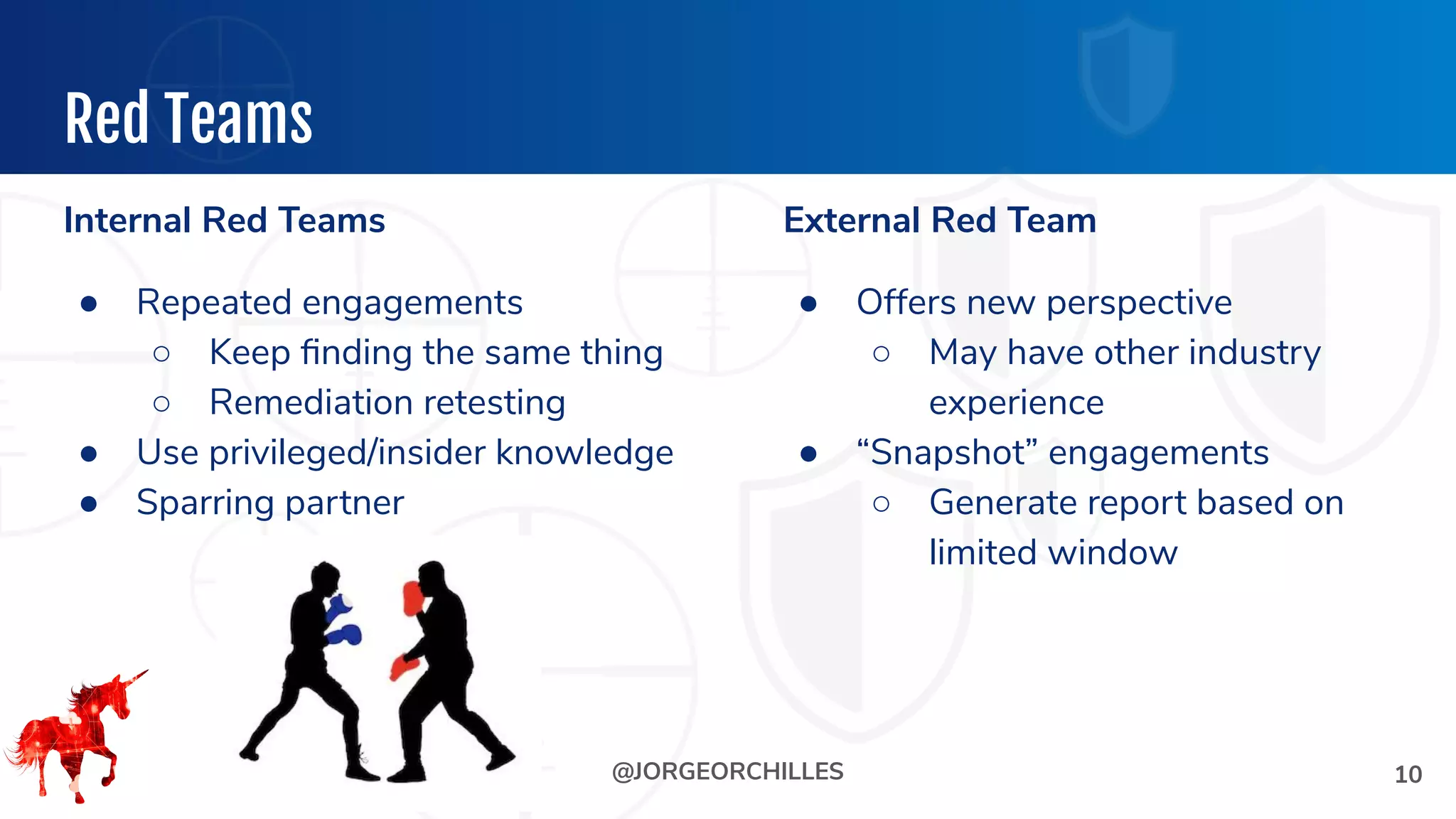
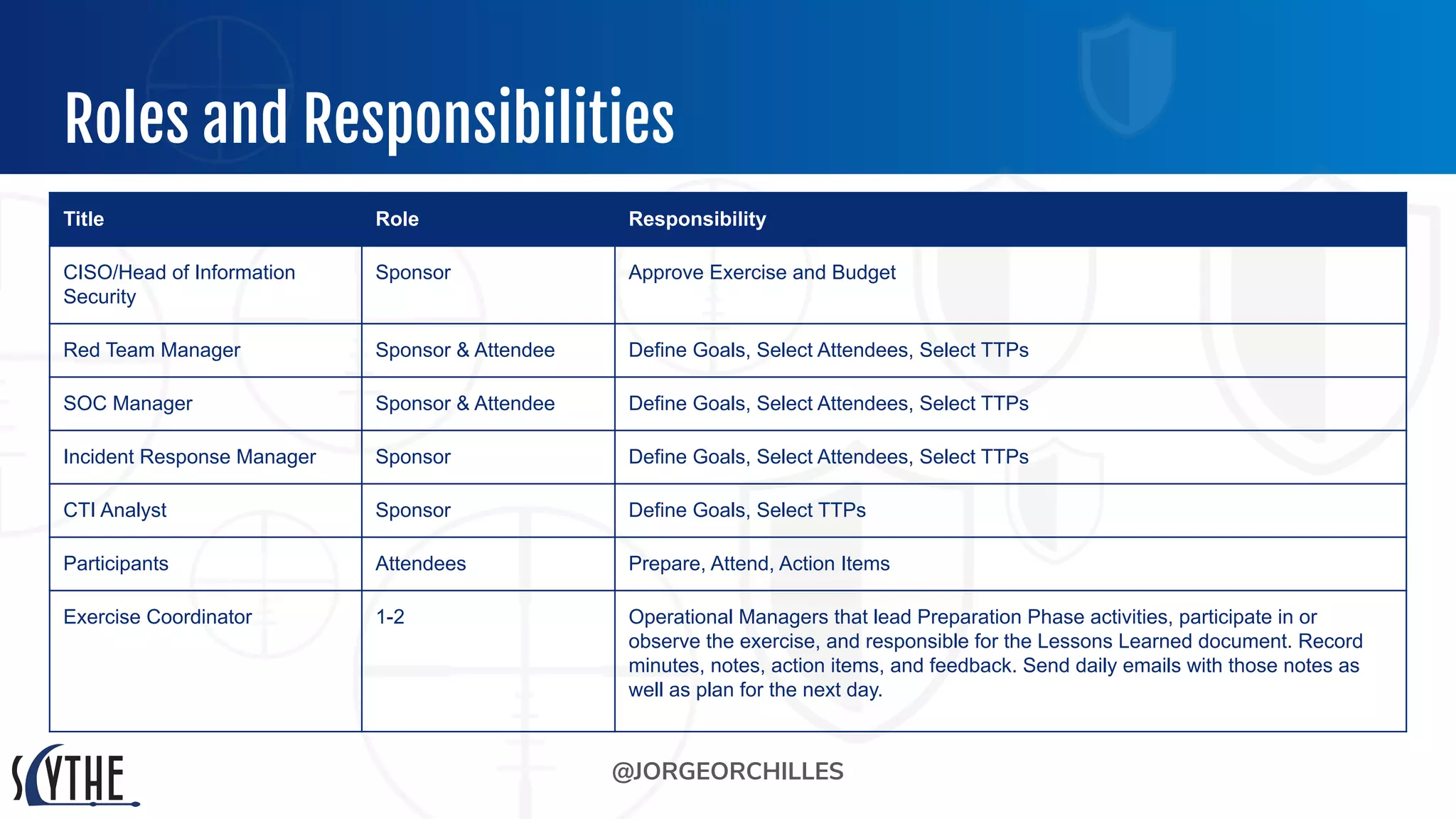
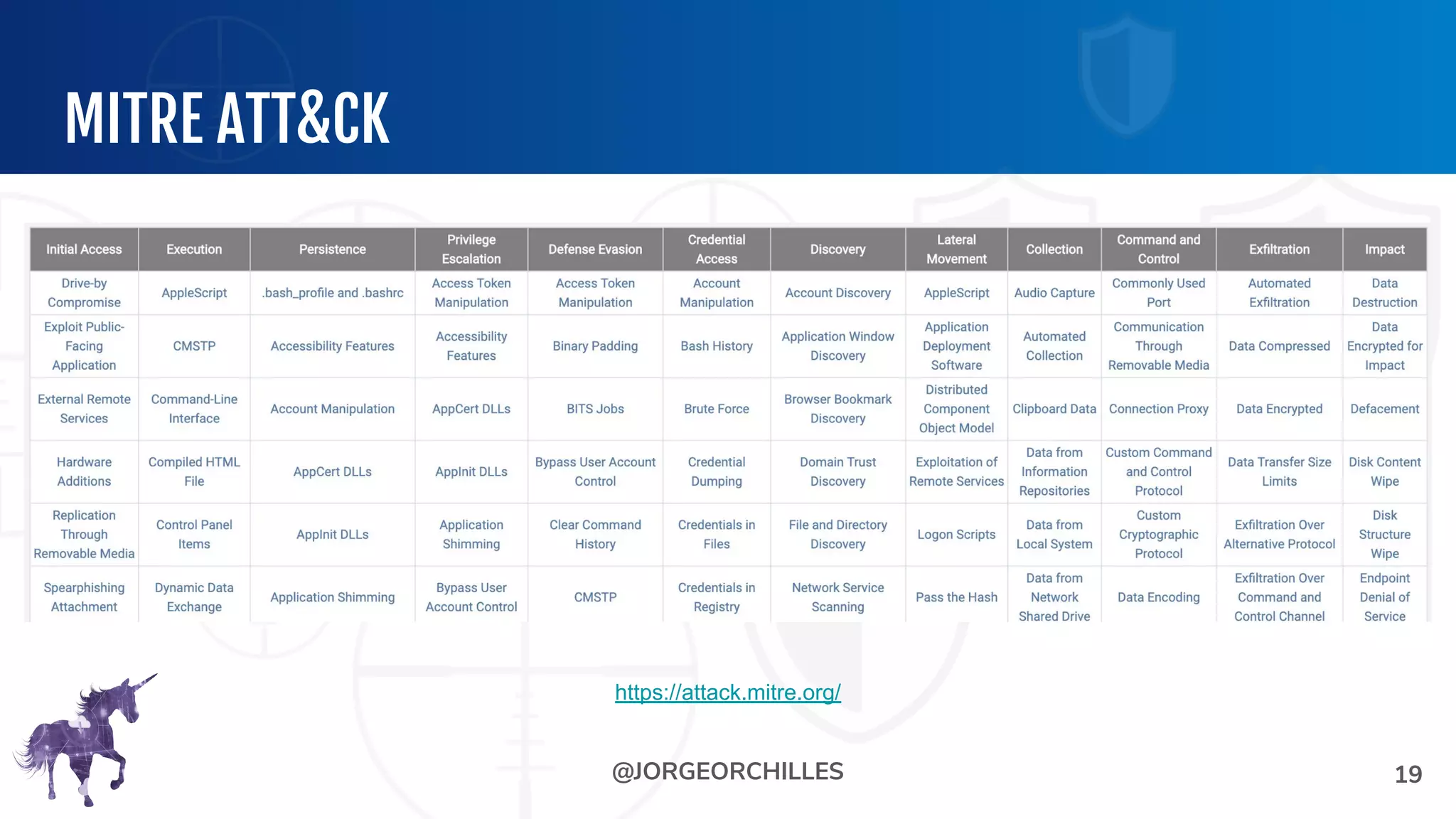
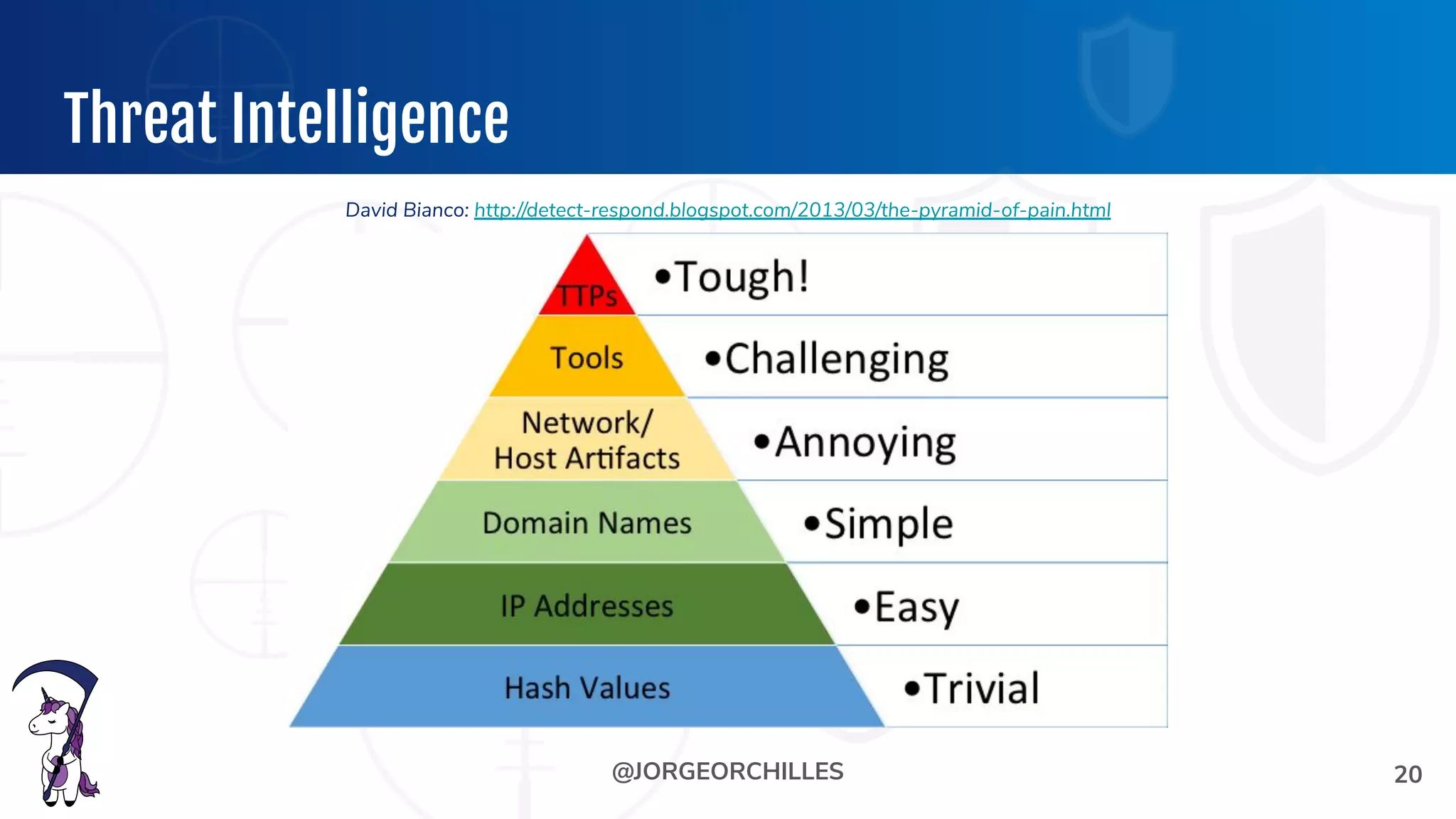
