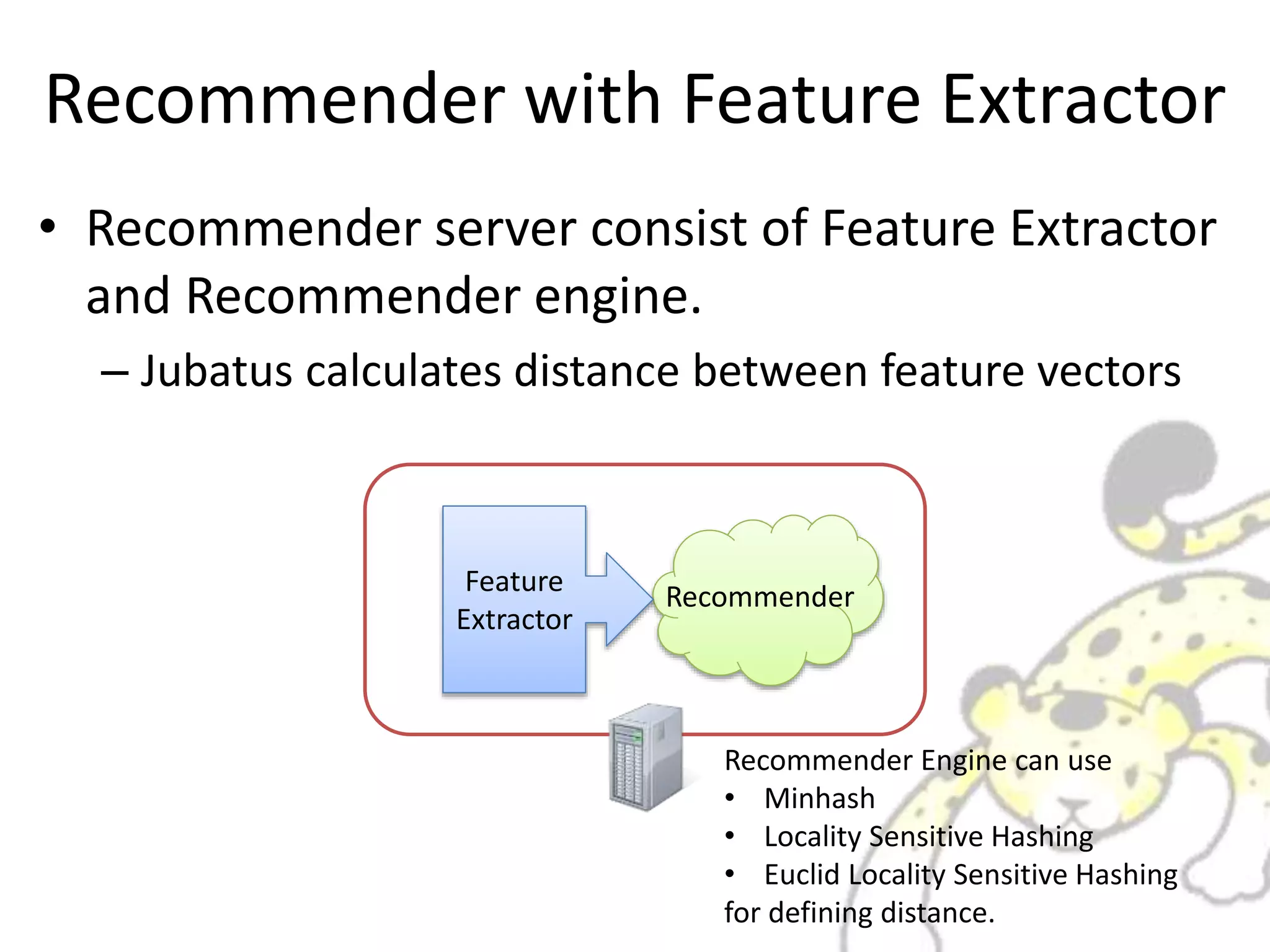
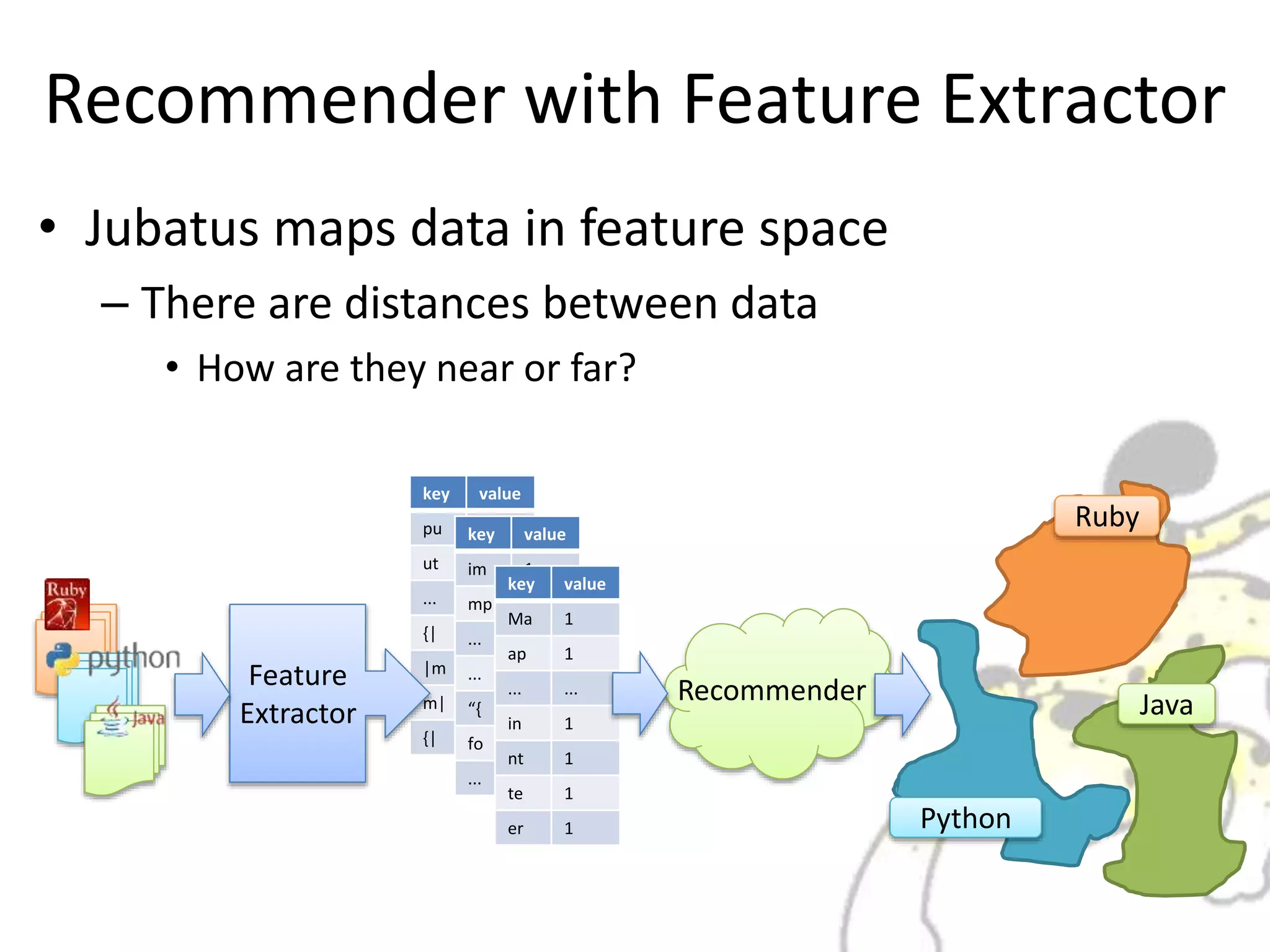
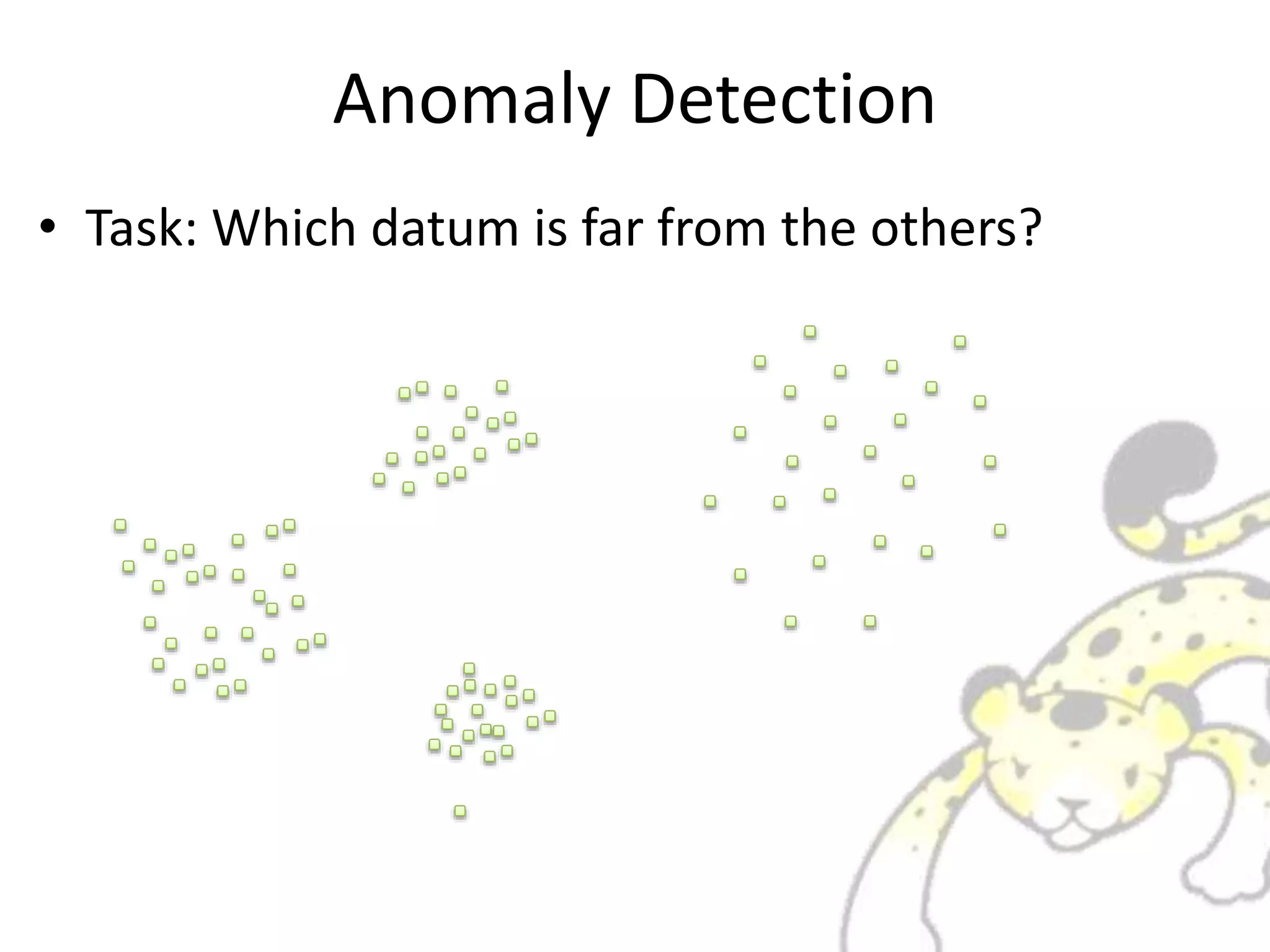
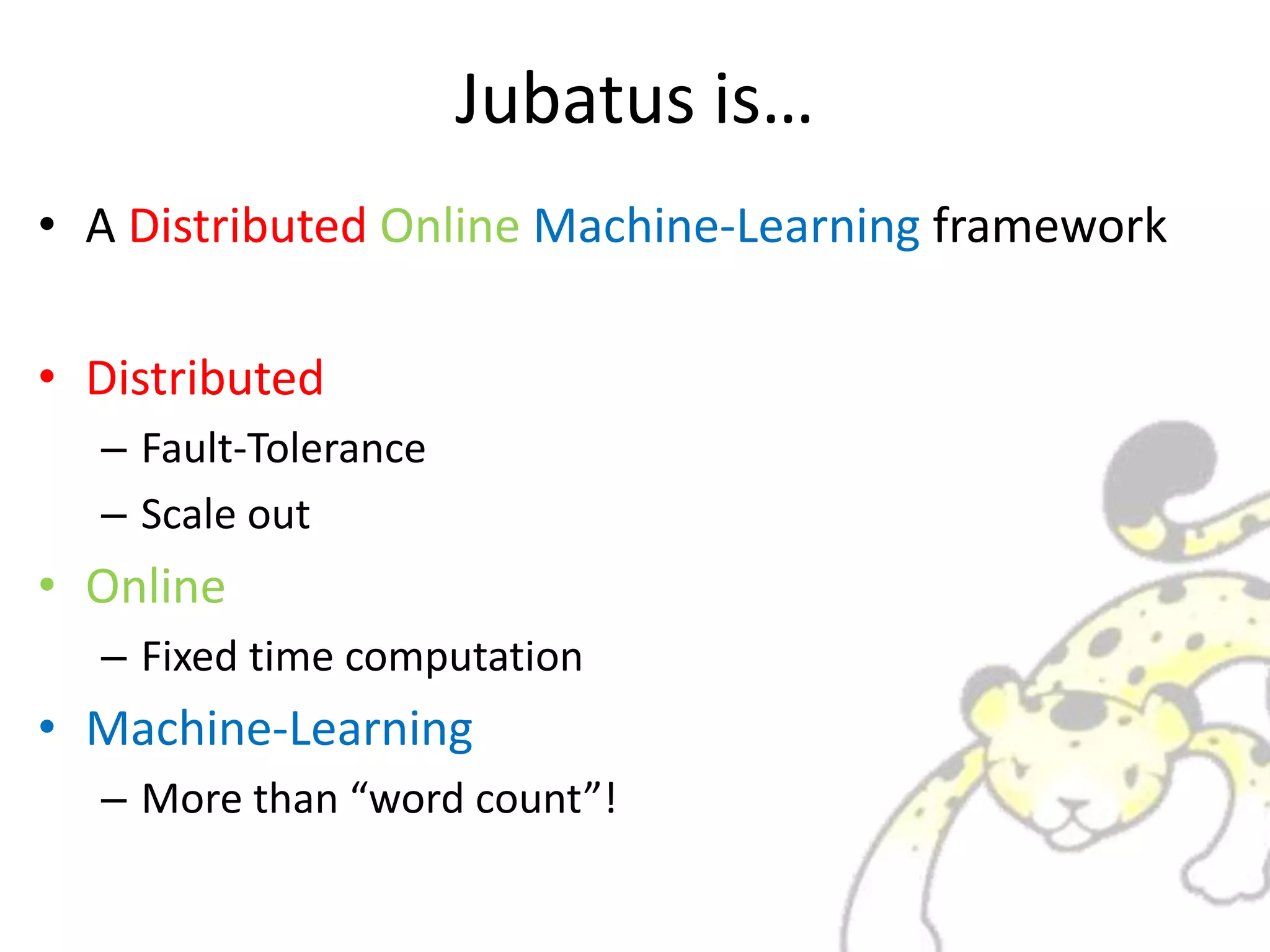
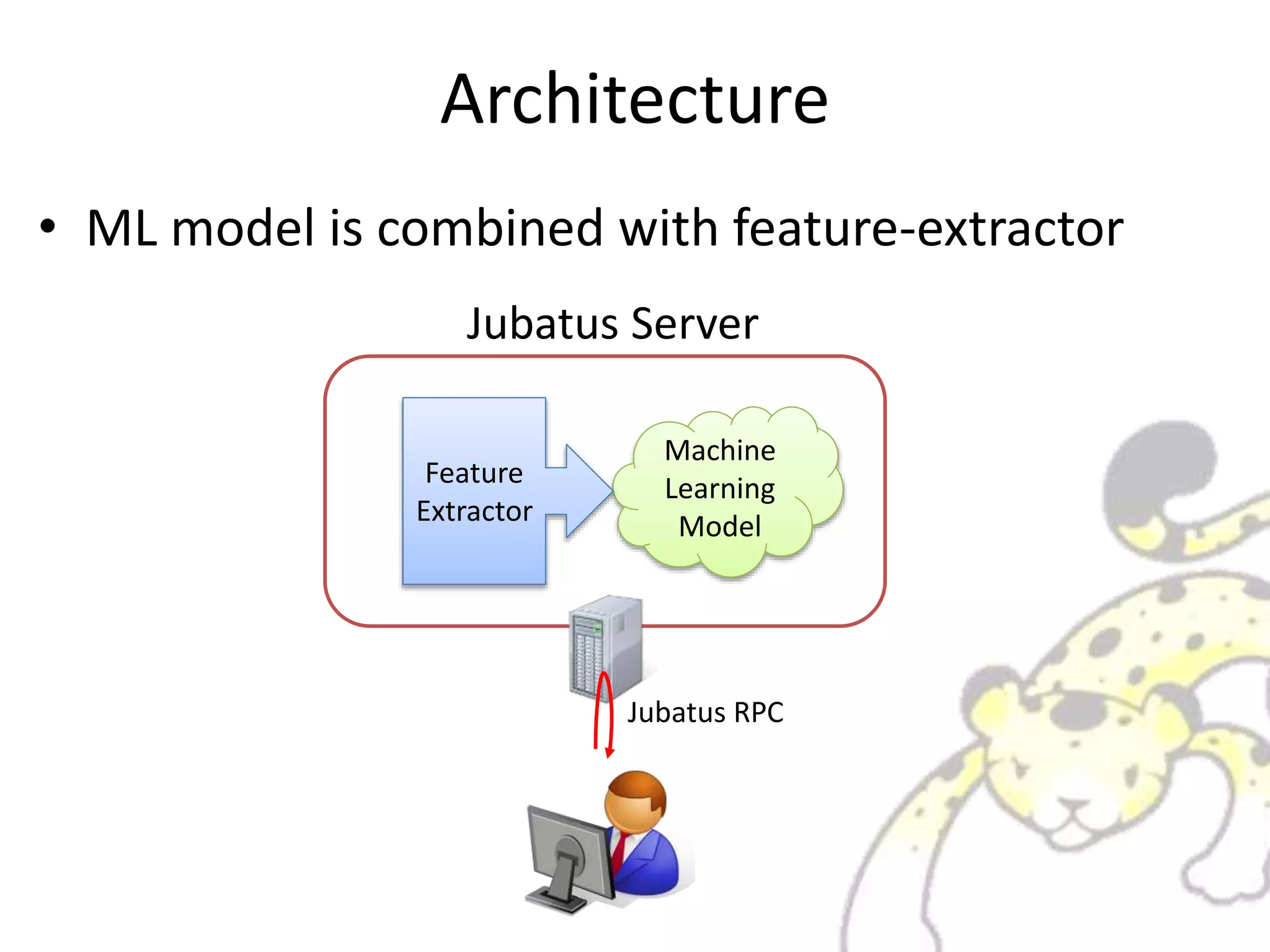
