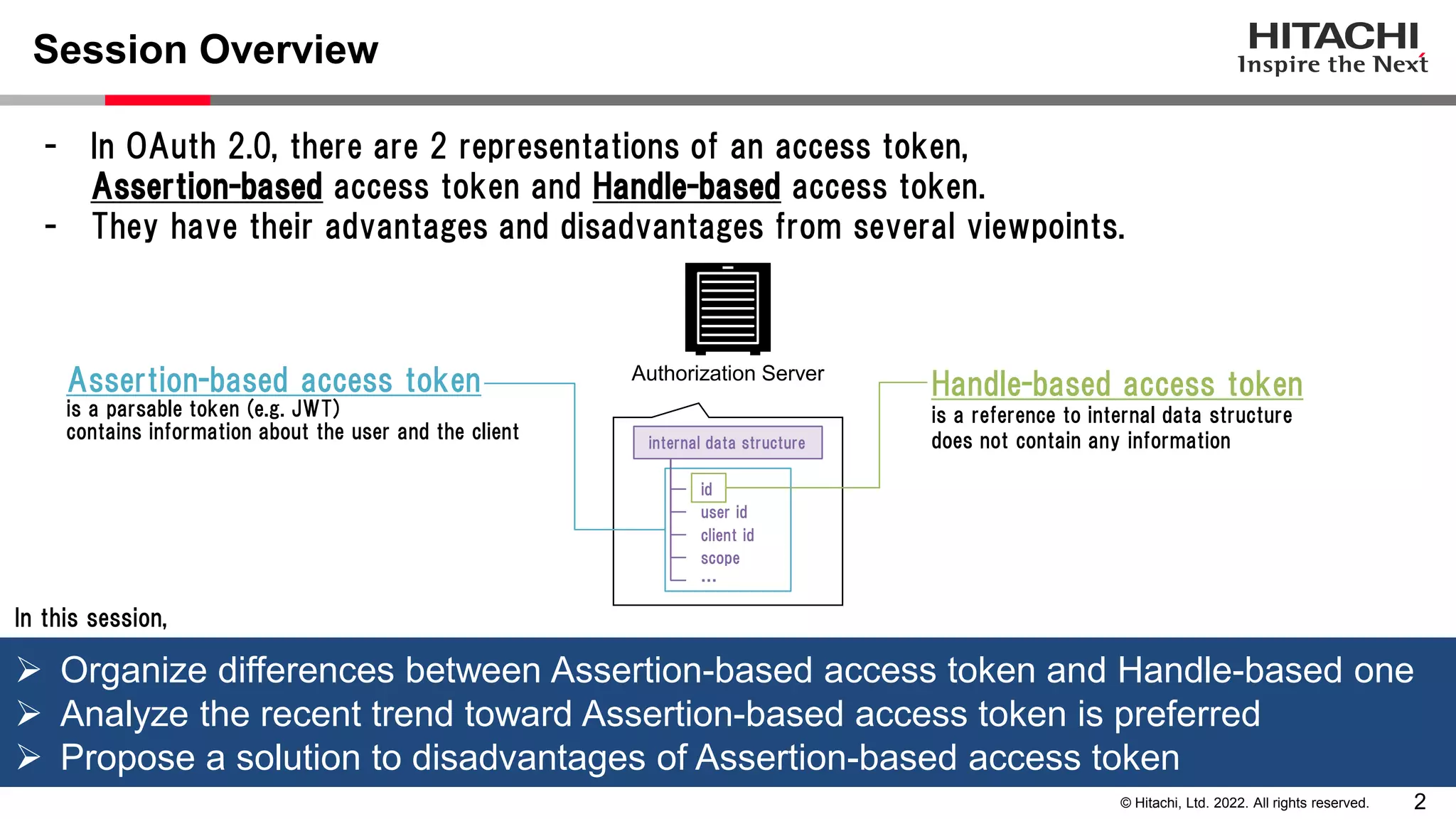
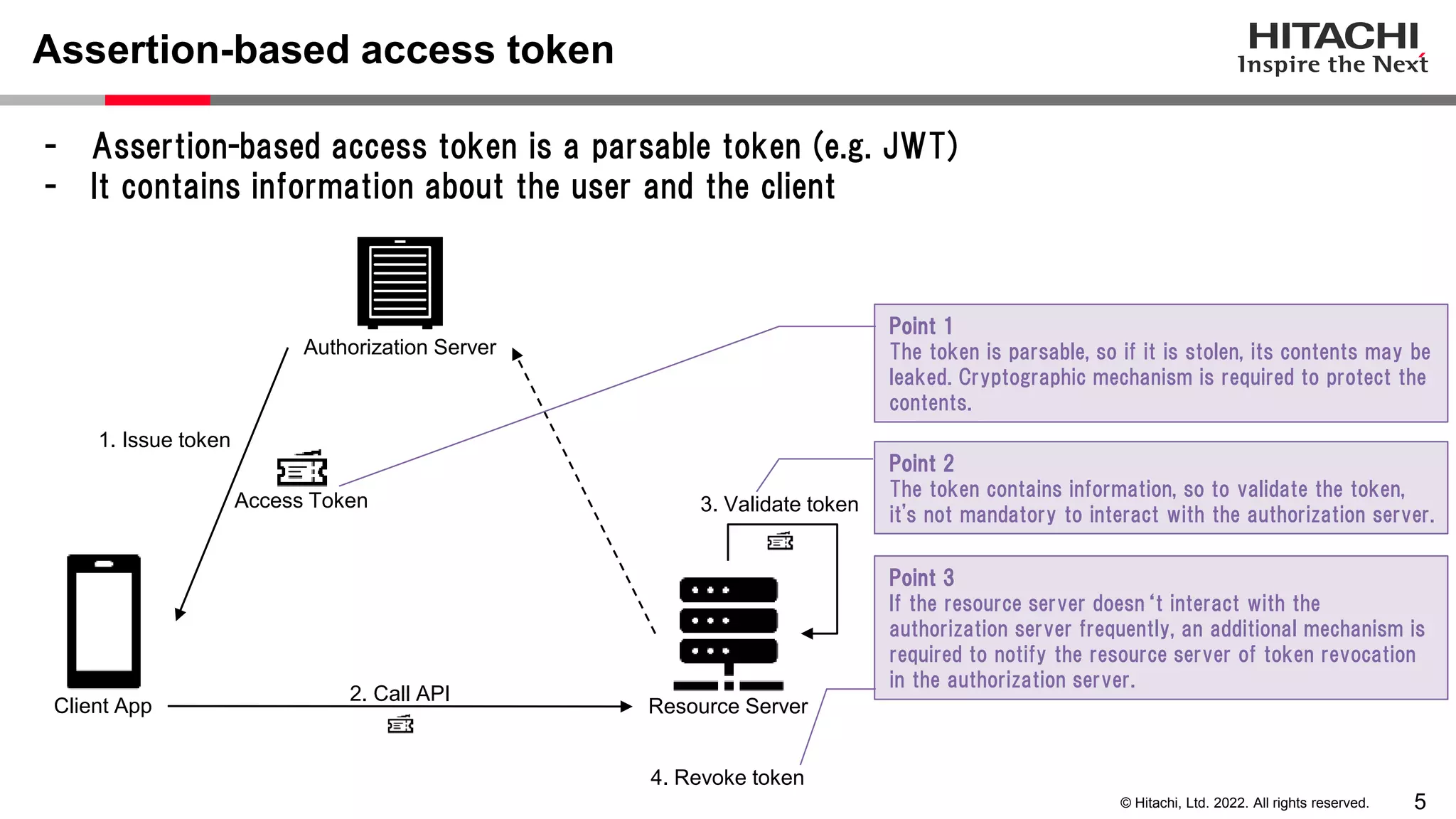
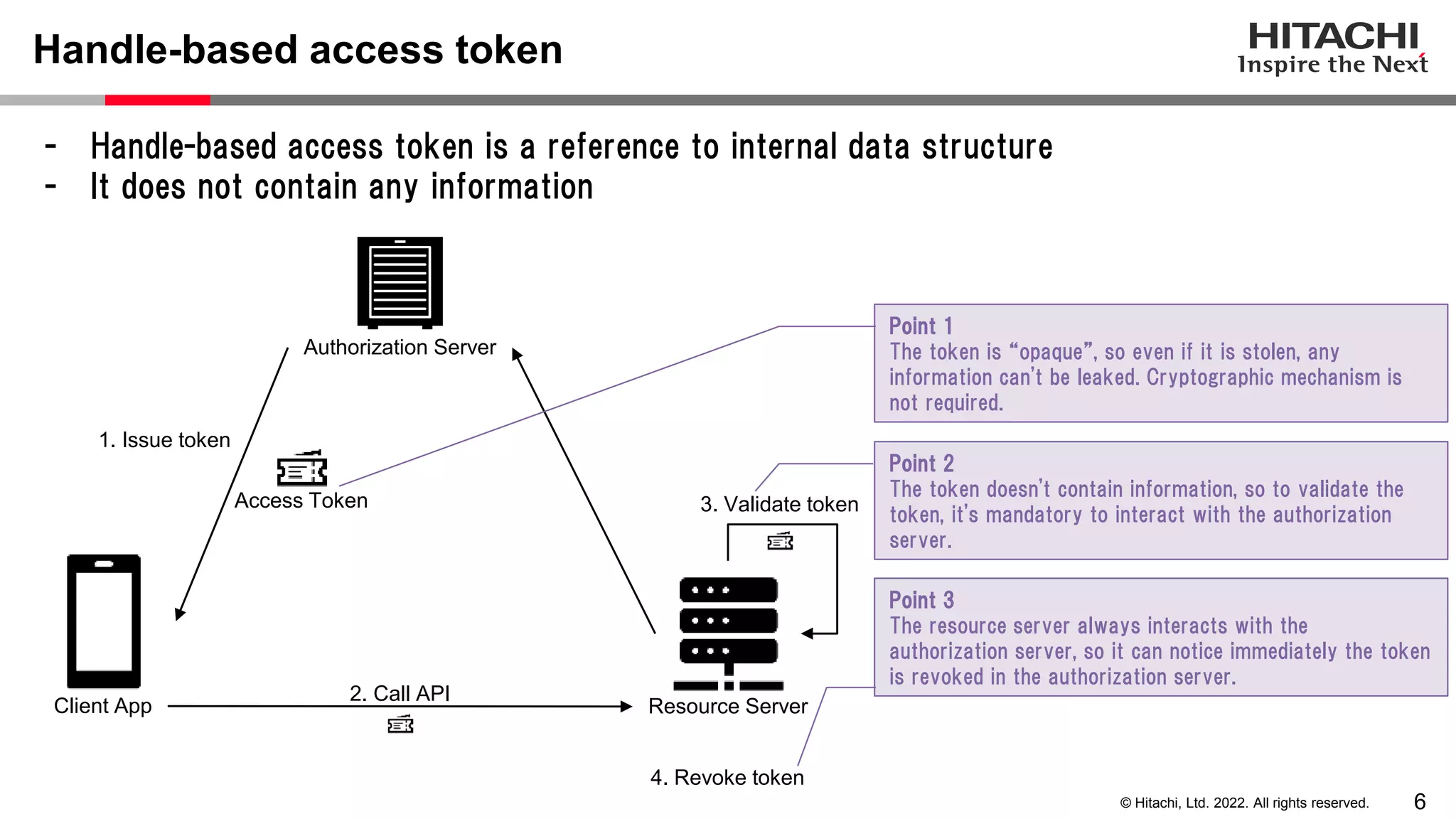
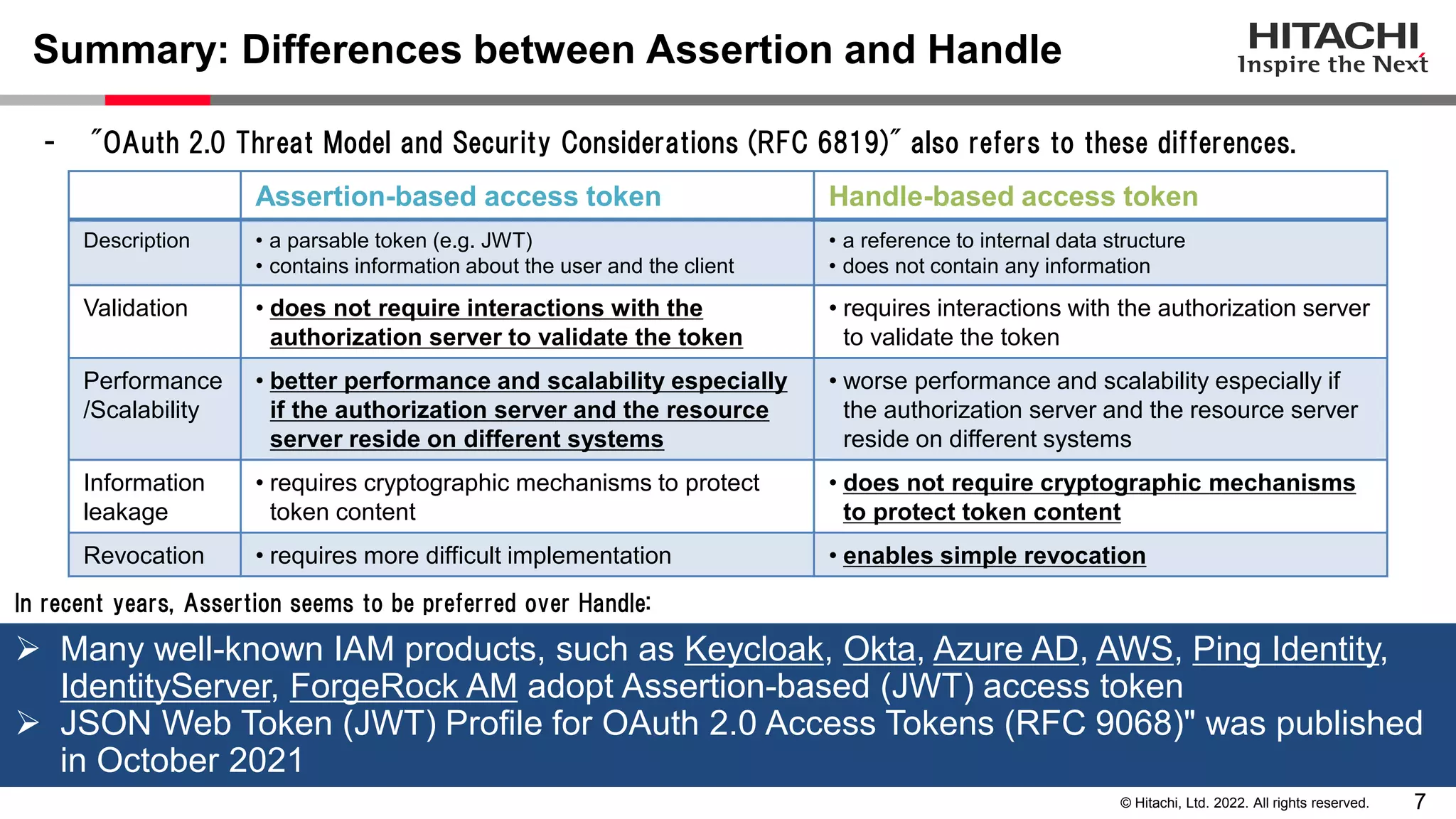
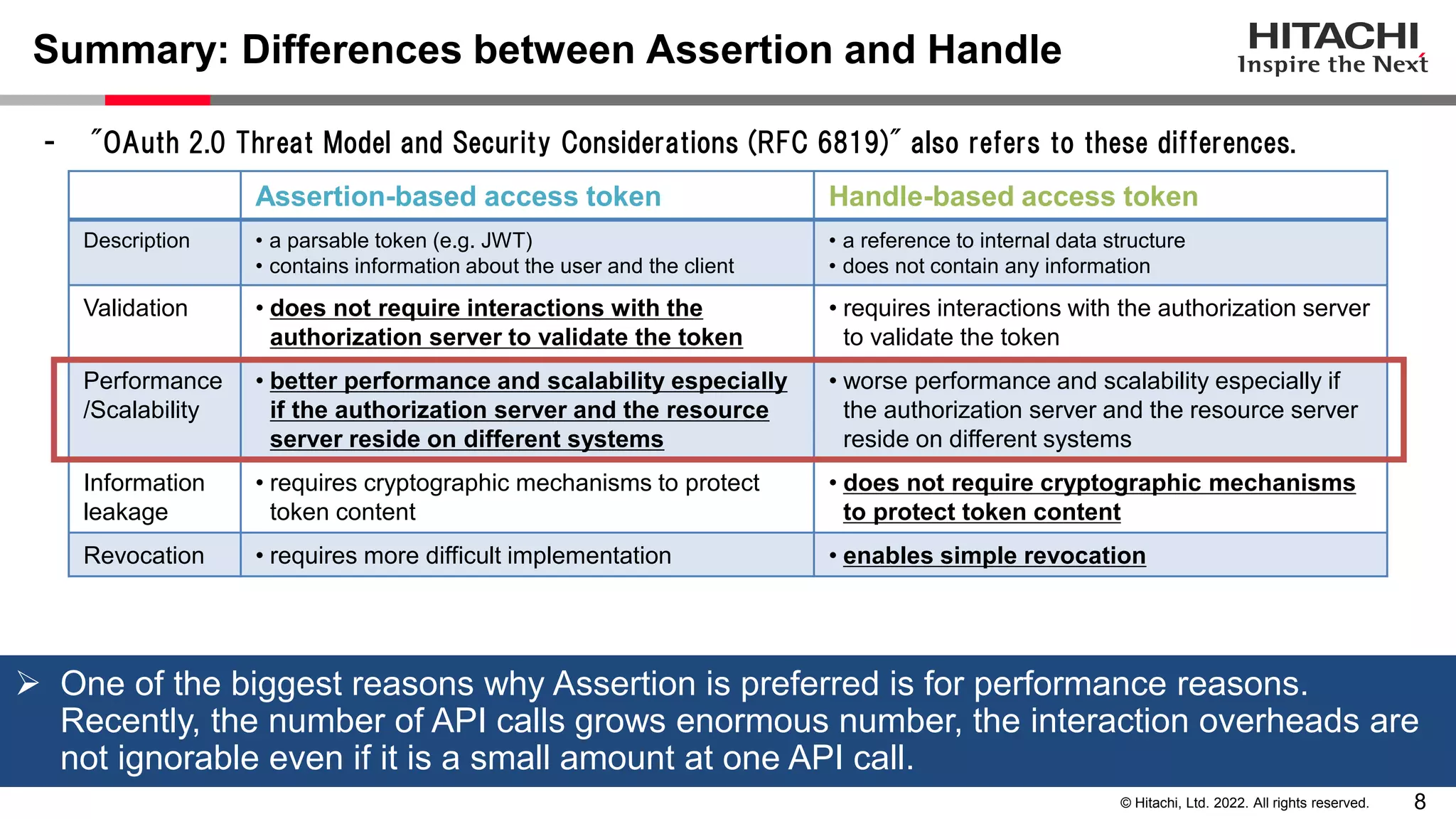
