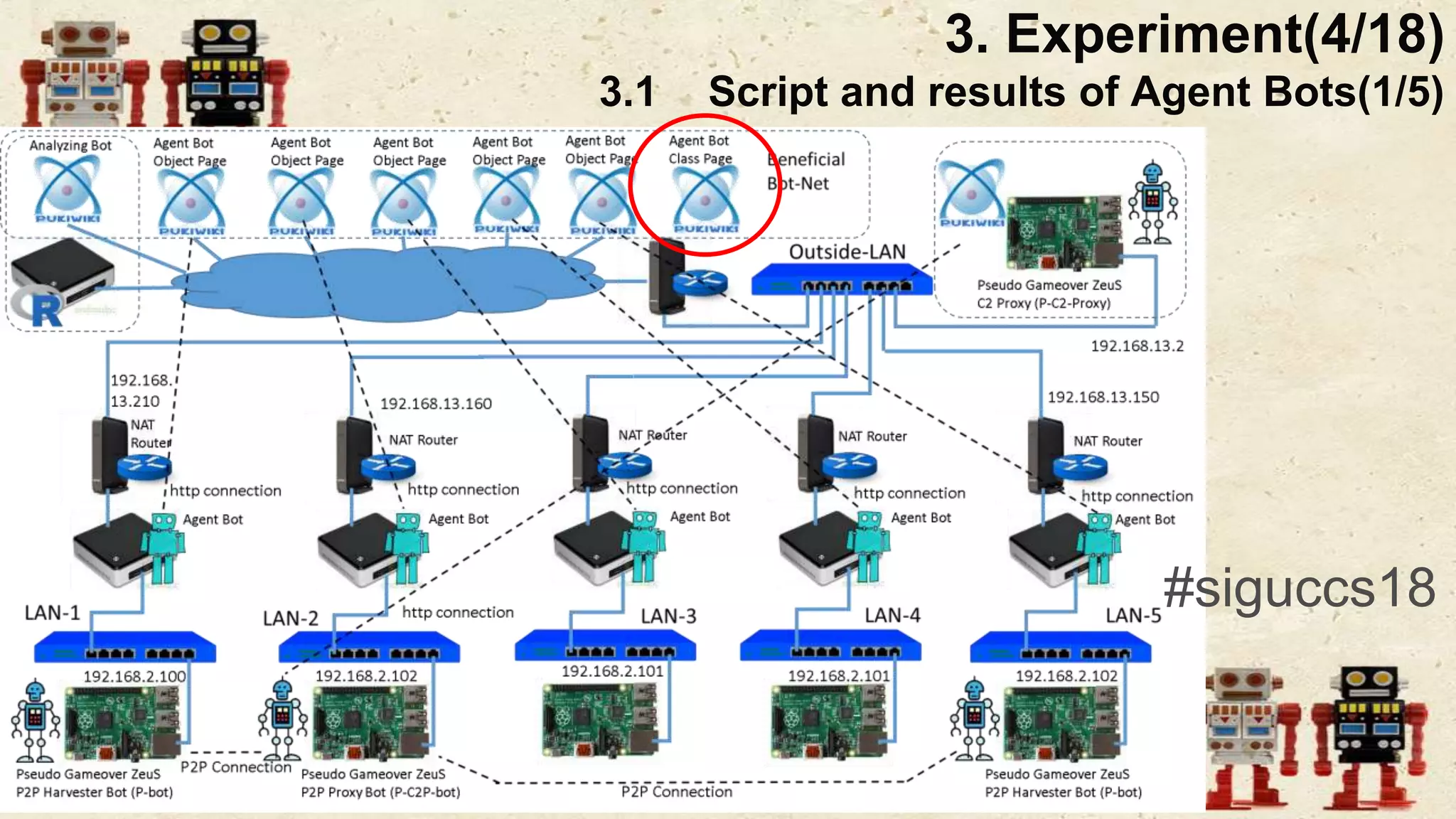
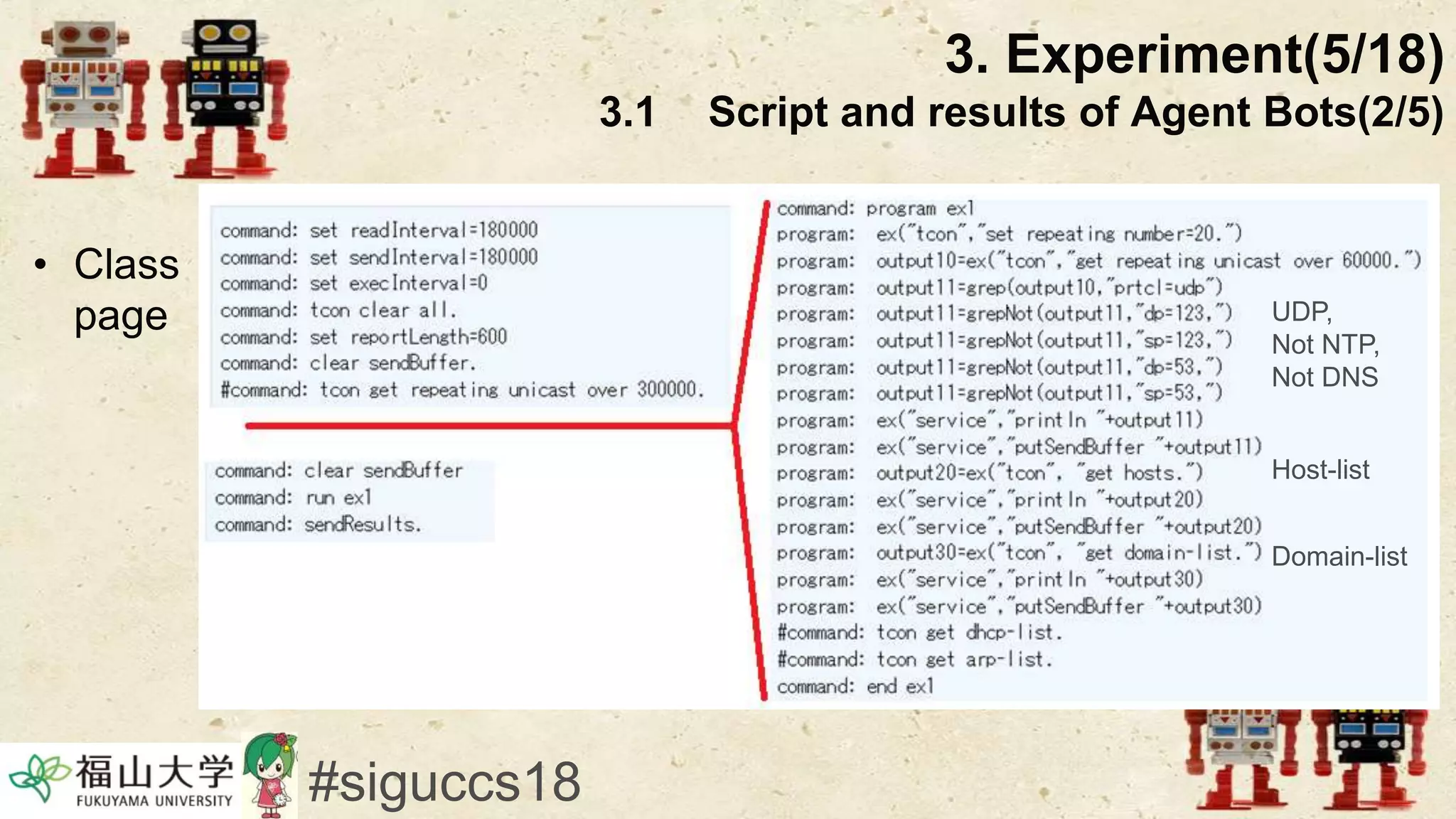
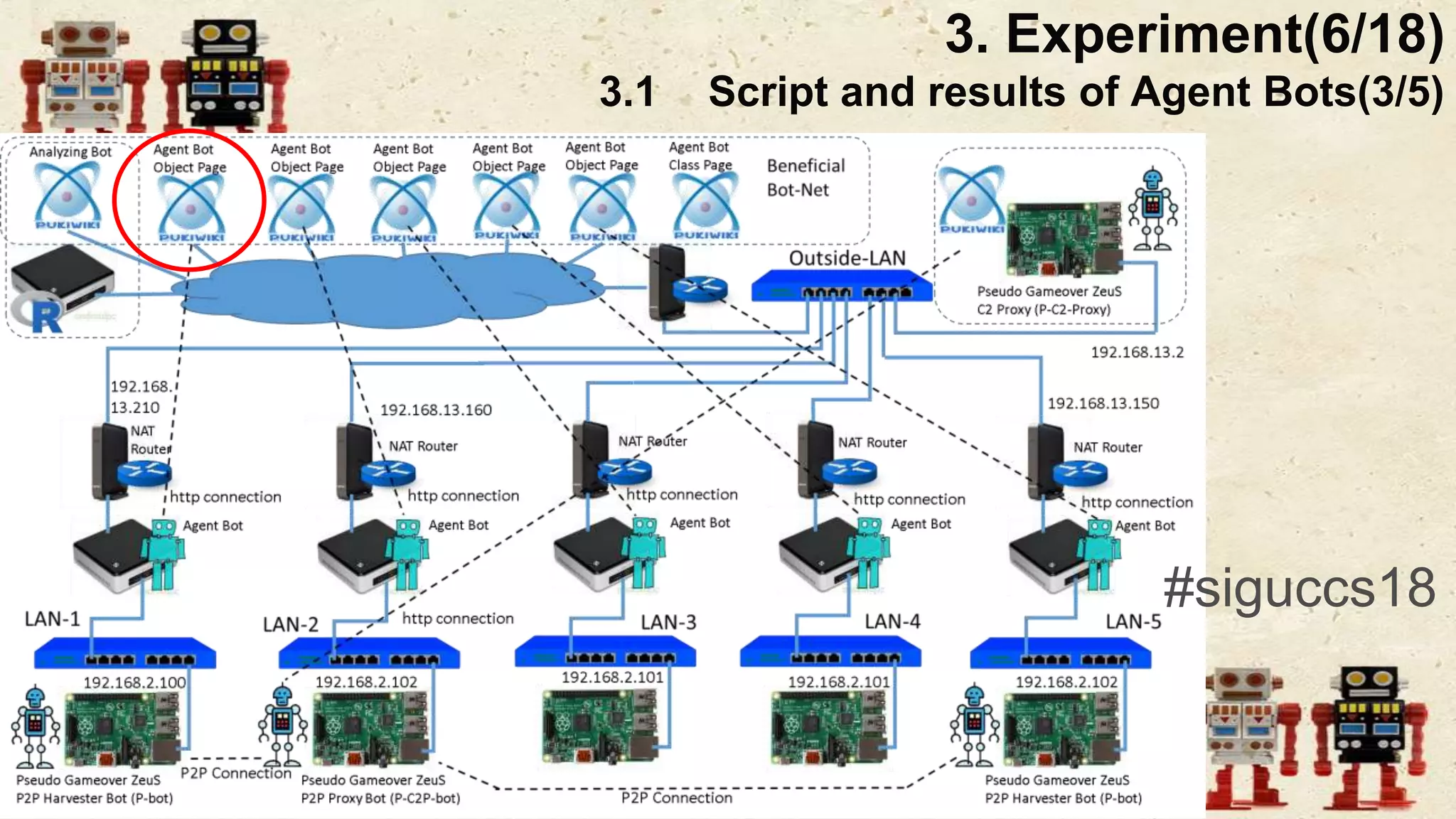
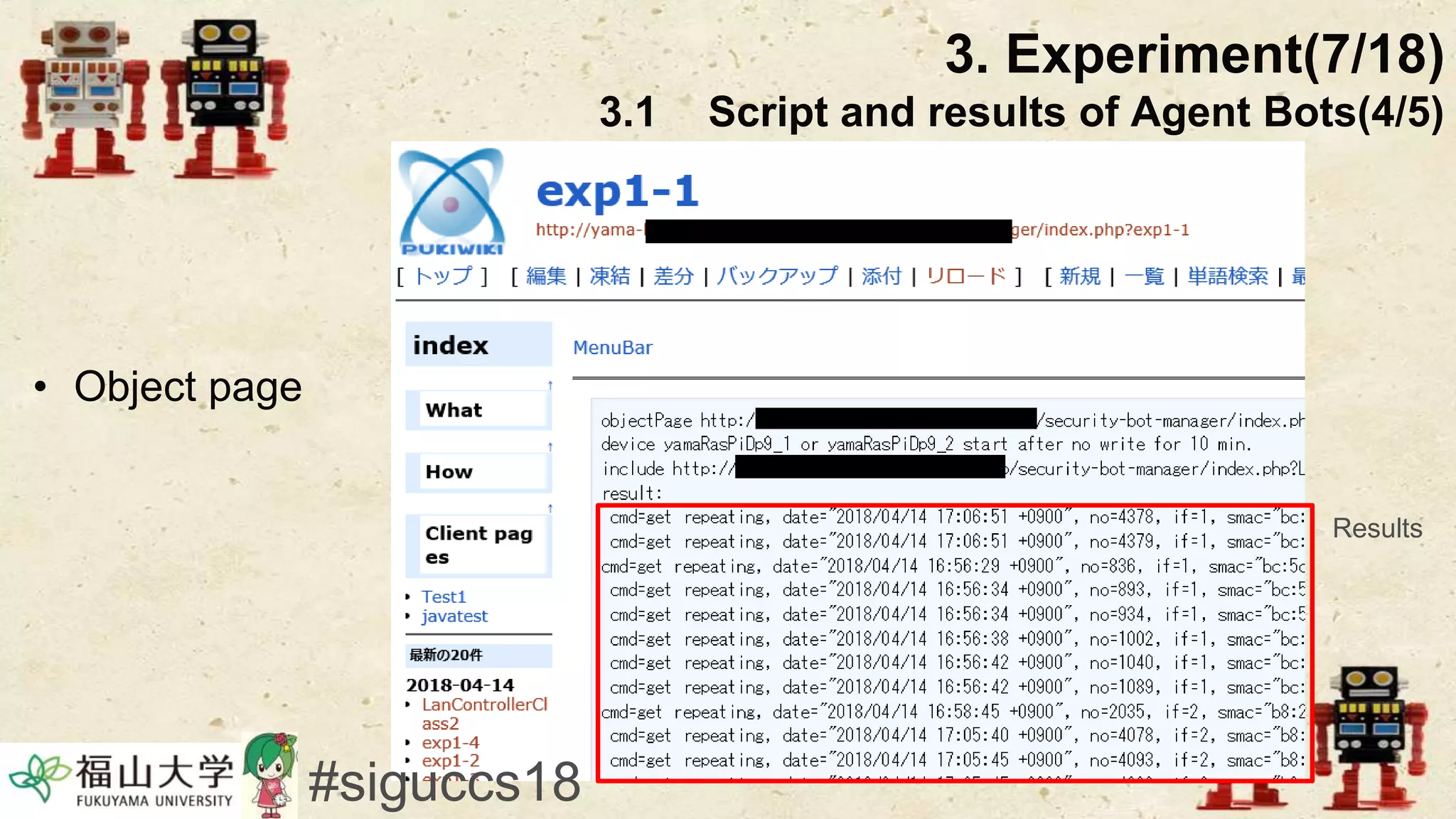