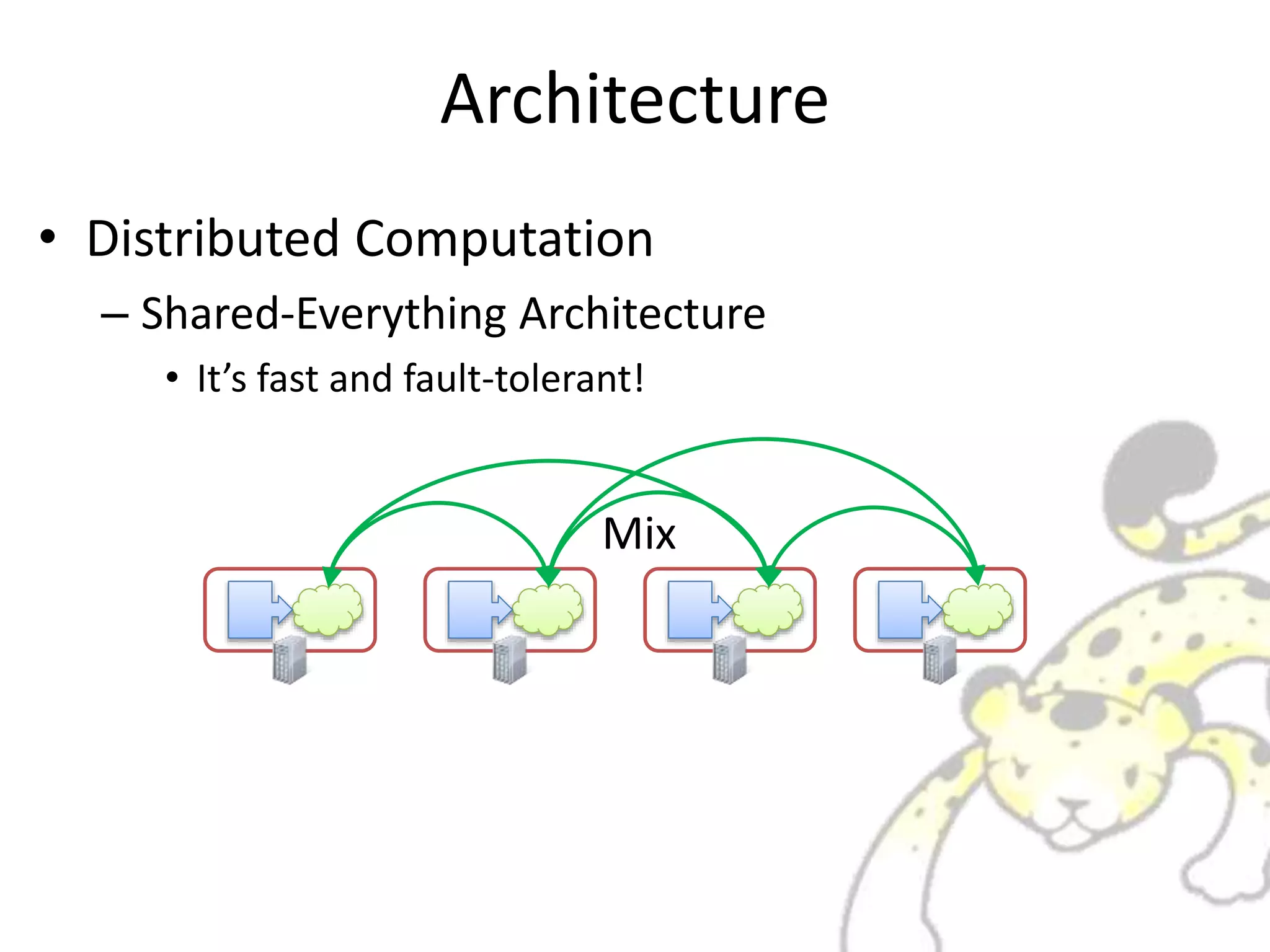
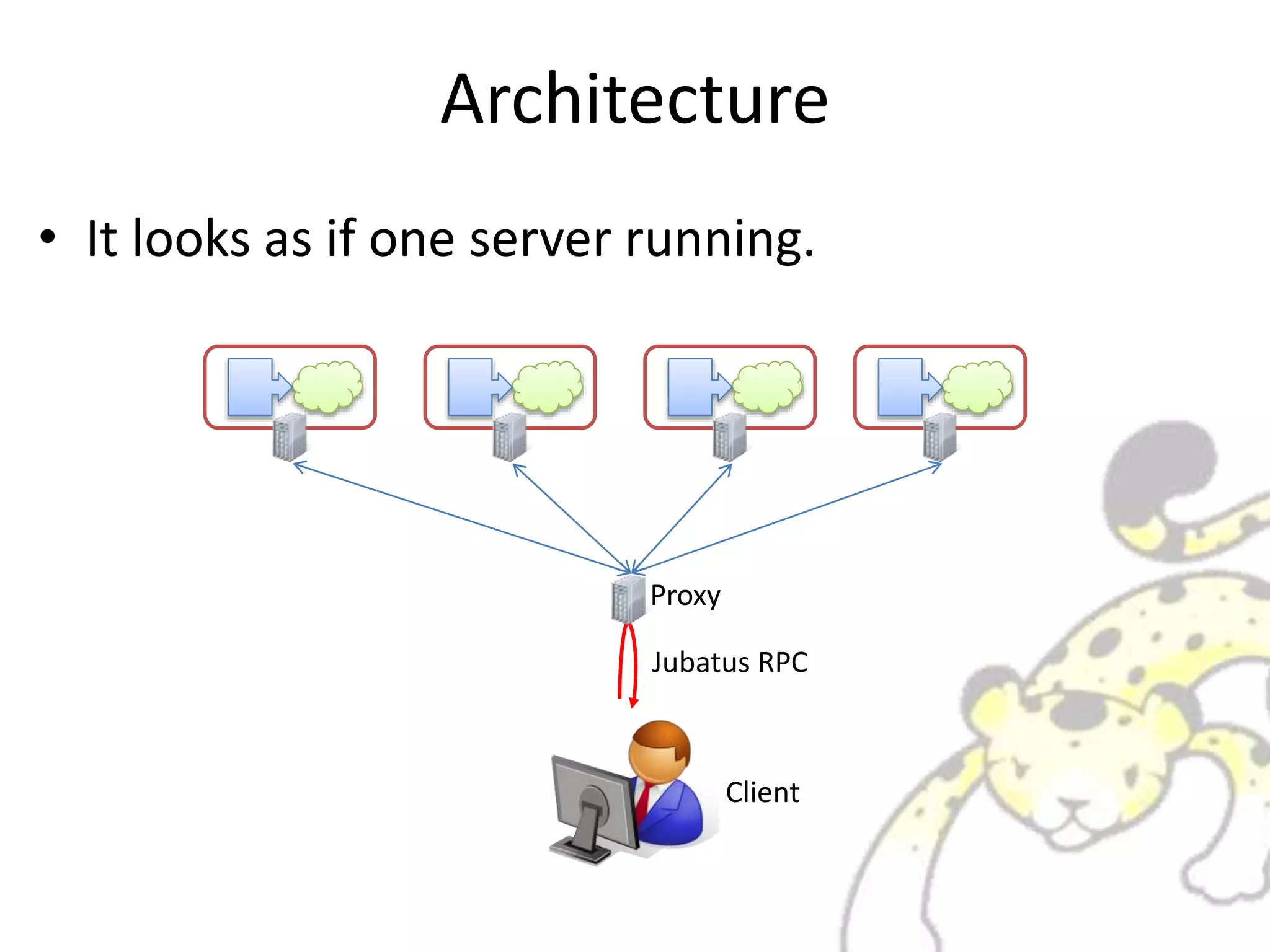
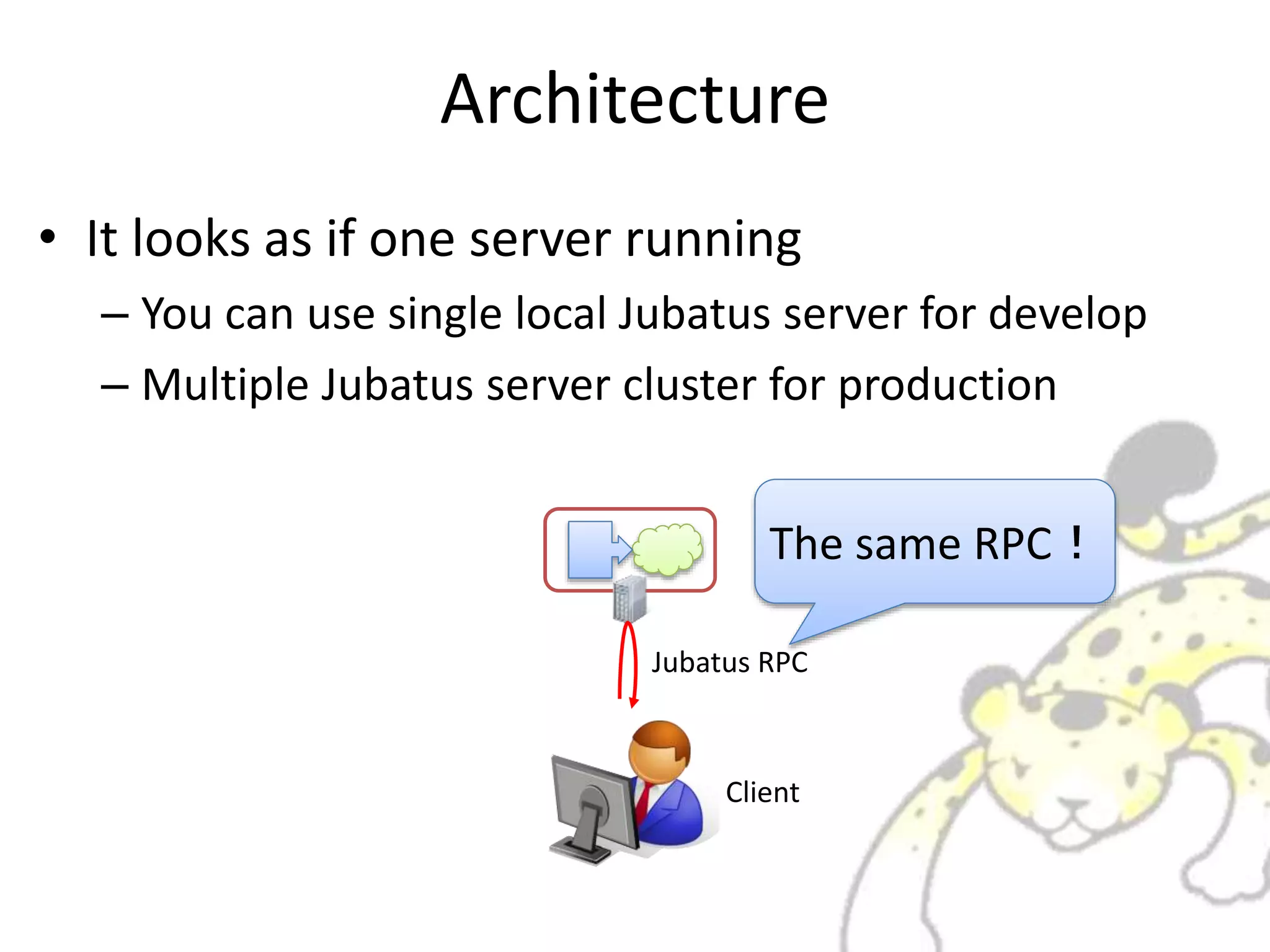
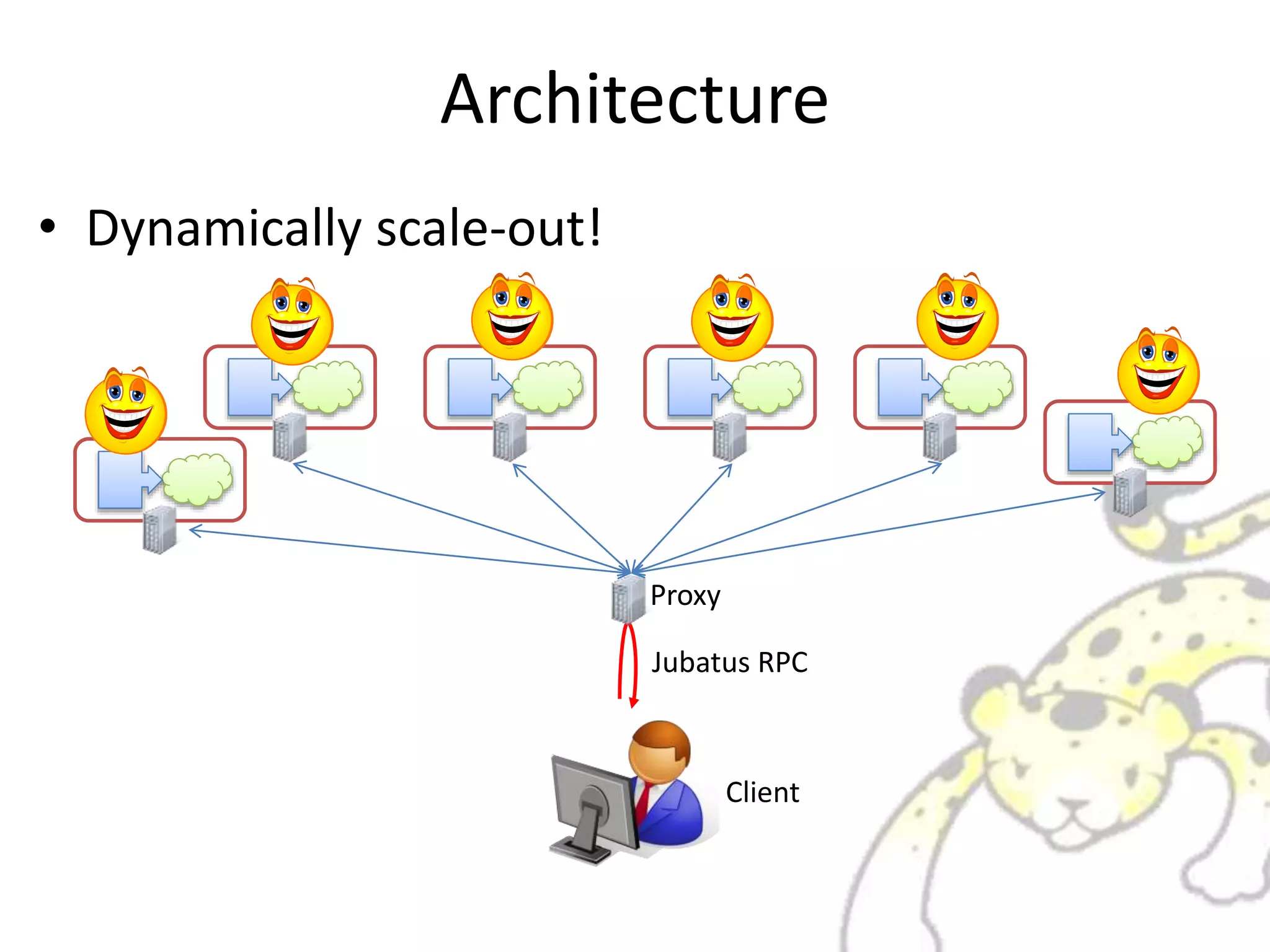
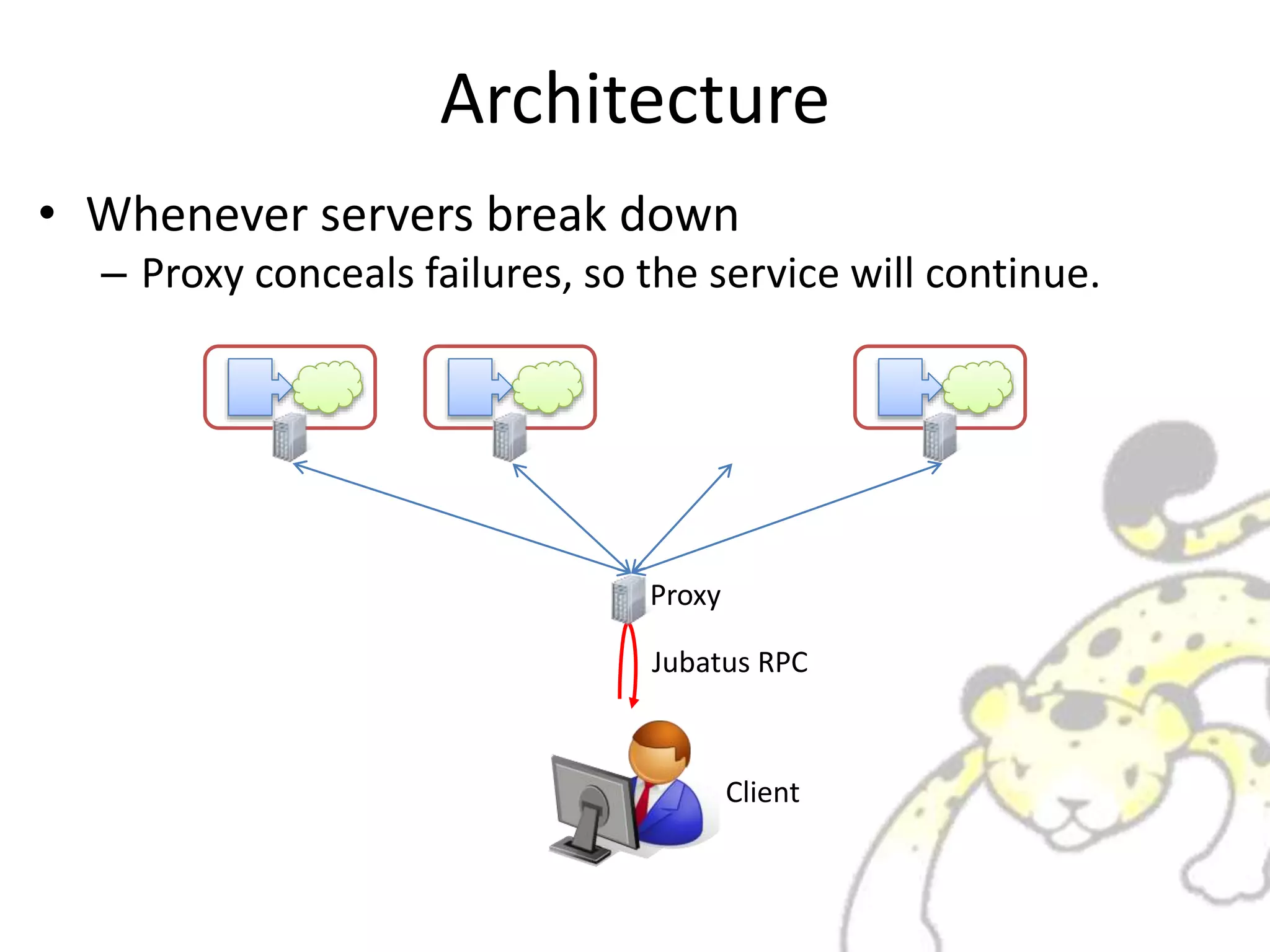
