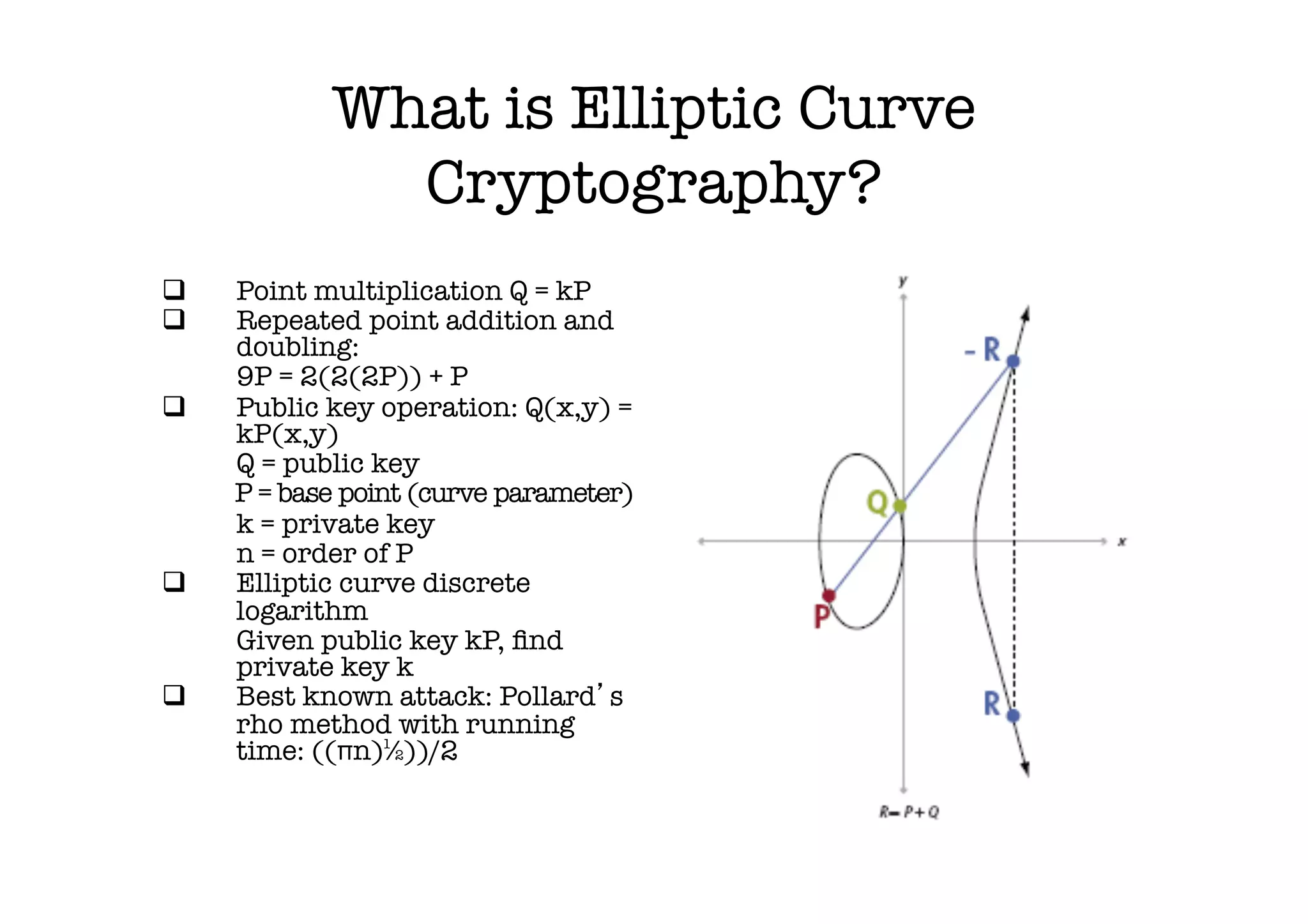
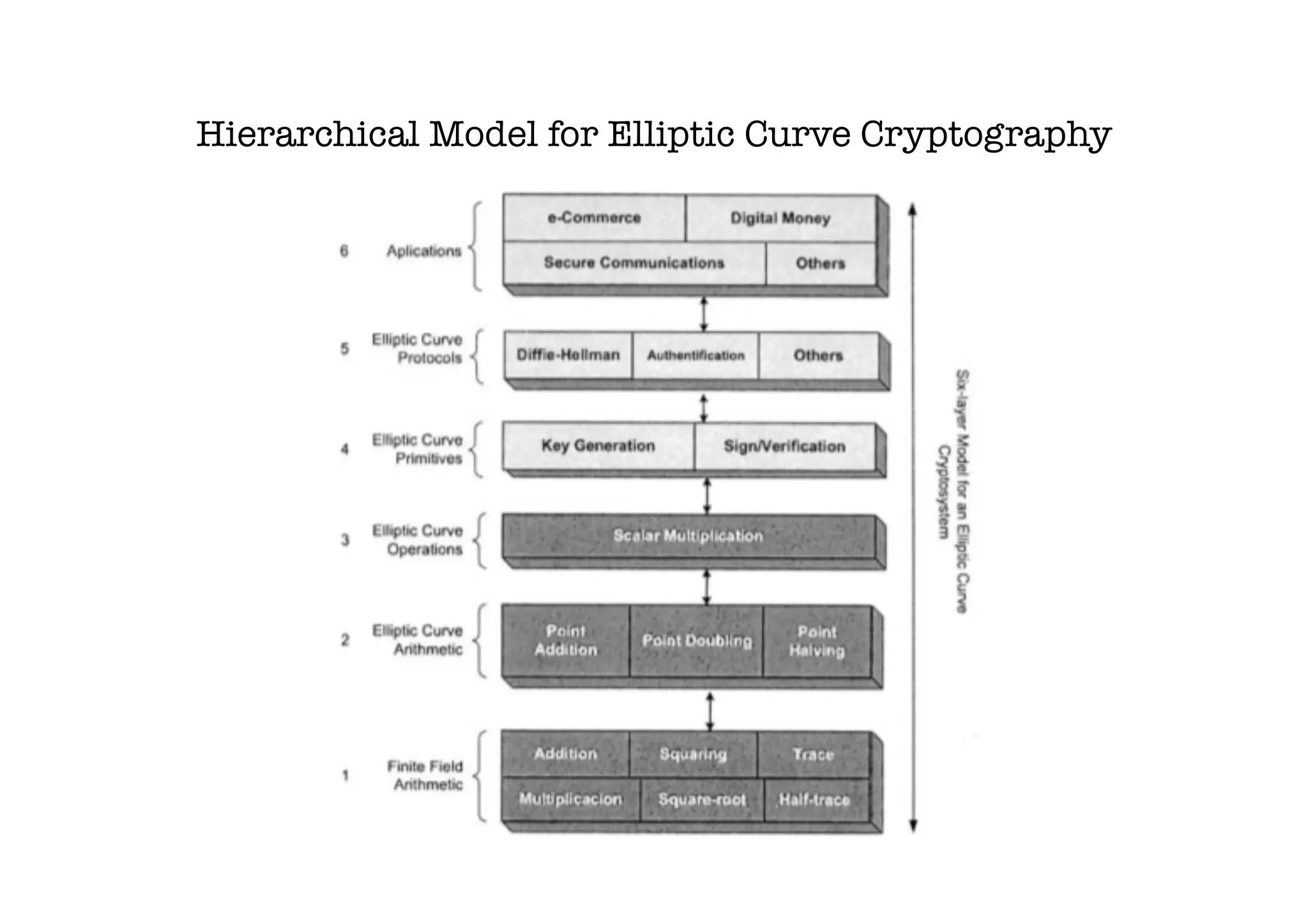
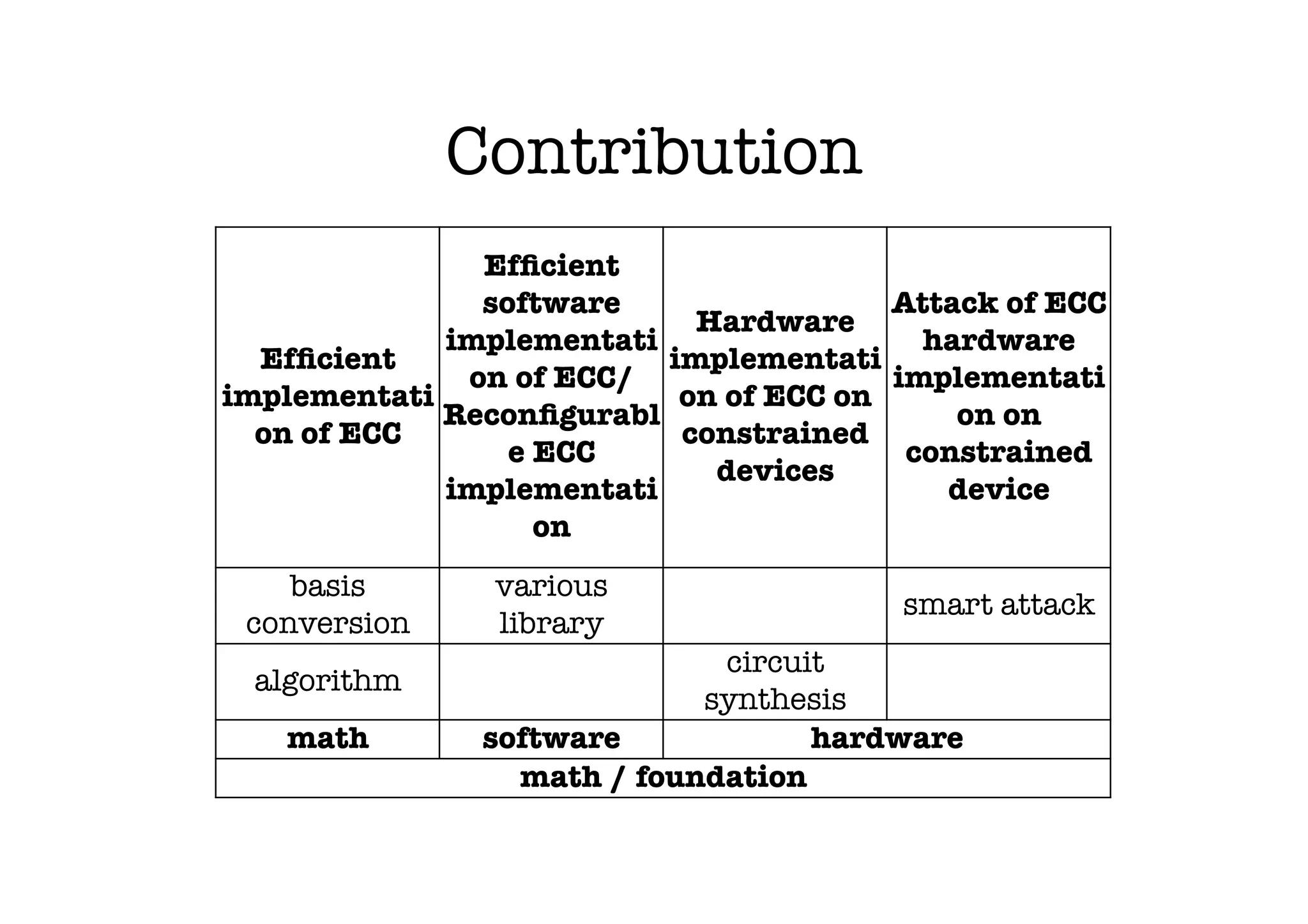
The document discusses the need for a PhD student to learn advanced mathematics for research into implementing elliptic curve cryptography on constrained devices. The research aims to develop efficient and secure implementations of elliptic curve cryptography algorithms for tiny spaces around 1mm2. This requires knowledge of number theory, finite fields, algebra, groups, rings, fields, polynomials and their properties to understand elliptic curve cryptography and implement the algorithms securely while targeting constrained devices. The student hopes to improve architectures, develop configurable ECC modules, and create efficient software and hardware implementations to measure the security, efficiency and performance of different approaches.

![My Research
q Title: Elliptic Curve Cryptography
Algorithm Implementation and
Design for Constrained Devices
q Target: Make it fits constrained
devices [constrained devices = some
tiny little spaces about 1mm2]](https://image.slidesharecdn.com/whyineedtolearnsomuchmathformyphdresearch-130308004427-phpapp01/75/Why-i-need-to-learn-so-much-math-for-my-phd-research-2-2048.jpg)