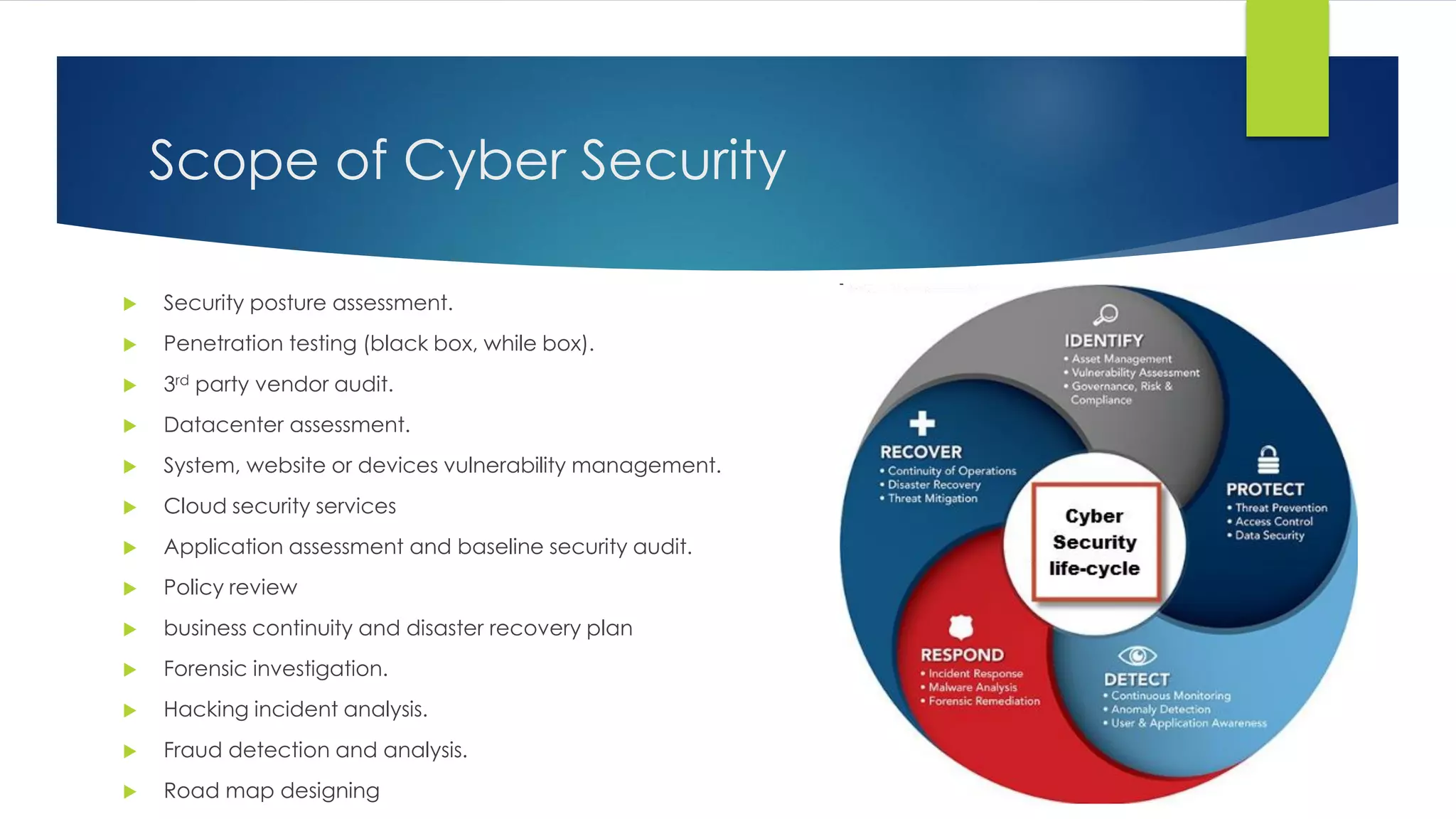
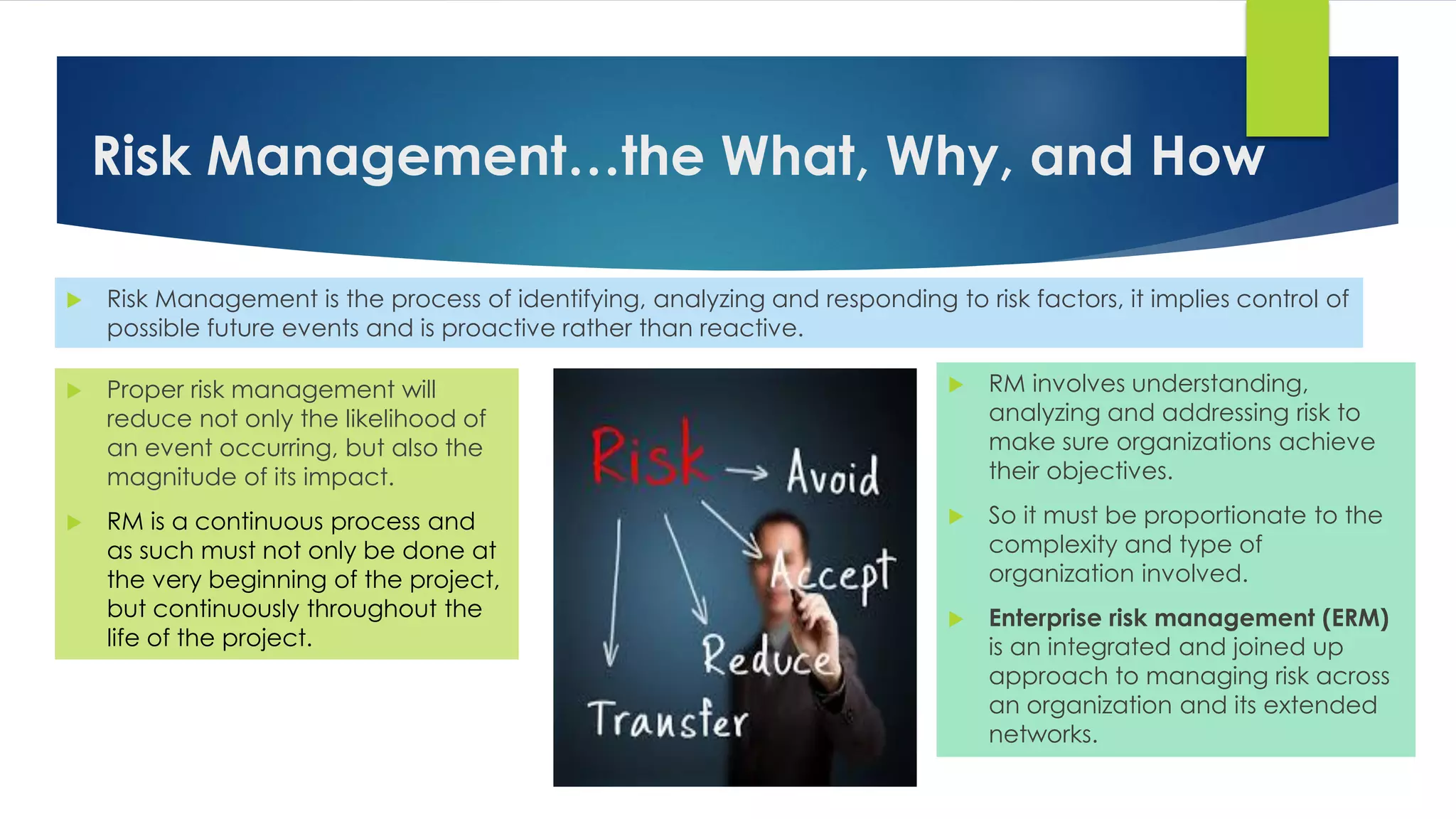
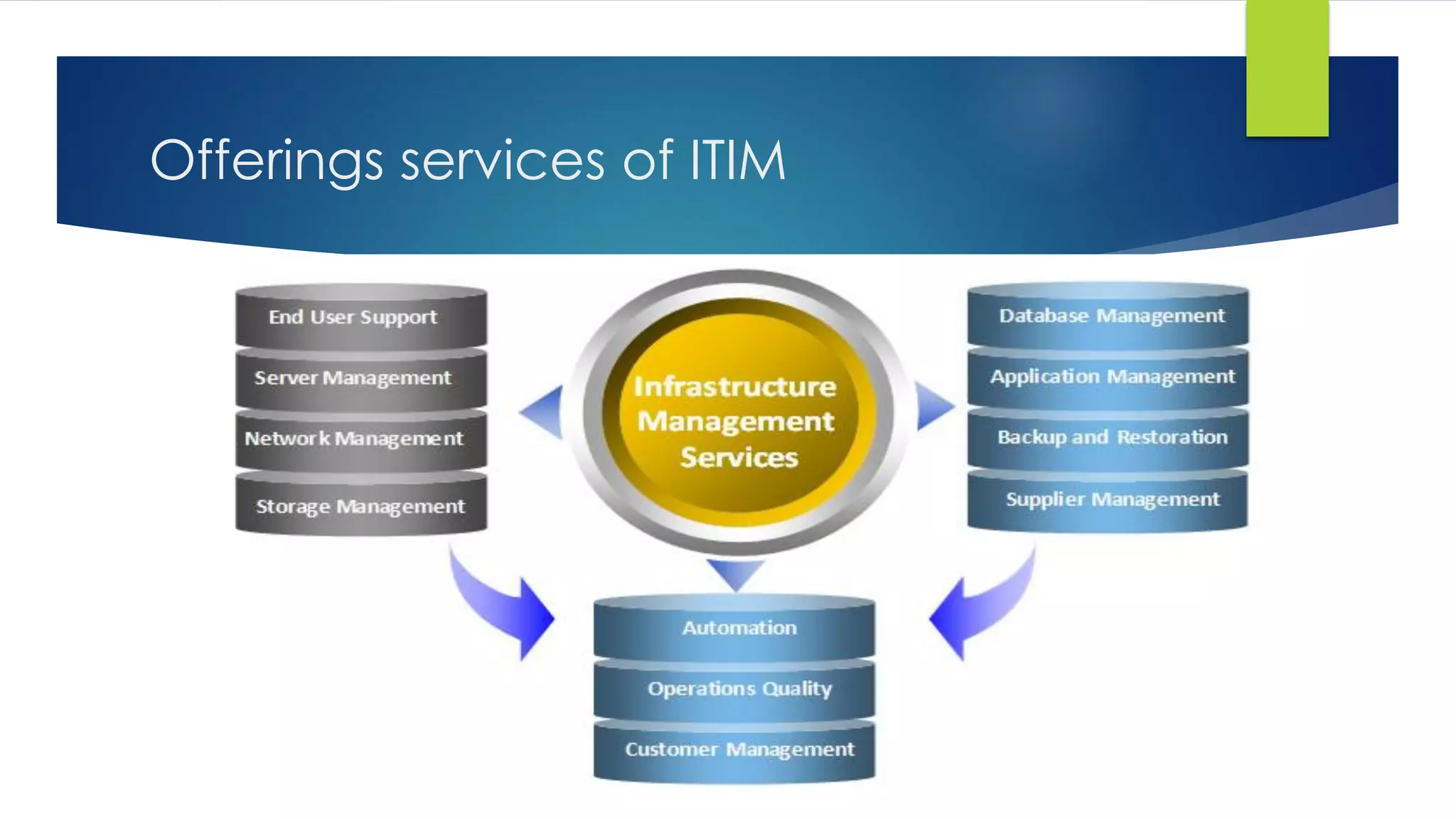
ZS Infotech is an IT support services and security solutions provider located in Selangor, Malaysia. They offer a full range of IT services customized for businesses, including acting as the client's internal IT department. Their services include IT staff augmentation, endpoint security, cyber security, risk management, and infrastructure management. For IT staff augmentation, they provide additional IT expertise on an as-needed basis. Their endpoint security protects company devices from threats. Cyber security helps secure companies from online threats. They assess risks and help with risk mitigation. And they manage clients' IT infrastructure services.