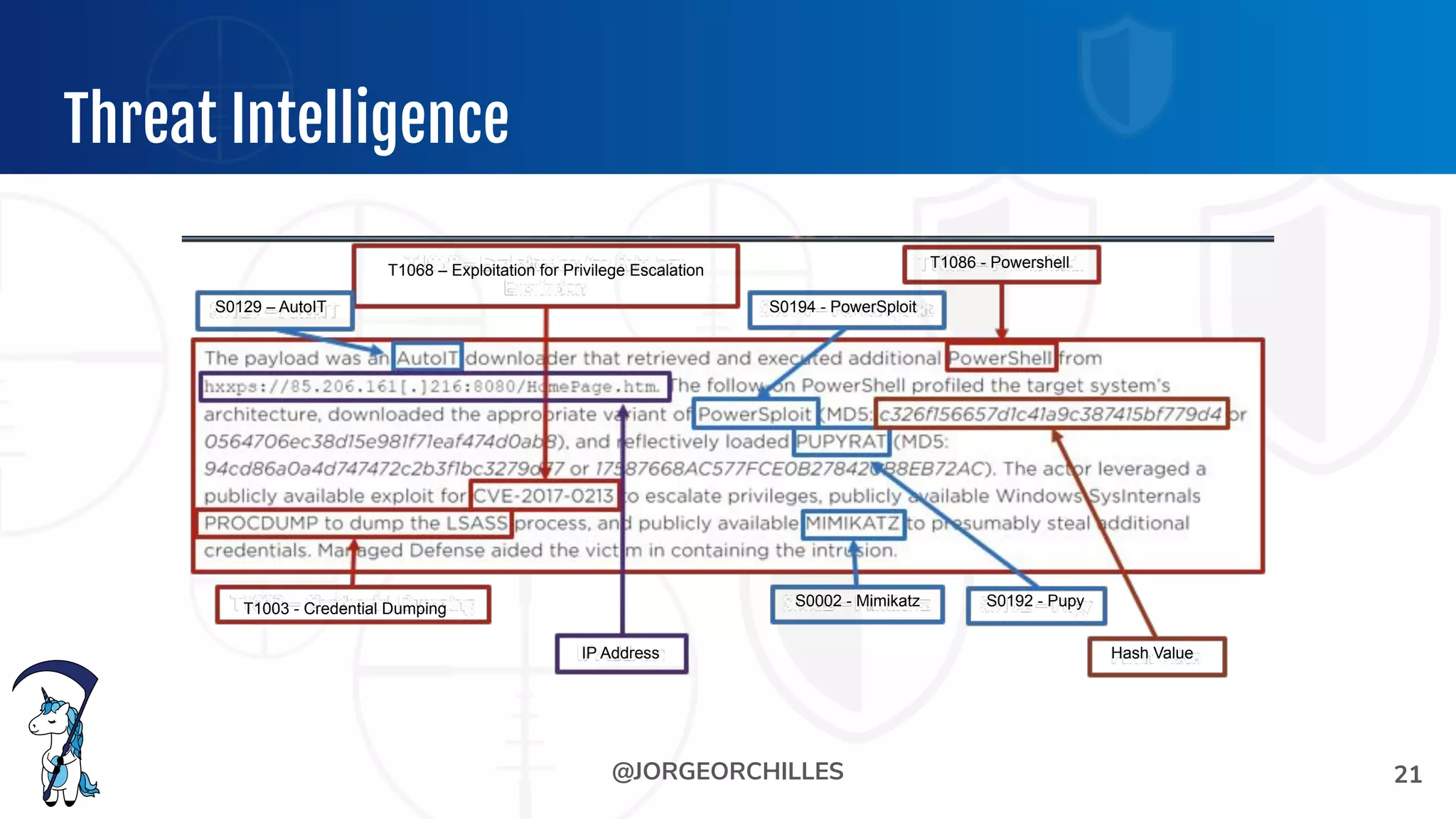
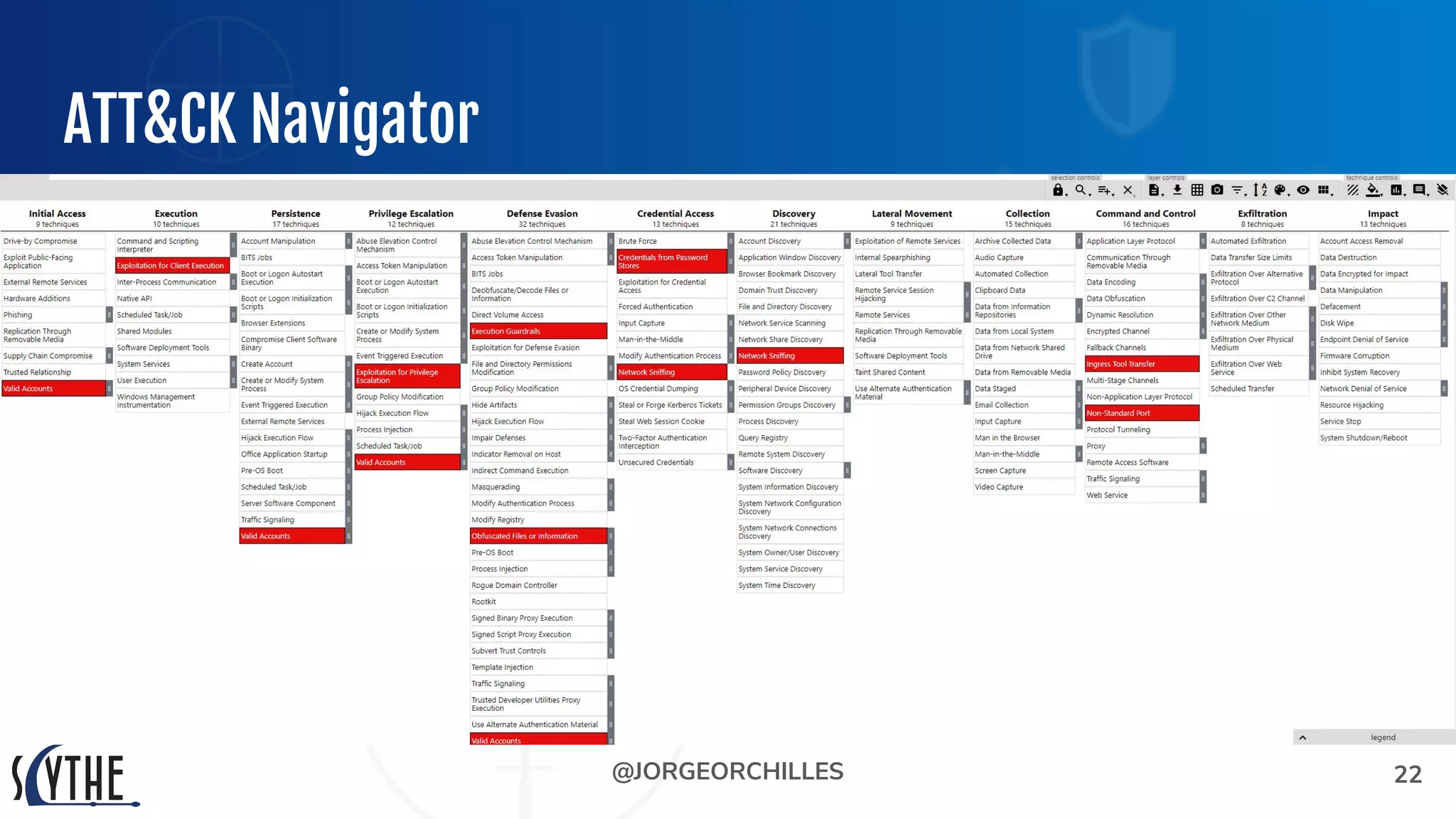
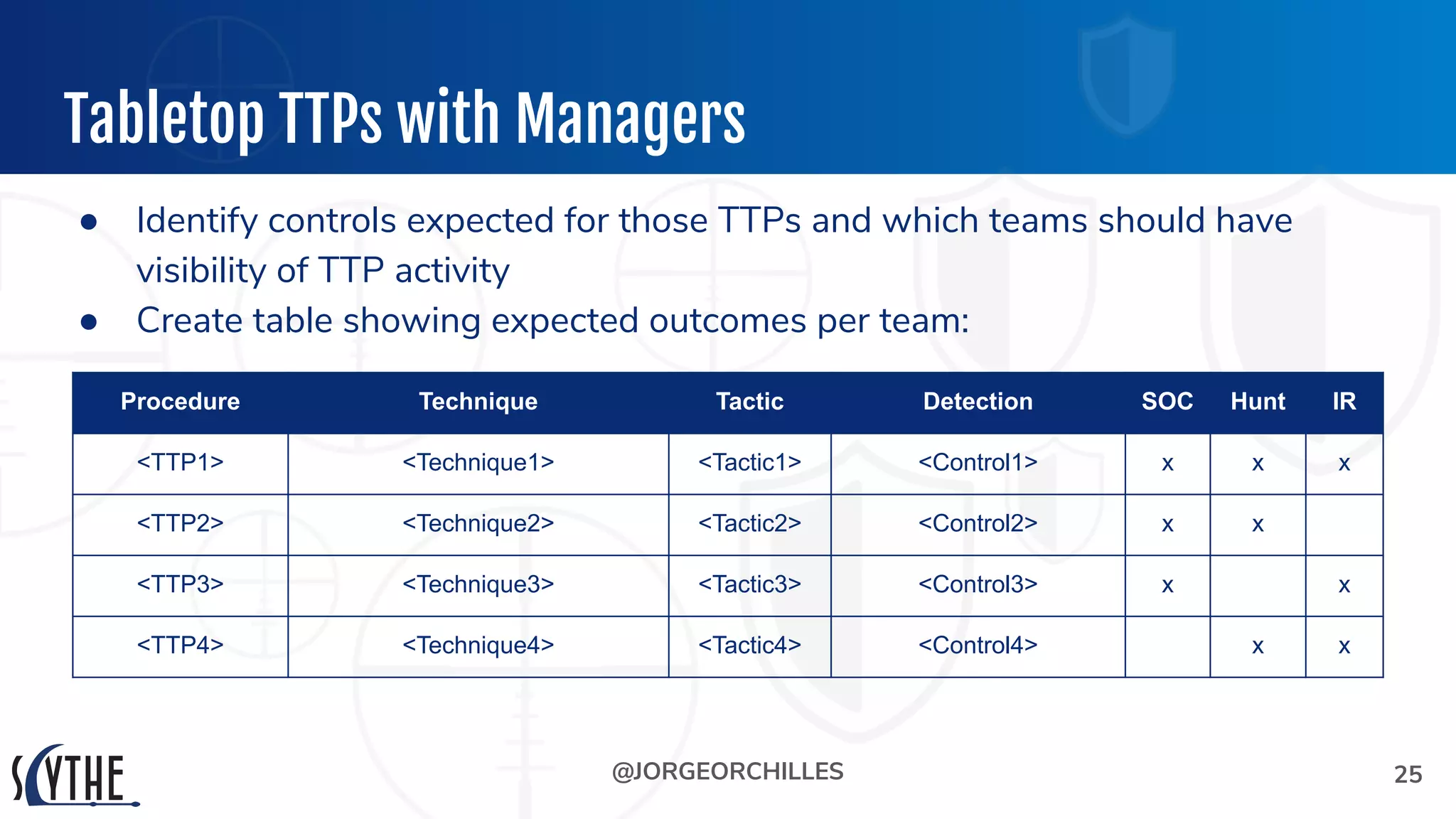
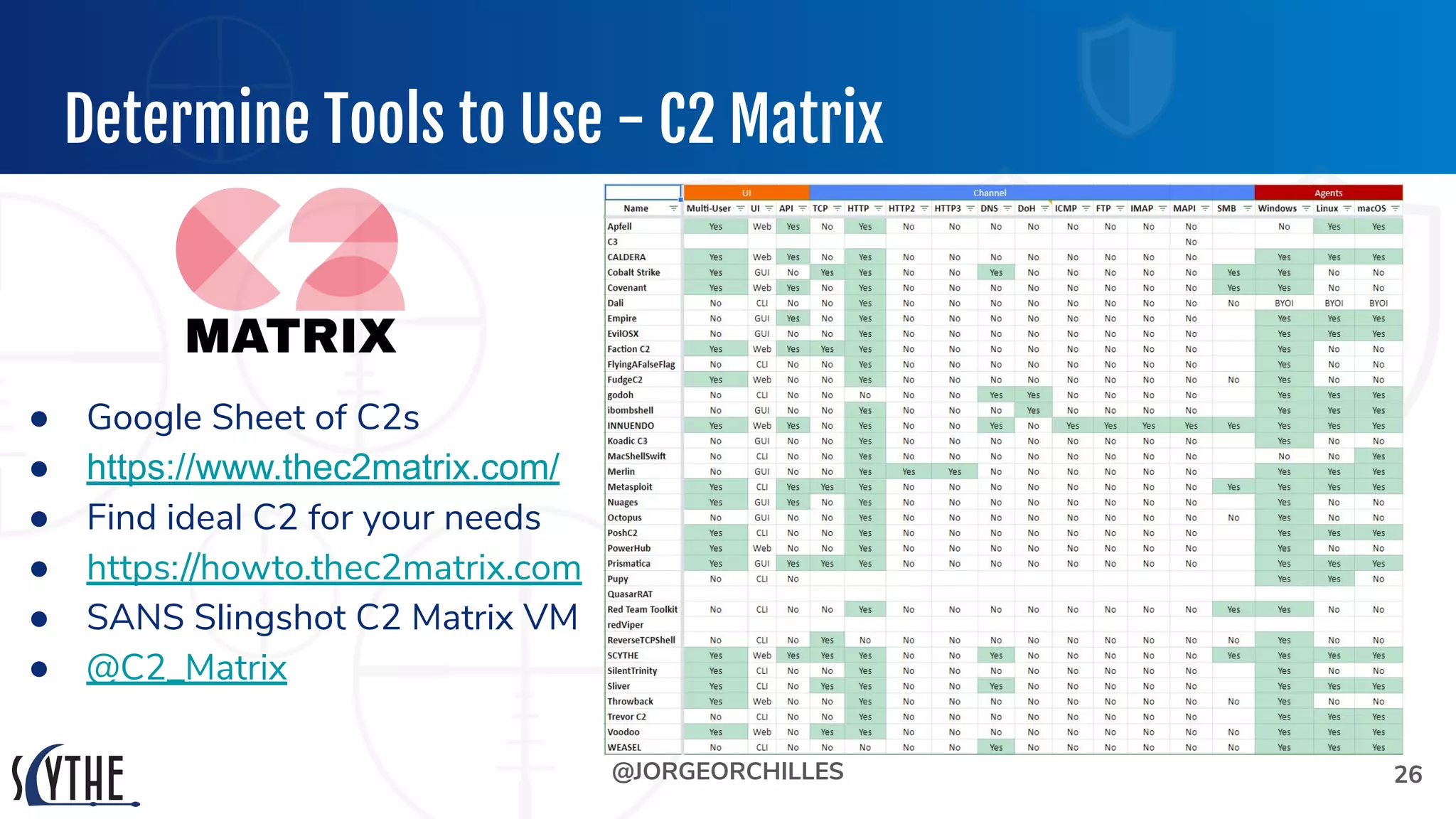