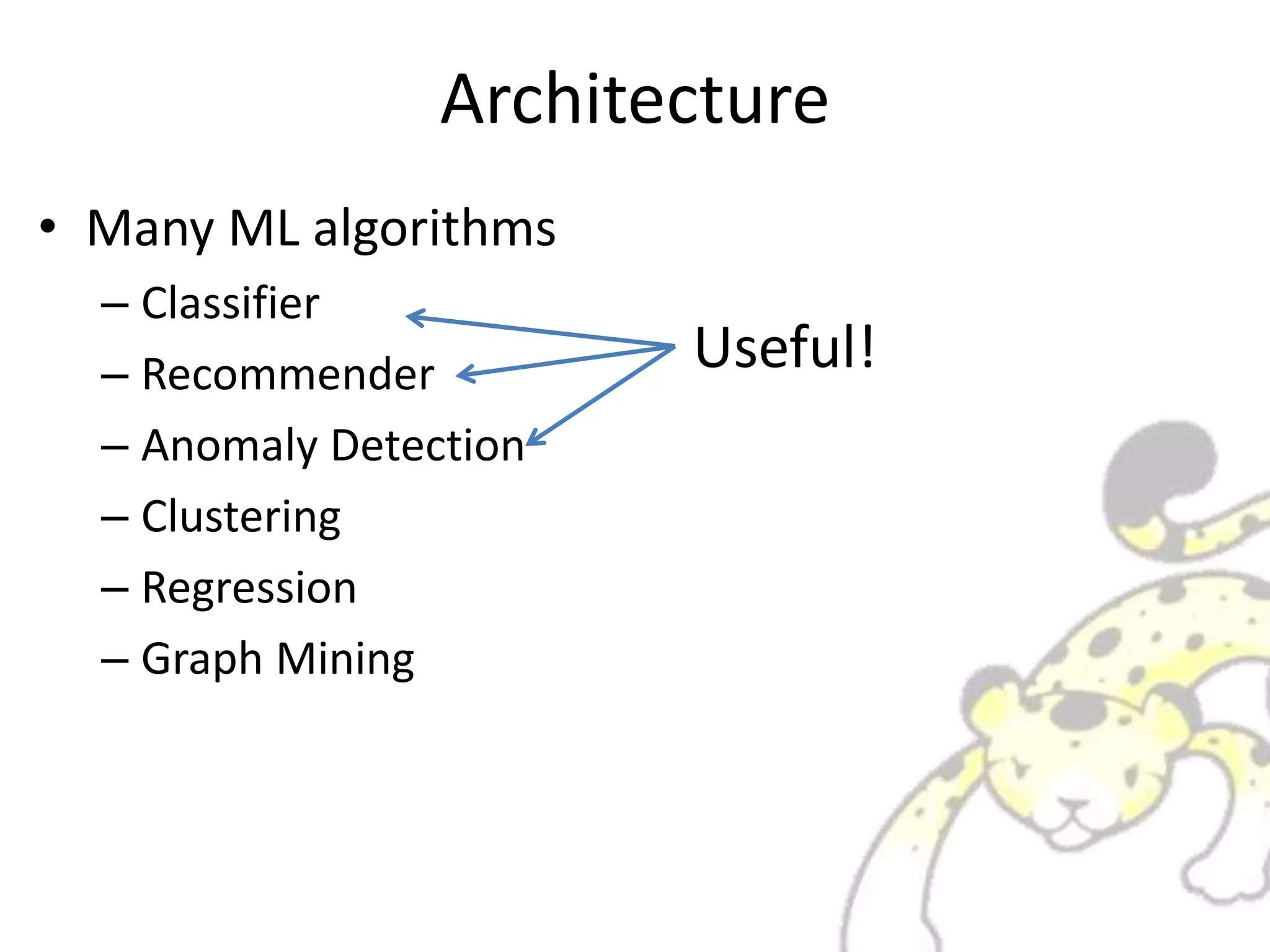
Jubatus is a distributed online machine learning framework that is distributed, fault tolerant, and allows for fixed time computation. It combines a machine learning model with a feature extractor. Jubatus uses a shared-everything architecture that allows it to be fast and fault tolerant. The architecture allows clients to access Jubatus through a single RPC interface even as the number of Jubatus servers scales out dynamically. Jubatus supports various machine learning algorithms including classification, recommendation, anomaly detection, clustering, and regression.