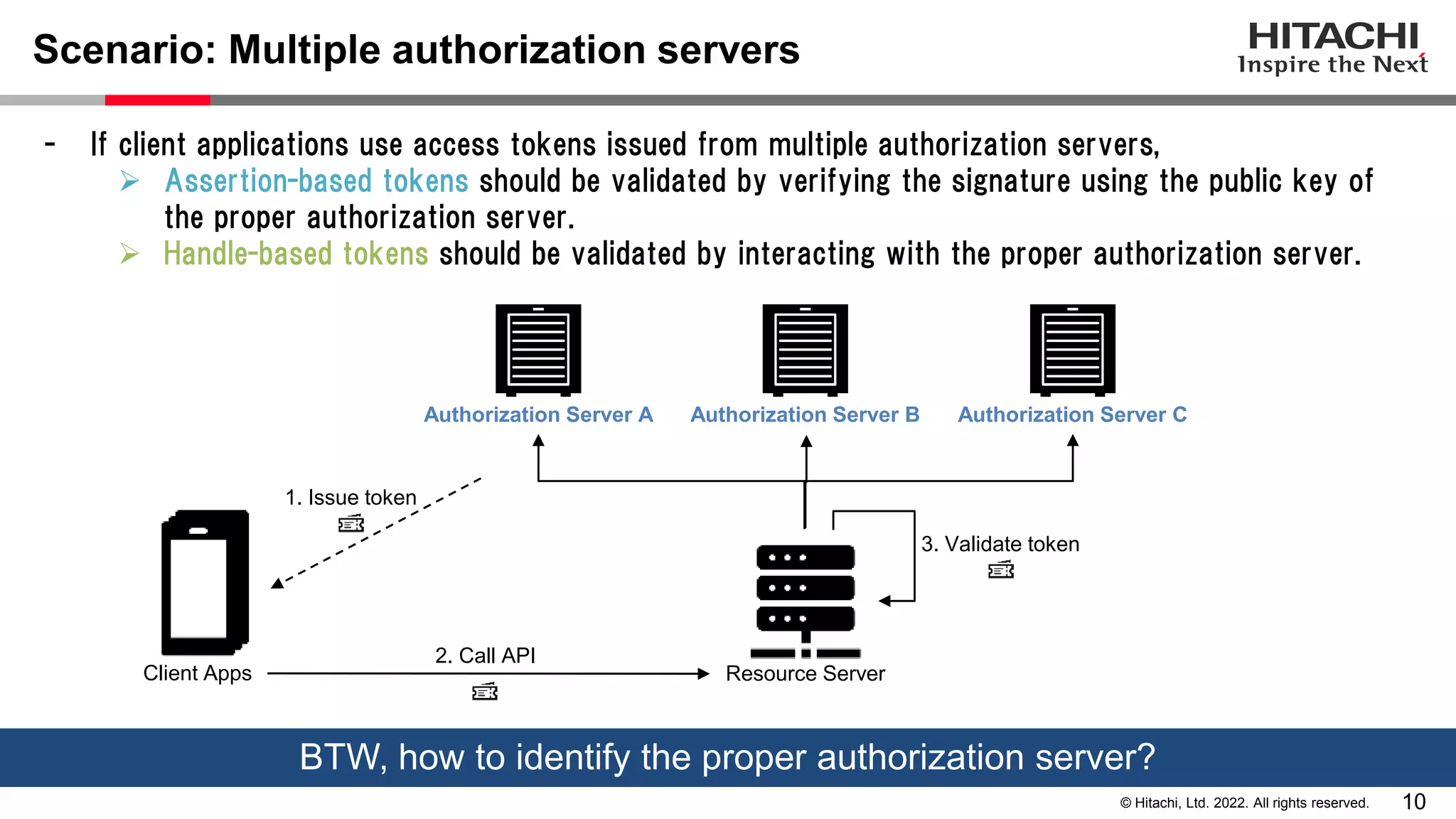
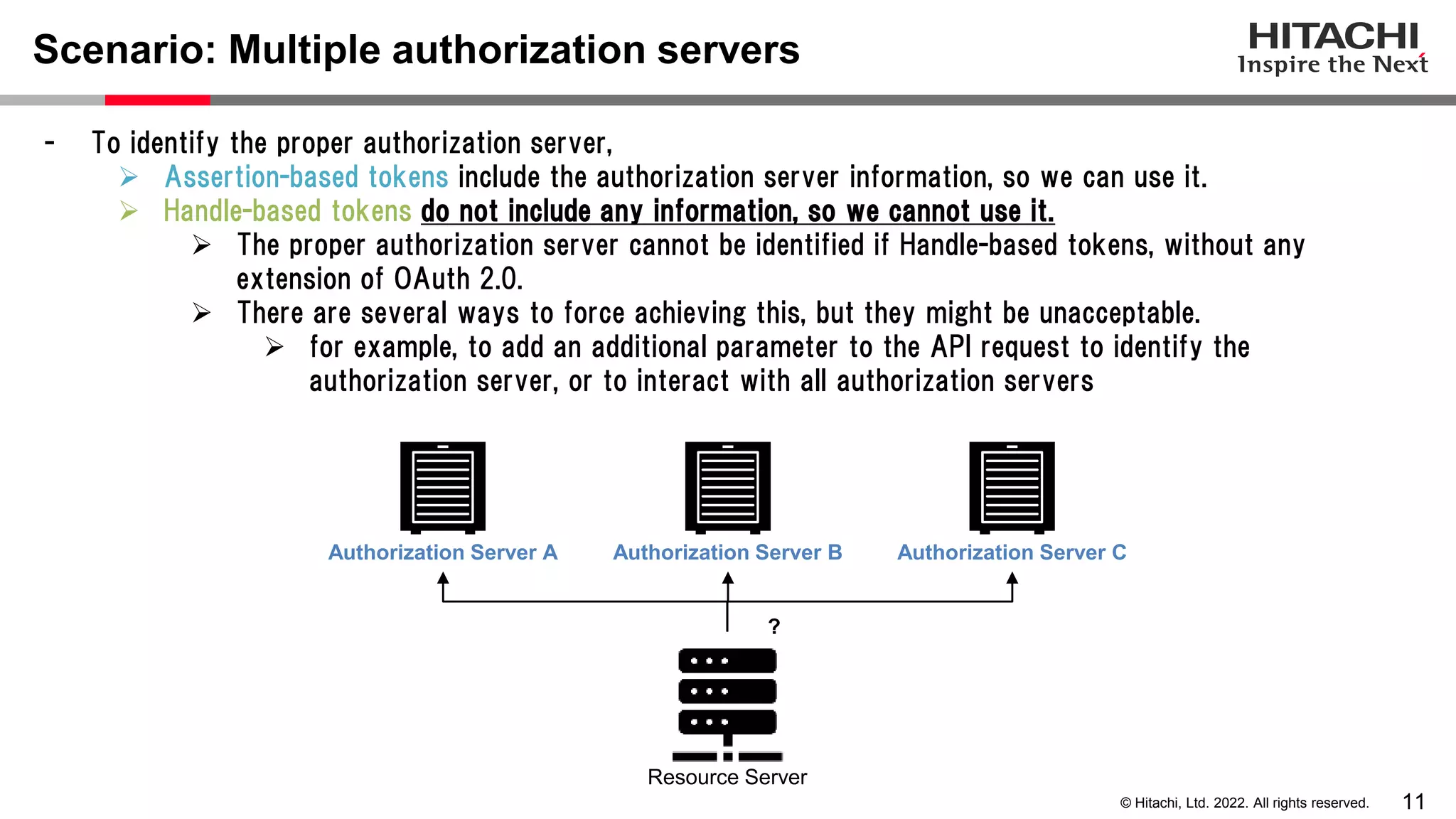
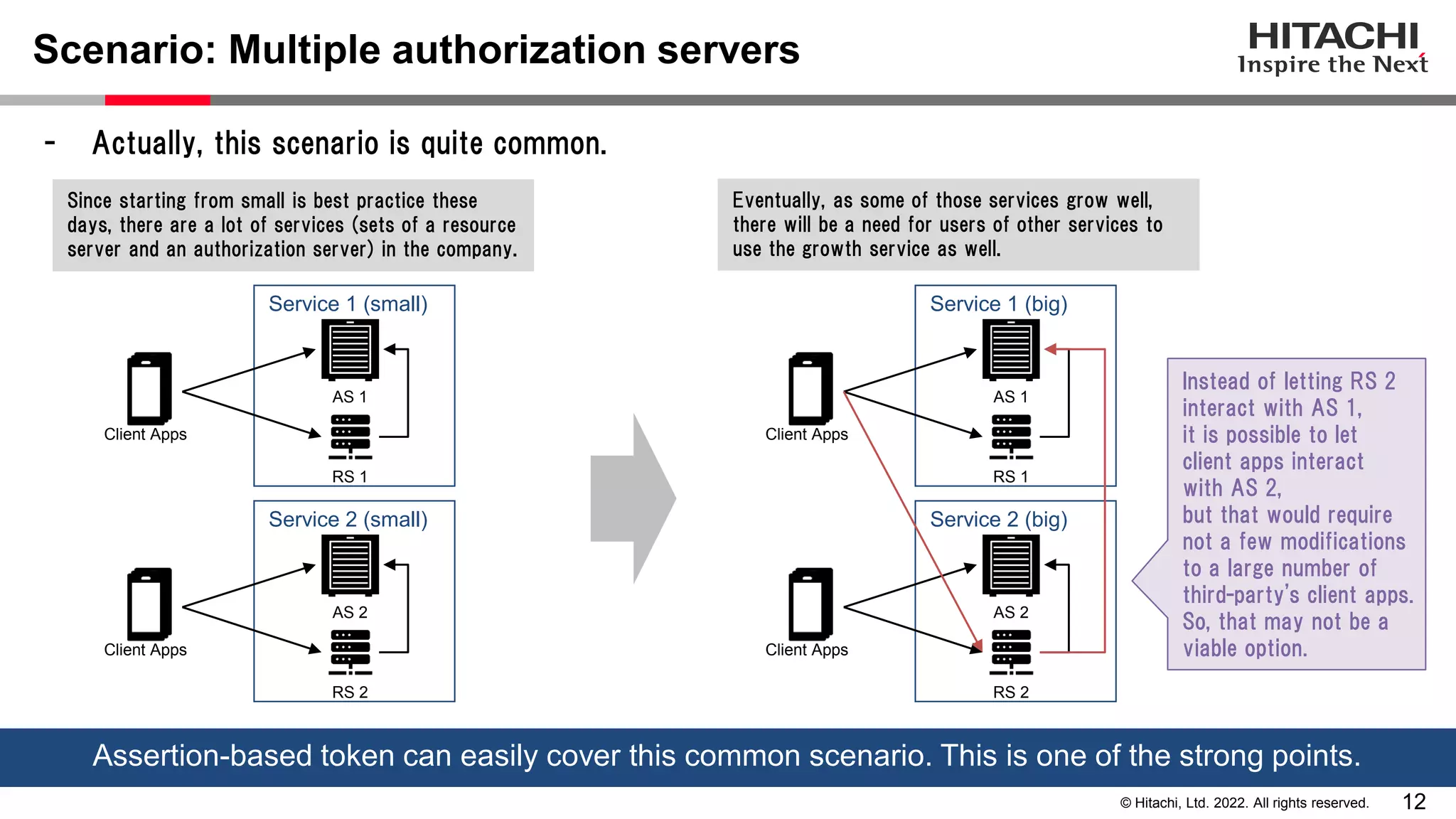
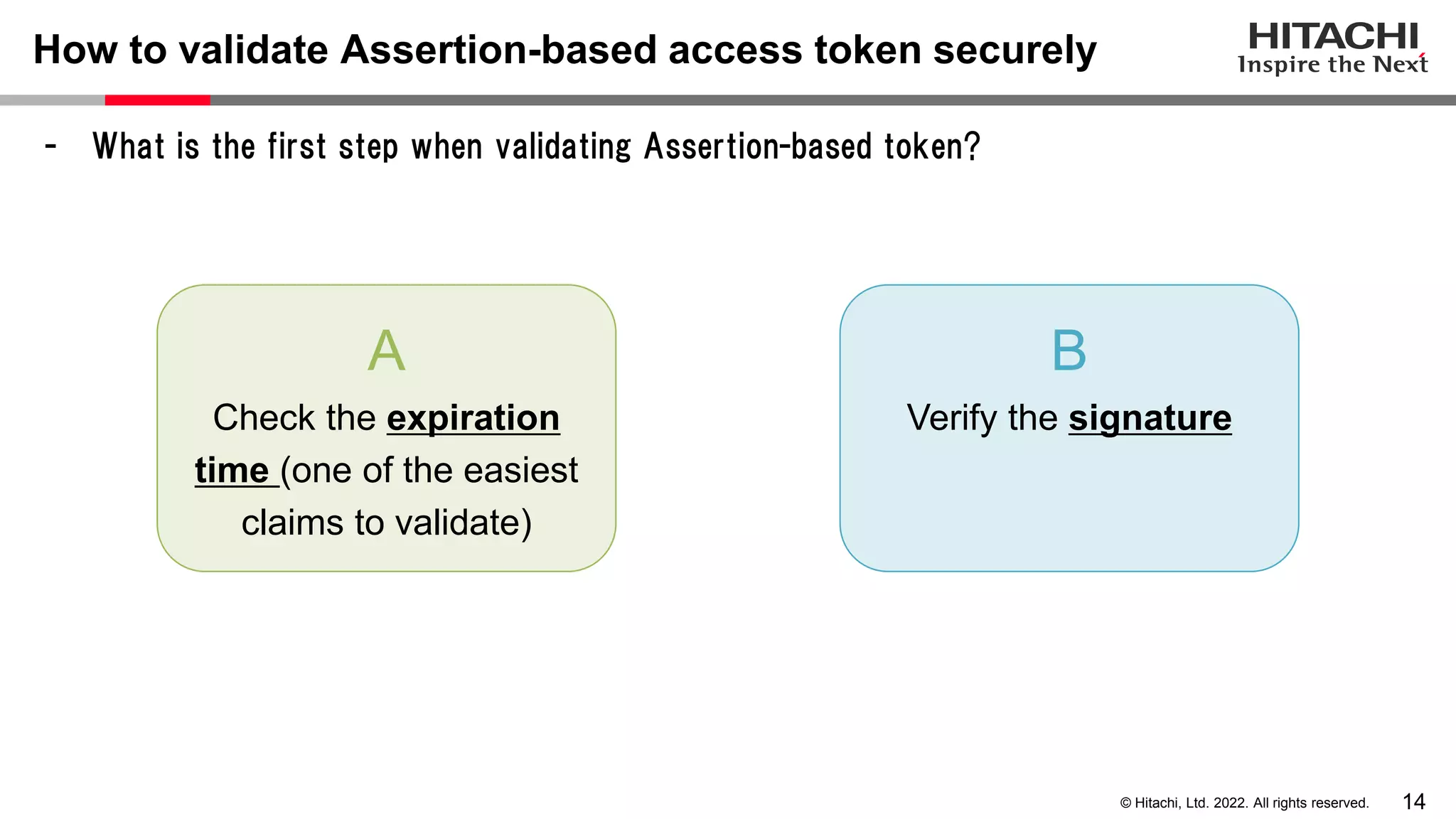
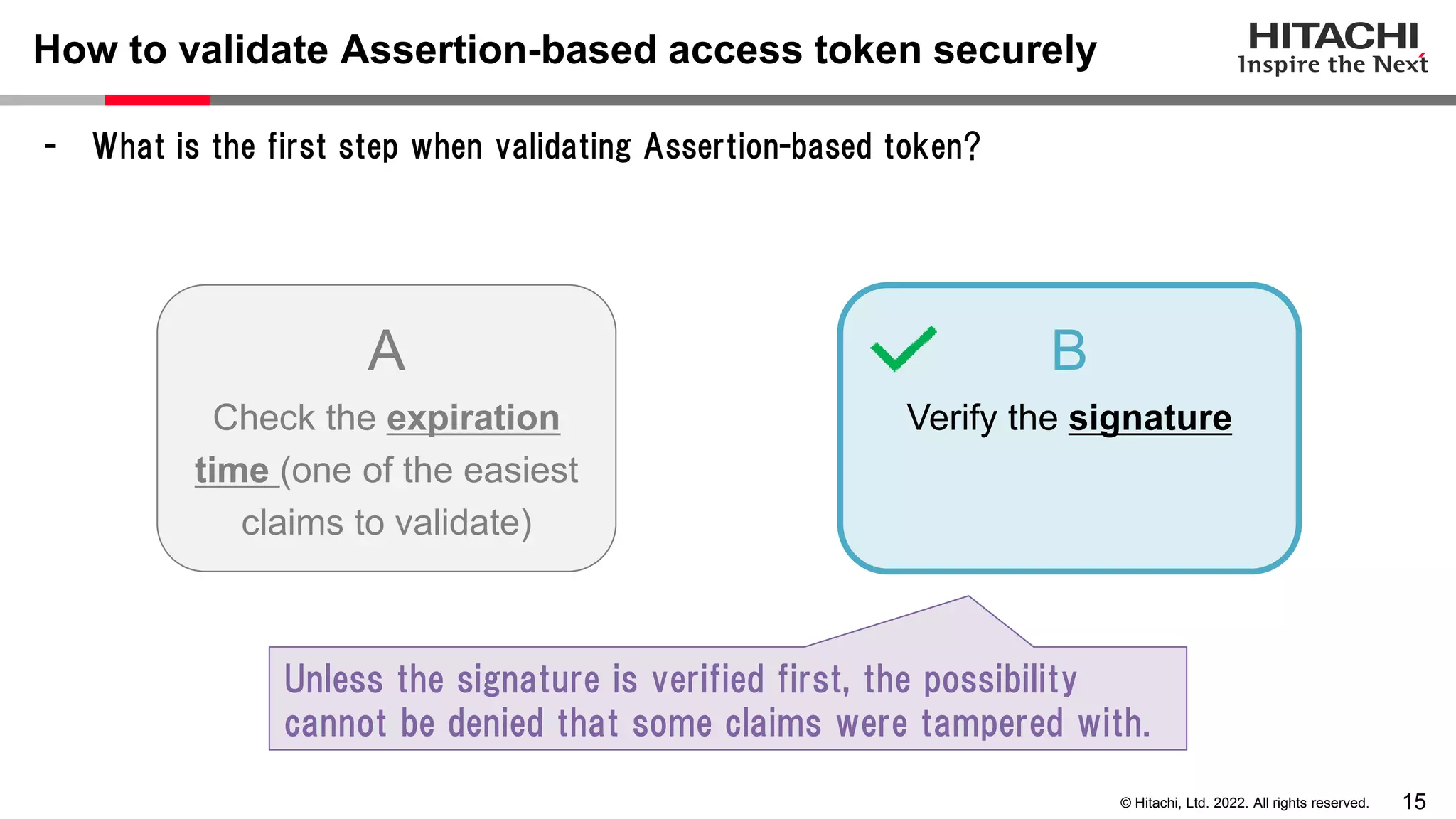