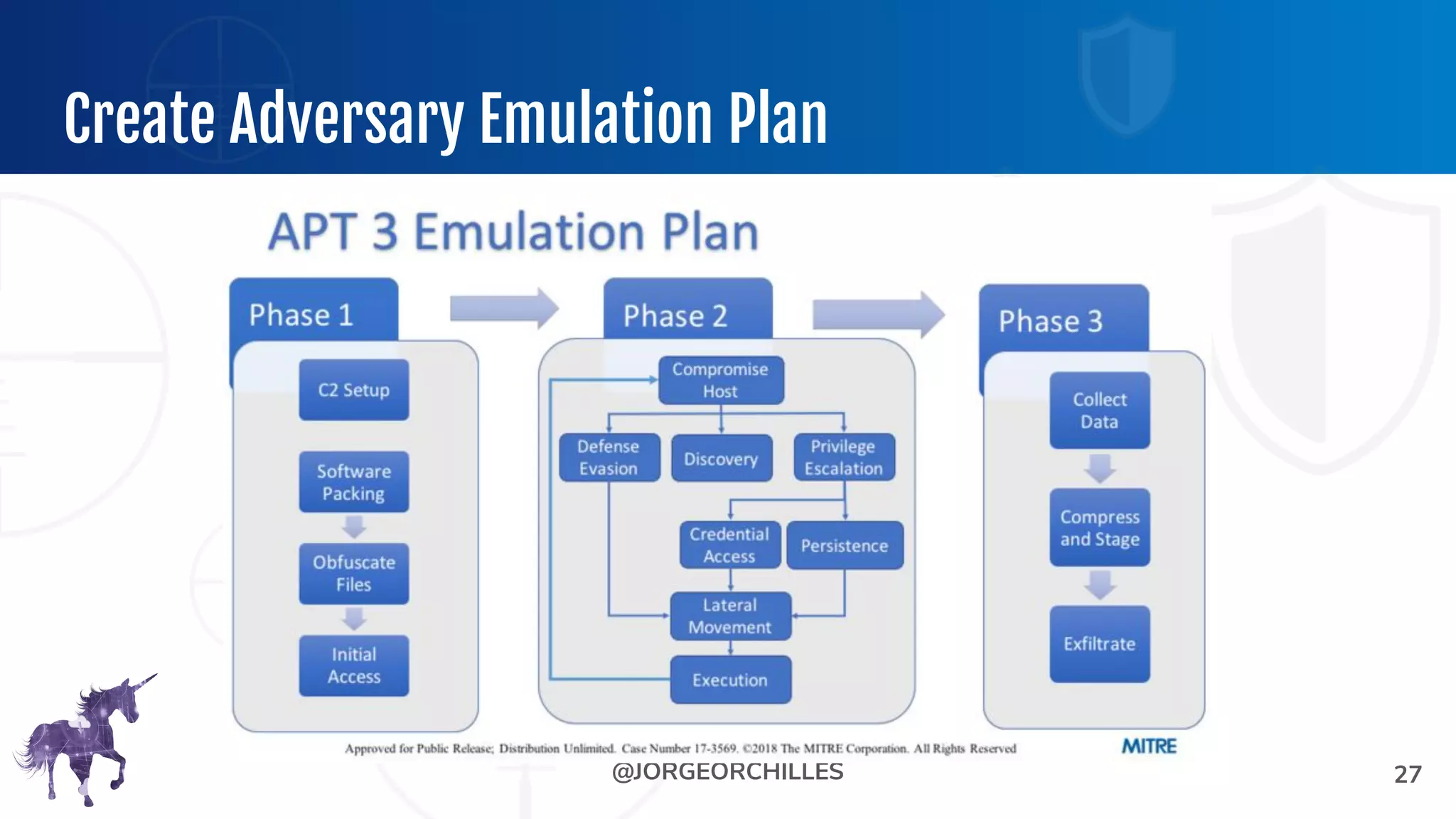
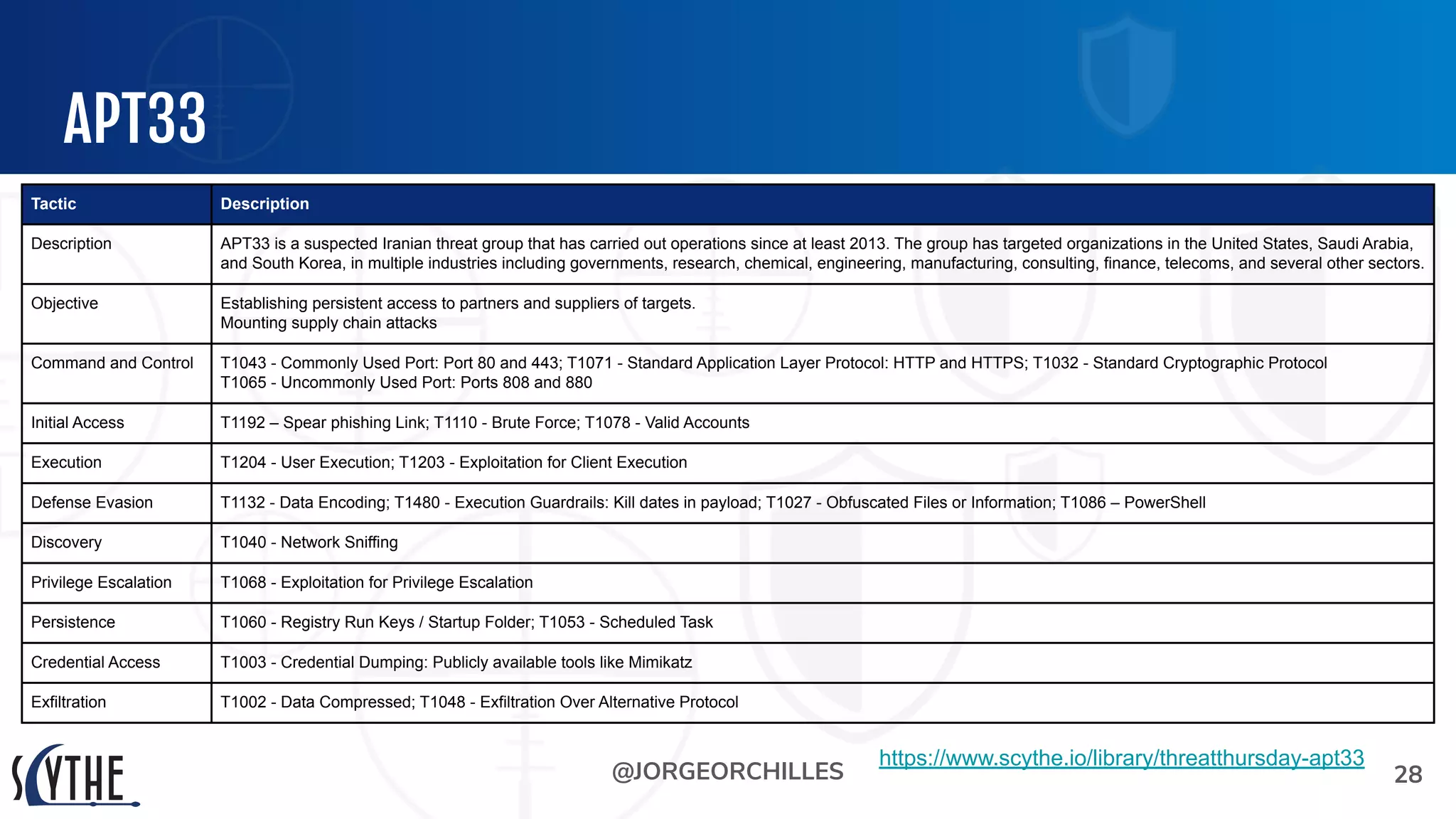
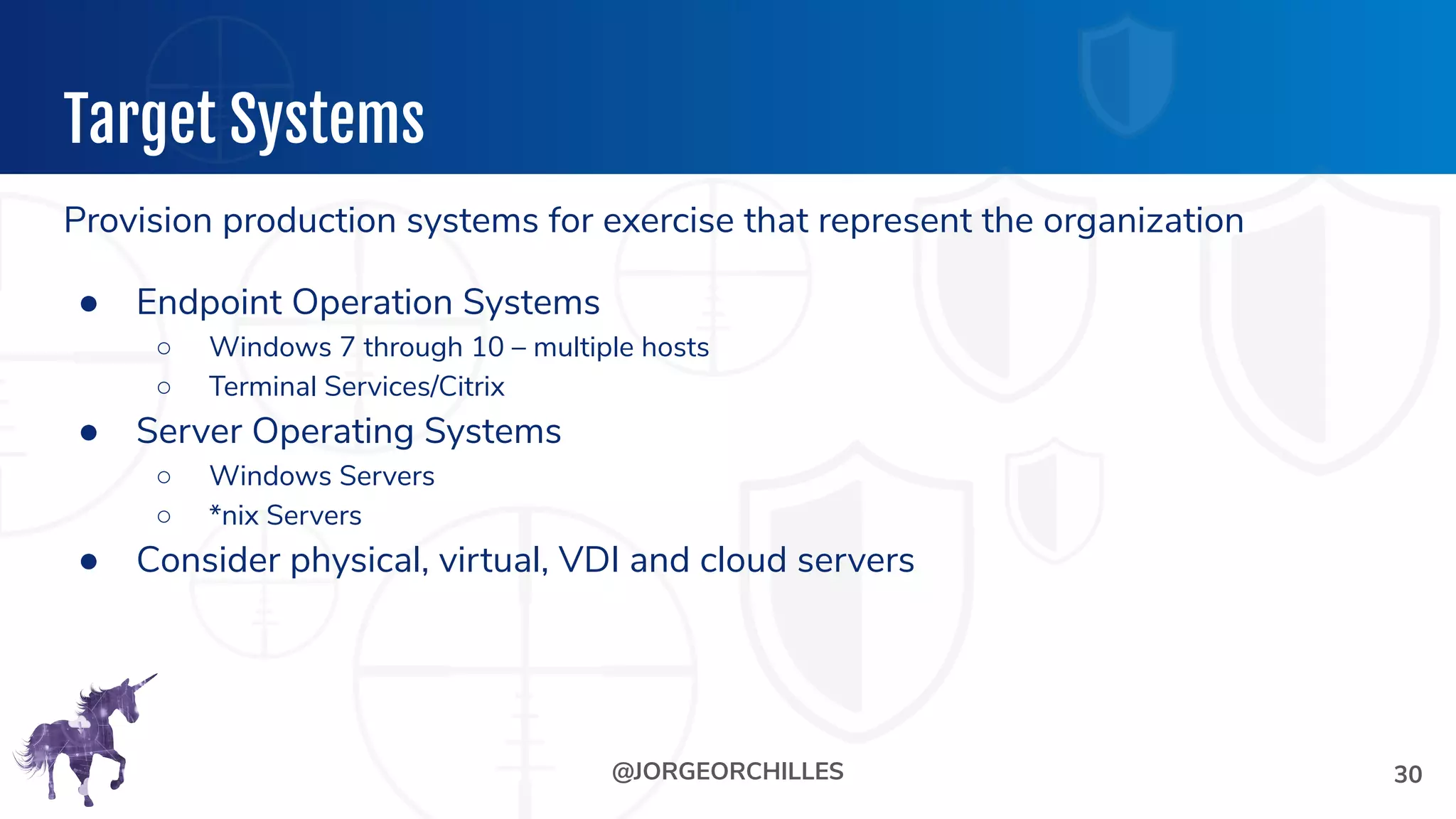