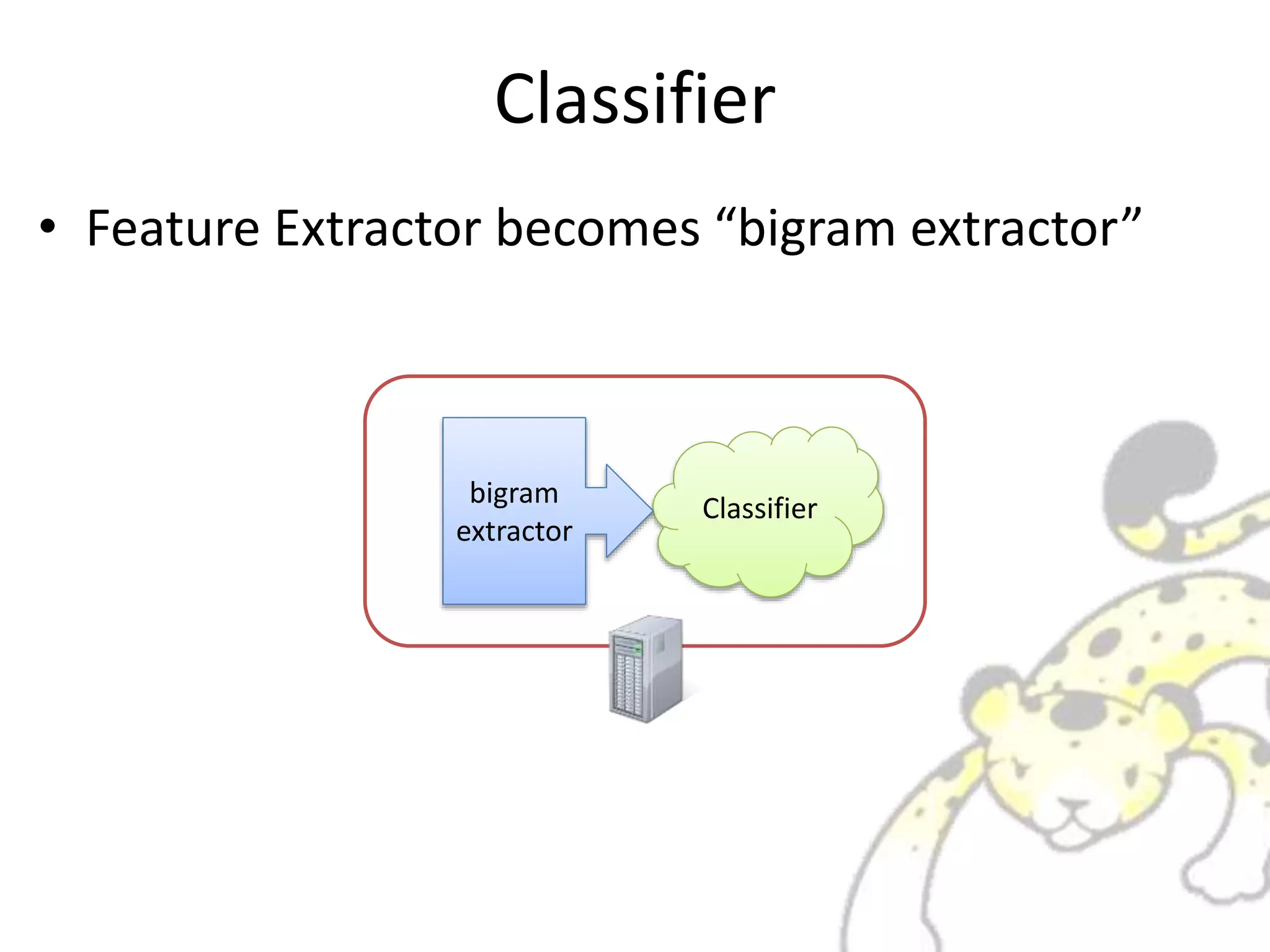
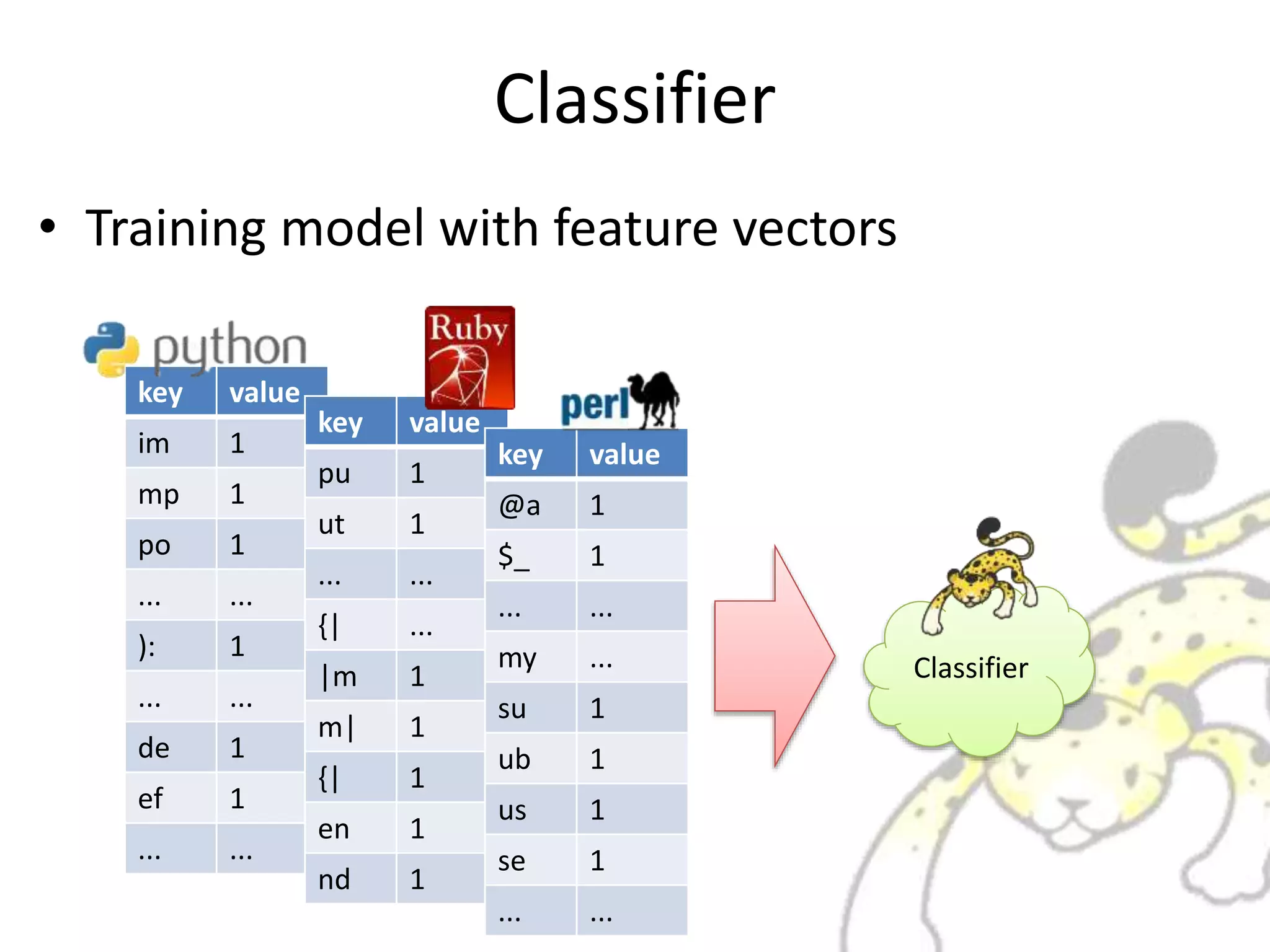
![Classifier
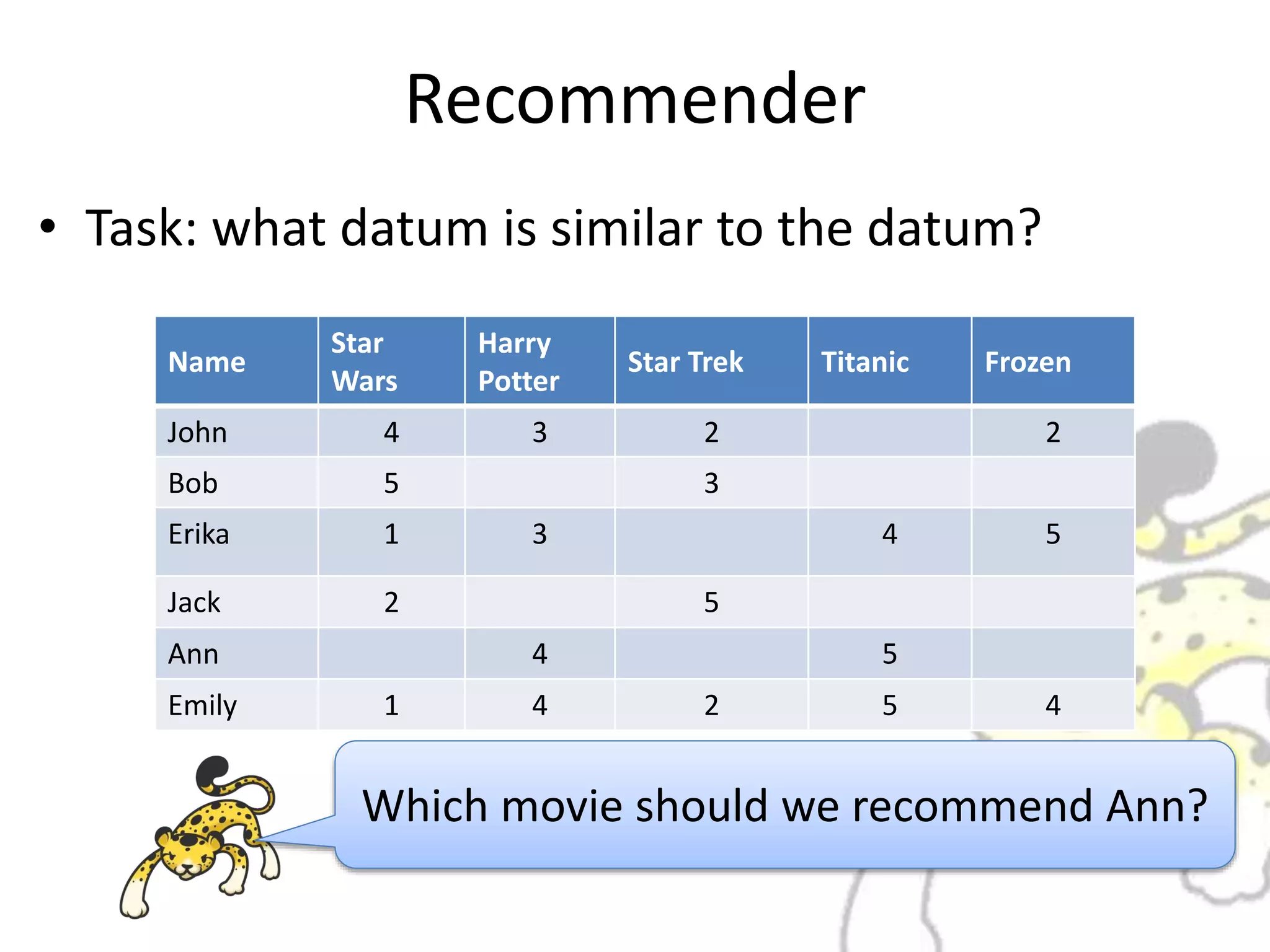
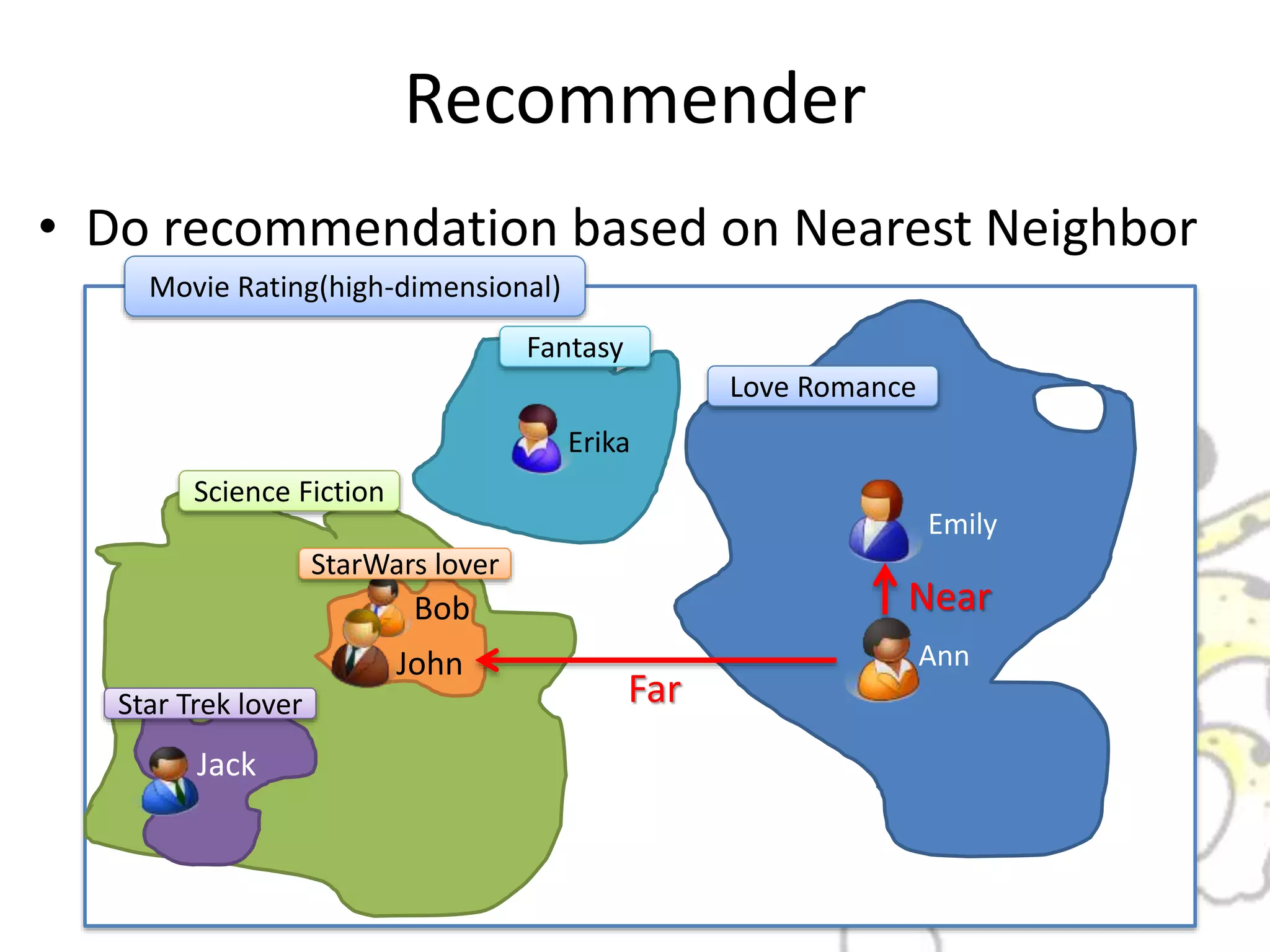
• Task: Classification of Datum
import sys
def fib(a):
if a == 1 or a == 0:
return 1
else:
return fib(a-1) + fib(a-2)
if __name__ == “__main__”:
print(fib(int(sys.argv[1])))
def fib(a)
if a == 1 or a == 0
1
else
return fib(a-1) + fib(a-2)
end
end
if __FILE__ == $0
puts fib(ARGV[0].to_i)
end
Sample Task: Classify what programming language used
It’s It’s](https://image.slidesharecdn.com/whatisjubatus-140606023057-phpapp02/75/What-is-jubatus-How-it-works-for-you-12-2048.jpg)
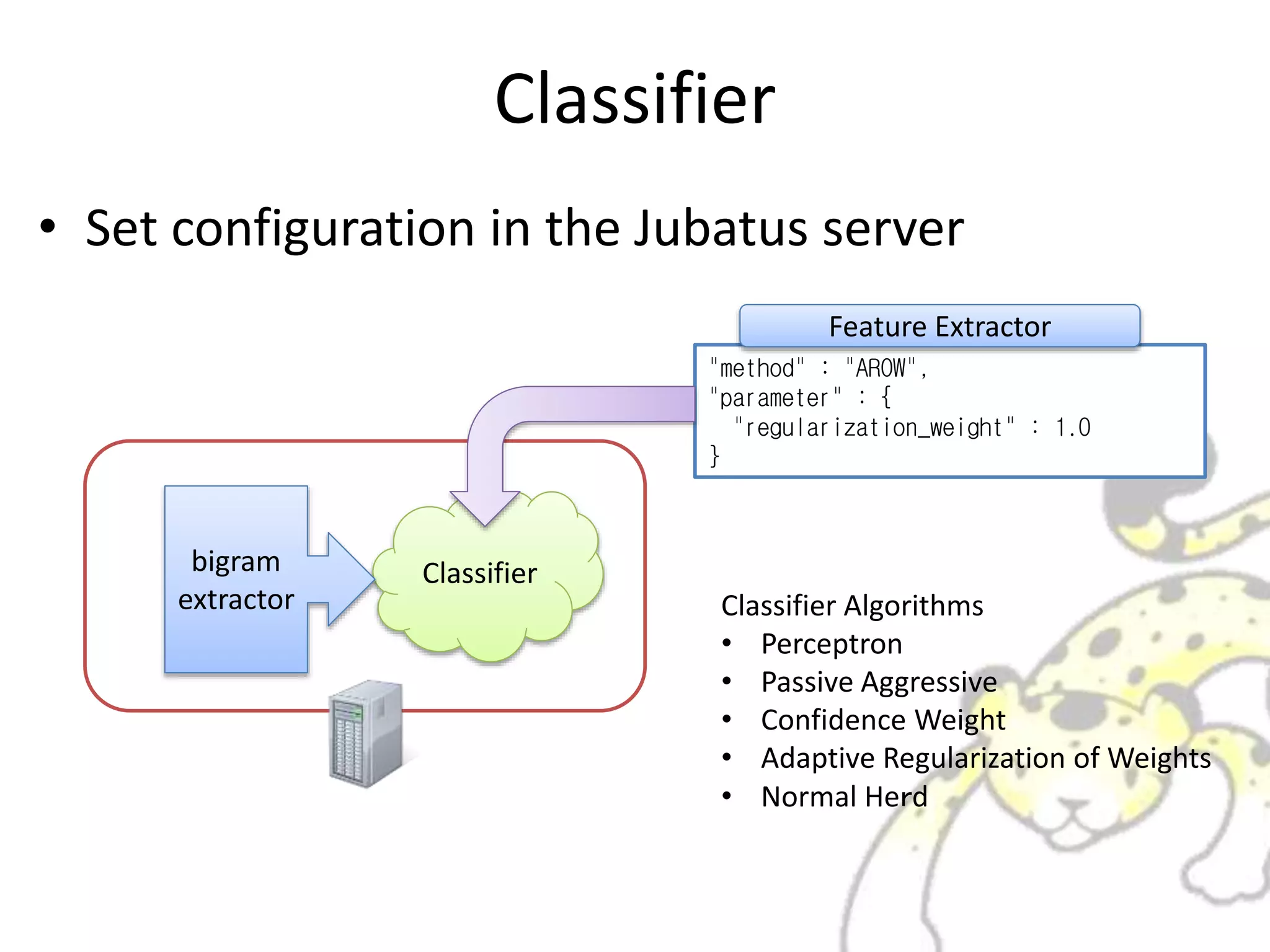
![Classifier
• Set configuration in the Jubatus server
ClassifierFreature
Extractor
"converter": {
"string_types": {
"bigram": {
"method": "ngram",
"char_num": "2"
}
},
"string_rules": [
{
"key": "*",
"type": "bigram",
"sample_weight": "tf",
"global_weight": "idf“
}
]
}
Feature Extractor](https://image.slidesharecdn.com/whatisjubatus-140606023057-phpapp02/75/What-is-jubatus-How-it-works-for-you-13-2048.jpg)
![Classifier
• Configuration JSON
– It does “feature vector design”
– very important step for machine learning
"converter": {
"string_types": {
"bigram": {
"method": "ngram",
"char_num": "2"
}
},
"string_rules": [
{
"key": "*",
"type": "bigram",
"sample_weight": "tf",
"global_weight": "idf“
}
]
}
setteings for extract feature from string
define function named “bigram”
original embedded function “ngram”
pass “2” to “ngram” to create “bigram”
for all data
apply “bigram”
feature weights based on tf/idf
see wikipedia/tf-idf](https://image.slidesharecdn.com/whatisjubatus-140606023057-phpapp02/75/What-is-jubatus-How-it-works-for-you-14-2048.jpg)
![Feature Extractor
• What bigram extractor does?
bigram
extractor
import sys
def fib(a):
if a == 1 or a == 0:
return 1
else:
return fib(a-1) + fib(a-2)
if __name__ == “__main__”:
print(fib(int(sys.argv[1])))
key value
im 1
mp 1
po 1
... ...