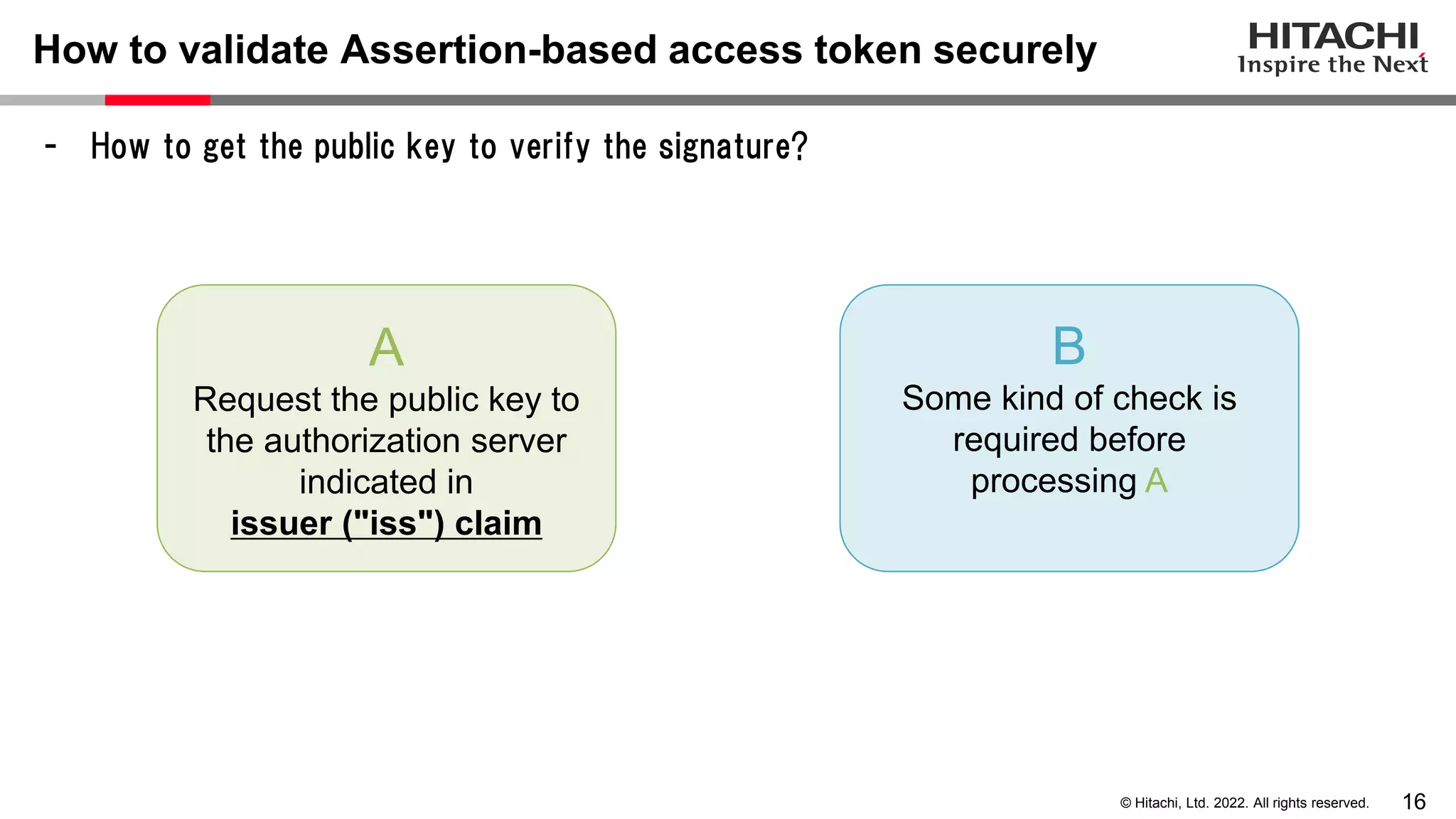
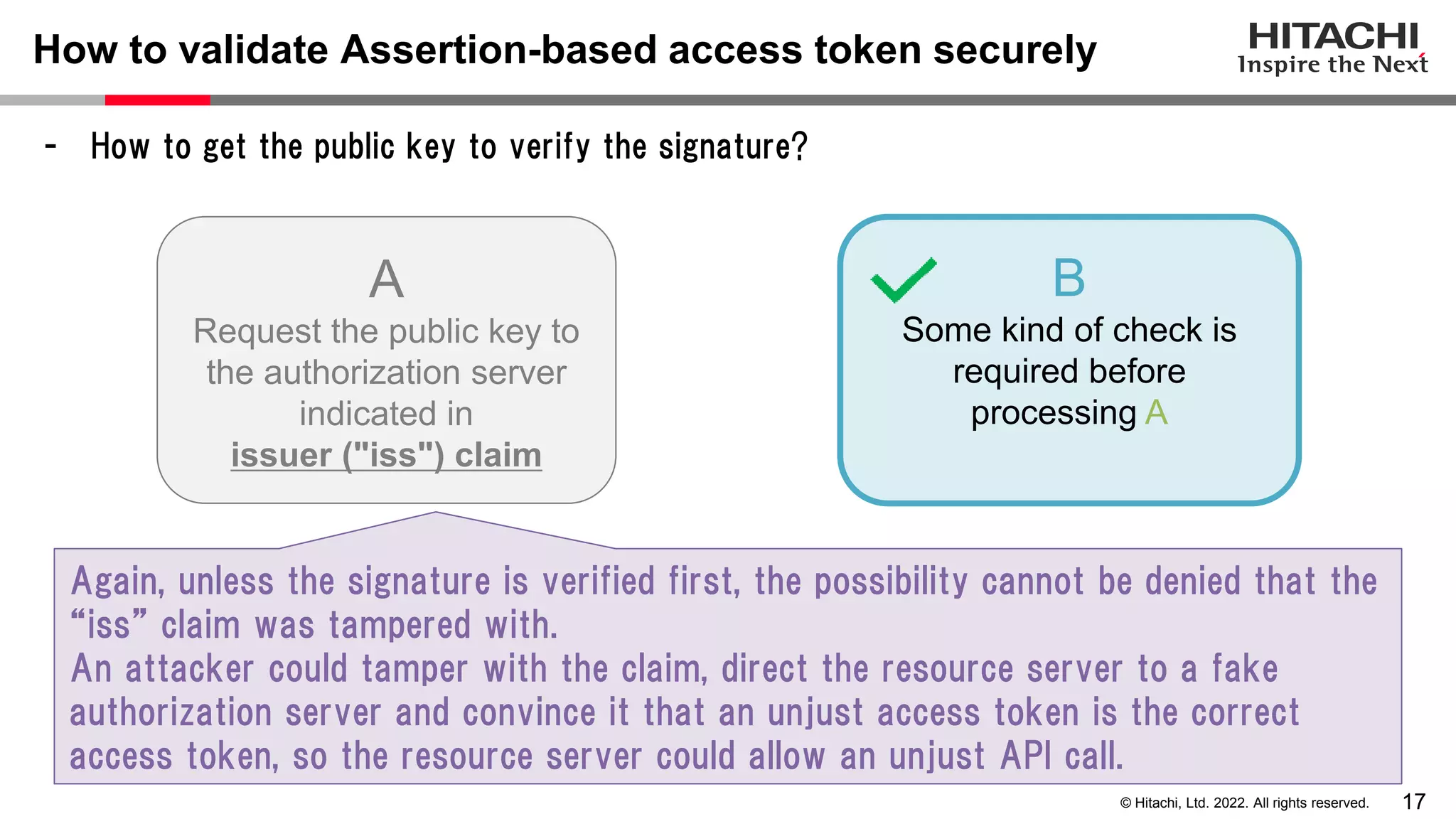
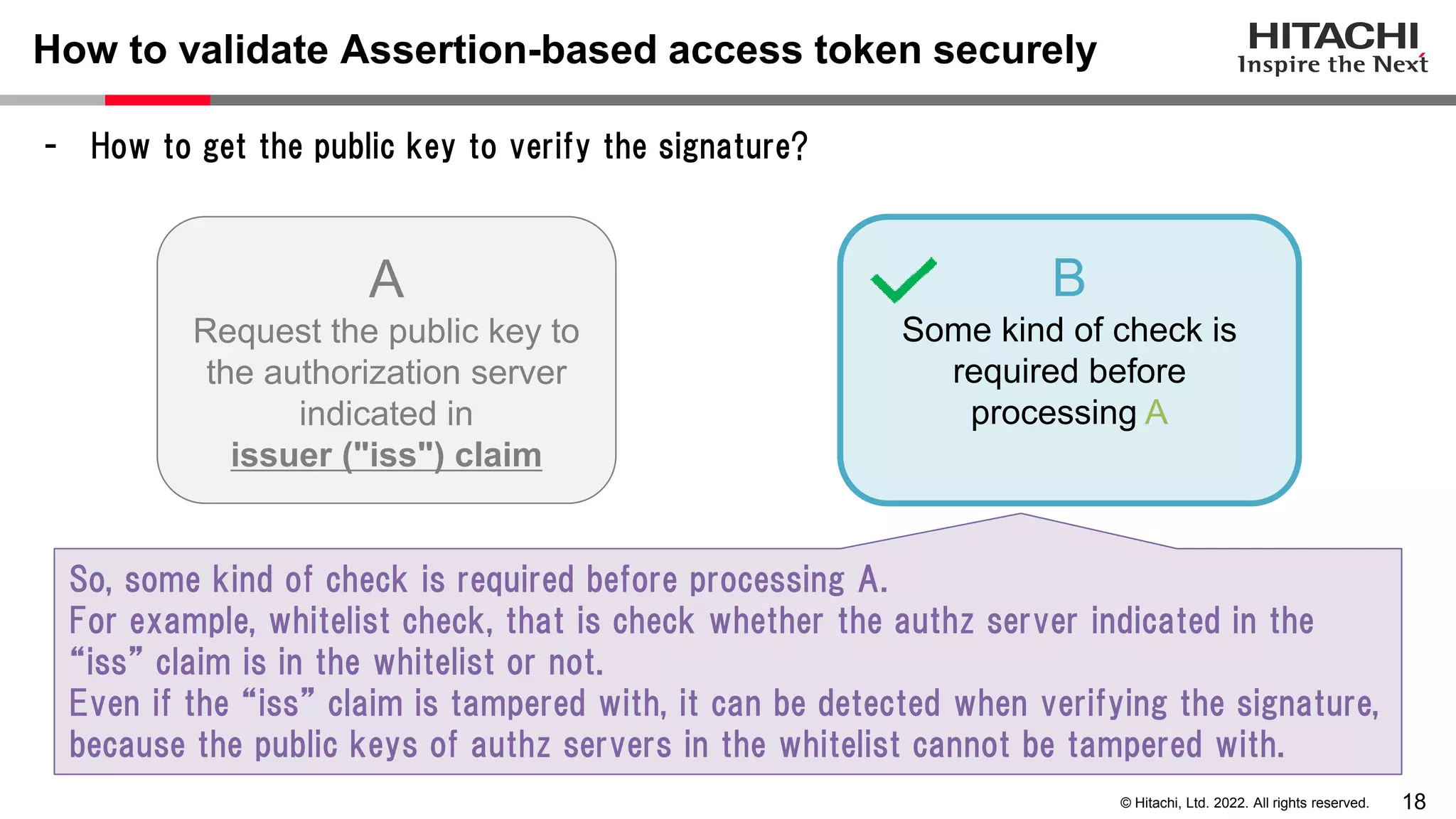
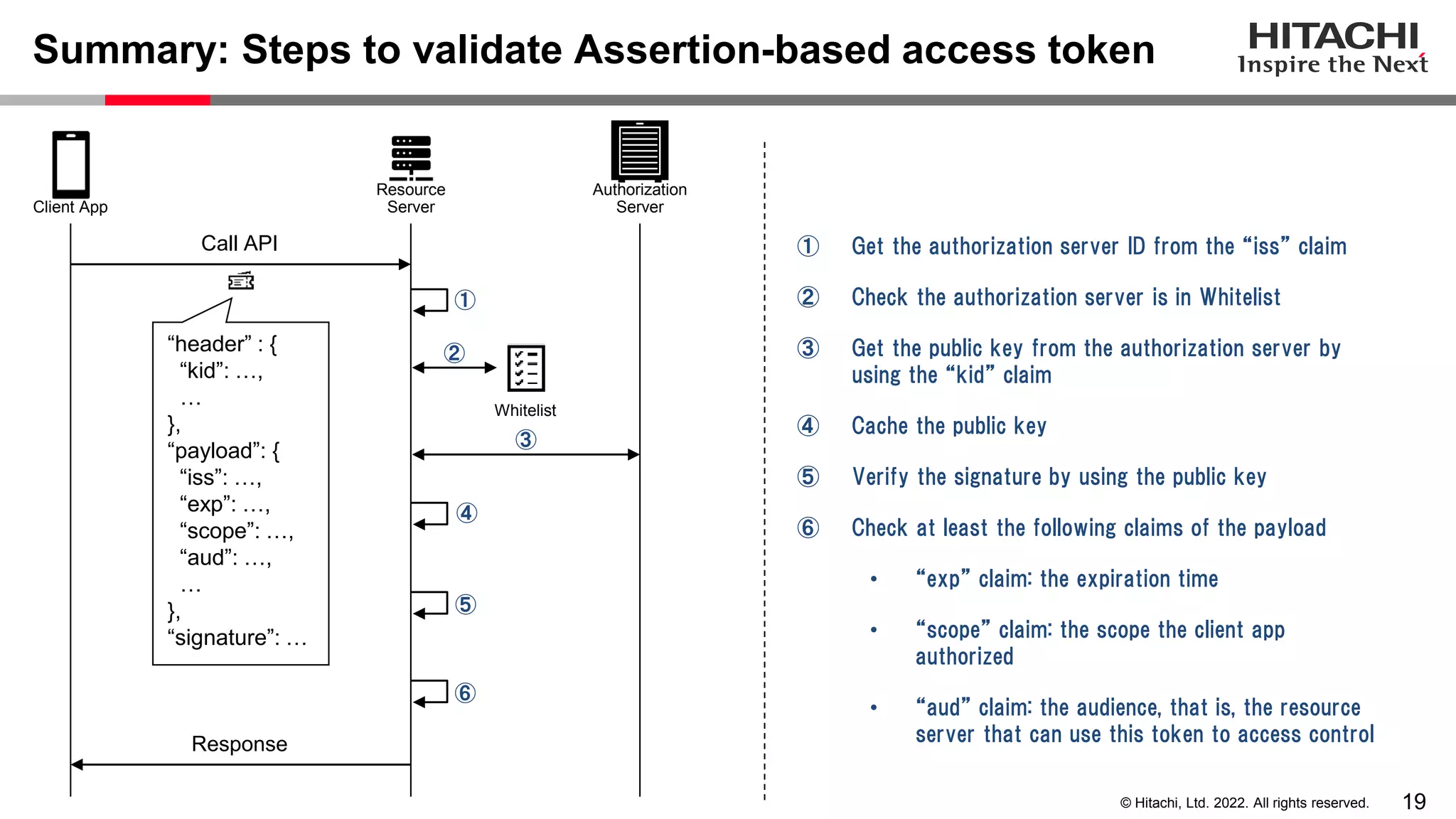
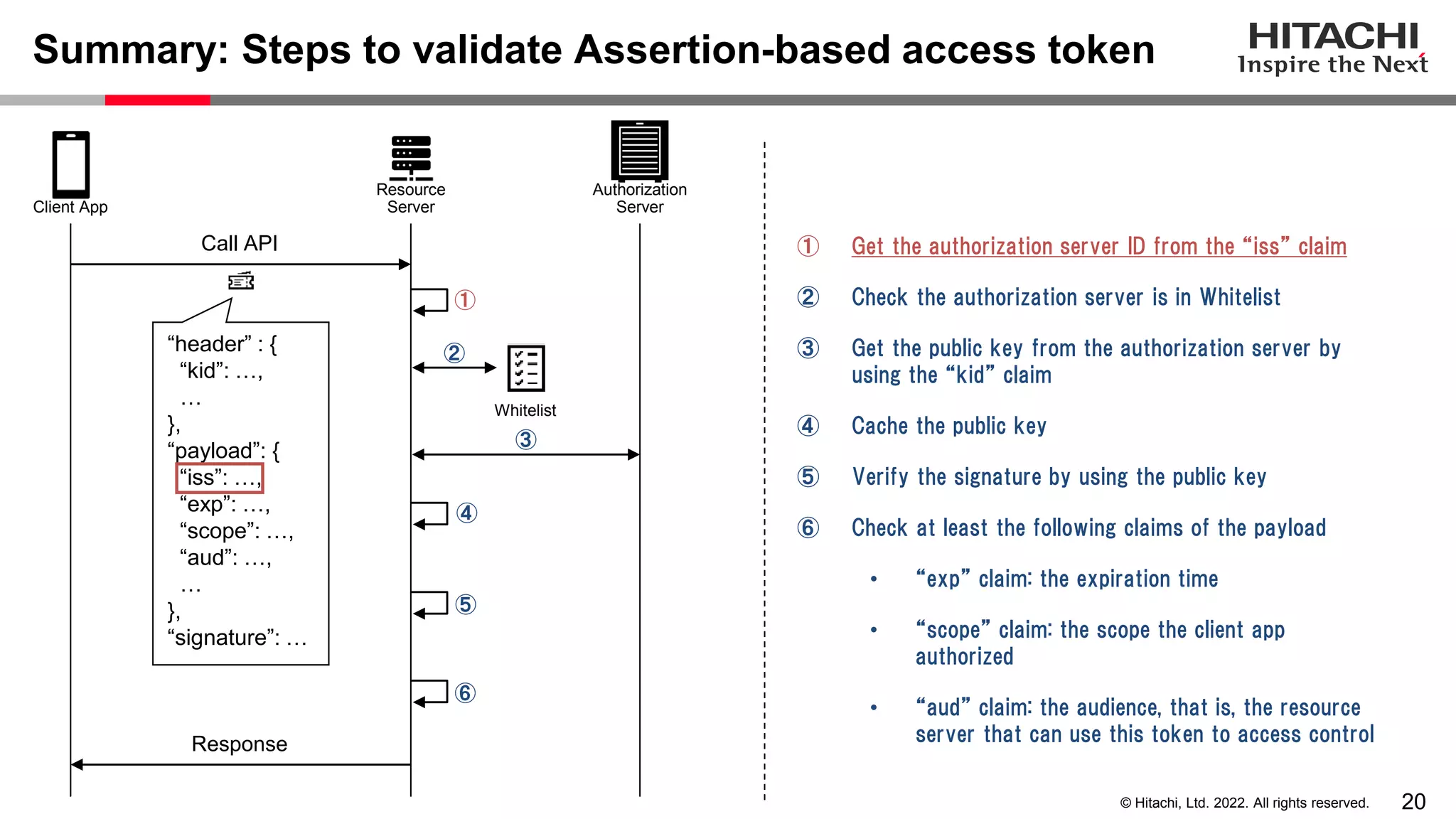
