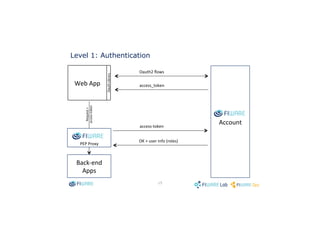
This document discusses adding identity management and access control to applications using FIWARE. It describes using the FIWARE Identity Manager for user authentication via OAuth 2.0 flows. It also discusses three levels of authorization: 1) authenticating users, 2) basic authorization of HTTP verbs and resource paths, and 3) advanced authorization using XACML policies. The document provides documentation links for the FIWARE Account, Access Control enabler, OAuth2 demo, and FIWARE Proxy.