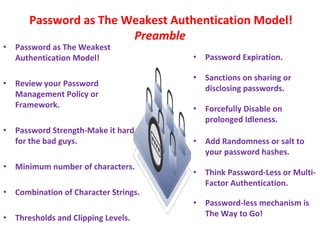
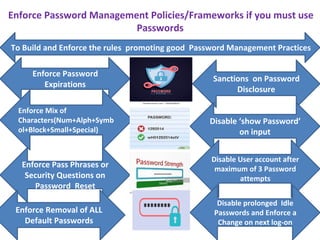
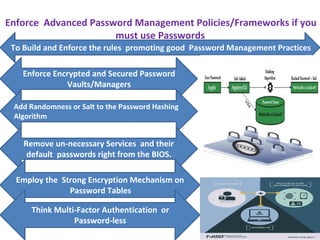
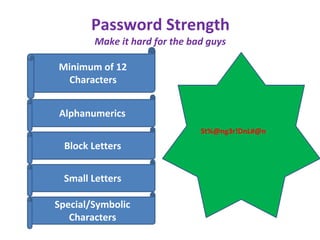
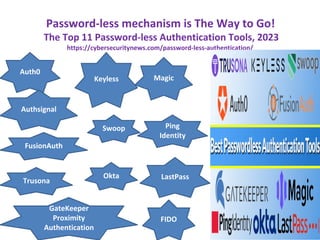
The document discusses the vulnerabilities of passwords as the weakest authentication model and emphasizes the need for improved password management policies. It suggests practices such as enforcing password complexity, implementing expiration policies, and utilizing multi-factor or password-less authentication. The author advocates for robust security measures to mitigate risks associated with password management on Password Management Day, 2023.