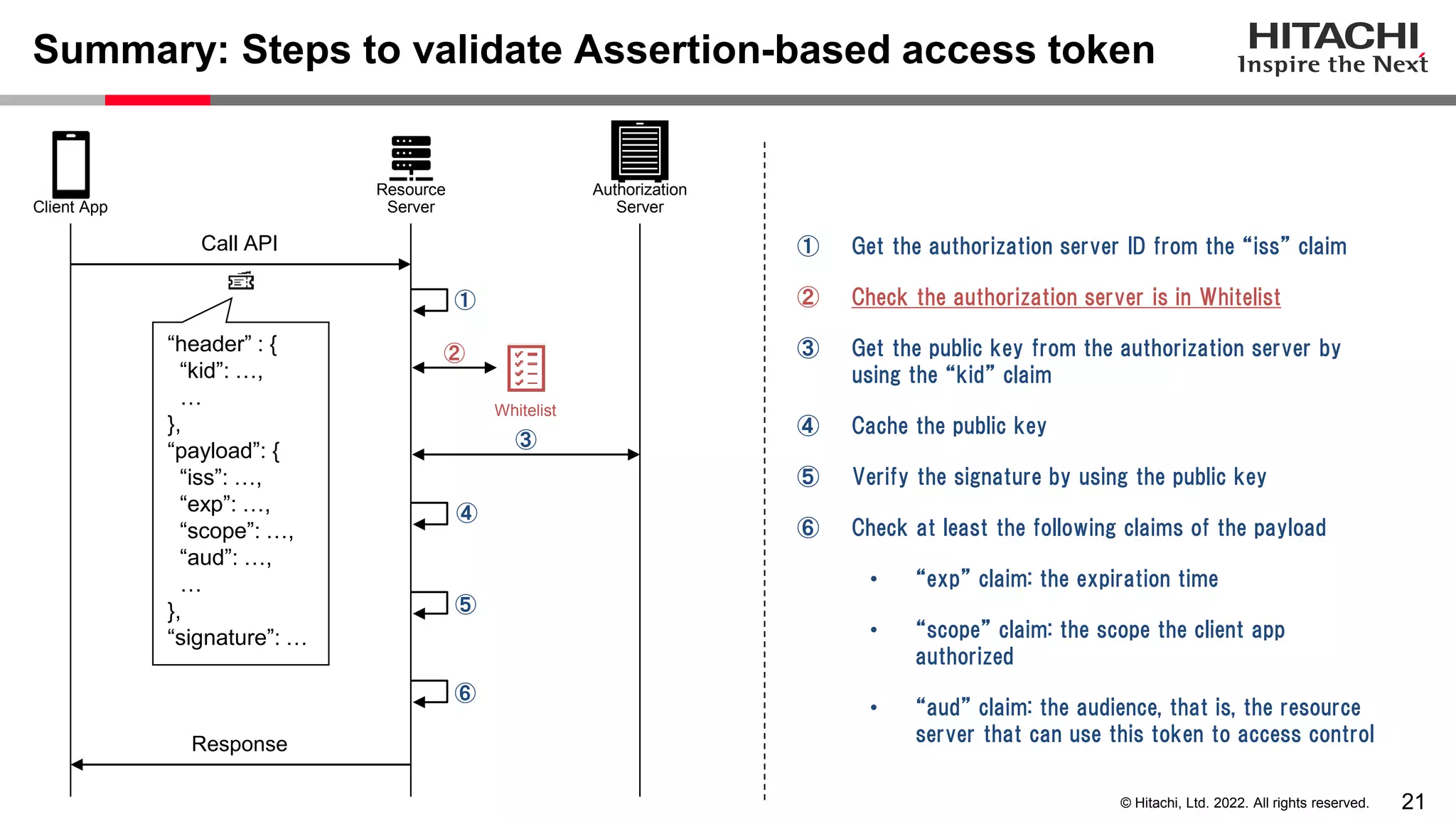
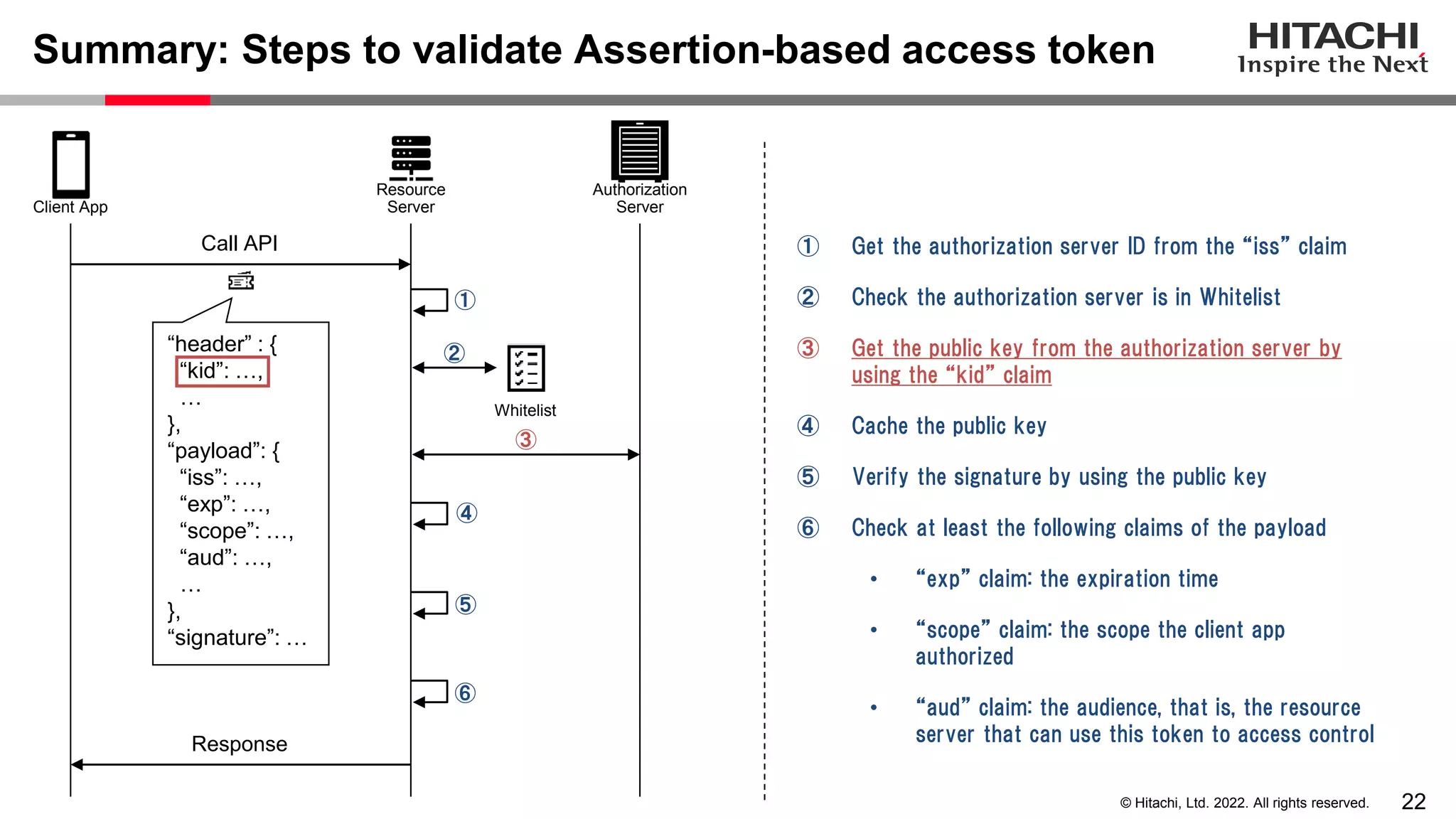
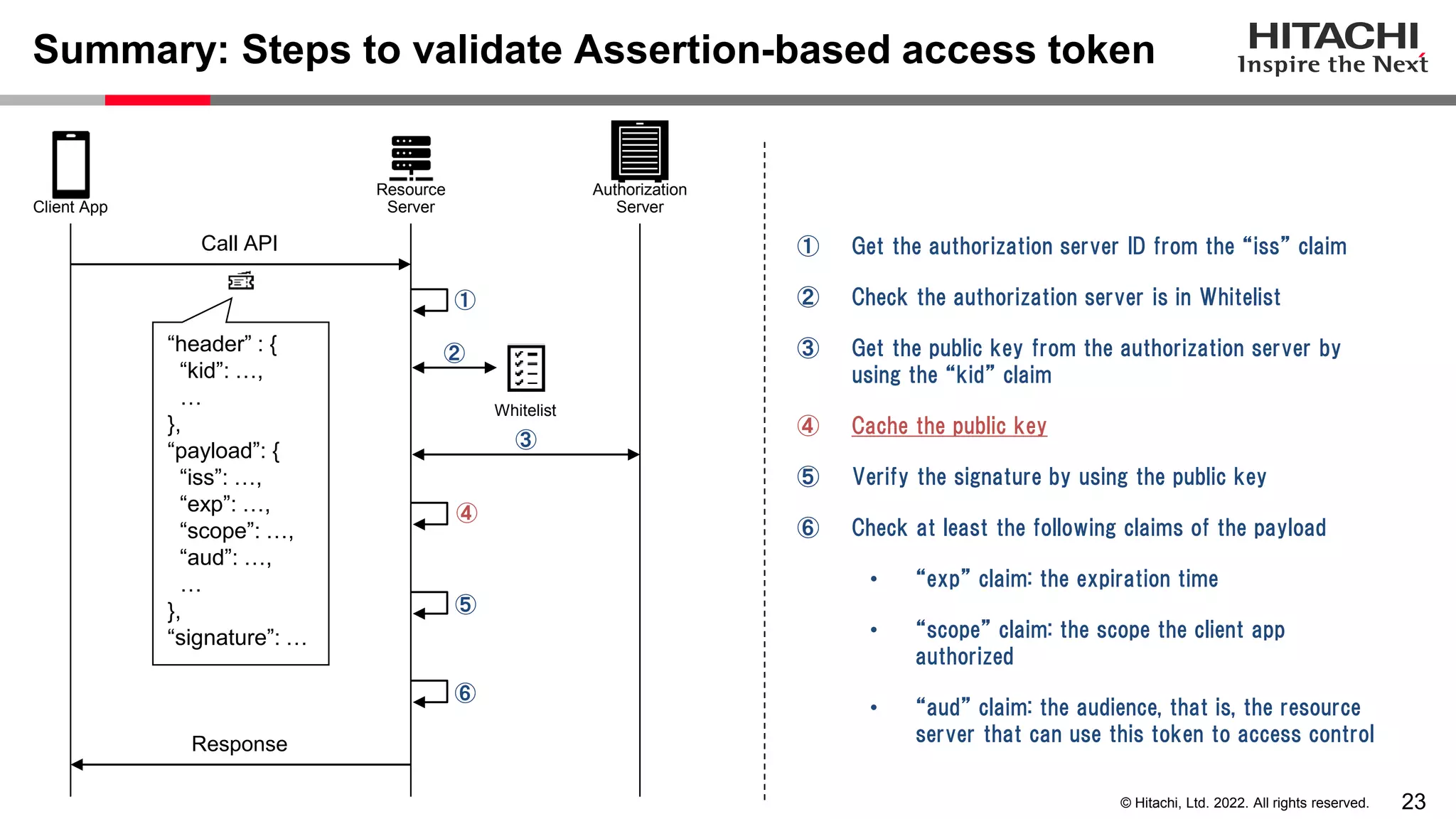
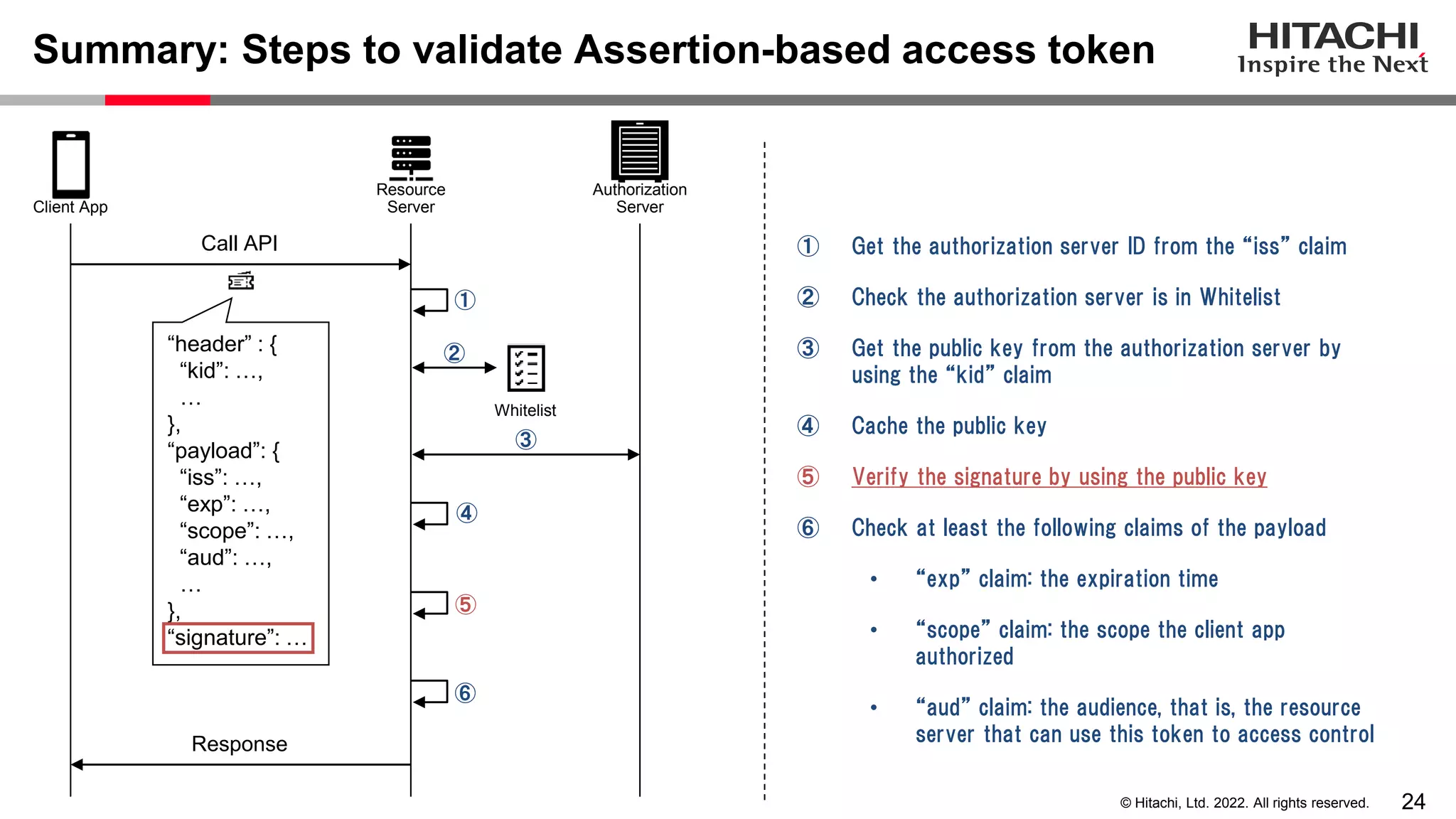
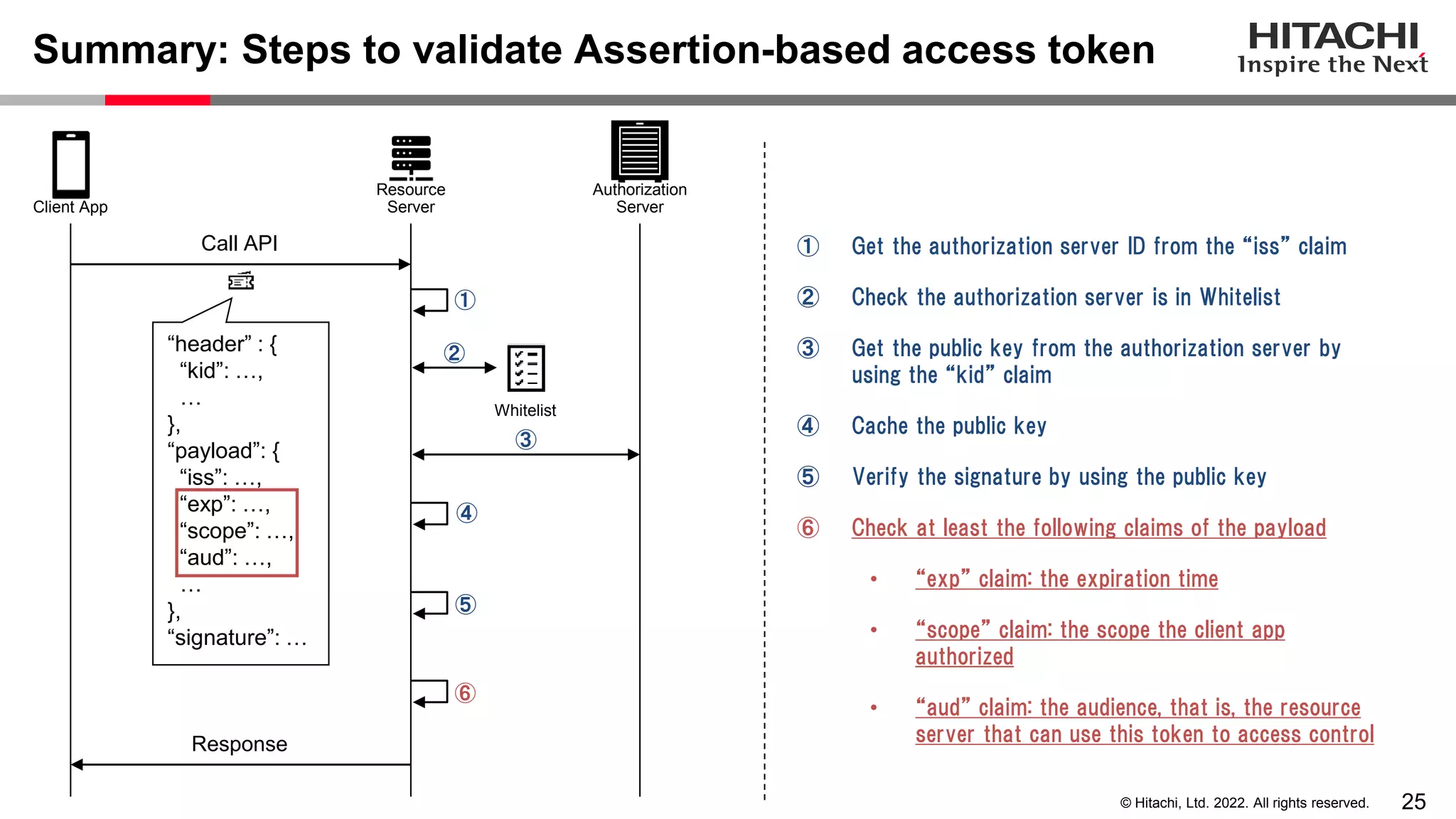
