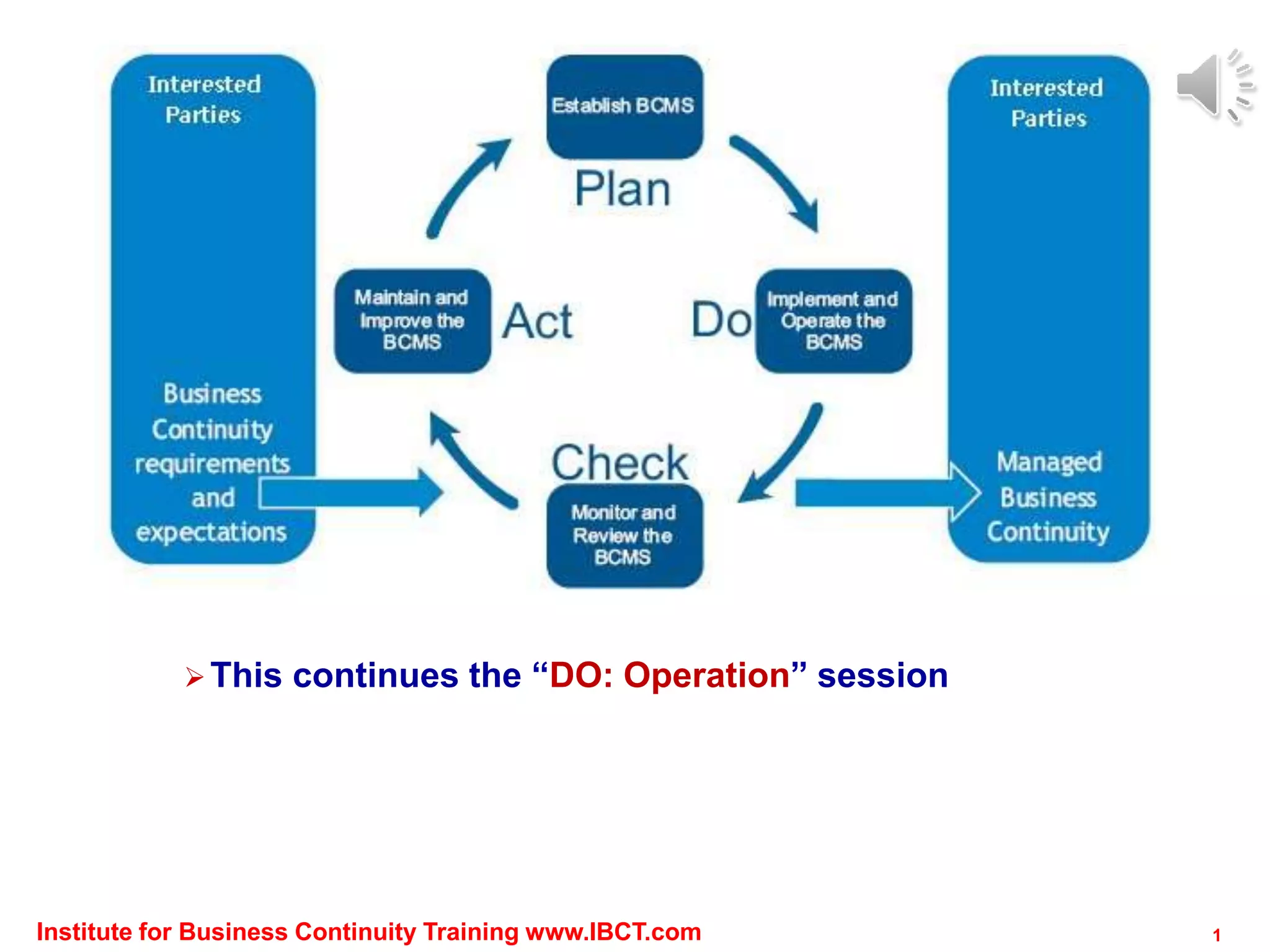
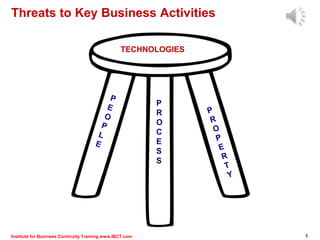
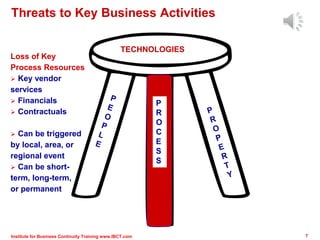
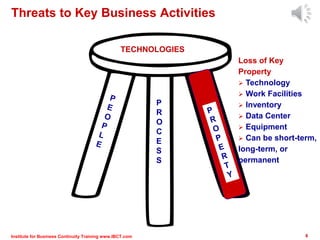
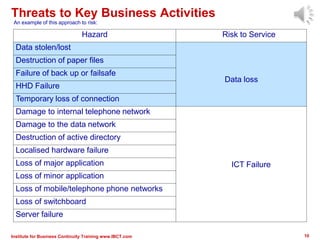
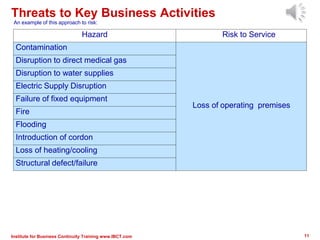
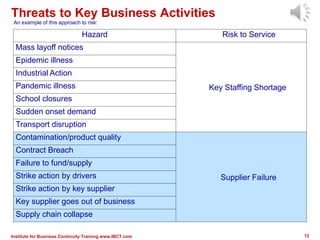
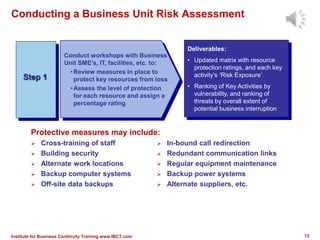
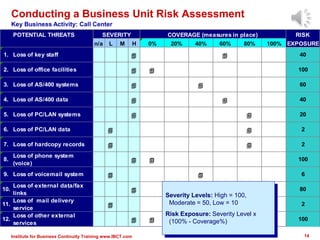
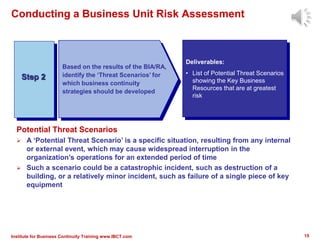
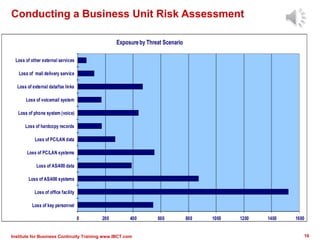
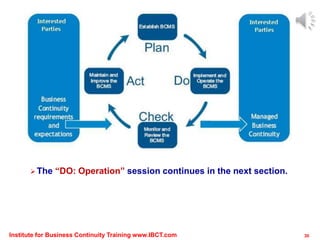
The document outlines a framework for conducting risk assessments in business continuity, focusing on evaluating threats to key business activities. It emphasizes the importance of a targeted vulnerability/threat assessment, identifying critical resources, and determining their risk exposure to ensure the continuity of operations. By employing an all-hazards approach, organizations can prioritize their resources and develop effective strategies to mitigate potential disruptions.