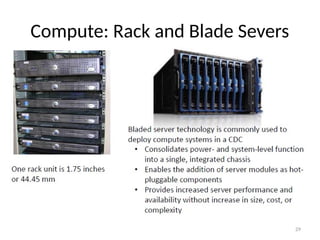
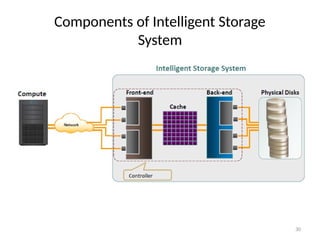
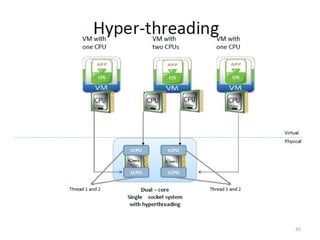
The document discusses virtualization in net-centric computing, highlighting its benefits such as resource utilization, service isolation, and the ability to run multiple operating systems on a single hardware platform. It explores hypervisor types, memory virtualization, and techniques for efficient virtualization, emphasizing the importance of safety, fidelity, and efficiency. Additionally, it reviews the evolution of virtualization technology and its application in modern data centers.






![7
Intro
• Solution: Virtualization
– Decouple [OS, service] pair from hardware.
– Multiplex lightly used services on common host
‐
hardware.
– Migrate services from host to host as needed.
– Introduce new [OS, service] pairs as needed
• Adding new services.
• Testing upgrades of existing services.
• Experimental usage.](https://image.slidesharecdn.com/csc4065virtualization-casestudy-241127080144-2ac57d30/85/CSC_406_5_Virtualization-Case-Study-it-s-base-on-virtualization-7-320.jpg)