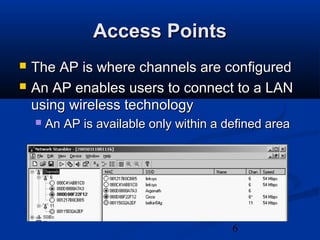
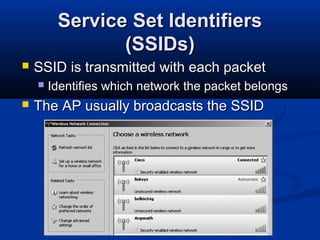
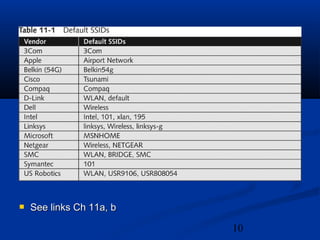
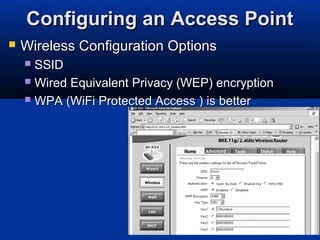
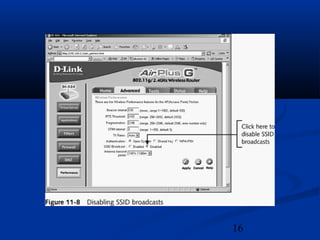
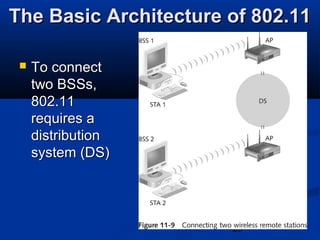
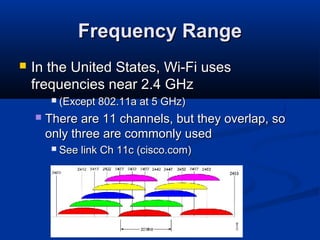
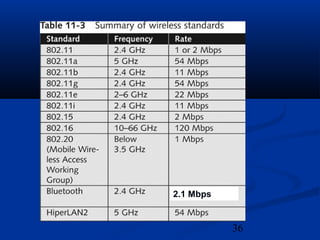
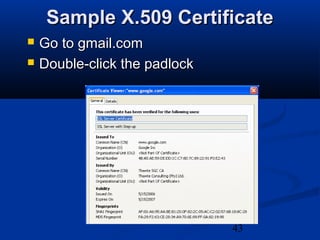
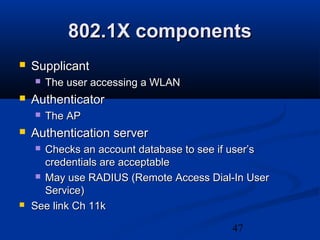
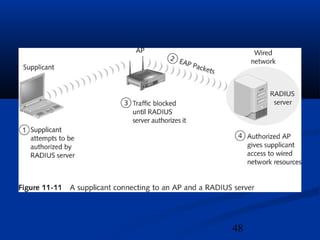
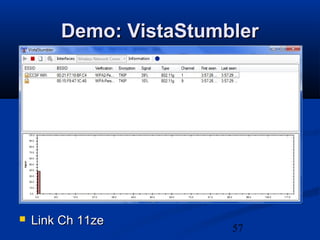
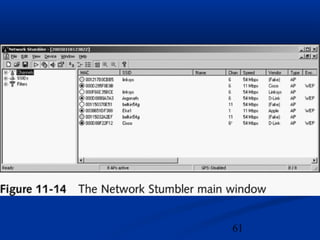
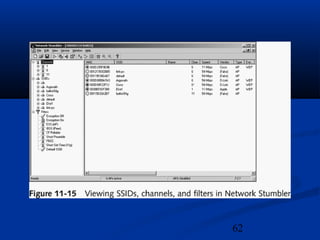
This chapter discusses hacking wireless networks. It explains wireless technology and standards such as 802.11. Authentication in wireless networks involves establishing that a user is authorized to use the network. Various wireless hacking tools and the process of "wardriving" are also described.