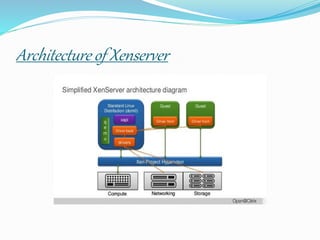
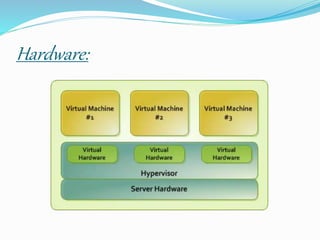
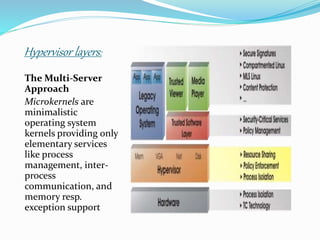
XenServer is a hypervisor developed by the Linux Foundation that allows multiple operating systems to run concurrently on the same computer hardware. It uses a microkernel design with four main layers: the hardware layer, the hypervisor layer, the virtual machine layers, and various software layers that provide services and management of virtualized resources across networks, storage, and applications. The hypervisor sits above the physical hardware and is responsible for sharing resources and enforcing access controls.