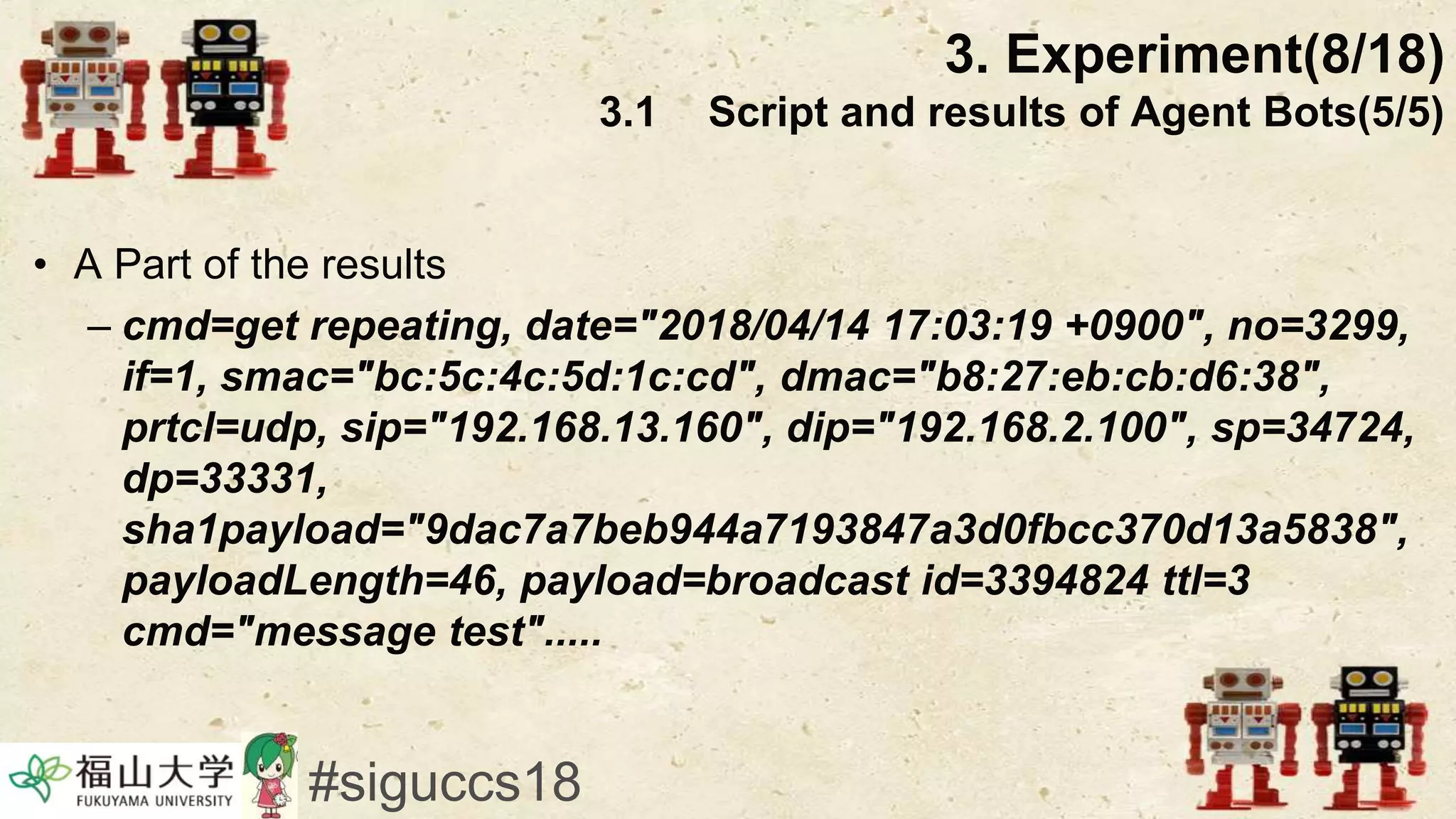
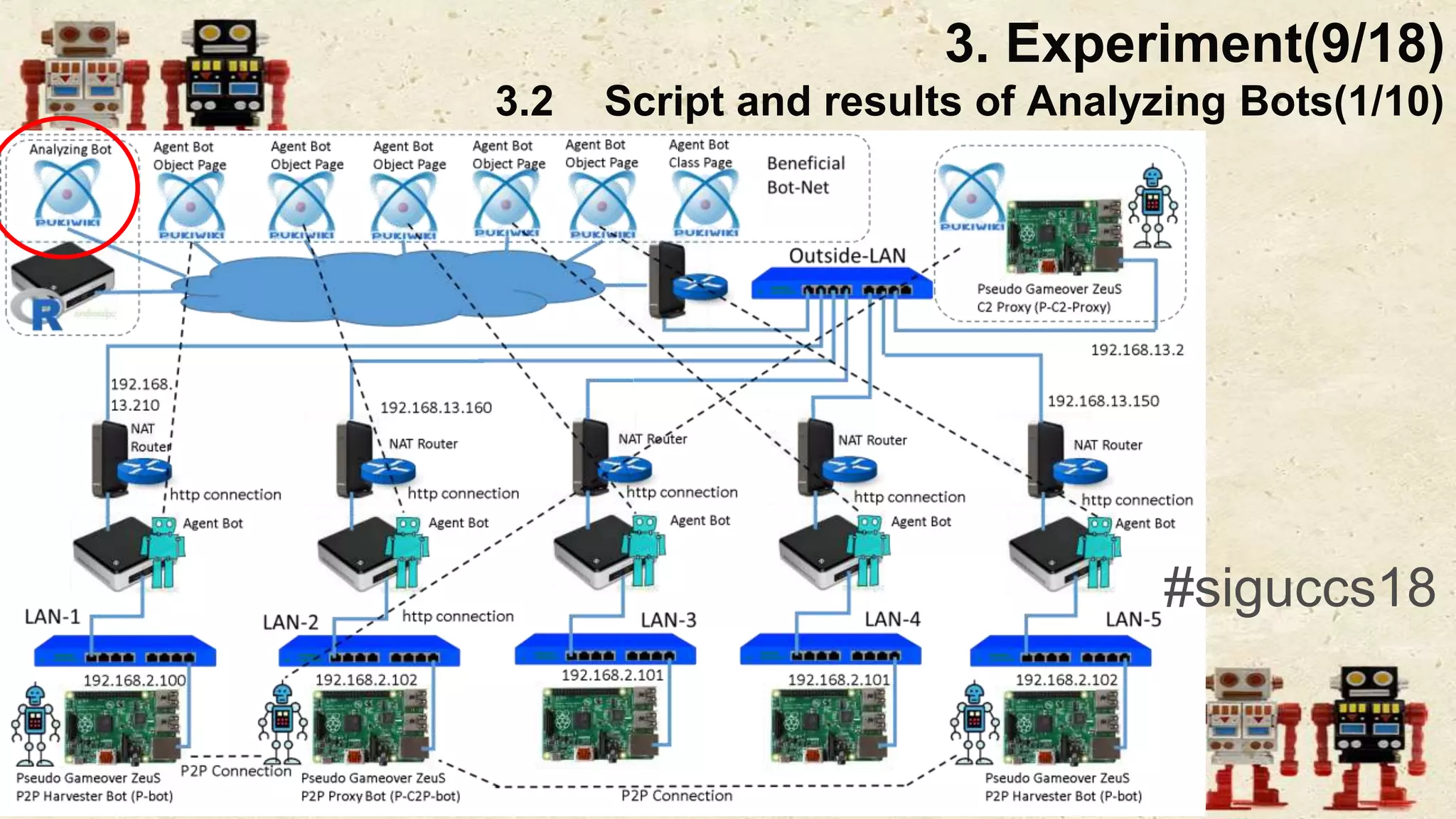
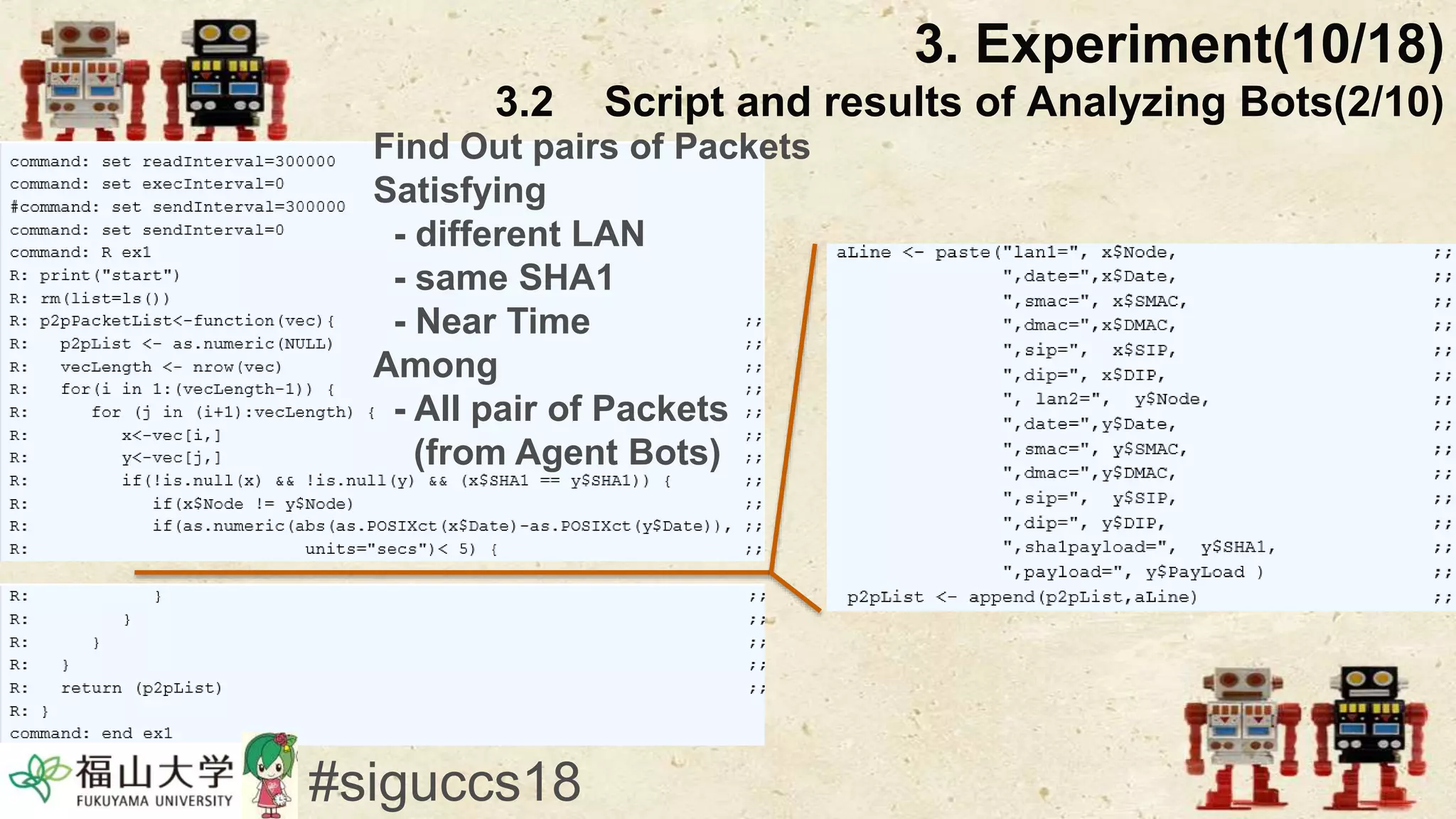
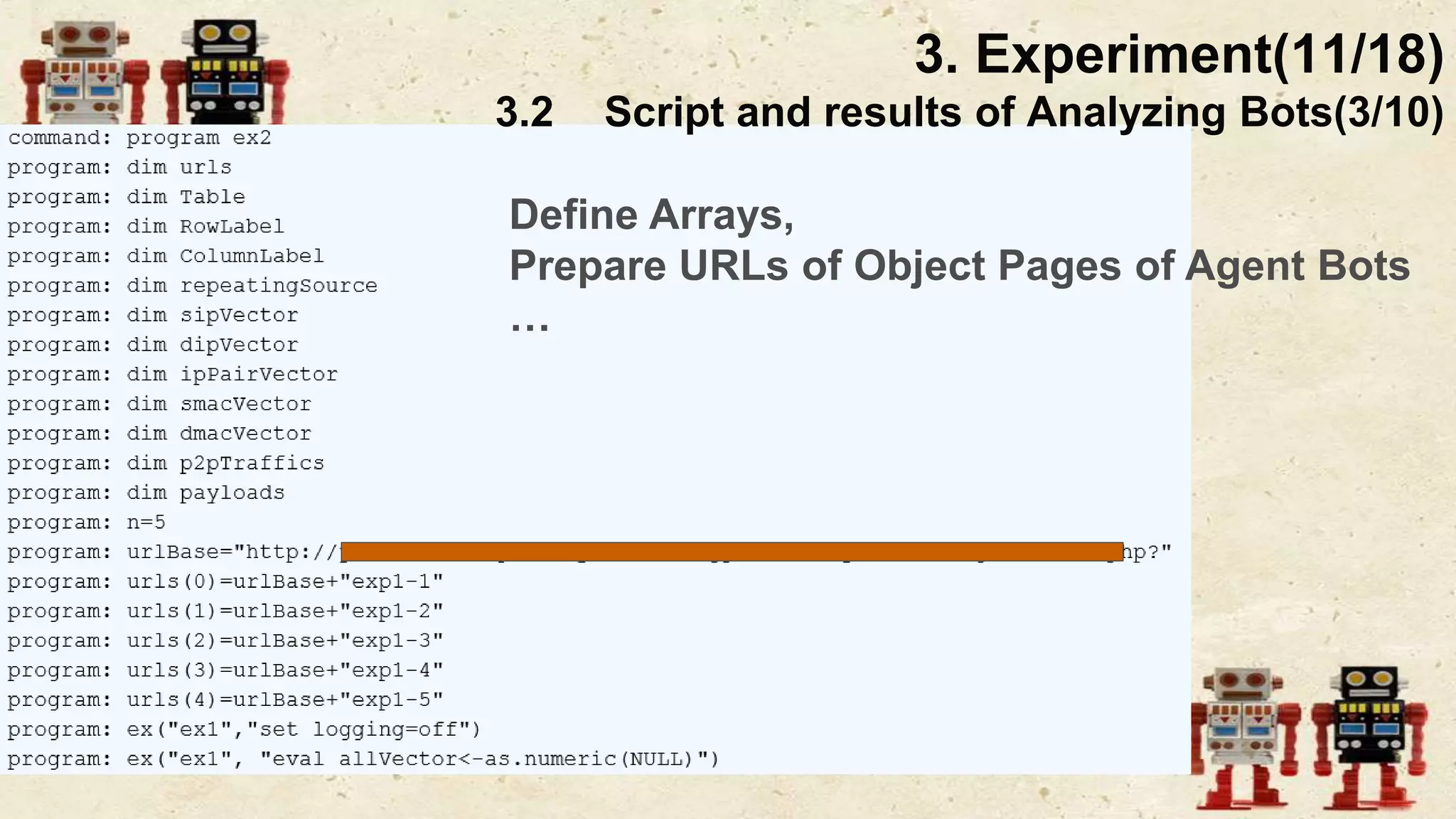
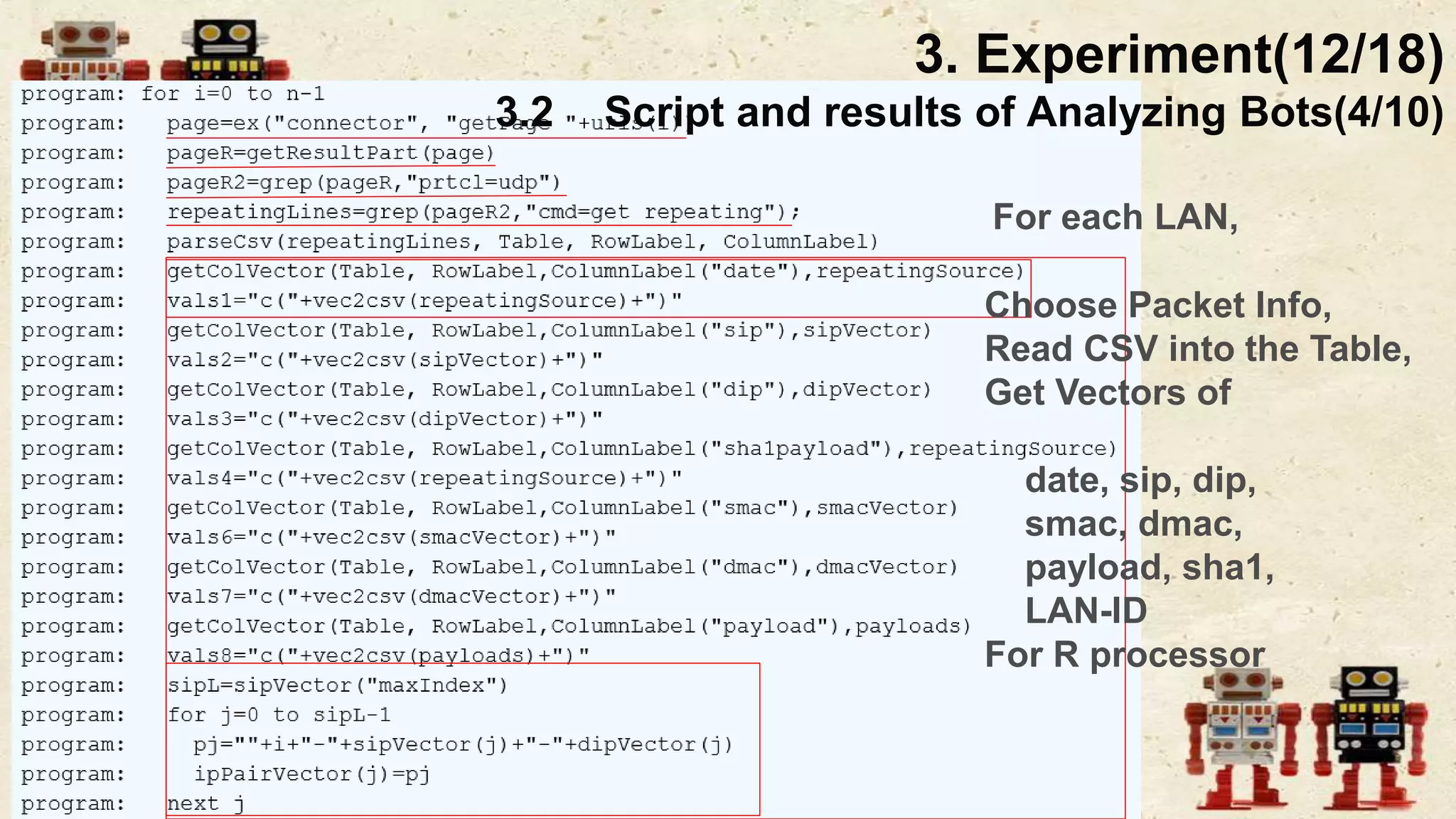