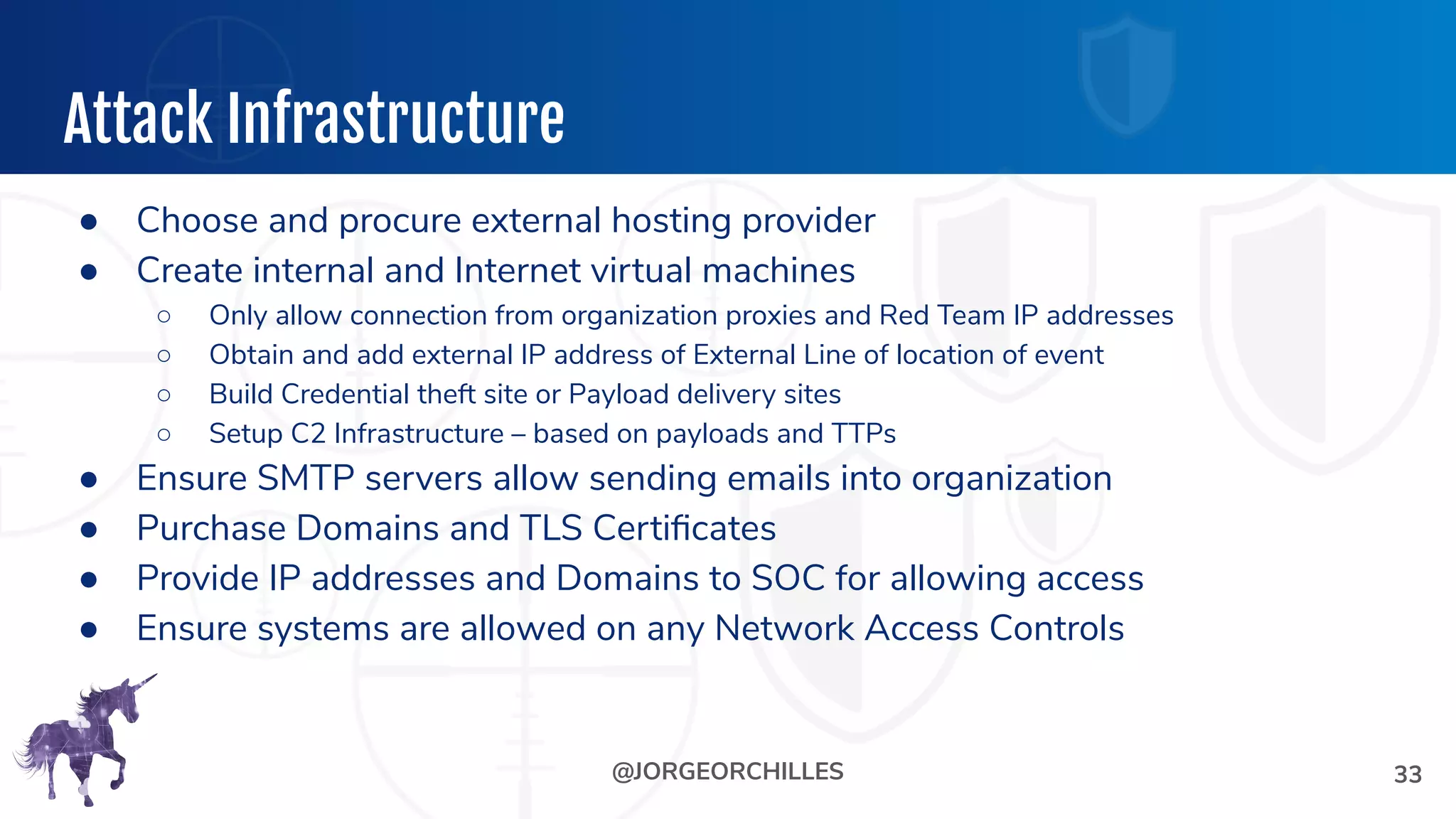
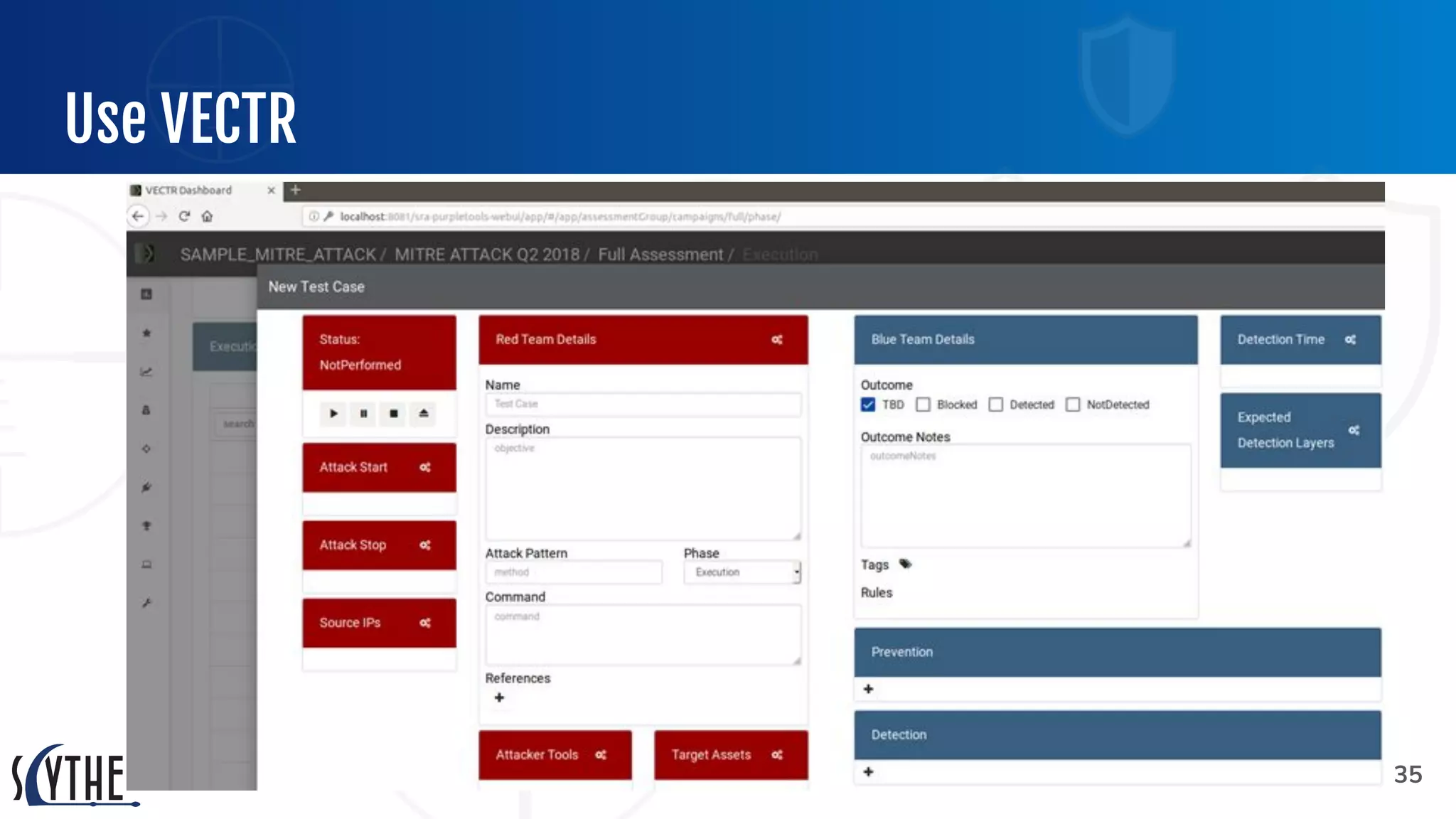
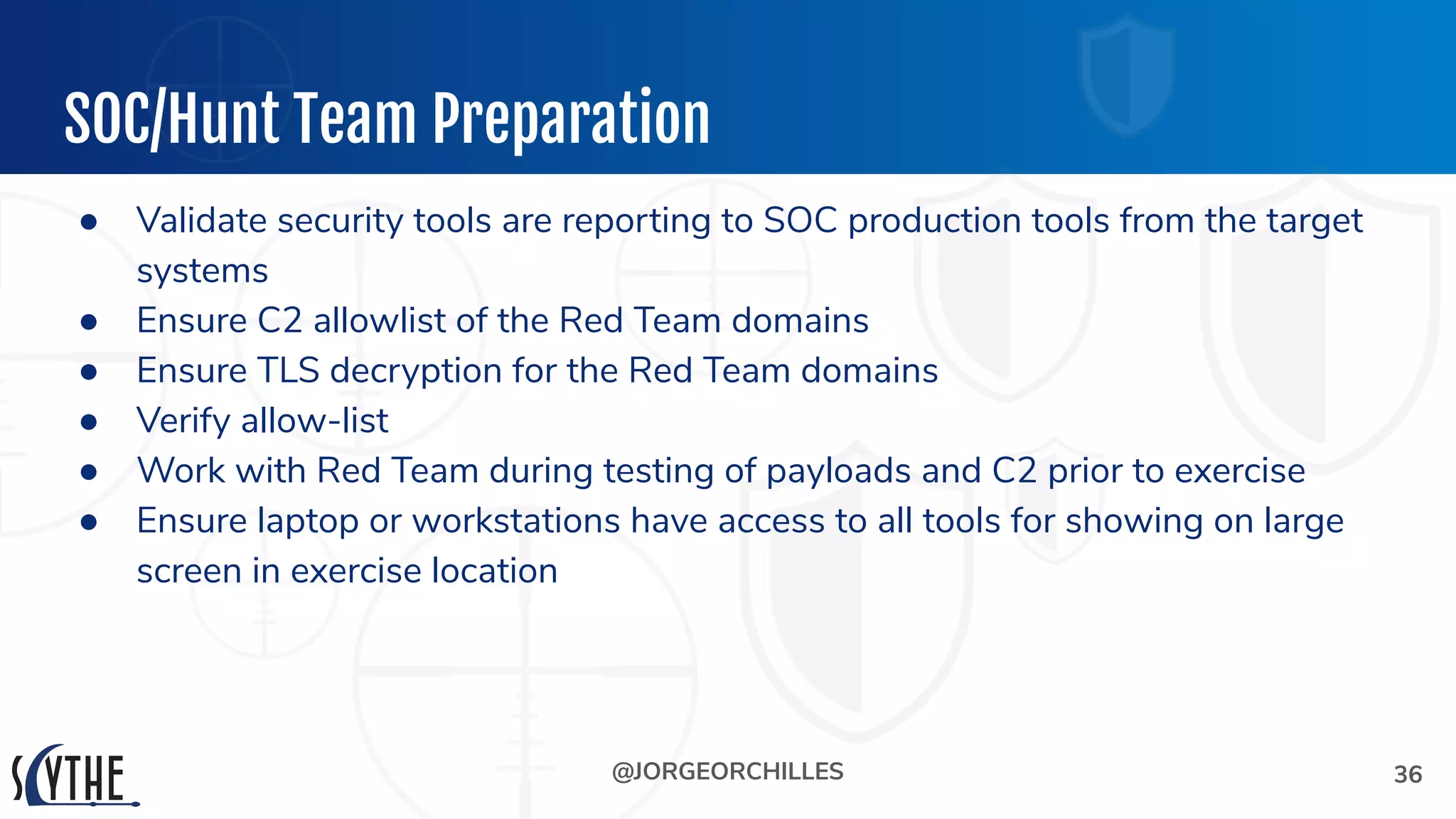
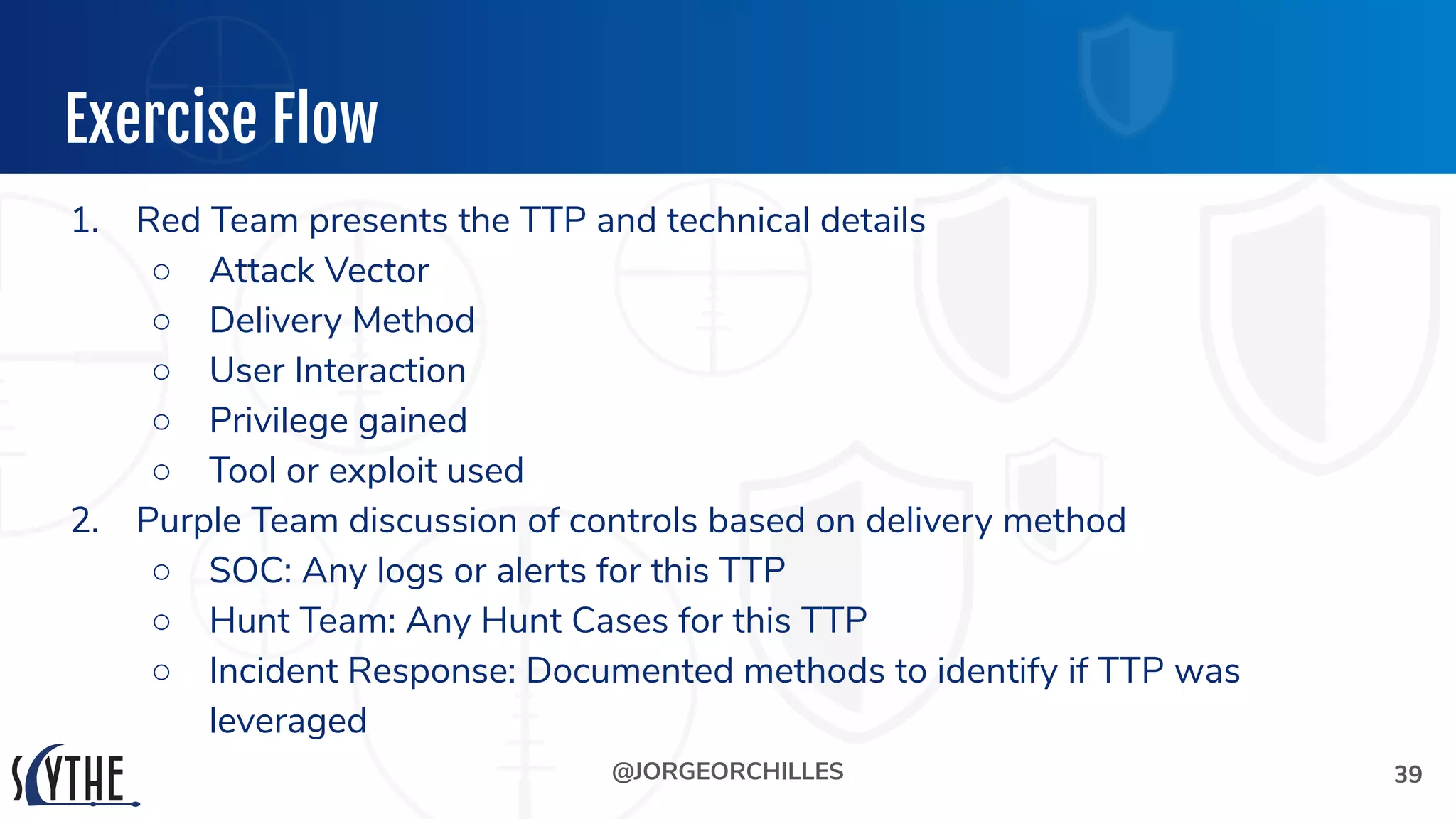