): 1
... ...
de 1
ef 1
... ...
Feature Vector](https://image.slidesharecdn.com/whatisjubatus-140606023057-phpapp02/75/What-is-jubatus-How-it-works-for-you-16-2048.jpg)
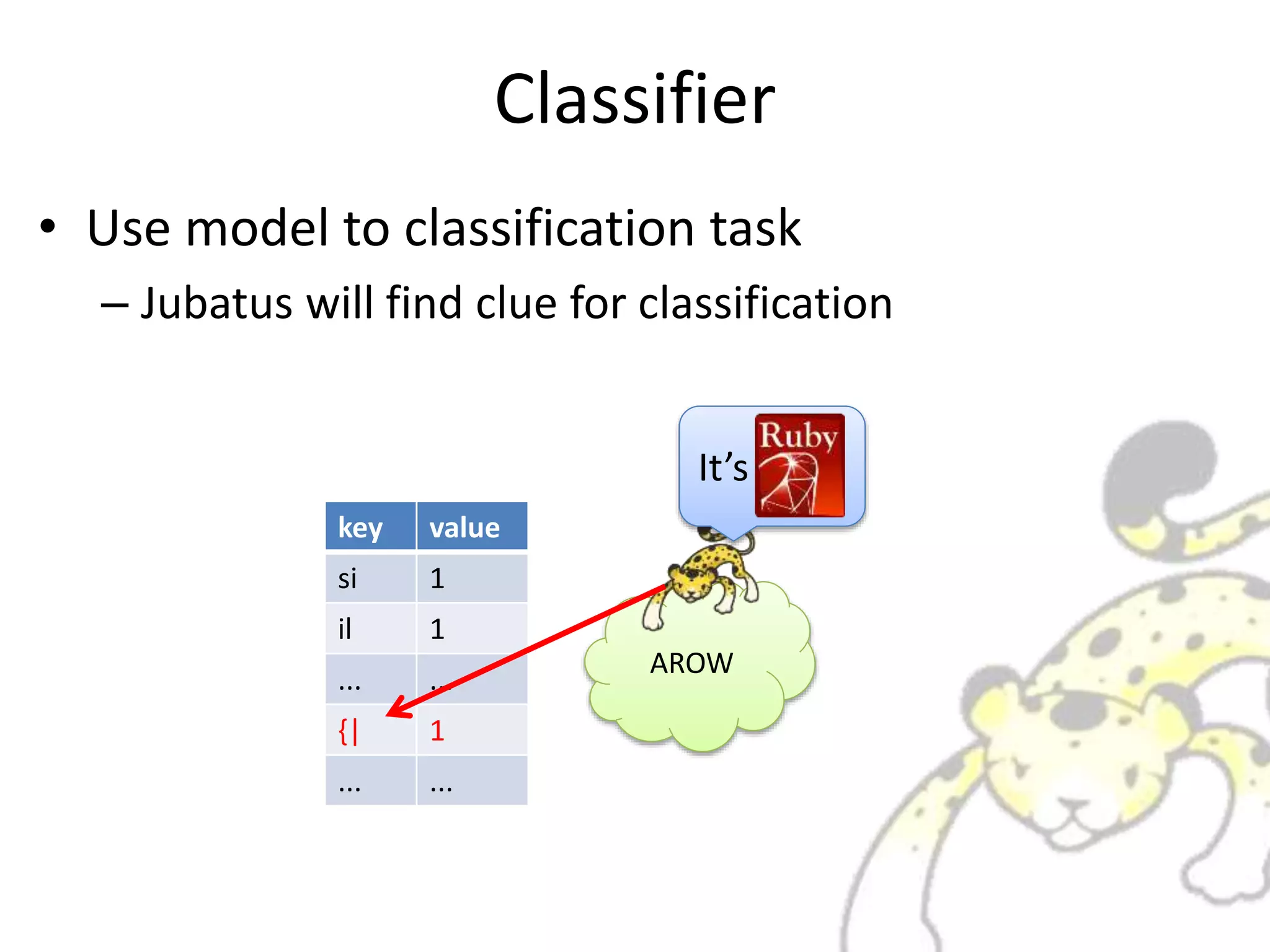
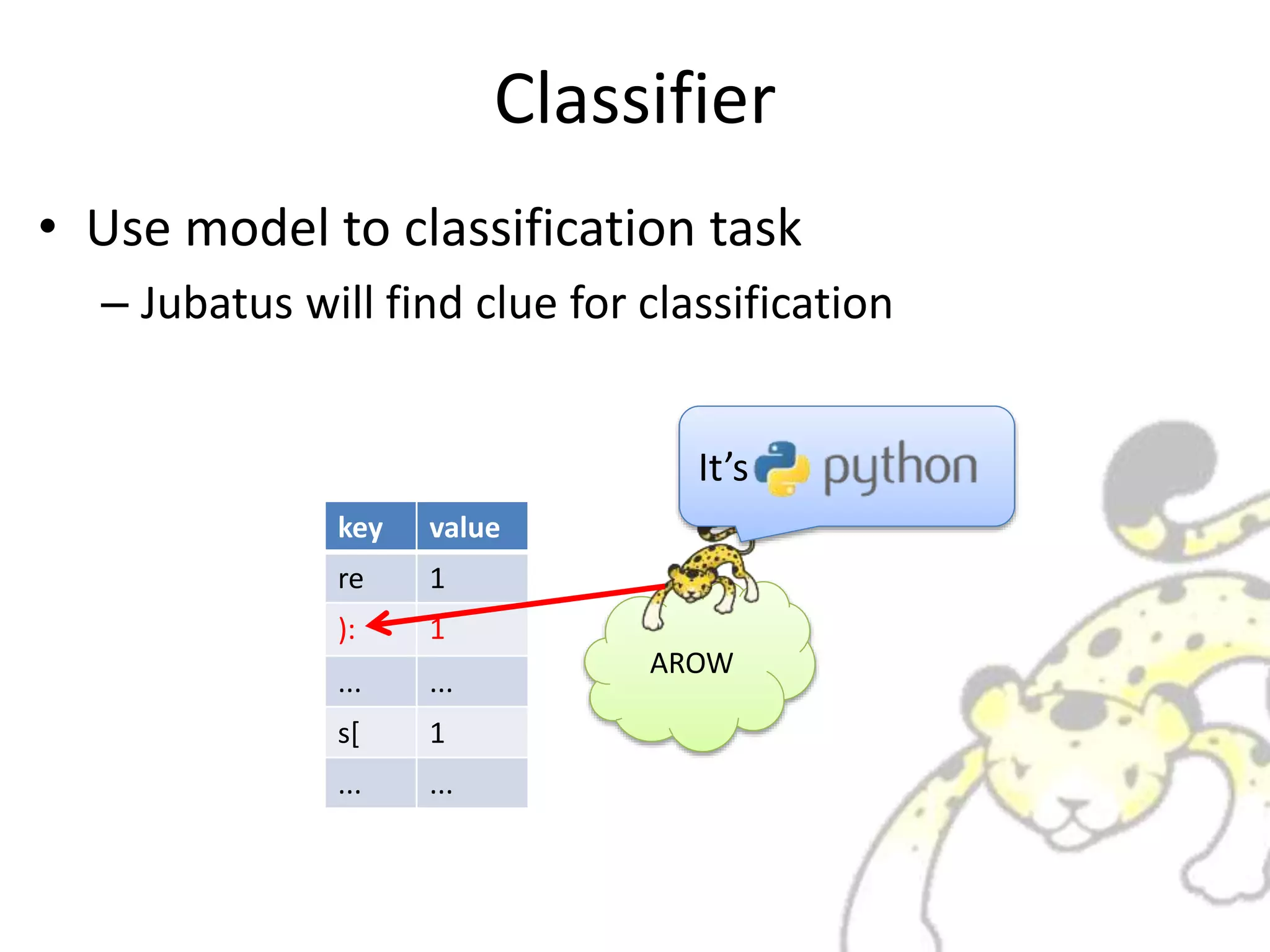
![Via RPC
• call feature extraction and classification from
client via RPC
AROWbigram
extractor
lang = client.classify([sourcecode])
import sys
def fib(a):
if a == 1 or a == 0:
return 1
else:
return fib(a-1) + fib(a-2)
if __name__ == “__main__”:
print(fib(int(sys.argv[1])))
key value
im 1
mp 1
po 1
... ...
): 1
... ...
de 1
ef 1
... ...
It may be](https://image.slidesharecdn.com/whatisjubatus-140606023057-phpapp02/75/What-is-jubatus-How-it-works-for-you-21-2048.jpg)