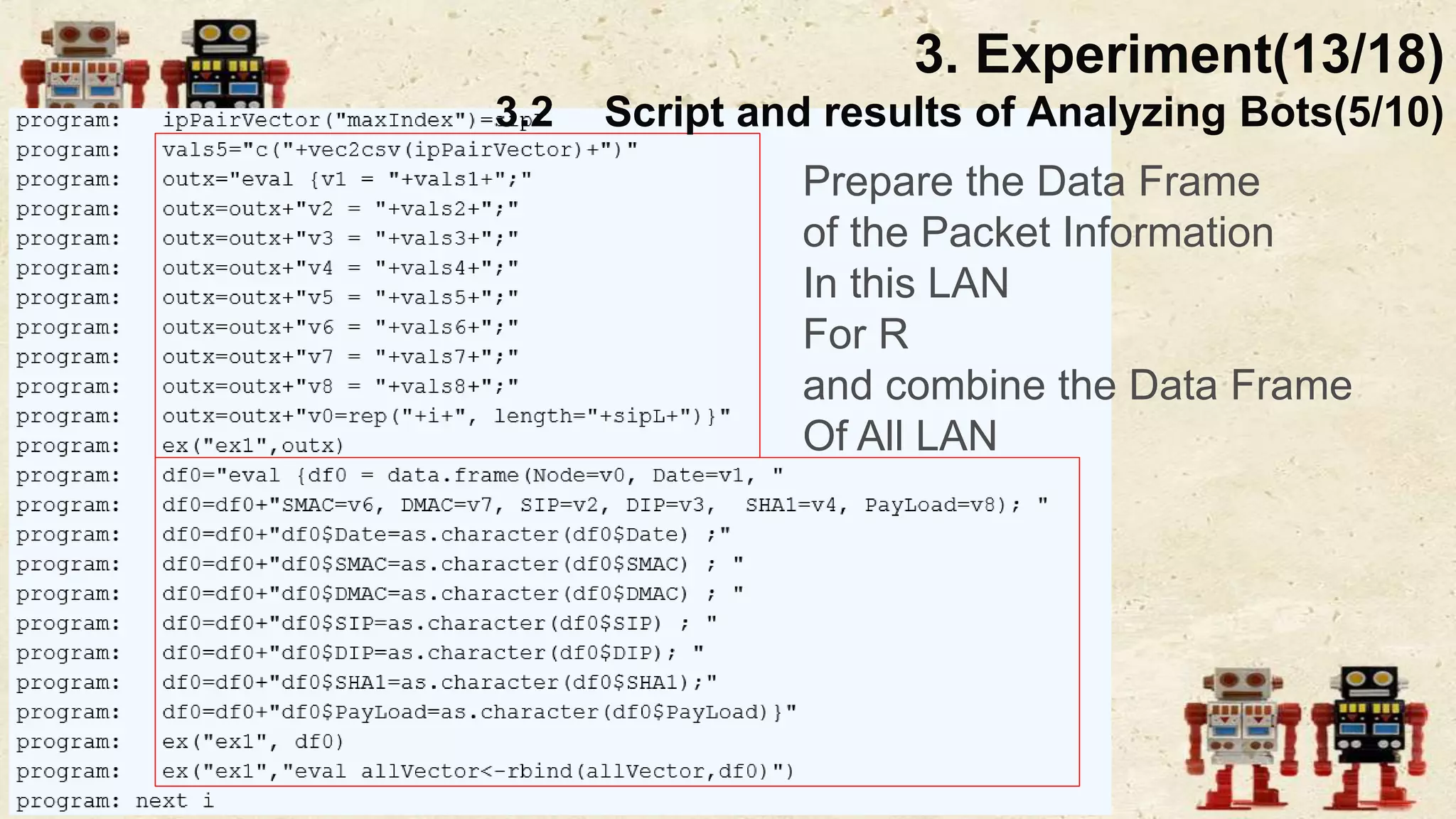
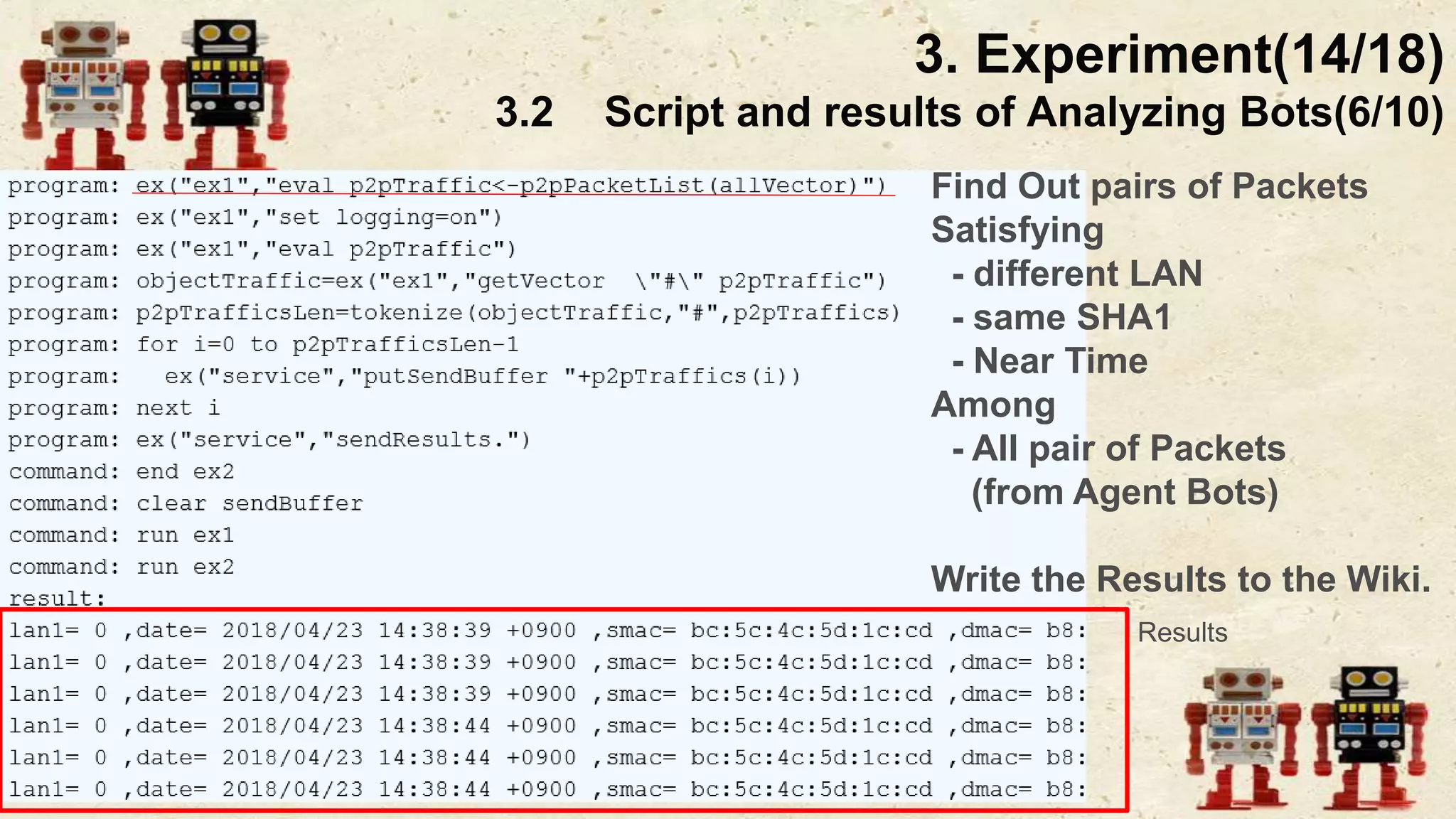
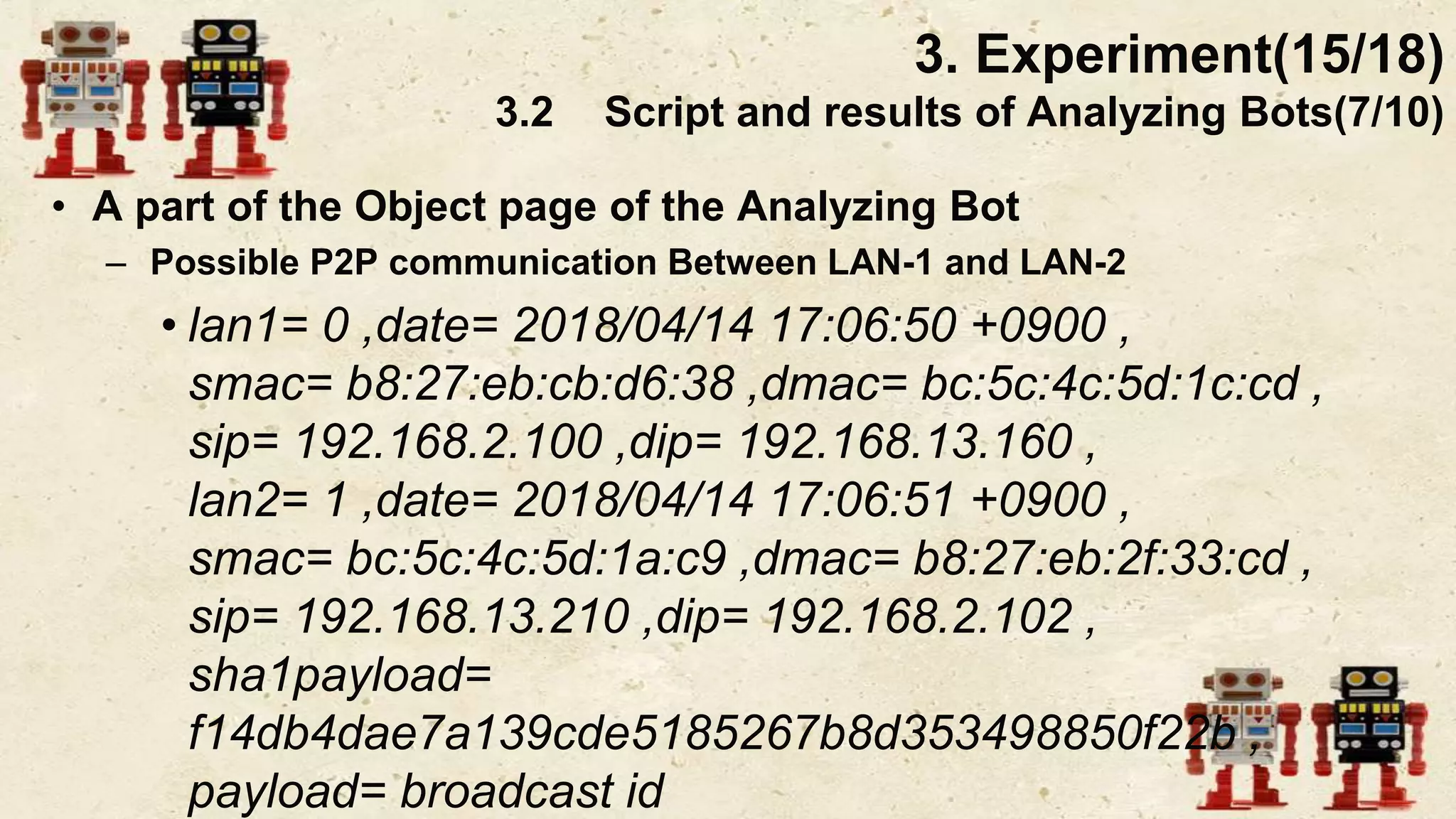
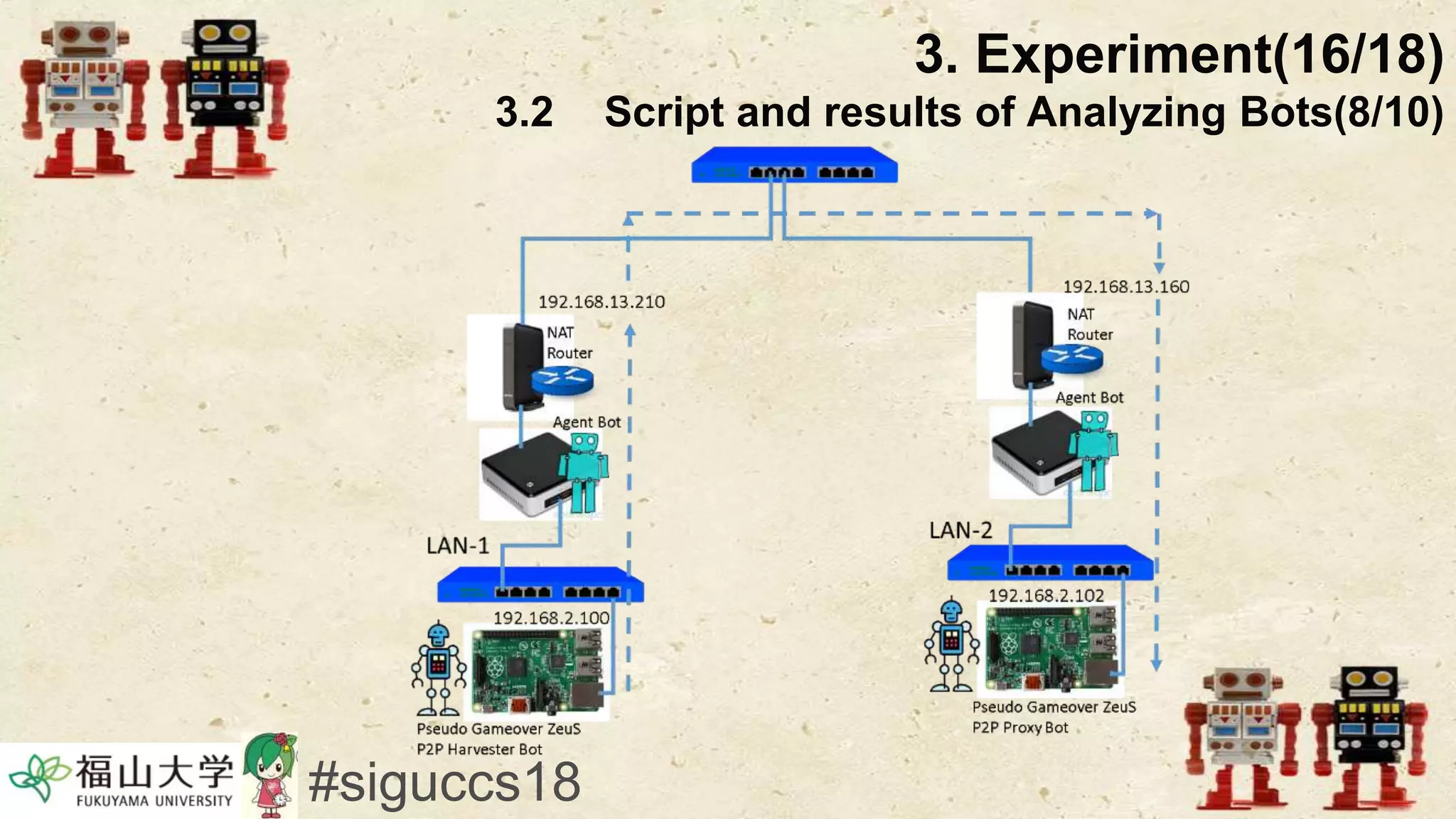