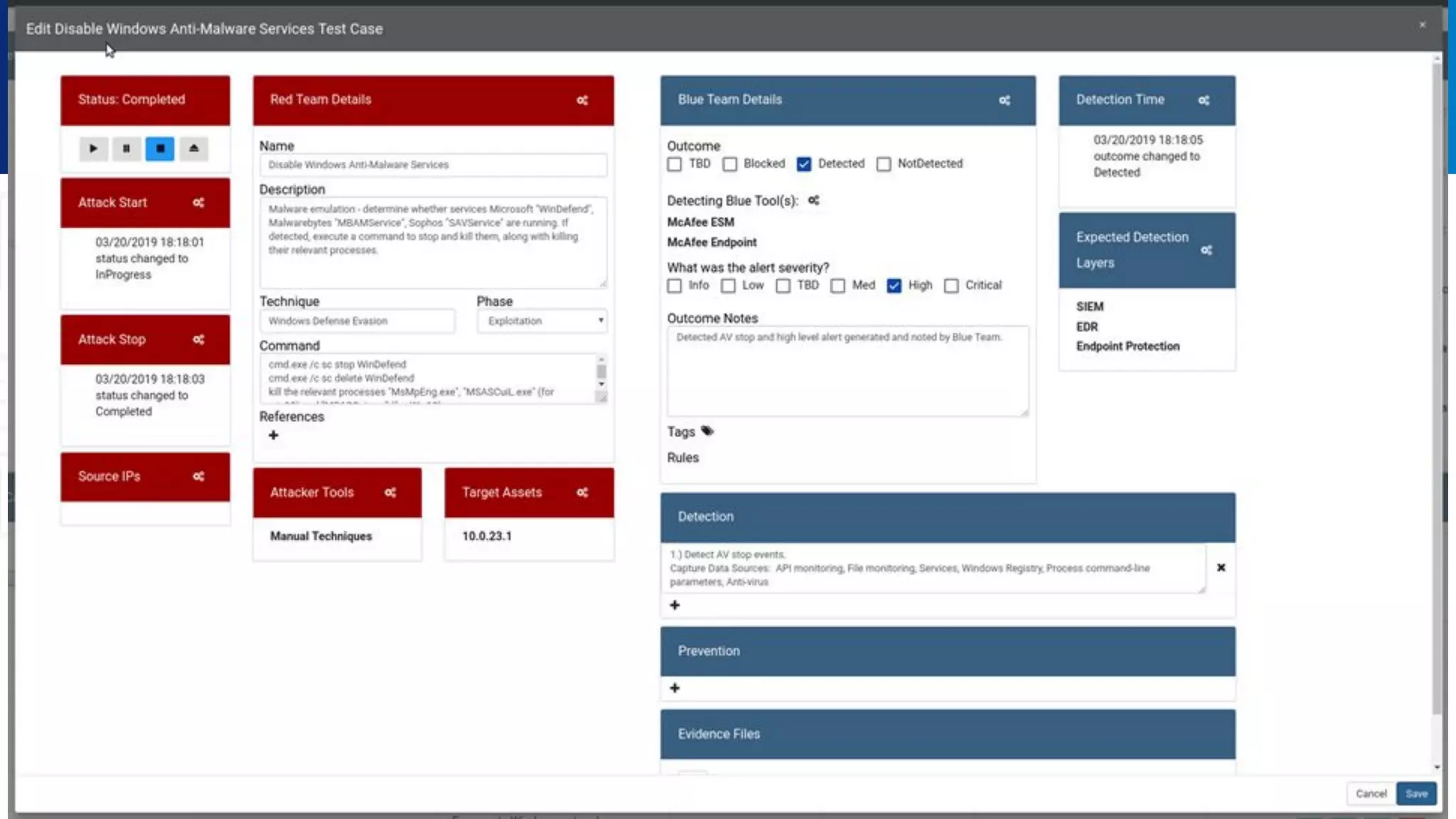
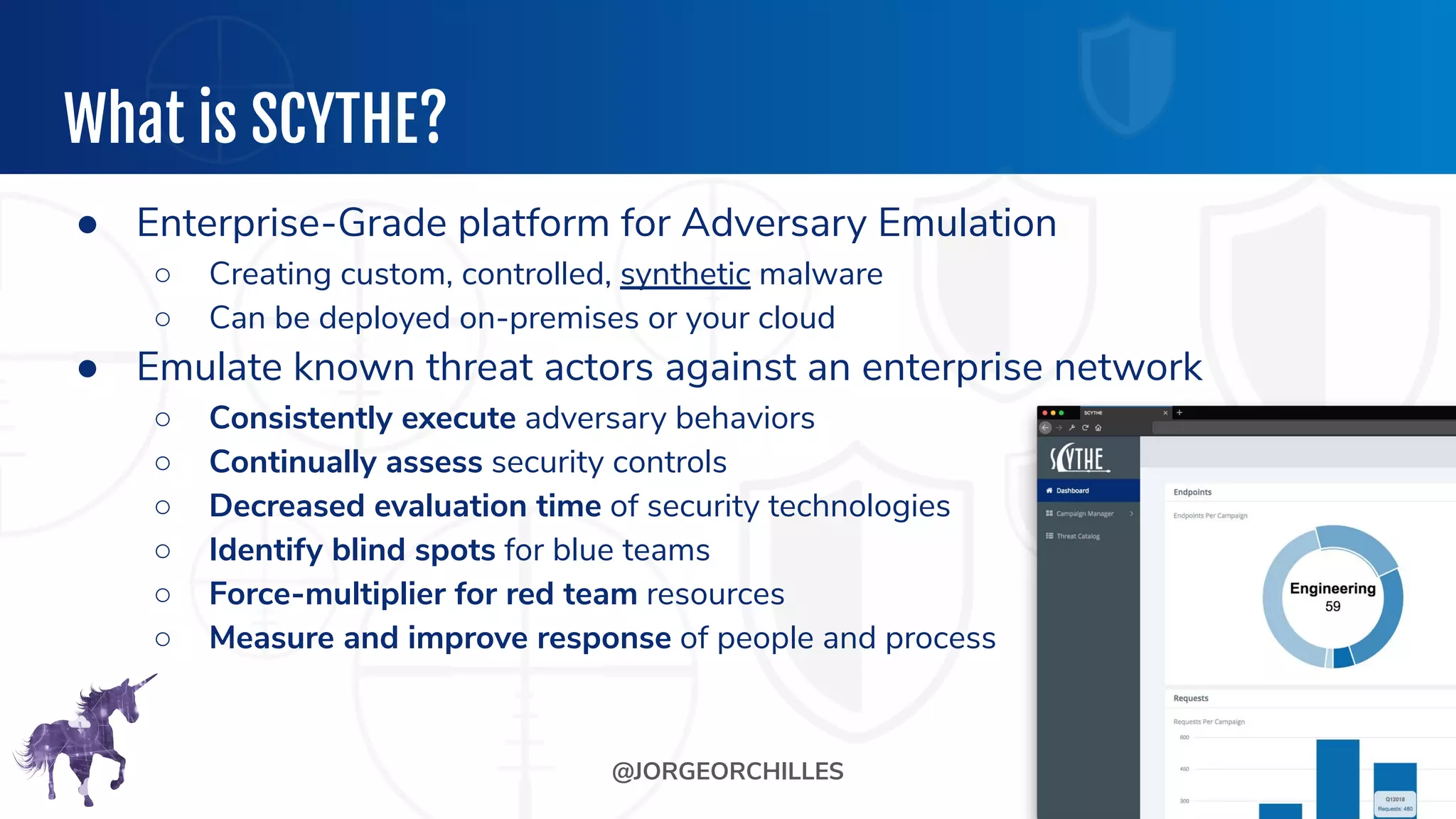
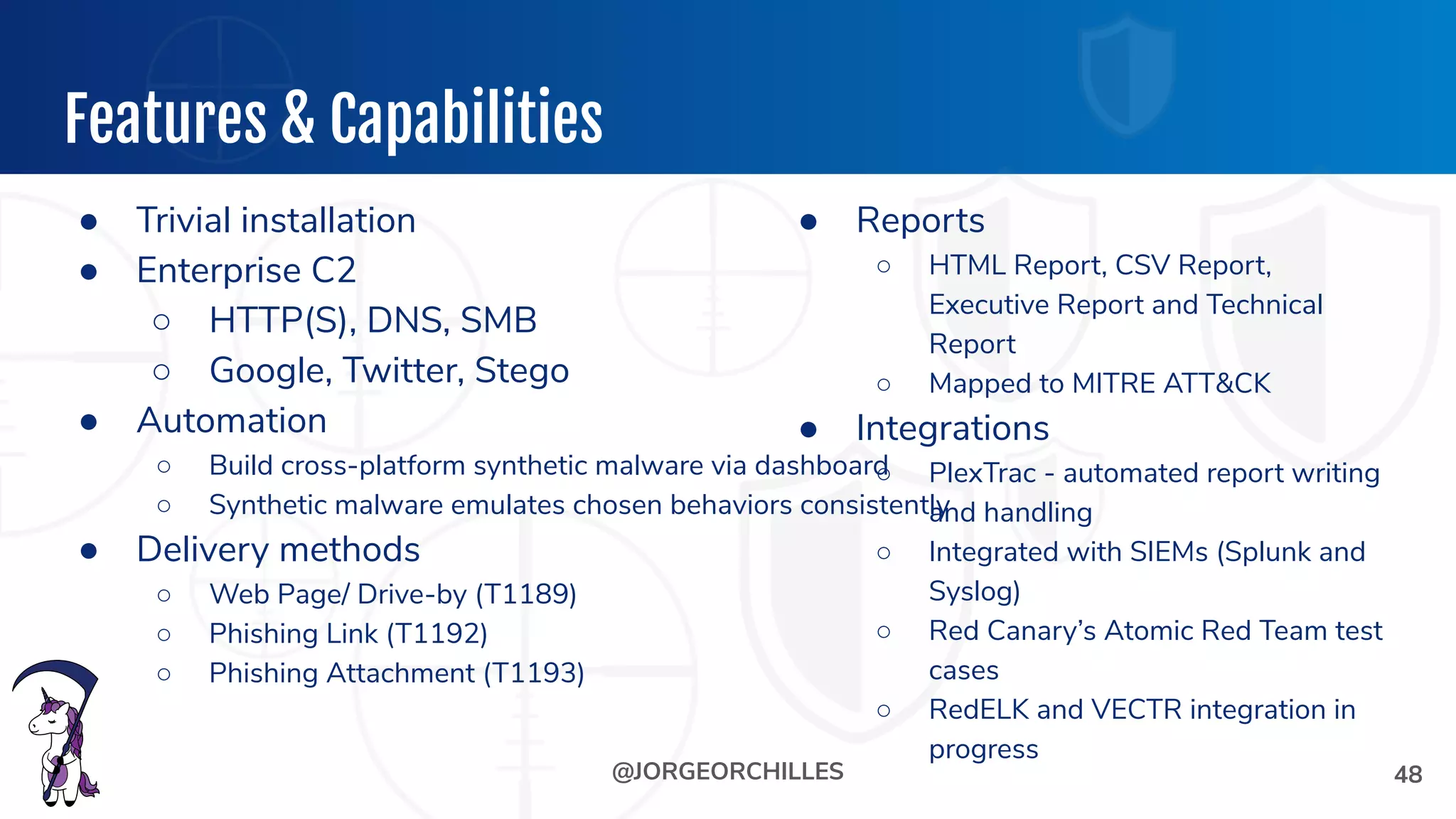
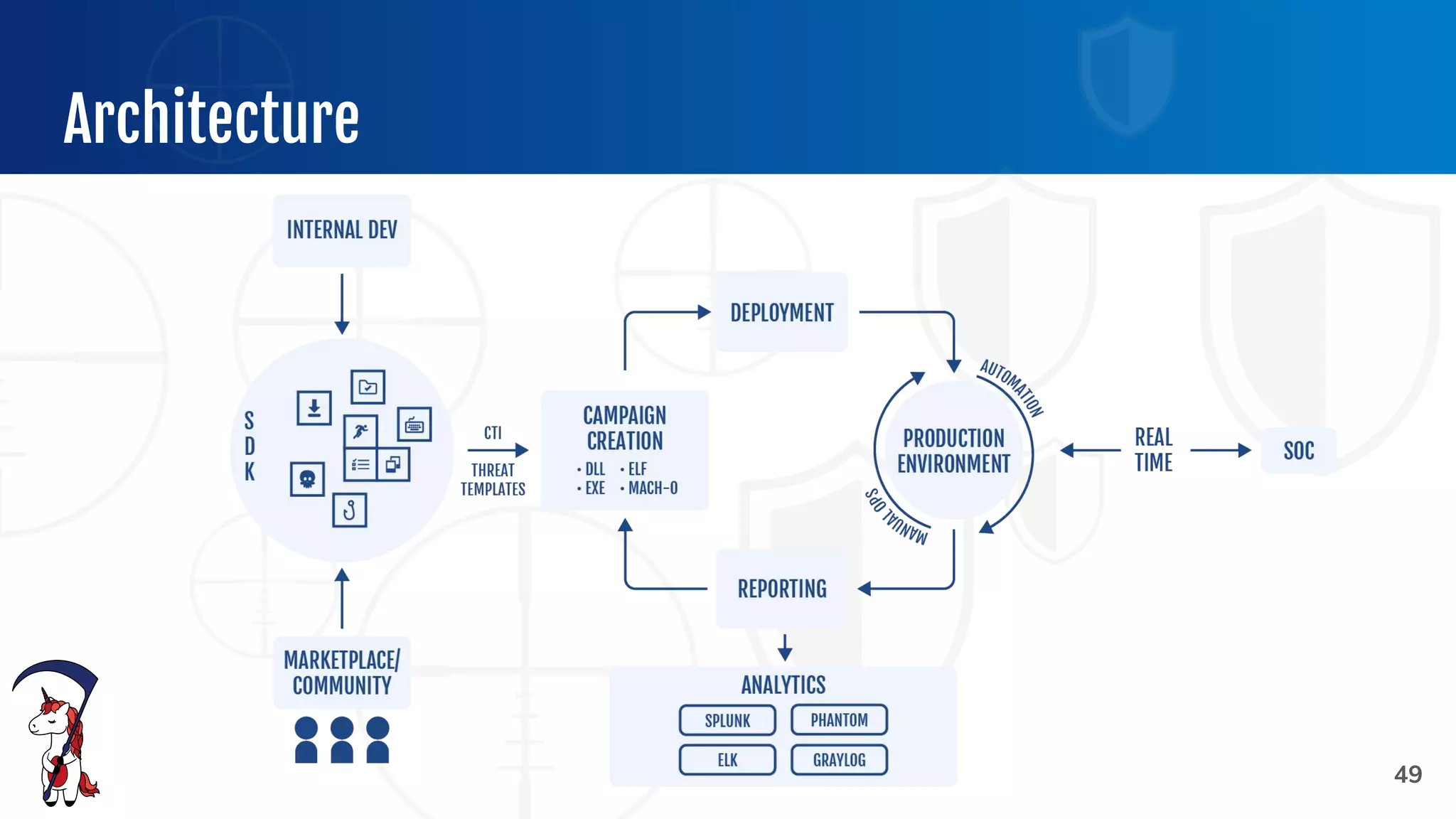
The document outlines the preparation and execution of purple team exercises, focusing on the collaboration between red and blue teams to enhance an organization's cybersecurity posture. It details roles, methodologies, threat intelligence, and logistics involved in conducting these exercises effectively. Key objectives include emulating adversarial behavior, measuring defenses, and improving detection and response capabilities within organizations.