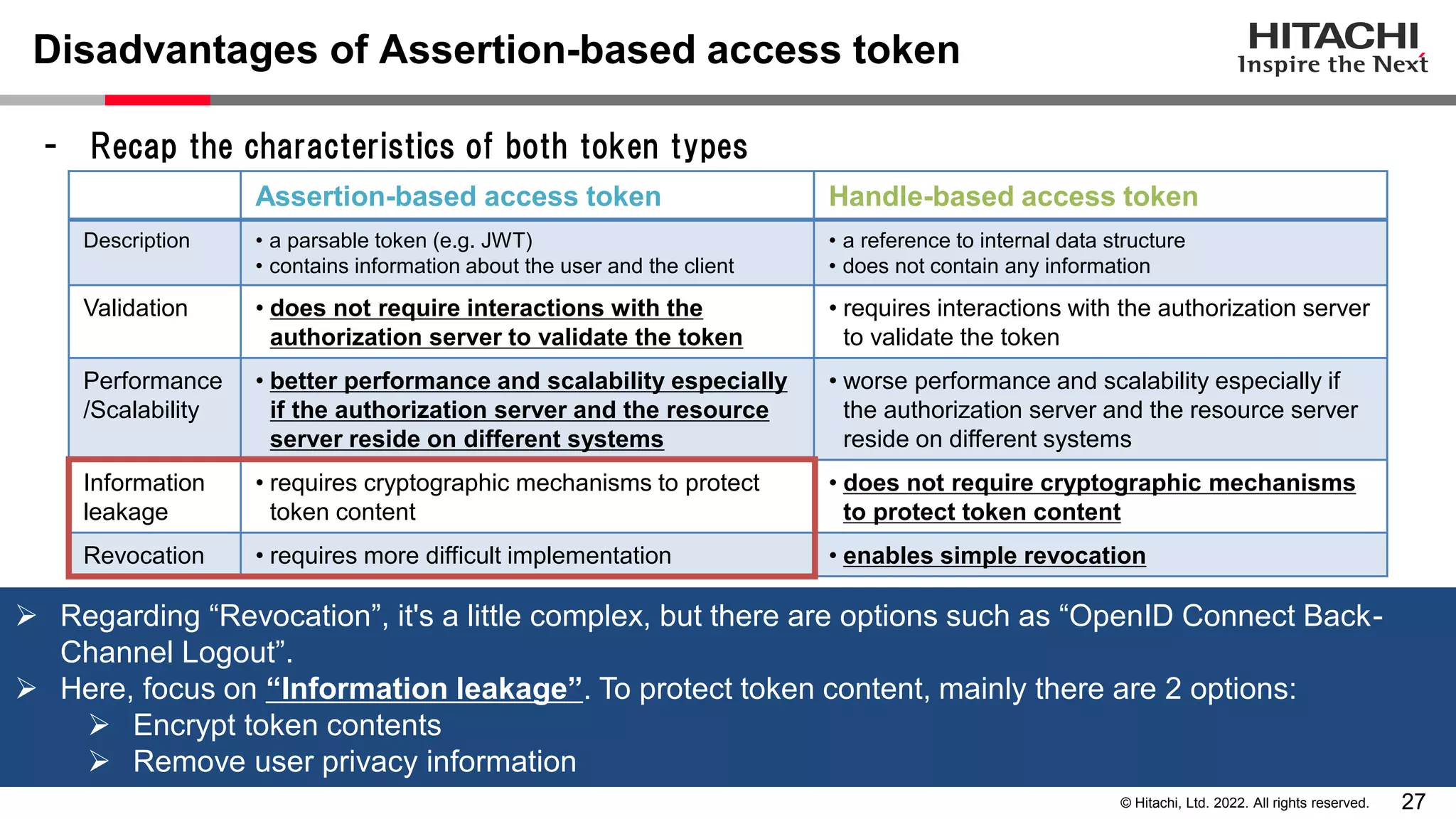
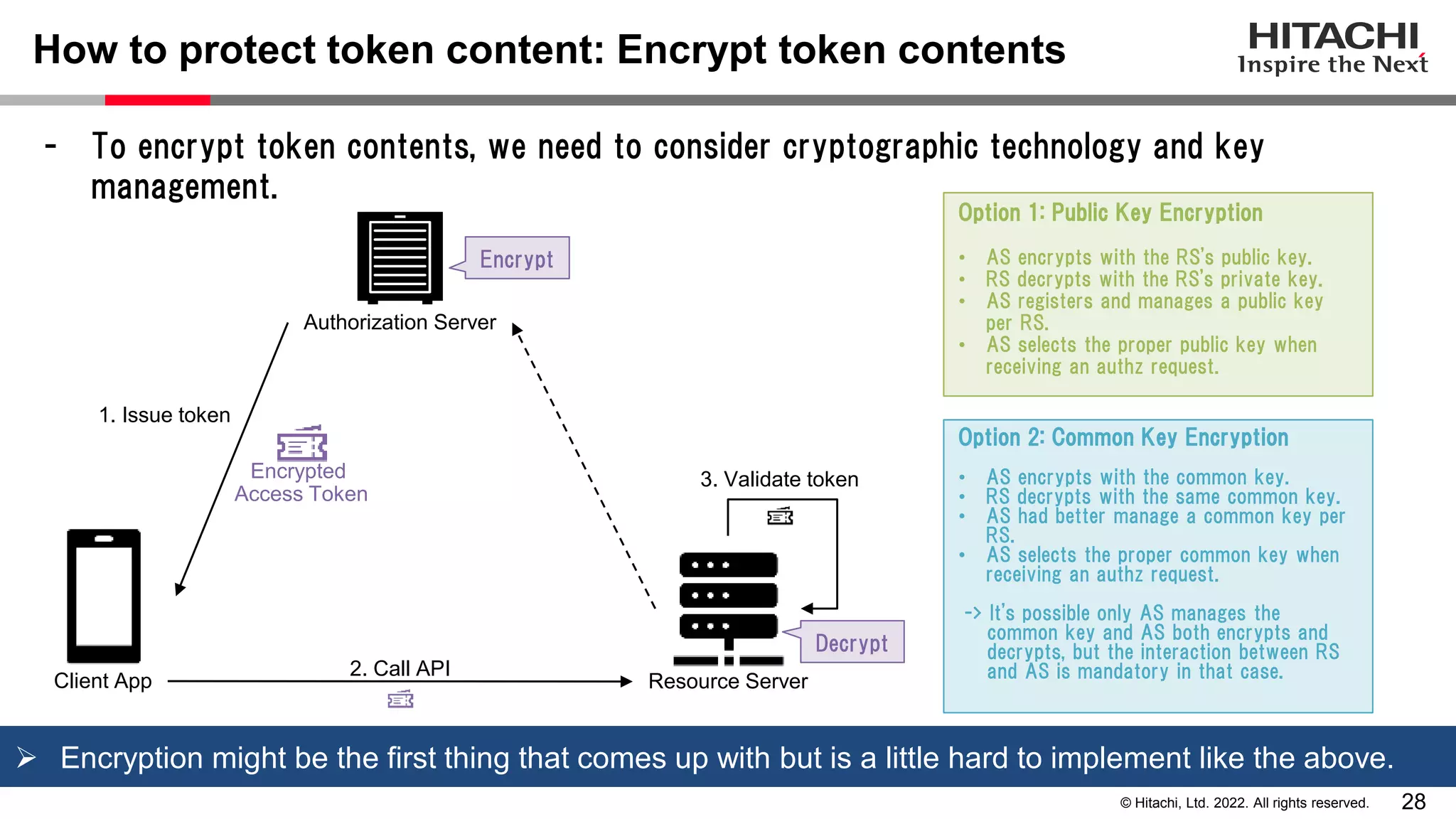
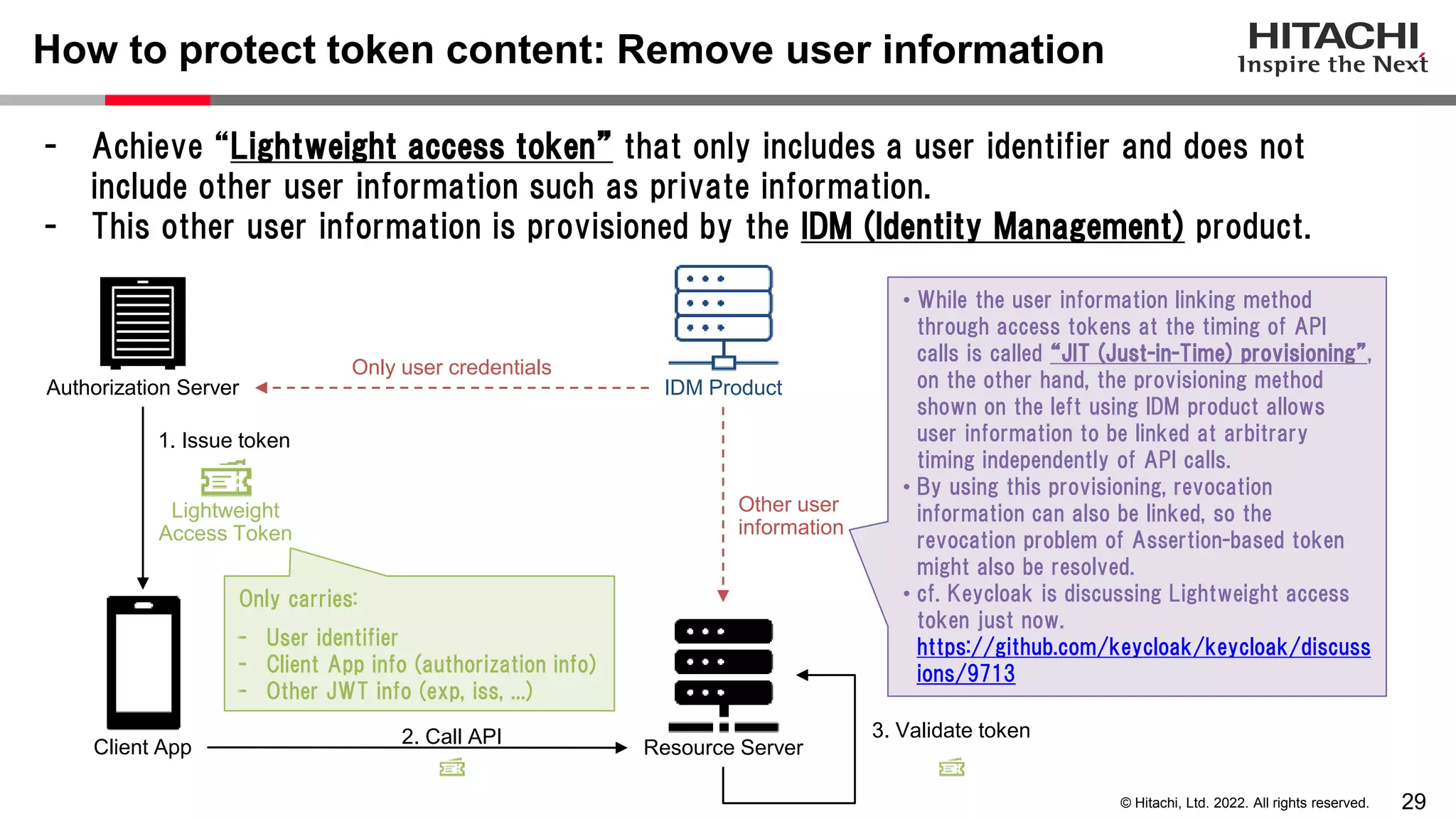
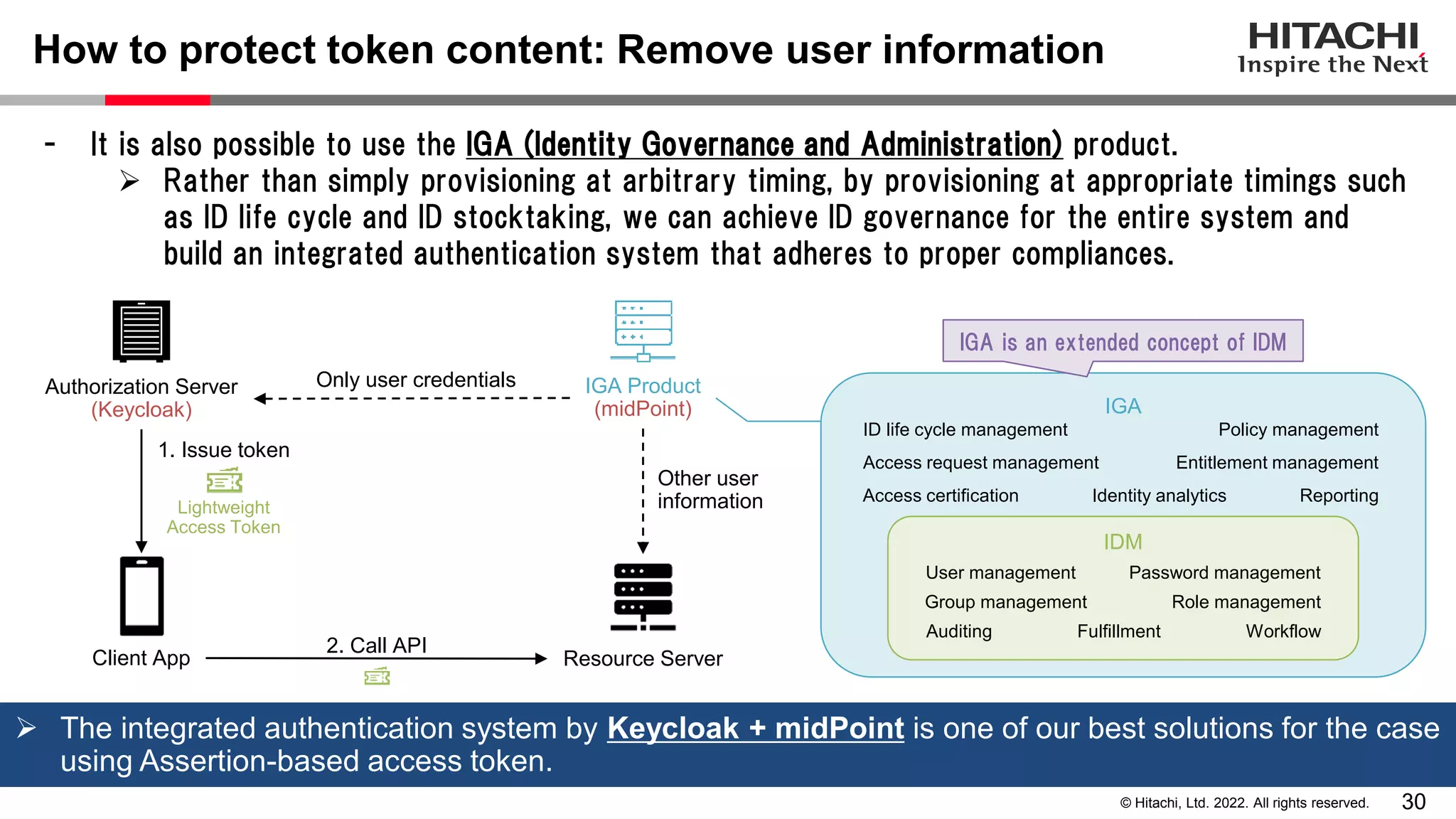
This document discusses the differences between assertion-based access tokens and handle-based access tokens in OAuth 2.0. Assertion-based tokens are parsable tokens like JWTs that contain user and client information, while handle-based tokens are opaque references. Assertion-based tokens have advantages for performance and scalability but require cryptographic protection, while handle-based tokens require validation through the authorization server. The document then examines scenarios where handle-based tokens could cause problems, such as with multiple authorization servers, and outlines secure validation steps for assertion-based tokens.