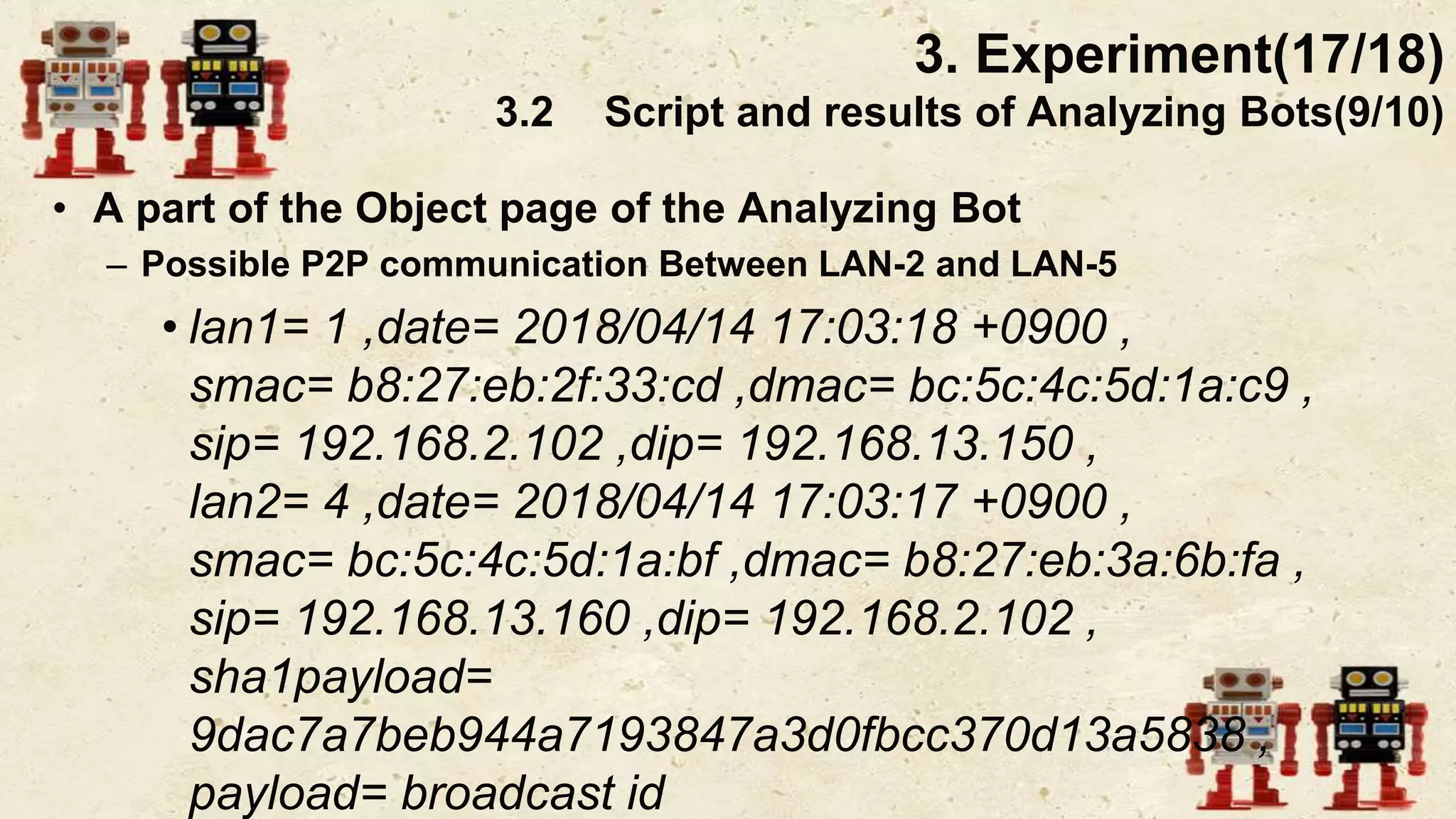
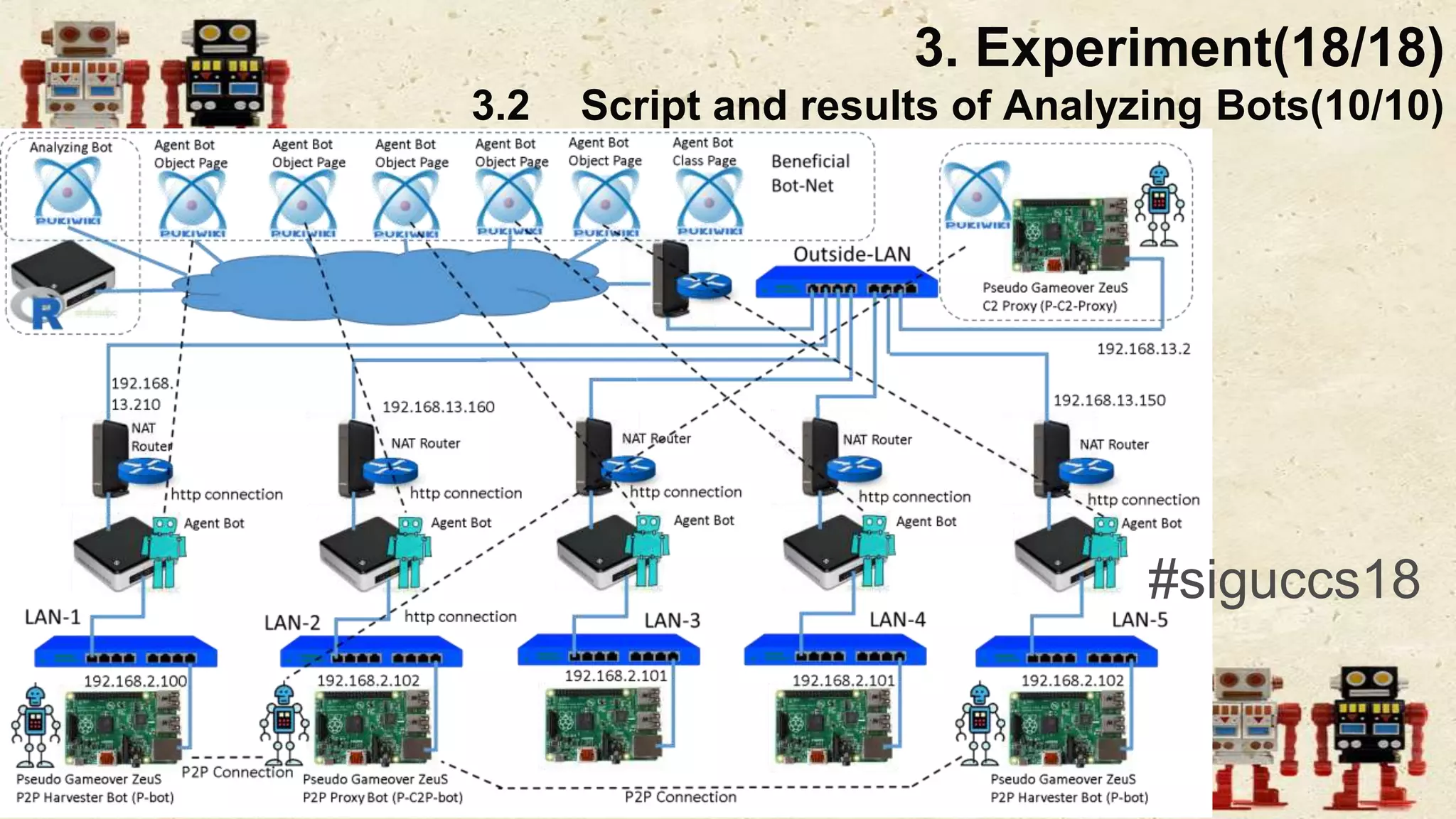
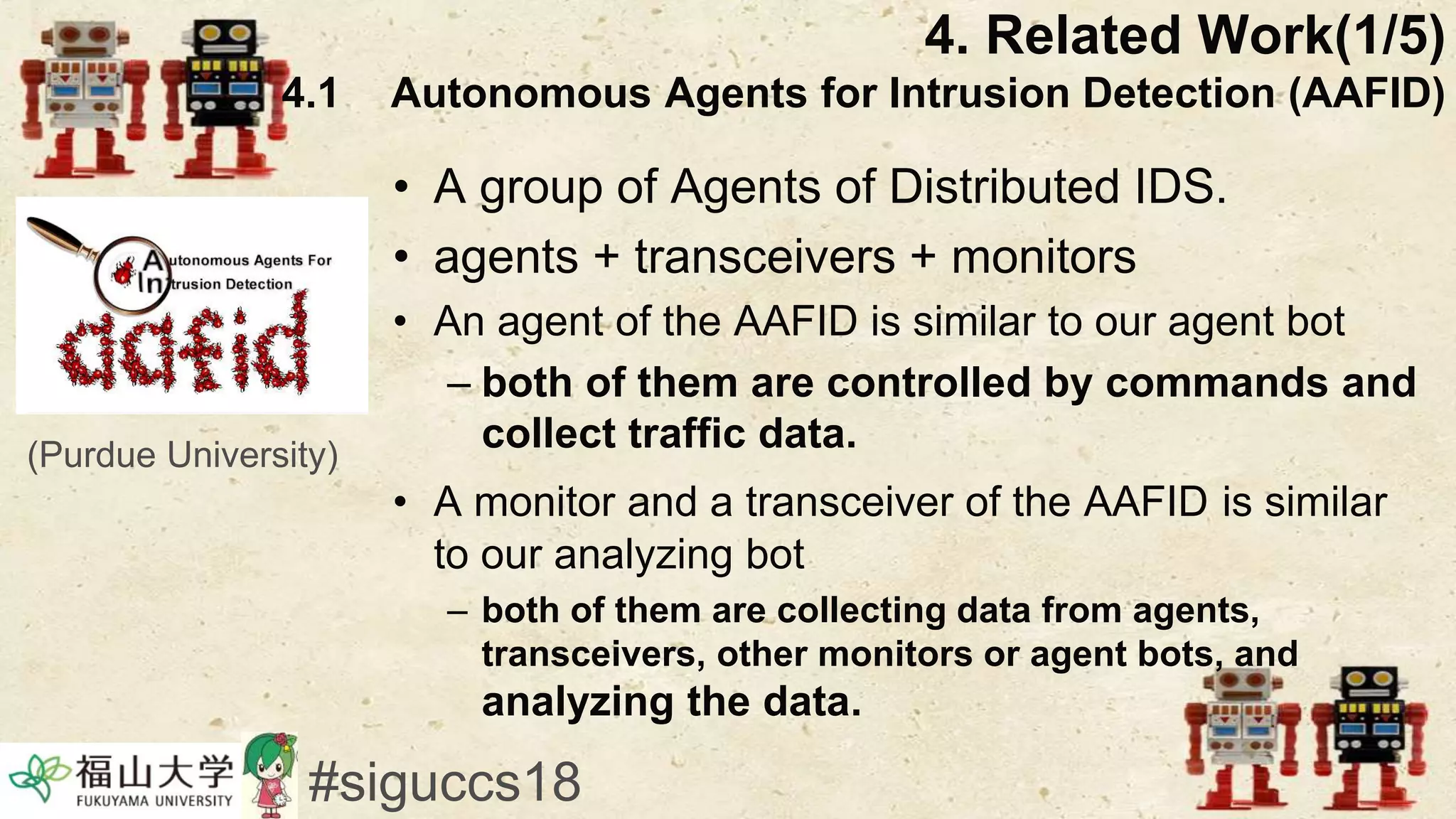
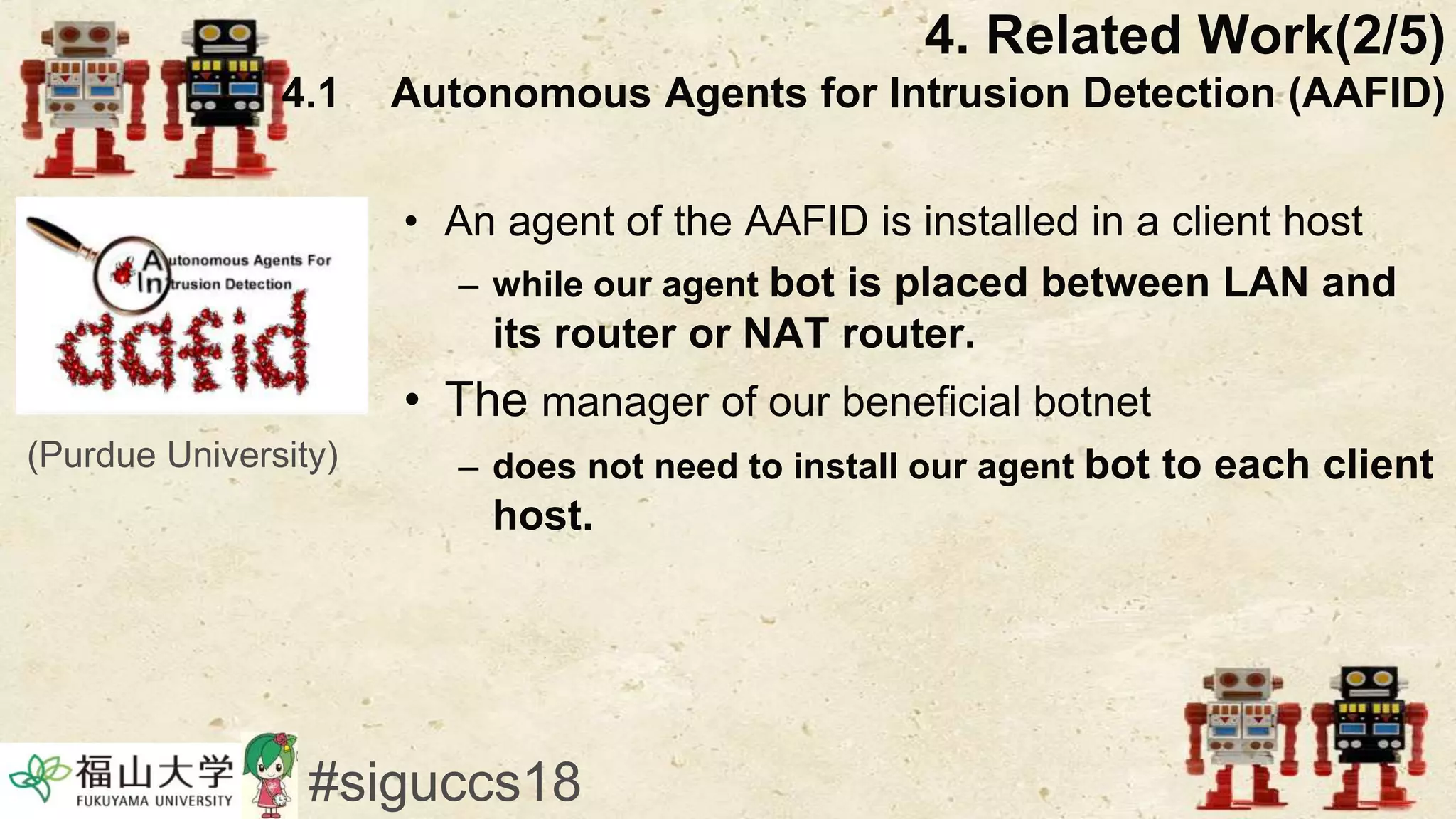
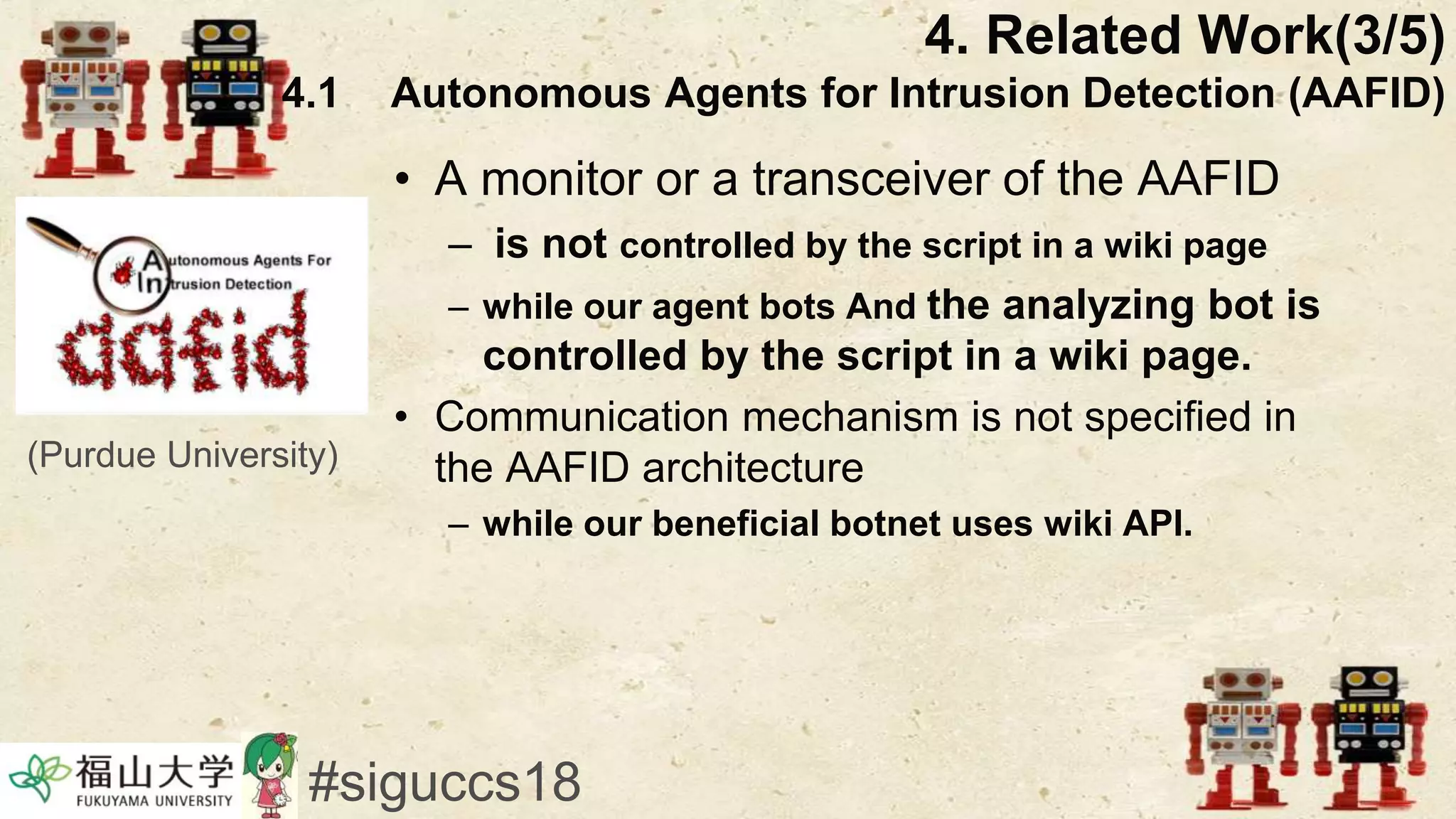
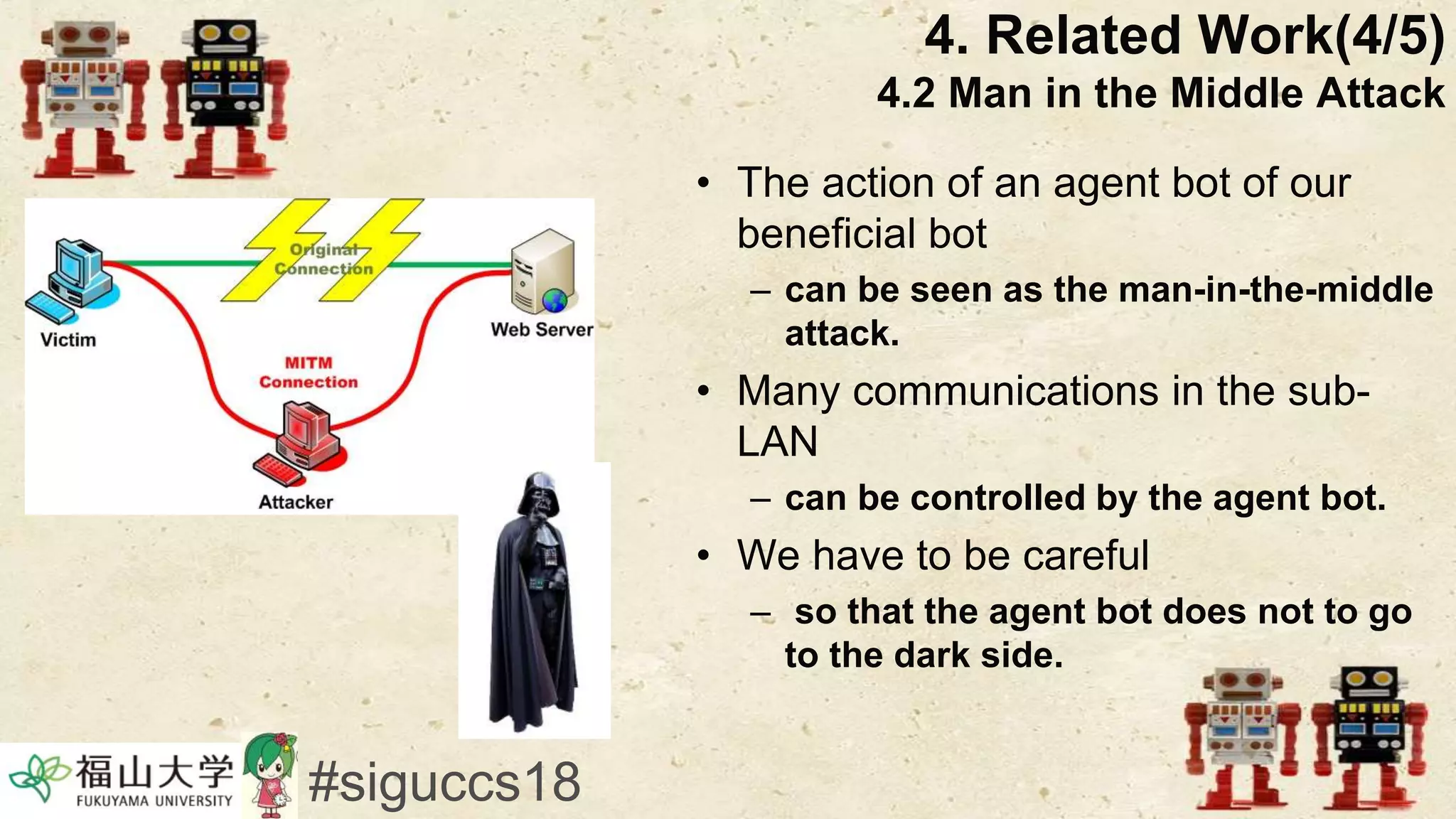
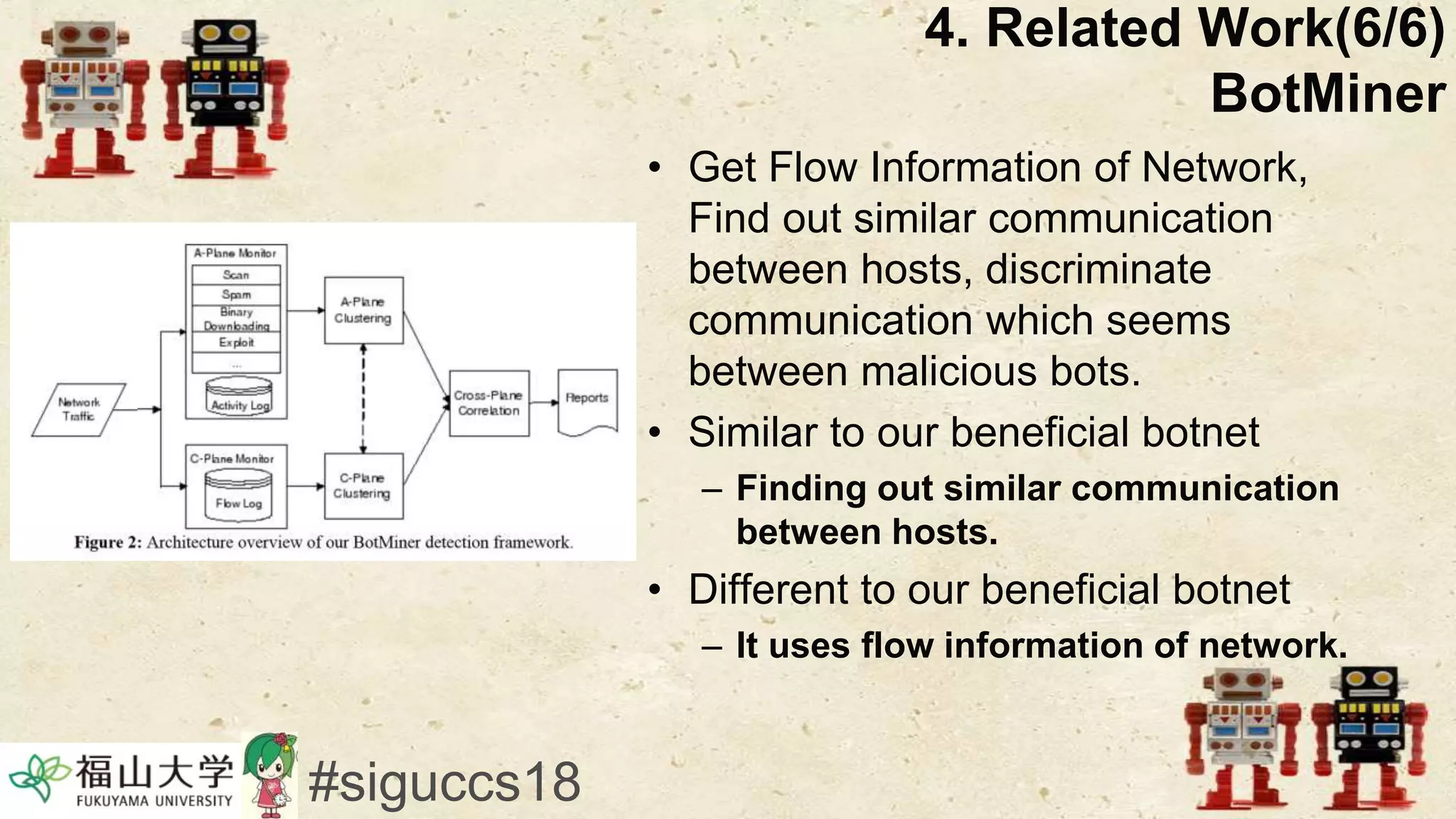
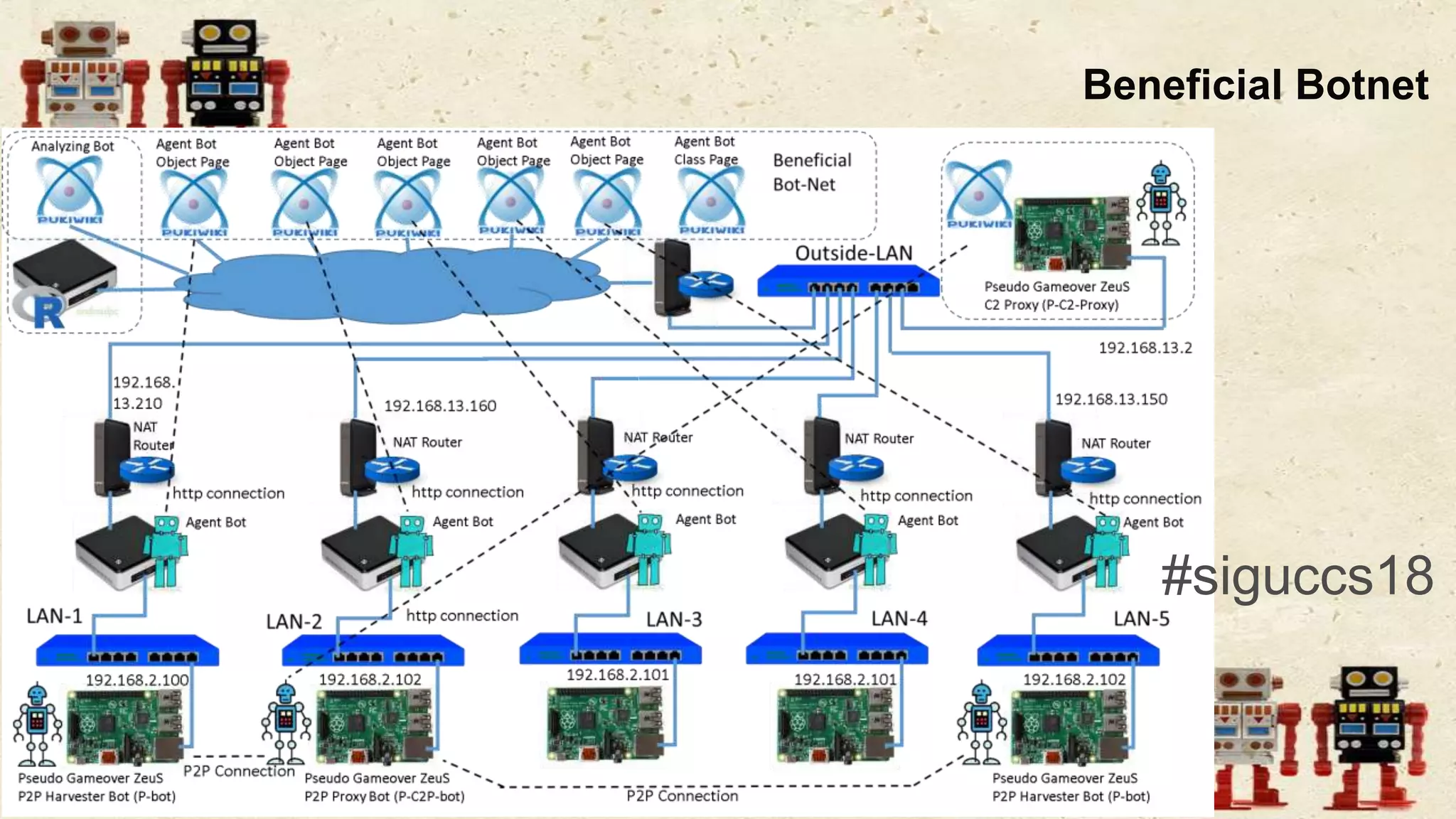
The document presents a beneficial botnet framework aimed at detecting malicious peer-to-peer botnets by utilizing a network of agent and analyzing bots to monitor and analyze communication within local area networks. It discusses the evolution and challenges posed by malicious botnets, particularly those employing decentralized communication techniques. Experimental results demonstrate the beneficial botnet's capability to identify and respond to potential threats while highlighting the need for improvements in speed and security.